An official website of the United States government
The .gov means it's official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you're on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
- Browse Titles
NCBI Bookshelf. A service of the National Library of Medicine, National Institutes of Health.
National Research Council (US) Whither Biometrics Committee; Pato JN, Millett LI, editors. Biometric Recognition: Challenges and Opportunities. Washington (DC): National Academies Press (US); 2010.


Biometric Recognition: Challenges and Opportunities.
- Hardcopy Version at National Academies Press
5 Research Opportunities and the Future of Biometrics
The first four chapters of this report explain much about biometric systems and applications and describe many of the technical, engineering, scientific, and social challenges facing the field. This chapter covers some of the unsolved fundamental problems and research opportunities related to biometric systems, without, however, suggesting that existing systems are not useful or effective. In fact, many biometric systems have been successfully deployed. For example, hand geometry systems serve to control access to, among others, university dorms, nuclear power plants, and factories, where they record time and location. 1 Automated fingerprint identification systems (AFISs) integrate automatic and manual processes in criminal justice applications and civilian applications such as national identity systems.
An emerging technology such as biometrics typically confronts unrealistic performance expectations and is sometimes unfairly compared with approaches such as passwords that are not really alternatives. An effective biometric solution does not have to be—nor can it be—100 percent accurate or secure. For example, if there exists a 1 percent possibility of successful “buddy punching” (signing in for a friend or colleague), a hand geometry system can easily be seen as preventing 99 percent of such fraud. A particular application demands not perfection but satisfactory performance justifying the additional investments needed for the biometric system. In any given case, the system designer should understand the application well enough to achieve the target performance levels.
Nevertheless, solutions to the problem of recognizing individuals have historically been very elusive, and the effort needed to develop them has consistently been underestimated. Because humans seem to recognize familiar people easily and with great accuracy, such recognition has sometimes incorrectly been perceived as an easy task. Considering that a number of governments around the world have called for the nationwide use of biometrics in delivering crucial societal functions such as passports, there is an urgent need to act. Excepting for their application in national forensic AFISs, biometric recognition systems have never been tried at such large scales nor have they dealt with the wide use of nonforensic sensitive personal information. The current performance of some biometric systems—in particular with regard to the combination of error rate, robustness, and system security—may be inadequate for large-scale applications processing millions of users at a high throughput rate.
If there is a pressing public need for these applications, and if it is determined that biometric systems and technologies are the most appropriate way to implement them, then our understanding of the underlying science and technology must be robust enough to support the applications. 2 There is no substitute for realistic performance evaluations and sustained investment in research and development (R&D) to improve human recognition solutions and biometric systems. 3 The rest of this chapter outlines a research agenda focusing on (1) technical and engineering considerations, (2) social challenges, and (3) broader public policy considerations. The chapter concludes with a high-level overview of what constitutes a well-designed biometric system.
- TECHNOLOGY AND ENGINEERING RESEARCH OPPORTUNITIES
In recent years several research agendas for biometric technologies and systems have set important challenges for the field. 4 The issues and research opportunities raised in this chapter are meant to complement, not replace or supersede these other articulations. Indeed, the U.S. government has created or funded several interdisciplinary, academia-based research programs that provide an institutional foundation for future work. The focus of this report has been on broad systems-level considerations, particularly for large-scale applications, and the technical challenges outlined in this Chapter reflect that focus. But as these other agendas demonstrate, there are numerous opportunities for deeper understanding of these systems at almost every level. This section lays out several technical and engineering areas the committee believes would benefit from sustained research and further investigation: human factors, understanding the underlying phenomena, modality-related technical challenges, opportunities to advance testing and evaluation, statistical engineering aspects, and issues of scale.
Human Factors and Affordance
Because biometric technologies and systems are deployed for human recognition applications, understanding the subject-technology interface is paramount. A key piece of the biometric recognition process is the input of the human characteristic to be measured. With the exception of recent work at NIST-IAD 5 and at Disney, very little effort has been expended on the “affordance”—the notion that what is perceived drives the action that occurs, or, put another way, that form can drive function—of biometric systems. 6 Biometric systems should implicitly (or explicitly) suggest to the user how they are to be interacted with. 7
International standards, such as the International Organization for Standardization (ISO)/IEC 19795 series, 8 generally contain an informative annex on best practices for data collection for the modality under consideration. For example, ISO/IEC 19794-5 contains an annex on best practices for face images specifying that full frontal face poses should be used and rotation of the head should be less than +/− 5 degrees from frontal in every direction. This requirement presents an affordance challenge that has not yet been adequately addressed by the technologies—namely, how can a system be designed to suggest to the user a pose that meets this requirement? (The committee was told about one system that presented an image that, when viewed from the proper angle, was clearly visible to the user.) Similar challenges exist with every modality/application combination and will require a modality- and application-specific set of solutions.
“Quality” has been used to indicate data collected in compliance with the assumptions of the matching algorithms, such that recognition performance of the algorithm can be maximized, which means that “affordance” and data “quality” are tightly linked. System operators and administrators face their own challenges when interfacing with the systems. How should the interfaces of attended systems be designed so that the operator knows how and when to collect proper images, how to recognize when poor-quality images have been collected, and how to guide the data subject in making better presentations? Very little research in this area has been conducted, and there is opportunity for significant progress.
Distinctiveness and Stability of Underlying Phenomena
There are many open questions about the distinctiveness of the underlying biometric traits in these systems and about human distinctiveness generally. One typical assumption in the design of most biometric systems has been that characteristics, if properly collected, are sufficiently distinctive to support the application in question. This assumption has not, however, been confirmed by scientific methods for specific biometric characteristics, either by prospectively collecting and analyzing biometric samples and feature patterns or by exploiting databases of samples or feature patterns assembled for other purposes. A broad and representative sampling of the population in which distinctiveness is being evaluated should be obtained and a minimum quality specification should be set to which biometric samples should conform. More generally, the development of a scientific foundation for reliably determining the distinctive ness of various biometric traits under a variety of collection modes and environments is needed.
In other words, what is the effective limit on accuracy for a specific biometric trait in a realistic operating environment? This becomes a particularly important question at scale—that is, when the systems are expected to cope with large user populations and/or large reference databases. Even in DNA analysis, there has been controversy and uncertainty over how to estimate distinctiveness. 9 In biometric systems, “ground truth”—the collection of facts about biometric data subjects and recognition events to allow evaluation of system performance—is challenging, particularly for passive surveillance systems, where failures to acquire may be difficult to detect. 10
There are also open questions about the stability of the underlying traits—how persistent (stable) will a given individual’s biometric traits be over time? Some biometric traits, such as fingerprints, appear to be reasonably stable, but others, such as facial characteristics, can change significantly over even short periods of time. Depending on the capture and matching algorithms, changes in a trait over time may or may not have an effect on system performance and whether that person is appropriately recognized. Understanding more about the stability of common biometric traits will be important, especially if biometric systems are deployed for comparatively long (years or decades) periods of time.
All of this suggests several avenues of research that could strengthen the scientific underpinnings of the technology. There needs to be empirical analysis of base-level distinctiveness and the stability of common biometric modalities, both absolutely and under common conditions of capture, and research into what types of capture and what models and algorithms produce the most distinguishable and stable references for given modalities. Further, the scalability of various modalities under different capture and modeling conditions must be studied. The individuality of biometric identifiers, their long- and short-term physiological/pathological variations, and their relationship to the user population’s genetic makeup all merit attention as well.
Modality-Related Research
Every biometric system relies on one or more biometric modalities. The choice of modality is a key driver of how the system is architected, how it is presented to the user, and how match vs. nonmatch decisions are made. Understanding particular modalities and how best to use the modalities is critical to overall system effectiveness. Research into several interrelated areas will bring continued improvement:
- Sensors. Reducing the cost of sensor hardware; improving the signal-to-noise ratio, the ease of use and affordability, and the repeatability of measures; and extending life expectancy.
- Segmentation. Improving the reliability of identifying a region of interest when the user presents his or her biometric characteristics to the system—for example, locating the face(s) in an image or separating speech signal from ambient noise.
- Invariant representation. Finding better ways to extract invariant representation (features) from the inherently varying biometric signal—that is, what kind of digital representation should be used for a face (or fingerprint or other feature) such that the trait can be recognized despite changes in pose, illumination, expression, aging, and so on.
- Robust matching. Improving the performance of the matching algorithm in the presence of imperfect segmentation, noisy features, and inherent signal variance.
- Reference update. Developing ways to update references so that they can account for variations and the aging of reference data in long-lived systems.
- Indexing. Developing binning and partitioning schemes to speed up searches in large databases.
- Robustness in the face of adversaries. Improving robustness to attacks, including the presentation of falsified biometric traits (perhaps, for example, through automated artifact detection).
- Individuality. Exploring the distinctiveness of a particular biometric trait and its relationship to the matching performance. Does information about distinctiveness serve to increase understanding of the effective limits on matching performance, for example?
In addition to the general challenges described above, there are also challenges specific to particular biometric modalities and traits. While the following discussion does not describe all the challenges for each modality, it does offer some potentially fruitful avenues of investigation for the most common ones.
An ongoing challenge for facial recognition is segmentation—distinguishing facial features from surrounding information. Another signifi cant challenge for it is invariant representation—that is to say, finding a representation that is robust and persistent even when there are changes in pose, expression, illumination, and imaging distance, or when time has passed.
Specific challenges with respect to fingerprints include reducing the failure to enroll (FTE) and failure to acquire (FTA) rate, perhaps through the design of new sensors, artifact detection, image quality definition and enhancement, and high-resolution fingerprint matching. Fingerprint-based biometric systems could also be improved by increasing the speed of capture and minimizing contact, particularly for 10-print systems.
Iris recognition systems present R&D opportunities in the following areas: sensors; optimization of the illumination spectrum; reducing FTE and FTA rates; capturing and recognizing the iris at greater distances and with movement of the subject; and reducing the size of the hardware.
Improving speaker separation, normalizing channels, and using higher-level information (that is, beyond basic acoustic patterns) would all offer opportunities to improve voice recognition. In addition, robustness and persistence are needed in the face of language and behavioral changes and the limited number of speech samples.
Information Security Research
In many applications, biometric systems are one component of an overarching security policy and architecture. The information security community is extensive and has long experience with some of the challenges raised by biometric systems, which gives it a real opportunity for fruitful and constructive interaction with the biometrics community. Biometric systems pose two kinds of security challenges. The first is the use of biometrics to protect—provide security for—information systems. For what types of applications and in which domains is an approach incorporating biometric technologies most appropriate? This is a question for the broader information security community as well as the biometrics community and requires that we understand the goals and needs of an application to ascertain whether a biometrics-based approach is useful.
Assuming that a biometrics system is in place, the second security challenge is the security, integrity, and reliability of the system itself. 11 Information security research is needed that addresses the unique problems of biometric systems, such as preventing attacks based on the presentation of fake biometrics, the replay of previously captured biometric samples, and the concealment of biometric traits. Developing techniques for protecting biometric reference information databases to avoid their use as a source of fake biometrics is another area for such research. Decision analysis and threat modeling are other critical areas requiring research advances that will allow employing biometric systems more fully across a range of applications.
Testing and Evaluation Research
Testing and evaluation are an important component in the design, development, and deployment of biometric systems. Several areas related to the testing and evaluation of biometric systems are likely to prove fruitful. This section describes a few of them. While there has been significant work on testing and evaluating a variety of approaches, 12 it is the committee’s view that an even broader approach has merit. Moreover, while standardized evaluations of biometric systems are highly useful for development and comparison, their results may not reliably predict field performance. Methods used successfully for the study and improvement of systems in other fields (for example, controlled observation and experimentation on operational systems guided by scientific principles and statistical design and monitoring) should be used in developing, maintaining, assessing, and improving biometric systems. (See Chapter 3 for lessons that may be applicable from other domains.) The work over the last decade within the international standards community to reach agreement on fundamental concepts, such as how error rates are to be measured, has clarified the application of test methods under the usual laboratory conditions for biometric systems deployments. 13 Guidance for potential deployers of biometric systems on what is even a useful and appropriate initial set of questions to ask before getting into the details of modalities and so forth, as developed by a number of groups, has proven particularly useful. 14 And of course, in addition to the technical questions that need to be addressed, there are issues regarding how to measure cost over the life cycle of the system and how to assess potential and actual return on investment (ROI). Unfortunately, ROI analysis methodologies and case studies have been lacking in comparison to other types of assessments. See Box 5.1 for a brief discussion and example of an ROI assessment.
Return on Investment and Suitability Considerations. Determining the return on investment (ROI) for a biometric system is very much dependent on the application. It is based, among other things, on the risk the system is mitigating, the severity of the (more...)
Ultimately, determining the performance of an operational system requires an operational test, because adequately modeling all of the factors that impact human and technology performance in the laboratory is extremely difficult. Although the international standards community has made progress in developing a coherent set of best practices for technology and scenario testing, guidelines for operational testing are still under development and have been slowed by the community’s general lack of experience with these evaluations and a lack of published methods and results. 15 Designing a system and corresponding tests that can cope with ongoing data collection is a significant challenge, making it difficult for a potential user of biometric systems, such as a federal agency, to determine how well a vendor’s technology might operate in its applications and to assess progress in biometric system performance. Careful process and quality control analysis—as distinct from traditional, standardized testing of biometric systems that focuses on match performance for a test data set—at all stages of the system life cycle is essential. In addition, testing methods and results should be sufficiently open to allow disinterested parties to assess the results.
