Why Exabeam
- Security Leaders
- Security Engineers
- Security Analysts

Analyst Corner

r-tec entscheidet sich für die Exabeam Security Operations Platform zur Unterstützung seiner SOC-, MDR- und Vorfallsreaktions-Services
- Exabeam Security Log Management
- Exabeam SIEM
Exabeam Fusion
- Exabeam Security Analytics
- Exabeam Security Investigation
- Cloud-scale Security Log Management
- Powerful Behavioral Analytics
- Automated Investigation Experience
- Exabeam Security Operations Platform
Featured Data Sheet

AI-driven Exabeam Fusion: Bring an end to your SIEM nightmares. It’s time for faster, easier, and more accurate threat detection, investigation, and response (TDIR). Exabeam Fusion applies AI and automation to security operations workflows for a holistic approach to combating cyberthreats, delivering the most effective TDIR. AI-driven detections pinpoint high-risk threats by learning normal behavior ... Read more »
- By Industry
- Financial Services
- Higher Education
- Manufacturing
- By Use Case
- Compromised Insider
- Malicious Insider
- External Threats
Featured Solution Brief

Exabeam Copilot
Exabeam Copilot revolutionizes the Exabeam Security Operations Platform with a generative AI experience, empowering security teams with powerful productivity and insights. Through natural language processing (NLP), security analysts and engineers can effortlessly create complex search queries, in almost any language, bypassing the need for advanced programming knowledge. This generative AI capability accelerates the training of ... Read more »
- Content Library
- The New CISO Podcast
- Exabeam CTF
- TEN18 by Exabeam
- InfoSec Trends
- Security Operations Center
- Incident Response
- SIEM Trends
- Company News
- New-Scale SIEM
- SIEM Security
- Information Security
- Event Logging
- Log Management
- Insider Threats
- MITRE ATT&CK
- Cloud Security
- GDPR Compliance
- PCI Compliance
- HIPAA Compliance
Featured Resource

Threat Detection, Investigation, and Response (TDIR): A Primer
Find a partner.
- Solution Providers
- Global Service Partners
- Tech Alliances
- MSSP & MDR Partners
- Become a Partner
- About the Partner Program
- Partner Portal
- Exabeam for Good
- Diversity and Inclusion
News and Events
- Press Releases
- Documentation
- GitHub Content Library
- Sales Inquiries
- General Inquiries
- Office Locations
Press Enter to search
- Gartner Magic Quadrant
- Product Portfolio
- Industry Solutions and Use Cases
- Product Features
- Exabeam Blog
Incident Response › Incident Response Plan 101: The 6 Phases, Templates, and Examples
Incident Response Plan 101: The 6 Phases, Templates, and Examples

Published March 07, 2022
Author --> Orion Cassetto
Reading time 10 mins
How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation.
What is an incident response plan.
An incident response plan is a set of tools and procedures that your security team can use to identify, eliminate, and recover from cybersecurity threats. It is designed to help your team respond quickly and uniformly against any type of external threat.
Incident response plans ensure that responses are as effective as possible. These plans are necessary to minimize damage caused by threats, including data loss, abuse of resources, and the loss of customer trust.
Need an incident response solution? Request an incident response demo .
In this article:
Why is an incident response plan important?
What are the incident response steps.
- What incident response planning typically includes
Incident response plan templates to get you started quickly
Incident response plan examples: learn from leading organizations, how to make an incident response plan successful, what are the key roles in an incident response plan.
- The next generation of incident response: Security Orchestration, Automation and Response (SOAR)
The Ponemon Institute’s Cost of Cyber Crime Study showed that the typical organization experiences an average of 145 security incidents per year and spends $13 million annually year to defend itself. An effective response process can act to significantly reduce these costs. Incident response planning also protects your company’s reputation. IDC found that 80% of consumers would take their business elsewhere if directly affected by a data breach. If a security breach is not handled properly, the company risks losing business, as well as investor and shareholder confidence.
Additional benefits of incident response plans include:
- Data protection — securing backups, ensuring sufficient identity and access management, and timely patching of vulnerabilities.
- Reputation reinforcement — Effective incident response shows a brand’s commitment to security and privacy, and can save a company’s reputation in the event of a breach.
- Cost reduction — According to a study by IBM , the average cost of a breach is $4.35 million. Incident response planning can significantly reduce this cost by limiting the damage caused by an attack.
According to the SANS Institute’s Incident Handlers Handbook, there are six steps that should be taken by the Incident Response Team, to effectively handle security incidents.
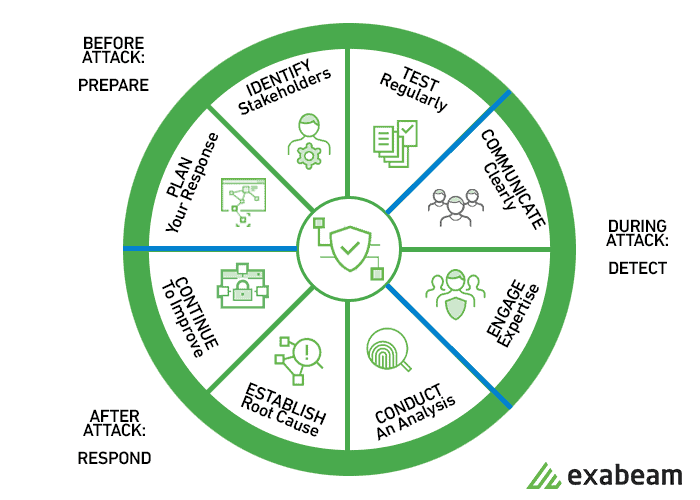
1. Preparation – Perform a risk assessment and prioritize security issues, identify which are the most sensitive assets, and which critical security incidents the team should focus on. Create a communication plan, document roles, responsibilities, and processes, and recruit members to the Cyber Incident Response Team (CIRT).
2. Identification – The team should be able to effectively detect deviations from normal operations in organizational systems, and when an incident is discovered, collect additional evidence, decide on the severity of the incident, and document the “Who, What, Where, Why, and How”.
3. Containment – Once the team identifies a security incident, the immediate goal is to contain the incident and prevent further damage:
- Short-term containment — for example, isolating network segments or taking down infected production servers and handing failover.
- Long-term containment — applying temporary fixes to affected systems to allow them to be used in production, while rebuilding clean systems.
4. Eradication – The team must identify the root cause of the attack, remove malware or threats, and prevent similar attacks in the future. For example, if a vulnerability was exploited, it should be immediately patched.
5. Recovery – The team brings affected production systems back online carefully, to ensure another incident doesn’t take place. Important decisions at this stage are from which time and date to restore operations, how to verify that affected systems are back to normal, and monitoring to ensure activity is back to normal.
6. Lessons Learned – This phase should be performed no later than two weeks from the end of the incident, to ensure the information is fresh in the team’s mind. The purpose of this phase is to complete documentation of the incident, investigate further to identify its full scope, understand where the response team was effective, and areas that require improvement.
Incident response planning typically includes:
- The organization’s incident response strategy and how it supports business objectives
- Roles and responsibilities involved in incident response
- Procedures for each phase of the incident response process
- Communication procedures within the incident response team, with the rest of the organization, and external stakeholders
- How to learn from previous incidents to improve the organization’s security posture
An incident response plan forms the basis of your incident response cycle:
Following are four detailed templates you can use to kick off your incident response planning:
TechTarget’s incident response plan template (14 pages) includes scope, planning scenarios, and recovery objectives; a logical sequence of events for incident response and team roles and responsibilities; notification, escalation and declaration procedures; and incident response checklists. Download the template
Thycotic’s incident response template (19 pages) includes roles, responsibilities and contact information, threat classification, actions to be taken during incident response, industry-specific and geographic-dependent regulations, and a response process, as well as instructions on how to customize the template to your specific needs. Download the template (requires registration)
Sysnet’s security incident response plan (11 pages) includes how to recognize an incident, roles and responsibilities, external contacts, initial response steps, and instructions for responding to several common incident types, such as malware and unauthorized wireless access. Download the template (requires registration)
California Government Department of Technology incident response plan (4 pages) includes a 17-step checklist for incident team members to follow, with reference to more detailed procedures for specific types of incidents (which you will have to create on your own). Download the template
When developing an incident plan, it is valuable to see actual examples of plans created by other organizations. Some of the examples won’t be applicable to your industry’s incident scenarios, but can provide some inspiration.
See examples of plans from the following organizations:
- Carnegie Mellon University — including definitions, roles and responsibilities, methodology, incident response phases, guidelines for insider threats and interaction with law enforcement, and documentation
- Tulane University — including scope, roles, and responsibilities, incident definitions, escalation levels and response stages per level of criticality
- Wright State University — including scope, response steps, usage of security tools, and an intrusion checklist
What are the key considerations for incident response?
An incident response plan should include the following elements to be effective:
- Senior management support — Management support will allow you to recruit the most qualified members for your response team, and create processes and information flows that will help you manage an incident effectively.
- Consistent testing — An incident response plan is not worth much if it’s only on paper: it must be put to the test. Conducting a planned (or even better, unplanned) security drill, running through the plan, and identifying weak spots will go a long way toward validating that the team is ready for a real incident.
- Balance between detail and flexibility — The plan must have specific, actionable steps the team can follow quickly when an incident occurs. At the same time, creating rigid processes leads to complexity and an inability to deal with unexpected scenarios. Create a detailed plan, but allow for flexibility to support a wide range of incidents. Updating the plan frequently can also help with flexibility — reviewing the plan every six months or so can help you account for new types of security issues and attacks that affect your industry.
- Clarify communication channels — The plan should make it clear who the incident team should communicate with, via which communication channels, and what information should be conveyed. This is a critical and sometimes overlooked part of the response process. For example, there should be clear guidelines on what level of detail should be communicated to IT management, senior management, affected departments, affected customers, and the press.
- Know your stakeholders — Who are the key roles within the organization who should care and be involved in a security incident? These might change depending on the type of incident and the organizational resources targeted. Stakeholders could include department managers, senior management, partners, customers, and legal.
- Keep the plan simple — A well-known management principle, “Keep it Simple, Stupid” (KISS), should also be applied to response plans. A complicated plan, even if very well thought out, is not likely to be accurately followed in real time. Keep details, steps, and procedures down to an absolute minimum, to ensure that the team can process and apply them to the incident as they enter the “fog of war.”
An incident response plan is not complete without a team that can carry it out — the Computer Security Incident Response Team (CSIRT). An incident response team is a group of people — either IT staff with some security training or full-time security staff in larger organizations — who collect, analyze, and act upon information from an incident.
They are the focal point of the incident, and are responsible for communicating with other stakeholders within the organization, and external parties such as legal counsel, press, law enforcement, affected customers, etc.
What is the relationship between an incident response plan and a disaster recovery plan?
An incident response plan should be complemented by a disaster recovery plan. The latter prescribes how an organization manages a catastrophic event such as a natural disaster or accidental loss of data. While an incident response plan focuses on identifying a security event and bringing it to closure, disaster recovery aims at bringing systems back online, subject to a Recovery Time Objective (RTO).
The next generation of incident response: Security Orchestration, Automation, and Response (SOAR)
There is no replacement for crafting an incident response plan and assigning dedicated individuals to be responsible for it. However, to make incident response more effective and make it possible to deal with more security incidents, a new category of tools has evolved that helps automate the response to security incidents.
Security Orchestration, Automation, and Response (SOAR) tools can:
- Integrate with other security tools, orchestrating them to enable a complex response to an attack
- Automate multi-step response procedures using security playbooks
- Support case management by recording all information related to a specific security incident, creating a complete event timeline, and helping analysts collaborate and add data and insights to the event
To see an example of an integrated security solution that includes SOAR as well as User and Entity Behavior Analytics (UEBA) and Security Information and Event Management (SIEM) capabilities, see Exabeam’s Incident Responder .
Learn more about Incident Response
- The Three Elements of Incident Response : Plan, Team, and Tools
- The Complete Guide to CSIRT Organization: How to Build an Incident Response Team
- 10 Best Practices for Creating an Effective Computer Security Incident Response Team (CSIRT)
- How to Quickly Deploy an Effective Incident Response Policy
- IT Security : What You Should Know
- Incident Response Steps : 6 Tips for Responding to Security Incidents
- Beat Cyber Threats with Security Automation
- IPS Security : How Active Security Saves Time and Stops Attacks in their Tracks
Need an incident response solution? Click here for an incident response demo .
Tags: Incident Response ,
Similar Posts

Spooky Season Brings a Toe-Curling Vulnerability

Defending Against Ransomware: How Exabeam Strengthens Cybersecurity

Why Airlines are Prone to Cyberattacks
Recent Posts

Centralized TDIR From Exabeam With New Threat Center, Automation Management, and Exabeam Copilot

Aligning With DORA for Financial Entities in the EU

Strengthening Cyber Defenses: Innovative Solutions for TDIR Challenges
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!
Privacy Overview
- UpGuard BreachSight
- UpGuard Vendor Risk
UpGuard Trust Exchange
Product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
What is an incident response plan.

