Manage Azure Policy with Terraform
I am going to reverse the order I would normally explain a concept, in this blog we will look at the call to the module first and then dive into each of the components.

The Module Call
The initiative definition.
Let's step into the initiative definition next.
There are four top-level keys that we have to set:
- name — unique name for the initiative.
- display_name — the name displayed with the initiative.
- description — a description of what the policy is for and does.
- policies — objects containing the value definitions of BuiltIn and Custom policies.
With these properties we will be able to pass in all of the relevant values into our policies for a range of environments, further, we can also set a default if we don't have values specific to an environment. Let's take a look at the two types of policy definitions.
First, let's take a look at the policy properties:
- type — the type of policy that we are referencing; Custom or BuiltIn .
- file — if the policy is Custom we require the name of the file to import. This will be forced into the ${path.root}/policies/ directory by the Terraform code.
- id — the GUID id of an existing Azure policy provided by Microsoft, this is required when type is set to BuiltIn .
- default — the default parameter and effect values.
- dev/uat/prd/... — the key is the environment and the keys must be the same as default , this provides an optional setting of policy parameters by the environment.
Inside the default or environment block we have the following few properties:
- effect — the effect this policy will have, deny as an example. This property cannot be set on BuiltIn policies.
Custom Policy Definition
The key at the beginning AllowedLocations is how we will reference our policy and retrieve its components in the Terraform code. By allowing us to pass in the file to a json file it allows us to easily create custom policies alongside the fantastic baseline policies that Microsoft already give us. In the above example if we were running our Terraform code in the uat environment our code would use the properties we have defined in default as there are no environment-specific overrides. Allowing this makes our Terraform more powerful as perhaps when we start with Azure policy we don't necessarily understand what each environment requires, or they all explicitly require the same types of enforcement.
Built-in Policy Definition
The above is how we would set our parameters for a Built-in Azure policy. Remembering that we cannot set the effect of this policy as that is set by Microsoft, if you did need to alter that effect then it would be best to use a custom policy.
The Custom Policy Definition
We won't go into the mud on how to write an Azure Policy Definition if you're interested in that then check out the Azure Policy definition structure article by Microsoft.
The main point here is that you have a json definition of the Azure Policy either that you have written from scratch or perhaps you're pulling from the Azure portal so that you're now able to change the effect. As you can see on the high-lighted line below the value for the effect key is using string interpolation which will be set by templatefile in our Terraform code later. This is how we are going to be setting the effect on a per-environment basis.
Now we get into the fun stuff 🎉! Whilst going through the module I am going to split it up into some sub-sections to make it easier for us to talk through. Further, the module supports three scopes; Management Group ( mg ), Subscription ( sub ), and Resource Group ( rg ) I will just be referencing the resource group code below as it is almost identical to the other scopes.
The Module Interface .css-1a60e3e{transition-property:var(--chakra-transition-property-common);transition-duration:var(--chakra-transition-duration-fast);transition-timing-function:var(--chakra-transition-easing-ease-out);cursor:pointer;-webkit-text-decoration:none;text-decoration:none;outline:2px solid transparent;outline-offset:2px;color:inherit;font-weight:var(--chakra-fontWeights-normal);opacity:0;margin-left:var(--chakra-space-2);}.css-1a60e3e:hover,.css-1a60e3e[data-hover]{opacity:1;color:var(--chakra-colors-accent-500);-webkit-text-decoration:underline;text-decoration:underline;}.css-1a60e3e:focus,.css-1a60e3e[data-focus]{opacity:1;color:var(--chakra-colors-accent-500);-webkit-text-decoration:underline;text-decoration:underline;} #
If you've worked with me or read my articles before you would know that I treat the variables.tf as our documented API interface, think of it like an OpenAPI definition for a REST API. We will go through each variable one by one.
Our first variable is initiative_definition this is where we pass the full path to our definition yaml file like we discussed in The Initiative Definition .
Secondly, we need to pass in an environment , this must be in whatever format you've used in the initiative definition otherwise our Terraform code won't be able to retrieve the properties for an environment.