Test Data Considerations
One challenge meriting attention is test data for biometric systems. Designing large-scale systems requires large test data sets that are representative of the subject population, the collection environment, and system hardware expected in the target application. How does one determine which user population will be representative of the target application? The committee believes it is unlikely that being representative of the target application is the same as being representative of the population as a whole, because the population that should be considered will vary depending upon the ultimate application for which the system is used. Legal and privacy concerns have limited the collection and sharing of both test and operational data (for example, various data sets collected by the U.S. government) with researchers, 16 raising the question of whether biometric data can be made nonidentifiable back to its origin. 17 If it cannot, could synthetic biometric data be created and used in lieu of real biometric data? 18 If the latter is possible, does the use of synthetic (imagined) data offer any scientific validity in assessing performance of a system using real data? When test results are available, who has access to them? These and related questions merit attention from not just the T&E community but the broader biometrics communities as well.
Usability Testing
Many factors related to usability can affect system effectiveness and throughput and may also affect how well the system performs its recognition tasks. Testing and evaluation mechanisms are therefore needed that provide insight into how well a system under consideration handles a variety of user interface expectations.
Despite the recent focus of NIST’s information access division on usability testing, there is still major work to be done. One potential area of investigation is to incorporate into the design of the interface information on the expected motor control and cognitive capabilities of the user popu lations. Such information would allow the use of public health statistics to estimate the percentage of the general population (or subpopulation) that would be expected to have either cognitive or physical difficulties using the systems. By incorporating this understanding of the skills expected of users, designers and developers could tune the interfaces in ways that would increase their usability.
Usability is affected by other factors as well. For example, some unknown percentage of the population has a condition in which the fingers do not possess the usual friction ridges central to the functioning of fingerprint-based biometric system. In addition, some unknown (but believed to be nonzero) percentage of the population has either no irises or irises of unusual shape. When setting baseline error rates, it is important to have estimates of the percentage of the population lacking the required trait, because this lack interacts with the design of sensors and algorithms. It may well be that each modality will have lower error rate bounds that cannot be improved upon by better sensors, algorithms, or collection procedures. More research is needed to understand this. Such questions are related to the distinctiveness and stability of the underlying biometric traits, discussed above.
Other usability considerations relate to the ease of participation. Is the system designed to take into account user needs (such as tables on which to set their items if necessary) and physical differences (such as height and weight)? What kinds of user assistance should be provided? What accommodations could be made for people who are unfamiliar with the system, or, conversely, for people who are very familiar with it (much as toll pass transponder users can use dedicated lanes on highways)?
ROI Analysis Methodologies and Case Studies
Determining the potential ROI and identifying which system characteristics contribute is an important means of evaluating any biometrics deployment. In addition to how well a system meets its requirements, there are issues about measuring cost over the life cycle of the system and assessing potential (and actual) ROI. There are relatively few ROI analysis methodologies and case studies. The research opportunity here is to develop methods for examining likely costs and cost savings that take into account the technical life cycle as well as ongoing maintenance and usage costs.
Evaluative Frameworks for Potential Deployers
In addition to system and technology tests, there is a significant opportunity to develop an evaluative model that would guide potential procurers and users of biometric systems. Guidance for potential users of biometric systems on an appropriate initial set of questions to ask before getting into the details of modalities and so forth has proven particularly useful. 19
Testing When Data Changes
Designing a system and tests that can cope with ongoing data collection after it has been deployed is a significant challenge. The characteristics of the data may change from what was assumed during testing. This could be due to changes in the technology, changes in the user population, changes in how the system is used, or all of the above. Such potential changes to the data make it a challenge for potential users of biometrics, such as federal agencies, to readily determine how well a given vendor’s technology might operate for the agency’s applications over time. Developing testing and evaluation methodologies that can account for such potential changes or offer information on how a system’s performance might change in the event of significant changes to the data characteristics is an opportunity for further investigation.
Operational Testing
Finally, operational testing is problematic in that most existing systems do not retain the data needed to determine error and throughput rates. Each system collects and stores different data in application-specific ways. Additionally, ground truth (all of the relevant facts about all participants) cannot be known in real applications with arbitrary user populations. Privacy rights of the data subjects may prevent using collected data for testing purposes. Lastly, because system operators may not wish others to know about operational performance for reasons of security, very few operational test results have ever been published. The ISO/IEC JTC1 SC37 standards committee has been working for a number of years on basic guidance for operational testing, but progress on this standard, to be known as ISO/IEC 19795, Part 6, has been slow, reflecting the inherent difficulties in making general statements about operational tests.
Systems-Level Statistical Engineering Research
In addition to the modality-related technical challenges outlined above, there are broad systems-level considerations to take into account. In particular, statistics and statistical engineering offer opportunities for progress and the development of design principles and model designs for operational testing of biometric systems and experimentation with modifiable system parameters. This section outlines some potential research questions in statistical engineering and biometric systems that merit attention.
Statistical approaches come into play with respect to the user populations, including cross-sectional and longitudinal studies of the variability of various biometric modalities over time, the association of biometrics with demographic and medical factors, and the effects of demographic factors and physical characteristics on failure to acquire and error rates.
Another systems-level consideration is error rates in biometric systems, including the following topics:
- The relative contribution to error of different phases and components of biometric recognition (on an algorithm-by-algorithm basis, because error rates and their causes are algorithm specific);
- The potential for algorithm-specific quality control measures to reduce error rates in varying populations of data subjects;
- The application of known statistical methods for analysis of cor- related data to estimation 20 of false match and false nonmatch rates for recognition tasks; and
- The investigation of new statistical models for the estimation as above but from biometric databases where information on replication is incomplete—that is, replication is known only for a subset, or some information about variation in replicate measurements is available from an external source.
Other areas of potential investigation include studies of statistical efficiency and cost-benefits of different approaches to choosing, acquiring, and utilizing multimodal biometrics of various sorts. Issues to be considered would include the relative algorithmic-dependent within-class and between-class variation of sample choice such as multiple instances of 2 fingerprints versus single instances of 10 fingerprints versus single instances of 2 fingerprints combined with two-dimensional facial imaging. The aim is to develop the most informative fusion methods based on application- and algorithm-dependent multivariate distributions of biometric features.
Research on Scale
There are many ways in which scale may manifest itself in biometric systems. These include the number of sensors in the system, the number of comparisons being performed for a given unit time or a given input sample, the number of users (including administrators and operators), the geographic spread of the system, the size of the potential user population, or any combination of these factors. Addressing issues of scale in biometric systems offers numerous opportunities for research.
For instance, one question is this: How does the number of persons who have references in the enrolled database affect the speed of the system and its error rates? For some applications and associated algorithmic approaches, the size of the database might not matter if typical operation involves only a one-to-one comparison—that is, one set of submitted samples being compared to one set of enrollment records. For large-scale identification and screening systems, sequentially performing a very large number of one-to-one matches is not effective; there is a need for efficiently scaling the system to control throughput and false-match error rates as the size of the database increases.
Typical approaches to scaling include (1) using multiple hardware units, (2) coarse pattern classification (for example, first classifying a fingerprint into classes such as arch, tented arch, whorl, left loop, and right loop), and (3) extensive use of exogenous data (such as gender, age, and geographical location) supplied by human operators. Although these approaches perform well in practice, they come at a price. Using hardware linearly proportional to the database size is expensive. Coarse pattern classification offers substantial scaling advantages even when single measures are available and even more advantage with multiple measures—for example, fingerprints from multiple fingers—but can add to the nonmatch error rates. Use of exogenous information creates a mechanism for intentionally avoiding identification—for example, dressing as the opposite sex or appearing older—if someone is trying to avoid being recognized by the system, not to mention potential privacy compromises.
Ideally, one would like to index biometric data patterns in some way similar to that used in conventional databases in order to benefit from lessons learned in other arenas. However, due to large intraclass variation in biometric data caused by variation in collection conditions and human anatomies and behaviors, it is not obvious how to ensure that samples from the same pattern fall into the same index bin. There have been very few published studies on reliably indexing biometric patterns. 21 Efficient indexing algorithms would need to be developed for each technology/modality combination. It is unlikely that any generic approach would be applicable to all biometric measures, although efforts to understand similarities and where lessons from one type of system can be applied to another are warranted.
False-match errors generally increase with the number of required comparisons in a large-scale identification or watch-list system. As most comparisons are false (for example, a submitted sample compared to the enrollment pattern of another person), increasing the size of the database increases the number of opportunities for a false match. However, in large-scale systems it is unlikely that a sample would be compared against every possible match in the database. Instead, just as with search algorithms generally, the set of items to compare against is winnowed according to certain criteria as quickly as possible to save time and memory. Because of the nonindependence of sequential comparisons using the same sample data, coupled with architectural and algorithm design choices that are aimed at finding any matches while sustaining throughput rate and limiting active memory, the relationship between the number of false matches and database size is a poorly understood issue meriting further investigation. 22
Although a watch-list database in a screening system is much smaller than that in a large-scale identification application, the number of continuous or active comparisons may be huge. Therefore, as in large-scale applications, the throughput and error-rate issues are also critical in screening applications. Computationally, scaling of large systems for near-real-time applications involving 1 million identities is becoming feasible, as is screening the traffic for 500 recognized identities. However, designing and building a real-time identification system involving 100 million identities is beyond our understanding. More research is needed here as well.
Social Science Research Opportunities
Biometric systems require an intimate association between people and the technologies that collect and record their biological and behavioral characteristics. This is true whether the application is overt or covert, negative claim or positive claim. It is therefore incumbent on those who conceive, design, and deploy biometric systems to consider the cultural and social contexts of these systems. Unfortunately, there are few rigorous studies of these contexts. Below is a framework for developing a portfolio of future research investigations that could help biometric systems better cope and perform within their cultural and social contexts.
Cultural and social issues arise at essentially two different levels—for the individual and for society. At the level of the individual, whether they are interacting actively or passively with a biometric system (for example, the person seeking entry to a facility), the issue is the performance of a biometric system. At the societal level, the issue is the social impact of the biometric system (for example, all are affected, either directly or indirectly, by the trade, tourism, and terrorism effects of a biometric passport).
At the level of the individual, social considerations are critical in the design, deployment and functioning of biometric systems. As we have noted, system performance may well be degraded if relevant social factors are not adequately taken into consideration. For example, religious beliefs that call for adherents to cover their faces in public make facial-recognition biometrics problematic. Thus if a biometric system is to work well for a broad range of people it must take into account behaviors resulting from such things as religion or social convention. Every biometric system has a protocol for how it is to be interacted with. The protocol may be simple or complex, uniform in application, or tailored to the individual. Obviously, however, a good protocol for a biometrics system must recognize variations in biological features. A system based on fingerprints must have ways to gracefully accommodate a person who is missing a finger or who otherwise does not have usable fingerprints.
In addition to the design issue of affordance, previously discussed, research is needed to determine effective, appropriate, and graceful protocols, processes, and devices that gain the cooperation of participants, and the protocols and devices must be acceptable to the community. In biometric systems that are essentially surveillance systems, compliance should be thought of as more than acquiescence and should extend to gracefully (perhaps without notice) promoting the types of behavior (for example, face pose and angle) that result in useful biometric measures. Full compliance represents the ideal interaction of the participant with the biometric system from the viewpoint of the system designers. Acceptability to the community refers to the endorsement, or at least the lack of active disapproval, by significant governmental and public leadership groups. In any case, community acceptability is not guaranteed. Influential parts of the community may find biometric systems overly intrusive, unfair to certain groups, or inadequately protective of the individual’s privacy.
The dimensions of individual compliance and community acceptability are discussed next. One part of the design process for particular systems or, more realistically, for a particular class of systems might be to develop data that predict how well the biometric system will perform in a target community and on factors that may make the system more acceptable to that community. Predictive aspects may just have a statistical relationship with subject compliance or community acceptability, while acceptability factors probably have a causal relationship. Developing data in these areas will provide the evidence needed to assess the relationships.
The extent and nature of participant compliance can be discovered and confirmed using either or both of two basic research strategies: field studies using ethnographic tools such as in cultural anthropology or attitude studies of using survey methods such as are common in sociology. Some of the things that might predict participant compliance include participant attitudes toward authority, their willingness to try new technology, their adherence to certain religious or cultural beliefs, and the geographic distribution of the population. Such work could, in theory, be part of the design work for biometrics systems but is generally not done, possibly because of the expense and effort involved. Research that sheds light on these issues would provide valuable information for those designing and building biometric systems.
Factors that motivate participant compliance can be discovered by experimental studies, essentially creating laboratory environments in which the factors can be controlled. This research paradigm is common in experimental psychology, but the extent to which such controlled studies might develop data that reflect factors encountered in operational applications is only speculative. Some candidate factors include self-interest, enforcement, inducement, social pressure, conviction, habit or practice, behavior of other actors, pleasantness of the experience, and attention to cultural norms. The more common approach is to survey data subjects who have just encountered an operational system to elicit their opinions, 23 but even this approach has rarely been applied.
