

You're signed out
Sign in to ask questions, follow content, and engage with the Community
- Canvas Student
- Student Guide
How do I submit an online assignment?
- Subscribe to RSS Feed
- Printer Friendly Page
- Report Inappropriate Content
in Student Guide
Note: You can only embed guides in Canvas courses. Embedding on other sites is not supported.
Community Help
View our top guides and resources:.
To participate in the Instructurer Community, you need to sign up or log in:
How to submit an assignment in Google Classroom, or retract a submission, on a computer or mobile device
- You can submit an assignment in Google Classroom under the "Classwork" section on the desktop site or mobile app.
- To submit an assignment in Google Classroom, you must first "View assignment" and then select the "Add or create" option under the "Your work" menu.
- Links and Google Drive attachments, including a document, slide, sheet, drawing, or PDF file, can all be uploaded and submitted in Google Classroom.
- You can upload multiple files, unsubmit assignments, and leave notes for your instructor in Google Classroom.
You've logged in to Google Classroom , have joined a class, and accessed class materials. Now, it's time to submit an assignment.
To submit an assignment in Google Classroom, you'll first need to navigate to the "Classwork" section. You can then find your assignment and attach your work.
From there, it's as easy as turning it in. Google Classroom also allows users to unsubmit their assignments if you need to make changes or leave a private comment for a teacher about the status of your work.
It's important to note that if you don't click "Turn in" after you attach your work, it won't be submitted. To verify the status of your assignment, double-check to see if it is labeled as "Turned in."
When submitting assignments to Google Classroom on mobile, you'll also need to make sure you have the iPhone or Android app installed. You can search and download Google Classroom through the app store on your phone.
Here's how to submit an assignment on Google Classroom.
How to submit an assignment in Google Classroom on desktop
1. Open your web browser and go to classroom.google.com .
2. Select your class.
3. At the top of your dashboard, choose "Classwork."
4. Click on an assignment, then select "View Assignment."
5. Under "Your Work," choose "Add or Create."
6. From there, click "Google Drive" to attach a document you've already created and saved in your Drive by selecting it from the file window that appears. If you have multiple documents, attach them all this way.
- Note: You can add a link to a Drive document or attach a file from your computer. You may also start an assignment here by creating a new document, slide, sheet, or drawing on this page.
7. To leave a private comment for your teacher, enter it in the appropriately labeled text box on the right. Then click the small triangular "paper airplane" icon to post it.
8. Next, click "Turn in" or "Mark as done" to confirm your submission and change the assignment status to "Turned in."
- Note: If your teacher has assigned a collaborative document that you worked on or another kind of outside assignment, you may see "Mark as done" instead of "Turn in."
How to unsubmit an assignment in Google Classroom on desktop
If you've submitted a document, but find that you need to edit out errors or add in missing content, Google Classroom offers a way to retract your submission. Navigate to the page you turned your assignment in, click "Unsubmit," and confirm. You can always turn it in again by following the above steps.
How to submit an assignment in Google Classroom on the mobile app
1. Open the Google Classroom app on your device.
2. Tap on your class.
3. Choose "Classwork" from the bottom of the app screen.
4. Select the assignment and expand the "Your work" card.
5. Tap "Add attachment" in the "Your work" card.
6. From there, click "Drive" to attach a document you've already created in Drive.
7. Tap "Turn in" or "Mark as done" and re-confirm.
How to unsubmit an assignment in Google Classroom on iPhone or Android
If you turned in the wrong thing or need to go back and add something to the assignment, you can unsubmit it. Navigate to the assignment, expand the "Your work" card, tap "Unsubmit," and confirm. You can always turn it in again the same way you did first.
Related coverage from Tech Reference :
How to create a google classroom on a computer or mobile device, how to log in to google classroom and access your course materials on a computer or mobile device, how to join a google classroom meeting from a link or code on any device, how to find your google classroom code on the desktop website or mobile app, so you can share it with your students, how to leave a google classroom on any device and unenroll yourself from the course.
On February 28, Axel Springer, Business Insider's parent company, joined 31 other media groups and filed a $2.3 billion suit against Google in Dutch court, alleging losses suffered due to the company's advertising practices.
Watch: Veterinarians debunk 15 dog myths
- Main content
Submit to an assignment
Preparing to submit.
To submit a paper to an assignment on Turnitin, the user must log in and upload a file to an existing assignment.
Assignments in Turnitin cannot accept student submissions until the assignment start date and time has passed.
Assignments may also reject submissions after the due date and time set by the instructor.
To check the start date and due date information, either click on the name of the assignment in the class portfolio page or view the start and due dates located under the assignment name.
This action opens a pop-up window showing assignment preference information, including start and due dates/times as well as other assignment information or special instructions.
Log in to turnitin.com (or turnitinuk.com if you're in the UK).
See our logging in guide if you can't quite remember how to log in to Turnitin.
Once you've logged in, you should see your homepage listing the classes you enrolled in .
Select the name of the class where you'd like to upload a file.
This will take you to your Class Homepage for that class.
Select the Open button to the right of the assignment name.
This will take you to the file submission page.
Uploading a submission
Before you proceed, we advise checking that the file you'd like to submit will be accepted. Check out the accepted file types and sizes before you begin.
Only a single file may be submitted to a Turnitin assignment. Any second or subsequent submission will overwrite the original submission in this assignment. Contact your instructor if there is more than one file that must be submitted to complete the directions given by your instructor; additional assignments may be created or you may need to combine multiple documents into a single file of an acceptable file type to be uploaded into Turnitin.
Before you submit you will be able to check the assignment details by selecting the assignment title bar.

To submit, select Upload Submission .
The ‘Submit File’ screen allows you to submit your paper to the assignment in three different ways.
Upload Submission
The Upload Submission method allows you to upload a file directly to Turnitin.

Select the Browse button, or drag your file directly onto the modal.
Make sure that you are uploading an allowed file type .
Once you are happy with your selected file for submission, select Upload and Review .
The Text Input method allows you to submit just the text of your assignment directly to Turnitin.

Enter or paste your submission title into the Submission Title field and then enter or paste your submission text into the Submission Text field.
Once you are happy with the text of your submission, select Upload and Review .
Cloud Submission
The Cloud Submission method allows you to submit from a cloud drive.

Select the Cloud Submissio n tab to open the cloud drive dropdown.
Select the cloud drive that contains the file you want to submit.
Select your file within the cloud drive.
Review and submit
Before you submit you will have an opportunity to check that the file you are about to submit is correct.
If resubmissions are not enabled for this assignment, you may not be able to resolve any incorrect submissions.

If you are happy with the file, select Submit to Turnitin to submit your assignment.
You will see a submission complete notice if your submission was successful. Please don't leave the submission process until you have seen this notice.

If resubmissions are allowed for the assignment and you need to resubmit your paper, you can click the resubmission icon. If you resubmit an edited paper, it will not compare to the first submission you made (i.e. you will not match the text to the previous submission resulting in a 90% match score).
After the submission has completed, a digital receipt is displayed in your browser window. A copy is also sent via email. It is important to use a valid email address to receive this copy of the digital receipt. Save the receipt and the submission ID it contains, as this is proof of a completed submission. If the digital receipt is not shown on screen after submission, return to the class portfolio page and view the assignment to ensure the paper submission completed correctly. Submissions can be checked and viewed by clicking on the title of the paper under the title column to the right of the assignment name.
Was this page helpful?
We're sorry to hear that., need to contact a human.

