
- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources

Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved

Latest Research Topics in Networking
Latest Research Topics in Networking offer newfangled project topics for our students from bachelors and master degree (B.E/M.E/M.Phil/M.Tech/MCA) in the field of networking. Networking is the biggest and fastest emerging area, making it hinder students with new research into networking technologies. However, students spend more money on their networking projects. To help our students, we also offer the latest networking projects at optimum cost as far as we also provided 5000+ projects from 120+ countries students from all over the world.
We develop projects both in software and hardware, and in software, we use both open source and proprietary software. We also suggest our students always choose the latest topics because the latest ideas only give something innovative and colorful.
Think well…Always be a part of us… we pose your pioneering projects…..
Topics in Networking
Latest Research Topics in Networking covers possible list of topics intended also for under graduate and also post graduate students and scholars. In networking, security is one of the major issues in all types of wired and wireless networks, e.g., cloud networking. There is also a lot of research in the networking field because it is also a vast area that prefers among more users.
Generally, networking is defined as the computing devices that exchange information and share ideas among individuals or groups of devices or users using either wired or wireless connection.
Let us see the latest topics in networking,
- Secure and control sensitive data also in cloud environment (any)
- The future of IoT and also bio metrics
- Software defined networking
- Network security and also cryptography
- Network Function Virtualization
- Cognitive computing and also machine learning
- Micro services architecture
- Adaptive security
- Augmented and virtual reality
- Cloud networking
- Big data analytics in mobile networking
- Smart personal assistants
- Wearable’s in sensor networks
- Blockchain as a service (BaaS)
- Containerization (traditional virtualization)
- Resource allocation SDN
- Ultra dense wireless networks planning
- SDN + Virtualized radio Access Networks also with Fog computing
- Spectrum efficiency enhancement by LTE-U also with Wi-Fi
- 5G wireless backhaul networks
- SDN based Elastic optical networks also in cloud.
- Green mobile cloud network: Green cloudlet
- C-RAN: Cloud Radio Access Network
- 5G networks multicasting
- Traffic engineering also in software defined networks
- D2D communication in 5G
- Over Wi-Fi secure device-to-device communication
- Cloud Robotics
- 5G networks for visible light communication
- Big data in mobile cloud networks
- Prevention and also in detection of network attacks
- SDN network automation to 802.11ac and also in IPv6
Simulation Tools, Software’s and Programming Languages Used in Networking Projects
Programming languages:.
- R-programming
- Matlab and also in scilab
Simulation Software’s:
- Psimulator2
- Network simulators (NS2 and also in NS3)
Other Tools:
- Matlab Simulink
- Matlab tool boxes
- Word net tool
- And also in MADAMIRA tool
We also provide a few collections of networking and simulation tools, software, and programming languages for developing projects in the networking and other areas. For each project, we give PPT, documents, video files, and also completed code implementation. Our additional support for our students is journal paper writing support, paper publication in high reputed journals, and thesis writing support.
A good beginning is often overt as happy endings…..
Let us come together for your immense research…… , related pages, services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work
- How it works
Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computer Networking Dissertation Topics
Published by Carmen Troy at January 5th, 2023 , Revised On August 16, 2023
A dissertation is an essential aspect of completing your degree program. Whether you are pursuing your master’s or are enrolled in a PhD program, you will not be awarded a degree without successfully submitting a thesis. To ensure that your thesis is submitted successfully without any hindrances, you should first get your topic and dissertation outline approved by your professor. When approving, supervisors focus on a lot of aspects. However, relevance, recency, and conciseness of your topic play a huge role in accepting or rejecting your topic.
As a computer networking student, you have a variety of networking topics to choose from. With the field evolving with each passing day, you must ensure that your thesis covers recent computer networking topics and explores a relevant problem or issue. To help you choose the right topic for your dissertation, here is a list of recent and relevant computer networking dissertation topics.
2022 Computer Networking Dissertation Topics
Topic 1: an evaluation of the network security during machine to machine communication in iot.
Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT.
Objectives:
- To evaluate the factors affecting the network security of IoT devices.
- To determine the methods for increasing data integrity in M2M communication against physical tampering and unauthorised monitoring.
- To evaluate the network security issues associated with M2M communication in IoT and offer suitable recommendations for improvement.
Topic 2: An analysis of the cybersecurity challenges in public clouds and appropriate intrusion detection mechanisms.
Research Aim: The aim of the research is to analyse the cybersecurity challenges in public clouds and the appropriate intrusion detection mechanisms.
Objectives:
- To analyse the types of cybersecurity threats impacting public clouds.
- To determine some of the competent intrusion detection techniques that can be used in cloud computing.
- To investigate the cybersecurity challenges in public clouds and offer mitigating with appropriate intrusion detection techniques.
Topic 3: Investigating the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
Research Aim: The research aims to investigate the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
- To analyse the benefits of SaaS ERP over traditional ERP.
- To evaluate the characteristics of SaaS architecture in cloud computing and determine its varieties.
- To investigate how SaaS cloud ERP impacts business scalability and cost-effectiveness.
Topic 4: An evaluation of the requirements of cloud repatriation and the challenges associated with it.
Research Aim: The research aims to evaluate the requirements of cloud repatriation in organisations and the associated challenges
- To analyse the key factors of cloud repatriation.
- To determine the challenges associated with cloud repatriation from public clouds.
- To evaluate the need for cloud repatriation in organisations and the associated complexities
Topic 5: An examination of the security mechanisms in decentralised networks and the ways of enhancing system robustness
Research Aim: The research aims to investigate the security mechanisms in decentralised networks and the ways of enhancing system robustness.
- To analyse the concept of decentralised networks and understand its difference from centralised networks.
- To analyse the security mechanisms in decentralised networks for determining how it offers visibility and traceability.
- To investigate the security mechanisms in decentralised networks and how system robustness can be increased for better privacy and security.
Computer Networking Dissertation Topics for 2021
Exploring the importance of computer networking in today’s era.
Research Aim: Even though computer networking has been practised for a few years now, its importance has increased immensely over the past two years. A few main reasons include the use of technology by almost every business and the aim to offer customers an easy and convenient shopping experience. The main aim of this research will be to explain the concepts of computer networking, its benefits, and its importance in the current era. The research will also discuss how computer networking has helped businesses and individuals perform their work and benefit from it. The research will then specifically state examples where computer networking has brought positive changes and helped people achieve what they want.
Wireless Networks in Business Settings – An Analysis
Research Aim: Wireless networks are crucial in computer networking. They help build networks seamlessly, and once the networks are set up on a wireless network, it becomes extremely easy for the business to perform its daily activities. This research will investigate all about wireless networks in a business setting. It will first introduce the various wireless networks that can be utilized by a business and will then talk about how these networks help companies build their workflow around it. The study will analyze different wireless networks used by businesses and will conclude how beneficial they are and how they are helping the business.
Understanding Virtual Private Networks – A Deep Analysis of their Challenges
Research Aim: Private virtual networks (VPN) are extremely common today. These are used by businesses and individuals alike. This research aims to understand how these networks operate and how they help businesses build strong and successful systems and address the challenges of VPNs. A lot of businesses do not adopt virtual private networks due to the challenges that they bring. This research will address these challenges in a way that will help businesses implement VPN successfully.