Aspects that predict the extent and nature of community acceptability can be discovered and confirmed using either or both of two basic research strategies: field studies of similar deployments using ethnographic tools—as indicated for participant compliance above, or focus groups that are asked to discuss how they view various characteristics of a biometric system such as are common in marketing studies. The kinds of aspects that might be predictive of community acceptability include resemblance to existing well-tolerated systems, operated under the auspices of a respected institution, or a system that meets all legal requirements
One factor in motivating community acceptability is whether community concerns—for example, fairness, privacy, and confidentiality—are addressed. Using data from research in these and related areas, it should be possible to address a variety of relevant questions, such as: Where on the scale of purely voluntary to mandatory is a particular biometric system? In largely voluntary systems does cooperation vary by subgroup such as age, sex, or race? Does habituation lead to greater cooperation? How important is it that participants believe they or others will not be harmed? What factors influence such trust? What are effective and appropriate compliance mechanisms for biometric systems? Although it is not reasonable to expect designers of a specific system to conduct such research, these questions could be addressed as part of a more general research agenda.
- PUBLIC POLICY CONSIDERATIONS AND RESEARCH OPPORTUNITIES
Numerous issues come into play beyond technical and engineering considerations in government use of biometric systems. These other issues include the following:
- To what extent can the need for a biometric system be satisfied by current technical capability? Balancing mandates with maturity of systems and technology is critical. Aggressive schedules can push technology development forward but not all challenges can be addressed on short notice.
- Is there sufficient flexibility and time to support the risk management needed to develop and deploy a biometric system? Governments must avoid increasing risk through overly constrained integration and testing timelines and budgets. The risks include the possibility not only that the system will fail or be compromised but also the possibility that the system will be rejected by its users or be so cumbersome or inefficient that it is withdrawn from use.
- Should participation in the system be mandated? Such a mandate might foster a climate of distrust or social unrest.
- What is the nature of the biometrics workforce? To the extent that biometric systems and related technologies are seen as important to meet public policy goals, is there sufficient incentive to grow and maintain the needed expertise? Training and maintaining consistent biometrics workforce has been difficult. Several organizations recently announced plans to create certification programs for professionals, but consensus must be reached on what skills are required of a professional in this area. The creation of a biometrics undergraduate program at West Virginia University is a step in the right direction. (The program has a ready customer: the FBI’s Criminal Justice Information Center in Clarksburg, West Virginia.)
- The sourcing of the technology is crucial to the government’s successful deployment of technological and information systems, including biometric systems. There is an inherent danger in relying on companies with manufacturing, research, or development activities centered overseas. For biometric systems, especially, the risk is the potential for U.S. biometric data to be collected by foreign governments, inviting scrutiny of U.S. information on border control systems and other critical infrastructure by persons not cleared by the U.S. government.
The social science considerations described above may have impacts on broader public policy considerations. Systematic empirical research and factual analysis would help provide an evidence case for public policy in this area. Some key research questions that have an impact on public policy include the following:
- What lessons can be learned from environmental impact statements and privacy impact assessments that might be relevant to deciding whether social impact assessments for biometric systems are useful?
- Do existing or proposed biometric systems represent a serious potential for identity theft?
- How have authoritarian regimes made use of human recognition methods to assert their control over individuals? In what ways might biometric systems enable these sorts of uses? How could such a risk be mitigated?
- To what extent are privacy requirements, interagency control issues, and policy constraints, or the perception thereof, inhibiting the research use and sharing of existing biometric data?
- What belief sets, if any, lead to an aversion to certain biometric technologies?
A reliable and effective biometric system may be perceived as providing irrefutable proof of identity of an individual, notwithstanding the many uncertainties already mentioned, raising concerns for users. Will the information regarding biometrics-based access to resources be used to track individuals in a way that infringes on privacy or anonymity? Will biometric data be used for an unintended purpose: For example, will fingerprints provided for access control be matched against fingerprints in a criminal database? Will data be used to cross-link independent records from the same person—for example, health insurance and grocery purchases? How would a user be reassured that a biometric system is being used for the intended purpose only?
Designing information systems—not only biometric systems—whose functionality is verifiable during deployment is very difficult. One solution might be a system that meticulously records recognition decisions and the people who accessed the logged decisions using a biometric-based access control system. Such a system could automatically warn users if a suspicious pattern is seen in the system administrator’s access of users’ logs. Another solution might be biometric cryptosystems—cryptographic keys based on biometric samples. Radical approaches such as total transparency attempt to solve the privacy issues in a novel way. But there are no obviously satisfactory solutions on the horizon for the privacy problem. Additional research on the relationship between biometric (bodily) information and privacy is needed.
The privacy protections required to facilitate data collection from and about biometric systems need to be clearly established. Because many of these systems are deployed to satisfy security needs, it is reasonable to expect that performance and vulnerability data need to be protected. For best results, the data sets for such research should be very large, contain very few errors in ground truth (metadata indexing), be appropriately randomized, and represent the populations of interest to target applications. To the extent consistent with privacy and security, the results of the studies should be published in the peer-reviewed scientific literature and the biometric samples used made widely available to other researchers.
- REALIZING A WELL-DESIGNED BIOMETRIC SYSTEM
Research in the areas described above is warranted more than ever as biometric systems become widespread and are used in critical applications. This report concludes by taking a step back and presenting a vision of a well-designed biometric system that should persist even as progress is made on the challenges described earlier in this chapter.
A well-designed biometric system includes more than technology. It is a complex combination of technology, public policy, law, human processes, and social consensus. In the long term, there may be new modalities that allow recognizing human characteristics and behaviors quickly and effectively with little or no interaction on the individual’s part. Human beings may turn out to possess distinctive traits that have yet to be fully explored or that cannot be suitably represented by present technology. Some of the potential sources of suitable signals currently being pursued include inductive signature and brain waves (EKG activity). Each of these potential signal sources could bring with it a new set of societal and policy issues requiring exploration.
Even with all of these uncertainties, and even with the many intriguing open questions that merit research, the committee believes that the following framework for a well-designed biometric system will apply for the foreseeable future. Progress in such research will lead to even more well-designed systems. This framework is offered as both an evaluative tool and as a development tool.
A well-designed biometric recognition system will have (at least) the following characteristics:
- The system will be designed to take into account that no biometric characteristic is entirely stable and distinctive. In other words, it will take into account that biometric similarity represents a likely, not a definitive, recognition and and that the corresponding is true for a failure to find similarity. In particular, presumptions and burdens of proof will be designed conservatively, with due attention to the system’s inevitable imperfections.
- The policies of such a system will recognize that any claimed probabilities of correctness depend on external assumptions about dynamic presentation distributions, and that these assumptions, whether subjective or based on estimates from past internal or external data, are fallible. It will enable system operators and users to recognize that biometric information has a life cycle. Biometric information is collected or modified during, for example, enrollment, recognition, and so on. But policies should also recognize that changes in the biometric characteristics of the individual can lead to incorrect or failed recognition.
- The system will be designed so that system operators and users recognize that some inaccurate information may be created and stored in the databases linked to biometric references, and that over time information in these databases will become out of date. In particular, the reliability of information in the database is independent of the likelihood of correct recognition. The system will be designed to handle challenges to the accuracy of database information in a fair and effective way.
- Because the system’s sensors and back-end processes are not perfectly accurate, it will need to handle failures to enroll, failures to acquire samples, and other error conditions gracefully and without violating dignity, privacy, or due process rights.
- Because some individuals will attempt to force the system into failure modes in order to avoid recognition, the system’s failure modes must be just as robustly designed as the primary biometrics-based process.
- The system’s security, privacy, and legal goals must be explicit and publicly stated, and they must be designed to protect against a specific and enumerated set of risks. The system will specifically address the possibility that malicious individuals may be involved in the design and/or operation of the system itself.
- It will recognize that biometric traits are inherently not secret and will implement processes to minimize both privacy risks and risks of misrecognition arising from this fact.
- CONCLUDING REMARKS
This report lays out a broad systems view and outlines many of the subject areas with which biometrics research intersects. The committee also describes many open research problems, ranging from deep scientific questions about the nature of individuality to vexing technical and engineering challenges. It raises questions about appropriate system architecture and life-cycle design as well as questions about public policy regarding both private sector and government use of biometric systems. It notes that biometrics is an area that benefits from analyzing very large amounts of data. These and other aspects of biometrics suggest many fruitful areas and interesting problems for researchers from a range of disciplines.
A.K. Jain, R. Bolle, and S. Pankanti, eds., Biometrics: Personal Identification in Networked Society, Norwell, Mass.: Kluwer Academic Publishers (1998), as cited in A.K. Jain, S. Pankanti, S. Prabhakar, L. Hong, A. Ross, and J. Wayman, Biometrics: A Grand Challenge, Proceedings of the 18th International Conference on Pattern Recognition, Cambridge, England (2004). Available at http://biometrics .cse .msu.edu/Publications /GeneralBiometrics /Jainetal_BiometricsGrandChallenge _ICPR04.pdf .
The National Science Foundation Center for Identification Technology Research is one program taking an interdisciplinary approach to research related to biometrics. More information about the center is available at http://www .nsf.gov/eng /iip/iucrc/directory/citr.jsp .
Standardization efforts, discussed elsewhere in this report, can help facilitate the cycle of build-test-share for transitioning the technology from concept to business solution.
See, for example, A.K. Jain, S. Pankanti, S. Prabhakar, L. Hong, A. Ross, and J. Wayman, Biometrics: A Grand Challenge, Proceedings of the 18th International Conference on Pattern Recognition, Cambridge, England (2004); National Science and Technology Council, Subcommittee on Biometrics, “The National Biometrics Challenge” (2006), available at http://www .biometrics .gov/Documents/biochallengedoc.pdf ; E. Rood and A.K. Jain, Biometrics Research Agenda, report of an NSF Workshop (2003); and Mario Savastano, Philip Statham, Christiane Schmidt, Ben Schouten, and Martin Walsh, Appendix 1: Research challenges, BioVision: Roadmap for Biometrics in Europe to 2010, Astrid Albrecht, Michael Behrens, Tony Mansfield, Will McMeechan, and Marek Rejman-Greene, eds. (2003), available at http://ftp .cwi.nl/CWIreports /PNA/PNA-E0303.pdf .
M. Theofanos, B. Stanton, and C. Wolfson, Usability and biometrics: Assuring successful biometric systems, NIST Information Access Division (2008); M. Theofanos, B. Stanton, C. Sheppard, R. Micheals, J. Libert, and S. Orandi, Assessing face acquisition, NISTIR 7540, Information Access Division Information Technology Laboratory (2008); and M. Theofanos, B. Stanton, C. Sheppard, R. Micheals, Nien-Fan Zhang, J. Wydler, L. Nadel, and W. Rubin, Usability testing of height and angles of ten-print fingerprint capture, NISTIR 7504 (2008).
J.J. Gibson, The theory of affordances, in Perceiving, Acting, and Knowing , Robert Shaw and John Bransford, eds. Hillsdale, N.J.: Erlbaum Associates (1977).
This idea can be extended even to systems where the subject is unaware of the interaction but behaviors are being suggested to facilitate data collection.
“Information technology—biometric performance testing and reporting,” ISO/IEC 19795.
P.J. Bickel, Discussion of “The evaluation of forensic DNA evidence,” Proceedings of the National Academy of Sciences 94(11): 5497 (1997). Available at http://www .pnas.org/content/94/11/5497 .full?ck=nck .
Ted Dunstone and Neil Yager, Biometric System and Data Analysis: Design, Evaluation, and Data Mining , New York: Springer Science+Business Media (2008).
See NRC, Toward a Safer and More Secure Cyberspace , Washington, D.C.: The National Academies Press (2007) for an in-depth discussion of security.
NIST’s emerging National Voluntary Laboratory Accreditation Program (NVLAP) for biometrics represents progress in formalizing testing programs but does not yet provide specific testing methods required for different products and applications and does not yet address operational testing. The NVLAP Handbook 150-25 on Biometrics Testing is available at http://ts .nist.gov/Standards /Accreditation /upload/NIST-Handbook-150-25 _public_draft_v1_09-18-2008 .pdf .
Note that while these standards are aimed at a broad swath of systems, they are not seen as appropriate for governments to use for large-scale AFIS systems, where they would need to be tested for conformance to standards, compliance with system requirements, alignment with capacity and accuracy requirements, and satisfaction of availability and other traditional system parameters.
For example, the recommendations of the U.K. Biometrics Working Group in “Use of Biometrics for Identification and Authentication: Advice on Product Selection, Issue 2.0” (2002). Available at http://www .cesg.gov.uk /policy_technologies /biometrics/media/biometricsadvice.pdf .
ISO/IEC 19795-6, Biometric Performance Testing and Reporting—Part 6: Testing Methodologies for Operational Evaluation, is under development by ISO JTC1 SC37.
Government operational biometric data—that is, personally identifiable information (PII)) for research and testing are governed by the privacy impact assessments (PIAs) and system-of-record notices (SORNs) associated with the specific systems, which are required by the Privacy Act of 1974. Whether the Privacy Act provides the latitude to use operational biometric and biometric-related data for large-scale research and testing purposes (during acquisition and operation) so long as data privacy and integrity are adequately protected is subject to interpretation. Various scenarios for how such data might be shared include these: (1) using the data (such as from IAFIS or US-VISIT) internal to the agency collecting the data, (2) using such data outside the agency collecting the data (such as providing multiagency data to NIST for analysis), or (3) providing such data to a university and/or industry team for analysis, etc. Assuming the Privacy Act permits such uses, then the PIAs and SORNs would have to specify such use of the data. The NIST multimodal biometric application resource kit (MBARK) data set is an example of test data collected but not disseminated for privacy reasons. The Department of Homeland Security (DHS) has released its former IDENT database to NIST for testing (NIST reports refer to it as DHS-2), but it has not been released to general researchers.
