

Cyber Crime Essay For Students

Table of Contents
Cyber Crime Essay: In today’s digital age, the internet has become an integral part of our lives. While it offers numerous benefits, it also brings with it a dark side – cybercrime. It is imperative for all individuals to be well-informed about the world of cybercrime, what it is, its types, and its impact. In this article, we have provided you with sample essays on cybercrime of varying lengths to help you get started on your own essay.
What is Cyber Crime?
Cybercrime, simply put, is criminal activity conducted online. It encompasses a wide range of illegal activities that use computers and the internet as tools to commit crimes. These crimes can be broadly categorized into four main types: financial, personal, political, and property crimes.
Fill Out the Form for Expert Academic Guidance!
Please indicate your interest Live Classes Books Test Series Self Learning
Verify OTP Code (required)
I agree to the terms and conditions and privacy policy .
Fill complete details
Target Exam ---
Whether you need a 100-word overview or a more detailed 500-word essay on the topic “Cyber Crime Essay”, we’ve got your back. Refer to the sample essays given below.

Sample Essays on Cyber Crime
100-word essay on cyber crime.
Cybercrime, the dark underbelly of the digital world, is on the rise. It encompasses a range of illegal activities conducted through computers and the internet, including hacking, phishing, and online fraud. Cybercriminals exploit vulnerabilities for financial gain or personal satisfaction, causing harm to individuals and organizations. The consequences can be devastating, from financial loss to emotional distress and stolen identities. To combat cybercrime, awareness and vigilance are paramount. Adopting strong passwords, using antivirus software, and practicing safe online behavior are steps we can all take to protect ourselves in this interconnected age. Cybercrime is a threat we must confront in our digital lives.
Cyber Crime Essay: 250 Words
In today’s technology-driven world, where we rely heavily on the internet and digital devices for various aspects of our lives, the threat of cybercrime looms larger than ever. Cybercrime encompasses a wide range of illegal activities carried out in the digital realm, and its impact extends far beyond just financial losses.
Hacking, a prevalent cybercrime, involves malicious individuals gaining unauthorized access to systems, risking sensitive data compromise, leading to dire consequences such as identity theft and financial ruin.
Phishing scams, a common cybercrime, deceive victims into disclosing personal data, enabling criminals to commit theft and fraud with the acquired information.
Online fraud is rampant in the cyber world. Criminals create fake websites or online marketplaces to dupe unsuspecting victims into making payments for goods or services that don’t exist. Victims can lose substantial sums of money in such scams.
To combat cybercrime, prioritize cybersecurity by practicing safe online behavior, updating passwords, and using reliable antivirus software. Keeping software and operating systems up to date is crucial for enhanced protection.
Additionally, organizations and governments need to invest in robust cybersecurity infrastructure and enact stricter regulations to deter cybercriminals. Raising awareness about the risks and consequences of cybercrime is a collective responsibility that can help safeguard our digital world.
In conclusion, cybercrime is a growing menace that affects individuals, businesses, and society as a whole. Understanding the various forms of cybercrime and taking proactive steps to protect ourselves and our digital assets are essential in this interconnected age. Only through collective efforts can we hope to mitigate the ever-present threat of cybercrime.

Cyber Crime Essay: 300 Words
In our increasingly digitized world, cybercrime has emerged as a formidable challenge. Cybercrime refers to criminal activities carried out through computer networks and the internet, encompassing a wide range of illicit actions that exploit vulnerabilities in our interconnected systems.
One prevalent form of cybercrime is hacking, where individuals or groups gain unauthorized access to computer systems or networks, often with malicious intent. Hacked systems can lead to data breaches, identity theft, and financial losses for individuals and organizations alike.
Phishing is another common cybercrime tactic, where scammers impersonate legitimate entities to trick individuals into revealing sensitive information, such as login credentials or credit card details. These deceptive schemes can result in severe financial and personal consequences for victims.
Online fraud, including various scams and schemes, poses significant risks. It includes activities like advance-fee fraud, Ponzi schemes, and online auction fraud. Victims may suffer substantial financial losses, and recovery can be challenging.
Cyberbullying and online harassment are personal cybercrimes that target individuals through hurtful, threatening, or offensive online behavior. These acts can have profound psychological and emotional effects on victims.
To combat cybercrime, individuals and organizations must prioritize cybersecurity. This involves using strong, unique passwords, enabling two-factor authentication, and keeping software and antivirus programs up to date. Cybersecurity awareness and education are crucial to recognizing and avoiding potential threats.
Governments and law enforcement agencies worldwide are also working to combat cybercrime by strengthening legislation and collaborating on international cybercrime investigations. However, prevention starts with individual responsibility and vigilance.
In conclusion, cybercrime is an evolving threat that affects us all in the digital age. As technology advances, so do the methods employed by cybercriminals. Staying informed, practicing safe online behavior, and implementing robust cybersecurity measures are essential steps to protect ourselves and our digital assets from the growing menace of cybercrime.
500-Word Essay on Cyber Crime:
In our increasingly interconnected world, where digital technology permeates every aspect of our lives, the threat of cybercrime has become a pressing concern. Cybercrime encompasses a wide range of illicit activities that occur in the digital realm, using computers, networks, and the internet as tools for criminal intent. This essay explores the evolving landscape of cybercrime, its various forms, the consequences it brings, and the measures individuals and organizations can take to combat this growing menace.
The Landscape of Cybercrime
Cybercrime is a multifaceted problem, constantly evolving as technology advances. It includes various forms, such as hacking, phishing, identity theft, online fraud, cyberbullying, and more. The motives behind cybercrime can be financial gain, political agenda, personal vendettas, or even thrill-seeking.
Hacking is one of the most prevalent forms of cybercrime. It involves unauthorized access to computer systems, networks, or data. Hackers exploit vulnerabilities to steal sensitive information, disrupt services, or distribute malware.
Phishing, on the other hand, is a deceitful practice where cybercriminals impersonate legitimate entities to trick individuals into revealing personal information or login credentials. This information is then used for malicious purposes, such as identity theft or financial fraud.
Identity theft is a pervasive cybercrime, with victims experiencing devastating consequences. Cybercriminals use stolen personal information to open fraudulent accounts, apply for loans, or engage in criminal activities, often leaving the victim to deal with the legal and financial fallout.
Online fraud includes various scams and schemes, such as Ponzi schemes, fake online marketplaces, and investment fraud. Victims of online fraud can lose substantial sums of money, often with little hope of recovery.
The social impact of cybercrime is also significant. Cyberbullying and online harassment have become increasingly common, especially among young people. The anonymity provided by the internet allows perpetrators to engage in hurtful behavior, leading to emotional and psychological distress for the victims.
The Consequences of Cybercrime
The consequences of cybercrime are far-reaching and extend beyond financial losses. Individuals can experience emotional distress, anxiety, and a loss of trust in online interactions. Businesses and organizations face significant financial and reputational damage when data breaches occur. Governments grapple with the challenge of protecting national security and critical infrastructure from cyberattacks.
Solutions and Prevention
To combat cybercrime effectively, individuals, organizations, and governments must work together and adopt proactive measures. Here are some key steps:
- Cybersecurity Awareness : Raising awareness about the risks of cybercrime is essential. Individuals should educate themselves about online threats and practice safe online behavior.
- Strong Passwords : Using strong, unique passwords for each online account is crucial. Employing password managers can help manage and generate complex passwords.
- Antivirus Software : Reliable antivirus and anti-malware software can detect and block malicious threats.
- Regular Software Updates : Keeping software, operating systems, and applications up to date is essential to patch security vulnerabilities.
- Two-Factor Authentication : Enable two-factor authentication (2FA) wherever possible to add an extra layer of security to your accounts.
- Secure Data Handling : Exercise caution when sharing personal information online. Only provide sensitive data on trusted websites.
- Cybersecurity Training : Organizations should invest in cybersecurity training for their employees to recognize and respond to threats effectively.
- Legal Frameworks : Governments need to enact and enforce comprehensive cybersecurity laws and regulations to deter cybercriminals.
- International Collaboration : Cybercrime often crosses international borders, so international collaboration among governments and law enforcement agencies is crucial.
The threat of cybercrime is an ever-growing challenge in our digital age. As technology advances, so do the methods and sophistication of cybercriminals. To effectively combat cybercrime, individuals, organizations, and governments must prioritize cybersecurity through awareness, education, and the implementation of robust security measures. Only by working together can we hope to mitigate the risks and consequences of cybercrime and ensure a safer digital future for all.
Check Other Essays:
FAQs on Cyber Crime Essay
What is cyber crime in short essay.
Cybercrime refers to criminal activities carried out using computers or the internet. Examples include online fraud, hacking, identity theft, and cyberbullying. These crimes can have serious consequences, such as financial loss, personal harm, or damage to one's reputation. To combat cybercrime, individuals must stay vigilant and follow online safety practices.
What is cyber security in 100 words?
Cybersecurity is the practice of safeguarding digital systems, networks, and data from a wide range of cyber threats and unauthorized access. It involves implementing measures and technologies to protect information integrity, confidentiality, and availability. Cybersecurity encompasses various aspects, including the use of strong passwords, encryption, firewalls, antivirus software, and intrusion detection systems. It is essential in today's interconnected world to mitigate the risks of data breaches, hacking, malware attacks, and other malicious activities that can lead to financial losses, reputational damage, and the compromise of personal and sensitive information. Cybersecurity is an ongoing effort to maintain the security and resilience of digital environments.
Is cyber crime bad?
Yes, cybercrime is bad as it can result in financial loss, emotional distress, and harm to individuals and organizations.
What are the causes of cybercrime?
The causes of cybercrime include technological vulnerabilities, lack of cybersecurity awareness, financial motivations, and anonymity provided by the internet.
Related content
Talk to our academic expert!
Language --- English Hindi Marathi Tamil Telugu Malayalam
Get access to free Mock Test and Master Class
Register to Get Free Mock Test and Study Material
Offer Ends in 5:00

Essay on Cybercrime for Students & Children in 1000 Words
In this article you will read an Essay on Cybercrime in English 1000 words for students and children. It includes its meaning, types, causes and prevention tips.
Table of Contents
The malicious activity of Cybercrime was first reported in 1970 when new computerized phones were being targeted. Tech-savvy people found ways to play long-distance calls through a series of codes.
hey were the first to exploit the system by modifying both software and hardware to steal long-distance phone time.
It was the instance that made people understand that computer systems are more vulnerable to criminal activity, and the more complex the system became, it became more susceptible to Cybercrime.
What is Cybercrime?
Cybercrime is a crime that is conducted involving computers and networks. The computer might be the tool used to commit the crime or the intended target on which the crime has been committed.
Cybercrime may be a crime to intentionally harm the reputation of an individual in the digital world, which might cause virtual, physical, and mental harm to the individual.
It also threatens a person’s and nation’s security and financial health. Issues like hacking, copyright infringement, unwarranted mass surveillance are the significant and high prolific crimes that are committed.
Computers can be used as both tools and targets depending on the type of hacker utilizing the equipment. These crimes involve less technical expertise and typically exploit human weakness.
Just like individuals walking around leaves marks, a skilled tracker can follow. Cyber criminals leave identities and locations even though they provide the best efforts to track their tracks.
To develop the clues, international treaties are ratified between the countries so that they can follow the concern of hackers committing crimes and frauds.
Types of Cybercrime
1. identity theft.
In this sort of Cybercrime, criminals access the profile of the user and use their personal information to steal funds or commit fraud based on the user.
The criminal can also generate your digital account and utilize the same to commit fraud and even claim benefits from the various government schemes in your name.
The criminal uses the password obtained from hacking the victim’s personal information from social media or by sending phishing emails.
2. Cyberstalking
This Cybercrime involves online harassment where the victim is subjected to a plethora of online messages and emails.
Typically, the stalker uses social media , websites, and search engines to intimate the victim and instils fear. The stalker knows the victim and makes the person feel afraid and concerned for their safety.
3. Cyberextortion
This kind of crime also occurs when the website, email server is threatened with repeated denial of service or attacks by hackers. The hackers demand money in return for a promise to stop attacking and provide protection.
By the latest reports, Cybercrime extortion is increasingly attacking the corporate website and their networks, crippling their capability to operate and demanding payments to restore their service.
At least 20-30 cases are reported each month regarding extortion and are not even reported to Cybercrime cells.
4. Cyberwarfare
The department of the US Army has noted the increase of cyber warfare in recent times due to constant change in the geostrategic significance.
It is one of the fronts that the defence body of every country is focused on to thwart hackers from attacking the computer networks of their country.
Further, all the essential utilities of a country, including the defence systems, are monitored controlled through computers and networks with little human intervention.
The criminals are continually finding ways to penetrate the network systems so that they can extort money from the government of the countries. The Defence bodies of the states are always trying to be ten steps ahead of the criminal hackers to defend their homelands.
5. Financial Frauds and Crime
Computer frauds are where there is a misrepresentation of facts intended to cause harm to an individual or an organization. The evasion will result in altering the data in unauthorized ways like entering the false data or by entering illegal instruction or processes.
Modifying or deleting the stored data. Other frauds may include bank fraud or theft of classified information. These types of crimes lead to the loss of confidential information or financial information.
Through the automated teller machine (ATM), many people get cash nowadays by using cards and typing personal identification numbers (PINs).
Criminals have developed ways to intercept both data in the magnetic stripe on the cards and the PIN to create fake cards and withdraw cash from the ATM.
6. Drug trafficking through darknets
Drug traffickers are always finding ways to sell their products & find new customers for their products.
In this modern age of time, Darknet is one of the places in the digital world where criminals are selling their products to the customers without even coming into physical contact with them.
7. Social Engineering
It is the kind of crime in which the criminals make direct contact with the victim, usually through phone or email.
They try to gain the confidence of the victim by posing as customer service agents so that the victim gives away the required information willingly. Usually, the data is like a password; the company, the victim, works for or has bank information.
Cybercriminals will try to find out as much information through social networking and try to add you as your friend on social accounts. Once they gain entry to your accounts, they can sell your information or secure the report in your name.
Potentially Unwanted Programs known as PUPs are less threatening than other cyber-crimes but are a type of malware. The purpose of these programs is to uninstall necessary software from your system, including search engines and pre-downloaded apps.
They can include spyware or adware; it is, therefore, an excellent idea to install antivirus software to avoid malicious downloads.
9. Phishing
Phishing is the type of attack that involves hackers sending a malicious attachment along with email or the URLs to the users to gain access to their computers and accounts.
Cybercriminals are becoming more established; these mails are also not flagged as spam. Sometimes the users are tricked into emails claiming they must change the password or update their billing information, giving the hacker access.
10. Illegal Contents:
Cybercrime also involves hackers sharing inappropriate content that can be considered highly offensive and distressing. Offensive content can include criminal activities, intense violence, and sexual activity between two adults.
Illegal contents also include the radicalizing of the youths and leading them to commit terror-related activities. These types of materials are available on both the everyday internet and anonymous dark web.
Crime and Cybercrime have increasingly become significant problems for society. Both in the public webspace and dark web space, cybercriminals are highly skilled and are not easy to find.
Cybercrime has generated a foremost threat to those who use the internet with loads of information stolen by hackers and causing a dent in the economy.
Causes of Cybercrime
As I have mentioned above Cybercrime is of several types so using the internet without knowing the proper security information is not good.
Below we have given a few major causes of Cybercrime:
1. Lack of knowledge
Today internet is one of the most important places to get information about everything. You will get every information on any topic when you search on internet.
But using it without knowledge is dangerous which is one of the major causes of Cybercrime. Most of the peoples only get hacked only because of lack of knowledge.
So, before entering to the cyber world you must have the knowledge of above given types of Cybercrimes.
2. Using internet without limitations
Using internet is very easy but using without any limitation is one of the major causes of Cybercrimes. You must have some limits to share your data on internet.
If you use social media you must set up your privacy settings properly. Sharing All of your personal data on internet without any limitation cause data hacks and Cybercrimes.
Not only this Childrens are more susceptible to cybercrime now a days because they are now sticking with their mobile phones and laptops most of the time. this issue started after the rise of online education all over the world.
Few parents are aware of this type of issue and they always limit their kid’s device usage.
Sharing your card and bank details on internet for any type of fake offer another cause of Cybercrime. In short words you must have to create few limitations during using your device network on internet.
3. Using Cracked software
Most people use cracked software and applications in their devices. It is another major cause of Cybercrime.
Hacker’s crack software’s and put malware inside it. So, when users install it in their PC and mobile the hacker gets into their device and easily steals their passwords, Wi-Fi details, and important data.
4. Storing of data in small space
Still in this digital world people are keeping their important documents and data in small space of their PC and mobile phone. This is causing the ultimate cybercrime.
Always try to keep your private and important data in secure cloud folder or cloud data base with 2FA and OTP verification enabled.
How to prevent cybercrime?
In this modern-day age of technology, hackers are taking over our systems, and no one is safe. The crime is also not easily detectable, but there are ways to protect yourself from these crimes like educating yourself and your colleagues and taking preventive measures.
There are few simple steps to protect yourself from Cybercrime. Let’s go through those points:
1. Use a premium security service in your device
Must use a premium security app in your electronic device which will secure your files and scan your network. Also, most of the security software’s secure your data from ransomware attacks.
2. Use password protection apps and plugins
If someone hacks your Google password, he will easily get all the credential saved on Chrome browser. So nowadays it is better to install an extra Password Manager with Two-Factor Authentication (2FA).
Most of the password managers are available for both PC and Smartphones . So, it will be easy for you to synchronize your passwords on both of your devices. Most of the cybercrime today is happening only because of password hack.
3. Keep your device and OS software updates
Updating your device regularly is the most important thing in device security, it avoids new Malware and cybercrime. So always update as soon as possible when you get a new security patch notification on your device.
4. Properly set up your social media privacy settings
Now a days most of the people use social media but using it properly is most important. Most of the hackers stole personal information from social media accounts.
Correctly editing your privacy settings in social media keeps your profile secure and visible to your near and dear ones only. Opening it to everyone may lead to account hacking or stealing of important personal details.
5. Use a strong password in your network devices
Using an automatic password generation tool or extension in your device provides you with a better strong password. Not only this, try to change your wireless network passwords every month if possible.
6. Always use child mode when kids are using devices
Children in everyone’s house use their parent’s laptop and smartphone but nobody keeps limitations during their usage. Kids are not aware of any type of Cybercrime so they may make mistakes which may cause personal and important data hacks.
Most of the Smartphones and computers are now coming with a child mode option. Always ON that option when your child is using your phone.
7. Use a reliable VPN to secure your identity
If you are worried about your personal data hack using a VPN in your device solves this problem. When the VPN is active nobody will track you and know your location.
Accessing your accounts became hard to hack by hackers. Using a VPN stops most of the cybercrime happening nowadays.
8. Stay updated about the latest security breaches
Every OS and device company provides regular updates to their users. The main reason for it is the latest security patches keep the devices secure from new vulnerabilities. So, always update your device software as soon as you get.
9. Keep knowledge of what to do when you’re hacked?
Hackers are very clever so maybe after doing all the above precautions you may get hacked. After gone hand everybody gets worried about their important files and data.
Every country has different departments and laws for dealing with cybercrimes. You must know what to do when you are hacked. In India there is a National Cybercrime Reporting Portal where you can report your issue.
Cybercrime is one of the major security concerns for all of us. We need to use our online work using with secure connection and database.
Also, you should aware of different types of cyber hacks happening now a days. You can also go through various Cybercrime prevention steps to avoid any cyberattack.
Following all the step keeps you away from cyber hack and secure you from fraud. I hope this Essay on Cybercrime helped you to understand all about it in short.
1 thought on “Essay on Cybercrime for Students & Children in 1000 Words”
This essay helps me a lot in my project. It is in simple language and in understable type. It helps me in my exam also. Thank you so much for this essay
Leave a comment Cancel reply
- Technical Support
- Find My Rep
You are here
Cybercrime and Society
- Majid Yar - Lancaster University, UK, Lancaster University
- Kevin F. Steinmetz - Kansas State University, USA
- Description
See what’s new to this edition by selecting the Features tab on this page. Should you need additional information or have questions regarding the HEOA information provided for this title, including what is new to this edition, please email [email protected] . Please include your name, contact information, and the name of the title for which you would like more information. For information on the HEOA, please go to http://ed.gov/policy/highered/leg/hea08/index.html .
For assistance with your order: Please email us at [email protected] or connect with your SAGE representative.
SAGE 2455 Teller Road Thousand Oaks, CA 91320 www.sagepub.com
I have used Drs. Steinmetz and Yar's textbook for a variety of cybercrime courses. They consistently provide the most current information, which is very difficult to do given the rapid pace of technology advancements. Moreover, they explore how cybercrime topics are framed using longstanding theories as well as those less discussed in the field. It is simply a wonderful text that is easily accessible to a wide spectrum of students.
This was a well informed resource for student police officers, in a growing and challenging area that is exploited by criminals. This will assist the development of students understanding.
Preview this book
For instructors, select a purchasing option, related products.