The most important input variable for us is the assignment variable, this is where we pass in a single or list of resource IDs we are going to be assigning the policy initiative. Allowing a list of assignments means that we can deal with assignments on a larger scale than a single resource. This is especially powerful when operating in an enterprise environment.
The name property of the assignments object we will use as part of our exemptions process, this ensures there is an easy and intentional lookup for us when we are trying to exempt a resource from a given initiative.
We also have some validation ensuring that the scope passed in is valid for our scenario.
When Azure Policy is concerned there is always going to be a requirement to be able to exempt some resources from having that policy applied/enforced on them. We manage that here through the use of the exemptions variable. This variable allows us to pass in a list of our exemptions object. We have the assignment_reference which as we mentioned above is a reference to name in the assignments object. This allows us to cleanly look up which assignment we are looking to exempt a given resource for.
In this variable, we need to validate that our exemption scope is valid, not only valid for Azure but for our given scenario. For instance, you can exempt a single resource from a policy but our module only supports down to the resource group is the most granular level. The second thing we are validating is that the category on the exemption is one of the two valid strings as expected by Microsoft.
Local Variables and Setup #
The first few pieces of setup that we are going to do is get some random_uuid 's setup that we can use for unique names of our policies, assignments and exemptions. Some properties in the azurerm the provider will auto-generate names for us, and others won't. In this instance, we are going to be dealing with the generation of the names.
Next, we need to decode our initiative_definition yaml into a Terraform object that we can use throughout our module. The policies local variable is a convenience variable for us so that we can quickly access the property. Also, if the way we access the policies object/key from our yaml file changes the code that consumes the policies doesn't need to know about that change.
Policy definitions #
We use an azurerm_policy_definition resource for a Custom policy and the azurerm_policy_definition data source for our BuiltIn policies. Doing so allows us to support both in our module.
When we are creating a Custom policy we have an object that is the filename of a policy json file before creating these policy instances we need to complete the templatefile on each policy. We will loop through our local.policies object and decodes each file to json once the templatefile action has been performed and we have applied the effect either via a default key from our initiative definition or an environment-specific one. This will only occur when the type property is Custom . Then we simply take the properties from our json and plug them into the resource. Some properties such as; metadata , policy_rule , and parameters require to have jsonencode on the object we are retrieving from the policy json as when we do our for_each those are converted into objects that Terraform can deal with.
For the data source, we simply need to loop through our local.policies object and filter to only use objects where the type property is BuiltIn . We do this by using a for expression within the for_each block. You can read more about that in my post Terraform For Expressions .
Policy Initiative #
Now that we have all of our policies in the state we require them its time to create our initiative and pass in the parameter values to each policy.
First off we will merge all our policies, both the resource and the data source. This will give us a single object to operate on. Using the new all_policies object we will get the parameter values, this will be environment specific if available otherwise it will return default . Having a pre-populated property for this allows for easy access within the azurerm_policy_set_definition resource.
Now we have two objects; all_policies and parameters these two combined are what allow us to set up all the policies within the initiative. Using a dynamic block -which you can read more about here - we will iterate over each policy in local.all_policies and assign the parameter_values from the local.parameters variable based on the key from our for_each . This is easily possible as when we created the local.parameters variable we did so by doing a for_each over the local.all_policies variable, this means that both the dynamic block and our parameters variable will use the same value as a key.
Policy Assignment #
The actual policy assignment portion of the module is most likely the simplest part. In this, we simply for through the var.assignment.assignments list and return a map where the key is the name property and the value is the id property of our assignments object.
We do however do a check on scope to ensure that we are operating on the right scope for the right resource type. In this instance the resource group. If we were doing this on azurerm_management_group_policy_assignment the resource then our check would be if var.assignment.scope == "mg" . You can see that in the full module code the terraform-azurerm-policy-initiative repository on my GitHub.
Policy Exemption #
The exemptions are where things get a little funkier, as we need to be able to match zero or more exemptions to the correct assignment.