Fingerprint images that are sufficiently similar to the original fingerprint can be reconstructed from data representations of the fingerprints. See J. Feng and A.K. Jain, FM model based fingerprint reconstruction from minutiae template, International Conference on Biometrics (2009), pp. 544-553. Available at http://biometrics .cse .msu.edu/Publications /Fingerprint/FengJain_FMModel_ICB09 .pdf .
SFINGE, a fingerprint synthesis technique, is described in Chapter 6 of D. Maltoni, D. Maio, A.K. Jain, and S. Prabhakar, Handbook of Fingerprint Recognition , 2nd edition, Springer Verlag (2009).
The NRC report Protecting Individual Privacy in the Struggle Against Terrorists: A Framework for Assessment (The National Academies Press, Washington, D.C., 2008) provides a framework for assessing program efficacy as well as impacts on privacy. The U.K. Biometrics Working Group developed another such document, which is available at http://www .cesg.gov.uk /policy_technologies /biometrics/media/biometricsadvice.pdf .
The committee notes the reluctance to use interval estimation because of lack of agreement on how to handle systematic errors except through personal probability. See ISO/IEC, Guide 98-3 (1995) Guide to the Expression of Uncertainty in Measurement .
J.L. Wayman, Multi-finger penetration rate and ROC variability for automatic fingerprint identification systems, in N. Ratha and R. Bolle, eds., Automatic Fingerprint Recognition Sys tems , New York: Springer Verlag (2003).
See, for example, J.L. Wayman, Error rate equations for the general biometric system, IEEE Robotics and Automation 6(1): 35-48, and H. Jarosz, J.-C. Fondeur, and X. Dupré, Large-scale identification system design, J.L. Wayman, A.K. Jain, D. Maltoni, and D. Maio, eds., Biometric Systems: Technology, Design, and Performance Evaluation , New York: Springer (2005).
As was done, for example, by the Orkand Corporation in Personal Identifier Project: Final Report , California Department of Motor Vehicles report DMV88-89 (1990).
- Cite this Page National Research Council (US) Whither Biometrics Committee; Pato JN, Millett LI, editors. Biometric Recognition: Challenges and Opportunities. Washington (DC): National Academies Press (US); 2010. 5, Research Opportunities and the Future of Biometrics.
- PDF version of this title (1.3M)
In this Page
Recent activity.
- Research Opportunities and the Future of Biometrics - Biometric Recognition Research Opportunities and the Future of Biometrics - Biometric Recognition
Your browsing activity is empty.
Activity recording is turned off.
Turn recording back on
Connect with NLM
National Library of Medicine 8600 Rockville Pike Bethesda, MD 20894
Web Policies FOIA HHS Vulnerability Disclosure
Help Accessibility Careers
A Survey on Biometric Authentication: Toward Secure and Privacy-Preserving Identification
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Help | Advanced Search
Computer Science > Cryptography and Security
Title: advancements in biometric technology with artificial intelligence.
Abstract: Authentication plays a significant part in dealing with security in public and private sectors such as healthcare systems, banking system, transportation system and law and security. Biometric technology has grown quickly recently, especially in the areas of artificial intelligence and identity. Formerly, authentication process has depended on security measures like passcodes, identity fobs, and fingerprints. On the other hand, as just a consequence of these precautions, theft has increased in frequency. In response, biometric security was created, in which the identification of a person is based on features derived from the physiological and behavioral traits of a human body using biometric system. Biometric technology gadgets are available to the public as they are embedded on computer systems, electronic devices, mobile phones, and other consumer electronics. As the fraudulent is increasing demand and use of biometric electronic devices has increased. As a consequence, it may be possible to confirm a person's distinct identification. The goal of this study is to examine developments in biometric systems in the disciplines of medicine and engineering. The study will present the perspectives and different points of view of the secondary data, highlighting the need for more in-depth understanding and application of biometric technology to promote its development in the digital era. The study's findings may inspire people and businesses to more effectively incorporate biometric technologies in order to reduce the risks to data and identity security.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
biometric security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Two-Level Biometric Security System For Voting
Optimized content adaptive approach for image detailed enhancement to reduce color distortion.
Digital imaging has significantly influenced the outcome of research in various disciplines. For example, artificial intelligence and robotics, biometric security, multimedia and image processing, etc. Technically, image processing and the Human Visual System (HVS) relies heavily on image enhancement to improve the content of the image. One of the biggest challenges in image processing is detail enhancement due to halo artefacts and gradient inversion artefacts at edges. It has been used to enhance the visual quality of an image. Most algorithms that used to enhance the detail of an image essentially depend on edge-preserving decomposition techniques. in general, the image consist of two major elements are a base layer and a detail layer, which extracted by edge-preserving decomposition algorithms. The detail layer is enhanced to improve the details of the generated image. we propose in this paper, a new model to preserve the sharp edges and achieve better visual quality than the existing norm-based algorithm to enhance the details of the image. Experiments show that the proposed method reduces the distortion at the edges. It improves the details of the generated image significantly.
Cancelable biometric security system based on advanced chaotic maps
Biometric security: a review to future.
This paper presents the different biometric with their limitations and introduces their alternative in form of brain biometric, Breath biometrics, and Tongue biometrics. Brain biometric uses brain wave while breath biometric uses one’s breath and tongue biometric uses a tongue’s shape and variation to distinguish them and present a good alternative for the presently used biometric like fingerprint, iris recognition, face recognition.
Biometric security management based on Internet of Things
Model of the "biometry-code" converter based on artificial neural networks for analysis of facial thermograms.
Existing asymmetric encryption algorithms involve the storage of a secret private key, authorized access to which, as a rule, is carried out upon presentation of a password. Passwords are vulnerable to social engineering and human factors. Combining biometric security techniques with cryptography is seen as a possible solution to this problem, but any biometric cryptosystem should be able to overcome the small differences that exist between two different implementations of the same biometric parameter. This is especially true for dynamic biometrics, when differences can be caused by a change in the psychophysiological state of the subject. The solution to the problems is the use of a system based on the "biometrics-code" converter, which is configured to issue a user key after presentation of his/her biometric image. In this case, the key is generated in advance in accordance with accepted standards without the use of biometric images. The work presents results on using thermal images of a user for reliable biometric authentication based on a neural network "biometrics-code" converter. Thermal images have recently been used as a new approach in biometric identification systems and are a special type of biometric images that allow us to solve the problem of both the authentication of the subject and the identification of his psychophysiological state. The advantages of thermal imaging are that this technology is now becoming available and mobile, allowing the user to be identified and authenticated in a non-contact and continuous manner. In this paper, an experiment was conducted to verify the images of thermograms of 84 subjects and the following indicators of erroneous decisions were obtained: EER = 0.85 % for users in the "normal"state.

Behavioral Biometric Data Analysis for Gender Classification Using Feature Fusion and Machine Learning
Biometric security applications have been employed for providing a higher security in several access control systems during the past few years. The handwritten signature is the most widely accepted behavioral biometric trait for authenticating the documents like letters, contracts, wills, MOU’s, etc. for validation in day to day life. In this paper, a novel algorithm to detect gender of individuals based on the image of their handwritten signatures is proposed. The proposed work is based on the fusion of textural and statistical features extracted from the signature images. The LBP and HOG features represent the texture. The writer’s gender classification is carried out using machine learning techniques. The proposed technique is evaluated on own dataset of 4,790 signatures and realized an encouraging accuracy of 96.17, 98.72 and 100% for k-NN, decision tree and Support Vector Machine classifiers, respectively. The proposed method is expected to be useful in design of efficient computer vision tools for authentication and forensic investigation of documents with handwritten signatures.
Enhanced Palmprint Identification Using Score Level Fusion
Palm print identification has been used in various applications in several years. Various methods have been proposed for providing biometric security through palm print authentication. One such a method was feature level fusion which used multiple feature extraction and gives higher accuracy. But it needed to design a new matcher and acquired many training samples. However, it cannot adapt to scenarios like multimodal biometric, regional fusion, contactless and complete direction representation. This problem will be overcome by score level fusion method. In this article, we propose a salient and discriminative descriptor learning method (SDDLM) and gray-level co-occurrence matrix (GLCM).The score values of SDDLM and GLCM are integrated using score level fusion to provide enhanced score. Experiments were conducted on IITD palm print V1 database. The combination of SDDLM AND GLCM methods will be useful in achieving higher performance. It provides good recognition rate and reduces computation burden.
AI and Deep Learning in Biometric Security
Challenges and opportunities in biometric security: a survey, export citation format, share document.
Biometric ticketing to start opening day for Phillies at all stadium entrances

The Philadelphia Phillies are promoting facial recognition ticketing to all of the main entrance gates at Citizens Bank Park following a successful debut as a pilot project last year.
Major League Baseball is introducing its Go-Ahead Entry program, a top prospect in biometric ticketing and access control, to all stadiums league-wide during the 2024 season.
Fans submit a selfie through the MLB Ballpark app and enter at gates where Go-Ahead Entry is implemented without showing a ticket or their phone. The service was first deployed to the first base gate at Citizens’ last year, and expanded to the third base gate during the season.
Phillies CTO Sean Walker told Sports Business Journal that the number of registrations and anecdotal fan response makes it clear that the program will be a success. With the service operating at all gates, the team will be able to gather data on the rate of registrations to uses by fans and the speed of the biometric lines.
An MLB spokesperson told the publication that Go-Ahead Entry got fans into the stadium 68 percent faster than the usual entry methods with physical or smartphone-based tickets.
In addition to the Phillies, the Houston Astros , the San Francisco Giants and one other team will have the biometric ticketing system in place by opening day. The Giants have deployed Go-Ahead Entry at the Lefty O’Doul and 2nd and King gates.
Related Posts

Article Topics
biometric ticketing | contactless biometrics | face biometrics | MLB Go-Ahead Entry | selfie biometrics
Latest Biometrics News
- Westminster Forum talks digital ID regulation, rollout and security
Digital Identity is the focal point of the latest Westminster Forum policy conference, for which key stakeholders and policymakers in…
Idemia digital ID unit could be sold off first for €1.1B: report
The Smart Identity wing of Idemia could be the first domino to fall in a piece-by-piece sell-off by owner Advent,…
US airlines face review of personal information and data collection practices
The U.S Department of Transportation (DOT) is undertaking a privacy review of the country’s ten largest airlines to ensure proper…
Signicat adds digital signature expertise with SmartWorks acquisition
In a strategic move to strengthen its digital identity solutions, Signicat has acquired Iceland-based digital signatures provider SmartWorks. By combining…
Public sector digital ID contracts for Net Group, KOMSCO, Fujitsu
Contracts have been awarded to Net Group in Estonia, and Korea’s state printer in Costa Rica to support the rollout…
UK outlines digital development strategy for developing nations
Digital public infrastructure (DPI), including the international digital identity for development project, will be one of the central priorities of…
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Continue Reading

Most Read From This Week
- Face biometrics for identity proofing draws big investment and cautionary notes
- Smart Engines claims new facial recognition system uses no biometric information
- GSA names 8 identity proofing companies for $194.5M in Login.gov contracts
- Mastercards from Thales and FPC, Idex Biometrics launch in Turkey
- Worldcoin makes core components of iris biometric imaging software open source
- EU cybersecurity agency outlines good practices for remote identity proofing
- UK data watchdog to investigate country’s troubled immigration IT systems
- Financial fraud is exploding, fueled by cheap and easy generative AI tools
- New crop of latent fingerprint algorithms set new highs in NIST testing
- AI for secure digital identity revolutionizing banking in Pakistan
- Daily Biometrics News
Featured Company
- More Biometrics Companies
Biometrics Insight, Opinion
- MOSIP President makes a diagnosis of Connect 2024, outlines future focus
- Biometrics: the future of payment security
- Takeaways from recent Meta BIPA decision: What companies need to know
- Biometrics is not enough: Salesforce exec on enterprise MFA and digital identity
- Biometrics Industry Interviews
Digital ID In-Depth
- CSIS encourages private sector DPI investment as UN pushes for safeguards
- NADRA’s digital solutions empowering Pakistan’s e-government initiatives
- Digital ID part of social contract between govt, citizens: World Bank, Verizon chiefs
- Digital ID Biometrics
Biometrics White Papers
- Protect your business and customers from threat of account fraud
- A buyer’s guide to online identity verification
- Generative AI: How to protect your business in the golden age of fraud and disinformation
- Metrics that matter – How to evaluate identity verification technology
- Digital travel: definition and benefits
- More White Papers

Biometrics Events
- SecureFaces: A privacy-centric approach to biometric authentication Online: Apr 4, 2024
- Global Age Assurance Standards Summit Manchester, UK and online: Apr 8 - Apr 12, 2024
- 10th Annual Identity Management Symposium National Harbor, MD: Apr 10 - Apr 11, 2024
- LiveScan solutions: Improving speed and quality in biometric capture for law enforcement Online: Apr 16, 2024
- ID@Borders and Future of Travel Conference 2024 Helsinki, Finland: Apr 18 - Apr 19, 2024
- More Biometrics Events
A Systematic Review on Physiological-Based Biometric Recognition Systems: Current and Future Trends
- Review article
- Published: 23 February 2021
- Volume 28 , pages 4917–4960, ( 2021 )
Cite this article
- Kashif Shaheed ORCID: orcid.org/0000-0002-7399-6211 1 ,
- Aihua Mao 1 ,
- Imran Qureshi 2 ,
- Munish Kumar 3 ,
- Qaisar Abbas 4 ,
- Inam Ullah 5 &
- Xingming Zhang 1
1759 Accesses
22 Citations
1 Altmetric
Explore all metrics
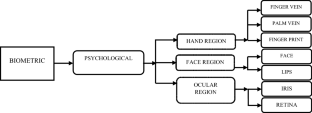
Biometric deals with the verification and identification of a person based on behavioural and physiological traits. This article presents recent advances in physiological-based biometric multimodalities, where we focused on finger vein, palm vein, fingerprint, face, lips, iris, and retina-based processing methods. The authors also evaluated the architecture, operational mode, and performance metrics of biometric technology. In this article, the authors summarize and study various traditional and deep learning-based physiological-based biometric modalities. An extensive review of biometric steps of multiple modalities by using different levels such as preprocessing, feature extraction, and classification, are presented in detail. Challenges and future trends of existing conventional and deep learning approaches are explained in detail to help the researcher. Moreover, traditional and deep learning methods of various physiological-based biometric systems are roughly analyzed to evaluate them. The comparison result and discussion section of this article indicate that there is still a need to develop a robust physiological-based method to advance and improve the performance of the biometric system.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price excludes VAT (USA) Tax calculation will be finalised during checkout.