A Survey of the Application of Wireless Sensor Networks
Research Aim: Wireless sensor networks are self-configured, infrastructure-less wireless networks to pass data. These networks are now extremely popular amongst businesses because they can solve problems in various application domains and possess the capacity to change the way work is done. This research will investigate where wireless sensor networks are implemented, how they are being used, and how they are performing. The research will also investigate how businesses implement these systems and consider factors when utilizing these wireless sensor networks.
Computer Network Security Attacks – Systems and Methods to Respond
Research Aim: With the advent of technology today, computer networks are extremely prone to security attacks. A lot of networks have security systems in place. However, people with nefarious intent find one way to intrude and steal data/information. This research will address major security attacks that have impacted businesses and will aim to address this challenge. Various methods and systems will be highlighted to protect the computer networks. In addition to this, the research will also discuss various methods to respond to attacks and to keep the business network protected.
Preventing a Cyberattack – How Can you Build a Powerful Computer Network?
Research Aim: Cyberattacks are extremely common these days. No matter how powerful your network is, you might be a victim of phishing or hacking. The main aim of this research will be to outline how a powerful computer network can be built. Various methods to build a safe computer network that can keep data and information will be outlined, and the study will also highlight ways to prevent a cyberattack. In addition to this, the research will talk about the steps that should be taken to keep the computer network safe. The research will conclude with the best way and system to build a powerful and safe computer network.
Types of Computer Networks: A Comparison and Analysis
Research Aim: There are different types of computer networks, including LAN, WAN, PAN, MAN, CAN, SAN, etc. This research will discuss all the various types of computer networks to help readers understand how all these networks work. The study will then compare the different types of networks and analyze how each of them is implemented in different settings. The dissertation will also discuss the type of computer networks that businesses should use and how they can utilize them for their success. The study will then conclude which computer network is the best and how it can benefit when implemented.
Detecting Computer Network Attacks by Signatures and Fast Content Analysis
Research Aim: With technological advancement, today, many computer network attacks can be detected beforehand. While many techniques are utilized for detecting these attacks, the use of signatures and fast content analysis are the most popular ones. This research will explore these techniques in detail and help understand how they can detect a computer network attack and prevent it. The research will present different ways these techniques are utilised to detect an attack and help build powerful and safe computer networks. The research will then conclude how helpful these two techniques are and whether businesses should implement them.
Overview of Wireless Network Technologies and their Role in Healthcare
Research Aim: Wireless network technologies are utilised by several industries. Their uses and benefits have helped businesses resolve many business problems and assisted them in conducting their daily activities without any hindrance. This networking topic will help explore how wireless network technologies work and will talk about their benefits. This research aims to find out how wireless technologies help businesses carry out their daily routine tasks effortlessly. For this research, the focuas will be the healthcare industry. The study will investigate how wireless network technology has helped the healthcare sector and how it has benefited them to perform their daily tasks without much effort.
Setting up a Business Communication System over a Computer Network
Research Aim: Communication is an essential aspect of every business. Employees need to communicate effectively to keep the business going. In the absence of effective communication, businesses suffer a lot as the departments are not synchronized, and the operations are haphazard. This research will explore the different ways through which network technologies help conduct smooth and effective communication within organizations. This research will conclude how wireless networks have helped businesses build effective communication systems within their organization and how they have benefited from it. It will then conclude how businesses have improved and solved major business problems with the help of these systems.
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find computer networking dissertation topics.
To find computer networking dissertation topics:
- Follow industry news and emerging technologies.
- Investigate unresolved networking challenges.
- Review recent research papers.
- Explore IoT, cybersecurity, cloud computing.
- Consider real-world applications.
- Select a topic aligned with your expertise and career aspirations.
You May Also Like
Here is a list of Research Topics on Philosophy to help you get started with the process of findings related dissertation idea of philosophy.
Need interesting and manageable chemical engineering dissertation topics or thesis? Here are the trending chemical engineering dissertation titles so you can choose the most suitable one.
Need interesting and manageable law dissertation topics or thesis? Here are the trending law dissertation titles so you can choose the most suitable one.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
Topics in Networking Research
- Conference paper
- Cite this conference paper

- Debasis Mitra 1
Part of the book series: Lecture Notes in Computer Science ((LNCCN,volume 4516))
Included in the following conference series:
- International Teletraffic Congress
1404 Accesses
What are the big movements in networking that researchers should heed? A standout is the global spread of communities of interest (the networking analogue of the flat world) and their need for “dynamic virtual networks” that support rich applications requiring resources from several domains. The imperative for inter-networking, i.e., the enablement of coordinated sharing of resources across multiple domains, is certain. This challenge has many facets, ranging from the organizational, e.g., different, possibly competing, owners to the technical, e.g., different technologies. Yet another key characteristic of the emerging networking environment is that the service provider is required to handle ever-increasing uncertainty in demand, both in volume and time. On the other hand there are new instruments available to handle the challenge. Thus, inter-networking and uncertainty management are important challenges of emerging networking that deserve attention from the research community.
We describe research that touch on both topics. First, we consider a model of data-optical inter-networking, where routes connecting end-points in data domains are concatenation of segments in the data and optical domains. The optical domain in effect acts as a carrier’s carrier for multiple data domains. The challenge to inter-networking stems from the limited view that the data and optical domains have of each other. Coordination has to be enabled through parsimonious and qualitatively restrictive information exchange across domains. Yet the overall optimization objective, which is to maximize end-to-end carried traffic with minimum lightpath provisioning cost, enmeshes data and optical domains. This example of inter-networking also involves two technologies. A mathematical reflection of the latter fact is the integrality of some of the decision variables due to wavelengths being the bandwidth unit in optical transmission. Through an application of Generalized Bender’s Decomposition the problem of optimizing provisioning and routing is decomposed into sub-problems, which are solved by the different domains and the results exchanged in iterations that provably converge to the global optimum.
In turning to uncertainty management we begin by presenting a framework for stochastic traffic management. Traffic demands are uncertain and given by probability distributions. While there are alternative perspectives (and metrics) to resource usage, such as social welfare and network revenue, we adopt the latter, which is aligned with the service provider’s interests. Uncertainty introduces the risk of misallocation of resources. What is the right measure of risk in networking? We examine various definitions of risk, some taken from modern portfolio theory, and suggest a balanced solution. Next we consider the optimization of an objective which is a risk-adjusted measure of network revenue. We obtain conditions under which the optimization problem is an instance of convex programming. Studies of the properties of the solution show that it asymptotically meets the stochastic efficiency criterion. Service providers’ risk mitigation policies are suggested. For instance, by selecting the appropriate mix of long-term contracts and opportunistic servicing of random demand, the service provider can optimize its risk-adjusted revenue. The “efficient frontier”, which is the set of Pareto optimal pairs of mean revenue and revenue risk, is useful to the service provider in selecting its operating point.
Joint work with Qiong Wang and Anwar Walid, Bell Labs, Murray Hill.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Author information
Authors and affiliations.
Bell Labs, Alcatel-Lucent, Murray Hill, NJ 07974, USA
Debasis Mitra
You can also search for this author in PubMed Google Scholar
Editor information
Rights and permissions.