Essay on Cyber Crime | 500+ Words
Cybercrime is like a shadow lurking in the digital world, ready to harm us. In this essay, we will explore the world of cybercrime, its types, consequences, and how we can protect ourselves in the digital age.
Defining Cybercrime:
Cybercrime involves illegal activities conducted online. These crimes can harm individuals, organizations, and even entire nations.
The Digital Revolution
The rise of technology has brought convenience but also vulnerabilities. Cybercriminals exploit these vulnerabilities for personal gain.
Types of Cybercrime
Cybercrime takes many forms, including hacking, identity theft, online scams, and cyberbullying. Each poses unique risks and challenges.
Hacking and Data Breaches
Hackers gain unauthorized access to computer systems, stealing valuable data. These breaches can lead to financial loss and privacy violations.
Identity Theft
Identity theft involves stealing personal information for fraudulent purposes. Victims can face financial ruin and emotional distress.
Online Scams
Scammers trick people into giving away money or personal information. Awareness and skepticism are key defenses against these scams.
Cyberbullying
Cyberbullying involves using the internet to harass or harm others. It can have devastating effects on mental and emotional well-being.
The Impact of Cybercrime
Cybercrime has far-reaching consequences, affecting individuals, businesses, and governments. It erodes trust and security in the digital world.
Financial Loss
Victims of cybercrime often suffer financial losses. Recovering stolen funds can be challenging, and the impact can be long-lasting.
Emotional Toll
The emotional toll of cybercrime can be severe. Victims may experience fear, anxiety, and a loss of trust in online interactions.
Expert Opinions on Cybercrime
Experts in cybersecurity emphasize the importance of vigilance, education, and strong security measures in protecting against cyber threats.
Cybersecurity Measures
Protecting against cybercrime requires cybersecurity measures like strong passwords, antivirus software, and regular software updates.
The Role of Education
Education about online safety is vital. Schools and organizations should teach digital literacy and cybersecurity from an early age.
Online Privacy
Protecting online privacy means being cautious about sharing personal information and understanding the importance of data protection laws.
Reporting Cybercrime
Reporting cybercrime to law enforcement is crucial. It helps track down cybercriminals and prevent further harm.
International Cooperation
Cybercrime is a global issue. International cooperation and laws are essential to combating it effectively.
The Future of Cybersecurity
As technology evolves, so do cyber threats. Ongoing research and innovation in cybersecurity are essential to staying ahead of cybercriminals.
Conclusion of Essay on Cyber Crime
In conclusion, cybercrime is a digital menace that affects us all. Whether it’s hacking, scams, or cyberbullying, the consequences can be devastating. However, we can protect ourselves by staying informed, practicing good cybersecurity habits, and reporting cybercrime when it occurs.
The digital age has brought us incredible opportunities, but it has also brought risks. It is our responsibility to navigate this digital world with caution and vigilance. By doing so, we can reduce the impact of cybercrime and make the internet a safer place for everyone. Cybersecurity is not just a personal responsibility; it’s a collective effort to keep our digital world secure and trustworthy.
Also Check: The Essay on Essay: All you need to know
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection

Cybercrime: Victimization, Perpetration, and Techniques
James hawdon.
Virginia Tech, Blacksburg, VA USA
The creation of the World Wide Web revolutionized communication. At the turn of the twenty-first century, roughly 413 million people used the internet (Roser & Ortiz-Ospina, 2015 ). A mere 21 years later, nearly 4.7 billion people, or about 60% of the world’s population, actively use the internet (We Are Social, & DataReportal, & Hootsuite, 2021 ). The pace of innovation in information technology, from the introduction of email in the 1960s to the rise of multiple social media platforms in the early 2000s to the rise of the Internet of Things (Iot) and 5 g, has been astonishing. It is now almost inconceivable to imagine life without access to the internet. Yet the IT revolution, like all technological revolutions, has been a dual-edge sword. Indeed, the internet’s many benefits and drawbacks have been discussed in numerous forums, and these discussions will undoubtedly continue as long as we remain dependent on this technology. This special edition of the American Journal of Criminal Justice contributes to those discussions by considering one of the drawbacks: cybercime.
Cybercrime, or the use of computer technology or online networks to commit crimes, ranges from fraud and identity theft to threats and intimidation. Cybercrime and its many manifestations has clearly increased over the past 20 years. For example, cybercrime costs increased from approximately $3 trillion in 2015 to more than $6 trillion in 2021, and these are expected to increase to over $10.5 trillion by 2025 (Morgan, 2020 ). In the U.S. alone, approximately 23 percent of households experience some sort of cybercrime annually (Reinhart, 2018 ; Hawdon et al., 2020 ). Indeed, in the same way that larceny characterized the twentieth century, cybercrime is characterizing the twenty-first century (Albanese, 2005 ). And these facts just reflect the economic costs of cybercrime and do not account for the non-monetary harms caused by cyberviolence. Cyberstalking, online sexual exploitation, cyber-harassment and bullying, threats of violence, and online violent extremism are also commonly committed acts of cyberviolence (FBI, 2021 ).
In many ways, it is unsurprising that cybercrime has increased in recent years. As technology becomes more sophisticated, so do cybercriminals, and cybercriminals now target individuals, businesses, healthcare facilities, educational institutions, and governments. As more people engage in an ever-increasing variety of online activities and more businesses conduct their affairs online, it is predictable that there would be a rise in cybercrime. To use the familiar language of Routine Activity Theory (Cohen & Felson, 1979 ), we have a lot more suitable targets in insufficiently guarded space being victimized by an increasing number motivated offenders. It is also unsurprising that there is a growing body of literature dedicated to cybercrime as scholars scramble to understand the ever-evolving phenomena. Entire journals are now dedicated to its study, and new academic disciplines have been created to try to prevent it. While our understanding of cybercrime has accumulated quickly and impressively, there is so much about cybercrime that we still do not know. This special issue of the A merican Journal of Criminal Justice offers nine new articles to help fill that knowledge gap.
The articles included in this issue reflect three broad areas of cybercrime research: cybercrime victimization, cybercrime perpetration, and techniques and facilitators of cybercrime. While there is some overlap, the issue includes three papers focused on each of these three areas.
The first area covered in the special issue focuses on cybercrime victimization. This area has generated the most research to date. In part because victims of cybercrime are relatively easy to find, considerable research has been conducted on cybervictimization across a variety of cybercrimes. Three of the articles in this special issue focus on cybervictimization, and they add to the literature in interesting ways by providing cross-national perspectives, building on theoretical traditions, or providing systematic summaries of the state of field at this time.
The first article in this section by Michelle Wright and a team of colleagues investigates how adolescent from China, Cyprus, the Czech Republic, India, Japan, and the United States explain being a victim of cyberbully. The investigation compares if how adolescents explain victimization varies by setting (private vs. public), medium (offline vs cyber), and severity and if cultural differences alter these relationships. Their findings suggest the need for prevention and intervention efforts to consider the role of setting, medium, severity, and cultural values if they are to be successful.
The second paper focusing on victimization builds on the frequent finding that problematic social media use is associated with negative life experiences and provides empirical support for a theoretical link between problematic social media use and cybervictimization. The analysis, conducted by colleagues Eetu Marttila, Aki Koivula, and Pekka Räsänen, is framed in Routine Activity Theory/Lifestyle-Exposure Theory. The results indicate that not only is problematic social media use strongly correlated with cybervictimization in a between-subject analysis, but within-subject analyses also reveal that problematic social media use has a cumulative effect on victimization.
The third paper bridges research on cybercrime victimization and cybercrime perpetration and provides a glimpse at the state of knowledge about a specific form of cyberviolence. Catherine Marcum and George Higgins conduct a systematic review of literature investigating both offending and victimization of cyberstalking, cyberdating abuse, and interpersonal electronic surveillance. Using a number of electronic databases, the authors focus on 31 studies to identify correlates of involvement in these cybercrimes. Victims are disproportionately female. Other correlates of victimization include overall social media use, risky online behavior, and negative external factors such as being attached to abusive peers. Correlates of perpetration provide support for a number of leading criminological theories as perpetrators tend to have low levels of self-control, associate with delinquent peers, and have low levels of parental supervision. As more research is conducted, there is a great need for more systematic literature reviews so we can begin to better refine our understanding and identify the theoretical approaches that provide the most insight into the world of cybercrime.
There are another three articles included in this special issue that focus on cybercrime perpetration. All three articles test traditional criminological theories and find support for them. In the first, Adam Bossler uses Sykes and Matza’s ( 1957 ) techniques of neutralization to examine the effects of techniques of neutralization on college students’ willingness to commit cybercrime, specifically hacking websites to deface them or compromise foreign and domestic financial and government targets. An overall techniques of neutralization scale significantly predicts being willing to commit cyberattacks even after controlling for other relevant factors. In addition to the theoretical implications of finding strong support for Sykes and Matza’s framework, the findings also have implications for situational crime prevention efforts aimed at removing excuses for offenders.
In another article focusing on perpetration, Thomas Dearden and Katalin Parti use a national online sample of 1,109 participants and find strong support for social learning theory as measures of both online and offline social learning correlate with a measure of cyber-offending. However, the authors also argue that self-control will interact with social learning variables to further influence the likelihood of cyber-offending. Overall, they find that both social learning and self-control, individually and as an interaction, are good predictors of cyber-offending.
In the final article dedicated to investigating the perpetration of cybercrime, Ashley Reichelmann and Matthew Costello use a nationally representative sample to explore how various dimensions of American national identity relate to producing online hate materials. The analysis reveals that higher levels of salience and public self-regard are weakly related to producing online hate. However, the findings suggest that understanding the nuances of “what it means to be American” is important for fully understanding the phenomenon of cyberhate, especially in this polarizing time when what it means to “be American” is frequently questioned.
Another three articles deal with perpetrating cybercrimes or “pseudo-cybercrimes,” but their focus is on how these crimes are committed. That is, the investigations deal with using the Dark Web or the surface web to make illegal or pseudo-legal purchases of illegal or quasi-legal substances. In the first paper in the section, Eric Jardine provides a crime script for purchasing drugs on the Dark Web. The script involves four generic stages (i.e. Informational Accumulation; Account Formation; Market Exchange; Delivery/Receipt) and provides an opportunity to review known law enforcement interventions that have effectively targeted each stage of the script to reduce the use of these online markets. The paper highlights numerous steps that law enforcement could take to effectively reduce the illegal selling and purchasing of drugs on the Dark Web.
Next, Robert Perdue engages in green criminology and focuses on the illegal trade of endangered species. Noting that regulating this trade is a critical, and very difficult, challenge for conservationists and law enforcement agents, Perdue examines the role the Internet plays in critically endangered plant transactions, but instead of focusing on the Dark Web, he investigates eBay to understand the extent to which such trades occur in plain sight. He finds that nearly a third of the critically endangered plant species examined were for sale in some form on eBay. Yet, despite the evidence that there is a high degree of open trading in these species, the complexity of the international legal frameworks regulating these transactions makes it difficult to ascertain their legality. Nevertheless, at least a subset of these sales are probably unlawful.
Finally, J. Mitchell Miller and Holly Ventura Miller provide insight into the computer-facilitated gray market of pseudo-legal marijuana sales in Los Vegas, Nevada. The ethnographic study reveals how various cannabis products are illegally diverted from legal markets to the gray market, and how brokers use the Internet in clever ways to advertise their products and services to a public that is likely unaware that they are engaging in illegal activities by skirting the regulations and tight control of the legal market.
Taken together, these three papers highlight the tremendous difficulties with regulating e-commerce. While the Dark Web provides an environment to conduct illegal transactions with minimal risk, it turns out that the Dark Web may be unnecessary for many illegal cyber-purchases. Given the surface web is convenient, widely available, and scarcely policed, many cybercriminals simply commit their crimes in the open. Using the language of Routine Activity Theory again, the internet—Dark or Surface—is an environment largely devoid of capable guardians.
As a whole, I believe these nine papers speak to the current state and future promise of cybercriminology. Currently, we are building a large body of empirical studies that speak to patterns of victimization and perpetration. With respect to victimization, we have learned a lot about who is likely to be victimized and how the patterns of victimization vary by type of cybercrime. We also have a good understanding of the activities that increase the likelihood of victimization, the emotional and financial costs of being a victim, and how people view victims depending on the setting and type of victimization. The body of evidence supporting a slightly modified version of Routine Activity Theory/Lifestyle-Exposure Theory is increasingly impressive, and the papers by Marttila, Koivula, and Räsänen as well as the article by Marcum and Higgins offer additional support for aspects of this theoretical approach.
Similarly, our understanding of cybercrime perpetration has expanded exponentially in recent years. While finding samples of cybercriminals is always a challenge, the growing body of evidence suggests that the behavior of cybercriminals is largely explained by the same set of factors that can account for the behavior of more traditional criminals. That is, cybercriminals tend to have low levels of self and social control, are largely unsupervised, experience strains, and learn the how, when, and why of their crimes from their associates. The papers in this issue offer additional support for techniques of neutralization, social learning theory, and self-control theory. While there are nuanced differences in how some criminogenic factors play out in the virtual and offline worlds, our existing theories appear to be robust as many of our theories apply to both online and offline criminal behavior. A number of the differences that exist largely relate to the asynchronous nature of many online interactions. The fact that online interactions can occur synchronously as well as asynchronously expands our networks and provide additional opportunities for others beyond our immediate environment to influence us and for us to commit crimes. The full ramifications of these changes in social networks, criminogenic forces, and criminal opportunities are not understood; however, we understand these far better today than we did even just a few years ago.
We also have a far greater understanding of the techniques of committing cybercrimes. We know considerably more about the use of the Dark Web to find and purchase illegal goods and services, and we have learned that the Surface Web plays a significant role in computer-dependent crimes. Moreover, as the article by Miller and Miller highlights, information technology has helped blur the line between legal, pseudo-legal, and illegal behaviors. What work in this area really highlights is how difficult it is to monitor and police the internet. While there is certainly social control exercised on the internet, there are limits to the effectiveness of this control (see Hawdon et al., 2017 ). Yet, by understanding the patterns of victimization, the underlying causes of perpetration, and the techniques that facilitate cybercrime, we become better armed in designing strategies to prevent it, defend against it, mitigate its adverse effects, and prosecute those who commit it. All of the articles included in this issue further that understanding.
The Special Issue
The process of selecting the articles for this special issue was perhaps unusual but also rather intensive. The process began by me inviting a group of scholars to submit manuscripts for the special issue. I selected these scholars because I knew of their work and was confident they would submit quality papers that covered a wide range of topics in the area of cybercrime. After discussing their planned submissions with the authors to assure there would be good topic coverage, the authors submitted their paper. An anonymous scholar and I reviewed these initial submissions (the anonymous scholar served as a typical double-blind reviewer). Each contributing author also reviewed one or two of the included articles. Authors then revised their work based on the reviewers’ comments and resubmitted the papers. Each contributing author was then asked to read all nine revised papers. Then, the authors and I took advantage of the brief pause in the COVID-19 pandemic and gathered for a two-day workshop in Asheville, North Carolina as part of the Center for Peace Studies and Violence Prevention’s annual research workshop program. The lone exception to this was our Finnish colleagues who were unable to get a special visa to visit the U.S. at that time. These colleagues joined the workshop via Zoom. The authors/workshop participants then discussed and provided feedback on all of the articles. The authors then made final revisions to their papers based on these discussions. Thus, these papers have been through three rounds of revisions. As the editor of the special edition, I am proud of the finished product.
is a professor of sociology and Director of the Center for Peace Studies and Violence Prevention at Virginia Tech. Dr. Hawdon’s research focuses on how communities influence the causes and consequences of violence. He is currently researching how online communities influence online hate, extremism, political polarization, and cybercrime. Since 2013, he and his colleagues have collected multiple waves of data on online hate speech and extremism in the Finland, France, Germany, Poland, Spain, the United Kingdom, and the United States. His recent work has been funded by the National Institute of Justice, the National Science Foundation, and The Commonwealth Cyber Initiative. He has published eight books and over 130 articles, books chapters, and technical reports.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
- Albanese JS. Fraud: The characteristic crime of the 21st Century. Trends in Organized Crime. 2005; 8 :5–16. doi: 10.1007/s12117-005-1033-9. [ CrossRef ] [ Google Scholar ]
- Cohen LE, Felson M. Social change and crime rate trends: A routine activity approach. American Sociological Review. 1979; 44 (4):588–608. doi: 10.2307/2094589. [ CrossRef ] [ Google Scholar ]
- Federal Bureau of Investigation . 2020 Internet crime report. U.S. Government Printing Office; 2021. [ Google Scholar ]
- Hawdon J, Costello C, Ratliff T, Hall L, Middleton J. Conflict management styles and cybervictimization: An extension of routine activity theory. Sociological Spectrum. 2017; 37 (4):250–266. doi: 10.1080/02732173.2017.1334608. [ CrossRef ] [ Google Scholar ]
- Hawdon J, Parti K, Dearden TE. Cybercrime in America amid COVID-19: The initial results from a natural experiment. American Journal of Criminal Justice. 2020; 45 :546–562. doi: 10.1007/s12103-020-09534-4. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Morgan, S. (2020). Cybercrime to cost the World $10.5 Trillion Annually by 2025. Cybercrime Magazine , November 13, 2020. https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
- Reinhart, R. J. (2018). One in four Americans have experienced cybercrime. Gallup Politics . https://news.gallup.com/poll/245336/one-four-americans-experienced-cybercrime.aspx
- Roser, M. H. R. & Ortiz-Ospina, E. (2015). "Internet". Published online at OurWorldInData.org. Retrieved from: ' https://ourworldindata.org/internet ' [Online Resource]
- Sykes GM, Matza D. Techniques of neutralization: A theory of delinquency. American Sociological Review. 1957; 22 (6):664–670. doi: 10.2307/2089195. [ CrossRef ] [ Google Scholar ]
- We Are Social, & DataReportal, & Hootsuite. (2021). Global digital population as of January 2021 (in billions) [Graph]. In Statista . Retrieved September 24, 2021, from https://www.statista.com/statistics/617136/digital-population-worldwide/
- Entertainment
- Environment
- Information Science and Technology
- Social Issues
Home Essay Samples Crime
Essay Samples on Cyber Crimes
The issues related to digital crimes or illegal actions in cyberspace are not only typical for Data Science or Law students because cyberbullying also has a strong effect on a person’s emotional state. Therefore, most college students that deal with Sociology, Education, and Healthcare also research the topics that relate to cybercrimes. As a way to keep your paper well-structured, you can check our free cyber crimes essay that has it all – from introduction with a thesis to topic sentences and a conclusion that can be used as a great reference as you write and think over inspiring ideas. Remember to include statistical information and surveys to help your paper be reliable. Make sure that you paraphrase your sources or use direct quotes with a proper referencing style.
Causes and Effects of Cyber Crime: Unraveling the Digital Threat Landscape
Cyber crime, a rapidly growing menace in the digital age, has profound effects on individuals, organizations, and society as a whole. This essay delves into the complex causes and effects of cyber crime to examine its far-reaching consequences on privacy, economy, and security. By understanding...
- Cyber Crime
- Cyber Crimes
Cyber Crime: Navigating the Digital Underworld
Welcome to the realm of technology and its dark counterpart – cyber crime. In our interconnected world, where the digital landscape continues to expand, the prevalence and sophistication of cyber crimes have become a pressing concern. This essay delves into the intricate web of cyber...
Digital Forensics: The Science Behind Solving Cybercrimes
1. Introduction In the current era, the majority of the population relies heavily over the usage of technology for everything. From social media to businesses conducting their operations there is increased reliance and usage of technology. Hence, as society evolves and technology marches forward our...
- Cyber Security
- Digital Devices
Digital Evidence: The Key to Successful Investigations & Prosecutions
1. Introduction Almost all crimes nowadays have some form of digital evidence associated to them. Digital evidence by its nature is very fluid and transient but the digital investigation takes a lot of time to complete. One small change in digital evidence can make the...