Our first problem to solve is how we reference the correct Terraform resource block given each assignment type ( mg , sub , rg ) has its own Terraform resource. We do this by using the local variables' ability to reference a resource rather than a string. The try is important as Terraform will try to evaluate each of these even if they're not called which would be fine except that they will never all exist at the same time given assignment can only be done on a single scope.
With the above we can now access the right Terraform resource with the following:
To be honest, the ability to reference other resources with locals is INCREDIBLY powerful!!
Now that we can get the right policy assignment it's time to deal with the exemption side of things. For this, we are going to for through our assignments and our exemptions variables to create a new data structure containing all the relevant pieces of data. The assignment_id key will only ever return one value due to the use of the one function, this behavior is 💯 what we want if there was an instance where there were more than one assignment ID for a specific assignment_reference we would know someone has made a mistake. At this stage, we also validate that the assignment.scope is correct.
You can read more about the for expressions in my Terraform For Expressions post.
The name property is something that we construct out of the random_uuid for the exemptions as well as the last component of the resource ID. In the instance of a resource group that will be the name of the resource group. We also use this same logic to generate the id or key field on our for_each it is because of this that the resource we are referencing must exist before this code is run. If the resource does not exist then Terraform will error out saying that it is unable to determine the value of something that is part of the ID of a map. Whilst this behavior is not ideal I also don't think that it is that bad. The reason being is that should we ever try and exempt a policy on a resource that doesn't exist Terraform/Azure is going to wig out, therefore the behavior is more or less the same just at a different place in the run.
Closing Out #
Today we have gone through a module I've created to deal with creating Azure Policy initiatives. We went through the initiative definition, the custom policy definition and the module itself. By using this module we are now easily able to deploy and manage Azure Policies and exemptions on our cloud platform at scale. We also ensured that we can have the right level of flexibility when it comes to setting the parameter values and the effects on an Azure Policy.
For me, this was not what I would call an easy module to write, as it required me to think about how I could get the most amount of configuration information into the module without making it overly complex to consume. However, going back to My Development Workflow helped me through the process. This module had four iterations before it got to what we have here today.
You can find this module at BrendanThompson/terraform-azurerm-policy-initiative
I would love to hear from you on if you think this module is useful and what you have done to manage something as complex as Azure Policy in your cloud environment!
azurerm_role_assignment
Assigns a given Principal (User or Application) to a given Role.
Example Usage (using a built-in Role)
Example usage (custom role & service principal), example usage (custom role & user), argument reference.
The following arguments are supported:
name - (Optional) A unique UUID/GUID for this Role Assignment - one will be generated if not specified. Changing this forces a new resource to be created.
scope - (Required) The scope at which the Role Assignment applies too, such as /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333 , /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup , or /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup/providers/Microsoft.Compute/virtualMachines/myVM . Changing this forces a new resource to be created.
role_definition_id - (Optional) The Scoped-ID of the Role Definition. Changing this forces a new resource to be created. Conflicts with role_definition_name .
role_definition_name - (Optional) The name of a built-in Role. Changing this forces a new resource to be created. Conflicts with role_definition_id .
principal_id - (Required) The ID of the Principal (User or Application) to assign the Role Definition to. Changing this forces a new resource to be created.
Attributes Reference
The following attributes are exported:
- id - The Role Assignment ID.
Role Assignments can be imported using the resource id , e.g.
© 2018 HashiCorpLicensed under the MPL 2.0 License. https://www.terraform.io/docs/providers/azurerm/r/role_assignment.html
Azure Authorization Assignment
This page shows how to write Terraform and Azure Resource Manager for Authorization Assignment and write them securely.
Review your .tf file for Azure best practices
Shisho Cloud, our free checker to make sure your Terraform configuration follows best practices, is available (beta).
azurerm_role_assignment (Terraform)
The Assignment in Authorization can be configured in Terraform with the resource name azurerm_role_assignment . The following sections describe 10 examples of how to use the resource and its parameters.