Reprints and permissions
Copyright information
© 2007 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper.
Mitra, D. (2007). Topics in Networking Research. In: Mason, L., Drwiega, T., Yan, J. (eds) Managing Traffic Performance in Converged Networks. ITC 2007. Lecture Notes in Computer Science, vol 4516. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-72990-7_3
Download citation
DOI : https://doi.org/10.1007/978-3-540-72990-7_3
Publisher Name : Springer, Berlin, Heidelberg
Print ISBN : 978-3-540-72989-1
Online ISBN : 978-3-540-72990-7
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Networking is central to modern computing, from WANs connecting cell phones to massive data stores, to the data-center interconnects that deliver seamless storage and fine-grained distributed computing. Because our distributed computing infrastructure is a key differentiator for the company, Google has long focused on building network infrastructure to support our scale, availability, and performance needs, and to apply our expertise and infrastructure to solve similar problems for Cloud customers. Our research combines building and deploying novel networking systems at unprecedented scale, with recent work focusing on fundamental questions around data center architecture, cloud virtual networking, and wide-area network interconnects. We helped pioneer the use of Software Defined Networking, the application of ML to networking, and the development of large-scale management infrastructure including telemetry systems. We are also addressing congestion control and bandwidth management, capacity planning, and designing networks to meet traffic demands. We build cross-layer systems to ensure high network availability and reliability. By publishing our findings at premier research venues, we continue to engage both academic and industrial partners to further the state of the art in networked systems.
Recent Publications
Some of our teams.
Cloud networking
Global networking
Network infrastructure
We're always looking for more talented, passionate people.

Communications and Networking Research Group
Search form.
- Publications
PUBLICATIONS
Journal articles | other papers | conference papers | book chapters | technical reports, journal articles.
134. Vishrant Tripathi, Nick Jones, Eytan Modiano, Fresh-CSMA: A Distributed Protocol for Minimizing Age of Information, IEEE Journal on Communications and Networks, 2024.
133. Bai Liu, Quang Nguyen, Qingkai Liang, Eytan Modiano, Tracking Drift-Plus-Penalty: Utility Maximization for Partially Observable and Controllable Networks, IEEE/ACM Transactions on Networking, 2024.
132. Xinzhe Fu, Eytan Modiano, Optimal Routing to Parallel Servers with Unknown Utilities – Multi-armed Bandit With Queues, IEEE/ACM Transactions on Networking, January 2022.
131. Bai Liu, Qingkai Liang, Eytan Modiano, Tracking MaxWeight: Optimal Control for Partially Observable and Controllable Networks, IEEE/ACM Transactions on Networking, August 2023.
130. Xinzhe Fu, Eytan Modiano, Joint Learning and Control in Stochastic Queueing Networks with unknown Utilities, Proceedings of the ACM on Measurement and Analysis of Computing Systems, 2023.
129. Vishrant Tripathi, Rajat Talak, Eytan Modiano, Information Freshness in Multi-Hop Wireless Networks, IEEE/ACM Transactions on Networking,” April 2023.
128. Xinzhe Fu, Eytan Modiano, “ Learning-NUM: Network Utility Maximization with Unknown Utility Functions and Queueing Delay ,” IEEE/ACM Transactions on Networking,” 2022.
127. Bai Liu, Qiaomin Xie, Eytan Modiano, " RL-QN: A Reinforcement Learning Framework for Optimal Control of Queueing Systems ," ACM Transactions on Modeling and Performance Evaluation of Computing Systems (TOMPECS), 2022.
126. Xinzhe Fu and E. Modiano, “ Elastic Job Scheduling with Unknown Utility Functions ,” Performance Evaluation, 2021.
125. Bai Liu and E. Modiano, “ Optimal Control for Networks with Unobservable Malicious Nodes ,” Performance Evaluation, 2021.
124. Vishrant Tripathi, Rajat Talak, Eytan Modiano, " Age Optimal Information Gathering and Dissemination on Graphs ,” Transactions on Mobile Computing, April 2021.
123. Xinyu Wu, Dan Wu, Eytan Modiano, “ Predicting Failure Cascades in Large Scale Power Systems via the Influence Model Framework, ” IEEE Transactions on Power Systems, 2021.
122. Roy D. Yates, Yin Sun, D. Richard Brown III, Sanjit K. Kaul, Eytan Modiano and Sennur Ulukus, “ Age of Information: An Introduction and Survey, ” Journal on Selected Areas in Communications, February 2021.
121. Jianan Zhang, Abhishek Sinha, Jaime Llorca, Anonia Tulino, Eytan Modiano, “ Optimal Control of Distributed Computing Networks with Mixed-Cast Traffic Flows ,” IEEE/ACM Transactions on Networking, 2021.
120. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, " Learning Algorithms for Minimizing Queue Length Regret ,” IEEE Transactions on Information Theory, 2021.
119. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, “ Throughput Maximization in Uncooperative Spectrum Sharing Networks ,” IEEE/ACM IEEE/ACM Transactions on Networking, Vol. 28, No. 6, December 2020.
118. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, “ Learning algorithms for scheduling in wireless networks with unknown channel statistics ,” Ad Hoc Networks, Vol. 85, pp. 131-144, 2019.
117. Rajat Talak, Eytan Modiano, “ Age-Delay Tradeoffs in Queueing Systems ,” IEEE Transactions on Information Theory, 2021.
116. Rajat Talak, Sertac Karaman, Eytan Modiano, " Improving Age of Information in Wireless Networks with Perfect Channel State Information ,” IEEE/ACM Transactions on Networking, Vol. 28, No. 4, August 2020.
115. Igor Kadota and Eytan Modiano, “ Minimizing the Age of Information in Wireless Networks with Stochastic Arrivals ,” IEEE Transactions on Mobile Computing, 2020.
114. Rajat Talak, Sertac Karaman, Eytan Modiano, “ Optimizing Information Freshness in Wireless Networks under General Interference Constraints ,” IEEE/ACM transactions on Networking, Vol. 28, No. 1, February 2020.
113. X. Fu and E. Modiano, " Fundamental Limits of Volume-based Network DoS Attacks ," Proceedings of the ACM on Measurement and Analysis of Computing Systems, Vol. 3, No. 3, December 2019.
112. Rajat Talak, Sertac Karaman, Eytan Modiano, “ Capacity and Delay Scaling for Broadcast Transmission in Highly Mobile Wireless Networks ,” IEEE Transactions on Mobile Computing, 2019.
111. Abhishek Sinha and Eytan Modiano, “ Throughput-Optimal Broadcast in Wireless Networks with Point-to-Multipoint Transmissions , IEEE Transactions on Mobile Computing, Vol. 19, No. 9, September 2020.
110. Yu-Pin Hsu, Eytan Modiano, Lingjie Duan, “ Scheduling Algorithms for Minimizing Age of Information in Wireless Broadcast Networks with Random Arrivals ,” IEEE Transactions on Mobile Computing, Vol. 19, No. 12, December 2020.
109. Xiaolin Jiang, Hossein S. Ghadikolaei, Gabor Fodor, Eytan Modiano, Zhibo Pang, Michele Zorzi, Carlo Fischione, " Low-latency Networking: Where Latency Lurks and How to Tame It ,” Proceedings of the IEEE, 2019.