Abi Tyas Tunggal
An incident response plan is a set of written instructions that outline your organization's response to data breaches , data leaks , cyber attacks and security incidents.
Incident response planning contains specific directions for specific attack scenarios, avoiding further damages, reducing recovery time and mitigating cybersecurity risk .
Incident response procedures focus on planning for security breaches and how organization's will recover from them.
Without a formal IR plan in place, organizations may not detect attacks or may not know what to do to contain, clean up and prevent attacks when detected.
Remember, techniques like IP attribution aren't always helpful and your organization may not be able to recover stolen data and needs to know what it will do in that event.
Why is Incident Response Planning Important?
Incident response planning is important because it outlines how to minimize the duration and damage of security incidents, identifies stakeholders, streamlines digital forensics , improves recovery time, reduces negative publicity and customer churn.
Even small cybersecurity incidents, like a malware infection, can snowball into bigger problems that ultimately lead to data breaches , data loss and interrupted business operations.
A proper incident response process allows your organization to minimize losses, patch exploitable vulnerabilities , restore affected systems and processes and close the attack vector that was used.
Incident response encompasses preparation for unknown and known cyber threats , reliably identifying root causes of security incidents and post-incident disaster recovery.
It allows organizations to establish best practices for incident handling and develop a communication plan that may involve notifying law enforcement, employees and staff.
Incident response is a crucial component of preventing future incidents and running an organization that processes sensitive data like personally identifiable information (PII) , protected health information (PHI) or biometrics .
Every security event can have a short term and long term impact on your organization. According to IBM and the Ponemon Institute the average cost of a data breach in 2022 was $4.35 million.
Beyond the cost, business continuity, customer loyalty and brand protection are massive concerns, especially as organizations increasingly rely on third-party vendors .
While it's impossible to remove all security issues, an effective incident response process can mitigate the largest cybersecurity risks .
Learn how to create an Incident Response Plan >
Who is Responsible for Incident Response Planning?
Organizations should form a computer security incident response team (CSIRT) who is responsible for analyzing, categorizing and responding to security incidents.
Incident response teams can include:
- Incident response manager: oversees and prioritizes actions during detection, containment and recovery of an incident. They may also be required to convey high-severity incidents to the rest of the organization, customers, law enforcement, regulations and the public where applicable.
- Security analysts: support and work directly with affect resources, as well as implementing and maintaining technical and operational controls.
- Threat researchers: provide threat intelligence and context around security incidents. They may use third-party tools and the Internet to understand current and future threats. Organizations will often outsource this function if the expertise does not exist in-house. If this is your organization, look for tools or services that can automatically monitor for leak credentials, data leaks and third-party and fourth-party vendor security posture .
That said, effective incident response relies on cross-functional incident response team members from all parts of the organization.
Without stakeholders from senior leadership, legal, human resources, IT security and public relations, incident response teams can prove ineffective.
Senior leadership support is particularly necessary to gather necessary resources, funding, staff and time from different teams. This may be a Chief Information Security Officer (CISO) or Chief Information Officer (CIO) at a large organization or even the CEO or a board member at smaller organizations.
Legal counsel can help the organization understand which data breaches must be reported to regulators and customers, as well as advice around liability for third-party vendor data breaches .
Where an incident is from an insider threat , human resources can assist with removal of staff and access credentials.
Finally, public relations are essential to ensure an accurate, consistent and truthful message is communicated to the regulators, media, customers, shareholders and other stakeholders.
What are the Different Types of Security Incidents?
There are many types of security incidents and ways to classify them. This is largely an organizational decision, what is considered critical at one organization may be minor at another. That said, there are a range of common cyber incidents every organization should be aware of and plan for:
- Ransomware and other types of malware
- Man-in-the-middle attacks
- Social engineering like phishing and spear phishing
- Exploits of CVE -listed vulnerabilities
- Corporate espionage
- OPSEC failures
- Data breaches
- Email spoofing
- Domain hijacking
- Typosquatting
- Denial of service (DoS)
Each of these security incidents is common enough to warrant a formal incident response process and recovery plan. Security analysts need to be aware that even small incidents can open up new attack vectors that lead to larger attacks. This is why real-time threat intelligence is so important.
Another important, often overlooked security incident is those that involve your third-party vendors and their vendors. This is known as third-party risk and fourth-party risk .
Security teams need to understand the impact that vendors can have on their organization's security posture . Even if third-parties aren't conducting critical business activities, they still represent significant vendor risk .
This is because they may have access to sensitive data or property, and your organization may be accountable for their security failures.
Avoiding incidents is as much about vendor risk management as it is about managing your internal information security , data security , network security and information risk management .
Look for vendors with SOC 2 assurance, ask to see their information security policy and develop a vendor management policy that contains a third-party risk management framework that allows your organization to easily perform cybersecurity risk assessments on current and potential vendors.
What Tools are Available for Incident Response Teams?
There are tools and industry standards that can be helpful to incident response teams. Tools can be split into three categories:
For prevention, an organization may employ a security scanner and a data leak detection tool to prevent leaked credentials and other sensitive data being exposed due to poor S3 security or a lack of configuration management .
Detection could be covered by antivirus software, network intrusion detection systems , security incident and event management (SIEM) software or a vulnerability scanner that checks CVE .
A common response tool is remediation workflows where incident response teams can request remediation, track and close third-party attack vectors .
What is the Industry Standard for Incident Response?
There are two frameworks that have become industry standard, the NIST Incident Response Process and the SANS Incident Response Process.
The NIST Incident Response Process is four steps:
- Preparation
- Detection and analysis
- Containment, eradication and recovery
- Post-incident activity
Whereas, the SANS Incident Response Process is six:
- Identification
- Containment
- Eradication
- Lessons learned
As you can see, both NIST and SANS have all the same components and flow with different verbiage and clustering.
Whether you follow NIST, SANS or another incident response plan template, your IR plan should:
- Provide an overview
- Identify and describe roles and responsibilities
- Be tailored to specific business risks and needs
- Outline the current state of information security , data security and network security
- Have clear detection and identification procedures
- Specify tools, technologies and resources needed for containment and eradication
- Outline recovery and follow-up tasks
- Have a communication plan
- Be well tested
- Have version control or a section to outline when and who made revisions
What are the Metrics Incident Response Teams Should be Measured Against?
Incident response is like any aspect of an organization, what gets measured gets managed. Ongoing management includes setting and measuring incident response goals, as well as periodically testing the incident response plan in tabletop exercises to ensure that all stakeholders are comfortable with their duties and responsibilities.
Common metrics include:
- Your security rating
- Competitor security ratings
- Number of vendors
- Average vendor security rating
- Distribution of vendor security ratings
- Lowest rated vendors
- Least improved vendors
- Highest rated vendors
- Most improved vendors
- Number of security questionnaires sent
- Number of security questionnaires received
- Vendor risks remediated
- Number of incidents detected
- Number of incidents missed
- Number of incidents requiring actions
- Number of repeat incidents
- Number of known attack vectors
- Average remediation time
- Number of data breaches and data leaks
- Average vendor security posture
- Number of stakeholders present in incident response plan review meetings
- Number of stakeholders present in incident response plan tabletop exercises
- Possible procurement of cybersecurity software, e.g. software to automate vendor risk management
- Other security initiatives, e.g. cybersecurity awareness training, website risks, email security, network security , malware and brand protection
What is the Difference between an Incident Response Plan and Business Continuity Plan?
While an incident response plan and business continuity plan have a similar goals – minimize the impact of unforeseen events and keep the business running – incident response planning generally has a higher level of visibility.
Incident response plans are concerned with security incidents and breaches that impact information security, network security and data security.
Business continuity plans focus on creating a system to prevent and recover from potential threats to a company, whether that be personnel, assets or natural disasters.
This is why most organizations have two seperate documents for incident response and business continuity, which often reference each other.
How UpGuard Scale Your Organization's Incident Response Team by Detecting Data Leaks and Preventing Third-Party Breaches
UpGuard BreachSight can help monitor for DMARC, combat typosquatting , prevent data breaches and data leaks , avoiding regulatory fines and protecting your customer's trust through cyber security ratings and continuous exposure detection.
UpGuard Vendor Risk can minimize the amount of time your organization spends managing third-party relationships by automating vendor questionnaires and continuously monitoring your vendors' security posture over time while benchmarking them against their industry.
Reviewed by

Kaushik Sen
Ready to see upguard in action, join 27,000+ cybersecurity newsletter subscribers.
Related posts
The top cybersecurity websites and blogs of 2023, 14 cybersecurity metrics + kpis you must track in 2024, what are security ratings cyber performance scoring explained, how to prevent data breaches in 2024 (highly effective strategy).

Why is Cybersecurity Important?
What is typosquatting (and how to prevent it).
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
- Skip to content
- Skip to search
- Skip to footer
What Is an Incident Response Plan for IT?
What does an incident response plan do?
An incident response plan is a set of instructions to help IT staff detect, respond to, and recover from network security incidents. These types of plans address issues like cybercrime, data loss, and service outages that threaten daily work.
- Incident response (1:22)
- Network security checklist
Contact Cisco
- Get a call from Sales
Call Sales:
- 1-800-553-6387
- US/CAN | 5am-5pm PT
- Product / Technical Support
- Training & Certification
A sufficient incident response plan offers a course of action for all significant incidents. Some incidents lead to massive network or data breaches that can impact your organization for days or even months. When a significant disruption occurs, your organization needs a thorough, detailed incident response plan to help IT staff stop, contain, and control the incident quickly. For physical disruptors, such as natural disasters and flooding, create a disaster recovery plan .
What is an incident recovery team?
An incident recovery team is the group of people assigned to implement the incident response plan. Generally, these are members of the IT staff who collect, preserve, and analyze incident-related data. Your IT staff may need to work with lawyers and communications experts to make sure that legal obligations are met.
Why do you need an incident response plan?
If your network hasn’t been threatened yet, it will be. If it has, then you know the chaos that can follow a cyber attack. Whether a threat is virtual (security breaches) or physical (power outages or natural disasters), losing data or functionality can be crippling. An incident response plan and a disaster recovery plan help you mitigate risk and prepare for a range of events.
How can you be sure your network is ready for a disaster?
Your network will never be 100 percent secure, so you must prepare both your network and your employees for crises to come. In addition to an incident response plan, you need a thorough disaster recovery plan that can mitigate the damage caused by a disaster.
Are there tools that help automate an incident response plan?
Cisco Umbrella Investigate helps to automate many of the most common steps in an incident response. Investigate's rich threat intelligence adds the security context needed to uncover and predict threats.
Follow the five steps below to maintain business continuity.
How to create an incident response plan
1. determine the critical components of your network.
To protect your network and data against major damage, you need to replicate and store your data in a remote location. Because business networks are expansive and complex, you should determine your most crucial data and systems. Prioritize their backup, and note their locations. These actions will help you recover your network quickly.
2. Identify single points of failure in your network and address them
Just as you should back up your data, you should have a plan B for every critical component of your network, including hardware, software, and staff roles. Single points of failure can expose your network when an incident strikes. Address them with redundancies or software failover features. Do the same with your staff. If a designated employee can’t respond to an incident, name a second person who can take over. By having backups and fail-safes in place, you can keep incident response and operations in progress while limiting damage and disruption to your network and your business."
3. Create a workforce continuity plan
During a security breach or a natural disaster, some locations or processes may be inaccessible. In either case, the top priority is employee safety. Help ensure their safety and limit business downtime by enabling them to work remotely. Build out infrastructure with technologies such as virtual private networks (VPNs) and secure web gateways to support workforce communication.
4. Create an incident response plan
Draw up a formal incident response plan, and make sure that everyone, at all levels in the company, understands their roles.
An incident response plan often includes:
- A list of roles and responsibilities for the incident response team members.
- A business continuity plan.
- A summary of the tools, technologies, and physical resources that must be in place.
- A list of critical network and data recovery processes.
- Communications, both internal and external.
5. Train your staff on incident response
Only IT may need to fully understand the incident response plan. But it is crucial that everyone in your organization understands the importance of the plan. After you’ve created it, educate your staff about incident response. Full employee cooperation with IT can reduce the length of disruptions. In addition, understanding basic security concepts can limit the chances of a significant breach.
Connect with us
- All Cisco Secure Products
- Secure Endpoint
- Secure Firewall
- Cisco SecureX threat response
- Cisco Umbrella
- Breach Defense
- Latest Cybersecurity Reports
Related network security topics
- What Is Vulnerability Management?
- What Is Network Security?
- What Is a Cybersecurity Specialist?
- What Is Cyber Insurance?
- What Is Threat Prevention?
- Network Security Checklist
- What Is Machine Learning in Security?
- What Is a Data Breach?
- What Is Disaster Recovery?
Follow Cisco Secure