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Abbas EI, Mieee MES (2017) Face recognition rate using different classifier methods based on PCA, pp 37–40
Abrishami-Moghaddam H, Farzin H, Moin MS (2008) A novel retinal identification system. Eurasip J Adv Signal Process. https://doi.org/10.1155/2008/280635
Article MATH Google Scholar
Adjimi A, Hacine-Gharbi A, Ravier P, Mostefai M (2017) Extraction and selection of binarised statistical image features for fingerprint recognition. Int J Biometrics 9(1):67–80. https://doi.org/10.1504/IJBM.2017.084133
Article Google Scholar
Aglio-caballero A, Ríos-Sánchez B, Sánchez-Ávila C, Giles MJMD (2017) Analysis of local binary patterns and uniform local binary patterns for palm vein biometric recognition. In: 2017 international carnahan conference on security technology (ICCST). IEEE, pp 1–6
Ahmadi N, Akbarizadeh G (2018) Hybrid robust iris recognition approach using iris image pre-processing, two-dimensional gabor features and multi-layer perceptron neural network/PSO. IET Biometrics 7(2):153–162. https://doi.org/10.1049/iet-bmt.2017.0041
Ahmadi N, Akbarizadeh G (2018) Iris tissue recognition based on GLDM feature extraction and hybrid MLPNN-ICA classifier. Neural Comput Appl. https://doi.org/10.1007/s00521-018-3754-0
Ahmadi N, Nilashi M, Samad S, Rashid TA, Ahmadi H (2019) An intelligent method for iris recognition using supervised machine learning techniques. Opt Laser Technol 120(2018):105701. https://doi.org/10.1016/j.optlastec.2019.105701
Ahmed T, Sarma M (2018) An advanced fingerprint matching using minutiae-based indirect local features. Multimed Tools Appl 77(15):19931–19950. https://doi.org/10.1007/s11042-017-5444-9
Aleem S, Sheng B, Li P, Yang P, Feng DD (2019) Fast and accurate retinal identification system: using retinal blood vasculature landmarks. IEEE Trans Ind Inf 15(7):4099–4110. https://doi.org/10.1109/TII.2018.2881343
Ali YH, Razuqi ZN (2017) Palm vein recognition based on centerline. Iraqi J Sci 58(2):726–734
Google Scholar
Ananth C (2017) Iris recognition using active contours. SSRN Electron J 2(1):27–32. https://doi.org/10.2139/ssrn.3028575
Arsalan M, Hong HG, Naqvi RA, Lee MB, Kim MC, Kim DS et al (2017) Deep learning-based iris segmentation for iris recognition in visible light environment. Symmetry. https://doi.org/10.3390/sym9110263
Barpanda SS, Sa PK, Marques O, Majhi B, Bakshi S (2018) Iris recognition with tunable filter bank based feature. Multimed Tools Appl 77(6):7637–7674. https://doi.org/10.1007/s11042-017-4668-z
Benalcazar DP, Perez CA, Bastias D, Bowyer KW (2019) Iris recognition: comparing visible-light lateral and frontal illumination to NIR frontal illumination. In: Proceedings—2019 IEEE winter conference on applications of computer vision, WACV 2019, pp 867–876. https://doi.org/10.1109/WACV.2019.00097
Bharadwaj S, Vatsa M, Singh R (2014) Biometric quality: a review of fingerprint, iris, and face. Eurasip J Image Video Process 2014(1):1–28. https://doi.org/10.1186/1687-5281-2014-34
Bhardwaj I, Londhe ND, Kopparapu SK (2017) A spoof resistant multibiometric system based on the physiological and behavioral characteristics of fingerprint. Pattern Recognit 62:214–224. https://doi.org/10.1016/j.patcog.2016.09.003
Bhavani M (2013) Human identification using finger images. Int J Comput Trends Technol 4(1):258–263
MathSciNet Google Scholar
Bhukya S (2019) A hybrid biometric identification and authentication system with retinal verification using AWN classifier for enhancing security. https://doi.org/10.1007/978-981-13-1580-0
Borra SR, Reddy GJ, Reddy ES (2016) A broad survey on fingerprint recognition systems. In: Proceedings of the 2016 IEEE international conference on wireless communications, signal processing and networking, WiSPNET 2016, pp 1428–1434. https://doi.org/10.1109/WiSPNET.2016.7566372
Boubchir L, Aberni Y, Daachi B (2018) Competitive coding scheme based on 2D log-gabor filter for palm vein recognition. In: 2018 NASA/ESA conference on adaptive hardware and systems (AHS), vol (i), pp 152–155
Buciu I, Gacsadi A (2016) Biometrics systems and technologies: a survey. Int J Comput Commun Control 11(3):315–330. https://doi.org/10.15837/ijccc.2016.3.2556
Cancian P, Di Donato GW, Rana V, Santambrogio MD, Elettronica D, Bioingegneria I, Milano P (2017) An embedded gabor-based palm vein recognition system, pp 405–408
Cao K, Jain AK (2018) Fingerprint indexing and matching: an integrated approach. In: IEEE international joint conference on biometrics, pp 437–445. https://doi.org/10.1109/BTAS.2017.8272728
Cao K, Jain AK (2019) Automated latent fingerprint recognition. IEEE Trans Pattern Anal Mach Intell 41(4):788–800. https://doi.org/10.1109/TPAMI.2018.2818162
Chauhan S, Arora AS, Kaul A (2010) A survey of emerging biometric modalities. Procedia Comput Sci 2:213–218. https://doi.org/10.1016/j.procs.2010.11.027
Chen Z, Huang W, Lv Z (2015) Towards a face recognition method based on uncorrelated discriminant sparse preserving projection. https://doi.org/10.1007/s11042-015-2882-0
Choraś M (2007) Human lips recognition. Adv Soft Comput 45:838–843. https://doi.org/10.1007/978-3-540-75175-5_104
Choraś M (2010) The lip as a biometric. Pattern Anal Appl 13(1):105–112. https://doi.org/10.1007/s10044-008-0144-8
Article MathSciNet Google Scholar
Chugh T, Cao K, Jain AK (2018) Fingerprint spoof detection using minutiae-based local patches. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 581–589. https://doi.org/10.1109/BTAS.2017.8272745
Czajka A, Bowyer KW (2018) Presentation attack survey. ACM Comput Surv 51(4):1–35. https://doi.org/10.1145/3232849
Czajka A, Bowyer KW (2018) Presentation attack detection for iris recognition: an assessment of the state-of-the-art. ACM Comput Surv 51(4):86
Czajka A, Moreira D, Bowyer KW, Flynn PJ (2019) Domain-specific human-inspired binarized statistical image features for Iris recognition. In: Proceedings of IEEE winter conference on applications of computer vision, WACV 2019, pp 959–967. https://doi.org/10.1109/WACV.2019.00107
Dargan S, Kumar M (2020) A comprehensive survey on the biometric recognition systems based on physiological and behavioral modalities. Expert Syst Appl 143:113114. https://doi.org/10.1016/j.eswa.2019.113114
Darlow LN, Rosman B (2018) Fingerprint minutiae extraction using deep learning. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 22–30. https://doi.org/10.1109/BTAS.2017.8272678
Das S, Muhammad K, Bakshi S, Mukherjee I, Sa PK, Sangaiah AK, Bruno A (2019) Lip biometric template security framework using spatial steganography. Pattern Recognit Lett 126:102–110. https://doi.org/10.1016/j.patrec.2018.06.026
Deljavan Amiri M, Akhlaqian Tab F, Barkhoda W (2009) Retina identification based on the pattern of blood vessels using angular and radial partitioning. In: Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), 5807 LNCS, pp 732–739. https://doi.org/10.1007/978-3-642-04697-1_68
Deng J (2017) Marginal loss for deep face recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition workshops
Deng J (2019) ArcFace: additive angular margin loss for deep face recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, no 1
Deng J, Lu X (2019) Lightweight face recognition challenge. In: Proceedings of the international conference on computer vision workshop. https://doi.org/10.1109/ICCVW.2019.00322
Ding H, Zhou SK, Chellappa R (2017) FaceNet2ExpNet: regularizing a deep face recognition net for expression recognition. In: Proceedings of the12th IEEE international conference on automatic face & gesture recognition (FG 2017), pp 118–126. https://doi.org/10.1109/FG.2017.23
Dongyang DU, Lijun LU, Ruiyang FU, Lisha Y, Wufan C, Yaqin LIU (2019) Palm vein recognition based on end-to-end convolutional neural network 39(2):207–214. https://doi.org/10.12122/j.issn.1673-4254.2019.02.13
Donida Labati R, Genovese A, Muñoz E, Piuri V, Scotti F (2018) A novel pore extraction method for heterogeneous fingerprint images using convolutional neural networks. Pattern Recognit Lett 113:58–66. https://doi.org/10.1016/j.patrec.2017.04.001
Dua M, Gupta R, Khari M, Crespo RG (2019) Biometric iris recognition using radial basis function neural network. Soft Comput 23(22):11801–11815. https://doi.org/10.1007/s00500-018-03731-4
Duan Y, Lu J, Member S, Feng J, Zhou J (2017) Context-aware local binary feature learning for face recognition 8828:1–14. https://doi.org/10.1109/TPAMI.2017.2710183
Engineering C, Gables C (2017) Low resolution face recognition in surveillance systems using discriminant correlation analysis, pp 912–917. https://doi.org/10.1109/FG.2017.130
Fachrurrozi M (2017) Multi-object face recognition using content based image retrieval (CBIR), no x, pp 193–197
Fairuz MS, Habaebi MH, Elsheikh EMA (2019) Pre-trained based CNN model to identify finger vein. Bull Electr Eng Inform 8(3):855–862. https://doi.org/10.11591/eei.v8i3.1505
Fronitasari D, Indonesia U, Gunawan D, Indonesia U (2017) Palm vein recognition by using modified of local binary pattern (LBP) for extraction feature, pp 18–22
Gao Y, Zhao M, Yuille AL (2017). Semi-supervised sparse representation based classification for face recognition with insufficient labeled samples. https://doi.org/10.1109/TIP.2017.2675341
Gomez-barrero M, Kolberg J, Busch C (2018) Towards multi-modal finger presentation attack detection. In: 2018 14th international conference on signal-image technology & internet-based systems (SITIS), pp 547–552. https://doi.org/10.1109/SITIS.2018.00089
Gumede A, Viriri S, Gwetu M (2017) Hybrid component-based face recognition. In: Proceedings of the conference on information communication technology and society, pp 0–5
Guo X, Zhu E, Yin J (2018) A fast and accurate method for detecting fingerprint reference point. Neural Comput Appl 29(1):21–31. https://doi.org/10.1007/s00521-016-2285-9
Hamdan B, Mokhtar K (2016) Face recognition using angular radial transform. J King Saud Univ Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2016.10.006
Harish M, Karthick R, Rajan RM, Vetriselvi V (2019) Iccce 2018. In: Proceedings of the international conference on communications and cyber physical engineering 2018, vol 500. https://doi.org/10.1007/978-981-13-0212-1
Hassner T, Sahin G, Medioni G, Masi I, Tu A (2019) Face-specific data augmentation for unconstrained face recognition. Int J Comput Vis 127:642–667. https://doi.org/10.1007/s11263-019-01178-0
Hatanaka Y, Tajima M, Kawasaki R, Saito K, Ogohara K, Muramatsu C, Fujita H (2017) Retinal biometrics based on iterative closest point algorithm. In: Proceedings of the annual international conference of the IEEE engineering in medicine and biology society, EMBS. https://doi.org/10.1109/EMBC.2017.8036840
Haware S, Barhatte A (2017) Retina based biometric identification using SURF and ORB feature descriptors. In: 2017 international conference on microelectronic devices, circuits and systems, ICMDCS 2017, 2017 January, pp 1–6. https://doi.org/10.1109/ICMDCS.2017.8211697
Heinsohn D, Villalobos E, Prieto L, Mery D (2019) Face recognition in low-quality images using adaptive sparse representations. Image Vis Comput 85:46–58. https://doi.org/10.1016/j.imavis.2019.02.012
Hemanth J (2018) Palm vein recognition based on competitive code, LBP and DCA fusion strategy
Hofbauer H, Jalilian E, Uhl A (2019) Exploiting superior CNN-based iris segmentation for better recognition accuracy. Pattern Recognit Lett 120:17–23. https://doi.org/10.1016/j.patrec.2018.12.021
Hosny KM, Elaziz MA (n.d.) Face recognition using exact Gaussian-hermit moments. https://doi.org/10.1007/978-3-030-03000-1
Hou B, Yan R (2019) Convolutional auto-encoder model for finger-vein verification. IEEE Trans Instrum Meas. https://doi.org/10.1109/tim.2019.2921135
Hsieh SH, Li YH, Wang W, Tien CH (2018) A novel anti-spoofing solution for iris recognition toward cosmetic contact lens attack using spectral ICA analysis. Sensors (Switzerland). https://doi.org/10.3390/s18030795
Hu Y, Sirlantzis K, Howells G (2017) A novel iris weight map method for less constrained iris recognition based on bit stability and discriminability. Image Vis Comput 58:168–180. https://doi.org/10.1016/j.imavis.2016.05.003
Huang J, Zhang Y, Zhang H, Cheng K (2019) Sparse representation face recognition based on gabor and CSLDP feature fusion. In: 2019 Chinese control and decision conference (CCDC), no 1, pp 5697–5701