- Turnitin.com
- Release Notes
- Known Issues
- Privacy and Security
- System Status
for Education
- Google Classroom
- Google Workspace Admin
- Google Cloud
Easily distribute, analyze, and grade student work with Assignments for your LMS
Assignments is an application for your learning management system (LMS). It helps educators save time grading and guides students to turn in their best work with originality reports — all through the collaborative power of Google Workspace for Education.
- Get started
- Explore originality reports
Bring your favorite tools together within your LMS
Make Google Docs and Google Drive compatible with your LMS
Simplify assignment management with user-friendly Google Workspace productivity tools
Built with the latest Learning Tools Interoperability (LTI) standards for robust security and easy installation in your LMS
Save time distributing and grading classwork
Distribute personalized copies of Google Drive templates and worksheets to students
Grade consistently and transparently with rubrics integrated into student work
Add rich feedback faster using the customizable comment bank
Examine student work to ensure authenticity
Compare student work against hundreds of billions of web pages and over 40 million books with originality reports
Make student-to-student comparisons on your domain-owned repository of past submissions when you sign up for the Teaching and Learning Upgrade or Google Workspace for Education Plus
Allow students to scan their own work for recommended citations up to three times
Trust in high security standards
Protect student privacy — data is owned and managed solely by you and your students
Provide an ad-free experience for all your users
Compatible with LTI version 1.1 or higher and meets rigorous compliance standards
Product demos
Experience google workspace for education in action. explore premium features in detail via step-by-step demos to get a feel for how they work in the classroom..
“Assignments enable faculty to save time on the mundane parts of grading and...spend more time on providing more personalized and relevant feedback to students.” Benjamin Hommerding , Technology Innovationist, St. Norbert College
Classroom users get the best of Assignments built-in
Find all of the same features of Assignments in your existing Classroom environment
- Learn more about Classroom
Explore resources to get up and running
Discover helpful resources to get up to speed on using Assignments and find answers to commonly asked questions.
- Visit Help Center
Get a quick overview of Assignments to help Educators learn how they can use it in their classrooms.
- Download overview
Get started guide
Start using Assignments in your courses with this step-by-step guide for instructors.
- Download guide
Teacher Center Assignments resources
Find educator tools and resources to get started with Assignments.
- Visit Teacher Center
How to use Assignments within your LMS
Watch this brief video on how Educators can use Assignments.
- Watch video
Turn on Assignments in your LMS
Contact your institution’s administrator to turn on Assignments within your LMS.
- Admin setup
Explore a suite of tools for your classroom with Google Workspace for Education
You're now viewing content for a different region..
For content more relevant to your region, we suggest:
Sign up here for updates, insights, resources, and more.
How To Write an Email For Submission Of Assignment
Welcome to this informative article that will guide you on how to write an effective email for the submission of your assignment. If you’re unsure about how to draft an email for submitting your assignment, this article is here to help you!
Table of Contents
What To Do Before Writing the Email
Before you start writing the actual email, it’s important to take a few preparatory steps to ensure that your email is clear, concise, and professional:
- Gather all necessary information related to your assignment, such as the due date, submission guidelines, and any specific instructions given by your instructor.
- Review your assignment to ensure it meets the requirements and makes sense.
- If your instructor has provided a specific email address or subject line to use, make note of it.
- Consider attaching your assignment in the appropriate format if required.
What to Include In the Email
When composing your email for assignment submission, it’s important to include the following parts:
Subject Line
Choose a subject line that clearly indicates the purpose of your email. For example, “Assignment Submission – [Course Name]”. This helps the recipient identify the email’s content quickly.
Begin your email with a polite and professional greeting, such as “Dear Professor [Last Name],” or “Hi [Instructor’s Name],”. Use the appropriate salutation based on your relationship with the recipient.
Introduction
Introduce yourself briefly and mention the course or assignment you are submitting. This provides context for the recipient.
In the body of the email, mention any relevant details or specific instructions provided by your instructor. Clearly state that you are submitting your assignment and acknowledge the due date. If there are any additional comments or questions related to the assignment, include them here.
End your email with a courteous closing, such as “Thank you,” or “Best regards,” followed by your full name and contact information. This shows professionalism and makes it easy for the recipient to respond if necessary.
Email Template – Assignment Submission
Subject: Assignment Submission – [Course Name] Dear Professor/Instructor [Last Name], I hope this email finds you well. I am writing to submit my assignment for the [Course Name]. The assignment is attached in the required format. I have completed the assignment as per the given guidelines and it is ready for submission. The due date for the assignment is [Due Date]. If you have any further instructions or clarifications, please let me know. Thank you for your time and consideration. I look forward to hearing from you soon. Best regards, [Your Full Name] [Your Contact Information]
Writing an effective email for the submission of an assignment is essential to ensure clarity and professionalism. By following the steps outlined in this article, you can confidently compose your email and increase the likelihood of a positive response. Remember to always be polite, concise, and include all necessary information. Good luck with your assignment!
Additional tips:
- Double-check all the information before sending the email to avoid any errors or omissions.
- Use a professional email address and avoid using casual or inappropriate language.
- If there is a specific email format recommended by your institution, consult it for guidance.