Incident response (sometimes called cybersecurity incident response) refers to an organization’s processes and technologies for detecting and responding to cyberthreats, security breaches or cyberattacks. A formal incident response plan enables cybersecurity teams to limit or prevent damage.
The goal of incident response is to prevent cyberattacks before they happen, and to minimize the cost and business disruption resulting from any cyberattacks that occur.
Ideally, an organization defines incident response processes and technologies in a formal incident response plan (IRP) that specifies exactly how different types of cyberattacks should be identified, contained, and resolved. An effective incident response plan can help cybersecurity teams detect and contain cyberthreats and restore affected systems faster, and reduce the lost revenue, regulatory fines, and other costs associate with these threats. IBM’s Cost of a Data Breach 2022 Report found that organizations with incident response teams and regularly tested incident response plans had an average data breach cost USD 2.66 million lower than that of organizations without incident response teams and IRPs.
Gain insights to prepare and respond to cyberattacks with greater speed and effectiveness with the IBM Security X-Force Threat Intelligence Index.
Register for the Cost of a Data Breach report
A security incident, or security event, is any digital or physical breach that threatens the confidentiality, integrity, or availability or an organization’s information systems or sensitive data. Security incidents can range from intentional cyberattacks by hackers or unauthorized users, to unintentional violations of security policy by legitimate authorized users.
Some of the most common security incidents include:
- Phishiing and social engineering
- DDoS attacks
- Supply chain atttacks
- Insider threats
Ransomware. Ransomware is a type of malicious software, or malware, that locks up a victim's data or computing device and threatens to keep it locked—or worse—unless the victim pays the attacker a ransom. According to IBM's Cost of a Data Breach 2022 report, ransomware attacks rose by 41 percent between 2021 and 2022.
Learn more about ransomware .
Phishing and social engineering. Phishing attacks are digital or voice messages that try to manipulate recipients into sharing sensitive information, download malicious software, transferring money or assets to the wrong people, or take some other damaging action. Scammers craft phishing messages to look or sound like they come from a trusted or credible organization or individual—sometimes even an individual the recipient knows personally.
Phishing is the most costly and second most common cause of data breaches, according to IBM's Cost of a Data Breach 2022 report. It’s also the most common form of social engineering—a class of attack that hacks human nature, rather than digital security vulnerabilities, to gain unauthorized access to sensitive personal or enterprise data or assets.
Learn more about social engineering .
DDoS attacks. In a distributed denial-of-service (DDoS) attack, hackers gain remote control of large numbers of computers and use them to overwhelm a target organization’s network or servers with traffic, making those resources unavailable to legitimate users.
Learn more about DDoS attacks .
Supply chain attacks. Supply chain attacks are cyberattacks that infiltrate a target organization by attacking its vendors—for example, by stealing sensitive data from a supplier’s systems, or by using a vendor’s services to distribute malware. In July 2021, cybercriminals took advantage of a flaw in Kaseya's VSA platform (link resides outside ibm.com) to spread ransomware to customers under the guise of a legitimate software update. Even though supply chain attacks are increasing in frequency, only 32 percent of organizations have incident response plans prepared for this particular cyberthreat, according to IBM's 2021 Cyber Resilient Organization Study.
Learn more about supply chain security.
Insider threats. There are two types of insider threats. Malicious insiders are employees, partners, or other authorized users who intentionally compromise an organization’s information security. Negligent insiders are authorized user who unintentionally compromise security by failing to follow security best practices—by, say, using weak passwords, or storing sensitive data in insecure places.
Learn more about insider threats .
Incident response planning
As noted previously, an organization’s incident response efforts are guided by an incident response plan. Typically these are created and executed by a computer security incident response team (CSIRT) made up of stakeholders from across the organization—the chief information security officer (CISO), security operations center (SOC) and IT staff, but also representatives from executive leadership, legal, human resources, regulatory compliance, and risk management.
An incident response plan usually includes
- The roles and responsibilities of each member of the CSIRT;
- The security solutions—software, hardware, and other technologies—to be installed across the enterprise.
- A business continuity plan outlining procedures for restoring critical affected systems and data as quickly as possible in the event of an outage;
- A detailed incident response methodology that lays out the specific steps to be taken at each phase of the incident response process, and by whom;
- A communications plan for informing company leaders, employees, customers, and even law enforcement about incidents;
- Instructions for documenting for collecting information and documenting incidents for post-mortem review and (if necessary) legal proceedings.
It’s not uncommon for the CSIRT to draft different incident response plans for different types of incidents, as each type may require a unique response. According to the IBM® 2021 Cyber Resilient Organization Study , most organizations have specific incident response plans pertaining to DDoS attacks, malware and ransomware, and phishing, and nearly half have plans for insider threats.
Some organizations supplement in-house CSIRTs with external partners providing incident response services. These partners often work on retainer, assist with various aspects of the incident management process, including preparing and executing IRPs.
The incident response process
Most IRPs also follow the same general incident response framework based on incident response models developed by the SANS Institute, the National Institute of Standards and Technology (NIST), and the Cybersecurity and Infrastructure Agency (CISA).
Preparation. This first phase of incident response is also a continuous one, to make sure that the CSIRT always has the best possible procedures and tools in place to respond to identify, contain, and recover from an incident as quickly as possible and within minimal business disruption.
Through regular risk assessment the CSIRT identifies network vulnerabilities, defines the various types of security incidents that pose a risk to the network, and prioritizes each type according to its potential impact on the organization. Based on this risk assessment, the CSIRT may update existing incident response plans or draft new ones.
Detection and Analysis. During this phase, security team members monitor the network for suspicious activity and potential threats. They analyze data, notifications, and alerts gathered from device logs and from various security tools (antivirus software, firewalls) installed on the network, filtering out the false positives and triaging the actual alerts in order of severity.
Today, most organizations use one or more security solutions—such as SIEM (security information and event management) and EDR (endpoint detection and response)—to help security teams monitor and analyze security events in real time, and automate incident detection and response processes. (See “Incident response technologies” for more.)
The communication plan also comes into play during this phase. Once the CSIRT has determined what kind of threat or breach they're dealing with, they'll notify the appropriate personnel before moving to the next stage of the incident response process.
Containment. The incident response team takes steps to stop the breach from doing further damage to the network. Containment activities can be split into two categories:
- Short-term containment measures focus on preventing the current threat from spreading by isolating the affected systems, such as by taking infected devices offline.
- Long-term containment measures focus on protecting unaffected systems by placing stronger security controls around them, such as segmenting sensitive databases from the rest of the network.
At this stage, the CSIRT may also create backups of affected and unaffected systems to prevent additional data loss, and to capture forensic evidence of the incident for future study.
Eradication. After the threat has been contained, the team moves on to full remediation and complete removal of the threat from the system. This involves actively eradicating the threat itself—for example, destroying malware , booting an unauthorized or rogue user from the network—and reviewing both affected and unaffected systems to ensure that no traces of the breach are left behind.
Recovery. When the incident response team is confident the threat has been entirely eradicated, they restore affected systems to normal operations. This may involve deploying patches, rebuilding systems from backups, and bringing remediated systems and devices back online.
Post-incident review. Throughout each phase of the incident response process, the CSIRT collects evidence of the breach and documents the steps it takes to contain and eradicate the threat. At this stage, the CSIRT reviews this information to better understand the incident. The CSIRT seeks to determine the root cause of the attack, identify how it successfully breached the network, and resolve vulnerabilities so that future incidents of this type don't occur.
The CSIRT also reviews what went well and looks for opportunities to improve systems, tools, and processes to strengthen incident response initiatives against future attacks. Depending on the circumstances of the breach, law enforcement may also be involved in the post-incident investigation.
As noted above, in addition to describing the steps CSIRTs should take in the event of a security incident, incident response plans typically outline the security solutions that incident response teams should have in place to carry out or automate key incident response workflows, such as gathering and correlating security data, detecting incidents in real-time, and responding to in-progress attacks.
Some of the most commonly used incident response technologies include:
- SIEM (security information and event management) : SIEM aggregates and correlates security event data from disparate internal security tools (for example firewalls, vulnerability scanners, threat intelligence feeds) and from devices on the network. SIEM can help incident response teams fight ‘alert fatigue’ by indicators of actual threats from the huge volume of notifications these tools generate.
- SOAR (security orchestration, automation, and response): SOAR enables security teams to define playbooks—formalized workflows that coordinate different security operations and tools in response to security incidents—and to automate portions of these workflows where possible.
- EDR (endpoint detection and response) : EDR is software that is designed to automatically protect an organization's end users, endpoint devices and IT assets against cyberthreats that get past antivirus software and other traditional endpoint security tools. EDR collects data continuously from all endpoints on the network; it analyzes the data in real time for evidence of known or suspected cyberthreats, and can respond automatically to prevent or minimize damage from threats it identifies.
- XDR (extended detection and response): XDR is a cybersecurity technology that unifies security tools, control points, data and telemetry sources, and analytics across the hybrid IT environment (endpoints, networks, private and public clouds) to create a single, central enterprise system for threat prevention, detection, and response. A still-emerging technology, XDR has the potential to help overextended security teams and security operations centers (SOCs) do more with less by eliminating silos between security tools and automating response across the entire cyberthreat kill chain.
- UEBA (user and entity behavior analytics) : (UEBA) uses behavioral analytics, machine learning algorithms, and automation to identify abnormal and potentially dangerous user and device behavior. UEBA is effective at identifying insider threats—malicious insiders or hackers that use compromised insider credentials—that can elude other security tools because they mimic authorized network traffic. UEBA functionality is often included in SIEM, EDR, and XDR solutions.
- ASM (attach surface management) : ASM solutions automate the continuous discovery, analysis, remediation, and monitoring of the vulnerabilities and potential attack vectors across all the assets in an organization's attack surface. ASM can uncover previously unmonitored network assets, map relationships between assets,
Get the security protection your organization needs to improve breach readiness with an incident response retainer subscription from IBM Security. When you engage with our elite team of IR consultants, you have trusted partners on standby to help reduce the time that it takes to respond to an incident, minimize its impact and help you recover faster before a cybersecurity incident is suspected.
Threat detection is only half of the security equation. You also need a smart incident response to the growing volume of alerts, multiple tools, and staff shortages. Accelerate incident response with automation, process standardization, and integration with your existing security tools with IBM.
With the growing number of laptops, desktops and remote workers, sophisticated cybercriminals have even more open doors to your organization. From these entry points, they can often proceed deep and unnoticed. IBM delivers a turnkey, 24x7 threat prevention, detection and fast response capability, fueled by threat intelligence and proactive threat hunting to identify and remediate advanced threats.
Build a robust strategy for meeting your incident response challenges.
Ransomware is malware that holds victims' devices and data hostage until a ransom is paid.
Insider threats occur when authorized users deliberately or accidentally expose sensitive data or network assets.
Understand your cyberattack risks with a global view of the threat landscape
The Cost of a Data Breach report explores financial impacts and security measures that can help your organization avoid a data breach, or in the event of a breach, mitigate costs.
Understand your cybersecurity landscape and prioritize initiatives together with senior IBM security architects and consultants in a no-cost, virtual or in-person, 3-hour design thinking session.
Cybersecurity threats are becoming more advanced and more persistent, and demanding more effort by security analysts to sift through countless alerts and incidents. IBM Security QRadar SIEM helps you remediate threats faster while maintaining your bottom line. QRadar SIEM prioritizes high-fidelity alerts to help you catch threats that others simply miss.
How to Create an Incident Response Plan + Template
Like business continuity planning , incident management is part of a broader security and emergency management effort that can help an organization respond and recover from disruptions affecting its information systems, mission and business processes, personnel, and primary facility.
Let’s cover what an incident response plan is, why it’s important, and how to create one below.
What is an incident response plan?
An incident response (IR) plan is a document containing a predetermined set of instructions or procedures to detect, respond to, and limit the consequences of a security incident. These instructions or procedures should help an organization before, during, and after confirmed or suspected security incidents.
What is a cyber incident response plan?
A cyber incident response plan documents the instructions or procedures to detect, respond to, and limit the consequences of cyber attacks against an organization’s information system.
So while an incident response plan may establish procedures to address any security incident, a cyber incident response plan establishes procedures to specifically address malicious computer incidents. Examples of malicious computer incidents include:
- Unauthorized access to a system or data
- Denial of service attack
- Virus, worm, Trojan horse, or another type of malicious logic that makes unauthorized changes to system hardware, software, or data
This plan may be included as an appendix of an organization’s business continuity plan.
In NIST Special Publication 800-34, Revision 1, incident response plan was changed to cyber incident response plan.
Use trust to accelerate growth
Why is an incident response plan important.
An incident response plan can help an organization detect, respond, and recover from a security incident or event faster and more cost effectively. It clearly lays out what needs to be done so personnel can perform incident response more effectively, efficiently, and consistently. This can help personnel minimize loss or theft of information and disruption of services caused by incidents, which can result in significant cost savings.
For example, in IBM's 2022 Cost of a Data Breach report , nearly three-quarters of organizations said they had an IR plan, while 63% of those organizations said they regularly tested the plan. The organizations with an IR team that tested an IR plan saved $2.66 million in breach costs on average versus those with no IR team and IR plan testing. This represents a 58% cost savings.

NIST incident response plan
The NIST SP 800-61 publication — also known as the Computer Security Incident Handling Guide — is designed to help organizations establish successful computer security incident response capabilities and handle incidents efficiently and effectively. Most of its guidelines revolve around analyzing incident-related data and determining the appropriate response to each incident.
NIST recommends that an incident response plan should include the following:
- A mission statement
- Strategies and goals
- Senior management approval
- An organizational approach to incident response
- How the incident response team will communicate with the rest of the organization and other organizations
- Metrics for measuring the incident response capability and its effectiveness
- A roadmap for maturing the incident response capability
- How the program fits into the overall organization
These recommendations and other guidelines in NIST 800-61 are incorporated in the steps below.
Recommended reading

Essential Guide to Security Frameworks & 14 Examples
How to create an incident response plan
Writing and maintaining an incident response plan requires collaboration and coordination among key stakeholders across an organization Below we’ll outline the step-by-step process to help you get started.
1. Create an incident response policy
Before starting an incident response plan, you need to establish your organization's incident response policy. This policy is the foundation for your incident response program and should:
- Define which events are considered incidents
- Establish the organizational structure for incident response
- Define roles and responsibilities
- List the requirements for reporting incidents
The plan should then provide a roadmap for implementing your incident response program based on the policy.
2. Define short and long-term goals of incident response program
The incident response plan should indicate both short- and long-term goals for the program. This will require you to establish metrics for measuring the program’s effectiveness and progress towards those goals.
Examples of metrics are:
- Number of incidents handled
- Total amount of labor spent working on the incident
- Average time it takes the incident response team to respond to the initial report of an incident
3. Identify the incident response team and its responsibilities.
You should have an appointed incident response team in place to manage security incidents. The incident response plan should indicate who is part of the incident response team and what its main objectives and responsibilities are.
4. Establish requirements for incident handlers
When an incident occurs, incident handlers must analyze the incident data, determine the impact of the incident, and act appropriately to limit the damage and restore normal services. This requires excellent technical skills in certain areas, such as system administration, network administration, programming, technical support, or intrusion detection. Depending on the staffing model of your incident response team, you may have team members specialize in multiple technical areas or have at least one proficient person in each major area.
Your organization’s incident response plan should indicate requirements for incident handlers, including how often they should be trained.
5. Define the incident response process
A critical part of any incident response plan is how it defines the organizational approach to incident response.
The process should include:
- Detection : How are incidents detected? Is automation used?
- Reporting : How are incidents reported by internal and external sources?
- Response : What are the procedures for responding to an incident?
- Review : How is the incident handling process reviewed? Are meetings held after major incidents? Are follow-up reports created for each resolved incident?
As you consider what steps you’ll take during an incident, you should also consider how you’ll accomplish them efficiently. Incident management tooling can accelerate and streamline your process by automating actions like alerts, pulling metrics reports, coordinating stakeholders, and more. Some tools like Rootly even offer additional support and features — like communications and retrospective templates, consultation with incident response experts, and other resources to develop your organization’s incident response capabilities.
6. Define a communications strategy
An incident response plan should explain how the incident response team will communicate with the rest of the organization and outside parties, such as law enforcement, the media, and other incident response organizations.
The team should plan and document several communication methods in the incident response plan. Examples might include:
- Telephone calls
- Daily briefings in person
- Voice mailbox greeting for current incident status and update
7. Provide a roadmap for maturing incident response capabilities
Your incident response program should evolve to reflect new threats, improved technology, and lessons learned from major incidents. To ensure it improves and matures over time, you should provide a roadmap in your incident response plan. This roadmap may include holding a “lessons learned” meeting with all involved parties after a major incident. This can be critical for improving security measures and the incident handling process itself over time.
8. Review, update, and test this plan regularly
According to NIST SP 800-61, incident response plans should be reviewed and tested at least annually to ensure the organization is maturing its information security capabilities over time and making progress towards its goals for incident response.
Incident response plan template
Use the template below to simplify the process of creating an incident response plan for your organization.

GRC Overview
What is grc and why is it important, the 3 components of grc, navigating cybersecurity governance, 14 common types of cybersecurity attacks in 2023, data governance: definition, principles, and frameworks, how to build a smart data governance strategy, data governance metrics and kpis, what is a risk management strategy + examples, risk assessment: purpose, process, and software + template, what is risk mitigation + strategies, how to create a risk register + template, how to write a business continuity plan + template, what is a change management process + template, what is third-party risk management + policy, compliance and auditing, security compliance: how to keep your business safe & meet regulations, 15 essential regulatory and security compliance frameworks, what is continuous compliance + how to achieve it, how to conduct an effective internal compliance audit, how to implement a grc program, how to implement a grc program + checklist, success metrics for grc programs, how to measure grc maturity, grc tools and resources, grc automation, what is grc software and how does it work, top benefits of adopting grc software, how to choose a grc software solution.
- Business & Technology
- FortiGuard Labs Threat Research
- Industry Trends
- Customer Stories
- PSIRT Blogs
CISO Collective
A Guide to Incident Response Plans, Playbooks, and Policy
When we work with customers, we often discover that they are confused about the terminology and incident response (IR) documentation that they should have within their organization. When managing a cyberattack, we recommend three documents: the incident response policy, the incident response plan, and incident response playbooks. In this article, we cover the purpose of each document along with guidance on the key components for an organization.