Hussein ME, Spinoulas L, Xiong F, Abd-Almageed W (2019) Fingerprint presentation attack detection using a novel multi-spectral capture device and patch-based convolutional neural networks. In: 10th IEEE international workshop on information forensics and security. WIFS 2018:1–8. https://doi.org/10.1109/WIFS.2018.8630773
Ito K, Aoki T (2018) Recent advances in biometric recognition. ITE Trans Media Technol Appl 6(1):64–80. https://doi.org/10.3169/mta.6.64
Jacob IJ (2019) Capsule network based biometric recognition system 01(02):83–93
Jain A, East L, Ruud B, Pankanti S, Yorktown H (2002) Introduction to biometrics. Anil Jain Michigan State University. Biometrics: Personal Identification in Networked Society (ii), p 19
Jain AK, Kumar A (2012) Biometric recognition: an overview, pp 49–79. https://doi.org/10.1007/978-94-007-3892-8_3
Jalilian E, Uhl A (2019) Enhanced segmentation-CNN based finger-vein recognition by joint training with automatically generated and manual labels. In: 2019 IEEE 5th international conference on identity, security, and behavior analysis (ISBA), pp 1–8. https://doi.org/10.1109/isba.2019.8778522
Jang HU, Kim D, Mun SM, Choi S, Lee HK (2017) DeepPore: fingerprint pore extraction using deep convolutional neural networks. IEEE Signal Process Lett 24(12):1808–1812. https://doi.org/10.1109/LSP.2017.2761454
Jasim YA, Al-Ani AA, Al-Ani LA (2019) Iris recognition using principal component analysis. In: Proceedings—2018 1st annual international conference on information and sciences, AiCIS 2018, pp 89–95. https://doi.org/10.1109/AiCIS.2018.00028
Jeon WS, Rhee SY (2017) Fingerprint pattern classification using convolution neural network. Int J Fuzzy Logic Intell Syst 17(3):170–176. https://doi.org/10.5391/IJFIS.2017.17.3.170
Ji H, Sun Q, Ji Z, Yuan Y, Zhang G (2017) Collaborative probabilistic labels for face recognition from single sample per person. Pattern Recognit 62:125–134. https://doi.org/10.1016/j.patcog.2016.08.007
Joshi I, Anand A, Vatsa M, Singh R, Roy SD, Kalra PK (2019) Latent fingerprint enhancement using generative adversarial networks. In: Proceedings—2019 IEEE winter conference on applications of computer vision, WACV 2019, pp 895–903. https://doi.org/10.1109/WACV.2019.00100
Kang W, Lu Y, Li D, Jia W (2019) From noise to feature: Exploiting intensity distribution as a novel soft biometric trait for finger vein recognition. IEEE Trans Inf Forens Secur 14(4):858–869
Kaur B, Singh S, Kumar J (2018) Robust iris recognition using moment invariants. Wireless Pers Commun 99(2):799–828. https://doi.org/10.1007/s11277-017-5153-8
Keilbach P, Kolberg J, Gomez-Barrero M, Busch C, Langweg H (2018) Fingerprint presentation attack detection using laser speckle contrast imaging. In: 2018 international conference of the biometrics special interest group, BIOSIG 2018, pp 1–6. https://doi.org/10.23919/BIOSIG.2018.8552931
Kerrigan D, Trokielewicz M, Czajka A, Bowyer K (2019) Iris recognition with image segmentation employing retrained off-the-shelf deep neural networks. http://arxiv.org/abs/1901.01028
Khan T, Donald B, Khan M, Kong Y (1983) Efficient hardware implementation for fingerprint image enhancement using anisotropic gaussian filter. IEEE Trans Image Process 23(1):309–317. https://doi.org/10.1002/qua.560230126
Khan AI, Wani MA (2019) Patch-based segmentation of latent fingerprint images using convolutional neural network. Appl Artif Intell 33(1):87–100. https://doi.org/10.1080/08839514.2018.1526704
Khodadoust J, Khodadoust AM (2017) Fingerprint indexing based on minutiae pairs and convex core point. Pattern Recognit 67:110–126
Kim H, Cui X, Kim MG, Nguyen THB (2019) Fingerprint generation and presentation attack detection using deep neural networks. In: Proceedings—2nd international conference on multimedia information processing and retrieval, MIPR 2019, pp 375–378. https://doi.org/10.1109/MIPR.2019.00074
Kr P, Lenc L (2019) Novel texture descriptor family for face recognition 2:37–47. https://doi.org/10.1007/978-3-030-20915-5
Kr P, Lenc L (2019) Enhanced local binary patterns for automatic face recognition 2:27–36. https://doi.org/10.1007/978-3-030-20915-5
Král P, Lenc L and Vrba A (2019) Enhanced local binary patterns for automatic face recognition. In: International conference on artificial intelligence and soft computing. Springer, Cham, pp 27–36
Krish RP, Fierrez J, Ramos D, Alonso-Fernandez F, Bigun J (2019) Improving automated latent fingerprint identification using extended minutia types. Inf Fusion 50:9–19. https://doi.org/10.1016/j.inffus.2018.10.001
Kumar SVM, Nishanth R, Sani N, Joseph AJ, Martin A (2019) Specular reflection removal using morphological filtering for accurate iris recognition. In: 6th IEEE international conference on smart structures and systems, ICSSS 2019, pp 1–4. https://doi.org/10.1109/ICSSS.2019.8882863
Lee EC, Jung H, Kim D (2011) New finger biometric method using near infrared imaging. Sensors 11(3):2319–2333. https://doi.org/10.3390/s110302319
Li C (2017) Dependence structure of gabor wavelets for face recognition, pp 0–4
Li J, Feng J, Kuo CCJ (2018) Deep convolutional neural network for latent fingerprint enhancement. Signal Process Image Commun 60:52–63. https://doi.org/10.1016/j.image.2017.08.010
Li L, Ge H, Tong Y, Zhang Y (2017). Face recognition using gabor-based feature extraction and feature space transformation fusion method for single image per person problem. https://doi.org/10.1007/s11063-017-9693-4
Li G, Kim J (2016) Author’s accepted manuscript palmprint recognition with local micro-structure tetra pattern reference. Pattern Recognit. https://doi.org/10.1016/j.patcog.2016.06.025
Lin BS, Yao YH, Liu CF, Lien CF, Lin BS (2017) Impact of the lips for biometrics. IEEE Access 5:794–801. https://doi.org/10.1109/ACCESS.2017.2649838
Linsangan NB, Panganiban AG, Flores PR, Poligratis HAT, Victa AS, Torres JL, Villaverde J (2019) Real-time iris recognition system for non-ideal iris images. ACM Int Conf Proc Ser. https://doi.org/10.1145/3313991.3314002
Liu JLC, Chen X, Zhou J, Tan T, Zheng N, Zha H, Hutchison D (2018) Pattern recognition and computer vision
Liu X, Kan M, Wu W, Shan S (2017) VIPLFaceNet : an open source deep face recognition SDK 11(2):208–218
Liu N, Liu J, Sun Z, Tan T (2017) A code-level approach to heterogeneous iris recognition. IEEE Trans Inf Forens Secur 12(10):2373–2386. https://doi.org/10.1109/TIFS.2017.2686013
Liu Y, Member S, Lin C, Guo J, Member S (2012) Impact of the lips in facial biometrics 21(6):3092–3101
Liu H, Yang L, Yang G, Yin Y (2018) Discriminative binary descriptor for finger vein recognition. IEEE Access 6:5795–5804. https://doi.org/10.1109/ACCESS.2017.2787543
Liu H, Yang G, Yang L, Yin Y (2019) Learning personalized binary codes for finger vein recognition. Neurocomputing 365:62–70. https://doi.org/10.1016/j.neucom.2019.07.057
Liu M, Zhou Z, Shang P, Xu D (2019) Fuzzified image enhancement for deep learning in iris recognition. IEEE Trans Fuzzy Syst. https://doi.org/10.1109/tfuzz.2019.2912576
Llano EG, García Vázquez MS, Vargas JMC, Fuentes LMZ, Ramírez Acosta AA (2018) Optimized robust multi-sensor scheme for simultaneous video and image iris recognition. Pattern Recognit Lett 101:44–51. https://doi.org/10.1016/j.patrec.2017.11.012
Lu J, Member S, Liong VE, Member S, Zhou J (2017) Simultaneous local binary feature learning and encoding for homogeneous and heterogeneous face recognition 8828:1–14. https://doi.org/10.1109/TPAMI.2017.2737538
Lu Yu, Xie S, Wu S (2019) Exploring competitive features using deep convolutional neural network for finger vein recognition. IEEE Access 7:35113–35123. https://doi.org/10.1109/ACCESS.2019.2902429
Lu Y, Yan J, Gu K (2018) Review on automatic lip reading techniques. Int J Pattern Recognit Artif Intell 32(7):1–21. https://doi.org/10.1142/S0218001418560074
Lv J (2018) A new discriminative collaborative neighbor representation method for robust face recognition, pp 74713–74727
Lv J-J, Shao X, Huang J, Zhou X, Zhou X, Lv J, Zhou X (2016) Face-specific data augmentation for unconstrained face recognition. Neurocomputing. https://doi.org/10.1016/j.neucom.2016.12.025
Malik F, Azis A, Nasrun M, Setianingsih C, Murti MA (2018) Face recognition in night day using method eigenface, pp 103–108
Manickam A, Devarasan E, Manogaran G, Priyan MK, Varatharajan R, Hsu CH, Krishnamoorthi R (2019) Score level based latent fingerprint enhancement and matching using SIFT feature. Multimed Tools Appl 78(3):3065–3085. https://doi.org/10.1007/s11042-018-5633-1
Mariño C, Penedo MG, Penas M, Carreira MJ, Gonzalez F (2006) Personal authentication using digital retinal images. Pattern Anal Appl 9(1):21–33. https://doi.org/10.1007/s10044-005-0022-6
Marra F, Poggi G, Sansone C, Verdoliva L (2018) A deep learning approach for iris sensor model identification. Pattern Recognit Lett 113:46–53. https://doi.org/10.1016/j.patrec.2017.04.010
Mathematics A (2018) Biometric retinal security system for user identification and authentication in smartphones 119(14):187–202
Mazumdar JB (2018) Retina based biometric authentication system: a review. Int J Adv Res Comput Sci 9(1):711–718. https://doi.org/10.26483/ijarcs.v9i1.5322
Mazumdar JB, Nirmala SR (2018) Retina based biometric authentication system: a review. Int J Adv Res Comp Sci 9(1):711–718
Mazumdar J, Nirmala SR (2019) Person identification using parabolic model-based algorithm in color retinal images. https://doi.org/10.18178/ijeetc.8.6.358-366
Meng XJ, Yin YL, Yang GP, Xi XM (2013) Retinal identification based on an improved circular gabor filter and scale invariant feature transform. Sensors (Switzerland) 13(7):9248–9266. https://doi.org/10.3390/s130709248
Minaee S, Abdolrashidi A (2019) DeepIris: iris recognition using a deep learning approach. http://arxiv.org/abs/1907.09380
Mir SA, Khan S, Bhat MA, Mehraj H (2018) Person identification by lips using SGLDM and support vector machine 4(1):152–157
Miura N, Nagasaka A, Miyatake T (2004) Feature extraction of finger vein patterns based on iterative line tracking and its application to personal identification. Syst Comput Jpn 35(7):61–71. https://doi.org/10.1002/scj.10596
Miura N, Nagasaka A, Miyatake T (2007) Extraction of finger-vein patterns using maximum curvature points in image profiles. IEICE Trans Inf Syst E90-D(8):1185–1194. https://doi.org/10.1093/ietisy/e90-d.8.1185
Moorfield J, Wang S, Yang W, Bedari A, Van Der Kamp P (2020) A Möbius transformation based model for fingerprint minutiae variations. Pattern Recognit 98:107054. https://doi.org/10.1016/j.patcog.2019.107054
Morales S, Naranjo V, Angulo J, Legaz-Aparicio AG, Verdú-Monedero R (2017) Retinal network characterization through fundus image processing: significant point identification on vessel centerline. Signal Process Image Commun 59:50–64. https://doi.org/10.1016/j.image.2017.03.013
Mura V, Orru G, Casula R, Sibiriu A, Loi G, Tuveri P et al. (2018) LivDet 2017 fingerprint liveness detection competition 2017. In: Proceedings—2018 international conference on biometrics, ICB 2018, pp 297–302. https://doi.org/10.1109/ICB2018.2018.00052
Nachar R, Inaty E, Bonnin PJ, Alayli Y (2020) Hybrid minutiae and edge corners feature points for increased fingerprint recognition performance. Pattern Anal Appl 23(1):213–222
Naseem I, Aleem A, Togneri R, Bennamoun M (2017) Iris recognition using class-specific dictionaries. Comput Electr Eng 62:178–193. https://doi.org/10.1016/j.compeleceng.2015.12.017
Nguyen DL, Cao K, Jain AK (2019) Automatic latent fingerprint segmentation. In: 2018 IEEE 9th international conference on biometrics theory, applications and systems, BTAS 2018, pp 1–9. https://doi.org/10.1109/BTAS.2018.8698544
Nguyen DL, Cao K, Jain AK (2018) Robust minutiae extractor: integrating deep networks and fingerprint domain knowledge. In: Proceedings—2018 international conference on biometrics, ICB 2018, pp 9–16. https://doi.org/10.1109/ICB2018.2018.00013
Nguyen K, Fookes C, Jillela R, Sridharan S, Ross A (2017) Long range iris recognition: a survey. Pattern Recognit 72:123–143. https://doi.org/10.1016/j.patcog.2017.05.021
Nguyen K, Fookes C, Ross A, Sridharan S (2017) Iris recognition with off-the-shelf CNN features: a deep learning perspective. IEEE Access 6:18848–18855. https://doi.org/10.1109/ACCESS.2017.2784352
Oliveira A, Pereira S, Silva CA (2018) Retinal vessel segmentation based on fully convolutional neural networks. Expert Syst Appl 112:229–242. https://doi.org/10.1016/j.eswa.2018.06.034