Due: Sat May 25 11:59 pm Late submissions accepted until Sun May 26 11:59 pm
Assignment by Michael Chang & Julie Zelenski idea originated by Randal Bryant & David O'Hallaron (CMU). Modifications by Nick Troccoli, Brynne Hurst, Kathleen Creel and Jonathan Kula.
Learning Goals
This assignment focuses on understanding assembly code representations of programs. You will be building your skills with:
- reading and tracing assembly code
- understanding how data access, control structures, and function calls translate between C and assembly
- reverse-engineering
- understanding the challenges of writing secure and robust systems
- understanding privacy, trust, and the role of the ethical penetration tester
- mastering the gdb debugger!
You have been hired as a security expert for Stanford Bank (a fictional on-campus bank). They need you to investigate reports of infiltration and security issues and replicate the issues so that they can fix them.
There are three parts to this assignment, each of which can be completed independently:
- an ATM withdrawal program containing some vulnerabilities - you'll need to use your C and assembly skills to find and demonstrate how to exploit these vulnerabilities.
- A dataset that you will use to deanonymize bank users.
- The SecureVault program, a new product designed by the bank to provide increased security to the master vault. You'll be given an executable of the SecureVault program (no C code provided!) to show that it is possible to reverse engineer this program and break into the master vault without being told the passwords.
These problems are like C/assembly "puzzles" to solve, and we hope you enjoy solving them and exploring this material as much as we enjoyed creating them!
Note: check out our assignment overview video on Canvas ; it goes over the different parts of the assignment, what to expect, and tips and tricks! Note the overview video is from this quarter last year, but the assignment is the same (save for the fact that questions 2 and 3 are exchanged).
Spring 2024: Lecture 21 (Fri 5/17) is necessary to work on questions 3 and 4 in part 2 of this assignment.
A few reminders:
- The working on assignments page contains info about the assignment process.
- The collaboration policy page outlines permitted assignment collaboration, emphasizing that you are to do your own independent thinking, design, writing, and debugging. Even without any code being submitted, you should not be doing any joint debugging/development, sharing or copying written answers, sharing specific details about SecureVault behavior, etc. If you are having trouble completing the assignment on your own, please reach out to the course staff; we are here to help!
To get started on this assignment, clone the starter project using the command
View Full Starter File List
- vault : Your SecureVault executable program, custom-generated for each student.
- custom_tests : The file where you will add custom tests to reproduce vulnerabilities in the provided ATM withdrawal program.
- input.txt : A blank text file where you should add the passwords for each SecureVault level, one per line. See the section on SecureVault for more information.
- readme.txt : A file where you should add answers to short written questions for all three parts of the assignment.
- .gdbinit : A gdb configuration file you can optionally use to run certain gdb commands each time gdb launches. See the section on using GDB in SecureVault for more information.
- samples : A symbolic link to the shared directory for this assignment. It contains:
- atm : The executable ATM program, which you will explore for vulnerabilities.
- atm.c : The C source code for the ATM program, which you will explore for vulnerabilities. Note that you're not able to edit or recompile this code/executable.
- checkins.csv : A file containing public social media location check-in data for various locations on Stanford campus over the past three months.
- search_checkins : An executable program to search the check-in data.
- bank : a folder containing the following:
- customers.db : A file with the list of all users and balances for the ATM program.
- transactions.csv : A file with ATM transaction information from the past three months at the Stanford campus ATM.
- SANITY.INI and sanity.py : Files to configure and run sanity check. You can ignore these files.
- wordlist : A list of dictionary words used for SecureVault.
- tools : Contains symbolic links to the sanitycheck and submit programs for testing and submitting your work. ( codecheck is not needed on this assignment)
You will be using gdb frequently on this assignment. Here are essential resources as you work - note that you should make sure you have downloaded the CS107 GDB configuration file mentioned in the Getting Started Guide if you didn't previously do so.
Open Getting Started Guide Open GDB Guide Open Lab5 GDB Tips Open Lab6 GDB Tips
1. ATM Security
Stanford Bank recently updated the ATM software to a version with some additional features. The IT team reviewed the new code and thought it all looked good, but having now installed it in production, they are observing some suspicious activity. The bank has called you because your superior C and assembly skills are just what's needed to investigate and resolve these problems!
In the samples folder, they have provided you the code ( atm.c ) and compiled executable ( atm ), which you can examine/run but cannot recompile or edit (since they want to ensure you work with the same executable installed on the ATMs themselves). The ATM program is invoked with an amount and the credentials for a particular account. If the credential is authorized and the account has sufficient funds, the amount is withdrawn and dispersed in cash. Accounts must maintain a minimum balance of $50, and the ATM is supposed to maintain bank security by rejecting unauthorized access. Every time you run the program, it will print out information to the terminal about the transaction that took place, or the error that occurred, if any. For example, if you ask to withdraw $100 from your account balance of $107, it should be denied with an error message because that would bring your current $107 balance below the required minimum of $50. If you try to sneak cash from another account or use a fake name, your credential should get rejected as unauthorized.
Here are a few examples - try it out yourself! Note that $USER automatically acts as your SUNET ID, and every account balance is set to be $107. Also, each time you run the program anew, all balances return to their original starting levels. No money actually changes hands in this ATM, which is a blessing given its security flaws.
Expand ATM Sample Runs
The bank has identified three anomalies in the ATM program behavior that they need your help investigating. For each of the anomalies (a), (b), and (c) below, you will need to do the following:
- include a test case in your custom_tests file to showcase how to reproduce the vulnerability. Note that there may be more than one way to trigger a vulnerability.
- A concise description of the underlying defect in the code.
- An explanation of exactly how you constructed your test case to exploit it.
- Your recommendation for fixing it. The bank is not looking for a major rewrite/redesign, so in your proposed changes you should directly address the vulnerability with minimal other disruption. Note that there may be more than one possible remedy for fixing each issue. Also make sure you do not remove intended functionality of the bank program, and account for any potential additional security issues introduced by your proposed fix .
NOTE: when running your own custom tests, make sure to inspect the output to ensure your tests are causing the behavior you expect! The sanitycheck tool itself does not verify that the tests cause the specified exploits.
As you work through your investigation, you will need to review the source code for the atm program. The program is roughly 175 lines of C code of similar complexity to what you have been writing this quarter, and is decomposed and fairly readable, though sorely lacking in comments. You should find that the program's approach seems reasonable and the code is sincere in its attempt to operate correctly. As you're reading, take a minute to reflect on how far your awesome C skills have come to let you read through this provided program!
NOTE: when running the ATM program under GDB, make sure you are in the samples folder first before running gdb atm .
a) Negative Balances
A prior version of the ATM program restricted a withdrawal to be at most the full account balance, allowing the customer to drain their account to $0, but no further. The current version has changed the withdraw function to require a non-zero minimum balance. The expected behavior should be that all account balances stay above this minimum. However, the bank saw an (otherwise ordinary) withdrawal transaction that not only caused an account to go below the minimum, but also overdrew so far as to end up with a negative balance. Oops, that's definitely not supposed to happen! Review the C code for the withdraw function, specifically the changes from the old version. It seems to work in many cases, but apparently not all. Read carefully through this function to try and discover the flaw - your understanding of signed and unsigned integers will be useful here! Once you have found the vulnerability, determine a command to make a withdrawal as yourself that withdraws more money than is present in your account . Put this command in custom_tests , and answer the specified readme questions.
b) Unauthorized Account Access
The bank has also received a customer complaint about an unauthorized withdrawal from their account. It seems that another user with different credentials was able to successfully withdraw money from the aggrieved customer's account. Moreover, the credential used appears to be entirely fake - no such user exists in the database! A user should not be able to access a different customer's account and especially not by supplying a bogus credential! Review the C code for the find_account function that is responsible for matching the provided username to their account number. It seems to work properly when the username matches an existing account, but not when the username doesn't match an existing account. Trace through line by line how the function executes when called with an invalid username that is not in the database. What lines are executed? Once you do this, you'll find that the function appears to behave unpredictably. Your next task is to examine the generated assembly to determine precisely how the function will behave - your understanding of the %rax / %eax register will be useful here! Once you have found the vulnerability, determine a command with a designed bogus name credential to withdraw $40 from one of the CS107 staff member's accounts. Put this command in custom_tests , and answer the specified readme questions. (The samples/bank/customers.db file contains information about all valid users and their balances, and the first 15 users in the database are staff accounts.)
c) Accessing The Master Vault
The most worrisome issue is repeated illicit withdrawals from the master vault account, account number 0. The name on the master account is not an actual user, so this account cannot be accessed using the simple username-based credential. Instead, the user must specify two account arguments, the account's number and its secret passcode, as a form of heightened security, like this:
At first the bank thought the vault passcode had been leaked, but changing the passcode did nothing to thwart the attack. In a fit of desperation, the bank removed the vault passcode file altogether, figuring this would disable all access to the vault, yet the rogue user continues to make withdrawals from it! It seems that the high-security passcode authentication may have its own security flaw! The code that handles this authentication is in the lookup_by_number and read_secret_passcode functions. These functions work correctly in many situations, but fail in certain edge cases. Remember that it seems that in certain cases supplied credentials are accepted despite the lack of a saved passcode file . The vulnerability is subtle in the C code, so you should also use GDB to examine the code at the assembly level and diagram out the memory on the stack for these functions . This problem is similar to the stack diagramming/exploit problem from lab6 - revisit that problem if you need a refresher! Your exploit should not involve reading from any file. Once you have found the vulnerability, determine a command to withdraw $300 from the bank vault despite its disabled passcode . Put this command in custom_tests , and answer the specified readme questions.
2. Dataset Aggregation
Separate from the faulty ATM software, Stanford Bank believes that someone was able to gain access to their account logs and get a list of ATM transaction information for their Stanford campus ATM. The company believes that this poses little threat because the transaction logs have limited recorded data. However, you are concerned that this data can be combined with other available data in dangerous ways, such as to learn private information. For instance, knowing someone's history of large (or small) transactions might tell you about their financial situation; knowing memberships in clubs or organizations might tell you about social relationships and webs of networks. Your task is to combine this data with another dataset you have found of public location check-ins to show the harms of a potential data breach. To aid in investigating your concerns, the bank has made the ATM transaction data available to you in the samples/bank/transactions.csv file. This file has one account transaction per line, and each transaction occurred at the Stanford campus ATM. Each line has the following format:
For example, here is one line from the file that represents a withdrawal of $15 on 2/15/21 at 4:54PM:
Transactions with the same account identifier are guaranteed to be for the same bank account, but the identifier doesn't give any information about whose account it is (intentionally done by the bank to obfuscate the data).
You have already downloaded a publicly-available location checkins dataset from an online social network, in the file samples/checkins.csv . It is too large to read through manually, so you also already created a program search_checkins that displays that checkin data and lets you search through it more easily. Run the program ( samples/search_checkins ) for instructions on how to use it.
Show the risks of dataset aggregation and express your concerns to the bank managers by answering the following questions in your readme.txt . Note that you are not expected to create any additional programs to parse or otherwise process these datasets with code - the intent is for you to skim the transactions.csv file by hand and use it along with the search_checkins program to answer the following questions.
- a) The likely user who made multiple large transactions?
- b) Two (there may be more, but you must identify only two) likely members of the Stanford SecurityStars Club, which has a club meeting on the 15th of each month where people must bring $15 to pay their membership dues? (Assume they are procrastinators in withdrawing the money)
- How were you able to de-anonymize the transactions data?
- Beyond encrypting the data, what recommendations would you give to Stanford Bank to further anonymize or obfuscate the account data in the case of accidental data breaches?
- Use one or more of the four models of privacy discussed in lecture to explain why disclosure of the information that can be aggregated here is (or is not) a violation of privacy.
3. SecureVault
Stanford Bank is rolling out a new tool, SecureVault, to provide increased security at the master vault at each of their branches. Employees must enter four secret passwords into this program to gain access to the master vault. For extra security, the bank creates a different SecureVault program for each branch with different expected passwords; the bank headquarters does not give the source code to any of the branches; and the program triggers an alarm that notifies the central system each time an incorrect password is entered. They are confident that this means only someone who is told the password can get access, and any potential intruders will be detected by the alarm system. They have hired you to test this. Your task is to show that you can reverse engineer the program to gain access to the bank vault without being told the password, and without alerting central security.
Do not start by running SecureVault and entering passwords to "see what will happen" . You will quickly learn that what happens is the alarm goes off and it deducts points :-) When started, SecureVault waits for input and when you enter the wrong password, it will raise the alarm and notify the central system, deducting points. Thoroughly read the SecureVault information below before attempting to enter any passwords! There is a lot of information below, but it is included to help provide useful tips for you to work through this part of the assignment.
Without the original source code, all you know is that SecureVault has four "levels" of security, each with a different password. If the user enters the correct password, it deactivates the level and the program proceeds on. But given the wrong input, SecureVault raises an alarm by printing a message, alerting central security and terminating. To reach the master vault, one needs to successfully disarm each of its levels.
This is where the bank needs your help. Each of you is assigned a different generated SecureVault executable unique to you, generated just as they would be for each bank branch. Your mission is to apply your best assembly detective skills to reverse engineer the SecureVault executable to work out the input required to pass each level and reach the master vault, thus proving the insecurity of the bank's approach.
Specifically, you must fill in your input.txt file with the passwords to defuse each level in order, 1 per line, for each level you have solved. You must also answer the following questions in your readme.txt file. Make sure to verify your input.txt file (with appropriate protections!) to ensure proper formatting and that all lines are entered correctly before submitting! We will test by running ./vault input.txt on your submission, using the original SecureVault program generated for you. Here are the readme questions to work through as you go:
- What tactics did you use to suppress/avoid/disable alarms?
- level_1 contains an instruction near the start of the form mov $<multi-digit-hex-value>,%edi . Explain how this instruction fits into the operation of level_1 . What is this hex value and for what purpose is it being moved? Why can this instruction reference %edi instead of the full %rdi register?
- level_2 contains a jg that is not immediately preceded by a cmp or test instruction. Explain how a branch instruction operates when not immediately preceded by a cmp or test . Under what conditions is this particular jg branch taken?
- Explain how the loop in the winky function of level_3 is exited.
- Explain how the mycmp function is used in level_4 . What type of data is being compared and what ordering does it apply?
- How would you describe Stanford Bank’s trust model? (In other words: who among the bank headquarters, the bank branches, and you was trusted?) Justify your answer.
SecureVault Information
From the SecureVault assembly, you will work backwards to construct a picture of the original C source in a process known as reverse-engineering . Note that you don't necessarily need to recreate the entire C source; your goal is to work out a correct input to pass the level. This requires a fairly complete exploration of the code path you follow to deactivate the level, but any code outside that path can be investigated on a need-to-know basis. Once you understand what makes your SecureVault program "tick", you can supply each level with the password it requires to disarm it. The levels get progressively more complex, but the expertise you gain as you move up from each level increases as well. One confounding factor is that SecureVault raises an alarm whenever it is given invalid input. Each time the alarm goes off (except for a free pass the first time), it notifies central security (the CS107 staff) and points are deducted from your score. Thus, there are consequences to setting off the alarm -- you must be careful!
The bank has confirmed to you a few things about how the SecureVault programs operate:
- If you start SecureVault with no command-line argument, it reads input typed at the console.
If you give an argument to SecureVault, such as input.txt :
SecureVault will read all lines from that file and then switch over to reading from the console. This feature allows you to store inputs for solved levels in input.txt and avoid retyping them each time.
Alarms can be triggered when executing at the shell or within gdb. However, gdb offers you tools you can use to intercept the alarms, so your safest choice is to work under gdb and employ preventive measures.
- It is not possible to know for sure whether the central system (course staff) is notified about an alarm. You must use your investigative skills and best defensive measures!
- The central system will give you a free pass (no point deduction) the first time they are notified about an alarm.
- The SecureVault program in your repository was lovingly created just for you and is unique to your id. It is said that it can detect if an impostor attempts to run it and won't play along.
- The SecureVault program is designed for the myth computers (running on the console or logged in remotely). There is a rumor that it will refuse to run anywhere else.
- It seems as though the function names were left visible in the object code, with no effort to disguise them. Thus, a function name of initialize_vault or read_five_numbers can be a clue. Similarly, it seems to use the standard C library functions, so if you encounter a call to qsort or sscanf , it is the real deal.
- There is one important restriction: Do not use brute force! You could write a program to try every possible input to find a solution. But this is trouble because a) you lose points on each incorrect guess which raises an alarm, b) trying all possible inputs will take an eternity and risk saturating the network, and c) part of your submission requires answering questions that show you understanding of the assembly code, which guessing will not provide :)
Using tools such as gdb , objdump and new tools nm and strings is critical to effectively investigating and disarming each level. Once you are familiar with the tools at your disposal, first work to reliably prevent alarms from triggering , then proceed with disarming each of the levels .
Step 1: Familiarity with Tools
Here are some helpful tools to gather general information:
- nm : use the nm utility ( nm vault ) to print what's called the "symbol table" of the executable, which contains the names of functions and global variables and their addresses. The names may give you a sense of the structure of the SecureVault program.
- strings : use the strings utility ( strings vault ) to print all the printable strings contained in the executable, including string constants. See if any of these strings seem relevant in determining the passwords.
- gdb lets you single-step by assembly instruction, examine (and change!) memory and registers, view the runtime stack, disassemble the object code, set breakpoints, and more. Live experimentation on the executing SecureVault program is the most direct way to become familiar in what's happening at the assembly level.
- Compiler Explorer : pull up tools like the Compiler Explorer interactive website from lab, or gcc on myth , to compile and explore the assembly translation of any code you'd like. For example, if you're unsure how to a particular C construct translates to assembly, how to access a certain kind of data, how break works in assembly, or how a function pointer is invoked by qsort , write a C program with the code in question and trace through its disassembly. Since you yourself wrote the test program, you also don't have to fear it setting off any alarms :-) You can compile directly on myth using a copy of a Makefile from any CS107 assignment/lab as a starting point, and then use gdb or objdump to poke around.
GDB Suggestions
GDB is absolutely invaluable on this assignment. Here are some suggestions on how to maximize your use of gdb in addition to the tips in lab5 and lab6 :
- Expand your gdb repertoire. The labs have introduced you to handy commands such as break , x , print , info , disassemble , display , watch , and stepi/nexti . Here are some additional commands that you might find similarly useful: jump , kill , and return . Within gdb, you can use help name-of-command to get more details about any gdb command. See the quick gdb reference card for a summary of many other neat gdb features.
Get fancy with your breakpoints. You can breakpoints by function name, source line, or address of a specific instruction. Use commands to specify a list of commands to be automatically executed whenever a given breakpoint is hit. These commands might print a variable, dump the stack, jump to a different instruction, change values in memory, return early from a function, and so on. Breakpoint commands are particularly useful for installing actions you intend to be automatically and infallibly completed when arriving at a certain place in the code. (hint!)
gdb kill workaround : gdb 9.2 (current version on myth as of 04/2021) has a bug when attempting to use kill in the commands sequence for a breakpoint that creates a cascade of problems --can cause gdb itself to crash or hang. The gdb command signal SIGKILL can be used as an alternate means to kill a program from a commands sequence that doesn't trip this bug.
Use a .gdbinit file . The provided file named .gdbinit in the assignment folder can be used to set a startup sequence for gdb. In this text file, you enter a sequence of commands exactly as you would type them to the gdb command prompt. Upon starting, gdb will automatically execute the commands from it. This will be a convenient place to put gdb commands to execute every time you start the debugger. Hint: wouldn't this be useful for creating breakpoints with commands that you want to be sure are always in place when running the SecureVault program? The .gdbinit file we give you in the starter repo has only one command to echo Successfully executing commands from .gdbinit in current directory . If you see this message when you start gdb, it confirms the .gdbinit file has been loaded. If you see an error message about auto-loading .gdbinit being declined when starting gdb, this means you haven't installed the CS107 GDB configuration file - see the top of this page for instructions.
- Custom gdb commands . Use define to add your own gdb "macros" for often-repeated command sequences. You can add defines to your .gdbinit file so you have access to them in subsequent gdb sessions as well.
- Fire up tui mode (maybe...). The command layout asm followed by layout reg will give you a split window showing disassembly and register values. This layout will display current values for all registers in the upper pane, the sequence of assembly instructions in the middle pane, and your gdb command line at the bottom. As you single-step with si , the register values will update automatically (those values that changed are highlighted) and the middle pane will follow instruction control flow. This is a super-convenient view of what is happening at the machine level, but sadly, you have to endure a number of quirks and bugs to use it. The tui mode can occasionally crash gdb itself, killing off gdb and possibly the SecureVault program while it's at it. Even when tui is seemingly working, the display has a habit of turning wonky, often fixable by the refresh command (use this early and often!) but not always. A garbled display could cause you to misunderstand the program state, misidentify where your SecureVault is currently executing, or accidentally execute a gdb command you didn't intend. Any alarm suppression mechanism that requires you, the fallible human, to take the right action at a critical time could easily be waylaid by interference, so don't attempt tui before you have invincible automatic protection against alarms. Selective use of auto-display expressions (introduced in lab6) is a great alternative with less disruption. You can exit tui using ctrl-x a and re-enter it again (this doesn't require leaving gdb and losing all your state).
Step 2: General Investigation and Preventing Alarms
Once you are familiar with the tools at your disposal, your next step is to gather general information about how the SecureVault program works to figure out how to reliably prevent alarms from triggering . There are simple manual blocks that give some measure of protection, but it is best to go further to develop an invincible guard. Feel free to use any technique at your disposal, such as leveraging gdb features, tweaking the global program state, modifying your setup, tricking the SecureVault program into running in a safe manner, etc. Avoiding the alarm entirely is one straightforward approach to ensure that we won't hear about it, but there are ways to selectively disable just the transmission portion to the central system (course staff) . Once you figure how to set up appropriate protection against alarms, you will then be free to experiment with the levels without worry. Note that the program can only trigger an alarm when it is "live", i.e., executing in shell or running with gdb .
Step 3: Disarming Levels
Your next task is to approach each level individually to figure out a password that disarms it. There may be more than one password for each level; your task is to enter your 4 passwords, one per line, starting with level 1, into your input.txt file. Here are key tips for how to approach your reverse engineering exploration:
- Run the program live in GDB (with appropriate alarm protections!) and step through to better understand its behavior. Reading and diagramming the assembly by hand is useful to an extent, but quickly becomes infeasible with larger programs.
- Break the assembly into chunks. For instance, if it calls any functions, that's a good stopping point to orient yourself and understand the assembly just up to that point.
- Use gdb to verify your hypotheses. Verify key assumptions you make about the vault behavior to ensure you're on the right track. One helpful trick is you can change register contents while running gdb. E.g. if you think "I believe if %rdi stored this, it would do that", then try it! You can do p $rdi = val to change register contents mid-program. Or if you think something is a char * , cast and print it out, e.g. p (char *)$rdi .
- Document your knowns and unknowns. If you run into a situation where you are stuck due to seemingly-conflicting assumptions, document them and re-verify them. If you have multiple conflicting assumptions, at least one must not be the case.
- Use compiler explorer to see what code looks like in assembly. If you think you happened upon e.g. a loop, if statement, etc. try using compiler explorer to type in some code quickly and see what that code looks like in assembly. If it resembles the assembly you're seeing, perhaps that can help you better understand its structure.
- Use library functions to your advantage. If you spot a call to what looks like a library function, it's the real deal. Use the man page for that function to learn about what parameters it takes in, what it does, and what it returns. This can give you key information about the types of data in different registers - e.g. if you see a call to strlen , then the value put into %rdi must be of type char * , and what's stored in %rax afterwards must be a size_t string length.
- When tracing an unknown function, before dissecting its behavior first learn about the input/output of the function and what role it plays. Does it return anything? What parameters does it take in? If it has a return value, is it checked to be something in particular? Going into a function with an idea of what must be returned for you to continue with the vault can help you focus on understanding how to achieve that.
Sanity Check
The default sanitycheck test cases are ATM inputs and one test case that reports the line count of your input.txt file. This sanitycheck is configured to only allow test cases for ATM in your custom_tests file. The SecureVault executable is not run by sanitycheck.
Once you are finished working and have saved all your changes, check out the guide to working on assignments for how to submit your work. We recommend you do a trial submit in advance of the deadline to allow time to work through any snags. You may submit as many times as you would like; we will grade the latest submission. Submitting a stable but unpolished/unfinished version is like an insurance policy. If the unexpected happens and you miss the deadline to submit your final version, this previous submit will earn points. Without a submission, we cannot grade your work.
We would also appreciate if you filled out this homework survey to tell us what you think once you submit. We appreciate your feedback!
For this assignment, here is a tentative point breakdown (out of 119):
- custom_tests (24 points) Each successful attack test case earns 8 points. We will test by running tools/sanitycheck custom_tests on your submission. Your custom_tests should contain 3 test cases, one for each ATM attack.
- readme.txt (55 points) The written questions will be graded on the understanding of the issues demonstrated by your answers and the thoroughness and correctness of your conclusions.
- Input.txt (40 points) Each SecureVault level you have solved earns 10 points. We will test by running ./vault input.txt on your submission. The input.txt file in your submission should contain one line for each level you have solved, starting from level 1. Malformed entries in your input.txt or wrong line-endings will cause grading failures. To avoid surprises, be sure that you have verified your input.txt in the same way we will in grading (i.e., ./vault input.txt ).
- SecureVault alarms triggered (up to 6 points deducted) Each alarm notification (beyond the first one) that reaches the staff results in a 1 point deduction, capped at 6 points total.
Post-Assignment Check-in
How did the assignment go for you? We encourage you to take a moment to reflect on how far you've come and what new knowledge and skills you have to take forward. Once you finish this assignment, your assembly skills will be unstoppable, and you will have a better understanding of trust, privacy and security! You successfully found vulnerabilities in a program using its source and assembly, and reverse engineered a complex program without having access to its source at all. Rock on!
To help you gauge your progress, for each assignment/lab, we identify some of its takeaways and offer a few thought questions you can use as a self-check on your post-task understanding. If you find the responses don't come easily, it may be a sign a little extra review is warranted. These questions are not to be handed in or graded. You're encouraged to freely discuss these with your peers and course staff to solidify any gaps in you understanding before moving on from a task.
- What are some of the gdb commands that allow re-routing control in an executing program?
- What is the main indication that an assembly passage contains a loop?
- What makes someone a trustworthy fiduciary or guardian of personal data? How and why should an institution like a bank protect the privacy of its customers?
- Explain the difference between a function's return value and its return address.
- Consider the mechanics of function pointer work at the assembly level. How is a call through a function pointer the same/different when compared to an ordinary function call?
- For performance reasons, the compiler prefers storing local variables in registers whenever possible. What are some reasons that force the compiler to store a local variable on the stack instead?
- For the instruction sequence below, what must be true about values of op1 and op2 for the branch to be taken? What changes if ja is substituted for jg ? cmp op1,op2 jg target