Why Do We Need an Incident Response Policy?
The incident response policy is the foundational document of any incident response team. It should act as a blueprint for incident response throughout the organization. Like any policy, this document sets the rules and governance around incident response for the organization. Unlike the other IR documents, the policy should be broad and not change much, if at all.
What should an incident response policy contain?
At a minimum, the policy should outline the core incident response elements for the organization, including:
- The purpose of incident response and why it is required
- Why the policy was created
- The scope of the policy (who and what does the policy apply to)
- Who within the organization is responsible for enforcing the policy
- Definitions for incident response and other key terms, such as event and incident
- The requirements that must be met by the incident response team and larger organization
- A mandate on the creation of the incident response plan, which should include the key elements required of the plan
Creating an incident response policy holds the organization accountable for making incident response a priority.
What Is the Incident Response Plan?
The incident response plan provides guidance on how to respond to various incident types. The Cybersecurity and Infrastructure Security Agency (CISA) defines the incident response plan as “a written document, formally approved by the senior leadership team, that helps your organization before, during, and after a confirmed or suspected security incident.” The CISA definition includes two components that should not be overlooked:
- The incident response plan must be approved by senior leadership and should ideally have an executive sponsor. Having leadership approval gives incident responders confidence and acknowledgment that they can take any action as defined by the plan to contain, eradicate, and recover from an incident. Without this approval in place, teams may be hesitant to act or be required to wait for approvals before taking time-sensitive actions, which could result in financial or reputational damage.
- The incident response plan should cover how to detect, analyze, contain, eradicate, and recover from an incident. The incident response lifecycle has two crucial parts that should not be glossed over preparation and post-incident activities. The incident response plan should define and cover all phases of the incident response lifecycle, including both before and after the incident.
What are the key elements of an incident response plan?
Although no one-size-fits-all incident response template exists, the plan should contain the following items:
- A mission statement
- Goals and objectives
- Roles and responsibilities, including primary and out-of-band contact information for the incident response team members
- Communication procedures for both internal and external communications
- Incident severity levels
- Incident types
- Incident definitions (incident, event, data breach)
- Incident response procedures in alignment with organizations' chosen incident response lifecycle
Readers are encouraged to review NIST 800-61 , which is an excellent guide for what should be contained within the incident response plan and also provides guidance on the incident response lifecycle.
The incident response plan is the guidebook to handling incidents. It should be a living document that is updated and tended to regularly. Fortinet recommends a bi-annual review of the plan and a review after each major incident. This timing ensures that any lessons learned from an incident are incorporated and that changes to the organization are considered and implemented into the plan.
What Is the Purpose of an Incident Response Playbook?
Incident response playbooks standardize the response to a specific type of incident with procedures that include specific actions that the organization must take to prepare for, respond to, and recover from specific incident types.
Using the National Institute of Standards and Technology (NIST) incident response framework as an example, an incident response playbook provides detailed guidance on each phase of incident response: preparation, detection and analysis, containment, eradication, recovery, and post-incident activity.
For example, during the analysis phase, the incident response plan may dictate that it is necessary to perform analysis on any file, process, or account suspected of malicious use during the incident. Although the incident response plan provides the general analysis steps that need to occur for any incident type, a ransomware playbook provides the detailed analysis steps of a ransomware incident, such as reviewing the owner of an encrypted file to determine the account used for encryption.
The playbook should define what specific actions need to be taken during the phase of incident response and the team or individual responsible for performing the action. Keep in mind these actions can be both technical, such as restoring the file server from backup to nontechnical, such as constructing external communications to customers and distributing the communications.
What are the common scenarios for incident response playbooks?
To determine which playbooks to create, it is best to evaluate the current risks to the organization and develop playbooks around the risks that fall higher on the risk register. Common types of playbooks include:
- Ransomware playbook
- Data breach or data loss playbook
- Malware playbook
- Denial-of-service playbook
- Insider threat playbook
- Social engineering playbook
- Website compromise playbook
- Zero-day vulnerability playbook
The difference between an incident response plan and playbook in a data breach
To drive home the difference between the incident response plan and a playbook, here’s an example of what should be included in a data breach playbook. When developing a playbook, the organization should follow the incident response lifecycle defined within the incident response plan and the response efforts. This example uses the NIST lifecycle.
Preparation
To respond to a data breach, the organization must first define what constitutes a data breach, including all applicable laws, regulations, and contractual obligations around the data for which the organization is responsible. Organizations should get legal advice about what constitutes a data breach and include that information within the playbook.
Detection and Analysis
Determining whether a data breach has occurred requires that tools and technologies are in place, understood, and monitored by the organization. These solutions may be unique to an incident that involves the loss of data, such as a data loss prevention solution or dark web monitoring. With these items in place, processes can be built into the playbook to detect and respond to a data loss incident.
Once a breach is detected, the team collects evidence and maintains a proper chain of custody. This effort may need to be outsourced to an external incident response or forensics team. Regardless of whether the investigation is conducted internally or externally, steps should be defined within the playbook as to the analysis that must occur to discover the depth, severity, and root cause of the incident. With an incident involving data loss, another incident is likely to be occurring, such as phishing, malware, or even ransomware. Depending on what the other malicious activity is, it may be necessary to reference additional playbooks.
Containment, Eradication, and Recovery
To define actionable steps for containment, eradication, and recovery, it is important to consider communications during the incident. The type and nature of the data loss may lead to disclosure notifications to various organizations and individuals, such as regulators or even government entities. A data breach playbook should, at a minimum, reference the required communications procedures. Communications and legal teams may both need to be involved during an incident.
During containment and eradication, the organization should use tools and technologies, such as endpoint detection and response (EDR) or a virtual local area network (VLAN) to isolate hosts and eradicate the threat. Regardless of the method, the playbook should define the exact methods and, if necessary, link to documentation on how to perform the tasks.
Recovery from a data breach incident often involves data restoration. Keep in mind, that once integrity is lost, it cannot be regained. However, systems and data can still be restored to ensure threats are eradicated. Recovery may include restoration from backup, so the playbook should include information about data restoration tools and processes.
Post-Incident Activity
Post-incident activity for a data breach can be more intensive than other types of incidents, such as a lost or stolen laptop, because of the regulatory requirements related to the type of data compromised. For example, if customer Personally Identifiable Information (PII) for the state of California is impacted, the organization must ensure all requirements set forth by California’s reporting requirements have been met.
Developing incident response documentation, including playbooks is no small endeavor. However, it can and should be done to help reduce the impact of an incident and guide responders on what needs to be done.
Ensure Incident Response Documents Are Complete and Comprehensive
Incident response plans and playbooks should clearly define all of the individuals and teams that have a stake in the incident response process, even if they are only performing one or two actions. By defining roles and responsibilities and having these individuals become familiar with the documentation through readthroughs and tabletop exercises, team members across the organization know what they need to do and when.
Incident response documentation should contain communication templates with information about the who, what, when, and how:
- Who is going to be drafting and conducting internal and external communications?
- Who do we need to communicate with (regulators, insurance, customers, partners, vendors)?
- What needs to be communicated?
- When should the communication occur?
- How is communication going to occur, especially if companywide email is unavailable?
incident response , incidence response
Related Posts
5 critical targets illustrate the need for cutting-edge healthcare cybersecurity, ransomware response checklist: a guide for cisos, 6 key cybersecurity metrics for your board of directors that will show value, news & articles.
- News Releases
- News Articles
Security Research
- Threat Research
- FortiGuard Labs
- Ransomware Prevention
Connect With Us
- Fortinet Community
- Partner Portal
- Investor Relations
- Product Certifications
- Industry Awards
- Social Responsibility
- CyberGlossary
- Blog Sitemap
- (866) 868-3678
Copyright © 2024 Fortinet, Inc. All Rights Reserved
What is incident response?
Explore how effective incident response helps organizations detect, address, and stop cyberattacks.

Incident response defined
Before defining incident response it’s important to be clear on what an incident is. In IT, there are three terms that are sometimes used interchangeably but mean different things:
- An event is an innocuous action that happens frequently such as creating a file, deleting a folder, or opening an email. On its own an event typically isn’t an indication of a breach but when paired with other events may signal a threat.
- An alert is a notification triggered by an event, which may or may not be a threat.
- An incident is a group of correlated alerts that humans or automation tools have deemed likely to be a genuine threat. On their own, each alert may not appear to be a major threat but when combined, they indicate a possible breach.
Incident response is the actions that an organization takes when it believes IT systems or data may have been breached. For example, security professionals will act if they see evidence of an unauthorized user, malware, or failure of security measures.
The goals of the response are to eliminate a cyberattack as quickly as possible, recover, notify any customers or government agencies as required by regional laws, and learn how to reduce the risk of a similar breach in the future.
How does incident response work?
Incident response typically starts when the security team gets a credible alert from a security information and event management (SIEM) system.
Team members need to verify that the event qualifies as an incident and then isolate infected systems and remove the threat. If the incident is severe or takes a long time to resolve, organizations may need to restore back up data, deal with a ransom, or notify customers that their data was compromised.
For this reason, people other than the cybersecurity team are typically involved in the response. Privacy experts, lawyers, and business decision makers will help determine the organization’s approach to an incident and its aftermath.
Types of security incidents
There are several ways that attackers try to access a company’s data or otherwise compromise its systems and business operations. Here are several of the most common:
In a ransomware attack, bad actors use malware to encrypt critical data and systems and then threaten to make the data public or destroy it if the victim doesn’t pay a ransom.
Denial of service
In a denial-of-service attack (DDoS attack), a threat actor overwhelms a network or system with traffic until it slows or crashes. Typically, attackers target high-profile companies like banks or governments with the goal of costing them time and money, but organizations of all sizes can be victims of this type of attack.
Man in the middle
Another method that cybercriminals use to steal personal data is to insert themselves in the middle of an online conversation between people who believe they are communicating privately. By intercepting messages and copying them or changing them before sending them to the intended recipient, they try to manipulate one of the participants into giving them valuable data.
Insider threat
Although most attacks are conducted by people outside an organization, security teams also need to be on the lookout for insider threats. Employees and other people who legitimately have access to restricted resources may inadvertently or in some cases intentionally leak sensitive data.
Unauthorized access
A lot of security breaches start with stolen account credentials. Whether bad actors acquire passwords via a phishing campaign or by guessing a common password, once they gain access to a system they can install malware, do network reconnaissance, or escalate their privileges to allow them access to more sensitive systems and data.
What is an incident response plan?
Responding to an incident requires a team to work together efficiently and effectively to eliminate the threat and satisfy regulatory requirements. In these high-stress situations, it’s easy to become flustered and make mistakes, which is why many companies develop an incident response plan. The plan defines roles and responsibilities and includes the steps needed to properly resolve, document, and communicate about an incident.
Importance of an incident response plan
A significant attack doesn’t just damage the operations of an organization, it also affects the business’s reputation among customers and the community, and it may have legal ramifications too. Everything, including how quickly the security team responds to the attack and how executives communicate about the incident, influences its overall cost.
Companies that hide the damage from customers and governments or who don’t take a threat seriously enough may run afoul of regulations. These types of mistakes are more common when participants don’t have a plan. In the heat of the moment, there’s a risk that people will make rash decisions driven by fear that wind up hurting the organization.
A well-thought-out plan lets people know what they should be doing at each phase of an attack, so they don’t have to make it up on the fly. And after recovery if there are questions from the public, the organization will be able to show exactly how it responded and give customers peace of mind that it took the incident seriously and implemented the steps necessary to prevent a worse outcome.
Incident response steps
There’s more than one way to approach incident response, and many organizations rely on a security standards organization to guide their approach. SysAdmin Audit Network Security (SANS) is a private organization that offers a six-step response framework , which is outlined below. Many organizations also adopt the National Institute of Standards and Technology (NIST) incident recovery framework .
- Preparation - Before an incident occurs, it’s important to reduce vulnerabilities and define security policies and procedures. In the preparation phase, organizations conduct a risk assessment to determine where they have weaknesses and prioritize assets. This phase includes writing and refining security procedures, defining roles and responsibilities, and updating systems to reduce risk. Most organizations regularly revisit this stage and make improvements to policies, procedures, and systems as they learn lessons or technologies change.
- Threat identification - In any given day, a security team may receive thousands of alerts that indicate suspicious activity. Some of them are false positives or may not rise to the level of an incident. Once an incident has been identified, the team digs into the nature of the breach and documents findings, including the source of the breach, the type of attack, and attacker goals. In this stage, the team also needs to inform stakeholders and communicate next steps.
- Threat containment - Containing a threat as quickly as possible is the next priority. The longer bad actors are allowed access, the greater damage they can do. The security team works to rapidly isolate applications or systems that are under attack from the rest of the networks. This helps prevent the attackers from accessing other parts of the business.
- Threat elimination - Once containment is complete, the team removes the attacker and any malware from affected systems and resources. This may involve taking systems offline. The team also continues to keep stakeholders informed of progress.
- Recovery and restoration - Recovering from an incident may take several hours. Once the threat is gone, the team restores systems, recovers data from backup, and monitors affected areas to ensure the attacker doesn’t return.
- Feedback and refinement - When the incident is resolved, the team reviews what happened and identifies improvements that can be made to the process. Learning from this phase helps the team enhance the organization’s defenses.
What is an incident response team?
An incident response team, which is also called a computer security incident response team (CSIRT), a cyber incident response team (CIRT), or a computer emergency response team (CERT), includes a cross-functional group of people in the organization who are responsible for executing the incident response plan. This includes not only the people who remove the threat but also those who make business or legal decisions related to an incident. A typical team includes the following members:
An incident response manager, often the director of IT, supervises all phases of the response and keeps internal stakeholders informed.
Security analysts research the incident to try to understand what is happening. They also document their findings and gather forensic evidence.
Threat researchers look outside the organization to gather intelligence that provides additional context.
Someone from management, such as a chief information security officer or a chief information officer, provides guidance and serves as a liaison to other executives.
Human resources specialists help manage insider threats.
General counsel helps the team navigate liability issues and ensures that forensic evidence is collected.
- Public relations specialists coordinate accurate external communication to the media, customers, and other stakeholders.
An incident response team may be a subset of a security operations center (SOC), which handles security operations beyond incident response.
Incident response automation
In most organizations, networks and security solutions generate far more security alerts than the incident response team can realistically manage. To help it focus on legitimate threats, many businesses implement incident response automation. Automation uses AI and machine learning to triage alerts, identify incidents, and root out threats by executing a response playbook based on programmatic scripts.
Security orchestration automation and response (SOAR) is a category of security tools that businesses use to automate incident response. These solutions offer the following capabilities:
Correlate data across multiple endpoints and security solutions to identify incidents for humans to follow up on.
Run a pre-scripted playbook to isolate and address known incident types.
Generate an investigative timeline that includes actions, decisions and forensic evidence that can be used for analysis.
Bring in relevant external intelligence for human analysis.
How to implement an incident response plan
Developing an incident response plan may seem daunting, but it can significantly reduce the risk that your business will be unprepared during a major incident. Here’s how to get started:
Identify and prioritize assets
The first step in an incident response plan is knowing what you’re protecting. Document your organization’s critical data, including where it lives and its level of importance to the business.
Determine potential risks
Every organization has different risks. Become familiar with your organization’s greatest vulnerabilities and evaluate the ways an attacker could exploit them.
Develop response procedures
During a stressful incident, clear procedures will go a long way toward making sure the incident is addressed quickly and effectively. Start by defining what qualifies as an incident and then determine the steps your team should take to detect, isolate, and recover from the incident, including procedures for documenting decisions and collecting evidence.
Create an incident response team
Build a cross-functional team that is responsible for understanding the response procedures and mobilizing if there’s an incident. Be sure to clearly define roles and account for nontechnical roles that can help make decisions related to communication and liability. Include someone on the executive team who will be an advocate for the team and its needs at the highest levels of the company.
Define your communication plan
A communication plan will take the guesswork out of when and how to tell others inside and outside the organization what’s happening. Think through various scenarios to help you determine under what circumstances you need to inform executives, the entire organization, customers, and the media or other external stakeholders.
Train employees
Bad actors target employees at all levels of the organization, which is why it’s so important that everyone understands your response plan and knows what to do if they suspect that they’ve been the victim of an attack. Periodically, test your employees to confirm they can recognize phishing emails and make it easy for them to notify the incident response team if they accidentally click on a bad link or open an infected attachment.
Incident response solutions
Being prepared for a major incident is an important part of keeping your organization safe from threats. Setting up an internal incident response team will give you the confidence that you’ll be ready if you are victimized by a bad actor.
Take advantage of SIEM and SOAR solutions like Microsoft Sentinel that use automation to help you identify and automatically respond to incidents. Organizations with fewer resources can augment their teams with a service provider that can handle multiple phases of incident response. But whether you staff incident response internally or externally, make sure you have a plan.
Learn more about Microsoft Security
Microsoft threat protection.
Identify and respond to incidents across your organization with the latest in threat protection.

Microsoft Sentinel
Uncover sophisticated threats and respond decisively with a powerful SIEM solution, powered by the cloud and AI.
Microsoft Defender XDR
Stop attacks across endpoints, email, identities, applications, and data.
Frequently asked questions
What is incident response for.
Incident response is all the activities that an organization takes when it suspects a security breach. The goal is to isolate and root out attackers as quickly as possible, comply with data privacy regulations, and recover safely with as little damage to the organization as possible.
Who is responsible for incident response?
A cross-functional team is responsible for incident response. IT will typically be in charge of identifying, isolating, and recovering from threats, however there is more to incident response than finding and getting rid of bad actors. Depending on the type of attack, someone may have to make a business decision, such as how to address a ransom. Legal counsel and public relations professionals help ensure that the organization complies with data privacy laws, including appropriate notification of customers and governments. If the threat is perpetrated by an employee, human resources advises on appropriate action.
What is a computer security incident response team (CSIRT)?
CSIRT is another name for an incident response team. It includes a cross-functional team of people who are responsible for managing all aspects of incident response, including detecting, isolating, and eliminating the threat, recovery, internal and external communication, documentation, and forensic analysis.
What are incident response tools?
Most organizations use a SIEM or a SOAR solution to help them identify and respond to threats. These solutions typically aggregate data from multiple systems and use machine learning to help identify true threats. They can also automate response for certain kinds of threat based on pre-scripted playbooks.
What is the incident response lifecycle?
The incident response lifecycle includes six stages:
- Preparation occurs before an incident has been identified and includes a definition of what the organization considers an incident and all the policies and procedures necessary to prevent, detect, eliminate, and recover from an attack.
- Threat identification is a process that uses both human analysts and automation to identify which events are real threats that need to be addressed.
- Threat containment is the actions that the team takes to isolate the threat and prevent it from infecting other areas of the business.
- Threat elimination includes steps to remove malware and attackers from an organization.
- Recovery and restoration include restarting systems and machines and restoring any data that was lost.
- Feedback and refinement is the process the team takes to uncover lessons from the incident and apply those learnings to policies and procedures.
Follow Microsoft
- Chat with sales
Available Mon to Fri from 6:00 AM to 6:00 PM Pacific Time.