Analysis of Russian Unethical Interference in the US 2016 Elections
Conduct is the aspect of self-determination, a legal term that incorporates the right of the people to make decisions for themselves, both the political affiliations (at a methodical stage) and their forthcoming destiny (at a more granular stage of policy). It is evidently this more...
Stressed out with your paper?
Consider using writing assistance:
- 100% unique papers
- 3 hrs deadline option
Cyberbullying: Locating The Problem And Finding Solutions To It
Cyberbullying refers to a type of harassment that is carried out using electronic methods such as through social media platforms and other websites. Cyberbullying has become an issue of concern, especially among the teenagers who are the main users of social media platforms (Hinduja and...
- Cyber Bullying
Ways Of How To Prevent Cyber Bullying In Modern Society
Introduction Have you heard the word cyber bullying? Cyber bullying is a new word that comes from cyber, which means virtual space, and bullying, which means violence. In the article 'Protecting Victims of Cyber bullying', Champagne said that 'Cyber bullying is defined as repeated harassment...
Technology As A Tool To Stop Cyber Bullying In Schools
Cyber bullying is such a hard concept to talk about, everyone has different opinions on the definition, or how to handle it. This paper discusses how technology can make a difference in helping stop cyber bullying, and if these situations are ethical. The paper will...
- Public School
The Issue Of Cyberbullying In Public Schools
Abstract This paper discusses the issue of Cyberbullying in our society. It examines the fundamentals of cyberbullying such as what cyberbullying is, the methods used to cyber bully, and the types of cyberbullying that occur. It will also explain how to prevent cyberbullying from taking...
Cyberbullying: The Rise Of A Problem Because Of Social Media
Social media has increased over the years of the 21st century and is a way for many teenagers to explore and communicate. Social networking sites, also known as SNS, or social media are places of communication that allows users to get involved, interact, and create...
Ways To Prevent And Solve The Issue Of Cyber Bullying
My topic is cyber bullying on social media, Cyber bullying is the act of using digital devices in order to harass, threaten or bully someone on social media. In this research paper, I will focus on the impact of cyber bullying on adolescent and why...
Overview of the Causes and Effects of Cyber Bullying
This paper will talk about the causes and effects of cyber-bullying, but first I will define the term. Cyber-bullying is often done by children who have increasingly early access to these technologies. The problem is compounded by the fact that a bully can hid behind...
Finding The Solutions To Cyberbullying: Opening A Discussion
There have been numerous students that feels reluctant to report cyberbullying incidents to adults in schools for various reasons. Cyberbullying is defined as bullying that takes place using digital technology. This may include social media networks, text messages or email. Recent research studies have shown...
The Rise Of Identity Theft In The American Society
According to the US Postal Service, identity theft is America’s fastest growing crime, a person must be very proactive and take significant steps to reduce exposure to identity theft by physical means or cyber attack. Unless an individual diligently checks credit history, financial accounts, and...
- Identity Theft
The Effects Of Cybercrime And Protection Against Identity Theft
The internet has improved and simplified principle parts of our everyday life, and while composing a manually written mail that takes days to be received, the web has made messages instantly received. It made communication with individuals around the globe much less demanding, and conversely...
The Destruction Brought By Identity Theft
Cybercrime is is increasing in skyrocketing way it is getting out of control. We are hearing about it every single day and it tough to control. There are different types of cyber crime that we hear on daily basis like Phishing, social engineering, Identity theft,...
The Safety And Protection Against Identity Theft And Cyber Crime
Cybercrime is increasing in skyrocketing way it is getting out of control. We are hearing about it every single day and it is ought to control. There are different types of cybercrime that we hear on daily basis like Phishing, social engineering, Identity theft, malware...
Methods Of Protection Against Identity Theft
Abstract In today’s world, not a day goes by that someone is not affected by cybercrimes or cyberterrorism which go hand in hand. It is important for the government and businesses to constantly stay up to date with the latest technology to help prevent a...
The Increase Of Identity Theft And Cyber Crime
Identity theft is intentionally use of someone else’s identity, usually as a method to gain financial, credit, or any other sort of benefits in his/her name. The victim of Identity theft could possibly suffer serious consequences especially if they get left held responsible for the...
Diving Into Dark Web: Delving Deep Into The Dark Side Of The Internet
Abstract The Deep Web is so large for search engines to cover completely. So, the Deep Web is the long tail of what’s left out of the whole Internet. The dark web subset of deep web is the World Wide Web content that exists on...
Should The Internet Be Controlled More Strictly In The U.s.
The Internet is one of the most important Inventions of the 20th Century. The internet is the work of dozens of pioneering scientists, programmers, and engineers who each developed new features and technologies that eventually merged to become the ‘’ information superhighway ‘’ we know...
- Julian Assange
How Cyberbullying Can Harm Person's Reputation and Affect Their Life
Cyberbullying is a crime that takes place online when one person attacks another through the internet. Before technology evolved bullying happened face to face, but through the years computers and cell phones came around and that's when cyberbullying was born. The effects of cyberbullying are...
Pros and Cons of Insanity Defense, Death Penalty and The History of Cybercrime Prosecution
What is the history of the insanity defense? The insanity defense can be dated back to around the 16th century. This defense was expanded upon by British Courts in order to devise the ‘wild beast’ test. This test disallowed a defendant from being held responsible...
- Death Penalty
- Insanity Defense
Prevention of Identity Theft Based on Real Examples
In this emerging world of technology, there are many people who use it for good; from connecting with friends on social media, to those donating to online support groups. However, emerging from the same world you have those who use the internet as a means...
- Crime Prevention
Internet Crimes And Their Preventions
Nowadays internet crimes are a common problem in the world, and everyone exposes to these crimes. These crimes can cause very serious damage to the individual and society. Many people and companies had suffered from the impact of these types of crimes. To protect us...
A Few Solutions To Prevent Cyber Warfare
In today’s technologically advanced world, cyber warfare and espionage, and cyber crimes in general have become an increasingly dangerous threat as almost every government entity and individual is exposed to the cyberspace in some way or the other. The first step that we should take,...
- Network Security
Cyber Attacks – The Challenge Of Modern World
Technology nowadays has become a part of our life and without a doubt it has already becoming one of the most crucial aspects of our life as well as the community. Even a simple task as string a hot coffee in the proses of making...
- Computer Security
Best topics on Cyber Crimes
1. Causes and Effects of Cyber Crime: Unraveling the Digital Threat Landscape
2. Cyber Crime: Navigating the Digital Underworld
3. Digital Forensics: The Science Behind Solving Cybercrimes
4. Digital Evidence: The Key to Successful Investigations & Prosecutions
5. Analysis of Russian Unethical Interference in the US 2016 Elections
6. Cyberbullying: Locating The Problem And Finding Solutions To It
7. Ways Of How To Prevent Cyber Bullying In Modern Society
8. Technology As A Tool To Stop Cyber Bullying In Schools
9. The Issue Of Cyberbullying In Public Schools
10. Cyberbullying: The Rise Of A Problem Because Of Social Media
11. Ways To Prevent And Solve The Issue Of Cyber Bullying
12. Overview of the Causes and Effects of Cyber Bullying
13. Finding The Solutions To Cyberbullying: Opening A Discussion
14. The Rise Of Identity Theft In The American Society
15. The Effects Of Cybercrime And Protection Against Identity Theft
- Jeffrey Dahmer
- Domestic Violence
- Verbal Abuse
- Animal Cruelty
- Child Abuse
- Physical Abuse
- Youth Violence
- Drug Trafficking
- Criminal Behavior
Need writing help?
You can always rely on us no matter what type of paper you need
*No hidden charges
100% Unique Essays
Absolutely Confidential
Money Back Guarantee
By clicking “Send Essay”, you agree to our Terms of service and Privacy statement. We will occasionally send you account related emails
You can also get a UNIQUE essay on this or any other topic
Thank you! We’ll contact you as soon as possible.
- Skip to main content
India’s Largest Career Transformation Portal
Essay on Cyber Crime for Students in English [Easy Words]
January 12, 2021 by Sandeep
Essay on Cyber Crime: Computer related networks that involve the use of computers, networks and gadgets can be interconnected to a cybercrime. In such crimes, the security of networks, persons, institutions or a whole nation could be at risk and threat. Hackers steal confidential data in unethical ways and utilize this information and data for spurious purposes. Cybercrimes are high functional frauds that can wipe off big online financial transactions and transfer the entire amount into criminal accounts.
Essay on Cyber Crime 500 Words in English
Below we have provided Cyber Crime Essay in English, suitable for class 6, 7, 8, 9 & 10.
Cyber Crime involves digital devices ( computer , hardware device, or network) as tools or targets. It can be defined as an unlawful act that is done to harm someone. It is one of the most complicated issues in the cyber world. Many people think cyber crime refers to targeting people and stealing their money. However, that is not the case.
Cybercrimes may include credit card frauds, voice phishing, distribution of viruses, cyber-stalking, child pornography, forgery, unauthorized access, etc. This is a fast-growing area of crime that happens over the internet . With the advancement in technology, we are leaning towards the internet all the more. It is needed for numerous activities like social networking, gaming, transaction, e-commerce, online studies, shopping, job seeking, etc.
The first case was recorded in 1820. It has been said that in these recent few years, at least 4000 cases have been filed in Malaysia. All of these cases consist of fraud, malware; file loss, hack threats, and denial of services. Major crime areas as per the government include piracy, cracking, and cyber-terrorism. Since more and more people are using computers, these types of cyber crimes will only keep increasing.
India and many other nations are dealing with the same crisis. An article reported China in itself has near about 300 million internet users. Criminals rely on computers as it is networked internationally. These criminals are organized and individual hackers. They mostly get involved for two reasons. The first one is that they want to prove themselves to be excellent at breaching computer software. The second reason is for monetary purposes. They mostly target big companies, organizations, or banks.
The increase in the speed of the internet has, in turn, increased the rate of circulation of data. The measures for investigation, control, and prevention of these illegal activities are very important to safeguard all the organizations. Highly skilled Cyber Crime expertise must be obtained by our Government. Doing so will help regulate this grave issue.
Types of Cyber Crimes
There is a range of activities that fall into the category of cyber crime. Let us take a look at them.
- Hacking: It refers to breaking into a person’s computer system without his/her knowledge or consent. It is also known as unauthorized trespassing in the cyber world. Hackers can access sensitive information of the user (like identity details, passwords, and credit card information).
- Cyber Stalking: This is one of the worst ways to harass a person. Victims of cyber-stalking are subjected to tons of messages and emails by the stalkers. Not responding to these often leads to grave outcomes.
- Identity Theft: Here, the person’s identity gets stolen. This includes his/her name, bank details, social security number, birthday, credit or debit cards, etc. This information is misused by the criminals to commit fraudulent activities (like applying for new credit cards, getting medical services, collecting loans) which hamper the owner’s record.
- Phishing: This is a kind of email fraud wherein various mails are sent to the people. The content of the mail mostly seeks financial information of the person. These emails might look like they are coming from an authentic source (but they are not).
- Malware: It is Internet-based software that is programmed to damage a computer system.
- Computer vandalism: This type of cyber crime destroys a computer’s data by transmitting viruses.
- Theft: It occurs when a person violates copyrights regulation. This is mostly noticed while downloading music, movies, or even games.
Laws related to Cyber Crimes
The Government has come up with several strict laws related to cyber crimes. These laws will help safeguard our interests. Also, they will be beneficial for controlling these crimes. Now, the police stations are equipped with cyber cells that quickly monitor the problem. In India, cyber crimes are usually registered under three categories. These are the IT Act, The Indian Penal Code, and The State Legislation’s.
The Ministry of Home Affairs has advised the State government to include facilities like technical infrastructure and skilled manpower to curb the cases of cyber crimes. Cyber Crime Police Officers can now receive training at the Forensic Lab of CBI.
Kerala, Tripura, Assam, and many other Indian states have started the training procedures. The Ministry of Home Affairs has also come up with an open platform (I4C) to fight against these crimes. I4C (Indian Cyber Crime Coordination Centre) helps victims to raise their complaints.
How to Prevent Cyber Crime
Now that we have these cyber laws, it is our responsibility to take steps to prevent these crimes. Protection measures must be taken if we want to secure ourselves. First of all, we must be aware of our online transactions. We can lose important information if our computer has spyware (and we are unaware of it).
237 Cyber Security Essay Topics, Ideas, and Examples
🏆 best cybersecurity essay topics and examples, 💡 most interesting cybersecurity topics to write about, 👍 good essay topics on cybersecurity, ⭐ simple & easy cyber security essay topics, ✍️ cyber security topics for college, ⌨️ good cyber security essay examples and topics, 🖱️ compelling computer security research topics, ❓ cyber security paragraph questions.
- Sources of Digital Forensic Data With live system data, the aim of the investigator is to capture information concerning volatile data that may disappear when a device powers off or it is disconnected from the network.
- Benefits and Dangers of Ethical Hacking The advantages of ethical hacking The following are some of the advantages associated with the use of ethical hacking in an organization. We will write a custom essay specifically for you by our professional experts 808 writers online Learn More
- Ethical and Illegal Computer Hacking For the ethical hackers, they pursue hacking in order to identify the unexploited areas or determine weaknesses in systems in order to fix them.
- Global Cybersecurity in the 21st Century Research Question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Artificial Intelligence in Cybersecurity The use of AI is regulated by a large amount of documentation, which should take into account the current legislation in the country of use and ethical issues related to AI, many of which have […]
- Cybersecurity Threats to Educational Institutions The rapid adoption of digital solutions is exposing schools to the cyber-security threat, which is currently the biggest concern that these institutions face as they make a complete shift from the analog to the digital […]
- The Future Career in Cybersecurity During the interview, it is necessary to highlight the knowledge of working as a graph as a mathematical theory and the simple use of spanning trees in cybersecurity.
- Hacking as a Crime and Related Theories The move to embrace the novel technology has led to the emergence of a new form of crime and behavior referred to as “hacking”. Today, the term is used to refer to individuals engaged in […]
- Kosovo 1999: Hacking the Military The paper addresses the motivation behind the attacks, the methods of attack, and the responses of the defenders to these attacks.
- Importance of Army Cybersecurity This includes bringing awareness to the cybersecurity issue, involving more people to combat the problem of cyberattacks, and organizing the information based on specialty and tasks that must be completed.
- Assessment of Cybersecurity Program Maturity Padgett-Beale Financial Services must choose the appropriate framework and standards, determine required regulations and laws to comply with, and identify the best practices for maturity assessment to achieve an impenetrable cybersecurity management program.
- Banking Sector Cyber Wars and International Hacking Flaws in the network allow hackers to access the systems. In efforts to reduce hacking in the country, a number of police units have been formed.
- The Impact of Mobile Devices on Cybersecurity The very popularity and extent of the use of mobile computing devices and the internet creates a special vulnerability to businesses.
- Hacking: Positive and Negative Perception The possible advantage of cooperating with hackers for security systems mangers of international organizations and governmental organizations is the probability to recruit them and use their knowledge to empower different organizations to improve their security […]
- Cybersecurity and Encryption Analysis: VPN, PKI & Firewalls The end-to-end encryption is the more complex process that can be discussed as the data encryption between the client application and the server provided with the help of additional technologies.
- Cyber Security Issue: RansomWare Until the victim pays a specific amount of money to the attackers within a particular time, cybercriminals can use the virus mentioned above to access the user’s sensitive personal or organizational information. The infection and […]
- Technology Acceptance Model and Cybersecurity In this context, the implementation of TAM in the company is critical for the effective functioning of the organization. In this context, the introduction of TAM leads to the fact that satisfaction directly affects the […]
- Cybersecurity Workforce in Emergent Nations The lack of help from developed countries in the training and education of a cybersecurity workforce for developing nations can negatively affect the former. Public and private organizations also contribute to the development of cybersecurity […]