108. Jianan Zhang, Edmund Yeh, Eytan Modiano, “ Robustness of Interdependent Random Geometric Networks ,” IEEE Transactions on Network Science and Engineering, Vol. 6, No. 3, July-September 2019.
107. Qingkai Liang, Hyang-Won Lee, Eytan Modiano, “ Robust Design of Spectrum-Sharing Networks ,” IEEE Transactions on Mobile Computing, Vol. 18, No. 8, August 2019.
106. A. Sinha, L. Tassiulas, E. Modiano, “ Throughput-Optimal Broadcast in Wireless Networks with Dynamic Topology ,” IEEE Transactions on Mobile Computing, Vol. 18, No. 5, May 2019.
105. Igor Kadota, Abhishek Sinha, Eytan Modiano, “ Scheduling Algorithms for Optimizing Age of Information in Wireless Networks With Throughput Constraints ,” IEEE/ACM Transactions on Networking, August 2019.
104. Igor Kadota, Abhishek Sinha, Rahul Singh, Elif Uysal-Biyikoglu, Eytan Modjano, “ Scheduling Policies for Minimizing Age of Information in Broadcast Wireless Networks ,” IEEE/ACM Transactions on Networking, Vol. 26, No. 5, October 2018.
103. Jianan Zhang and Eytan Modiano, “ Connectivity in Interdependent Networks ,” IEEE/ACM Transactions on Networking, 2018.
102. Qingkai Liang, Eytan Modiano, “ Minimizing Queue Length Regret Under Adversarial Network Models ,” Proceedings of the ACM on Measurement and Analysis of Computing Systems, Volume 2, Issue 1, April 2018, Article No.: 11, pp 1-32. (same as Sigmetrics 2018).
101. A. Sinha and E. Modiano, “ Optimal Control for Generalized Network Flow Problems ,” IEEE/ACM Transactions on Networking, 2018.
100. Hossein Shokri-Ghadikolaei, Carlo Fischione, Eytan Modiano “ Interference Model Similarity Index and Its Applications to mmWave Networks ,” IEEE Transactions on Wireless Communications, 2018.
99. Matt Johnston, Eytan Modiano, “ Wireless Scheduling with Delayed CSI: When Distributed Outperforms Centralized, ’ IEEE Transactions on Mobile Computing, 2018.
98. A. Sinha, G. Paschos, E. Modiano, “ Throughput-Optimal Multi-hop Broadcast Algorithms ," IEEE/ACM Transactions on Networking, 2017.
97. Nathan Jones, Georgios Paschos, Brooke Shrader, Eytan Modiano, " An Overlay Architecture for Throughput Optimal Multipath Routing ,” IEEE/ACM Transactions on Networking, 2017.
96. Greg Kuperman, Eytan Modiano, “ Providing Guaranteed Protection in Multi-Hop Wireless Networks with Interference Constraints ,” IEEE Transactions on Mobile Computing, 2017.
95. Matt Johnston, Eytan Modiano, Isaac Kesslassy, “ Channel Probing in Opportunistic Communications Systems ,” IEEE Transactions on Information Theory, November, 2017.
94. Anurag Rai, Georgios Paschos, Chih-Ping Lee, Eytan Modiano, " Loop-Free Backpressure Routing Using Link-Reversal Algorithms ", IEEE/ACM Transactions on Networking, October, 2017.
93. Matt Johnston and Eytan Modiano, “" Controller Placement in Wireless Networks with Delayed CSI ,” IEEE/ACM Transactions on Networking, 2017.
92. Jianan Zheng, E. Modiano, D. Hay, " Enhancing Network Robustness via Shielding ,” IEEE Transactions on Networking, 2017.
91. M. Markakis, E. Modiano, J.N. Tsitsiklis, “ Delay Analysis of the Max-Weight Policy under Heavy-Tailed Traffic via Fluid Approximations ,” Mathematics of Operations Research, October, 2017.
90. Qingkai Liang and E. Modiano, “ Survivability in Time-Varying Graphs ,” IEEE Transactions on Mobile Computing, 2017.
89. A. Sinha, G. Paschos, C. P. Li, and E. Modiano, “ Throughput-Optimal Multihop Broadcast on Directed Acyclic Wireless Networks ," IEEE/ACM Transactions on Networking, Vol. 25, No. 1, Feb. 2017.
88. G. Celik, S. Borst, , P. Whiting , E. Modiano, “ Dynamic Scheduling with Reconfiguration Delays ,” Queueing Systems, 2016.
87. G. Paschos, C. P. Li, E. Modiano, K. Choumas, T. Korakis, “ In-network Congestion Control for Multirate Multicast ,” IEEE/ACM Transactions on Networking, 2016.
86. H. Seferoglu and E. Modiano, “ TCP-Aware Backpressure Routing and Scheduling ,” IEEE Transactions on Mobile Computing, 2016.
85. H. Seferoglu and E. Modiano, “ Separation of Routing and Scheduling in Backpressure-Based Wireless Networks ," IEEE/ACM Transactions on Networking, Vol. 24, No. 3, 2016.
84. M. Markakis, E. Modiano, J.N. Tsitsiklis, “ Delay Stability of Back-Pressure Policies in the presence of Heavy-Tailed Traffic ,” IEEE/ACM Transactions on Networking, 2015.
83. S. Neumayer, E. Modiano, “ Network Reliability Under Geographically Correlated Line and Disk Failure Models ,” Computer Networks, to appear, 2016.
82. S. Neumayer, E. Modiano, A. Efrat, “ Geographic Max-Flow and Min-Cut Under a Circular Disk Failure Model ,” Computer Networks, 2015.
81. Marzieh Parandehgheibi, Hyang-Won Lee, Eytan Modiano, Survivable Path Sets: A new approach to survivability in multi-layer networks ,” IEEE Journal on Lightwave Technology, 2015.
80. G. Kuperman, E. Modiano, A. Narula-Tam, “ Network Protection with Multiple Availability Guarantees ,” Computer Networks, 2015.
79. G. Kuperman, E. Modiano, A. Narula-Tam, “ Analysis and Algorithms for Partial Protection in Mesh Networks ,” IEEE/OSA Journal of Optical Communications and Networks, 2014.
78. Krishna Jagannathan, Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Throughput Optimal Scheduling over Time-Varying Channels in the presence of Heavy-Tailed Traffic ,” IEEE Transactions on Information Theory, 2014.
77. Chih-Ping Li and Eytan Modiano, “ Receiver-Based Flow Control for Networks in Overload ," IEEE/ACM Transactions on Networking, Vol. 23, No. 2, 2015.
76. Matthew Johnston, Hyang-Won Lee, Eytan Modiano, “ A Robust Optimization Approach to Backup Network Design with Random Failures ,” IEEE/ACM Transactions on Networking, Vol. 23, No. 4, 2015.
75. Guner Celik and Eytan Modiano, “ Scheduling in Networks with Time-Varying Channels and Reconfiguration Delay ," IEEE/ACM Transactions on Networking, Vol. 23, No. 1, 2015.