How to Create an Incident Response Plan (+ Free Template)
Jenna Phipps
eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
While all businesses have to decide what cybersecurity measures they’re going to prioritize, incident response is one that isn’t optional. Incidents are going to happen, and the right (or wrong) one could put your company out of business. No one wants to go out of business because of sloppy preparation.
Preparing for incident response can help you minimize damage from cyber incidents — and prevent the next one from occurring. This guide to incident response plans will help your organization better prepare for incidents and develop a plan that fits your business needs.
Jump ahead to:
What is an Incident Response Plan?
Tips for effective incident response preparation, components of an incident response plan, how to create an incident response plan, free incident response templates, bottom line: developing a strong incident response plan.
An incident is an event that affects your scope of responsibility, and a response is how you deal with the incident. The scope of responsibility for cybersecurity personnel may be limited to cyberattacks on IT systems, such as ransomware attacks, phishing attacks, or DDoS attacks . For IT managers, the scope might expand to encompass physical IT systems and events such as a flooded data center, a lost executive laptop, or squirrels chewing on network cables.
In small companies where managers cover many roles, an incident might broaden to include personnel and business processes with events such as insider data theft , sexual harassment, embezzlement, or the failure of a machine on an assembly line. However, this piece will specifically focus on cybersecurity incidents like attacks and breaches .
Regardless of the incident scope, your goal is to be able to perform the necessary steps and take into account any unexpected contingencies. For that, you need an incident response plan, because responses need to be as quick and thorough as if you’d practiced them (spoiler alert: you should). The foundational principles of incident response preparation and execution outlined below will help you develop your plan.
Read more about incident response .
When your business is preparing for incident response procedures, you should analyze all the cybersecurity risks to your business, educate teams on incidents, and practice incident response scenarios. Ensuring that teams know as much as possible about incidents and your organization’s security systems will lead to better long-term preparation and reduced employee apprehension.
Run a risk assessment
While your security team may already know the majority of risks that the business faces, risk assessments often bring up ones that nobody thought of. Maybe a high-ranking IT employee just left last month, and their admin credentials to the company IAM account never got deactivated. Or maybe there’s a new vulnerability in a very old program, one that nobody worried about because it’s ancient. Maybe the doors to the main office don’t always lock properly, and anyone could just walk in. Risk assessments reveal details that your teams might not otherwise see.
Give team members necessary access
During an incident response scenario, your security and IT teams will need access to any computer systems or security solution necessary to perform their job. This might include an endpoint detection and response platform , a cloud backup solution, or a UEBA tool , depending on the employee’s role and experience. Equally as important, they should already know how to use it. Make sure you train your team on the security solutions in their arsenal before they are forced to use them to mitigate a threat.
Create a logical method for identifying incidents
Security software throws all kinds of false positives, and when a barrage of alerts hits, security teams can quickly be overwhelmed while trying to sort through potential incidents. They need to know how to identify a real incident and triage them by importance.
Your business should develop a logical system to help team members identify legitimate incidents. This could look like a list of characteristics that they check off to determine severity or an alert system that’s tiered based on potential danger.
Run simulations and tests
Once teams know more about potential risks, have access to the right programs, and know how to identify an incident, they need practice. Your security team, as well as potentially any involved IT personnel, should run simulations of an incident so they have hands-on experience mitigating threats. Teams shouldn’t be frozen in fear when the first incident occurs, and hosting plenty of test scenarios will help with that.
Because incident response plans are complex and detailed, they can have plenty of components. We recommend four overall strategies that your plan should include rather than create a laundry list.
Set up an incident response team
Your business won’t have an appropriate response to a security issue if no one knows what they’re supposed to be doing. When developing a response team, make sure that your IT and security teams:
- Know which team members are responsible for sending all alert messages.
- Know which team member is responsible for reporting to any relevant managers.
- Have clear step-by-step instructions so they know which actions to take in order.
- Know which team member they should ask for help if their part of the response plan gets out of hand.
The sooner each team member knows their roles and expectations, the sooner they’ll be able to confidently carry out an incident response scenario.
Additionally, your organization’s executive team may want to be apprised of incident management processes. Whether this looks like quarterly updates or weekly reports, ensure that your incident response team has an agreed-upon method of consistently updating relevant executives. They may want to know:
- How many incidents occurred in a given period of time (whether days, weeks, or months)
- The time frame in which the incident was successfully mitigated
- Any particular challenges that have arisen during a given period of time
Customize for multiple scenarios and systems
Here’s the tricky part of incident response: Not all incidents are equal, and not all computer systems are prioritized equally.
While one basic incident response plan might be the template for all security operations in your business, chances are that the actual response process will look different depending on the network or system affected. It’ll also vary depending on the severity of the incident. For example:
- In a ransomware-related incident, where malicious software has infiltrated a system, a security team might have more steps to follow than a credential stuffing and breach incident on, say, a company’s content planning board.
- Similarly, remediation steps will look different for an attack on a large database of customer information and a breach of an employee’s individual computer.
Incident response plans should be easily customizable for multiple systems and multiple types of attacks. This will take more initial work, but it’ll lead to better security procedures in the future.
Make it flexible
At first glance, this strategy looks like the complete opposite of the one before. How do you customize your incident response plan while also keeping it flexible and generic?
This will depend on your business, your security team, and the variety of systems you need to protect. Generally speaking, technology and personnel changes happen too quickly to be easily captured in a static document. A server web shell attack incident response plan designed last year when your organization had its on-site data center quickly became obsolete once you transitioned some of the servers to the cloud and transitioned others onto virtual machines.
You can still have multiple incident response plans, customized based on the incident or system. But make sure they’re easy to edit. They could be brief, taking a checklist form that can easily be edited. Or maybe they’re hosted in documentation software that automates edits when a policy is changed.
The goal of an incident response document is to be useful, not to consume hours of time to keep them current or to misdirect your team. However, checklists and decision trees can be helpful in keeping the team focused and reducing errors. The trick will be to strike a balance between details and generalizations to maximize utility and minimize obsolescence.
Develop a practical alert methodology
There’s such a thing as too many alerts, and important alerts can also be missed. To ensure neither of these things happen, consider what channel is most appropriate for an alert and vice versa . For example:
- For an urgent alert about a newly developing attack on a critical cloud application, you’ll want to tag all relevant team members in the alert and use the channel that your team will check most frequently. This might be Slack, Teams, or a security-specific application.
- For an alert that comes at the end of an incident response process, sending a mass email is often appropriate, since it isn’t as urgent and has a lot of follow-up information that will clog an app like Slack.
Also, keep in mind that many alerts aren’t sent directly from team members but come automatically from security software. Your IT and security admins will have to configure all solutions so they send alerts at the correct time and in the correct channel. Often, communication tools like Slack and Microsoft Teams integrate with popular security solutions so the alerts can populate in designated channels.
Developing a strong incident response plan can take months of meetings, strategizing, and keeping team members apprised of progress. The following steps will help your team create a strong overall incident response strategy.
Create an overview
Many incident response plan templates have an overview section that clearly states the purpose of the plan. Your teams should know exactly why the plan is important and what details it covers.
Assign tasks logically
Assign tasks to the team members that make sense. Security admins or IT managers should have greater responsibility in a response scenario than your team’s junior engineer or newest intern. That doesn’t mean they don’t have roles, though — they just need to make sense for their position and experience. A junior analyst might be responsible for sending logs of threat scans to their team leader to further study, for example.
Eliminate gray zones
When assigning responsibility, any gray zone or gap in responsibility can lead to confusion or even cause an incident to be overlooked. To prevent any vagueness, assign secondary responsibilities with overlap for every incident, asset, or threat.
In large organizations, some potential incidents, such as a misconfigured cloud data bucket exposed to the internet, may fall between departments. Ultimately, someone will need to step up and take responsibility for those items—and therefore, those incidents as well. For example, assign the cloud team to initially respond to incidents involving cloud assets with the cybersecurity team providing backup resources.
The assignment of backup resources will also be useful as a contingency plan. If your cloud team is based in an office currently disabled by a widespread blackout, a cybersecurity team member in another office assigned as a backup already knows to step up and address cloud issues without delay.
Choose the right documentation software
Your business may only need Google Docs or Microsoft Word for documenting an incident response plan. But you may want software with additional capabilities for creating and updating documents. Look for documentation software that has either security-specific templates or plenty of options that your teams can customize. You’ll want something with flexible templates that you can update easily, since incident response plans may need to change on a regular basis, and you want to eliminate as much manual work as possible.
Create a logical flow of alerts
Which alerts need to go to which team members and at what time? Make sure your automatic alerts are configured in appropriate order. Initial alerts must be examined for validity: is the incident causing a false positive, or should it be mitigated further? Security automation software allows teams to configure alerts to their specifications, setting logical requirements for an alert to be triggered. Personnel should know exactly when to send a manual alert, like an email or Slack message, too.
Be in line with insurance policies
Insurance policies can also heavily influence how businesses respond to an incident—particularly cybersecurity. Some policies require initial contact to be made with an insurer who will deploy their own incident response team. Others might require specific documentation and forensic evidence to pay out on expenses related to an incident. Work with legal counsel and insurance representatives to make sure the requirements are well understood and incorporated into your incident response plans.
Incorporate stakeholder feedback
Plans developed only by those assigned direct responsibility will suit their needs and expectations, but they might overlook the needs and issues of others. Once you’ve drafted an IR plan, send it to any relevant business executives, legal counsel, key vendors, and possibly even affected key customers for feedback. These stakeholders may point out additional considerations to protect the organization against lawsuits, violating regulations, or unnecessary business disruptions.
Once you’ve incorporated appropriate feedback, you’ll be ready with the final draft of the plan.
Keep the incident response plan current
Your business should regularly update incident documentation on a quarterly, annual, or event-driven schedule. Documentation software will help with this. Then you should effectively circulate the incident response documents. The circulation can be through a shared file server, but we recommend using email and printed versions, so key information will remain available for a wide variety of emergencies.
Two leading bodies in the cybersecurity industry provide detailed incident response templates:
- National Institute of Standards of Technology template
- SANS templates (categorized by specific areas of incident response)
While your business may want to copy such a template, they’re also good resources to inform your team’s individual plan, too. These are tools you can use to develop your own template, especially if your team hasn’t done this before and wants to pull from industry leading expertise.
Learn more about the incident response process and different frameworks .
There is no single correct approach or template for an incident response strategy. It will vary depending on your business’s priorities, your IT and security teams’ experience, and the threats you most commonly face. But practicing incident response, giving team members detailed instructions, and carefully documenting processes are just a few ways to strengthen your business’s overall approach to breaches and cyberattacks.
Article written by Chad Kime on Dec. 9, 2021 and updated by Jenna Phipps on Aug. 23, 2023.
Does your business need some additional help developing an incident response strategy? Read about the best incident response software next.
Get the Free Cybersecurity Newsletter
Strengthen your organization’s IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices.
Previous article
Next article

Subscribe to Cybersecurity Insider
Strengthen your organization’s IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices.
IT Security Resources
Hackergpt 2.0 unveils new ai cyber defense strategies.

6 Best Enterprise Password Managers for 2024 Rated

VulnRecap 3/11/24 – JetBrains & Atlassian Issues Persist

6 Best Single Sign-On (SSO) Providers & Solutions in 2024

Top Cybersecurity Companies
Get the free newsletter.
Subscribe to Cybersecurity Insider for top news, trends & analysis
Related Articles
What Is Cross-Site Scripting (XSS)? Types, Risks & Prevention

What Is an Application Level Gateway? Guide on How ALGs Work

How to Perform a Firewall Audit in 11 Steps (+Free Checklist)

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Incident Response Plan (IRP) Basics
This factsheet provides an overview of an Incident Response Plan and how it should be implemented before, during, and after a cybersecurity incident.
Resource Materials
Related resources, secure cloud business applications: hybrid identity solutions guidance, cybersecurity advisory committee (csac) reports and recommendations, cyber threats to medical technology and communication technology protocols, top cyber actions for securing water systems.
- Experiencing a breach?
- Managed Cybersecurity
- Cybersecurity Compliance
- All-in-One Defense
- Risk Reduction
- Malware & Ransomware Protection
- Incident Response
- Incident Response Planning
- Virtual CISO
- Phishing Simulation Exercises
- Cybersecurity Maturity Assessment
- Customer Stories
- Leadership Team
- vs Arctic Wolf
- vs Huntress
- vs SentinelOne
January 25, 2022
Incident response plan: What it is & 4 key components
By Katie Yahnke

Security Intelligence
Unprecedented Pro-Russian DDoS attack on French state websites

What is the future of cybersecurity?