- Cybersecurity and Social Networks Recently, there have been many trends the security of information and communication technologies, in particular, due to the expansion of the reach of social media which increase the size of social network, which has taken […]
- The Different Sides of Hacking In a general sense, computer hacking involves the intrusion of the computing privacy of other people, damage of the computing property of other people like files, software etc.or the theft of private information by unauthorized […]
- Sony Corporation Hacking and Security System The organization had to stop the hackers and ensure information did not flow freely but it was unfortunate, as the company sought the services of the California court because it had no capacity to deal […]
- Computer Forensics Tools and Evidence Processing The purpose of this paper is to analyze available forensic tools, identify and explain the challenges of investigations, and explain the legal implication of the First and Fourth Amendments as they relate to evidence processing […]
- Cybersecurity in the Financial Services Industry In reaction to ransomware attacks, a business such as a bank may have to spend a substantial amount of money, which may cause customers to lose faith in the safety of their funds.
- Cyber Security Technologies The technology is regularly designed to alter the attack surface of a network, making it hard for attackers to access a system and reducing the susceptibilities and predictabilities available at any time.
- Ethical, Legal, and Social Implications of Hacking So as to discuss the ethical, lawful, and ethical inferences of this concern, people need an understanding of the phrase ethical hacking.
- Cybersecurity Dilemmas: Technology, Policy and Incentives The value of the assets determines the amount of time and resources that can be invested to protect a particular system.
- The Department of Homeland Security’s Cybersecurity Mission Cybersecurity is evolving rapidly, and DHS’s cybersecurity mission is equipped with models adapting to the ever-changing security and information dynamics. The DHS cybersecurity mission is designed with models that adapt to changing dynamics and landscapes.
- The Biggest Cybersecurity Treat to Expect First of all, all employees who somehow use the Internet of Things devices and have access to the corporate IoT network are to be trained to utilize it correctly.
- Securing Offboarded Employees: Modern Cybersecurity Strategies Disgruntled employees can be potentially dangerous to the whole company’s well-being due to cybercrimes that can affect the entire company’s work.
- Advanced Research Methods in Cybersecurity Performance measurements refer to the internal functions of the company and ways in which cybersecurity management contributes to the accomplishment of critical tasks within the firm.
- Gaps in Cyber Security Caused by BYOD In conclusion, these vulnerabilities caused by the insufficient regulation and general unpreparedness of organizational and public networks expose facilities that use BYOD to severe risks of data leaks and hacker attacks.
- Cybersecurity Threats in Physician Practice The purpose of the source is to inform readers of the strategies to help healthcare professionals identify, avoid and respond to ransomware dangers.
- Digital Forensic Analysis of Fitbit The comparison of the results and the analyses of the data as a result of the research gave the authors of the article a conclusion in regards to the methodology that has evidence-based results in […]
- Cybersecurity Contingency & Incident Review Process Next, it is necessary to implement various stages of digital transformation of cybersecurity, which include improving the maturity of enterprises in cybersecurity issues and the use of new solutions.
- Forensic Accounting and Cyber Security The recent trend of increased exposure due to the access of extended financial and fraud concerns by social media and the internet has necessitated the need to curb the tendency.
- Hacking Prevention: Mobile Phone Anti-Virus However, the less discussed and addressed subject is the cybersecurity of mobile phones, which are among the most used and vital devices for the majority of the population.
- Legal Risks of AI Cybersecurity in the European Union Thus, this paper seeks to fill the gap on whether or not safety and security can be covered in cybersecurity for AI by the same rules that are used in private law. The EU has […]
- Cyber Security: Critical Infrastructure Protection Objects of forensic science are storage mediums that are not part of other devices and which fulfill the function of information storage as the main one.
- Cybersecurity: Firewall and Testing The most effective and reliable way to test a software program of a firewall for its security would be firewall penetration testing.
- Relation Between Cybersecurity and Cybercrime Meanwhile, one should not assume that cybersecurity is the prerogative of technicians and software engineers only since the consequences of a breach will affect the entire business or private life of those not associated with […]
- Cybersecurity in 2021-2022: Cybersecurity Advancements In IoT, Blockchain is being utilized to protect connected devices through decentralization and encryption, adding to the evolving nature of system security.
- Encryption and Hacking Techniques There are several advantages of text-based encryption, and they include the fact that the data can be used across different devices through the concept of multi-device encryption techniques.
- The US, Russia, and China Cybersecurity Conflict The current situation in the space of cybersecurity provides a significant example of how complicated this area of National Security and its influence on foreign politics can be.
- Cybersecurity and Geopolitics Relationship Provision of security to information technology and the tools used in the technology is also paramount. Cyber security is also described as measures and operations that are put in place to be to ensure that […]
- Cybersecurity and Corporations’ Input to It Whatever committee or board of directors is in charge of overseeing cybersecurity risks, the primary goal is for an organization to have an integrated approach to preparing for and protecting against cyber incidents and detecting […]
- Cybersecurity and Corporations’ Role First, it is worth indicating some of the key reasons for corporations to be in the center of cybersecurity discussion. In April, the company rejected the possibility of a data breach and apparently did not […]
- Cybersecurity and Geopolitical Issues Geopolitics is the study of integration and effect of earth geography and physical outlay on the political structures, and international relations and reforms that affect the same at different levels.
- Virtual Reality and Cybersecurity As a result, it is the mandate of the framework entities to establish solutions to the inherent barriers to the implementation of the business plan.
- Cybersecurity Policy Regarding Critical Infrastructures The article will explicitly analyze the processes behind cybersecurity development as well as the impact of the cybersecurity polies to the global security policies.
- Cybersecurity: Critical Infrastructure Control Systems The most vital stages of this nature include the analysis of the situation, the assessment of goals to make sure that they are realistic, and the expected effectiveness of implementing new policies.
- Cybersecurity in the United States Thus, the current research project is going to address the following question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Cybersecurity: The Matter of National Security However, if the security of cyberspace is critically evaluated and all the risks eliminated, cyberspace can be an asset that will continue to transform the world.
- Cybersecurity Advancements in Electric Power Systems Therefore, there will be an increase in the volume of work performed, a reduction in design time and an increase in the quality of work through the use of technology in the next five years.
- Cybersecurity Dangers and Their Analysis The officer clicks the file, and the malware attacks the system stealing the data and bypassing some security measures. The cyber security framework under the NIST is helping organizations to understand and manage cybersecurity.
- The US and Apple Relationship in the Field of Cybersecurity In this paragraph, an important aspect is to determine the degree of interaction between the two structures. This paper argues that in times of crisis, such powers should be surrendered to the more considerable public […]
- Data Management and Cybersecurity Namely, the principal standard of the HIPAA, as well as the concept of cybersecurity, have proven to factor into some of the key aspects of my professional and personal life.
- Cybercrime and Cybersecurity as Challenges One will also learn the defensive cyber security technologies and techniques used in modern organizations to protect systems data and achieve Knowledge of the maintenance and design of reliable and safe information systems.
- Digital Forensics Tools and Software One of the most famous software programs for digital forensics is Autopsy, a toolkit that examines the images present on a device’s hard drive.
- Tim Cook’s Leadership and Apple’s Cybersecurity In this paper, the main types of leadership that can be applied to the leadership style of Tim Cook are considered.
- Cybersecurity Weaknesses: The Case of LinkedIn The Internet has become the largest storage of personal and corporate information in the history of the world. The data relating to hundreds of millions of users was leaked online in the Dark Web segment […]
- The Importance of Leadership Skills in the Field of Cybersecurity The wider the information networks cover the world, the more frequent and dangerous cyber-attacks are, and the more cybersecurity specialists become in demand.
- White Hat and Black Hat Hacking On the other hand, White Hats work with companies and help them identify weaknesses in their systems and fix relevant vulnerabilities to ensure that attackers cannot illegally gain access to data.
- Modern Cybercrime: Most Recent Threats and Cybersecurity This is due to the fact that the Internet is a public open system in which data moves uncontrollably and can be discovered, intercepted, or stolen if the correct knowledge of the equipment is applied.
- Cybersecurity Strategy, Law, and Policy Team Assignment It may be critical to prevent cybersecurity breaches or data leaks to maintain the effective functioning of the government and ensure the sovereignty of the country.
- The Cybersecurity Threat Landscape The threats may come from different sources, and the criminals may focus on distinct vulnerabilities in the security of the system.
- Public-Private Partnerships for Election Systems Cybersecurity In public contracts, the private sector provides the service directly to the public and bears all the associated end-user risks. Private parties can use all the gained knowledge and expertise to conduct security assessments of […]
- Solving the Cybersecurity Workforce Crisis Since cyber security specialists are highly demanded in the current market, the private sector has been offering increased compensation in comparison with the government sector, which has led to decreased interest in IT positions in […]
- Cryptographic Algorithms: The Use in Cyber Security Cryptographic protection of a system depends on two factors, 1) the strength of the keys and effectiveness of associated protocols, and 2) protection of said keys via key management.
- Cybersecurity Implementation Plan for PBI-FS Therefore, the current plan will define the objectives, goals, and objectives, and scope of the implementation. The implementation of the cybersecurity management plan pursues both business and project goals and objectives.
- Facebook Compatibility With Padgett-Beale Cybersecurity Philosophy The purpose of this paper is to evaluate Facebook on the subject of cybersecurity and compatibility with Padgett-Beale’s cybersecurity philosophy and goals.
- Cybersecurity Issues in Industrial Critical Infrastructure This way, the author analyzes the potential impact of various cybersecurity threats capable of interrupting the stability of the supply of energy to communities and industries.
- Supply Chain’s Cybersecurity and Risk Analysis Since there are so many parties involved, it is crucial to assess every part of the process, from obtaining the raw material to the delivery to the customer. Cybersecurity is the critical answer to most […]
- Amazon Inc.’s Business Profile and Cybersecurity On the contrary, Amazon has continued to rise in the industry and has expanded from selling only books to trade in nearly any product and providing various services.
- Integrating Cybersecurity Framework With Information Technology Governance Frameworks ISMS builds a model of relationships between the aforementioned activities, and, as Almuhammadi and Alsaleh argue, companies “understand their cyber security risk management approach and what are the processes in place to manage the risk”.
- Cybersecurity, Ethics, and Privacy in the Global Business Environment Therefore, the purpose of this paper is to cover the types of possible threats and mitigation methods, explain the importance of a continuity plan, and outline ethical and privacy concerns for organizations.
- Cybersecurity: Multi-State Information Sharing and Analysis Center The MS-ISAC also advises the agencies on the best tools available in the market that provide the best protection of the government systems and data.
- Cybersecurity Strategy and Plan of Action Padgett-Beale’s primary intention of merging the company was to relocate the call epicenter to a property owned by the company roughly 10 miles from the company’s previous location and opposite the newly released Padgett-Beale resort.
- Digital Forensic Examination, DVR Another application would be to determine the network’s or a user’s IP and track their online activity. The information can be used to determine an unknown individual’s location and possibly identity, or for a known […]
- Cybersecurity and How It Impacts Identity Protection and/or Ransomware Firstly, organizational leadership should not undervalue the importance of cybersecurity since the risk of losing the data stored in the company’s database may harm the corporate reputation and trustworthiness.
- Cybersecurity in the Energy Sector The stable supply of energy is the key to the normal functioning of American society, as it fuels all essential industries that ensure the vitality of the nation.
- Cybersecurity for Open Data Initiatives Governments continue to play a vital role in the open data movement.Data.gov was developed under OPEN Government Data Act; this is Title II of Foundations for the Evidence-based Policymaking Act.
- Sifers-Grayson Company: The Cybersecurity Breach Finally, the recommendations, as per the improvement of the incident response capability, are introduced to ensure the elimination of the identified drawbacks and the compliance of the engineering company with the security requirements presented by […]
- Computer Forensic Incident All evidence should be collected in the presence of experts in order to avoid losing data as well as violating privacy rights.N.
- Cybersecurity Necessity and Benefits Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender’s cognitive state, possibilities for automation, and an attacker’s subjective traits.
- Cybersecurity Incident Response and Risk Minimization Such plan or strategy represents a list of steps, which should be immediately taken in case of a cyber-attack to limit the potential damage and reduce expenses.
- Internet Hacking and Cybersecurity Conundrum Analysis Many people have gained access to computer systems, the Internet, and related products and services, leading to the emergence of cyber-related threats. Cybersecurity improvements are vital to the continuous developments in information technology, national security, […]
- Internet Hacking and Cybersecurity Conundrum Therefore, the increasing number of attacks during the pandemic could be handled with the help of machine learning and have the numerous human workers assigned to less crucial tasks that actually require human judgment.
- Government and Private Sector in Cybersecurity Richards highlights the government’s leading role in the context of cyber threats while stating that the number of attacks is still on the increase.
- Ethical Hacking: Is It a Thing? Computer programmers implemented the term ‘hacker’ at the beginning of the 1960s in the framework of a positive definition for an individual of dexterous software development skill.
- Computer Network Security Legal Framework With the introduction of cloud computing, the need of data protection has been rising significantly within computer networks to facilitate the protection of Intellectual Property among the users.
- Computer Forensics and Audio Data Retrieval Advanced technology in the modern society has contributed to the increase in computer and computer supported criminal activities due to the soaring increases in the number of internet users across the world and computerization of […]
- Cyber Security: Security Audit On the issue of computers and laptops, I learned from the administration that each laptop was specifically assigned to a single person who was entrusted with a password known to him and the organization’s administration […]
- Computer Forensics: Data Acquisition Data acquisition is a branch of computer forensics concerned with the retrieval of data originally located on a suspect medium such as a hard drive.
- Computer Forensic Timeline Visualization Tool The necessity to save time in computer forensic investigations is the basis of the tool that Olssen and Boldt came up with.
- The Qatar Independence Schools’ Computer Network Security Control The result of the interviews mainly outlined several common themes and patterns in terms of the design of the proposed security system.
- Computer Sciences Technology and HTTPS Hacking Protection Many are assured when they see the SSL symbol of a lock at the bottom of the screen and feel their information is confidential and the website is protected.
- Moral Issues Surrounding the Hacking of Emails The devises to enter into another people’s email and steal information in the email is called Email Hacking. It should noted that stealing of valuable information through email hacking has become a phenomenon in both […]
- Hacking Government Website From the View of Right and Justice Computer crimes refers to the use of the computer system or the internet to commit criminal activities A computer crime is an unlawful act done via a computer or a network and some of the […]
- COBIT5 vs. ITIL4 in Cybersecurity Significantly, ITSM is the alignment of information systems and enterprise IT services with business and the needs of the customer who is the end-user.
- Cybercrime and Cybersecurity: Data Protection One of the biggest Constitutional concerns for electronic surveillance as well as search and seize of evidence is protected by the Fourth Amendment which limits any such activities against the private persons, property, or effects […]
- Cyber Security Threat and Its Impact on the UAE In 2018, the UAE government and private sector were the subject of a total of 230 cyber attacks, as The National UAE reports.
- Agility and Situational Awareness in the Context of Cyber Security As a result, measures should be implemented to create cyber security, which will protect the information resources of an organization from damage.
- Research Tools Used by Computer Forensic Teams Computer Forensics is a branch of digital forensics which is used in “identifying, preserving, recovering, analyzing and presenting facts and opinions about the information”.