Understanding the Life Cycle of an Option Trade
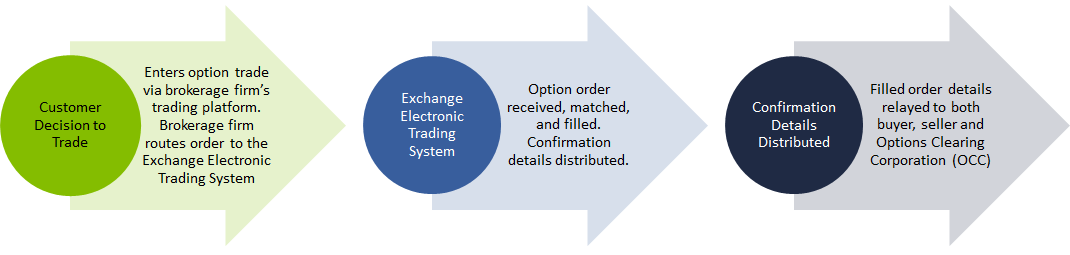
Exercise and Assignment
- Before expiration : An American style option holder has the right to exercise an option before its expiration. Should they choose to do so, an option holder must submit an exercise notice to their brokerage firm along with instructions. These instructions are then relayed to OCC which in turn triggers the assignment process.
- On expiration : OCC administers the automatic exercise process, which occurs when an option contract is a penny or more in-the-money. This procedure is also known as exercise-by-exception, or ex-by-ex. Even when expiring options meet these criteria, the options will not be automatically exercised if contrary instructions are received by OCC.
- Contrary Exercise Advice : A long options holder has the right to exercise as well as the right to not exercise an options contract. This is especially important on an option’s expiration date when the ex-by-ex process is applied. The holder of a long in-the-money (ITM) option at expiration may decide not to exercise whereas the long out-of-the-money (OTM) option holder may decide to exercise their option contract. In either circumstance, a ‘contrary exercise’ notice instructing OCC that the option holder elects not to follow the Ex-by-Ex procedure must be submitted to the OCC by the defined time deadline.
Exercises Notices Generate Assignments