Pandya B, Cosma G, Alani AA, Taherkhani A, Bharadi V, McGinnity TM (2018) Fingerprint classification using a deep convolutional neural network. In: 2018 4th international conference on information management, ICIM 2018, pp 86–91. https://doi.org/10.1109/INFOMAN.2018.8392815
Panetta K, Kamath SKM, Rajeev S, Agaian SS (2019) LQM: localized quality measure for fingerprint image enhancement. IEEE Access 7:104567–104576. https://doi.org/10.1109/access.2019.2931980
Parihar RS, Jain S (2019) A robust method to recognize palm vein using SIFT and SVM classifier 1:1703–1710
Park Y, Jang U, Lee EC (2018) Statistical anti-spoofing method for fingerprint recognition. Soft Comput 22(13):4175–4184. https://doi.org/10.1007/s00500-017-2707-3
Park K, Song M, Youn Kim S (2018) The design of a single-bit CMOS image sensor for iris recognition applications. Sensors (Switzerland). https://doi.org/10.3390/s18020669
Pei T, Zhang L, Wang B (2016) Decision Pyramid Classifier for face recognition under complex variations using single sample per person. Pattern Recognit. https://doi.org/10.1016/j.patcog.2016.11.016
Peng C, Gao X, Wang N, Li J (2018) Face recognition from multiple stylistic sketches: scenarios, datasets, and evaluation. Pattern Recognit 84:262–272. https://doi.org/10.1016/j.patcog.2018.07.014
Peralta D, García S, Benitez JM, Herrera F (2017) Minutiae-based fingerprint matching decomposition: methodology for big data frameworks. Inf Sci 408:198–212. https://doi.org/10.1016/j.ins.2017.05.001
Piciucco E, Maiorana E, Campisi P (2017) Biometric fusion for palm-vein-based recognition systems palm vein biometric recognition: state of the art, pp 18–28. https://doi.org/10.1007/978-3-319-67639-5
Piciucco E, Maiorana E, Campisi P (2018) Palm vein recognition using a high dynamic range approach, pp 1–8. https://doi.org/10.1049/iet-bmt.2017.0192
Qin H, He X, Yao X, Li H (2017) Finger-vein verification based on the curvature in Radon space. Expert Syst Appl 82:151–161. https://doi.org/10.1016/j.eswa.2017.03.068
Qin H, Wang P (2019) Finger-vein verification based on LSTM recurrent neural networks. Appl Sci (Switzerland) 9(8):1–18. https://doi.org/10.3390/app9081687
Qureshi I, Khan MA, Sharif M, Saba T, Ma J (2020) Detection of glaucoma based on cup-to-disc ratio using fundus images 19(1):1–16
Qureshi I, Ma J, Abbas Q (2019) Recent development on detection methods for the diagnosis of diabetic retinopathy. Symmetry 11(6):1–34. https://doi.org/10.3390/sym11060749
Qureshi I, Ma J, Shaheed K (2019) A hybrid proposed fundus image enhancement framework for diabetic retinopathy, pp 1–16. https://doi.org/10.3390/a12010014
Raja KB, Raghavendra R, Venkatesh S, Busch C (2017) Multi-patch deep sparse histograms for iris recognition in visible spectrum using collaborative subspace for robust verification. Pattern Recognit Lett 91:27–36. https://doi.org/10.1016/j.patrec.2016.12.025
Ramachandra R, Raja KB, Venkatesh SK, Busch C (2019) Design and development of low-cost sensor to capture ventral and dorsal finger vein for biometric authentication. IEEE Sens J 19(15):6102–6111. https://doi.org/10.1109/JSEN.2019.2906691
Rana HK (2017) SM Gr up SM journal of iris recognition system using PCA based on DWT. SM J Biometrics Biostat 2:1015. https://doi.org/10.5281/zenodo.2580202
Ranjani R, Priya C (2018) A survey on face recognition techniques: a review. Int J Pure Appl Math 118:253–274
Rathgeb C, Wagner J, Busch C (2019) SIFT-based iris recognition revisited: prerequisites, advantages and improvements. Pattern Anal Appl 22(3):889–906. https://doi.org/10.1007/s10044-018-0719-y
Roy ND, Biswas A (2019) Fast and robust retinal biometric key generation using deep neural nets
Rui Z, Yan Z (2019) A survey on biometric authentication: toward secure and privacy-preserving identification. IEEE Access 7:5994–6009. https://doi.org/10.1109/ACCESS.2018.2889996
Sahu B, Kumar Sa P, Bakshi S, Sangaiah AK (2018) Reducing dense local feature key-points for faster iris recognition. Comput Electr Eng 70:939–949. https://doi.org/10.1016/j.compeleceng.2017.12.048
Sang J, Wang H, Qian Q, Wu H, Chen Y (2018) An efficient fingerprint identification algorithm based on minutiae and invariant moment. Pers Ubiquit Comput 22(1):71–80. https://doi.org/10.1007/s00779-017-1094-1
De Santis M, Agnelli S, Don V, Gnocchi C (2017) 3D ultrasound palm vein recognition through the centroid method for biometric purposes, pp 1–4
Shaheed K, Liu H, Yang G, Qureshi I, Gou J, Yin Y (2018) A systematic review of finger vein recognition techniques. Information (Switzerland). https://doi.org/10.3390/info9090213
Shaheed K, Yang L, Yang G, Qureshi I, Yin Y (2018) Novel image quality assessment and enhancement techniques for finger vein recognition, pp 223–231
Shao L, Zhu R, B QZ (2016) A finger vein identification system based on image quality assessment, vol 3, pp 711–719. https://doi.org/10.1007/978-3-319-46654-5
Sharma RP, Dey S (2019). Quality analysis of fingerprint images using local phase quantization. https://doi.org/10.1007/978-3-030-29888-3_53
Shuyi L, Haigang Z, Jinfeng Y (2019) Finger vein recognition based on local graph structural coding and CNN. May, vol 8. https://doi.org/10.1117/12.2524152
Soh SC, Ibrahim MZ, Abas MF (2019) Image fusion based multi resolution and frequency partition discrete cosine transform for palm vein recognition. In: 2019 IEEE 6th international conference on industrial engineering and applications (ICIEA), pp 367–371
Soh SC, Ibrahim MZ, Yakno MB, Mulvaney DJ (2017) Palm vein recognition using scale invariant feature transform with RANSAC mismatching removal. IT Converg Secur 2017:2. https://doi.org/10.1007/978-981-10-6451-7
Song JM, Kim W, Park KR (2019) Finger-vein recognition based on deep densenet using composite image. IEEE Access 7:66845–66863. https://doi.org/10.1109/ACCESS.2019.2918503
de Souza GB, Santos DFdS, Pires RG, Marana AN, Papa JP (2018) Deep features extraction for robust fingerprint spoofing attack detection. J Artif Intell Soft Comput Res 9(1):41–49. https://doi.org/10.2478/jaiscr-2018-0023
Sun Y, Wang X, Tang X (2013) Deep convolutional network cascade for facial point detection. https://doi.org/10.1109/CVPR.2013.446
Sundararajan K, Woodard DL (2018) Deep learning for biometrics: a survey. ACM Comput Surv. https://doi.org/10.1145/3190618
Sutanty E, Rahayu DA, Rodiah, Susetianingtias DT, Madenda S (2017) Retinal blood vessel segmentation and bifurcation detection using combined filters. In: Proceeding—2017 3rd international conference on science in information technology: theory and application of IT for education, industry and society in big data era, ICSITech 2017, 2018 January, pp 563–567. https://doi.org/10.1109/ICSITech.2017.8257176
Svoboda J, Monti F, Bronstein MM (2018) Generative convolutional networks for latent fingerprint reconstruction. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 429–436. https://doi.org/10.1109/BTAS.2017.8272727
Syarif MA, Ong TS, Teoh ABJ, Tee C (2017) Enhanced maximum curvature descriptors for finger vein verification. Multimed Tools Appl 76(5):6859–6887. https://doi.org/10.1007/s11042-016-3315-4
Tams B (2013) Absolute fingerprint pre-alignment in minutiae-based cryptosystems. In: BIOSIG 2013—proceedings of the 12th international conference of the biometrics special interest group, pp 1–12
Tang Z, Wu X, Fu B, Chen W, Feng H (2018) Fast face recognition based on fractal theory. Appl Math Comput 321:721–730. https://doi.org/10.1016/j.amc.2017.11.017
Article MathSciNet MATH Google Scholar
Tann H, Zhao H, Reda S (2019) A resource-efficient embedded iris recognition system using fully convolutional networks. ACM J Emerg Technol Comput Syst 16(1):1–23. https://doi.org/10.1145/3357796
Tertychnyi P, Ozcinar C, Anbarjafari G (2018) Low-quality fingerprint classification using deep neural network. IET Biometrics 7(6):550–556. https://doi.org/10.1049/iet-bmt.2018.5074
Thapar D, Jaswal G, Nigam A (2018) PVSNet: palm vein authentication siamese network trained using triplet loss and adaptive hard mining by learning enforced domain specific features. In: 2019 IEEE 5th international conference on identity, security, and behavior analysis (ISBA), pp 1–8
Thompson J, Flynn P, Boehnen C, Santos-Villalobos H (2019) Assessing the impact of corneal refraction and iris tissue non-planarity on iris recognition. IEEE Trans Inf Forens Secur 14(8):2102–2112. https://doi.org/10.1109/TIFS.2018.2869342
Tran MH, Duong TN, Nguyen DM, Dang QH (2017) A local feature vector for an adaptive hybrid fingerprint matcher. In: Proceedings of KICS-IEEE international conference on information and communications with samsung LTE and 5G special workshop, ICIC 2017, pp 249–253. https://doi.org/10.1109/INFOC.2017.8001668
Travieso CM, Ravelo-García AG, Alonso JB, Canino-Rodríguez JM, Dutta MK (2019) Improving the performance of the lip identification through the use of shape correction. Appl Intell 49(5):1823–1840
Travieso CM, Zhang J, Miller P, Alonso JB (2014) Using a discrete Hidden Markov Model Kernel for lip-based biometric identification. Image Vis Comput 32(12):1080–1089. https://doi.org/10.1016/j.imavis.2014.10.001
Unar JA, Seng WC, Abbasi A (2014) A review of biometric technology along with trends and prospects. Pattern Recognit 47(8):2673–2688. https://doi.org/10.1016/j.patcog.2014.01.016
Wan C, Wang L, Phoha VV (2018) A survey on gait recognition. ACM Comput Surv. https://doi.org/10.1145/3230633
Wang X (2019) Palm vein recognition based on competitive code and, pp 179–183
Wang K, Kumar A (2019) Toward more accurate iris recognition using dilated residual features. IEEE Trans Inf Forens Secur 14(12):3233–3245
Wang Z, Ma S, Han M, Hu G (2017) Long-distance/environment face image enhancement method for recognition, no 1, pp 501–511. https://doi.org/10.1007/978-3-319-71607-7
Wang H, Yang X, Ma L, Liang R (2017) Fingerprint pore extraction using U-Net based fully convolutional network 1:474–483. https://doi.org/10.1007/978-3-319-69923-3
Xi X, Yang L (2017) Learning discriminative binary codes for finger vein recognition. Pattern Recognit 66:26–33. https://doi.org/10.1016/j.patcog.2016.11.002
Xia Z, Lv R, Zhu Y, Ji P, Sun H, Shi YQ (2017) Fingerprint liveness detection using gradient-based texture features. SIViP 11(2):381–388. https://doi.org/10.1007/s11760-016-0936-z
Xin M (2017) Palm vein recognition method based on fusion of local Gabor histograms. J China Univ Posts Telecommun 24(6):55–66. https://doi.org/10.1016/S1005-8885(17)60242-5
Yahaya YH, Shamsuddin SM, Leng WY, Technology D, Pertahanan U (2016) Finger vein feature extraction using discretization. November, pp 28–29
Yang W, Huang X, Zhou F, Liao Q (2014) Comparative competitive coding for personal identification by using finger vein and finger dorsal texture fusion. Inf Sci 268:20–32. https://doi.org/10.1016/j.ins.2013.10.010
Yang W, Ji W, Xue JH, Ren Y, Liao Q (2019) A hybrid finger identification pattern using polarized depth-weighted binary direction coding. Neurocomputing 325:260–268. https://doi.org/10.1016/j.neucom.2018.10.042
Yang W, Ma G, Li W, Liao Q (2013) Finger vein verification based on neighbor pattern coding. IEICE Trans Inf Syst E96-D(5):1227–1229. https://doi.org/10.1587/transinf.E96.D.1227
Yang J, Shi Y, Jia G (2017) Finger-vein image matching based on adaptive curve transformation. Pattern Recognit 66:34–43. https://doi.org/10.1016/j.patcog.2017.01.008
Yang W, Wang S, Hu J, Zheng G, Valli C (2019) Security and accuracy of fingerprint-based biometrics: a review. Symmetry. https://doi.org/10.3390/sym11020141
Yang W, Wang S, Hu J, Zheng G, Yang J, Valli C (2019) Securing deep learning based edge finger vein biometrics with binary decision diagram. IEEE Trans Ind Inf 15(7):4244–4253. https://doi.org/10.1109/TII.2019.2900665
Yang M, Wang X, Zeng G, Shen L (2017) Joint and collaborative representation with local adaptive convolution feature for face recognition with single sample per person. Pattern Recognit 66:117–128. https://doi.org/10.1016/j.patcog.2016.12.028
Yang J, Wei J, Shi Y (2019) Accurate ROI localization and hierarchical hyper-sphere model for finger-vein recognition. Neurocomputing 328:171–181. https://doi.org/10.1016/j.neucom.2018.02.098
Yang L, Yang G, Wang K, Liu H, Xi X, Yin Y (2019) Point grouping method for finger vein recognition. IEEE Access 7:28185–28195. https://doi.org/10.1109/ACCESS.2019.2901017
Yang L, Yang G, Xi X, Meng X, Zhang C, Yin Y (2017) Tri-branch vein structure assisted finger vein recognition. IEEE Access 5:21020–21028. https://doi.org/10.1109/ACCESS.2017.2728797