- Business and Cybersecurity Research Thus, a more sophisticated theoretical approach is taken to represent the goals of cyber security. A mediating variable, in turn, is the effectiveness of cyber security measures perceived from theory- and practice-related standpoints.
- Quality Control of Digital Forensics The quality control over computer forensic products is necessary because of the growth of the Internet services. Thus, the investigator and the lab are challenged not only with solving a case but also providing the […]
- Windows Logs: Improving Cybersecurity The specified event points to the need to configure the current settings of the master browser in order to address possible security issues and close the loopholes that potentially make the computer vulnerable to malware.
- Cybersecurity: Weak and Strong Passwords The strong passwords have a low probability of being guessed because the amount of possible iterations and combinations is extremely high.
- “Evolution of Federal Cyber Security” by J. Roth Even after training, the GAO report continued to demonstrate system control deficiencies due to failures in the identification of enough boundary security mechanisms, breakdown in the need to know, insufficient restriction of physical access, and […]
- US Brokerage Hacking by India Issue The personal accounts of the defendants were used to purchase shares of stocks, following which they hacked into other people’s accounts and made good use of their passwords and usernames.
- Cyber Security in the Energy Sector The organization’s innovation can be catalytic for the change in the industry of energy since the largest sources of carbon emissions are power plants that generate energy by burning fossil fuels.
- Computer Forensics in Criminal Investigation In this section, this paper will address the components of a computer to photograph during forensic photography, the most emergent action an investigating officer should take upon arriving at a cyber-crime scene, the value of […]
- Computer Forensics and Cyber Crime Due to age characteristics, the insufficient educational activity of parents, the provision of unlimited opportunities in the online environment, and also due to the low media literacy of the population, people can become victims of […]
- Computer Forensics: Identity Theft The forensics process that is maintained in the framework of computer-related technologies provides professionals with the opportunity to gather, analyze, and report on the information.
- Cyber Security: Shadow Brokers Hacker Group A concealed group of hackers stole several disks containing secret data belonging to the National Security Agency in 2013; In 2016, they announced an auction to sell off the data they had obtained illegally; […]
- Cybersecurity as a Leadership Challenge Cybercrime can lead to the leakage of important data, system interference, and the delivery of unsatisfactory services to consumers. This sophistication has amplified the insecurity of information systems to the extent of creating more threats […]
- Shadow Brokers Hacker Group and Cyber Security Industry Therefore, in order to prevent the recurrence of such attacks, the N.S.A.needs to strengthen the security system of particularly essential information to eliminate its diversion.
- Deutsche Telecom Company’s Cyber Security The present work deals with the issue of DDoS attacks and builds a case on one of the well-known IT companies to single out the problem, the immediate solutions and preventive practices, and the lessons […]
- Cybersecurity: Deutsche Telekom Company’s Case The example of Deutsche Telekom proves the importance of the development of cybersecurity programs and strategies to protect users and their interests.
- Cybersecurity Risks Affecting Enterprises From a national security standpoint, it is crucial to know and understand the nature of the enemy and be prepared for an increase in cyberterrorism attempts.
- Cyber Security and Employees The major factors that define the thriving of cyber ganging are the insufficient level of employees’ competence, the lack of knowledge about the technical side of information protection, and non-compliance with safety standards.
- Cybersecurity Directives and Laws Describe the National Strategy for the Physical Protection of Critical Infrastructures and Key Assets and how it attempts to protect cyber assets.
- Cybersecurity and Vital Elements The focus of any risk management effort is a standard system or a framework that help organizations and individuals to manage integrity, confidentiality, and data and ensure critical resources availability.
- Emerging Cyber Security Approaches and Technologies These emerging cyber security approaches and technologies are unique and new, and they look promising for securing critical infrastructures in the cyberspace.
- Hacking: White, Black and Gray Hats Living in the era of the Internet and online technology increases the vulnerability of the information stored online and on electronic devices.
- A Duty of Care for Cyber Security Hence, the sensitive data can be easily accessed by cyber criminals in the event that the cloud service is breached by users.
- Digital Forensics: Open Source Tools The National Software Reference Library is a project at the National Institute of Standards and Technology, the primary goals of which are to store all existing software, file profiles, and file signatures and to provide […]
- Digital Forensic Methodology In the event that sufficient information is available, the required system configuration should be developed by ensuring that the forensic software and hardware are established and validated.
- Automotive Industry’s Cybersecurity and Threats It is significant to ensure the security of this system because it focuses not only on the audio and video entertainment but also allows to control navigation system and manipulate the behavior of the car.
- Cybersecurity and Risk Control Implementation The first component of the risk treatment framework refers to the decision not to go through with the procedures that may present a risk; the second one stands for the minimization of the possibility of […]
- Online Predators and Childrens’ Cybersecurity To win the battle against online predators it is important to craft laws that were created by people with a thorough understanding of how perpetrators utilize information systems and the Internet to commit sexually-related cyber […]
- Computer and Digital Forensics and Cybercrimes This has greatly affected the success of computer forensics and it is the main drawback in this area. The world is now safer due to the increasing usage of computer forensics in court cases.
- The Role of U.S. Government in Cybersecurity According to the government of the United States, cybersecurity is among the most serious economic and security challenges that the government needs to deal with.
- Cyber Security’s and Counter Terrorism’ Intersection Realization of national interests is the concern of many states in the current international and security is the main challenge that each government is trying to cope up with given the fact terrorists are ever […]
- Cybercrime, Digital Evidence, Computer Forensics The website “howstuffworks” carries an article discussing the basics of computer forensics, this is a good example of a website that is useful in explaining or understanding the reality of cybercrime and digital evidence. Not […]
- Middle East Cybersecurity, E-Government, Ecommerce The findings in the research revealed that five main issues led to the reluctance in the adoption of e-commerce and e-governance by the Emirates.
- Growth Hacking and Marketing Methods As a result, it could be observed that the combination of the growth hacking methods and the permission-based marketing appear to be one of the most efficient techniques towards marketing that is low-cost and effective.
- Cybersecurity: Stuxnet Virus Cyber security is one of the major concerns of governments in the contemporary world. It is important to note that in case of Stuxnet the three aspects prove to be vulnerable.
- Ways to Stop Cell Phones Hacking Although it is in the view of many that their phones cannot be hacked as they only protect their computers from hacking, mobile phone operators are more predisposed to being hacked since a mobile operator […]
- The Threats of Cyber Security Under the PPD-21, the owners of the critical infrastructure will work with the government to hasten the process of strengthening the national critical infrastructure in terms of the much needed security.
- Two Greatest Hacking Systems in the USA Appropriating intellectual output of someone else is also a computer malpractice that is intolerable. Generally, Computer malpractice is seen when a person shows hasty and careless conducts or behaviors when making use of computer systems.
- Cybercrime: Gary McKinnon’s Hacking Event It is the lack of effective controls that accounts for most hacking incidences, as depicted by the case of Gary McKinnon who was able to gain unauthorized access to NASA and pentagon systems, deleting crucial […]
- Important Problem of Cybersecurity Simulations The information stored in the company’s database was encrypted to create confidence in the customers on the security of the data.
- Analysis of Mandiant Cyber Security Company The company’s innovation theories and products need to accommodate other companies that do not view cyber crime as a major risk on their systems.
- Leadership: Mandiant Cyber Security Company Kevin Mandia is the founder and the CEO of the company. The achievements behind Mandiant Cyber Security Company owe its success to the leadership styles exhibited in the firm.
- Adrian Lamo’s Hacking: Is It Right? The example of Galileo introduces a theory about the construction of the Solar System that was the target of interest of the well-known scientist.
- Computer Forensics and Digital Evidence When electronic data has been collected to identify the kind of the incident and introduce evidence of the crime, it is important to organize a meeting with the witness who can provide details of the […]
- Cyber Security Threat Posed by a Terrorist Group These among other features of the internet have been identified to form the basis of the cyber terrorism attacks. A comprehensive international collaboration among investigators and prosecution teams in cases of cyber attacks have also […]
- Information Security Fundamentals: Computer Forensics In addition, the paper provides an overview of the techniques used in obtaining evidence from the internet and web resources, the types of evidence that can be recovered from electronic and computer resources, and the […]
- Computer Forensics Related Ethics Due to advancement in technology, individual information can be kept in databases, the risk of accessing this data is evident and this necessity the need of such a law so as to ensure security.
- The Cyber Security Act of 2009 Analysis This would contribute to enormous benefits to both the government and private stakeholders by ensuring a cyber security strategy that serves the interests of all.
- Air Force and Cyber Security Policies The use of technology in processing financial transactions implies that there is need to boost the trustworthiness, security, resilience, and reliability.
- The Role of Computer Forensics in Criminology In fact, since the development of the virtual machine monitors, the live-state analysis in digital forensics has become common and easy to understand.
- Ethical Hacking: Bad in a Good Way Introduction of personal computers led to the increase in the number of hackers as well as hacker targets were widened. Many hackers lack the skills to damage network systems in a major way.
- Hacking: Social Engineering Online The information is fed to the main web site that’s runs the hacking software, where the information is sorted according to various numbers.
- Cyber Security in Private and Public Sectors The US has the Health Insurance Portability and Accountability Act that ensures that patients’ data remain accessible only to the authorized segment of the staff.
- Cyber Crime and Necessity of Cyber Security This is one of the policies that has been proposed to curb cyber crimes and is being debated in the congress.
- Cybersecurity in the Energy Industry In this regard, in the event that a cyber attack is launched against the energy sector, it is bound to have far reaching consequences.
- Ethics in Computer Hacking Hacking by no means follows ethics; the infiltration is to the benefit of hacker and loss of users of computer system, network or website.
- Computer Forensics and Investigations It is crucial in the investigation of crimes that are related to the manipulation of computer systems. For digital evidence to be admissible in court, investigations should be conducted in a manner that adopts the […]
- Preparing a Computer Forensics Investigation Plan However, if the information is thought to be contained in the permanent storage, then a computer has to be shut down before transporting it to a laboratory for forensic analysis. The first step in the […]
- Basic Operations of Computer Forensic Laboratories All computer forensic laboratories in the US have to adhere to the national standards before they could be certified. Standard computer forensic equipment is used to support standard procedures and conditions in the laboratories.
- Introducing Cybersecurity Policies: Challenges and Solutions The major purpose for establishing security guidelines is to set an organization’s data security standard and describe the role of employees in safeguarding the documents of the firm, as well as the significance of a […]
- Société Générale Bank: Effective Security Controls The management of the bank revealed that Kerviel exploited every loophole to hack the computer operations at the bank. It is also important to list the potential risks because it enables the security personnel to […]
- Computer Security Breaches and Hacking To avoid such an attack in the future, it is advisable to keep both the client and server applications up to date.
- Analysis of BJG Cybersecurity Consultants
- Analysis of Cybersecurity and Risk Management
- Analysis of Cybersecurity Metrics as Well a Governmental
- Analyzing the Impact of Mobile Devices on Cybersecurity
- Assessing the Impact of Cybersecurity Attacks on Power Systems
- Building Cybersecurity Awareness: What Should Both Companies and Consumers Do to Protect Themselves?
- Current Practice Analysis for IT Control and Security
- Why Cybersecurity Is Important?
- Cybersecurity in Banking Financial Services Secto
- Cybersecurity in the European Union: Resilience and Adaptability in Governance Policy
- Cyber Security : Is No Silver Bullet For Cybersecurity?
- Dealing With Cybersecurity Threats Posed by Globalized Information Technology Suppliers
- Emerging Technologies That Impact the Cybersecurity Field
- Hacker’s Culture and Cultural Aspects of Cybersecurity
- How Cybersecurity Is an Aspect of Security?
- How Cybersecurity Is Important Resources?
- How Policies, Laws and Regulations Affect the Cybersecurity Field?
- Is Cybersecurity a Big Deal?
- Risk Assessment Uncertainties in Cybersecurity Investments
- What Is Cybersecurity?
- When Cybersecurity Policy Is Discussed the Topics Often?
- Why Computer Scientists Should Care About Cybersecurity?
- Access Single Most Important Cybersecurity Vulnerability Facing IT Mangers
- Model for the Impact of Cybersecurity Infrastructure on Economic Development in Emerging Economies: Evaluating the Contrasting Cases of India and Pakistan
- Cybersecurity and Its Importance in the Modern World
- Architecture for Managing Knowledge on Cybersecurity in Sub-Saharan Africa
- Benefits of Using Cybersecurity
- Border and Cybersecurity in the United States
- Botching Human Factors in Cybersecurity in Business Organizations
- Companies Responsibilities in Enhancing Cybersecurity Chapter
- Cybersecurity and Law Enforcement
- Cybersecurity and Organizational Change Concept Map
- Cybersecurity at European Level: The Role of Information Availability
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity for Digital Financial Service
- Cybersecurity Policy Making at a Turning Point: Analysing a New Generation of National
- Effect of Bring Your Own Device (BYOD) on Cybersecurity
- Human Aspects in Cybersecurity on a Government Agency and a Private Organization
- Improvement of Cybersecurity Is Necessary
- Most Important Cybersecurity Vulnerability Facing It Managers Computer Knowledge
- Obama Administration’s Policy Views on Cybersecurity
- Review of Cybersecurity Risks of Medical Device Software
- Small Business Cybersecurity and the Public Cloud
- The Influence of Cybersecurity Define the Hacker Motives
- Effect of Cybersecurity on Higher Education
- Importance of Cybersecurity for The Future
- Role of Cybersecurity and Its Effects on the World
- Why Should Computer Scientists Care About Cybersecurity?
- What Are the Roles and Responsibilities of an Organization in Considering Cybersecurity?
- What Are Three Models for Sharing Cybersecurity Incident Information?
- What Are the Private Sector and Public Sector Cybersecurity Issues?
- How Do Policies, Laws, and Regulations Affect the Cybersecurity Field?
- How to Improving Password Cybersecurity Through Inexpensive and Minimally Invasive Means?
- What Kind Are International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- What Is the Most Important Cybersecurity Vulnerability Facing Managers in Computer Science?
- What Are New Concepts for Cybersecurity in Port Communication Networks?
- What Does Cyber Security Do?
- Is Cyber Security a Promising Career?
- What Are the Three Major Threats to Cyber Security Today?
- What Qualifications Do You Need for Cybersecurity?
- What Is a Cyber Security Example?
- What Are the Main Problems With Cyber Security?
- What Is the Biggest Threat to Cyber Security?
- What Are Cyber Security Tools?
- What Is the Risk in Cyber Security?
- What Is the Best Cyber Security?
- What Is Wireshark in Cyber Security?
- Which Are Fundamentals of Petroleum Energy & Mitigating Global Cybersecurity Attacks?
- Which International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- Which Vulnerability Assessments and Mitigating Global Cybersecurity Attacks on the Enterprise?
- Who Is the Founder of Cyber Security?
- What Are the Seven Types of Cyber Security?
- What Is the Most Significant Cybersecurity Company?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 27). 237 Cyber Security Essay Topics, Ideas, and Examples. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/
"237 Cyber Security Essay Topics, Ideas, and Examples." IvyPanda , 27 Feb. 2024, ivypanda.com/essays/topic/cybersecurity-essay-topics/.
IvyPanda . (2024) '237 Cyber Security Essay Topics, Ideas, and Examples'. 27 February.
IvyPanda . 2024. "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
1. IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
Bibliography
IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
- Security Management Essay Ideas
- Cyber Bullying Essay Ideas
- Internet Research Ideas
- Computer Forensics Essay Topics
- Data Mining Titles
- Crime Prevention Research Topics
- Hacking Essay Topics
- Cryptocurrency Essay Ideas
- Identity Theft Essay Ideas
- Viruses Research Topics
- Cryptography Paper Topics
- Encryption Essay Titles
- Internet Privacy Essay Topics
- Digital Transformation Topics
- Software Engineering Topics
- Follow us on Facebook
- Follow us on Twitter
- Criminal Justice
- Environment
- Politics & Government
- Race & Gender
Expert Commentary
Internet harassment and online threats targeting women: Research review
2015 review of studies and papers on issues relating to gender and online sexual harassment, as well as hate speech and threats targeting women and girls.