74. Matt Johnston, H.W. Lee, E. Modiano, “ Robust Network Design for Stochastic Traffic Demands ," IEEE Journal of Lightwave Technology, 2013.
73. Mihalis Markakis, Eytan Modiano, John Tsitsiklis, “ Max-Weight Scheduling in Queueing Networks With Heavy-Tailed Traffic, ” IEEE/ACM Transactions on Networking, 2014.
72. Kayi Lee, Hyang-Won Lee, Eytan Modiano, " Maximizing Reliability in WDM Networks through Lightpath Routing ,” IEEE ACM Transactions on Networking, 2014.
71. Krishna Jaggannathan and Eytan Modiano, “ The Impact of Queue Length Information on Buffer Overflow in Parallel Queues ,” IEEE transactions on Information Theory, 2013.
70. Krishna Jagannathan, Ishai Menashe, Gil Zussman, Eytan Modiano, “ Non-cooperative Spectrum Access - The Dedicated vs. Free Spectrum Choice ,” IEEE JSAC, special issue on Economics of Communication Networks & Systems, to appear, 2012.
69. Guner Celik and Eytan Modiano, “ Dynamic Server Allocation over Time Varying Channels with Switchover Delay ," IEEE Transactions on Information Theory, to appear, 2012.
68. Anand Srinivas and Eytan Modiano, " Joint Node Placement and Assignment for Throughput Optimization in Mobile Backbone Networks ,” IEEE JSAC, special issue on Communications Challenges and Dynamics for Unmanned Autonomous Vehicles, June, 2012.
67. Guner Celik and Eytan Modiano, “ Controlled Mobility in Stochastic and Dynamic Wireless Networks ," Queueing Systems, 2012.
66. Krishna Jagannathan, Shie Mannor, Ishai Menache, Eytan Modiano, “ A State Action Frequency Approach to Throughput Maximization over Uncertain Wireless Channels ,” Internet Mathematics, Vol. 9, Nos. 2–3: 136–160.
65. Long Le, E. Modiano, N. Shroff, “Optimal Control of Wireless Networks with Finite Buffers ,” IEEE/ACM Transactions on Networking, to appear, 2012.
64. K. Jagannathan, M. Markakis, E. Modiano, J. Tsitsiklis, “Queue Length Asymptotics for Generalized Max-Weight Scheduling in the presence of Heavy-Tailed Traffic,” IEEE/ACM Transactions on Networking, Vol. 20, No. 4, August 2012.
63. Kayi Lee, Hyang-Won Lee, Eytan Modiano, “ Reliability in Layered Networks with Random Link Failures, ” IEEE/ACM Transactions on Networking, December 2011.
62. Krishna Jagannathan, Eytan Modiano, Lizhong Zheng, “ On the Role of Queue Length Information in Network Control ,” IEEE Transactions on Information Theory, September 2011.
61. Hyang-Won Lee, Long Le, Eytan Modiano, “ Distributed Throughput Maximization in Wireless Networks via Random Power Allocation, ” IEEE Transactions on Mobile Computing, 2011.
60. Sebastian Neumayer, Gil Zussman, Rueven Cohen, Eytan Modiano, " Assessing the Vulnerability of the Fiber Infrastructure to Disasters, " IEEE/ACM Transactions on Networking, December 2011.
59. Kayi Lee, Eytan Modiano, Hyang-Won Lee, “ Cross Layer Survivability in WDM-based Networks ,” IEEE/ACM Transactions on Networking, August 2011.
58. Emily Craparo, Jon How, and Eytan Modiano, “Throughput Optimization in Mobile Backbone Networks,” IEEE Transactions on Mobile Computing, April, 2011.
57. Hyang-Won Lee, Kayi Lee, and Eytan Modiano, “Diverse Routing in Networks with Probabilistic Failures,” IEEE/ACM Transactions on Networking, December, 2010.
56. Guner Celik, Gil Zussman, Wajahat Khan and Eytan Modiano, “MAC Protocols For Wireless Networks With Multi-packet Reception Cabaility ,” IEEE Transactions on Mobile Computing, February, 2010.
55. Atilla Eryilmaz, Asuman Ozdaglar, Devavrat Shah, and Eytan Modiano, “Distributed Cross-Layer Algorithms for the Optimal Control of Multi-hop Wireless Networks,” IEEE/ACM Transactions on Networking, April 2010.
54. Murtaza Zafer and Eytan Modiano, “Minimum Energy Transmission over a Wireless Channel With Deadline and Power Constraints ,” IEEE Transactions on Automatic Control, pp. 2841-2852, December, 2009.
53. Murtaza Zafer and Eytan Modiano, “A Calculus Approach to Energy-Efficient Data Transmission with Quality of Service Constraints,” IEEE/ACM Transactions on Networking, 2009.
52. Anand Srinivas, Gil Zussman, and Eytan Modiano, “Construction and Maintenance of Wireless Mobile Backbone Networks,” IEEE/ACM Transactions on Networking, 2009.
51. Andrew Brzezinski, Gil Zussman, and Eytan Modiano, “Distributed Throughput Maximization in Wireless Mesh Networks Via Pre-Partitioning,” IEEE/ACM Transactions on Networking, December, 2008.
50. Amir Khandani, Eytan Modiano, Jinane Abounadi, Lizhong Zheng, “Reliability and Route Diversity in Wireless Networks,” IEEE Transactions on Wireless Communications, December, 2008.
49. Alessandro Tarello, Jun Sun, Murtaza Zafer and Eytan Modiano, “Minimum Energy Transmission Scheduling Subject to Deadline Constraints,” ACM Wireless Networks, October, 2008.
48. Murtaza Zafer, Eytan Modiano, “Optimal Rate Control for Delay-Constrained Data Transmission over a Wireless Channel,” IEEE Transactions on Information Theory, September, 2008.
47. Andrew Brzezinski and Eytan Modiano, “Achieving 100% Throughput In Reconfigurable IP/WDM Networks,” IEEE/ACM Transactions on Networking, August, 2008.
46. Michael Neely, Eytan Modiano and C. Li, “Fairness and Optimal Stochastic Control for Heterogeneous Networks,” IEEE/ACM Transactions on Networking, September, 2008.
45. Amir Khandani, Jinane Abounadi, Eytan Modiano, Lizhong Zheng, “Cooperative Routing in Static Wireless Networks,” IEEE Transactions on Communications, November 2007.
44. Murtaza Zafer, Eytan Modiano, “Joint Scheduling of Rate-guaranteed and Best-effort Users over a Wireless Fading Channel,” IEEE Transactions on Wireless Communications, October, 2007.
43. Krishna Jagannathan, Sem Borst, Phil Whiting and Eytan Modiano, “Scheduling of Multi-Antenna Broadcast Systems with Heterogeneous Users,” IEEE Journal of Selected Areas in Communications, September, 2007.Amir Khandani, Jinane
42. Anand Ganti, Eytan Modiano, and John Tsitsiklis, “Optimal Transmission Scheduling in Symmetric Communication Models with Intermittent Connectivity, ” IEEE Transactions on Information Theory, March, 2007.
41. Michael Neely and Eytan Modiano, “Logarithmic Delay for NxN Packet Switches Under Crossbar Constraints,” IEEE/ACM Transactions on Networking, November, 2007.