One-day, n-day, and zero-day vulnerabilities explained
An incident response (IR) plan is a formal document that guides an organization’s response to a cyber security incident. IR plans cover both the technical and business aspects of incident response, with recommended steps to help teams prepare for, detect, respond to, and recover from a potential cyber attack. On a larger scale, this document strengthens and matures your organization’s cyber security posture.
Before we dive into key components and best practices for your IR plan, let’s first explore what a cyber security incident really is.
What is a cyber security incident?
A cyber security incident is often defined as an event that breaches the “CIA triad”—confidentiality, integrity, and availability—a foundational principle in information security.
Consider these scenarios:
- Confidentiality is breached if there has been unauthorized use or disclosure of proprietary or confidential information, like in cases of ransomware .
- Integrity is breached if a document has been changed or is no longer authentic, like when threat actors edit invoices during business email compromise .
- Availability is breached if authorized users no longer have reliable or timely access to services and data, which commonly happens during denial-of-service attacks .
Contrary to popular belief, the attacker isn’t always a hoodie-wearing stranger who encrypts your files and demands payment to release them—though that certainly happens. Sometimes, it’s the employee who accidentally sent a customer’s data to the wrong email address or the external consultant whose laptop is compromised because they clicked “remind me later” too many times on a software update notification.
Dive deeper into the cyber threats to your business.
Download the Cyber Security 101 eBook to uncover the biggest threats to your business and five best practices to enhance your cyber security.
Download the eBook
Why create an incident response plan?
Incident response plans (also called cyber incident response plans or CIRPs for short) are useful during confirmed incidents—like a hacked email account. However, they’re also handy to investigate suspicious events, like finding new, strange code on your corporate website.
If developed properly, the plan will help you answer the following questions about a situation:
- What happened? You can’t stop an attacker if you don’t know how they got in. The steps in your incident response plan will help you identify where the breach happened and what or who was affected.
- Is the problem ongoing? Your CIRP will help you determine if the incident is over or still active. Are the attacker’s behaviours progressing? Are they moving laterally, installing backdoors, or changing account credentials?
- How do I make it stop? IR plans help you systematically carry out technical measures to stop an attack. It may guide you on removing malware, backdoors, or equipment, blocking traffic, or rebuilding the network.
- How do I know it stopped? How do you know it is over, and how do you prove it? The plan will help you confirm that the incident is over and that the team has resolved the root cause so that the same attack doesn’t happen again.
The biggest challenges of incident response
Incident response involves recovering a system to normal operations after an incident. Unfortunately, this isn’t as easy as it seems, especially when organizations don’t have:
- Internal processes to handle the incident, including defined roles
- The right threat or forensic data available, collected, and preserved
- Clarity on how or when to engage external parties, such as an IR team
- Comprehensive documentation of the company’s existing IT Infrastructure
- Guidance on what actions to take during a particular security incident
A properly developed incident response plan helps minimize or eliminate these pain points.
Key components of an incident response plan
It’s a good idea to have your incident response plan align with relevant frameworks (such as NIST or ISO 27001 ), and comply with regulations that govern your business, such as GDPR . And while there are many templates available for you to use, they should only be a starting point. It’ll be much more effective if the plan is customized to fit your company’s unique position.
With this in mind, here are four key sections to include in your incident response plan to make sure it aligns with IR best practices.
1. Introduction and basics
Your incident response plan should start with the basics. Include critical background information and key concepts that members of the response team should know.
Take time to define what “security incident” means to your business and its potential impacts. In your CIRP, explain what goals the plan is meant to meet. What is the scope? How often should the plan be reviewed, updated, or practiced? What types of security incidents does it address? Your response to a social engineering attack will be different from how you respond to an internal employee abusing administrative privileges—your plan should communicate which specific attacks and incidents this plan addresses.
2. Roles and responsibilities
Effective cyber security incident management requires collaboration and coordination across multiple departments. If everybody has a clear idea ahead of time about their role and responsibilities during an incident, things will definitely run smoother.
That’s why your incident response plan absolutely must detail the various roles that make up the IR team, along with their assigned responsibilities. Who’s on the incident response team, what’s their role and contact information, and who’s their replacement when unavailable or away from the office?
There are many more people involved in incident response than you may think. The team leader coordinates IR activities and reports to senior management, a lead investigator conducts the primary investigation, and often a specialized external cyber response team is brought in to help.
But beyond that, there should be someone who heads up the company’s communications strategy for internal and external stakeholders, another person who handles the customer service and support aspect, often a legal representative or compliance expert, and many more. These individuals may be internal or external, but regardless should be included in the document.
Make sure to include an emergency contact list containing your internally assigned individuals with space to add critical roles, if need be.
3. Key IT architectural highlights
Your incident response plan should map out your assets, data, users, devices, and other key aspects of your organization’s IT environment. Remember to include hardware located on-premises (especially if you have multiple offices), Internet of Things devices, endpoints, cloud-based services, accounts, cyber security tools, domains, and more.
The goal is to have a clear and definitive view of your entire IT infrastructure. This serves two purposes:
- This information will live in a central location and is readily available for reference during an incident.
- Mapping your infrastructure can highlight security gaps and blind spots that need addressing.
Your incident response plan should also touch on log and data retention. What logs should you keep and for how long? Having this information available and knowing where you can gather data from will support analysis, response, and reporting if an incident occurs.
This section can feel overwhelming, especially when you’re starting from scratch. A qualified external breach counsel can help identify and document your critical IT architecture.
4. Incident response playbooks
As part of the overall incident response plan, you should develop playbooks that outline the steps needed to contain, analyze, and recover from specific cyber security incidents, such as ransomware or email compromise. These documents guide your team through distinct actions and considerations during an active attack.
When building out your playbooks, consider your most significant security risks. There is no real need to dig into a cloud system compromise if you do not use cloud-based services, for instance.
Containing the cyber attack
One of the worst things you can do during incident response is delete everything to stop the threat—this is a mistake. Doing so may destroy critical evidence necessary for criminal prosecution, not to mention the post-incident report or various regulatory obligations. Instead, isolate the attacker so they cannot spread and cause further damage.
Your incident response plan should cover containment techniques. For example, you may have to disable compromised accounts, take systems offline, change settings or configurations, change passwords, or apply patches and updates. Each playbook should help guide your decision-making for containment.
Gathering and analyzing data
This section involves gathering and analyzing threat data—through disk images, logs, network sensors, endpoint agents, and similar—to develop a narrative about what happened.
During an incident response, you need to know what happened, how the incident was discovered, who discovered it, the areas of impact, the scope of the threat, and the effects on operations.
It’s important to figure out whether the attack will affect the company’s ability to serve users or clients and whether there have been breaches of confidentiality, integrity, or accessibility.
Eliminating and recovering from the threat
After analyzing the threat, your incident response plan should suggest steps for stopping it. You want to find and remove the root cause so that the attacker cannot re-enter. If any trace of the cyber criminal remains—if they still have access to an email account or a backdoor to re-enter the network—they may be able to cause further damage.
Your incident response playbook should detail how to restore and return the affected infrastructure to normal operations. Start by determining whether systems are fixable and can return to their pre-incident state. Make sure to harden your security as well and set up post-incident monitoring to confirm that the threat truly is gone, and your business is secure. Recovery will depend on the incident’s scale and impact, and every restoration plan should reflect investigative findings.
A key piece of this section also has to do with reporting and internal and external communications. Depending on any industry and geographical regulations that affect your business, you may be legally obliged to share public statements describing the breach and damage, remediation measures taken, and post-incident steps.
Best practices of an incident response plan
Keep these fundamentals in mind both while responding to incidents and developing your plan.
Keep your plan brief and simple: proactively preparing for a major security incident can minimize damage to the organization, while reducing incident cost and recovery time. But you don’t want to overdo it with a 1000+ page IR plan.
In other words, keep fluff and needless information to a minimum. Only add in necessary details. By keeping things brief, teams can work quickly, and your organization can recover with minimal damage.
Review, reflect, update: incident response shouldn’t be one-and-done. Implementing a formal revision schedule and conducting regular training can ensure your plan is as effective as possible.
Your incident response plan should outline a post-incident follow-up meeting to share lessons learned. What happened during the incident? What vulnerability was compromised? Do employees need new or different training? What were the plan’s strengths and weaknesses? What changes should be made to improve? How can you make sure the incident doesn’t recur?
Getting help for your IR plan
Having an actionable response plan in place is the most effective way to lower the costs and impact of a security incident, but it’s no easy task.
Our specialists can work with you to assess your current incident response policies and identify areas for improvement. You will receive a comprehensive report detailing our expert’s observations, comments, recommendations, and strategies, which you can then use to build a stronger, more resilient network.
Interested in taking the first step? Check out our Incident Response Planning webpage to learn more about this offering.
Related Resources

Cybersecurity assessments: Your fast path to a stronger defense

Strengthening your cybersecurity: From at-risk to resilient

The 2024 Employee Cybersecurity Handbook

Every Small Business Needs an Incident Response Plan. Here’s How to Start One.

Most small businesses have a list of priorities they’re focused on to make their business successful. For many, cybersecurity doesn’t show up very high on the list—if it shows up at all. Cybersecurity can seem complicated, its solutions are often expensive, and the threat from a cyberattack may seem unlikely. Even if a small business wants to take action, they may not have the internal resources and skills to even know where to start.
For these reasons, some small businesses may be tempted to ignore the threat or just hope that a cyberattack doesn’t happen to them. After all, one might think that malicious actors are probably focused on bigger fish. While it may seem that way in the news, the reality is that 43% of cyberattacks actually target small businesses, and the average cost of a data breach for a small business is $3.9 million, according to Cybint . In the cybersecurity world, it’s not a matter of “if” an incident like this will happen, but “when.”
Unlike larger companies, small businesses may be less equipped to bounce back from a cyber incident. It can be difficult or impossible to recover data that is lost if it’s not backed up. The financial damage of an attack can be substantial. Leaking or exposing customer data can damage a company’s reputation and result in loss of business. Fortunately, there are some practical—and in some cases low tech—steps that companies can take to protect their business and their reputation.
Cybersecurity is about people as much as technology
Protecting a business from a cyber incident isn’t just about standing up sophisticated cybersecurity tools. While malicious actors might try and break into a company’s IT systems through a direct attack, it is easier and more likely that such adversaries will try to gain access through a social engineering attack. This means that the biggest vulnerability to a business’s IT systems is actually their own employees. 95% of cybersecurity breaches are caused by human error, as reported by Cybint .
Through social engineering, malicious actors can prey on the good nature of your employees, manipulating them into handing over sensitive information. For example, a hacker may dupe your employee into clicking an email that installs a piece of malware. Employees who are stressed out, aren’t focused, or are particularly empathetic may be more vulnerable to these kinds of attacks. In creating a plan to protect against cybersecurity incidents, employee training and education are important tools in mitigating risk. This includes providing clear guidance on what employees should do if they spot, or are dealing with, a social engineering attack.
Reduce security risks with an incident response plan
For small businesses, having a plan in place to respond to cyber threats can go a long way in avoiding an incident in the first place, mitigating its impact if it does happen, and bouncing back to normal business operations as quickly and safely as possible. Being prepared is less about having the most sophisticated security technologies and more about knowing your IT environment, understanding your vulnerabilities, educating your employees, and putting into place the right controls to prevent unauthorized use of your IT systems, equipment, and devices.
If an attack does happen, some seemingly small precautions can make all the difference in the world in mitigating damage. This includes having updated contact information for your IT help desk, being able to shut off access to compromised systems quickly, and having your IT systems and data backed up separate from your IT environment in isolated backups.
Having a plan in place to address all of these situations greatly reduces the time to respond to, and recover from, cyber incidents. This type of plan is referred to as an incident response plan . Unique for every company, it is a guide created by your business to provide your employees and IT personnel with guidance on what to do in the event of an unauthorized access of your IT systems.
Incident response plans are typically broken down into four categories: 1) Preparation, 2) Identification, 3) Containment and eradication, and 4) Recovery. Let’s walk through each of these categories and see how they can help protect your business against a cyber incident or attack.
1) Preparation: Don’t fail to plan or you’ll be planning to fail
Any good incident response plan will include measures designed to prevent a cyber incident from happening in the first place as well as guidance on what to do if one happens. Here are some key tips:
Get your security contacts in order: An important part of preparing to handle a cyber incident is simply knowing who you can call if one happens. Keep an up-to-date list of important contacts and parties responsible for critical systems and business operations. You don’t want to be experiencing a breach or attack and be delayed trying to identify who to call. You can also consider partnering with an incident response or cyber insurance firm who can help in the event that an incident is too big for your business to handle. In either case, you should practice looking up contacts and resources on your list so you’ll be ready if the real thing happens.
List your critical business assets: For every business, there are critical IT assets that need to work for the business to function. An important part of any incident response plan is identifying which systems are critical to supporting business operations—whether it’s ecommerce, customer experience, point-of-sale, payments, inventory management, order processing, communications, etc.
Backup everything that is important to business continuity: It is critical to store backups of your data and software on infrastructure that is completely separate from your IT environment. That way, if a cyber incident happens, you won’t experience a loss of important data and you’ll have the ability to roll back to your “known good backups” and restore business operations.
Focus on controls over policies: Having a good security posture means being able to control, to a certain degree, how your employees use their work computers and devices to conduct business. While it may be beneficial to communicate a set of policies around how computers and devices can be used, this can be difficult to enforce. A better approach is to build controls into the technology itself. For example, instead of just telling employees not to install programs that aren’t work related, you can set up controls on users’ work devices that limit their rights to install such programs without permission from your IT department.
2) Identification: Know what you’ve got so you can defend it
A key success factor in cybersecurity for any small business is knowing what you have in your IT environment and how to defend it: What IT equipment do you have? Which security solutions and technologies are available to you? Who are your employees and what kind of access do they have to your systems? It may sound simple, but this IT inventory is a critical part of building your plan because you can’t defend what you don’t know about.
Know what’s in your environment: Understanding what you have in your environment will make defending it a lot easier. A big part of this is knowing what security solutions you have and what their capabilities are. You may find that you can use a tool you already have in a different way. For example, you can use your endpoint and detection response solution to block communications to a malicious IP address if you do not have a firewall on your endpoints.
Know what your risks are: The next step is understanding what types of malicious events are most likely to happen based on your environment specifics. This could include ransomware distributed via a phishing attack, or a distributed denial-of-service attack against legacy firewall systems, or the compromise of VPN accounts due to the lack of multifactor authentication through those remote services. Understanding the nature of these potential threats will make it easier to identify and respond to them if they ever happen.
Know your operating baselines: Next, you’ll want to identify your IT operating baselines. This refers to what business activity and operations generally look like when your people use your IT systems. This will help you know when you have a deviation from those baselines, which could indicate malicious activity or an incident. There are many professional services and solutions providers in the market that can monitor your systems and alert you of an anomaly.
Empower your employees: To strengthen your security posture, it’s important to provide clear and simple instructions on how employees can handle security issues and incidents. For example, you can set up a “spam email box” where employees can forward suspicious emails for inspection. To encourage this good security practice, you can highlight employees who reported those emails in a public forum and or give out prizes to those who reported these incidents.
Make security personal to gain buy-in: A great way to encourage employees to buy-in to good security practices is to make it relatable to their personal lives. Help your user base understand that security controls can be just as important at home as they are in a business context. Provide advice that helps employees protect their home and family—for example, explaining how they can teach friends and family to spot social engineering attacks such as phishing emails.
3) Containment and eradication: Mitigate the damage
The steps you took to identify your arsenal of security tools will be very important when it comes to containing and eradicating a cyber incident. Here are some key capabilities to stop an incident fast:
Stop lateral movement: Security incidents, such as unauthorized logins, can be contained with the right application of security tools, which many companies already have. For example, you can block the IP address of the attack on the firewall so that the attacker can no longer control the originally compromised endpoint.
Shut down access: An important tool in containing incidents is having the ability to quickly shut off access in the event of a breach. That means having a plan in place to lock user accounts, reset passwords, deactivate compromised equipment, and contact the relevant help desk resources and parties responsible for different IT functions.
Eradicate the threat: Once the threat is contained, you need to eradicate it—whether it’s removing malicious code, deleting malware, or removing forwarding rules that an adversary might have placed in a compromised user’s email account. If you find that you didn’t have the right tool in place to eradicate the threat quickly enough, it’s important to reevaluate the identification phase of your incident response plan to put in place the tool you’ll need in the future to address the threat. This exercise is a continual cycle of refining and improving your plan to continually strengthen your security posture.
Ensure the threat is gone: Next, you’ll want to confirm that the threat has been contained and eradicated everywhere. When eradicating an unauthorized user or a piece of malware during a cyber incident, you are removing the threat from a particular endpoint at a specific time. But that doesn’t ensure that the threat has been removed from the entire environment.
4) Recovery: Confirm that the threat has been neutralized
The recovery phase of your incident response plan is about safely returning to business as usual.
Return to business as usual: In the recovery phase, a compromise assessment needs to be done, during which you monitor for additional threats in an isolated environment and bring your systems back up to ensure no suspicious activity survived the rebuild. Malicious actors want persistence, and they achieve it through multiple doors of entry. The recovery phase is about confirming that the threat has been eradicated across systems, paving the way for you to restore your systems from backups and reintroduce them into your active environment as you return to business as usual.
The next step to protect your business
Having an incident response plan in place can go a long way to preventing cyber incidents from happening and limiting the damage if they do happen. The first step in any change is knowing what you don’t know. Converge can help you defend against cyber incidents and set up a continuity plan to protect your operations going forward.
Recent Posts
Leadership perspectives: a q&a with vic verola, evp of north american sales.
What led you to pursue a career in sales? I started my career as an engineer and was doing very well. I was generally consultative as an engineer and enjoyed client interaction. My father, who has always been in sales, influenced me heavily to pursue a career in sales...
The Sustainability Question
Alright, I’ll admit it – I enjoy my job. I find every day exciting and see each moment as an opportunity, although I know I’m lucky to admit such a secret, as not everyone has the chance to feel the same way I do. However, I will also admit that getting to this...
The Converge Advantage: Leading the Way in Technical Solutions and Client Satisfaction
As we set the stage for the year to come, I want to recognize the incredible strides we continue to make transforming a portfolio of diverse companies into a premier integrated leading-edge technical organization. At Converge, we are committed to a standard of...
Want To Read More?
Advanced Analytics
Application Modernization
Cloud Platforms
Cybersecurity
Digital Infrastructure
Digital Workplace
Managed Services
Talent Solutions
Press Releases
You May Also Like…

by Vic Verola
What led you to pursue a career in sales? I started my career as an engineer and was doing very well. I was generally...