Republish this article

This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License .
by John Wihbey and Leighton Walter Kille, The Journalist's Resource July 13, 2015
This <a target="_blank" href="https://journalistsresource.org/criminal-justice/internet-harassment-online-threats-targeting-women-research-review/">article</a> first appeared on <a target="_blank" href="https://journalistsresource.org">The Journalist's Resource</a> and is republished here under a Creative Commons license.<img src="https://journalistsresource.org/wp-content/uploads/2020/11/cropped-jr-favicon-150x150.png" style="width:1em;height:1em;margin-left:10px;">
Online harassment and threats are not a new phenomenon, but the degree to which these are directed at women and girls has begun to receive increased attention from news media , academia and law enforcement.
Forms of harassment can vary widely, from name-calling and trolling to persistent stalking and shaming to outright sexual and death threats. To some degree, the problem is structural and dates back to the Internet’s early days: The Telecommunications Act of 1996 allowed operators of websites to avoid liability for what users post, although the limits of this continue to be tested in the courts and many aspects of the Communications Decency Act provision are not entirely settled . But it remains the case that the wide-open environment that enables creativity, innovation and vigorous debate online paradoxically also enables derogatory, anonymous speech for which there is often little legal recourse .
Because of the volume of data and information they deal with, many Internet and social media companies struggle to articulate and enforce standards, even on more obvious issues such as the online messaging of violent extremists . Most warn that death threats, for example, are not protected by free speech , but banning users in an environment with anonymity is a challenge. In particular, the problems inherent on the microblogging platform Twitter, which, unlike Facebook, allows for anonymity, have been playing out publicly . Meanwhile, the controversy at Reddit that resulted in the resignation of CEO Ellen Pao in July 2015 again raises, among other things, issues over online harassment and the complex dynamics of addressing it.
As the totality and intensity of the harassment is being better understood, scholars have even begun to see this phenomenon as a profound civil rights issue for women and other groups such as racial minorities. Persistent threats can not only diminish well-being and cause psychological trauma but can undercut career prospects and the ability to function effectively in the marketplace and participate in democracy.
A 2014 Pew Research Center survey found that about 40% of Internet users say they have experienced harassment, and that females in particular age cohorts endure higher rates of threats:
Stalking and sexual harassment are more prevalent among young women than among young men. But they are also more prevalent among young women than among women even a few years older (those ages 25-29). Women ages 18-24 who use the Internet are more than twice as likely as women ages 25-29 to have experienced sexual harassment online (25% vs. 10%) and three times as likely to have been stalked online (26% vs. 8%). In addition, they are twice as likely as that older cohort to have been physically threatened (23% vs. 11%) and twice as likely to have been harassed for a sustained period of time (18% vs. 8%).
Further, according to the Pew survey, women were much more likely than men to say that their recent experience with harassment online was “extremely” or “very” upsetting.
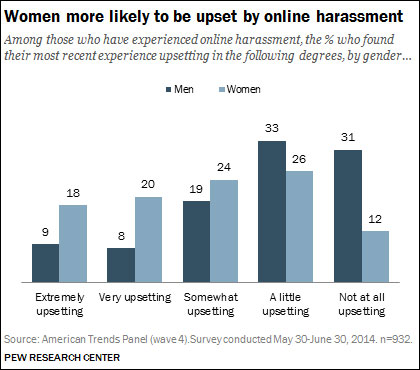
There have been a number of attempts at remedying the problem of cyber sexual harassment, from for-profit business models to new algorithmic software applications to detect and monitor threatening language.
The following studies and papers provide further perspective on these and related issues of online threats and harassment:
“Online Harassment, Defamation and Hateful Speech: A Primer of the Legal Landscape” Marwick, Alice E.; Miller, Ross W. Fordham Center on Law and Information Policy Report No. 2, June 2014.
Abstract: “This interdisciplinary project focused on online speech directed at women and seeks to provide a primer on (i) what legal remedies, if any, are available for victims of sexist, misogynist, or harassing online speech, and (ii) if such legal remedies and procedures exist, whether practical hurdles stand in the way of victims’ abilities to stop harassing or defamatory behavior and to obtain legal relief. The study concluded that while online harassment and hateful speech is a significant problem, there are few legal remedies for victims. This is partly due to issues of jurisdiction and anonymity, partly due to the protection of internet speech under the First Amendment, and partly due to the lack of expertise and resources on online speech at various levels of law enforcement. Given this landscape, the problem of online harassment and hateful speech is unlikely to be solved solely by victims using existing laws; law should be utilized in combination with other practical solutions.”
“Embodied Harms: Gender, Shame and Technology-Facilitated Sexual Violence” Henry, Nicola; Powell, Anastasia. Violence against Women , March 2015, doi: 10.1177/1077801215576581.
Abstract: “Criminality in cyberspace has been the subject of much debate since the 1990s, yet comparatively little attention has been paid to technology-facilitated sexual violence and harassment (TFSV). The aim of this article is to explore the ways in which retraditionalized gender hierarchies and inequalities are manifested in online contexts, and to conceptualize the cause and effects of TFSV as “embodied harms.” We argue that problematic mind/body and online/off-line dualisms result in a failure to grasp the unique nature of embodied harms, precluding an adequate understanding and theorization of TFSV.”
“Perpetuating Online Sexism Offline: Anonymity, Interactivity and the Effects of Sexist Hashtags on Social Media” Fox, Jesse; Cruz, Carlos; Lee, Ji Young. Computers in Human Behavior , November 2015, Vol. 52, 436-442. doi: 10.1016/j.chb.2015.06.024.
Abstract: “Sexism and sexual harassment are not uncommon in online environments such as social networking sites, forums, and video games. This experiment investigated whether users’ anonymity and level of interactivity with sexist content on social media influenced sexist attitudes and offline behavior. Participants (N = 172) used a Twitter account that was anonymous or had personally identifying details. They were asked to share (i.e., retweet) or write posts incorporating a sexist hashtag. After exposure, participants completed two purportedly unrelated tasks, a survey and a job hiring simulation in which they evaluated male and female candidates’ resumés. Anonymous participants reported greater hostile sexism after tweeting than nonanonymous participants. Participants who composed sexist tweets reported greater hostile sexism and ranked female job candidates as less competent than those who retweeted, although this did not significantly affect their likelihood to hire.”
“Online Incivility or Sexual Harassment? Conceptualising Women’s Experiences in the Digital Age” Megarry, Jessica. Women’s Studies International Forum, November–December 2014, Vol. 47, Part A, 46-55. doi: 10.1016/j.wsif.2014.07.012.
Abstract: “Launched in 2006, the growth of Twitter as a microblogging platform has been exponential, yet little research to date specifically considers women’s experiences of the medium. This article draws on a case study of the #mencallmethings hashtag, in which women describe and discuss the verbal abuse that they have received online from men. Providing a broad based context for the specific analysis of the #mencallmethings hashtag, I concentrate on the theoretical contributions made by western feminist research over the last 30 years to embed the aggressive harassment of women online in a wide review of types of threats to women. I argue that the harassment conveyed in the hashtag should be recognized as online sexual harassment, and a form of excluding women’s voices from the digital public sphere.”
“Addressing Gender-Based Harassment in Social Media: A Call to Action” Simons, Rachel Noelle. iConference 2015 proceedings.
Abstract: “Previous research indicates that women face a disproportionate amount of online harassment resulting from their identity as women. As a relatively new phenomenon, however, gender-based online harassment is not well understood. Social media platforms are a critical medium for gender-based online harassment and the effects of this harassment on women can be devastating both to their personal lives and to their professional careers. While the field of Information Studies is uniquely positioned to address the serious problem of gender-based online harassment, there are significant gaps in key areas of the literature related to this problem. Therefore, critical research is needed in order to produce key insights for empowering victims, for discouraging perpetrators, and for increasing awareness among social media platforms’ designers and managers. This knowledge can be grouped into three application areas: education, policy, and technological tools.”
“Exploring Differences in How Men and Women Respond to Threats to Positive Face on Social Media” Chen, Gina Masullo; Abedin, Zainul. Computers in Human Behavior , September 2014, Vol.38, 118-126. doi: 10.1016/j.chb.2014.05.029.
Abstract: “A three-condition (rejection, criticism, control) experiment (N = 78) with gender treated as an additional factor and moderating variable examined gender differences in response to two types of threats to positive face — rejection and criticism — on a social-networking site. Results showed it did not matter if men or women were rejected or criticized on a social-networking site; both threats to positive face lead to more retaliatory aggression, compared to the control. However, men retaliated to a greater extent than women to both types of threats. Also, men responded differently to criticism than to rejection, while women’s results did not vary. Findings are discussed in relation to face theory and politeness theory, particularly in regard to computer-mediated communication.”
“Sexual Harassment 2.0” Franks, Mary Anne. Maryland Law Review , 2012
Abstract: “The rise of sexual discrimination in cyberspace is only one of the most recent and most striking examples of the phenomenon’s increasing complexity. Sexual harassment law, however, has not kept pace with this evolution. Discrimination law has not been adequately ‘updated’ to address new and amplified practices of sex discrimination. Its two principal limitations are (1) it treats only sexual harassment that occurs in certain protected settings (e.g. the workplace or school) as actionable and (2) it assumes that both the activity and the resulting harm of sexual harassment occur in the same protected setting. Thus, it is unable to address any harassment that occurs completely or partially outside of traditionally protected settings. By contrast, this article proposes a ‘multiple-setting’ conception of sexual harassment that both moves beyond traditionally protected settings and explicitly acknowledges that sexual harassment in one setting can produce harms in another. In order to address multiple-setting harassment, a third-party liability regime similar to that of traditional sexual harassment law should be introduced into non-traditional contexts. In the particular case of online harassment, liability should attach to website operators. This regime will create an incentive for website operators to adopt preemptive, self-regulatory measures against online sexual harassment, much as employers have done in the offline setting.”
“Hate Speech in Cyberspace” Delgado, Richard; Stefancic, Jean. Wake Forest Law Review , Summer 2014, Vol. 49.
Summary: “The advent of the Internet, beginning around 1994, has not led to an improvement in civility or the quality of interpersonal relations. If subjective experiences are a guide, heavy users feel freer to take positions or espouse views that depart from our public values…. Since hate speech on the Internet is pervasive, rising, and unlikely to subside unaided, what should society do to counter it? Possible responses to Internet hate speech include those that one commonly hears with this type of utterance, including talking back to the aggressor. As we shall see, most of these avenues are even less efficacious than they are with ordinary speech. Because courts and legislatures are unlikely to tackle the Internet any time soon, while Internet providers and companies are even less likely to rein themselves in, new approaches are in order.”
“Cyber Civil Rights” Citron, Danielle Keats. Boston University Law Review , 2009, Vol. 89, 61-125.
Abstract: “Social networking sites and blogs have increasingly become breeding grounds for anonymous online groups that attack women, people of color, and members of other traditionally disadvantaged groups. These destructive groups target individuals with defamation, threats of violence, and technology-based attacks that silence victims and concomitantly destroy their privacy…. The social science literature identifies conditions that magnify dangerous group behavior and those that tend to defuse it. Unfortunately, Web 2.0 technologies accelerate mob behavior. With little reason to expect self-correction of this intimidation of vulnerable individuals, the law must respond. General criminal statutes and tort law proscribe much of the mobs’ destructive behavior, but the harm they inflict also ought to be understood and addressed as civil rights violations. Civil rights suits reach the societal harm that would otherwise go unaddressed and would play a crucial expressive role. Acting against these attacks does not offend First Amendment principles when they consist of defamation, true threats, intentional infliction of emotional distress, technological sabotage, and bias-motivated abuse aimed to interfere with a victim’s employment opportunities. To the contrary, it helps preserve vibrant online dialogue and promote a culture of political, social, and economic equality.”
“Criminalizing Revenge Porn” Citron, Danielle Keats; Franks, Mary Anne. Wake Forest Law Review , 2014, Vol. 49.
Abstract: “Violations of sexual privacy, notably the non-consensual publication of sexually graphic images in violation of someone’s trust, deserve criminal punishment. They deny subjects’ ability to decide if and when they are sexually exposed to the public and undermine trust needed for intimate relationships. Then too they produce grave emotional and dignitary harms, exact steep financial costs, and increase the risks of physical assault. A narrowly and carefully crafted criminal statute can comport with the First Amendment. The criminalization of revenge porn is necessary to protect against devastating privacy invasions that chill self-expression and ruin lives.”
“Abuse and Harassment Diminish Free Speech” Bernstein, Anita. Pace Law Review , Fall 2014, Vol. 35, Issue 1.
Abstract: “Like writings that come before it, this article challenges the chestnut that freedom comes at the expense of another progressive good. Equality, to some writers; antisubordination, to others; ‘civil rights’ also serves…. Abuse and harassment pull valuable words out of the marketplace of ideas, I argue. They lessen the discourse. Also following in the path of other writings, this article notes a few higher stakes present in online speech as contrasted with its lower-tech antecedents. Electronic discourse adds anonymity, amplification, and permanence; within this medium, these conditions reinforce each other…. In this article, I advocate measures against abuse and harassment because (not ‘even though’) I cherish free speech.”
“Sexism in Online Video Games: The Role of Conformity to Masculine Norms and Social Dominance Orientation” Fox, Jesse; Tang, Wai Yen. Computers in Human Behavior , April 2014, Volume 33, 314-320. doi: 10.1016/j.chb.2013.07.014.
Abstract: “Sexism toward women in online video game environments has become a pervasive and divisive issue in the gaming community. In this study, we sought to determine what personality traits, demographic variables, and levels of game play predicted sexist attitudes towards women who play video games. Male and female participants (N = 301) who were players of networked video games were invited to participate in an anonymous online survey. Social dominance orientation and conformity to some types of masculine norms (desire for power over women and the need for heterosexual self-presentation) predicted higher scores on the Video Game Sexism Scale (i.e., greater sexist beliefs about women and gaming). Implications for the social gaming environment and female gamers are discussed.”
Keywords: research roundup, cyberbullying, cyberstalking, gender, online harassment, social media, Reddit, Twitter, Facebook, sexism, anonymity, online sexism, invasion of privacy
About the Authors
John Wihbey
Leighton Walter Kille
Cyber Crime Essay
In this Cyber Crime Essay , we had discussed the classification of cybercrimes, how to prevent cybercrime & much more.
Cybercrime is a type of crime in which computer crime (hacking, spamming, etc.) is used as a tool to commit any crime.
Cybercriminals use computer and Internet technology to access personal information, trade secrets, etc.
In this article Essay on Cyber Crime , we had provided the essays in different word limits, which you can use as per your need:
Essay on Cyber Crime 150 words:
Most cybercrime is usually done for money today, but some people are trying to steal someone’s data, harm another person, and destroy someone’s network or computer.
In the present time, Cyber Crime remains a headache for the people; it is a severe problem; to stop this activity, every country in the world developed laws.
Under it, a very similar court of U.S. Cyber Crime, it is divided into three parts.
The first one in which computer equipment is its target, such as controlling the network of another.
Second, using the computer as a weapon, such as a denial of service attack.
Third, the computer is used as an accessory for crime, such as taking illegal data or stealing from the computer.
U.S. Court believes that Cyber Crime is a kind of dangerous malicious activity that means there is a conspiracy to spread from viruses.
In which much actionable data is taken and then entered into the systems of others, by doing this, copyrighted things are significantly damaged.
Other types of cybercrime include gaming, selling illegal items such as weapons, drugs, and children’s porn are some types of cybercrime.
Everyone thinks that merely stealing someone’s data is a cybercrime, but in defining the terms, we can say that cybercrime refers to the use of an electronic device (computer, laptop, etc.) to try to steal someone’s data or harm them using a computer.
Cybercrime is an illegal activity involving a range of issues ranging from theft using your system or I.P. Address as a tool for committing a crime.
It is an illegal act where a computer is used as a tool or target or both as follows:
These days cybercrime is a fast-growing area of crime, as technology is advancing, man is becoming dependent on the Internet for all his needs.
It makes shopping, gaming, online study, social networking, online jobs, and so on all available easily in one place.
Apart from other countries, India is not far from the place where the rate of cybercrime is increasing day by day.
Cybercrime is classified into four major types; these are financial, privacy, hacking, and cyber-terrorism.
The Generation in laptop is the age of processors.
Cyber Crime Essay 300 words:
Today many people all over the world are stealing personal information of people sitting at home through online Internet, which is called cybercrime.
First of all, let us tell you when a person can send ugly or rude messages to another person through email service. This Act hurts the mind of the person receiving the email.
Secondly, someone who has little knowledge of computers can develop Viruses on the Internet.
Email Services are commonly used or used to commit this misdeed. In every computer in which these email messages go, Virus ruins the computer after entry in the system, both the machine and its information can be badly destroyed.
In the hall itself, the Philippine police arrested the father of ‘I love you’ Virus. Individuals with wrong motives get information about access codes of Numbers to bank accounts.