40. Jun Sun, Jay Gao, Shervin Shambayati and Eytan Modiano, “Ka-Band Link Optimization with Rate Adaptation for Mars and Lunar Communications,” International Journal of Satellite Communications and Networks, March, 2007.
39. Jun Sun and Eytan Modiano, "Fair Allocation of A Wireless Fading Channel: An Auction Approach" Institute for Mathematics and its Applications, Volume 143: Wireless Communications, 2006.
38. Jun Sun, Eytan Modiano and Lizhong Zhang, “Wireless Channel Allocation Using An Auction Algorithm,” IEEE Journal on Selected Areas in Communications, May, 2006.
37. Murtaza Zafer and Eytan Modiano, "Blocking Probability and Channel Assignment for Connection Oriented Traffic in Wireless Networks," IEEE Transactions on Wireless Communications, April, 2006.
36. Alvin Fu, Eytan Modiano, and John Tsitsiklis, "Optimal Transmission Scheduling over a fading channel with Energy and Deadline Constraints" IEEE Transactions on Wireless Communications, March,2006.
35. Poompat Saengudomlert, Eytan Modiano and Rober Gallager, “On-line Routing and Wavelength Assignment for Dynamic Traffic in WDM Ring and Torus Networks,” IEEE Transactions on Networking, April, 2006.
34. Li-Wei Chen, Eytan Modiano and Poompat Saengudomlert, "Uniform vs. Non-Uniform band Switching in WDM Networks," Computer Networks (special issue on optical networks), January, 2006.
33. Andrew Brzezinski and Eytan Modiano, "Dynamic Reconfiguration and Routing Algorithms for IP-over-WDM networks with Stochastic Traffic," IEEE Journal of Lightwave Technology, November, 2005
32. Randall Berry and Eytan Modiano, "Optimal Transceiver Scheduling in WDM/TDM Networks," IEEE Journal on Selected Areas in Communications, August, 2005.
31. Poompat Saengudomlert, Eytan Modiano, and Robert G. Gallager, “Dynamic Wavelength Assignment for WDM All-Optical Tree Networks,” IEEE Transactions on Networking, August, 2005.
30. Ashwinder Ahluwalia and Eytan Modiano, "On the Complexity and Distributed Construction of Energy Efficient Broadcast Trees in Wireless Ad Hoc Networks," IEEE Transactions on Wireless Communications, October, 2005.
29. Michael Neely, Charlie Rohrs and Eytan Modiano, "Equivalent Models for Analysis of Deterministic Service Time Tree Networks," IEEE Transactions on Information Theory, October, 2005.
28. Michael Neely and Eytan Modiano, "Capacity and Delay Tradeoffs for Ad Hoc Mobile Networks," IEEE Transactions on Information Theory, May, 2005.
27. Li-Wei Chen and Eytan Modiano, "Efficient Routing and Wavelength Assignment for Reconfigurable WDM Networks with Wavelength Converters," IEEE/ACM Transactions on Networking, February, 2005. Selected as one of the best papers from Infocom 2003 for fast-track publication in IEEE/ACM Transactions on Networking.
26. Michael Neely and Eytan Modiano, "Convexity in Queues with General Inputs," IEEE Transactions on Information Theory, May, 2005.
25. Anand Srinivas and Eytan Modiano, "Finding Minimum Energy Disjoint Paths in Wireless Ad Hoc Networks," ACM Wireless Networks, November, 2005. Selected to appear in a special issue dedicated to best papers from Mobicom 2003.
24. Michael Neely, Eytan Modiano and Charlie Rohrs, "Dynamic Power Allocation and Routing for Time-Varying Wireless Networks," IEEE Journal of Selected Areas in Communication, January, 2005.
23. Chunmei Liu and Eytan Modiano, "On the performance of additive increase multiplicative decrease (AIMD) protocols in hybrid space-terrestrial networks," Computer Networks, September, 2004.
22. Li-Wei Chen and Eytan Modiano, "Dynamic Routing and Wavelength Assignment with Optical Bypass using Ring Embeddings," Optical Switching and Networking (Elsevier), December, 2004.
21. Aradhana Narula-Tam, Eytan Modiano and Andrew Brzezinski, "Physical Topology Design for Survivable Routing of Logical Rings in WDM-Based Networks," IEEE Journal of Selected Areas in Communication, October, 2004.
20. Randall Berry and Eytan Modiano, "'The Role of Switching in Reducing the Number of Electronic Ports in WDM Networks," IEEE Journal of Selected Areas in Communication, October, 2004.
19. Jun Sun and Eytan Modiano, "Routing Strategies for Maximizing Throughput in LEO Satellite Networks,," IEEE JSAC, February, 2004.
18. Jun Sun and Eytan Modiano, "Capacity Provisioning and Failure Recovery for Low Earth Orbit Satellite Networks," International Journal on Satellite Communications, June, 2003.
17. Alvin Fu, Eytan Modiano, and John Tsitsiklis, "Optimal Energy Allocation and Admission Control for Communications Satellites," IEEE Transactions on Networking, June, 2003.
16. Michael Neely, Eytan Modiano and Charles Rohrs, "Power Allocation and Routing in Multi-Beam Satellites with Time Varying Channels," IEEE Transactions on Networking, February, 2003.
15. Eytan Modiano and Aradhana Narula-Tam, "Survivable lightpath routing: a new approach to the design of WDM-based networks," IEEE Journal of Selected Areas in Communication, May 2002.
14. Aradhana Narula-Tam, Phil Lin and Eytan Modiano, "Efficient Routing and Wavelength Assignment for Reconfigurable WDM Networks," IEEE Journal of Selected Areas in Communication, January, 2002.
13. Brett Schein and Eytan Modiano, "Quantifying the benefits of configurability in circuit-switched WDM ring networks with limited ports per node," IEEE Journal on Lightwave Technology, June, 2001.
12. Aradhana Narula-Tam and Eytan Modiano, "Dynamic Load Balancing in WDM Packet Networks with and without Wavelength Constraints," IEEE Journal of Selected Areas in Communications, October 2000.
11. Randy Berry and Eytan Modiano, "Reducing Electronic Multiplexing Costs in SONET/WDM Rings with Dynamically Changing Traffic," IEEE Journal of Selected Areas in Communications, October 2000.
10. Eytan Modiano and Richard Barry, "A Novel Medium Access Control Protocol for WDM-Based LANs and Access Networks Using a Master-Slave Scheduler," IEEE Journal on Lightwave Technology, April 2000.
9. Eytan Modiano and Anthony Ephremides, "Communication Protocols for Secure Distributed Computation of Binary Functions," Information and Computation, April 2000.
8. Angela Chiu and Eytan Modiano, "Traffic Grooming Algorithms for Reducing Electronic Multiplexing Costs in WDM Ring Networks," IEEE Journal on Lightwave Technology, January 2000.
7. Eytan Modiano, "An Adaptive Algorithm for Optimizing the Packet Size Used in Wireless ARQ Protocols," Wireless Networks, August 1999.
6. Eytan Modiano, "Random Algorithms for Scheduling Multicast Traffic in WDM Broadcast-and-Select Networks," IEEE Transactions on Networking, July, 1999.