by Sheryl Moore
Alright, I’ll admit it – I enjoy my job. I find every day exciting and see each moment as an opportunity,...

by David Luftig
As we set the stage for the year to come, I want to recognize the incredible strides we continue to make transforming...
Let’s Talk
Privacy overview.
- Converge UK
- Converge Germany
At the end of your visit today, would you complete a short survey to help improve our services?
Thanks! When you're ready, just click "Start survey".
It looks like you’re about to finish your visit. Are you ready to start the short survey now?
Create an incident response plan
A workplace accident or emergency can be a traumatic experience and have a devastating effect on you, your staff and your business.
Having a plan for what to do in these situations can help ensure the continuity of your business.
What is an incident response plan
An incident response plan is a tool used to prepare your business for a disturbance or emergency. It is designed to reduce potential harm and damage to you and your business.
An incident response plan explains:
- what actions need to be taken
- how these actions will be completed
- who will complete them.
An incident response plan is different to a crisis management plan, which deals with an incident that is out of control despite the incident response plan being actioned.
The incident response plan is a key component of your business continuity plan.
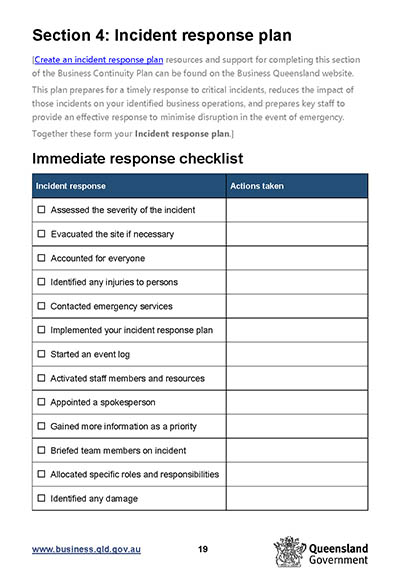
Business continuity plan template
The business continuity plan template includes an incident response plan section.
Download the business continuity planning template .
Managing priorities during an incident
During an incident or emergency, you may be faced with many issues happening at the same time which all need to be managed. A well-developed incident response plan will help you prioritise and delegate tasks during an emergency situation.
When developing your plan, consider how you and your staff will respond to:
- physical danger—this is your first priority. Make sure everyone on your premises is safe and receives medical attention if needed.
- feelings of stress, confusion or anger
- intense or negative media attention
- intense or negative responses from your stakeholders
- limited time to make decisions
- key staff being unavailable
- interruptions to your key business operations.
What to include in your incident response plan
A typical incident response plan includes the following items.
Create a checklist for the first actions you'll take when actioning your plan. This may include:
- evacuating and contacting emergency services
- ensuring everyone on your premises is accounted for
- briefing staff
- identifying immediate damage.
Clearly explain how people will evacuate your premises. This may include:
- a floor plan of the site
- an evacuation map with meeting place highlighted
- key contact names and phone numbers
- a staff and visitor log for the day
- a log of people present for completion once in the evacuation meeting place.
An emergency kit is a pack of important items, documents and equipment that you may need in the event of an incident or emergency. Keep your kit somewhere easily accessible so you can grab it if you need to leave quickly or evacuate.
A typical emergency kit contains:
- checklists for potential disasters (e.g. cyclone, severe storm, flood, bushfire, IT threat)
- first aid supplies
- torches, radios and batteries
- key computer data backed up onto an external hard drive or USB
- key contact details (e.g. staff, emergency services, your accountant, power and water companies)
- important business files (e.g. insurance policies, your business continuity plan , financial documents)
- other items you may need (e.g. signs, beacons).
Clearly define which staff will be involved in an incident response, and what their duties will be. This may include
- nominating an incident response team leader
- identifying key roles and who will fill them
- defining the responsibilities of each role.
Develop a list of important contact information. This may include:
- a list of internal contacts (e.g. staff)
- a list of external contacts (e.g. security services, insurance company, utility companies)
- emergency services contacts.
Use an event log to record information, decisions and actions during and immediately after an incident. This generally includes:
- the date and time something has happened
- details of the decision you are making, or action you are taking
- who was involved.
Work-related death, a serious injury or illness, or a dangerous incident
If an injury, illness or dangerous incident has occurred in your workplace you may be legally required to notify Workplace Health and Safety Queensland (WHSQ).
Learn about reporting incidents to WHSQ .
Storing your incident response plan
Consider how you might need to use your plan in an emergency and who might need to access it. Make sure you and other key people can access your plan both on-site and off-site. You could:
- keep a copy of your plan in the cloud
- keep a copy in another location
- use incident management software
- use internal apps or platforms.
Incident response team
Consider who is the best person to be your incident response team leader—as the business owner, this may not always be you. You may prefer to delegate this responsibility to a trusted senior staff member who:
- has prior experience
- is more regularly at your premises
- you can train to take charge.
Following an incident, employees critical to your business will need to focus on continuing the business, dealing with suppliers, customers, and other key stakeholders such as banks and insurance companies.
When planning your emergency response team, ensure you have suitable people in roles you know they are comfortable and can perform well in. Multiple roles can be performed by the same person if needed.
Even though your business may have a thorough incident response plan, emergency services may assume responsibility during an emergency situation.
Roles and responsibilities
Post-incident review.
Review your incident response procedures after an event or training session to identify gaps or areas where you can improve. Ask for feedback from everyone involved in the incident or training to ensure you pick up on issues from all areas of the response.
Incident response case studies
A fire breaks out in your business, but the staff member who is your appointed fire warden is on leave. Due to regular incident training, you had identified this as a potential risk, and had trained a backup fire warden to carry out the incident response plan.
The plan involved:
- calling 000
- conducting an emergency evacuation
- conducting a head count to ensure all staff and visitors were out of the building
- directing when and how fire extinguishers and fire blankets were to be used and by whom.
Ensure all staff are fully trained in your incident response plan, and know how to follow it should an incident occur.
Conducting regular practice drills within your workplace (e.g. a fire drill) will help all staff know the steps to take when an incident occurs. It will also help you to identify areas that need improvement, and make tweaks to your plan.
A small business had a ransomware attack on a computer. Ransomware is a tool used to encrypt or lock computer data until the business pays money to the attacker.
The business incident response plan included a checklist of immediate steps to take including:
- removing the computer from the network to prevent the spread to other computers and devices
- backing up all files regularly to allow them to be downloaded onto another computer with no ransomware
- contacting external technical support to remove the ransomware
- checking for breaches of data security through an external specialist
- reloading backed up files to the cleaned computer
- conducting a post-incident review.
Read more about online risks and IT security .
Also consider...
- Find out about writing a business continuity plan .
- Read how to develop a recovery plan .
- Last reviewed: 24 Nov 2022
- Last updated: 24 Nov 2022

Incident Response Plan vs Business Continuity Plan
May 8, 2023

An Incident Response Plan (IRP) and a Business Continuity Plan (BCP) are two key components of a comprehensive risk management strategy. They have different goals but can complement each other to help ensure your business is prepared for any disruption. Understanding the differences between these two plans can help you create a contingency plan that meets all of your business’s needs.
An incident response plan (IRP) and a business continuity plan (BCP) are two important documents that organizations should have in place to protect their data and operations. While they are both essential for any organization , they serve different purposes.
An incident response plan is designed to help an organization respond quickly and effectively to security incidents such as data breaches, malware attacks, or other cyber threats. Apart from the disaster recovery plan .
It outlines the steps that should be taken in each phase of incident response, including detection, containment, eradication, recovery, and post-incident analysis.
An effective IRP should also include roles and responsibilities for each team member involved in the process .
On the other hand, a business continuity plan is designed to help an organization prepare for unexpected events that could disrupt its operations. This includes natural disasters such as floods or earthquakes and human-caused disruptions like power outages or cyberattacks.
A BCP outlines the processes and procedures necessary for keeping critical operations running during these events. It also includes strategies for restoring normal operations once the event has passed.
Both an incident response plan and a business continuity plan are essential components of any organization’s cybersecurity strategy and key performance indicators for business continuity management.
They provide guidance on how to respond to incidents quickly and efficiently while minimizing disruption to operations so that businesses can remain secure and resilient in the face of any threat.

What is an Incident Response Plan?
An incident response plan (IRP) is a set of documented procedures that outlines the steps to be taken in the event of a security incident. It should include details on detecting, responding to, and limiting the consequences of malicious cyber activity.
The plan should also identify roles and responsibilities for security team members and provide guidance on how to communicate with stakeholders. Response procedures of service attacks and cyber incidents.
The incident response plan typically consists of six phases: preparation, identification, containment, eradication, recovery, and lessons learned. Preparation involves creating an inventory of assets and identifying potential threats.
Identification is when the security team identifies a malicious event or breach. Containment focuses on limiting the scope and impact of an attack by isolating affected systems or networks.
Eradication involves removing any malicious code or actors from the system. Recovery focuses on restoring normal operations while maintaining data integrity . Finally, lessons learned look at what went wrong during the incident and how it can be prevented in future incidents.
An IRP is designed to address specific incidents or emergencies. Incident response vs business continuity outlines how the organization will respond if it faces an incident or emergency, such as a natural disaster , security breach, or power outage.
The plan should include details on how to alert employees, customers, and other stakeholders; assign roles and responsibilities; assess the damage; take corrective action; and restore operations as quickly as possible.
It should also include information on where to find critical data, such as customer records or financial documents, in case they are destroyed or lost during the incident.
What is a Business Continuity Plan?
A BCP focuses more broadly on how to maintain operations in spite of disruptions . This could include anything from natural disasters to computer system malfunctions. Unlike an IRP, which focuses mainly on responding to an emergency after it has occurred, a BCP looks at ways to prevent potential disruptions from occurring in the first place by developing strategies for dealing with them if they do occur.
A well-crafted BCP will also provide guidance on testing processes and procedures before an incident occurs so that businesses can be sure their plans are effective when needed most.
What’s the difference between BCPs, DRPs, & Incident Response Plans
Business Continuity Plans (BCPs), Disaster Recovery Plans (DRPs), and Incident Response Plans (IRPs) are all important components of an organization’s contingency planning business continuity functions. BCPs are designed to help organizations prepare for and recover from any disruption , whether natural disasters, cyber-attacks, or other unforeseen events.
DRPs focus on the recovery of IT systems and data after a disaster or cyber incident has occurred. IRPs are specific procedures that should be followed when responding to a cyber-attack or other security incident.

Why is an Incident Response Plan Critical to Maintain Business Continuity?
The internet isn’t yet vulnerable to attacks, so it won’t happen. When you suffer unauthorized access to a computer network or other device, the effects may become overwhelming. Disaster Recovery Plans can help reduce risks and prepare for the future.
Recovery plans may reduce the time and cost associated with a security or data breach itself, allowing stakeholders to restructure forensic digital evidence to reduce recovery time, customer churns, and negative publicity. According to the Ponemon Institute, data breaches cost about $3.6m annually.
Who is Responsible for Developing an Incident Response Plan?
CSIRT will assess, classify and address security incidents if deemed relevant to the business. Incident response teams must be composed: Security experts should help and support the affected human resources, , and the team must execute technical and operational measures.
Incident response managers are responsible for the supervision of the investigation, surveillance, and recovery of a specific incident. The company will provide the firm with a severe breach to other employees, regulatory agencies, customer groups and the public if the breach happens.
The individual or team responsible for developing the IRP should have knowledge of the organization’s IT infrastructure and security policies. They should also have experience with incident response processes and procedures. In addition to developing the plan, they should also be responsible for training staff on how to use it in case of a security incident.
Developing Incident response plans and business continuity plans
Identify the plan’s objectives and goals.
Your goal is to maintain business continuity and ensure that you are unable to perform key activities in your essential business operations. These include key business operations throughout the organization: operations personnel, public relations, and communications.
However, each business has its own goal, which is crucial to its operation. It may be different according mainly to the type and size of the company. Once your goal is identified , map your strategic plans accordingly. Make sure the objectives are fully understood.
Identify the important business functions
When you’re considering whether your company will operate as an emergency response team or if your business needs other emergency management services, they need assistance. In addition to meeting customer needs, a company must maintain constant supplies of materials, keep track of inventories and meet ship-to-ship targets.
Identify the threat
The only way to reduce security threats accurately is by evaluating their severity. Start with infected hardware or patient zeros. The idea here is to find out who triggered the incident.
Only identifying the incident can give a reliable indication of deteriorating conditions. Instead of replicating the infected device, it is important that you find all the distinct indicators that indicate compromise that can then be used to search your entire property to find additional evidence of compromise.
Create an Incident Response Team
The response to incidents must involve a number of cross-functional leadership roles, as well as anyone else you believe is helpful within the group. Design a leader capable of making the right decisions and making consistent progress.
All staff members should have specialist knowledge in all technical and non-technical domains, a few examples of this include forensic investigations. Requiring outside specialists in incident handling.
Establish a communication plan
In the event of a catastrophe, a proper crisis communications plan is required. You need a communication strategy to communicate effectively with stakeholders within your own organization’s emergency management . In emergencies , communication may be limited by a sample message written for vendors, partners or staff. Incident response teams can improve their coordination of activity based on a carefully planned communication plan .
Conduct a Risk Assessment and Business Impact Analysis (BIA)
The BIA can identify significant threats to the organisation.
Keep the plan updated
Business continuity planning is essentially a long-term process . It should be evaluated continuously for its effectiveness. In emergency scenarios, teams may test their readiness through simulation tests. Based on data, adjust plans and review them.
Backup the important data
Take a copy of anything you can’t lose. Consider anything from client info through employee documents to company e-mail. The product also requires easy access in a disaster , enabling the firm to return quickly.
Many organisations store large amounts of information online but often rely upon paper documents. Contract documents, tax returns, and payroll documents have many examples . To prevent the loss of documents, use hard copies whenever possible.
What is the importance of an incident management plan?
Having ignored recent developments would have been a mistake, if not a major mistake. It’s essential to manage your business . Disruptions can be dangerous for companies – but even for smaller ones.
90% of small business owners are in financial trouble in a year. Those companies risk losing their customers, revenue, and good reputation.
Continue Business Operations
This helps maintain your business operation when a crisis strikes, reducing financial losses too. It gives everyone involved a sense of security and reassures them that your business will continue to grow. Communication across organizations is essential for keeping all employees informed.
It may cause problems in many organizations, with a large number of employees working remotely or with offices worldwide. Organisations should look at introducing solutions to facilitate instant, easy communication.
Gain competitive advantage
Make it easy to convince customers to come to your firm with an effective emergency response plan . How we respond to a crisis reflects much on our business reputation. Write an inspiring tale. Rapid thinking is a good way to be prepared to face the toughest competition.
Protect Your Supply Chain
Remember, natural disasters also affect suppliers . Assuring the distribution of risk across the supply chain ensures your plan provides for supply chain stability.
Reduce Financial Risk
Rapid action during a crisis can reduce the downtime in your business if needed . Longer downtime means greater costs and increased risks . Minimise the risk of damage by replacing functional items as quickly as possible.
When designing your organization’s risk management strategy , it’s important to consider both an Incident Response Plan and a Business Continuity Plan. While they have different goals—the former addressing specific incidents while the latter looking at broader strategies for maintaining operations—they can complement each other when properly implemented.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.
Building a Saas Business Continuity Plan Template
Business Continuity vs Disaster Recovery vs Incident Response plans
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Reach out to understand more about Enterprise Risk Management, Project Management and Business Continuity.
© 2024 Risk Management