They get these banks to transfer money to their accounts, and the banks do not even know. There is a need for a little cleverness, and these criminals are different.
Some individuals create a disturbance in the websites of private sector enterprises.
Friends, you will be surprised to know that they send Virus to those websites, get highly sensitive information from there, or try their best to spoil the image of any person or enterprise on a site by adopting propaganda.
Cybercrime in the States of India:
In 5 years, more than 5900 cases were reported in Maharashtra and made on top, with Uttar Pradesh nearly 5000 cases in second place and Karnataka in third place with over 3500 cases.
Cybercrime in India is registered under three main heads, I.T. Act, IPC (Indian Penal Code), and State Level Legislation (SLL). Also, read Cyber Crime Essay 400 words.
Cases of Cyber Laws under I.T.:
- Tampering with computer source documents – Sec. 65
- Computer Systems, Hacking with Data Transformation – Sec. 66
- Publishing pornographic information – Sec. 67
- Non-Authorized Access to Protected Systems – Sec. 70
- Privacy and breach of confidentiality – Sec. 72
- Publishing false digital signature certificate – Sec. 73
The web world or cyberspace is a vast community of millions and billions of users and websites.
Apart from this, people use it for various activities like shopping, movies, music, video games, transactions, and e-commerce, etc.
Due to this age of technology and easy access to the Internet, anyone can easily be reached; this has led to rapid growth since the last decade.
Moreover, the Internet has opened up an information world to which anyone can connect, due to this, the rate of crime, especially cybercrime, has increased very much.
Also, the rate of circulation of data increases significantly due to high internet speed, because of all these issues, cyber security has become a significant concern for society.
Essay on Cyber Crime 400 words:
Cybercrime has to become a significant problem all over the world, and due to which many cyber security agencies have been formed to take some action against this crime.
In many countries to stop this crime worldwide, many cybercrime agencies have been formed.
Like computers are used for hacking, but through cyber agents, these cyber agents get some evidence to catch hackers.
Several cases of hacking have been reported since opening cybercrime agencies, and cyber agents have caught several hackers.
Hackers are given many punishments, such as taking hefty fines from them or putting them in jail.
On the other hand, these cyber security people seek the help of many hackers to find other hackers who harass people.
So this cybercrime is a big problem in today’s world, and we should be aware of it and always be safe from these cybercriminals.
Cybercrime is the latest and perhaps most complicated problem in the cyber world. The term “cybercrime” is not defined anywhere in any law or Act passed or enacted by the Indian Parliament.
Any criminal activity that uses the computer either as a means to target or to eliminate further crimes comes under the cybercrime.
Cybercrime or computer oriented crime is a crime that involves a computer and a network.
Today the whole world is affected by cybercrime; it is involved in the illegal use of modern telecommunication networks (Internet, mobile phones) people makes committed crimes torture them, knowingly physical or mental damage, and damage to his reputation.
In today’s time, this is the work of many people, they steal people’s data and then start abusing them, and cybercrime can threaten the security and financial health of an individual or a nation.
Cybercrime is an illegal act where the computer is used as a means or target, or both ways.
Cybercrime is a broad term, which can also be defined as: “criminal activity where a computer or computer network is used as a means, target or place of criminal activity.”
Types of cybercrime:
Cybercrime is classified into four major types, financial, privacy, hacking, and cyber-terrorism.
Financial crimes mean stealing money from the account holders. Similarly, they also took the data of companies that could lead to financial crimes.
Also, they are at significant risk due to the transaction. Every year hackers steal the money from business people and government worth millions and crores of rupees.
Privacy crime involves stealing your data that you do not want to share with the world. Also, people suffer a lot, and some people even commit suicide due to the misuse of their data.
In hacking, they intentionally damage a website causing loss or damage to the public or the owner. Also, they destroy or modify existing sites to reduce their value.
This is a crime in which illegal control over a person’s website is done illegally. In this way, the owner of the website loses control and essential information on that website.
In modern-day terrorism has advanced 10-20 years ago. Still, cyber terrorism is not related only to terrorists or terrorist organizations, but threatening a person or property at the level of creating fear is also cyber terrorism. Also, read Cyber Crime Essay 600 words.
Measures to prevent cybercrime:
- Computer users should use a firewall to protect their computers from hackers.
- Computer users should install anti-virus software such as McAfee or Norton anti-virus.
- Cyber experts have advised users to only access secure websites.
- We should never give their credit card information to suspects or strangers.
- Users should develop strong passwords on their accounts, i.e., include characters and numbers in the password, and continuously update the password and login details.
- Monitor children and limit their use of the Internet.
- Check the security settings of Facebook, Twitter, and YouTube, and be careful, protect information to avoid hacking, use encryption for most sensitive files or financial records.
- For all vital information to create a back-up, and having it stored somewhere else, users should be cautious while using public Wi-Fi hotspots.
- Avoid handling financial transactions on these networks; users should be careful while giving personal information such as name, address, phone number, or financial information on the Internet, make sure that the websites are secure.
Cyber Crime Essay 600 words:
Cybercrime is a crime that is an excellent crime in our society; cybercrime is a type of crime that is done through computers.
It is created by misusing the computer, and it is networked improperly.
This cybercrime is designed by some to intentionally harm other people by hacking or obtaining their private information, and this can be done quickly by modern internet technology through which these people create crime in society.
Hackers who hack other people’s private information or personal information, later blackmail them and harass them.
Most of the women in our society have to face this problem of harassment; they have become the most victim of these hackers.
This problem of cybercrime is not only in India, but this problem is spread all over the world by many hackers who hack and harass people across the globe, most of the hackers are from Russia.
These Russians hack the accounts of many people and later blackmail them, it has become a significant problem worldwide.
This hacking is started with computers, and this internet connection hackers easily hack people’s information through the machine.
Nowadays, it is also easy to hack from mobile phones; this hacking created a big problem in society.
These hackers are steading all the money from bank accounts or other personal accounts of people.
They send a virus on the other computer, and this Virus affects the equipment, and many unwanted things come into their network, which causes a big problem for the device.
After this Virus causes some psychological effects of the user, they put that unwanted thing in their computer through the illness.
Types of cybercrimes include pornography, cyber fraud, defamation, cyberstalking, harassment, IPR theft, data hostage, money laundering, phishing, email bombing, cyber warfare, illegal FTF.
Cybercrime is different and more terrible as cybercrime than a traditional crime; the offence is committed in an electronic medium, a general rule under the penal provisions of the Information Technology Act.
The Indian Parliament considered it necessary to give effect to the resolution by which U.N.
The General Assembly adopted the Model Law on Electronic Commerce adopted by the United Nations Commission on Trade Law, which resulted in the passage of the Information Technology Act, 2000, a welcome step at a time when there was no law on the sector.
However, the Act has proved inadequate during its application, and the Act has some shortcomings.
Cases of spam, hacking, stalking and email fraud are widespread, although cyber crime cells have been set up in major cities, the problem is that most of the cases are unavailable due to lack of awareness.
The capacity of the human mind is immeasurable, it is not possible to eliminate cybercrime from cyberspace, and however, it is quite possible to investigate them.
The home user segment is the biggest recipient of cyber-attacks as they are less likely to set up security measures in place and therefore require that people be made aware of their rights and duties.
Allowing users to access any electronic items on their computer should install anti-virus software, firewall, interruption detection system to make the application of laws more rigorous for further investigation of crime, etc.
Also, read 1. Essay on Internet 2. Digital India Essay 3. Cashless Economy Essay 4. Essay on Computer
Conclusion:
Cybercrime is an act that is neither widespread nor exhaustive; the Information Technology Act has not distributed with cyber irritation, cyber robbery, and cyber defamation, and so on.
• Section Under Essays
Gupshups is the place to find the most inspirational & motivation quotes, essay, speechs & lot more.
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Essay on Cyber Crime
Cyber crime is the result of technological advancements. It is a dangerous crime involving the use of internet and computers. Cybercrime is undetectable at the initial phase but comes to notice with the consequences. Through this, the illegal transfer of data and information is made, which is of confidential value to an individual or a group.
Short and Long Essays on Cyber Crime in English
Essay on Cyber Crime for students of class 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11 and class 12 in English in 100, 150, 200, 250, 300, 500 words. Also find short Cyber Crime essay 10 lines.
Cyber Crime Essay 10 Lines (100 – 150 Words)
1) The crime done with the help of a computer network is termed as cybercrime.
2) Cybercrime can harm your privacy and security.
3) Cybercrime is an illegal act that tends to hack your private data.
4) Cybercriminals try to gain money through illegal methods.
5) Phishing, DoS attack, spoofing, etc are some common cybercrimes.
6) With the increasing use of the internet, cybercrimes are on the rise.
7) Cybercrime makes the victim helpless by stealing their money and credentials.
8) One should be conscious while using the internet.
9) Cybercrimes can affect a person, an organization, or even the government.
10) Cybercrime is the misuse of advanced technologies.
Essay 1 (250 Words) – Cyber Crime: A Threat to Society
Introduction
Crime is a word used for wrong deed or offence, but when it comes to cybercrime then, it can be defined as a crime done by internet to cause an immeasurable loss to the individual, organization, or the government. Cyber crime is a punishable offence committed by cyber criminals .
Cyber Crime – A Threat to Society
Cyber crime is the criminal act which takes place over the internet through computers as tools or targets or other smart devices meant for making our work easier. The hacker or criminals are having various motives of the crime. They may be involved to cause a loss to an individual, some organization or government.
Several examples of cyber crime include frauds, identity theft, cyberstalking, creating and sending malware like viruses for destroying the systems or steal the data to make money. People involved in such activities find them as an easy way of making money. Even many of the well-educated and knowledge full persons are involved in such activities. Instead of using their mind in a positive way they employ themselves in cyber crime activities. Day by day this is becoming a great threat to our society and nation.
Cybercrime is the most prevailing crime in the present scenario, done through the internet. It causes a severe loss to the victim. Therefore some of the measures should be taken by us to avoid such crimes. The vigilant behaviour and following the safety protocols are only helping aids which can reduce the occurrence of cybercrime.
Essay 2 (400 Words) – Cyber Crime: Classification and Impacts
Man has been innovative and inventive by nature, since early ages. The different needs gave rise to new devices, tools, and technologies. Technology is also a discovery of man for making work easier. The advancement in technology is useful on one side and on the other side has some devastating effects. Cybercrime is also a negative aspect of these technological developments. The individual, organization and groups are involved in committing such criminal activities.
Classification of Cyber Crimes
- Crime Against an Individual – Crime committed against an individual by use of an individual’s credit card details, confidential data and sending of spam emails. This crime is mainly done for making money.
- Crime Against an Organization – This is done against a firm, company or organization to get unauthorized access to the data. This is done either to reveal the important data and employee details of the company or for money-making.
- Crime Against Government – This is the crime against the nation, by getting access to the national data and records. This crime is of main concern as it concerned with the safety of the people of the nation.
Impacts of Cyber Crime
Cyber crime has ruined up the lives of many. The people involved in cyber crime are called hackers.
- If we discuss on an individual level, the people affected with this are still trying to adjust the loss. Some have opted to commit suicide. The ultimate loss of money and any data which is confidential make the person helpless and left out in a painful situation.
- On an organization level, the loss is made by stealing the data of the company or destroying the system by malware so that it may not work till the terms and conditions of the criminal get fulfilled. The companies are at a greater loss as their strategies and important data is stolen and leaked out.
- The government is also the victim of this offence. Much confidential data is leaked as the result of cyber crime at the government level, risking the nation’s sovereignty. This is a serious issue as it may happen that the lives of people of the nation are threatened and frightened. The loss can be economical too. Many lakh and crore have been lost from the nation because of these cyber crimes.
Cyber crime is an offence related to the use of the internet. It is dealt with some important information to be leaked in public or money-making in an easy way. Therefore we should be practicing some safety measures and security applications to prevent the crime.
Essay 3 (500 – 600 Words) – Cyber Crime
Cybercrime can be mentioned as illicit use of the internet and computers. The computers are either the target of the crimes or used as a weapon for the crime. These crimes have become a common part of our daily lives. Each and every day one or the other person is becoming the victim of cybercrime. Internet is accessed by a number of people at the same time for various purposes, these hackers make their way out of these opportunities.
Different Types of Cyber Crimes
- Phishing – This involves obtaining the personal information of the user by sending spam emails or by means of phishing website which resembles the same as authorized website.
- Identity Theft – This involves getting the information about credit or debit cards or bank details, further unwanted money can be easily deducted after the information is hacked.
- Malware Attacks – Malware is the hostile software which is designed to damage the computer or systems. This is done to access meaningful information or for doing some crime by using that system.
- ATM Frauds – The ATM machine is totally hacked in this crime. The criminals have developed the way to access both the data on the card along with the pin, further they are successful in making the duplicate of the cards and use the same to withdraw money.
- Cyber Stalking – The criminal is involved in following the person through online measures. They can even send malware to damage the systems to get the exact information. It involves harassment of the user.
- Pornography – The act of presenting sexual activity containing video, through pornographic websites.
- Spoofing – In this, an email is received and appears to be from some authentic source, but it is not the same. It is corrupted.
- Piracy – It is unauthorized access to the information which is confidential. Many of the times the government websites are hacked and files are pirated containing important data.
The First National Conference on National Crime Investigation and Crime Forensics
- Our nation India, for the first time had a national conference on national crime investigation held in New Delhi at headquarters of CBI (Central Bureau of Investigation) on 4 and 5 September 2019.
- The main motive of the conference was to create a common platform for the investigators, forensic teams and other officials involved to discuss various methods and ways to tackle the cyber-related crimes. The conference was of 2 days i.e. 4th and 5th September.
Cyber Crime Awareness
Different security measures should be followed to be safe from the dreadful act of cyber crime.
- Strong passwords should be used. The password must be a complex one, could not be possible to guess.
- Use antivirus programmes to keep the system free of malware.
- Continuously update the system.
- Be vigilant and use the presence of mind to avoid identity thefts.
- Make your children aware of the internet, so that they can state any misuse or harassment if they are going through.
- Maintain privacy settings over social media.
Cyber Security
Cyber security is saving our system, network, devices, and programmes from the attack of malicious software. Thus the illegal accessing of data can be stopped.
Importance – The information regarding any important issue of the nation or any data which is meant to be used personally, if gets shared will create several problems. Therefore if there will be a security check imposed at several levels, the information and important data can be saved from leaking.
Types of Cyber Security
- Network Security – Protects the network from being attacked by malware and thus using a secure network .
- Cloud security – Meant for safeguarding the data in the cloud resources .
- Information security – Helps in protecting the data from unauthorized or illegal access.
- End-user security – The user should be conscious of while inserting any external devices in the system, opening any mail or links.
- Application security – helps in keeping the system and software free of any threat .
Cyber crime is spreading its arms day by day. The most appropriate way of being safe from becoming the victim of its ill effects is following security measures. There are various ways by which we can protect our confidential information from being leaked. We should always focus on awareness as – ‘Prevention is better than cure’, especially when the cure is not available.
FAQs: Frequently Asked Questions
Ans . Cybercrime started in the world in the 1970s.
Ans . Ian Murphy was the first cybercriminal in the world.
Ans . Karuppannan Jaishankar is regarded as the father of Cyber criminology.
Ans . The Yahoo v. Akash Arora case was the first cybercrime case in India that happened in 1999.
Ans . The United States of America has the highest number of cybercrimes in the world.
Related Posts
Essay on digital india, cashless india essay, essay on child is father of the man, essay on causes, effects and prevention of corona virus, essay on dr. sarvepalli radhakrishnan, durga puja essay, essay on summer vacation, essay on my plans for summer vacation, essay on holiday, leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Home — Essay Samples — Law, Crime & Punishment — Cyber Crimes — Cyber Crimes and Cyber Security in Modern World
Cyber Crimes and Cyber Security in Modern World
- Categories: Cyber Crimes Cyber Security
About this sample