5. Eytan Modiano and Richard Barry, "Architectural Considerations in the Design of WDM-based Optical Access Networks," Computer Networks, February 1999.
4. V.W.S. Chan, K. Hall, E. Modiano and K. Rauschenbach, "Architectures and Technologies for High-Speed Optical Data Networks," IEEE Journal of Lightwave Technology, December 1998.
3. Eytan Modiano and Anthony Ephremides, "Efficient Algorithms for Performing Packet Broadcasts in a Mesh Network," IEEE Transactions on Networking, May 1996.
2. Eytan Modiano, Jeffrey Wieselthier and Anthony Ephremides, "A Simple Analysis of Queueing Delay in a Tree Network of Discrete-Time Queues with Constant Service Times," IEEE Transactions on Information Theory, February 1996.
1. Eytan Modiano and Anthony Ephremides, "Communication Complexity of Secure Distributed Computation in the Presence of Noise," IEEE Transactions on Information Theory, July 1992.
Other Papers
5. Eytan Modiano, "Satellite Data Networks," AIAA Journal on Aerospace Computing, Information and Communication, September, 2004.
4. Eytan Modiano and Phil Lin, "Traffic Grooming in WDM networks," IEEE Communications Magazine, July, 2001.
3. Eytan Modiano and Aradhana Narula, "Mechanisms for Providing Optical Bypass in WDM-based Networks," SPIE Optical Networks, January 2000.
2. K. Kuznetsov, N. M. Froberg, Eytan Modiano, et. al., "A Next Generation Optical Regional Access Networks," IEEE Communications Magazine, January, 2000.
1. Eytan Modiano, "WDM-based Packet Networks," (Invited Paper) IEEE Communications Magazine, March 1999.
Conference Papers
246. Xinyu Wu, Dan Wu, Eytan Modiano, “ Overload Balancing in Single-Hop Networks With Bounded Buffers ,” IFIP Networking, 2022.
245. Xinzhe Fu, Eytan Modiano, “ Optimal Routing for Stream Learning Systems ,” IEEE Infocom, April 2022.
244. Vishrant Tripathi, Luca Ballotta, Luca Carlone, E. Modiano, “ Computation and Communication Co-Design for Real-Time Monitoring and Control in Multi-Agent Systems ,” IEEE Wiopt, 2021.
243. Eray Atay, Igor Kadota, E. Modiano, “ Aging Wireless Bandits: Regret Analysis and Order-Optimal Learning Algorithm ,” IEEE Wiopt 2021.
242. Xinzhe Fu and E. Modiano, “ Elastic Job Scheduling with Unknown Utility Functions ,” IFIP Performance, Milan, 2021.
241. Bai Liu and E. Modiano, “ Optimal Control for Networks with Unobservable Malicious Nodes ,” IFIP Performance, Milan, 2021.
240. Bai Liu, Qiaomin Xie, Eytan Modiano, “ RL-QN: A Reinforcement Learning Framework for Optimal Control of Queueing Systems ,” ACM Sigmetrics Workshop on Reinforcement Learning in Networks and Queues (RLNQ), 2021.
239. Xinzhe Fu and E. Modiano, “ Learning-NUM: Network Utility Maximization with Unknown Utility Functions and Queueing Delay , ACM MobiHoc 2021.
238. Vishrant Tripathi and Eytan Modiano, “ An Online Learning Approach to Optimizing Time-Varying Costs of AoI ,” ACM MobiHoc 2021.
237. Igor Kadota, Muhammad Shahir Rahman, and Eytan Modiano, " WiFresh: Age-of-Information from Theory to Implementation ,” International Conference on Computer Communications and Networks (ICCCN), 2021.
236. Vishrant Tripathi and Eytan Modiano, “ Age Debt: A General Framework For Minimizing Age of Information ,” IEEE Infocom Workshop on Age-of-Information, 2021.
235. Igor Kadota, Eytan Modiano, “ Age of Information in Random Access Networks with Stochastic Arrivals ,” IEEE Infocom, 2020.
234. Igor Kadota, M. Shahir Rahman, Eytan Modiano, Poster: Age of Information in Wireless Networks: from Theory to Implementation , ACM Mobicom, 2020.
233. Xinyu Wu, Dan Wu, Eytan Modiano, “ An Influence Model Approach to Failure Cascade Prediction in Large Scale Power Systems ,” IEEE American Control Conference, July, 2020.
232. X. Fu and E. Modiano, " Fundamental Limits of Volume-based Network DoS Attacks ," Proc. ACM Sigmetrics, Boston, MA, June 2020.
231. Vishrant Tripathi, Eytan Modiano, “ A Whittle Index Approach to Minimizing Functions of Age of Information ,” Allerton Conference on Communication, Control, and Computing, September 2019.
230. Bai Liu, Xiaomin Xie, Eytan Modiano, “ Reinforcement Learning for Optimal Control of Queueing Systems ,” Allerton Conference on Communication, Control, and Computing, September 2019.
229. Rajat Talak, Sertac Karaman, Eytan Modiano, “ A Theory of Uncertainty Variables for State Estimation and Inference ,” Allerton Conference on Communication, Control, and Computing, September 2019.
228. Rajat Talak, Eytan Modiano, “ Age-Delay Tradeoffs in Single Server Systems ,” IEEE International Symposium on Information Theory, Paris, France, July, 2019.
227. Rajat Talak, Sertac Karaman, Eytan Modiano, “ When a Heavy Tailed Service Minimizes Age of Information ,” IEEE International Symposium on Information Theory, Paris, France, July, 2019.
226. Qingkai Liang, Eytan Modiano, “ Optimal Network Control with Adversarial Uncontrollable Nodes ,” ACM MobiHoc, Catania, Italy, June 2019.
225. Igor Kadota, Eytan Modiano, “ Minimizing the Age of Information in Wireless Networks with Stochastic Arrivals ,” ACM MobiHoc, June 2019.
224. Maotong Xu, Jelena Diakonikolas, Suresh Subramaniam, Eytan Modiano, “ A Hierarchical WDM-based Scalable Data Center Network Architecture ,” IEEE International Conference on Communications (ICC), Shanghai, China, June 2019.
223. Maotong Xu, Min Tian, Eytan Modiano, Suresh Subramaniam, " RHODA Topology Configuration Using Bayesian Optimization
222. Anurag Rai, Rahul Singh and Eytan Modiano, " A Distributed Algorithm for Throughput Optimal Routing in Overlay Networks ,” IFIP Networking 2019, Warsaw, Poland, May 2019.
221. Qingkai Liang and Eytan Modiano, " Optimal Network Control in Partially-Controllable Networks ,” IEEE Infocom, Paris, April 2019.
220. Xinzhe Fu and Eytan Modiano, " Network Interdiction Using Adversarial Traffic Flows ,” IEEE Infocom, Paris, April 2019.
219. Vishrant Tripathi, Rajat Talak, Eytan Modiano, " Age Optimal Information Gathering and Dissemination on Graphs ,” IEEE Infocom, Paris, April 2019.
218. Jianan Zhang, Hyang-Won Lee, Eytan Modiano, " On the Robustness of Distributed Computing Networks ,” DRCN 2019, Coimbra, Portugal, March, 2019.