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
HHS Statement Regarding the Cyberattack on Change Healthcare
The U.S. Department of Health and Human Services (HHS) is aware that Change Healthcare – a unit of UnitedHealth Group (UHG) – was impacted by a cybersecurity incident in late February. HHS recognizes the impact this attack has had on health care operations across the country. HHS’ first priority is to help coordinate efforts to avoid disruptions to care throughout the health care system.
HHS is in regular contact with UHG leadership, state partners, and with numerous external stakeholders to better understand the nature of the impacts and to ensure the effectiveness of UHG’s response. HHS has made clear its expectation that UHG does everything in its power to ensure continuity of operations for all health care providers impacted and HHS appreciates UHG’s continuous efforts to do so. HHS is also leading interagency coordination of the Federal government’s related activities, including working closely with the Federal Bureau of Investigations (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the White House, and other agencies to provide credible, actionable threat intelligence to industry wherever possible.
HHS refers directly to UHG for updates on their incident response progress and recovery planning. However, numerous hospitals, doctors, pharmacies and other stakeholders have highlighted potential cash flow concerns to HHS stemming from an inability to submit claims and receive payments. HHS has heard these concerns and is taking direct action and working to support the important needs of the health care community.
Today, HHS is announcing immediate steps that the Centers for Medicare & Medicaid Services (CMS) is taking to assist providers to continue to serve patients. CMS will continue to communicate with the health care community and assist, as appropriate. Providers should continue to work with all their payers for the latest updates on how to receive timely payments.
Affected parties should be aware of the following flexibilities in place:
- Medicare providers needing to change clearinghouses that they use for claims processing during these outages should contact their Medicare Administrative Contractor (MAC) to request a new electronic data interchange (EDI) enrollment for the switch. The MAC will provide instructions based on the specific request to expedite the new EDI enrollment. CMS has instructed the MACs to expedite this process and move all provider and facility requests into production and ready to bill claims quickly. CMS is strongly encouraging other payers, including state Medicaid and Children’s Health Insurance Program (CHIP) agencies and Medicaid and CHIP managed care plans, to waive or expedite solutions for this requirement.
- CMS will issue guidance to Medicare Advantage (MA) organizations and Part D sponsors encouraging them to remove or relax prior authorization, other utilization management, and timely filing requirements during these system outages. CMS is also encouraging MA plans to offer advance funding to providers most affected by this cyberattack.
- CMS strongly encourages Medicaid and CHIP managed care plans to adopt the same strategies of removing or relaxing prior authorization and utilization management requirements, and consider offering advance funding to providers, on behalf of Medicaid and CHIP managed care enrollees to the extent permitted by the State.
- If Medicare providers are having trouble filing claims or other necessary notices or other submissions, they should contact their MAC for details on exceptions, waivers, or extensions, or contact CMS regarding quality reporting programs.
- CMS has contacted all of the MACs to make sure they are prepared to accept paper claims from providers who need to file them. While we recognize that electronic billing is preferable for everyone, the MACs must accept paper submissions if a provider needs to file claims in that method.
CMS has also heard from providers about the availability of accelerated payments, like those issued during the COVID-19 pandemic. We understand that many payers are making funds available while billing systems are offline, and providers should take advantage of those opportunities. However, CMS recognizes that hospitals may face significant cash flow problems from the unusual circumstances impacting hospitals’ operations, and – during outages arising from this event – facilities may submit accelerated payment requests to their respective servicing MACs for individual consideration. We are working to provide additional information to the MACs about the specific items and information a provider’s request should contain. Specific information will be available from the MACs later this week.
This incident is a reminder of the interconnectedness of the domestic health care ecosystem and of the urgency of strengthening cybersecurity resiliency across the ecosystem. That’s why, in December 2023, HHS released a concept paper that outlines the Department’s cybersecurity strategy for the sector. The concept paper builds on the National Cybersecurity Strategy that President Biden released last year, focusing specifically on strengthening resilience for hospitals, patients, and communities threatened by cyber-attacks. The paper details four pillars for action, including publishing new voluntary health care-specific cybersecurity performance goals, working with Congress to develop supports and incentives for domestic hospitals to improve cybersecurity, increasing accountability within the health care sector, and enhancing coordination through a one-stop shop.
HHS will continue to communicate with the health care sector and encourage continued dialogue among affected parties. We will continue to communicate with UHG, closely monitor their ongoing response to this cyberattack, and promote transparent, robust response while working with the industry to close any gaps that remain.
HHS also takes this opportunity to encourage all providers, technology vendors, and members of the health care ecosystem to double down on cybersecurity, with urgency. The system and the American people can ill afford further disruptions in care. Please visit the HPH Cyber Performance Goals website for more details on steps to stay protected.
Sign Up for Email Updates
Receive the latest updates from the Secretary, Blogs, and News Releases
Subscribe to RSS
Receive latest updates

Related News Releases
Hhs expands tefca by adding two additional qhins, health resources and services administration takes historic new steps to transform the organ transplant system to better serve patients, guiding principles help healthcare community address potential bias resulting from algorithms, related blog posts.

Reflecting on Cybersecurity Awareness Month
Navigating section 752: insights from program managers on success, challenges, and tools for change, thank you to the 2023 civic digital fellows, media inquiries.
For general media inquiries, please contact [email protected] .
Health-ISAC Supports Health Industry Cybersecurity Strategic Plan
ORMOND BEACH, Fla., March 12, 2024 (GLOBE NEWSWIRE) -- Health-ISAC, a non-profit, member driven organization is pleased to contribute to the Health Industry Cybersecurity Strategic Plan ” (HIC-SP), recently published by the Healthcare and Public Health (HPH) Sector Coordinating Council (HSCC) Cybersecurity Working Group (CWG).

Health-ISAC’s Incident Response working group , a joint group with HSCC’s CWG, along with 174 other industry groups, collaborated for eighteen months to produce the HIC-SP, a roadmap for reaching ten goals outlined in the plan over the next five years.
“Health-ISAC’s operational coordination efforts compliment the strategic function of the HSCC in a shared mission for critical infrastructure resilience,” said Denise Anderson, President and CEO, Health-ISAC. “We are excited to support this very important endeavor and in particular achieve goals like number nine, which aims to establish and implement preparedness, response, resilience and access across the health ecosystem.”
The Health Industry Cybersecurity Strategic Plan is a call to action for organizations throughout the health ecosystem to implement foundational cybersecurity programs that address the operational, technological and governance challenges posed by significant health industry trends over the next five years.
ABOUT HEALTH-ISAC
Health-ISAC — a non-profit, private sector, member-driven organization — plays an essential role in providing situational awareness around cyber and physical security threats to the Healthcare Sector so that companies can detect, mitigate, and respond to ensure operational resilience. Health-ISAC connects thousands of healthcare security professionals worldwide to share peer insights, real-time alerts, and best practices in a trusted, collaborative environment. As the go-to source for timely, actionable, and relevant information, Health-ISAC is a force-multiplier that enables healthcare organizations of all sizes to enhance situation awareness, develop effective mitigation strategies and proactively defend against threats every single day.
ABOUT HSCC CYBERSECURITY WORKING GROUP
The Health Sector Coordinating Council (HSCC) Cybersecurity Working Group (CWG) is a government-recognized critical infrastructure industry council of more than 425 healthcare providers, pharmaceutical and medtech companies, payers and health IT entities partnering with government to identify and mitigate cyber threats to health data and research, systems, manufacturing and patient care. The CWG membership collaboratively develops and publishes freely-available healthcare cybersecurity best practices and policy recommendations, and produces outreach and communications programs emphasizing the imperative that cyber safety is patient safety. See https://HealthSectorCouncil.org .
Please direct media inquiries to: Julia Annaloro Marketing and Communications Associate [email protected] +1 321-593-1470 LinkedIn: https://www.linkedin.com/company/health-isac/ Twitter: https://twitter.com/HealthISAC
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/ad24e118-50f1-4c60-9b5c-a34eecd0419b


IMAGES
VIDEO
COMMENTS
A well-designed incident response plan can be the crucial differentiator that enables an organization to quickly contain the damage from an incident and rapidly recover normal business operations. Companies developing their incident response plans should follow these steps. Step 1. Create a policy.
A security and privacy control, the incident response plan is responsible for: Describing the structure and organization of the incident response capability and providing a high-level approach for how the capability fits into the overall organization. Defining the resources and management support needed to effectively maintain and mature this ...
1. Preparation - Perform a risk assessment and prioritize security issues, identify which are the most sensitive assets, and which critical security incidents the team should focus on. Create a communication plan, document roles, responsibilities, and processes, and recruit members to the Cyber Incident Response Team (CIRT). 2.
Define the CSIRT (Computer Security Incident Response Team) To act quickly and completely while an incident is unfolding, everyone on the CSIRT needs to know their responsibilities and the decisions that are theirs to make. The CSIRT should include a cross section of business and technical experts with the authority to take action in support of ...
A Business Continuity Plan will help get the business back up and running to meet its minimal SLA expectations, and a disaster recovery plan will help the business return to its original operational state before the attack. ... An incident response plan is also a requirement for certain cybersecurity regulations, including: HIPAA - Security ...
It is crucial a business has an incident response plan so that under the pressure of an incident the correct decisions can be made to bring the situation back under control. A cybersecurity incident can be a very daunting situation, if the response is not conducted in an orchestrated manner then the potential outcome could result in severe ...
An incident response plan is a document that outlines an organization's procedures, steps, and responsibilities of its incident response program. Incident response planning often includes the following details: how incident response supports the organization's broader mission. the organization's approach to incident response.
An incident response plan template is a document designed to help businesses develop their own IR plan and procedures. These templates are often based on existing frameworks, such as the National Institute of Standards and Technology's (NIST) Computer Security Incident Handling Guide or the SANS Institute's Incident Handlers Handbook.
An Incident Response Plan is a written document, formally approved by the senior leadership team, that helps your organization before, during, and after a confirmed or suspected security incident. Your IRP will clarify roles and responsibilities and will provide guidance on key activities. It should also include a cybersecurity list of key ...
An incident response plan is a set of written instructions that outline your organization's response to data breaches , data leaks , cyber attacks and security incidents. Incident response planning contains specific directions for specific attack scenarios, avoiding further damages, reducing recovery time and mitigating cybersecurity risk .
An effective incident response (IR) plan is a combination of people, processes and technologies that is documented, tested and trained in the event of a security incident. Incident response plans are designed to prevent data and monetary loss while supporting the restoration of regular business operations.
The Incident Response Plan should be updated and tested regularly, taking into account changes in the business environment, new threats, and lessons learned from previous incidents and tests. This helps ensure that the plan remains up-to-date and effective in responding to any incident.
The best way to prepare is to take stock of your technology and systems, identify the most likely threats, and enlist your team of experts to help you create and implement your response plan. 1 ...
An incident response plan often includes: A list of roles and responsibilities for the incident response team members. A business continuity plan. A summary of the tools, technologies, and physical resources that must be in place. A list of critical network and data recovery processes. Communications, both internal and external. 5. Train your ...
A formal incident response plan enables cybersecurity teams to limit or prevent damage. The goal of incident response is to prevent cyberattacks before they happen, and to minimize the cost and business disruption resulting from any cyberattacks that occur. Ideally, an organization defines incident response processes and technologies in a ...
Establish the organizational structure for incident response. Define roles and responsibilities. List the requirements for reporting incidents. The plan should then provide a roadmap for implementing your incident response program based on the policy. 2. Define short and long-term goals of incident response program.
The incident response plan should cover how to detect, analyze, contain, eradicate, and recover from an incident. The incident response lifecycle has two crucial parts that should not be glossed over preparation and post-incident activities. The incident response plan should define and cover all phases of the incident response lifecycle ...
A cross-functional team is responsible for incident response. IT will typically be in charge of identifying, isolating, and recovering from threats, however there is more to incident response than finding and getting rid of bad actors. Depending on the type of attack, someone may have to make a business decision, such as how to address a ransom.
Your business may only need Google Docs or Microsoft Word for documenting an incident response plan. But you may want software with additional capabilities for creating and updating documents ...
This factsheet provides an overview of an Incident Response Plan and how it should be implemented before, during, and after a cybersecurity incident. ... Cybersecurity Best Practices, Election Security. Related Resources. Mar 12, 2024. Publication. Secure Cloud Business Applications: Hybrid Identity Solutions Guidance. Mar 11, 2024. Publication ...
An incident response (IR) plan is a formal document that guides an organization's response to a cyber security incident. IR plans cover both the technical and business aspects of incident response, with recommended steps to help teams prepare for, detect, respond to, and recover from a potential cyber attack.
Having a plan in place to address all of these situations greatly reduces the time to respond to, and recover from, cyber incidents. This type of plan is referred to as an incident response plan. Unique for every company, it is a guide created by your business to provide your employees and IT personnel with guidance on what to do in the event ...
An incident response plan is a tool used to prepare your business for a disturbance or emergency. It is designed to reduce potential harm and damage to you and your business. who will complete them. An incident response plan is different to a crisis management plan, which deals with an incident that is out of control despite the incident ...
An incident response plan (IRP) and a business continuity plan (BCP) are two important documents that organizations should have in place to protect their data and operations. While they are both essential for any organization, they serve different purposes.. An incident response plan is designed to help an organization respond quickly and effectively to security incidents such as data breaches ...
An effective incident response plan addresses incident detection, analysis, containment, workarounds or fixes, prevention, logging of events, preservation of evidence, and post-incident review ...
FOR IMMEDIATE RELEASE March 5, 2024. Contact: HHS Press Office 202-690-6343 [email protected]. HHS Statement Regarding the Cyberattack on Change Healthcare. The U.S. Department of Health and Human Services (HHS) is aware that Change Healthcare - a unit of UnitedHealth Group (UHG) - was impacted by a cybersecurity incident in late February.
Health-ISAC's Incident Response working group, a joint group with HSCC's CWG, along with 174 other industry groups, collaborated for eighteen months to produce the HIC-SP, a roadmap for ...
Actions to support patients. UnitedHealth Group continues to make substantial progress in mitigating the impact to consumers and care providers of the unprecedented cyberattack on the U.S. health system and the Change Healthcare claims and payment infrastructure. Our focus has been on ensuring access to care and medications by addressing ...
Hence, a comprehensive Incident Response plan must be in place to ensure high service availability in case of cyber-attacks or operational errors. Currently, utility operators execute such plans mostly manually, requiring extensive time, effort, and domain expertise, and they are prone to human errors. ... business continuity on the smart meter ...