IGNOU June TEE 2024 assignment submission deadline further extended to May 31
The IGNOU June TEE 2024 exam is scheduled to be held from June 7 to July 13, 2024.

Vikas Kumar Pandit | May 17, 2024 | 03:35 PM IST
NEW DELHI: The Indira Gandhi National Open University (IGNOU) has again extended the deadline for submitting assignments for the June 2024 Term-End Examination (TEE) to May 31. The IGNOU June TEE 2024 exams will be held from June 7 to July 13, 2024.
New: IGNOU July 2024 registration link | Click here to download IGNOU June 2024 hall ticket
Latest : IGNOU July 2024 Re-Registration Started | IGNOU result out; Direct link
Click here to submit IGNOU projects/ dissertation/ practical files/ internship reports for June TEE 2024
Earlier, the last date to submit the IGNOU June TEE 2024 assignment was April 30. “With the approval of the Competent Authority, the last date for submission of assignments (both in hard copy and soft copy) for Term End Examinations, June 2024 for both ODL and online programmes, GOAL and EVBB has further been further extended up to 31st May 2024,” said an official notice from IGNOU.
The application process for IGNOU June TEE 2024 exam is underway and candidates can apply for the exam till May 25. Candidates will have to pay a late fee of Rs 1,100 along with the application fee to register for the exam.
During the registration process, candidates should pay a fee of Rs 200 per course for both theory and practical, lab courses. Candidates admitted from January 2023 onwards will be subject to extra charges for practical and project evaluations. These additional fees are Rs 300 per course for up to 4 credits and Rs 500 per course for more than 4 credits.
Also read IGNOU July Admission 2024: Registration begins for online, ODL courses
IGNOU June TEE 2024 Assignment: How to submit
Candidates are required to submit their IGNOU June TEE 2024 assignment in both hard and soft copies. Candidates can follow the steps given below to submit the assignment.
Visit the IGNOU’s official website, ignou.ac.in.
On the homepage, look for the IGNOU assignment submission link.
Now, log in by entering the required details
Submit the assignment and download the assignment submission receipt for future reference.
Follow us for the latest education news on colleges and universities , admission, courses, exams , research, education policies, study abroad and more..
To get in touch, write to us at [email protected] .
Allahabad University PG Admission 2024: PGAT registration begins; apply till June 5
Allahabad University will conduct PGAT 2024 in the third week of June. Aspirants can apply at allduniv.ac.in.
Featured News
- Placements By Branch 2024: Around 40% EE, ECE students at IITs, NITs fail to secure jobs
- ‘No evidence of widespread abuse’: UK panel recommends retaining graduate route visa
- Placements 2024: Even BTech computer science struggles with 60-80% placed in IITs, NITs; AI jobs rise
- ‘Better decision’: Why Karnataka teachers welcome scrapping of the four-year undergraduate programme
- IIT Gandhinagar Placements 2023-24: 59% students yet to be placed
- IIT ISM Dhanbad Placements 2023-2024: 40% students yet to be placed
Latest Education News
Cuet 2024 may 17 live: nta cuet ug day 3 exam concluded; paper analysis, answer key, admit card download link.

NEET UG 2024: SC refuses to grant stay on result declaration over alleged paper leak

CUET UG 2024 Day 3: Exam held in 620 centres; highest attendance in accountancy

Didn't do well in CMAT 2024, what next?

MSDE lays out framework for holistic development of trainers in the skilling ecosystem

Download Our App
Start you preparation journey for JEE / NEET for free today with our APP
New to the Faith
Catholic charities, ways to give, clergy directory.
Phone: 216-696-6525
Toll Free: 1-800-869-6525
Address: 1404 East 9th Street, Cleveland, OH 44114
- Our Bishops
- Our History
- Our Parishes
- Our Schools
- Catholic Directory
- Staff Directory
Share this Page
Clergy assignment changes – May 2024
- News of the Diocese
May 15, 2024