- Example Usage from GitHub
Review your Terraform file for Azure best practices
- condition optional - string
- condition_version optional - string
- description optional - string
- id optional computed - string
- name optional computed - string
- principal_id required - string
- principal_type optional computed - string
- role_definition_id optional computed - string
- role_definition_name optional computed - string
- scope required - string
- skip_service_principal_aad_check optional computed - bool
- create optional - string
- delete optional - string
- read optional - string
- update optional - string
>> from Terraform Registry
- Explanation in Terraform Registry
Assigns a given Principal (User or Group) to a given Role.
Tips: Best Practices for The Other Azure Authorization Resources
In addition to the azurerm_role_definition, Azure Authorization has the other resources that should be configured for security reasons. Please check some examples of those resources and precautions.
azurerm_role_definition
Ensure to grant targeted permissions for roles
It is better to avoid giving too many permissions to a role. By following the principle of least privilege, you can reduce the risk of credential leakage.
Review your Azure Authorization settings
In addition to the above, there are other security points you should be aware of making sure that your .tf files are protected in Shisho Cloud.
Microsoft.Authorization/roleAssignments (Azure Resource Manager)
The roleAssignments in Microsoft.Authorization can be configured in Azure Resource Manager with the resource name Microsoft.Authorization/roleAssignments . The following sections describe how to use the resource and its parameters.
- name required - string
- type required - string
- apiVersion required - string
The role definition ID used in the role assignment.
The principal ID assigned to the role. This maps to the ID inside the Active Directory. It can point to a user, service principal, or security group.
>> from Azure Resource Manager Documentation
The Other Related Azure Authorization Resources
Azure Authorization Azure User Assigned Identity
Azure Authorization Definition
- Frequently asked questions
What is Azure Authorization Assignment?
Azure Authorization Assignment is a resource for Authorization of Microsoft Azure. Settings can be wrote in Terraform.
Where can I find the example code for the Azure Authorization Assignment?
For Terraform, the SamPoddar/caf-terraform-landingzones-starter , Elgeario/Starter and joshfranzen/caf-terraform-landingzones-starter source code examples are useful. See the Terraform Example section for further details.
For Azure Resource Manager, the LRuttenCN/cloud-custodian , LRuttenCN/cloud-custodian and juggernauthk108/pastebin source code examples are useful. See the Azure Resource Manager Example section for further details.

Automate config file reviews on your commits
Fix issues in your infrastructure as code with auto-generated patches.
Table of Contents
- Best Practces for The Other Resources
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
azurerm_role_assignment Error loading role assignment #23639
abhilash-hm commented Oct 22, 2023
No branches or pull requests
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
What are Azure management groups?
- 17 contributors
If your organization has many Azure subscriptions, you may need a way to efficiently manage access, policies, and compliance for those subscriptions. Management groups provide a governance scope above subscriptions. You organize subscriptions into management groups; the governance conditions you apply cascade by inheritance to all associated subscriptions.
Management groups give you enterprise-grade management at scale, no matter what type of subscriptions you might have. However, all subscriptions within a single management group must trust the same Azure Active Directory (Azure AD) tenant.
For example, you can apply policies to a management group that limits the regions available for virtual machine (VM) creation. This policy would be applied to all nested management groups, subscriptions, and resources and allow VM creation only in authorized regions.
Hierarchy of management groups and subscriptions
You can build a flexible structure of management groups and subscriptions to organize your resources into a hierarchy for unified policy and access management. The following diagram shows an example of creating a hierarchy for governance using management groups.
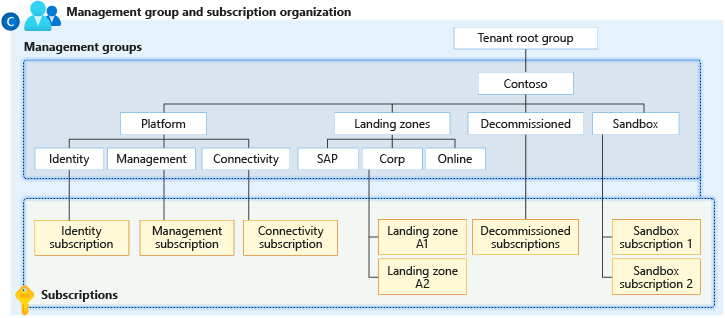
Diagram of a root management group holding both management groups and subscriptions. Some child management groups hold management groups, some hold subscriptions, and some hold both. One of the examples in the sample hierarchy is four levels of management groups, with the child level being all subscriptions.