Yang L, Yang G, Yin Y, Xi X (2018) Finger vein recognition with anatomy structure analysis. IEEE Trans Circuits Syst Video Technol 28(8):1892–1905. https://doi.org/10.1109/TCSVT.2017.2684833
Ye L, Wang H, Du M, He Y, Tao L (2019) Weber local descriptor with edge detection and double Gabor orientations for finger vein recognition. In: Tenth international conference on graphics and image processing (ICGIP 2018), vol 11069. International Society for Optics and Photonics, p 110693J
Yin B, Tran L, Li H, Shen X, Liu X (2018) Towards interpretable face recognition, pp 9348–9357
You W, Zhou W, Huang J, Yang F, Liu Y, Chen Z (2019) A bilayer image restoration for finger vein recognition. Neurocomputing 348:54–65. https://doi.org/10.1016/j.neucom.2018.06.085
Yuan X, Gu L, Chen T, Elhoseny M, Wang W (2018) A fast and accurate retina image verification method based on structure similarity. In: Proceedings—IEEE 4th international conference on big data computing service and applications, BigDataService 2018, pp 181–185. https://doi.org/10.1109/BigDataService.2018.00034
Yuan C, Li X, Wu QMJ, Li J, Sun X (2017) Fingerprint liveness detection from different fingerprint materials using convolutional neural network and principal component analysis. Comput Mater Continua 53(4):357–371
Yuan C, Sun X, Wu QMJ (2019) Difference co-occurrence matrix using BP neural network for fingerprint liveness detection. Soft Comput 23(13):5157–5169. https://doi.org/10.1007/s00500-018-3182-1
Zafar U, Ghafoor M, Zia T, Ahmed G, Latif A, Malik KR, Sharif AM (2019) Face recognition with Bayesian convolutional networks for robust surveillance systems
Zhang M, He Z, Zhang H, Tan T, Sun Z (2019) Toward practical remote iris recognition: a boosting based framework. Neurocomputing 330:238–252. https://doi.org/10.1016/j.neucom.2017.12.053
Zhang Y, Li W, Zhang L, Lu Y (2019) Adaptive gabor convolutional neural networks for finger-vein recognition. In: 2019 International Conference on High Performance Big Data and Intelligent systems, HPBD and IS 2019, (61572458), pp 219–222. https://doi.org/10.1109/HPBDIS.2019.8735471
Zhang Y, Shi D, Zhan X, Cao D, Zhu K, Li Z (2019) Slim-ResCNN: a deep residual convolutional neural network for fingerprint liveness detection. IEEE Access 7:91476–91487. https://doi.org/10.1109/access.2019.2927357
Zhao Z, Kumar A (2017) Towards more accurate iris recognition using deeply learned spatially corresponding features. In: Proceedings of the IEEE international conference on computer vision, 2017 October, pp 3829–3838. https://doi.org/10.1109/ICCV.2017.411
Zhao T, Liu Y, Huo G, Zhu X (2019) A deep learning iris recognition method based on capsule network architecture. IEEE Access 7:49691–49701. https://doi.org/10.1109/ACCESS.2019.2911056
Download references
Acknowledgements
The work of this paper is financially supported by NSF of Guangdong Province (No. 2019A1515010833) and fundamental Research Funds for the Central Universities (No. 2020ZYGXZR089).
Author information
Authors and affiliations.
School of Computer Science and Engineering, South China University of Technology, Guangzhou, 510006, China
Kashif Shaheed, Aihua Mao & Xingming Zhang
Key Laboratory of Space Photoelectric Detection and Perception, Ministry of Industry and Information Technology and College of Astronautics, Nanjing University of Aeronautics and Astronautics, Nanjing, 211106, Jiangsu, China
Imran Qureshi
Department of Computational Sciences, Maharaja Ranjit Singh Punjab Technical University, Bathinda, Punjab, 151001, India
Munish Kumar
College of Computer and Information Sciences, Imam Muhammad Ibn Saud Islamic University (IMSIU), Riyadh, 11432, Saudi Arabia
Qaisar Abbas
School of Software Engineering, Shandong University, Jinan, 250100, China
You can also search for this author in PubMed Google Scholar
Corresponding authors
Correspondence to Kashif Shaheed or Aihua Mao .
Ethics declarations
Conflict of interest.
The authors declare that they have no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Shaheed, K., Mao, A., Qureshi, I. et al. A Systematic Review on Physiological-Based Biometric Recognition Systems: Current and Future Trends. Arch Computat Methods Eng 28 , 4917–4960 (2021). https://doi.org/10.1007/s11831-021-09560-3
Download citation
Received : 12 August 2020
Accepted : 28 January 2021
Published : 23 February 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s11831-021-09560-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Find a journal
- Publish with us
- Track your research

IMAGES
COMMENTS
This paper presents an overview of the main topics related to biometric security technology, with the central purpose to provide a primer on this subject. Biometrics can offer greater security and ...
This paper contributes by (1) providing a concise and informative overview of biometrics and its implications for pricing, (2) presenting a typology of consumer archetypes regarding how consumers interact with biometric tracking which can be used for future research and (3) presenting a research agenda of current research opportunities in this ...
Biometric systems are increasingly replacing traditional password- and token-based authentication systems. Security and recognition accuracy are the two most important aspects to consider in designing a biometric system. In this paper, a comprehensive review is presented to shed light on the latest developments in the study of fingerprint-based biometrics covering these two aspects with a view ...
With an insight into the state-of-the-art research in biometrics for IoT security, this review paper helps advance the study in the field and assists researchers in gaining a good understanding of forward-looking issues and future research directions. ... In search of research papers, a number of databases (e.g., IEEE Xplore, Web of Science ...
In this paper, we present a comprehensive review of the recent advances in biometric recognition using deep learning frameworks. For each work, we provide an overview of the key contributions, network architecture, and loss functions, developed to push state-of-the-art performance in biometric recognition. We have gathered more than 150 papers ...
This paper analyses the adaptive biometric authentication systems presented in literature based on four aspects as shown in the taxonomy in Fig. 2. ... Current research in adaptive biometric authentication considers well-known attacks to biometric authentication systems such as spoofing, replay attacks, and poisoning attacks. ...
This paper conducts an extensive review of biometric user authentication literature, addressing three primary research questions: (1) commonly used biometric traits and their suitability for specific applications, (2) performance factors such as security, convenience, and robustness, and potential countermeasures against cyberattacks, and (3) factors affecting biometric system accuracy and po ...
Various biometric systems used to measure the unique biological and physiological characteristics of individuals to establish their identity. This paper reviews and scrutinizes the current biometrics systems used in the field of security in terms of usability, techniques, accuracy, advantages, and disadvantages. However, due to the diverse ...
Abstract—Authentication plays a significant part in dealing with security in public and private sectors such as healthcare systems, banking system, transportation system and law and security. Biometric technology has grown quickly recently, especially in the areas of artificial intelligence and identity. Formerly, authentication process has ...
I noticed some biometric research papers of biometric have explored and improved the corpo-ration of machine learning and biometric. Machine learning can greatly improve efficiency and reduce the cost of data collection. Because of the importance of data collection, some papers are directly dedicated to improving data acquisition
Office of Graduate Studies and Research, San José State University, San Jose, CA 95192-0025 USA ... We accept for the purposes of this paper the definition of biometrics from ISO/IEC JTC1 N3385, 16 Sept., 2009, as the "automated recognition of individualsbased on their behavioural and biological characteristics",but recognize
The first four chapters of this report explain much about biometric systems and applications and describe many of the technical, engineering, scientific, and social challenges facing the field. This chapter covers some of the unsolved fundamental problems and research opportunities related to biometric systems, without, however, suggesting that existing systems are not useful or effective. In ...
In order to overcome the difficulty of password management and improve the usability of authentication systems, biometric authentication has been widely studied and has attracted special attention in both academia and industry. Many biometric authentication systems have been researched and developed, especially for mobile devices. However, the existing biometric authentication systems still ...
The research suggests that the proposed algorithm has an accuracy rate of 95.7%, which is comparable to the Gabor-wavelet method at 95.5% [12]. One research paper [34] also explores the potential of deep learning in minutiae pattern recognition by the proposal of minutiae extraction network (MENet). This works on a similar principle as a ...
Research overview and biometric technologies 1 biometric information needed by the system, which is then converted to data that can be stored on a database. For biometrics to be globally adopted there is a need for international standards compatibility. 4. CONCEPTUAL RESEARCH CONTEXT
PDF | On Jan 1, 2019, Sunil Swamilingappa Harakannanavar and others published Comprehensive Study of Biometric Authentication Systems, Challenges and Future Trends | Find, read and cite all the ...
Abstract. Biometric authentication is a way of identifying and authenticating users. In this paper, we explain biometric authentication and its use in identifying users. Biometric authentication ...
5. Discussion and conclusion. This paper presented BDAS, a new biometric authentication system providing a decentralized and distributed authentication based on blockchain. BDAS improves the security and reliability of the existing biometric authentication systems by splitting a biometric template into fragments and managing them based on blockchain mechanism.
Authentication plays a significant part in dealing with security in public and private sectors such as healthcare systems, banking system, transportation system and law and security. Biometric technology has grown quickly recently, especially in the areas of artificial intelligence and identity. Formerly, authentication process has depended on security measures like passcodes, identity fobs ...
The purpose of this study is to identify the key impacts of biometric security applications and ways of minimising the risk liability of individual biometrics profile that would be kept in the database system/server. The term biometrics was derived from the Greek words bio (life) and metric (to measure). The concept of biometrics is dated back ...
Good Alternative . Brain Wave . Biometric Security. This paper presents the different biometric with their limitations and introduces their alternative in form of brain biometric, Breath biometrics, and Tongue biometrics. Brain biometric uses brain wave while breath biometric uses one's breath and tongue biometric uses a tongue's shape and ...
Fingerprint system is a keenly researched area in biometric technologies [9]. It is one of the most well-known biometrics across the globe for personal recognition and identification of ...
An MLB spokesperson told the publication that Go-Ahead Entry got fans into the stadium 68 percent faster than the usual entry methods with physical or smartphone-based tickets. In addition to the Phillies, the Houston Astros, the San Francisco Giants and one other team will have the biometric ticketing system in place by opening day.
Biometric deals with the verification and identification of a person based on behavioural and physiological traits. This article presents recent advances in physiological-based biometric multimodalities, where we focused on finger vein, palm vein, fingerprint, face, lips, iris, and retina-based processing methods. The authors also evaluated the architecture, operational mode, and performance ...