Father Christopher A. Cox concluded his appointment as administrator, St. Anselm Parish, Chesterland and he was appointed pastor, St. Anselm Parish, Chesterland, effective May 11.
Father David A. Stavarz concluded his appointment as parochial vicar, Holy Family Parish, Parma and he was been appointed administrator, Holy Family Parish, Parma, effective June 11.
Father Jozef A. Bozek concluded his appointment as parochial vicar, St. Sebastian Parish, Akron and he was been appointed administrator, St. Barbara Parish, Cleveland, effective June 30.
Father Michael A. Petkosek concluded his appointment as parochial vicar, St. Albert the Great Parish, North Royalton and he was appointed administrator, Mary, Queen of Apostles Parish, Brook Park, effective July 1.
Father Anthony J. Simone concluded his assignment as presbyteral moderator, St. Aloysius-St. Agatha Parish, Cleveland, effective June 30. His appointment as administrator, St. Jerome Parish, Cleveland remains unchanged.
Father Andrew M. Morkunas has been appointed presbyteral moderator, St. Aloysius-St. Agatha Parish, Cleveland, effective July 1. This appointment is in addition to his assignment as Catholic chaplain of University Hospitals (main campus) in Cleveland. His residence remains unchanged.
Father Joseph P. Robinson was transferred from parochial vicar, St. Columbkille Parish, Parma to parochial vicar, Sacred Heart of Jesus Parish, Wadsworth, effective June 11.
Father Patrick R. Schultz was transferred from parochial vicar, Sacred Heart of Jesus Parish, Wadsworth to parochial vicar, St. Luke Parish, Lakewood; parochial vicar, St. Clement Parish, Lakewood; and parochial vicar, St. James Parish, Lakewood, effective June 11.
Father Gregory J. Olszewski concluded his appointment as part-time parochial vicar at St. Joseph Parish, Strongsville and he was appointed parochial vicar of St. Joseph Parish, Strongsville and parochial vicar, St. John Neumann Parish, Strongsville, effective June 11.
Father Robert J. Reidy , senior parochial vicar, Mary, Queen of Apostles Parish, Brook Park s received permission to retire, effective Aug. 11. He also received permission to live in the rectory of St. Colman Parish, Cleveland as a senior priest-retired, effective Aug. 11.
Father Joseph T. Hilinski received permission to live in the rectory of St. Ladislas Parish, Westlake as a senior priest-retired, effective June 30.
Father Kevin M. Liebhardt received permission to live in the rectory of St. Mary Parish, Painesville as a senior priest-retired, effective June 30.
Father Daniel R. Fickes was been granted permission to participate in the sabbatical program at the Pontifical North American College from Sept. 9 to Nov. 22.
Father Stephen M. Spisak was been appointed chaplain of the Knights of Columbus Windermere Council 2726, effective immediately. This appointment is in addition to his assignment as parochial vicar, Communion of Saints Parish, Cleveland Heights.
Father John C. Retar was been appointed chaplain of the Department of Ohio Catholic War Veterans and Auxiliary, effective immediately. This appointment is in addition to his assignment as pastor, St. Vitus Parish, Cleveland.
Father Andrew J. Hoover was been appointed chaplain of the Knights of Columbus St. Anthony of Padua Parma Council 15614, effective immediately. This appointment is in addition to his assignment as administrator, St. Anthony of Padua Parish, Parma.
Deacon Michael F. Garvin , who will be ordained a priest of the Diocese of Cleveland on May 18, was appointed parochial vicar, St. Charles Borromeo Parish, Parma, effective June 11.
Deacon Donald G. Brandt was transferred from permanent deacon, St. Thomas More Parish, Brooklyn to permanent deacon, St. Clarence Parish, North Olmsted, effective June 30.
Deacon Daniel E. Bryan concluded his diaconal assignment at St. Clement Parish, Lakewood and he was granted retirement status as a deacon, effective July 1.
Deacon Robin R. Adair , senior deacon-retired, was appointed spiritual director for the Barberton Fire Department, effective immediately.
Deacon Michael Hayes Jr. , who was ordained a permanent deacon of the Diocese of Cleveland on May 4 was appointed permanent deacon, St. Christopher Parish, Rocky River, effective May 20.
Deacon Edward J. Linsky , who was ordained a permanent deacon of the Diocese of Cleveland on May 4, was appointed permanent deacon, Holy Spirit Parish, Garfield Heights, effective May 20.
Deacon Christopher M. Loxterman , who was ordained a permanent deacon of the Diocese of Cleveland on May 4, was been appointed permanent deacon, St. John Vianney Parish, Mentor, effective May 20.
Deacon Darrel T. Sherman , who was ordained a permanent deacon of the Diocese of Cleveland on May 4, was appointed permanent deacon, St. Peter Parish, North Ridgeville and permanent deacon, St. Julie Billart Parish, North Ridgeville, effective May 20.
Deacon Mark T. Tomecko , who was ordained a permanent deacon of the Diocese of Cleveland on May 4, was appointed permanent deacon, St. Francis Xavier Parish, Medina, effective May 20.
Deacon John L. Zarbo , who was ordained a permanent deacon of the Diocese of Cleveland on May 4, was appointed permanent deacon, St. Anthony of Padua Parish, Fairport Harbor, effective May 20.
Deacon Michael Puhalla , with the permission of Youngstown Bishop David J. Bonnar, was appointed permanent deacon at Holy Trinity Parish, Avon, effective May 15.
Find a parish to call home
Achieve academic excellence.
Subscribe! Sign up to receive news & updates
Notice of Data Security Incident
Child & Youth Protection
Our promise to protect, our pledge to heal.
To report an abuse, please contact local law enforcement and:
Kathleen McComb , Victim Assistance Coordinator
Response Services – 216-334-2999
- Canonical Services
- Catechetical Formation
- Catholic Education
- Clergy & Religious
- Communications
- Facilities Services
- Human Resources
- Mission Office
- Moderator of the Curia
- Parish Life
- Parish Locator
- Parish Directory
- School Locator
- School Directory
- In Remembrance
- Clergy Assignments
- Northeast Ohio Catholic
Diocesan Memo
Accreditation, live stream mass.
Catholic Diocese of Cleveland © 2024
Subscribe! Sign up to receive news & updates.
Photo Gallery

Washington Square News

Students arrested at Gould Plaza required to complete ‘dozens of writing assignments,’ faculty group says
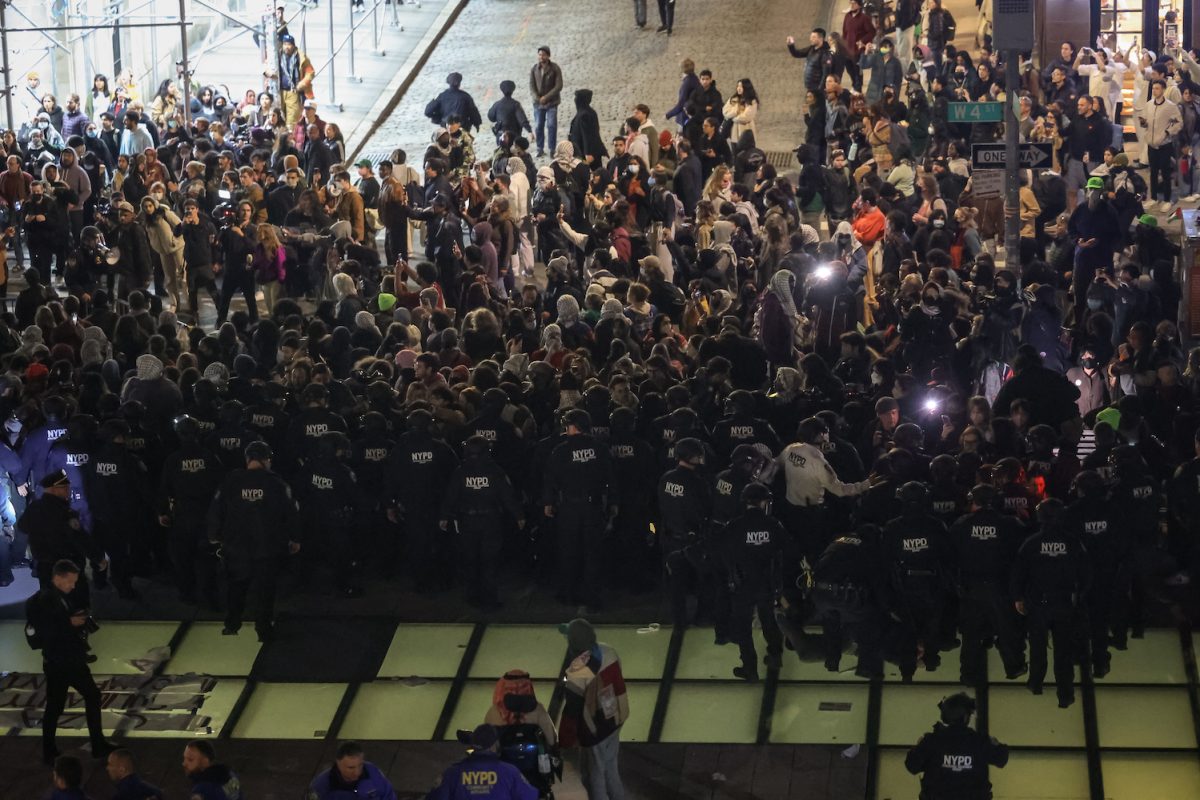
NYU’s Office of Student Conduct is allegedly requiring that some students arrested at the Gaza Solidarity Encampment in Gould Plaza write “reflection papers” and complete “dozens of writing assignments,” a recent Faculty & Staff for Justice in Palestine press release stated. The release said that in emails sent last week, the university informed students they would receive a censure — or a “ formal reprimand for violation of university policy ” — on their transcripts if they did not submit the assignments by May 29.
One of the assignments instructed students to write a reflection paper describing the “incident” for which they were called in the OSC and assessing whether the decision they made aligned with their “personal values.” The paper “cannot serve to justify” the student’s actions, “evaluate the actions of others, or challenge a conduct regulation,” according to the assignment’s instructions. The other assignment is a 49-page “series of readings and reflective activities” that aims to help students “learn about and understand” their own values and how their actions “affected others and the community.”
“Either they really don’t understand that these students are living their values, or this was just intended to be humiliating and infantilizing,” Sara Pursley, a CAS professor and FSJP member, said in an interview with WSN. “It’s ironic to say the least that, in an essay on integrity, they tell students they can’t actually talk about what their real values were.”
In the May 13 press release, FSJP also criticized NYU’s use of Advocate — a higher education software created by the “behavioral intervention management” company Symplicity — which the group claims houses the OSC’s writing prompts. The group noted that Symplicity, which supplies student conduct programs to NYU and over 250 universities, pleaded guilty in federal court on criminal hacking charges in 2014.
In a written statement to WSN, university spokesperson John Beckman called FSJP’s press release “disappointingly misleading” and said that the only people “determining the sanctions that students may receive from conduct proceedings” are staff at the OSC.
“The implication that there’s something insidious going on or that NYU has ‘outsourced’ adjudication of the university’s student conduct procedures is deceptive propaganda,” Beckman wrote. “Symplicity has nothing — repeat, nothing — to do with the specific sanctions NYU students may receive as a result of a conduct process.”
The FSJP press release comes after the university had allegedly dropped criminal charges brought against all protesters arrested at the pro-Palestinian encampment in Gould Plaza three weeks ago, including dozens of students and faculty . Since the encampment, on-campus groups, including FSJP and the NYU Palestine Solidarity Coalition have been demanding that NYU pardon students facing disciplinary action for their involvement in pro-Palestinian demonstrations, divest from companies with ties to Israel, shut down its study away site in Tel Aviv and remove police from campus.
NYU allegedly began disciplinary hearing for students who were involved with pro-Palestinian demonstrations on campus last week, although NYU PSC did not say how many students received misconduct violations or what university policies they were accused of violating. More recently, nine students were suspended and two were given persona non grata status after a demonstration in Bobst Library on Friday, according to NYU PSC.
Contact Dharma Niles at [email protected] .