You can create a hierarchy that applies a policy, for example, which limits VM locations to the West US region in the management group called "Corp". This policy will inherit all the Enterprise Agreement (EA) subscriptions that are descendants of that management group and will apply to all VMs under those subscriptions. This security policy cannot be altered by the resource or subscription owner, allowing for improved governance.
Management groups aren't currently supported in Cost Management features for Microsoft Customer Agreement (MCA) subscriptions.
Another scenario where you would use management groups is to provide user access to multiple subscriptions. By moving multiple subscriptions under that management group, you can create one Azure role assignment on the management group, which will inherit that access to all the subscriptions. One assignment on the management group can enable users to have access to everything they need instead of scripting Azure RBAC over different subscriptions.
Important facts about management groups
- 10,000 management groups can be supported in a single directory.
- This limit doesn't include the Root level or the subscription level.
- Each management group and subscription can only support one parent.
- Each management group can have many children.
- All subscriptions and management groups are within a single hierarchy in each directory. See Important facts about the Root management group .
Root management group for each directory
Each directory is given a single top-level management group called the root management group. The root management group is built into the hierarchy to have all management groups and subscriptions fold up to it. This root management group allows for global policies and Azure role assignments to be applied at the directory level. The Azure AD Global Administrator needs to elevate themselves to the User Access Administrator role of this root group initially. After elevating access, the administrator can assign any Azure role to other directory users or groups to manage the hierarchy. As an administrator, you can assign your account as the owner of the root management group.
Important facts about the root management group
- By default, the root management group's display name is Tenant root group and operates itself as a management group. The ID is the same value as the Azure Active Directory (Azure AD) tenant ID.
- To change the display name, your account must be assigned the Owner or Contributor role on the root management group. See Change the name of a management group to update the name of a management group.
- The root management group can't be moved or deleted, unlike other management groups.
- All resources in the directory fold up to the root management group for global management.
- New subscriptions are automatically defaulted to the root management group when created.
- Everyone who has access to a subscription can see the context of where that subscription is in the hierarchy.
- No one is given default access to the root management group. Azure AD Global Administrators are the only users that can elevate themselves to gain access. Once they have access to the root management group, the global administrators can assign any Azure role to other users to manage it.
Any assignment of user access or policy on the root management group applies to all resources within the directory . Because of this, all customers should evaluate the need to have items defined on this scope. User access and policy assignments should be "Must Have" only at this scope.
Initial setup of management groups
When any user starts using management groups, there's an initial setup process that happens. The first step is the root management group is created in the directory. Once this group is created, all existing subscriptions that exist in the directory are made children of the root management group. The reason for this process is to make sure there's only one management group hierarchy within a directory. The single hierarchy within the directory allows administrative customers to apply global access and policies that other customers within the directory can't bypass. Anything assigned on the root will apply to the entire hierarchy, which includes all management groups, subscriptions, resource groups, and resources within that Azure AD tenant.
Management group access
Azure management groups support Azure role-based access control (Azure RBAC) for all resource accesses and role definitions. These permissions are inherited to child resources that exist in the hierarchy. Any Azure role can be assigned to a management group that will inherit down the hierarchy to the resources. For example, the Azure role VM contributor can be assigned to a management group. This role has no action on the management group but will inherit to all VMs under that management group.
The following chart shows the list of roles and the supported actions on management groups.
*: The Management Group Contributor and Management Group Reader roles allow users to perform those actions only on the management group scope.
**: Role assignments on the root management group aren't required to move a subscription or management group to and from it.
See Manage your resources with management groups for details on moving items within the hierarchy.
Azure custom role definition and assignment
You can define a management group as an assignable scope in an Azure custom role definition. The Azure custom role will then be available for assignment on that management group and any management group, subscription, resource group, or resource under it. The custom role will inherit down the hierarchy like any built-in role. For information about the limitations with custom roles and management groups, see Limitations .