Words: 1481 |
Published: Aug 14, 2018
Words: 1481 | Pages: 3 | 8 min read
Table of contents
Disaster recovery, network security, cyber attacks, website defacement.
- Identification, authentication & authorization of the user.
- Cryptography.
Flooding Services

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
3 pages / 1494 words
3 pages / 1254 words
6 pages / 2847 words
1 pages / 569 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Cyber Crimes
In our increasingly interconnected world, where technology is deeply woven into the fabric of our daily lives, the specter of computer threats looms large. From malware attacks to hacking and data breaches, the digital landscape [...]
Lee, S. (2017). Encrypted Messaging: Keeping Your Conversations Secure. Security Boulevard.Smirnoff, V., & Turner, S. (2019). Symmetric Encryption: Definition, Types, and Examples. SecurityTrails.Almeida, R. (2019). Asymmetric [...]
Cybersecurity has become a very familiar term that has drawn increasing awareness of the danger of leaving cybercrimes unpunished. Because the world is moving more toward online trading and e-commerce, and basically living [...]
Cybercrime is emerging as a very serious threat in today’s world. The internet brings happiness to our lives but at the same time, it has some negative sides too. The cybercriminal is always in a search to find out the new ways [...]
There are myriad ways for the bad guys to get your information and use it for all sorts of nefarious purposes — mainly, stealing your money, althoughoccasionally for other kinds of fraud or to cover their tracks when committing [...]
Violence against family members is something women do at least as often as men. There are dozens of solid scientific studies that reveal in a startlingly different picture of family violence than what we usually see in the [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Skip to main content
- Keyboard shortcuts for audio player
NPR suspends veteran editor as it grapples with his public criticism

David Folkenflik

NPR suspended senior editor Uri Berliner for five days without pay after he wrote an essay accusing the network of losing the public's trust and appeared on a podcast to explain his argument. Uri Berliner hide caption
NPR suspended senior editor Uri Berliner for five days without pay after he wrote an essay accusing the network of losing the public's trust and appeared on a podcast to explain his argument.
NPR has formally punished Uri Berliner, the senior editor who publicly argued a week ago that the network had "lost America's trust" by approaching news stories with a rigidly progressive mindset.
Berliner's five-day suspension without pay, which began last Friday, has not been previously reported.
Yet the public radio network is grappling in other ways with the fallout from Berliner's essay for the online news site The Free Press . It angered many of his colleagues, led NPR leaders to announce monthly internal reviews of the network's coverage, and gave fresh ammunition to conservative and partisan Republican critics of NPR, including former President Donald Trump.
Conservative activist Christopher Rufo is among those now targeting NPR's new chief executive, Katherine Maher, for messages she posted to social media years before joining the network. Among others, those posts include a 2020 tweet that called Trump racist and another that appeared to minimize rioting during social justice protests that year. Maher took the job at NPR last month — her first at a news organization .
In a statement Monday about the messages she had posted, Maher praised the integrity of NPR's journalists and underscored the independence of their reporting.
"In America everyone is entitled to free speech as a private citizen," she said. "What matters is NPR's work and my commitment as its CEO: public service, editorial independence, and the mission to serve all of the American public. NPR is independent, beholden to no party, and without commercial interests."
The network noted that "the CEO is not involved in editorial decisions."
In an interview with me later on Monday, Berliner said the social media posts demonstrated Maher was all but incapable of being the person best poised to direct the organization.
"We're looking for a leader right now who's going to be unifying and bring more people into the tent and have a broader perspective on, sort of, what America is all about," Berliner said. "And this seems to be the opposite of that."

Conservative critics of NPR are now targeting its new chief executive, Katherine Maher, for messages she posted to social media years before joining the public radio network last month. Stephen Voss/Stephen Voss hide caption
Conservative critics of NPR are now targeting its new chief executive, Katherine Maher, for messages she posted to social media years before joining the public radio network last month.
He said that he tried repeatedly to make his concerns over NPR's coverage known to news leaders and to Maher's predecessor as chief executive before publishing his essay.
Berliner has singled out coverage of several issues dominating the 2020s for criticism, including trans rights, the Israel-Hamas war and COVID. Berliner says he sees the same problems at other news organizations, but argues NPR, as a mission-driven institution, has a greater obligation to fairness.
"I love NPR and feel it's a national trust," Berliner says. "We have great journalists here. If they shed their opinions and did the great journalism they're capable of, this would be a much more interesting and fulfilling organization for our listeners."
A "final warning"
The circumstances surrounding the interview were singular.
Berliner provided me with a copy of the formal rebuke to review. NPR did not confirm or comment upon his suspension for this article.
In presenting Berliner's suspension Thursday afternoon, the organization told the editor he had failed to secure its approval for outside work for other news outlets, as is required of NPR journalists. It called the letter a "final warning," saying Berliner would be fired if he violated NPR's policy again. Berliner is a dues-paying member of NPR's newsroom union but says he is not appealing the punishment.
The Free Press is a site that has become a haven for journalists who believe that mainstream media outlets have become too liberal. In addition to his essay, Berliner appeared in an episode of its podcast Honestly with Bari Weiss.
A few hours after the essay appeared online, NPR chief business editor Pallavi Gogoi reminded Berliner of the requirement that he secure approval before appearing in outside press, according to a copy of the note provided by Berliner.
In its formal rebuke, NPR did not cite Berliner's appearance on Chris Cuomo's NewsNation program last Tuesday night, for which NPR gave him the green light. (NPR's chief communications officer told Berliner to focus on his own experience and not share proprietary information.) The NPR letter also did not cite his remarks to The New York Times , which ran its article mid-afternoon Thursday, shortly before the reprimand was sent. Berliner says he did not seek approval before talking with the Times .

NPR defends its journalism after senior editor says it has lost the public's trust
Berliner says he did not get permission from NPR to speak with me for this story but that he was not worried about the consequences: "Talking to an NPR journalist and being fired for that would be extraordinary, I think."
Berliner is a member of NPR's business desk, as am I, and he has helped to edit many of my stories. He had no involvement in the preparation of this article and did not see it before it was posted publicly.
In rebuking Berliner, NPR said he had also publicly released proprietary information about audience demographics, which it considers confidential. He said those figures "were essentially marketing material. If they had been really good, they probably would have distributed them and sent them out to the world."
Feelings of anger and betrayal inside the newsroom
His essay and subsequent public remarks stirred deep anger and dismay within NPR. Colleagues contend Berliner cherry-picked examples to fit his arguments and challenge the accuracy of his accounts. They also note he did not seek comment from the journalists involved in the work he cited.
Morning Edition host Michel Martin told me some colleagues at the network share Berliner's concerns that coverage is frequently presented through an ideological or idealistic prism that can alienate listeners.
"The way to address that is through training and mentorship," says Martin, herself a veteran of nearly two decades at the network who has also reported for The Wall Street Journal and ABC News. "It's not by blowing the place up, by trashing your colleagues, in full view of people who don't really care about it anyway."
Several NPR journalists told me they are no longer willing to work with Berliner as they no longer have confidence that he will keep private their internal musings about stories as they work through coverage.
"Newsrooms run on trust," NPR political correspondent Danielle Kurtzleben tweeted last week, without mentioning Berliner by name. "If you violate everyone's trust by going to another outlet and sh--ing on your colleagues (while doing a bad job journalistically, for that matter), I don't know how you do your job now."
Berliner rejected that critique, saying nothing in his essay or subsequent remarks betrayed private observations or arguments about coverage.
Other newsrooms are also grappling with questions over news judgment and confidentiality. On Monday, New York Times Executive Editor Joseph Kahn announced to his staff that the newspaper's inquiry into who leaked internal dissent over a planned episode of its podcast The Daily to another news outlet proved inconclusive. The episode was to focus on a December report on the use of sexual assault as part of the Hamas attack on Israel in October. Audio staffers aired doubts over how well the reporting stood up to scrutiny.
"We work together with trust and collegiality everyday on everything we produce, and I have every expectation that this incident will prove to be a singular exception to an important rule," Kahn wrote to Times staffers.
At NPR, some of Berliner's colleagues have weighed in online against his claim that the network has focused on diversifying its workforce without a concomitant commitment to diversity of viewpoint. Recently retired Chief Executive John Lansing has referred to this pursuit of diversity within NPR's workforce as its " North Star ," a moral imperative and chief business strategy.
In his essay, Berliner tagged the strategy as a failure, citing the drop in NPR's broadcast audiences and its struggle to attract more Black and Latino listeners in particular.
"During most of my tenure here, an open-minded, curious culture prevailed. We were nerdy, but not knee-jerk, activist, or scolding," Berliner writes. "In recent years, however, that has changed."
Berliner writes, "For NPR, which purports to consider all things, it's devastating both for its journalism and its business model."
NPR investigative reporter Chiara Eisner wrote in a comment for this story: "Minorities do not all think the same and do not report the same. Good reporters and editors should know that by now. It's embarrassing to me as a reporter at NPR that a senior editor here missed that point in 2024."
Some colleagues drafted a letter to Maher and NPR's chief news executive, Edith Chapin, seeking greater clarity on NPR's standards for its coverage and the behavior of its journalists — clearly pointed at Berliner.
A plan for "healthy discussion"
On Friday, CEO Maher stood up for the network's mission and the journalism, taking issue with Berliner's critique, though never mentioning him by name. Among her chief issues, she said Berliner's essay offered "a criticism of our people on the basis of who we are."
Berliner took great exception to that, saying she had denigrated him. He said that he supported diversifying NPR's workforce to look more like the U.S. population at large. She did not address that in a subsequent private exchange he shared with me for this story. (An NPR spokesperson declined further comment.)
Late Monday afternoon, Chapin announced to the newsroom that Executive Editor Eva Rodriguez would lead monthly meetings to review coverage.
"Among the questions we'll ask of ourselves each month: Did we capture the diversity of this country — racial, ethnic, religious, economic, political geographic, etc — in all of its complexity and in a way that helped listeners and readers recognize themselves and their communities?" Chapin wrote in the memo. "Did we offer coverage that helped them understand — even if just a bit better — those neighbors with whom they share little in common?"
Berliner said he welcomed the announcement but would withhold judgment until those meetings played out.
In a text for this story, Chapin said such sessions had been discussed since Lansing unified the news and programming divisions under her acting leadership last year.
"Now seemed [the] time to deliver if we were going to do it," Chapin said. "Healthy discussion is something we need more of."
Disclosure: This story was reported and written by NPR Media Correspondent David Folkenflik and edited by Deputy Business Editor Emily Kopp and Managing Editor Gerry Holmes. Under NPR's protocol for reporting on itself, no NPR corporate official or news executive reviewed this story before it was posted publicly.
- Katherine Maher
- uri berliner

IMAGES
VIDEO
COMMENTS
Online crimes are often referred to as cybercrime and occur because 'the perpetrator uses special knowledge of cyberspace' (Furnell Citation 2002, 21). Cybercrime can therefore be viewed as a large umbrella term that encompasses computer-assisted crime in which computers and technology are used in a supporting role, such as the use of a ...
100-Word Essay on Cyber Crime. Cybercrime, the dark underbelly of the digital world, is on the rise. It encompasses a range of illegal activities conducted through computers and the internet, including hacking, phishing, and online fraud. Cybercriminals exploit vulnerabilities for financial gain or personal satisfaction, causing harm to ...
2. Cyberstalking. This Cybercrime involves online harassment where the victim is subjected to a plethora of online messages and emails. Typically, the stalker uses social media, websites, and search engines to intimate the victim and instils fear.The stalker knows the victim and makes the person feel afraid and concerned for their safety.
It is widely accepted that cybercrime is highly prevalent and increasing. A recent report suggests that Internet Service Providers (ISPs) record around 80 billion automated scans daily by online perpetrators with the aim of identifying targets for cybercrime (Lewis, 2018), and in the year ending September 2019, 1 million 'computer misuse' crimes were reportedly committed against households ...
Types of cybercrime. Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense ...
From hacktivism and digital disobedience to online harassment and sexual exploitation, Cybercrime and Society is the definitive book for undergraduate and postgraduate students studying modules in cybercrime and cybersecurity. In addition to the extensive updating and expansion of the topics covered in the 2019 edition, all kinds of new ...
Conclusion of Essay on Cyber Crime. In conclusion, cybercrime is a digital menace that affects us all. Whether it's hacking, scams, or cyberbullying, the consequences can be devastating. However, we can protect ourselves by staying informed, practicing good cybersecurity habits, and reporting cybercrime when it occurs.
The articles included in this issue reflect three broad areas of cybercrime research: cybercrime victimization, cybercrime perpetration, and techniques and facilitators of cybercrime. While there is some overlap, the issue includes three papers focused on each of these three areas. The first area covered in the special issue focuses on ...
Effects of Cyber Crime on Social Media. 2 pages / 933 words. The issue of cyber Crime has risen rapidly as a result of increased access to computers in the recent years compared to the past. Cyber Crime refers to criminal activities, which are carried out by the use of computers or the internet.
Cyber crime, a rapidly growing menace in the digital age, has profound effects on individuals, organizations, and society as a whole. This essay delves into the complex causes and effects of cyber crime to examine its far-reaching consequences on privacy, economy, and security. By understanding... Cyber Crime. Cyber Crimes.
Cyber Crime Is a Serious. PAGES 8 WORDS 2431. These "stepping stone" computes can be located anywhee in the physical wold because eal-space is ielevant to activity in cybespace (Benne, 379)." The use of stepping stones can make it difficult fo law enfocement to find whee an attack actually oiginated.
What is Cyber Crime. Cyber crime is the recent and perhaps the most knowing problem in the cyber world. "Cyber crime may be said to be those species, of which, genus is the common crime, and where either the computer is an subject of the behaviour forming crime" "Any criminal activity that uses a computer either as an instrumentality, target or a means for maintaining further crimes ...
Cybercrime is a criminal activity that uses a computer as an object over a network to commit a crime. Cybercriminals may include professional hackers, employees, children etc. BAL bharti case is an example of cybercrime committed by a juvenile. Harassment of friends was the reason. Email bombing is a technique of cybercrime.
Essay on Cyber Crime: Computer related networks that involve the use of computers, networks and gadgets can be interconnected to a cybercrime. In such crimes, the security of networks, persons, institutions or a whole nation could be at risk and threat. Hackers steal confidential data in unethical ways and utilize this information and data for spurious purposes.
Real World Example of Vulnerability, Risks and Threats. AbstractThe New York Times computer systems have fallen victim to cybersecurity attacks, following certain vulnerabilities that have allowed the hackers to infiltrate and access the sensitive…. Computer Science Cyber Crime Cyber Security. View full sample.
Cybersecurity Necessity and Benefits. Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender's cognitive state, possibilities for automation, and an attacker's subjective traits. Cybersecurity Incident Response and Risk Minimization.
But they are also more prevalent among young women than among women even a few years older (those ages 25-29). Women ages 18-24 who use the Internet are more than twice as likely as women ages 25-29 to have experienced sexual harassment online (25% vs. 10%) and three times as likely to have been stalked online (26% vs. 8%).
Cyber Crime Essay 600 words: Cybercrime is a crime that is an excellent crime in our society; cybercrime is a type of crime that is done through computers. It is created by misusing the computer, and it is networked improperly. This cybercrime is designed by some to intentionally harm other people by hacking or obtaining their private ...
Cyber Crime Essay. Cyber Crime is described as criminal activity committed via use of electronic communications with respect to cyber fraud or identity theft through phishing and spoofing. There are many other forms of cyber-crime also such as harassment, pornography etc. via use of information technology. 729 Words.
5523. In the 21st century, with the improvements in technology and science new concepts are integrated in our lives. Cyber crime is among those concepts that did not previously exist 15-20 years ago. Back In the old day's only conventional crime was discussed, which refers to those traditional, illegal behaviors that most people think of as ...
Speer (2000) defines cybercrime as activities in which computers, telephones, cellular equipment and other technological devices are used for illicit purposes. Most often cybercrime is done for personal information or financial gain. As a result, business organization, government agencies, online users and individuals become victims of ...
Essay 1 (250 Words) - Cyber Crime: A Threat to Society. Introduction. Crime is a word used for wrong deed or offence, but when it comes to cybercrime then, it can be defined as a crime done by internet to cause an immeasurable loss to the individual, organization, or the government. Cyber crime is a punishable offence committed by cyber ...
And in February 2024, the National Crime Agency took down LockBit, "the world's most harmful cyber-crime group", which had used ransomware attacks costing victims billions of pounds.
Cybersecurity is a process to save the networks, computer programs, and data from the illegal access or users that aim to access users data for personal uses and benefits. For the protection of data, many organizations develop a software. This software help to protect the data and information. Cybersecurity playing a big role in developing a ...
NPR suspended senior editor Uri Berliner for five days without pay after he wrote an essay accusing the network of losing the public's trust and appeared on a podcast to explain his argument.