Comments (2)
Cancel reply
Your email address will not be published. Required fields are marked *
Tana WILLIAMS • May 16, 2024 at 11:22 am
I’m absolutely appalled by what NYU is doing to these students who actually were living their values. It seems as if they want desperately to prove that these intelligent young people were actually influenced by outsiders Rather than accept that these young people, just as we did in my generation with the Vietnam war, we’re standing up for what they Believe is right. Just how far our University officials willing to go to prove their undying loyalty to Israel no matter what Israel does . If things hadn’t ended so quickly the way they did, I, disabled and 74 years old, would have been there in solidarity with these students. Sincerely, Tana S. Williams.
Bob • May 16, 2024 at 7:55 pm
They did not ask these students to change their values. They simply asked that they reflect on the values that led them to violate University policy and communicate those values in a more effective manner. The guidelines given are meant to avoid re- litigating the issue that led to the protest.
Should you give job applicants an assignment during the interview process? Be thoughtful about the ask

Hiring is a time-consuming and expensive endeavor. Companies need candidates who offer the right skills and experience for a given role, and who align with their organization’s vision and mission.
To find the best fit, many companies still lean on a strategy that continues to generate debate : the assignment. Some candidates believe their experience and interviews should give prospective employers enough information to determine whether they will fit the role. Employers have to ask themselves whether they are willing to turn off a strong candidate by asking them to do additional work.
Is the assignment valuable enough to the evaluation process that they cannot move someone forward without it? Sometimes it is—sometimes they help an employer decide between two strong candidates. And if they are necessary, how can employers make assignments fair and equitable for the candidate or candidates?
When done right, assignments help assess practical skills and problem-solving abilities, giving a clearer picture of a candidate beyond what their resume or interview reveals. But employers should be thoughtful about the ask. While it may make sense for roles that require specific technical expertise or creative thinking, it isn’t appropriate for all roles—so assignments should always be given with a clear reason for why they are needed.
Plus, they don’t just benefit the employer. For job seekers, an assignment during the interview process might also help them stand out from the competition. It can also offer a window into what their day-to-day in the new role might entail. Remember that the candidate should be interviewing the company, too. Having a test run of the work they’d be asked to do is a great way to see whether they believe the role is a fit.
However, there is a rift in how people perceive the assignment as part of the interview process. Workers today span many generations, each with unique values and expectations. Whereas older workers often prioritize stability and loyalty, younger millennials and Gen Zers are more focused on flexibility and work well-being, Indeed data shows .
This mindset impacts the amount of time and energy a candidate is willing to devote to each application. After multiple rounds of interviews and prep, taking on an in-depth assignment may feel like a bridge too far—especially if the expectations for the assignment are not clearly communicated ahead of time.
Some candidates are wary of providing free labor to a company that may use their work and not hire them. Hiring managers should be clear about how the work will be used. They may also consider offering compensation if the assignment requires more than a couple hours of someone’s time, or if they plan to use the work without hiring the candidate.
The key for early career candidates in particular is to ensure their time and efforts are respected. This is a win-win for employers: By providing clarity and transparency, they not only elicit the additional information they want from candidates, but they demonstrate that the organization is transparent and fair.
Equity is also imperative: Which candidates are being asked to complete assignments? Is the hiring team consistent in giving out assignments across ages, experience levels, and roles? There should always be a process and clear evaluation criteria in place to ensure fairness.
As we adapt to the rapidly evolving world of work, we must continue to think critically about each step in the hiring process. Candidate assignments can be a valuable tool, but only with appropriate respect for job seekers’ time and contributions.
With the right strategy, we can bridge the gap between generations in the workplace and build a hiring culture that values efficiency, talent, and integrity.
Eoin Driver is the global vice president of talent at Indeed.
More must-read commentary:
- Fannie Mae CEO: Beyoncé is right. Climate change has already hit the housing market—and homeowners aren’t prepared
- Congress could soon spell the end of employment arbitration—but it’s not all good news for American workers
- Outdated laws prevent gig economy workers from getting benefits. This pilot program shows the path forward
- No, combustion engines won’t be supplanted by electric vehicles—and they’re critical for sustainable transport
The opinions expressed in Fortune.com commentary pieces are solely the views of their authors and do not necessarily reflect the opinions and beliefs of Fortune .
Latest in Commentary

Corporate America is mobilizing to support democracy in 2024 and beyond. Here’s how

Big Tech is pouring billions into British AI investments—but the U.K. risks becoming a sidekick to U.S. tech giants

American families are struggling with debt. When it gets forgiven, the tax code treats it like extra income

The myth that money supply controls inflation is being revived. Here’s how it failed its most ardent believer—Margaret Thatcher

I grew up in Kenya’s biggest slum and know from experience: International aid must shift toward community-based organizations

Gen AI looks easy. That’s what makes it so hard
Most popular.

Amazon raised warehouse wages to $15 an hour 5 years ago. Today, half of workers surveyed told researchers they struggle to afford food or rent

Florida HBCU launches investigation after record $238 million ‘gift’ from 30-year-old hemp mogul is deemed likely worthless: ‘I wanted it to be real’

Thousands of North Koreans stole Americans’ identities and took remote-work tech jobs at Fortune 500 companies, DOJ says

Billionaire investor Ray Dalio warns U.S. is ‘on the brink’ and estimates a more than 1 in 3 chance of civil war

Jeff Bezos revealed his secret to Amazon’s success 25 years ago: ‘I asked everyone around here to wake up terrified every morning, their sheets drenched in sweat’