Example definition
Defining and creating a custom role doesn't change with the inclusion of management groups. Use the full path to define the management group /providers/Microsoft.Management/managementgroups/{ groupId } .
Use the management group's ID and not the management group's display name. This common error happens since both are custom-defined fields when creating a management group.
Issues with breaking the role definition and assignment hierarchy path
Role definitions are assignable scope anywhere within the management group hierarchy. A role definition can be defined on a parent management group while the actual role assignment exists on the child subscription. Since there's a relationship between the two items, you'll receive an error when trying to separate the assignment from its definition.
For example, let's look at a small section of a hierarchy for a visual.
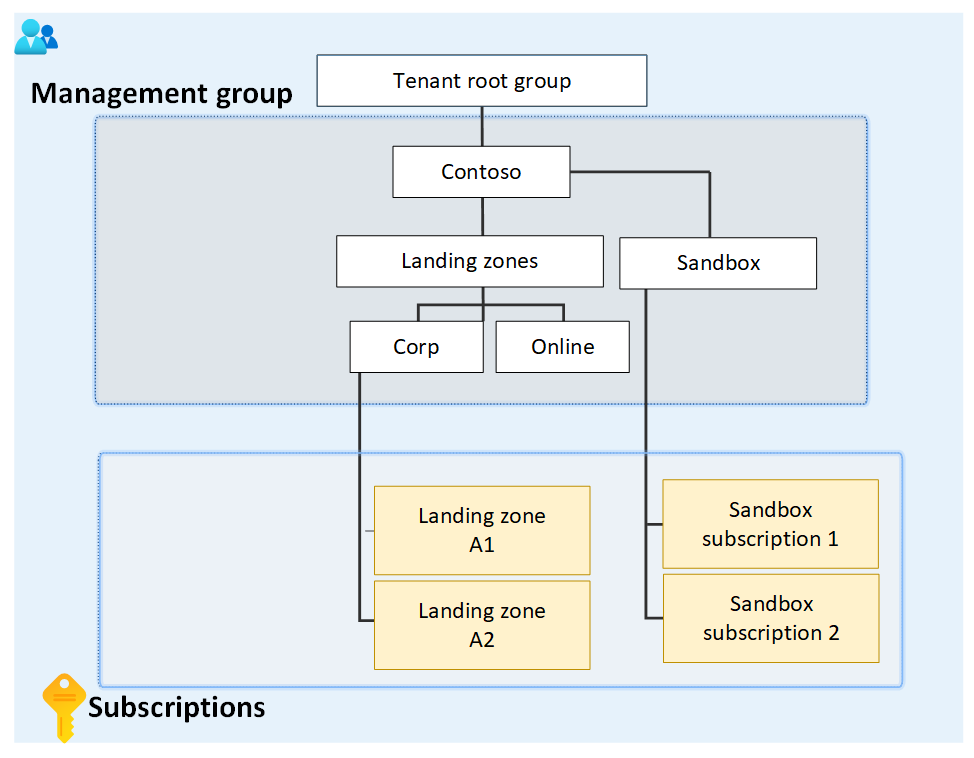
The diagram focuses on the root management group with child Landing zones and Sandbox management groups. The Landing zones management group has two child management groups named Corp and Online while the Sandbox management group has two child subscriptions.
Let's say there's a custom role defined on the Sandbox management group. That custom role is then assigned on the two Sandbox subscriptions.
If we try to move one of those subscriptions to be a child of the Corp management group, this move would break the path from subscription role assignment to the Sandbox management group role definition. In this scenario, you'll receive an error saying the move isn't allowed since it will break this relationship.
There are a couple different options to fix this scenario:
- Remove the role assignment from the subscription before moving the subscription to a new parent MG.
- Add the subscription to the role definition's assignable scope.
- Change the assignable scope within the role definition. In the above example, you can update the assignable scopes from Sandbox to the root management group so that the definition can be reached by both branches of the hierarchy.
- Create another custom role that is defined in the other branch. This new role requires the role assignment to be changed on the subscription also.
Limitations
There are limitations that exist when using custom roles on management groups.
- You can only define one management group in the assignable scopes of a new role. This limitation is in place to reduce the number of situations where role definitions and role assignments are disconnected. This situation happens when a subscription or management group with a role assignment moves to a different parent that doesn't have the role definition.
- Resource provider data plane actions can't be defined in management group custom roles. This restriction is in place as there's a latency issue with updating the data plane resource providers. This latency issue is being worked on and these actions will be disabled from the role definition to reduce any risks.
- Azure Resource Manager doesn't validate the management group's existence in the role definition's assignable scope. If there's a typo or an incorrect management group ID listed, the role definition is still created.
Moving management groups and subscriptions
To move a management group or subscription to be a child of another management group, three rules need to be evaluated as true.
If you're doing the move action, you need:
- Built-in role example: Owner
- Built-in role example: Owner , Contributor , Management Group Contributor
Exception : If the target or the existing parent management group is the root management group, the permissions requirements don't apply. Since the root management group is the default landing spot for all new management groups and subscriptions, you don't need permissions on it to move an item.
If the Owner role on the subscription is inherited from the current management group, your move targets are limited. You can only move the subscription to another management group where you have the Owner role. You can't move it to a management group where you're a Contributor because you would lose ownership of the subscription. If you're directly assigned to the Owner role for the subscription (not inherited from the management group), you can move it to any management group where you're assigned the Contributor role.
Azure Resource Manager caches management group hierarchy details for up to 30 minutes. As a result, moving a management group may not immediately be reflected in the Azure portal.
Audit management groups using activity logs
Management groups are supported within Azure Activity log . You can search all events that happen to a management group in the same central location as other Azure resources. For example, you can see all role assignments or policy assignment changes made to a particular management group.

When looking to query on management groups outside the Azure portal, the target scope for management groups looks like "/providers/Microsoft.Management/managementGroups/{ management-group-id }" .
Using the Azure Resource Manager REST API, you can enable diagnostic settings on a management group to send related Azure Activity log entries to a Log Analytics workspace, Azure Storage, or Azure Event Hub. For more information, see Management Group Diagnostic Settings - Create Or Update .
To learn more about management groups, see:
- Create management groups to organize Azure resources
- How to change, delete, or manage your management groups
- See options for How to protect your resource hierarchy
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
» azurerm_role_assignment
Assigns a given Principal (User or Application) to a given Role.
» Example Usage (using a built-in Role)
» example usage (custom role & service principal), » example usage (custom role & user), » argument reference.
The following arguments are supported:
name - (Optional) A unique UUID/GUID for this Role Assignment - one will be generated if not specified. Changing this forces a new resource to be created.
scope - (Required) The scope at which the Role Assignment applies too, such as /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333 , /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup , or /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup/providers/Microsoft.Compute/virtualMachines/myVM . Changing this forces a new resource to be created.
role_definition_id - (Optional) The Scoped-ID of the Role Definition. Changing this forces a new resource to be created. Conflicts with role_definition_name .
role_definition_name - (Optional) The name of a built-in Role. Changing this forces a new resource to be created. Conflicts with role_definition_id .
principal_id - (Required) The ID of the Principal (User or Application) to assign the Role Definition to. Changing this forces a new resource to be created.
» Attributes Reference
The following attributes are exported:
- id - The Role Assignment ID.
Role Assignments can be imported using the resource id , e.g.
Please enable Javascript to use this application

IMAGES
VIDEO
COMMENTS
API Management; Active Directory Domain Services; Advisor; Analysis Services; App Configuration; App Service (Web Apps) Application Insights ... azurerm_ pim_ eligible_ role_ assignment azurerm_ role_ assignment azurerm_ role_ assignment_ marketplace azurerm_ role_ definition azurerm_ user_ assigned_ identity Data Sources. azurerm_ role_ definition
Regarding the other request here: "Assigning role assignments to management groups, and policy assignment to management groups" - this should be possible today with the azurerm_role_definition and azurerm_policy_definition resources; albeit you can't create/reference Management Groups in Terraform at this time - would you be able to take a look ...