Young adults are getting cold feet about their highly anticipated $84 trillion wealth transfer
- Help Center
- Privacy Policy
- Terms of Service
- Submit feedback
- Announcements
- Organize and communicate with your class
- Create assignments
Create an assignment
This article is for teachers.
When you create an assignment, you can post it immediately, save a draft, or schedule it to post at a later date. After students complete and turn in their work, you can grade and return it to the students.
Open all | Close all
Create & post assignments
When you create an assignment, you can:
- Select one or more classes
Select individual students
Add a grade category, add a grading period, change the point value, add a due date or time, add a topic, add attachments, add a rubric.
- Turn on originality reports
Go to classroom.google.com and click Sign In.
Sign in with your Google Account. For example, [email protected] or [email protected] . Learn more .
- Enter the title and any instructions.
You can continue to edit and customize your assignment. Otherwise, if you’re ready, see below to post, schedule, or save your assignment .
Select additional classes
Assignments to multiple classes go to all students in those classes.
- Create an assignment (details above).
Unless you’re selecting multiple classes, you can select individual students. You can’t select more than 100 students at a time.
- Click a student's name to select them.
Use grade categories to organize assignments. With grade categories, you and your students can see the category an assignment belongs to, such as Homework or Essays . Teachers also see the categories on the Grades page.
For more information on grade categories, go to Add a grade category to posts or Set up grading .
To organize assignments and grades into your school or district’s grading structure, create grading periods, such as quarters or semesters.
- From the menu, select a grading period.
Tip: Before adding a grading period to an assignment, create a grading period for the class first. Learn how to create or edit grading periods .
You can change the point value of an assignment or make the assignment ungraded. By default, assignments are set at 100 points.
- Under Points , click the value.
- Enter a new point value or select Ungraded .
By default, an assignment has no due date. To set a due date:
- Click a date on the calendar.
- To create a topic, click Create topic and enter a topic name.
- Click a topic in the list to select it.
Note : You can only add one topic to an assignment.
Learn more about how to add topics to the Classwork page .
- Create an assignment.
- Important: Google Drive files can be edited by co-teachers and are view-only to students. To change these share options, you can stop, limit, or change sharing .
- To add YouTube videos, an admin must turn on this option. Learn about access settings for your Google Workspace for Education account .
- You can add interactive questions to YouTube video attachments. Learn how to add interactive questions to YouTube video attachments .
- Tip: When you attach a practice set to an assignment, you can't edit it.
- If you see a message that you don’t have permission to attach a file, click Copy . Classroom makes a copy of the file to attach to the assignment and saves it to the class Drive folder.
- Students can view file —All students can read the file, but not edit it.
- Students can edit file —All students share the same file and can make changes to it.
Note : This option is only available before you post an assignment.
Use an add-on
For instructions, go to Use add-ons in Classroom
For instructions, go to Create or reuse a rubric for an assignment .
For instructions, go to Turn on originality reports .
You can post an assignment immediately, or schedule it to post later. If you don’t want to post it yet, you can save it as a draft. To see scheduled and drafted assignments, click Classwork .
Post an assignment
- Follow the steps above to create an assignment.
- Click Assign to immediately post the assignment.
Schedule the assignment to post later
Scheduled assignments might be delayed up to 5 minutes after the post time.
- To schedule the same assignment across multiple classes, make sure to select all classes you want to include.
- When you enter a time, Classroom defaults to PM unless you specify AM.
- (Optional) Select a due date and topic for each class.
- (Optional) To replicate your selected time and date for the first class into all subsequent classes, click Copy settings to all .
- Click Schedule . The assignment will automatically post at the scheduled date and time.
After scheduling multiple assignments at once, you can still edit assignments later by clicking into each class and changing them individually.
Save an assignment as a draft
- Follow the steps above to create an assignment
You can open and edit draft assignments on the Classwork page.
Manage assignments
Edits affect individual classes. For multi-class assignments, make edits in each class.
Note : If you change an assignment's name, the assignment's Drive folder name isn't updated. Go to Drive and rename the folder.
Edit a posted assignment
- Enter your changes and click Save .
Edit a scheduled assignment
- Enter your changes and click Schedule .
Edit a draft assignment
Changes are automatically saved.
- Assign it immediately (details above).
- Schedule it to post at a specific date and time (details above).
- Click a class.
You can only delete an assignment on the Classwork page.
If you delete an assignment, all grades and comments related to the assignment are deleted. However, any attachments or files created by you or the students are still available in Drive.
Related articles
- Create or reuse a rubric for an assignment
- Create a quiz assignment
- Create a question
- Use add-ons in Classroom
- Create, edit, delete, or share a practice set
- Learn about interactive questions for YouTube videos in Google Classroom
Was this helpful?
Need more help, try these next steps:.

COMMENTS
Before submitting an assignment, you may want to review all assignment information, such as the assignment rubric, if any. This lesson shows how to turn in a standard online assignment. Learn how to submit a peer review assignment. Third-Party File Application Submissions
Click the Submit button to the right of the assignment name. This will take you to the file submission page. On the file submission page, make sure the phrase next to the Submit: heading says "Single File Upload." If it says "Cut and Paste Upload," use the dropdown menu (the down arrow) next to Submit: to switch to
Submit an assignment. When you finish your assignment, you must select Submit. If you don't, your instructor won't receive your completed assignment. If your instructor hasn't allowed multiple attempts, you may submit your assignment only once. Before you select Submit, be sure that you have attached any required files.
Submit an assignment. Your instructor provides all the information and files you need to complete an assignment. Be mindful of the time. If your instructor put a time limit on the assignment, you can keep track of how much time is left. A countdown appears at the top left of your screen and warns you as the time limit gets closer.
Select "Classwork" from the menu. 4. Click on an assignment, then select "View Assignment." Click "View assignment" after selecting the assignment you want to submit for. Sophie Putka/Business ...
Start, revise & submit assignments. To start your assignment, you first need to link your Google Account to Assignments. You can then open your assignment and, when you are finished, submit it for grading. If you edit your work before the due date, you can resubmit your assignment. You can attach any file type from Google Drive or your hard ...
Click the class Classwork.; Click the quiz View instructions.; Click the form and answer the questions. Click Submit. If the form is the only work for the assignment, the status of the assignment changes to Turned in.; If there's more work to do for the assignment, click Open assignment.; Turn in an assignment with an assigned doc
Instructors: Create, edit and delete courses and assignments. Create an assignment. Attach template files to an assignment. Create or reuse a rubric for an assignment. Turn on originality reports. How instructors and students share files. Add co-instructors. Set up Assignments in a Schoology course. Delete courses & assignments.
Submitting to an assignment. Turnitin uses the same Canvas upload process you'll already familiar with. If you haven't submitted using Canvas before, follow the steps below. Navigate to your course. From the Assignments tab, open your assignment.; Use the Submit Assignment button to get started. Use the Choose file button to find the file you'd like to upload.
In this video tutorial, I show you how to submit assignments in Google Classroom. With or without an attachment.Get a FREE DOMAIN NAME and 50% Off Web Hostin...
To submit a paper to an assignment on Turnitin, the user must log in and upload a file to an existing assignment. Assignments in Turnitin cannot accept student submissions until the assignment start date and time has passed. Assignments may also reject submissions after the due date and time set by the instructor.
In this Google Classroom tutorial, you'll see Google Classroom for students examples on how to submit assignments. https://bit.ly/DearDIS Subscribe for more!...
Easily distribute, analyze, and grade student work with Assignments for your LMS. Assignments is an application for your learning management system (LMS). It helps educators save time grading and guides students to turn in their best work with originality reports — all through the collaborative power of Google Workspace for Education. Get ...
View your submission and the SafeAssign reports associated with it by accessing the assignment after you submit your paper. This option is available only if allowed by your instructor. Return to the assignment you submitted previously. Under Assignment Details, select SafeAssign. View the overall match percentage that SafeAssign detected.
Use Assignments to create, collect, and give feedback on assignments in a learning management system (LMS). Before you begin To use Assignments, you need an LMS and a Google Workspace for Education ... Students can't submit classwork until you link your account. After you select Google Assignments as an external tool, choose an option based on ...
To submit an assignment. From the navbar, click Assignments. On the Assignments page, click on the assignment you want to submit to. Figure: Selecting an assignment for submission. Follow the assignment instructions, and do one of the following: Type your assignment directly in the Text Submission field.
Dear Professor/Instructor [Last Name], I hope this email finds you well. I am writing to submit my assignment for the [Course Name]. The assignment is attached in the required format. I have completed the assignment as per the given guidelines and it is ready for submission. The due date for the assignment is [Due Date].
A few reminders: The working on assignments page contains info about the assignment process.; The collaboration policy page outlines permitted assignment collaboration, emphasizing that you are to do your own independent thinking, design, writing, and debugging. Even without any code being submitted, you should not be doing any joint debugging/development, sharing or copying written answers ...
Should they choose to do so, an option holder must submit an exercise notice to their brokerage firm along with instructions. These instructions are then relayed to OCC which in turn triggers the assignment process. On expiration: OCC administers the automatic exercise process, which occurs when an option contract is a penny or more in-the ...
Earlier, the last date to submit the IGNOU June TEE 2024 assignment was April 30. "With the approval of the Competent Authority, the last date for submission of assignments (both in hard copy and soft copy) for Term End Examinations, June 2024 for both ODL and online programmes, GOAL and EVBB has further been further extended up to 31st May 2024," said an official notice from IGNOU.
Assignments is an add-on application for learning management systems (LMSs) to help you distribute, analyze, and grade student work with Google Workspace for Education. For file submissions, Assignments make Google Docs, Google Sheets, Google Slides, and Google Drive compatible with your LMS. You can use Assignments to save time distributing ...
Deacon Daniel E. Bryan concluded his diaconal assignment at St. Clement Parish, Lakewood and he was granted retirement status as a deacon, effective July 1. Deacon Robin R. Adair, ... Submit. Phone: 216-696-6525. Toll Free: 1-800-869-6525. Address: 1404 East 9th Street, Cleveland, OH 44114. Notice of Data Security Incident.
NYU's Office of Student Conduct is allegedly requiring that some students arrested at the Gaza Solidarity Encampment in Gould Plaza write "reflection papers" and complete "dozens of writing assignments," a recent Faculty & Staff for Justice in Palestine press release stated. The release said that in emails se nt last week, the university informed students they...
For job seekers, an assignment during the interview process might also help them stand out from the competition. It can also offer a window into what their day-to-day in the new role might entail ...
CLOSING DATE: 1600hrs 1 June 2024 PROJECTED BOARD DATE: 15 June 2024 Applications are being accepted for the following position: Unit: HHC 38 CAB (WTQJAA) Duty Title: Brigade Command Sergeant Major Position Number: 03044789 Grade: E-9/CSM MOS: 15Z Vacancies Authorized: 1 Female Assignment Eligibility: Yes Projected Entry Date: 1 September 2024 ***UPDATED POSTING*** All applicants who already ...
Create an assignment (details above). Under Due, click the Down arrow . Next to No due date, click the Down arrow . Click a date on the calendar. (Optional) To set a due time, click Time enter a time and specify AM or PM. Note: Work is marked Missing or Turned in late as soon as the due date and time arrive.