This module is a convenience wrapper around the azurerm_role_assignment resource to make it easier to create role assignments at different scopes for different types of principals. ... (Optional) The display name of the management group. role_assignments: (Required) The role assignments to be applied to the scope. role_definition: ...
I'm trying to create a new group and assign owner role to it via terraform but i'm facing issue to assignment . Below is the code. ... │ Error: Reference to undeclared resource │ │ on main.tf line 18, in resource "azurerm_role_assignment" "role-assign": │ 18: principal_id = data.azuread_group.group.object_id │ │ A data resource ...
The Terraform resources for Azure Policy use the Azure Provider. Create a new folder named policy-assignment and change directories into it. Create main.tf with the following code: Note. To create a Policy Assignment at a Management Group use the azurerm_management_group_policy_assignment resource, for a Resource Group use the azurerm_resource ...
In this instance the resource group. If we were doing this on azurerm_management_group_policy_assignment the resource then our check would be if var.assignment.scope == "mg". You can see that in the full module code the terraform-azurerm-policy-initiative repository on my GitHub.
This v0.13 module creates a nested Azure Management Group structure using a simple and dense input object. For an overview, please read the Management Groups documentation.. The default value for the input structure is based on Enterprise-Scale.. The input object has type = any for greater flexibility, including a mix and match of children and optional display_name attributes at the same scope ...
The Policy Assignment in Policy can be configured in Terraform with the resource name azurerm_management_group_policy_assignment. The following sections describe 10 examples of how to use the resource and its parameters.
Assigns a given Principal (User or Application) to a given Role.
The ID of the Subscription, Management Group or Resource group where the role is to be assigned. principal_ids: string: true: A list of Object IDs that define the User, Group or Service Principal to be assigned the role at the given scope. Module will iterate over each item, creating each assignment separately. role_definition_name: string: true
location - (Optional) The Azure Region where the Policy Assignment should exist. Changing this forces a new Policy Assignment to be created. metadata - (Optional) A JSON mapping of any Metadata for this Policy. not_scopes - (Optional) Specifies a list of Resource Scopes (for example a Subscription, or a Resource Group) within this Management ...
The Assignment in Authorization can be configured in Terraform with the resource name azurerm_role_assignment. The following sections describe 10 examples of how to use the resource and its parameters. ... (User or Group) to a given Role. >> from Terraform Registry. Tips: Best Practices for The Other Azure Authorization Resources ...
We even tried updating the resource type to azurerm_management_group_policy_assignment as these assignments are on the root management group. The same code with the latest version works on newly created assignments and roles. But the issue is only with the existing roles assignments that were created with version 2.57.0. Steps to Reproduce
Another scenario where you would use management groups is to provide user access to multiple subscriptions. By moving multiple subscriptions under that management group, you can create one Azure role assignment on the management group, which will inherit that access to all the subscriptions. One assignment on the management group can enable users to have access to everything they need instead ...
The ID of the Subscription, Management Group or Resource group where the role is to be assigned. principal_ids: string: true: A list of Object IDs that define the User, Group or Service Principal to be assigned the role at the given scope. Module will iterate over each item, creating each assignment separately. role_definition_name: string: true
Conflicts with role_definition_id. principal_id - (Required) The ID of the Principal (User or Application) to assign the Role Definition to. Changing this forces a new resource to be created. » Attributes Reference The following attributes are exported: id - The Role Assignment ID. » Import Role Assignments can be imported using the resource ...
<div class="navbar header-navbar"> <div class="container"> <div class="navbar-brand"> <a href="/" id="ember34" class="navbar-brand-link active ember-view"> <span id ...
I am trying to deploy the API management in the existing vnet subnet. Its an internal API management gateway stv2 so i have to provide the public IP as well as Public IP address is required to use availability zones since my service is in a virtual network".Other team has setup the required infrastructure already like vnets, subnets, Function ...
management_group_id - (Required) The Management Group ID at which the Policy Remediation should be applied. Changing this forces a new resource to be created. policy_assignment_id - (Required) The ID of the Policy Assignment that should be remediated.