217. Hyang-Won Lee, Jianan Zhang and Eytan Modiano, " Data-driven Localization and Estimation of Disturbance in the Interconnected Power System ,” IEEE Smartgridcomm, October, 2018.
216. Jianan Zhang and Eytan Modiano, " Joint Frequency Regulation and Economic Dispatch Using Limited Communication ,” IEEE Smartgridcomm, October, 2018.
215. Rajat Talak, Sertac Karaman, Eytan Modiano, " Scheduling Policies for Age Minimization in Wireless Networks with Unknown Channel State ,” IEEE International Symposium on Information Theory, July 2018.
214. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, " Online Learning Algorithms for Minimizing Queue Length Regret ,” IEEE International Symposium on Information Theory, July 2018.
213. Rajat Talak, Sertac Karaman, Eytan Modiano, " Distributed Scheduling Algorithms for Optimizing Information Freshness in Wireless Networks ,” IEEE SPAWC, Kalamata, Greece, June, 2018.
212. Rajat Talak, Sertac Karaman, Eytan Modiano, " Optimizing Information Freshness in Wireless Networks under General Interference Constraints ,” ACM MobiHoc 2018, Los Angeles, CA, June 2018.
211. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, " Learning Algorithms for Scheduling in Wireless Networks with Unknown Channel Statistics ,” ACM MobiHoc, June 2018.
210. Khashayar Kamran, Jianan Zhang, Edmund Yeh, Eytan Modiano, " Robustness of Interdependent Geometric Networks Under Inhomogeneous Failures ,” Workshop on Spatial Stochastic Models for Wireless Networks (SpaSWiN), Shanghai, China, May 2018.
209. Rajat Talak, Sertac Karaman, Eytan Modiano, " Optimizing Age of Information in Wireless Networks with Perfect Channel State Information ,” Wiopt 2018, Shanghai, China, May 2018.
208. Abhishek Sinha, Eytan Modiano, " Network Utility Maximization with Heterogeneous Traffic Flows ,” Wiopt 2018, Shanghai, China, May 2018.
207. Qingkai Liang, Eytan Modiano, " Minimizing Queue Length Regret Under Adversarial Network Models ,” ACM Sigmetrics, 2018.
206. Jianan Zhang, Abhishek Sinha, Jaime Llorca, Anonia Tulino, Eytan Modiano, " Optimal Control of Distributed Computing Networks with Mixed-Cast Traffic Flows ,” IEEE Infocom, Honolulu, HI, April 2018.
205. Qingkai Liang, Eytan Modiano, " Network Utility Maximization in Adversarial Environments ,” IEEE Infocom, Honolulu, HI, April 2018.
204. Igor Kadota, Abhishek Sinha, Eytan Modiano, " Optimizing Age of Information in Wireless Networks with Throughput Constraints ,” IEEE Infocom, Honolulu, HI, April 2018.
203. QIngkai Liang, Verina (Fanyu) Que, Eytan Modiano, " Accelerated Primal-Dual Policy Optimization for Safe Reinforcement Learning ,” NIPS workshop on “Transparent and interpretable machine learning in safety critical environments,"December 2017.
202. Rahul Singh, Xueying Guo,Eytan Modiano, " Risk-Sensitive Optimal Control of Queues ,” IEEE Conference on Decision and Control (CDC), December 2017.
201. Rajat Talak, Sertac Karaman, Eytan Modiano, " Minimizing Age of Information in Multi-Hop Wireless Networks ,” Allerton Conference on Communication, Control, and Computing, September 2017.
200. Abhishek Sinha, Eytan Modiano, " Throughput-Optimal Broadcast in Wireless Networks with Point-to-Multipoint Transmissions ,” ACM MobiHoc, Madras, India, July 2017.
199. Rajat Talak, Sertac Karaman, Eytan Modiano, " Capacity and delay scaling for broadcast transmission in highly mobile wireless networks ,” ACM MobiHoc, Madras, India, July 2017.
198.5 . Y.-P. Hsu, E. Modiano, and L. Duan, " Age of Information: Design and Analysis of Optimal Scheduling Algorithms ,” IEEE International Symposium on Information Theory (ISIT), 2017.
198. Qingkai Liang and Eytan Modiano, " Coflow Scheduling in Input-Queued Switches: Optimal Delay Scaling and Algorithms ,” IEEE Infocom, Atlanta, GA, May 2017.
197. Jianan Zhang and Eytan Modiano, " Robust Routing in Interdependent Networks ,” IEEE Infocom, Atlanta, GA, May 2017.
196. Abhishek Sinha, Eytan Modiano, " Optimal Control for Generalized Network Flow Problems ,” IEEE Infocom, Atlanta, GA, May 2017.
195. Rajat Talak*, Sertac Karaman, Eytan Modiano, " Speed Limits in Autonomous Vehicular Networks due to Communication Constraints ,” IEEE Conference on Decision and Control (CDC), Las Vegas, NV, December 2016.
194. Marzieh Parandehgheibi*, Konstantin Turitsyn, Eytan Modiano, " Distributed Frequency Control in Power Grids Under Limited Communication ,” IEEE Conference on Decision and Control (CDC), Las Vegas, NV, December 2016.
193. Igor Kadota, Elif Uysal-Biyikoglu, Rahul Singh, Eytan Modiano, " Minimizing Age of Information in Broadcast Wireless Networks ,” Allerton Allerton Conference on Communication, Control, and Computing, September 2016.
192. Jianan Zhang, Edmund Yeh, Eytan Modiano, " Robustness of Interdependent Random Geometric Networks ,” Allerton Conference on Communication, Control, and Computing, September 2016.
191. Abhishek Sinha, Leandros Tassiulas, Eytan Modiano, " Throughput-Optimal Broadcast in Wireless Networks with Dynamic Topology ,” ACM MobiHoc'16, Paderborn, Germany, July, 2016. (winner of best paper award)
190. Abishek Sinha, Georgios Paschos, Eytan Modiano, " Throughput-Optimal Multi-hop Broadcast Algorithms ,” ACM MobiHoc'16, Paderborn, Germany, July, 2016.
189. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, " Throughput Maximization in Uncooperative Spectrum Sharing Networks ,” IEEE International Symposium on Information Theory, Barcelona, Spain, July 2016.
188. Thomas Stahlbuhk, Brooke Shrader, Eytan Modiano, " Topology Control for Wireless Networks with Highly-Directional Antennas ,” IEEE Wiopt, Tempe, Arizona, May, 2016.
187. Qingkai Liang, H.W. Lee, Eytan Modiano, " Robust Design of Spectrum-Sharing Networks ,” IEEE Wiopt, Tempe, Arizona, May, 2016.
186. Hossein Shokri-Ghadikolae, Carlo Fischione and Eytan Modiano, " On the Accuracy of Interference Models in Wireless Communications ,” IEEE International Conference on Communications (ICC), 2016.
185. Qingkai Liang and Eytan Modiano, " Survivability in Time-varying Networks ,” IEEE Infocom, San Francisco, CA, April 2016.
184. Kyu S. Kim, Chih-Ping Li, Igor Kadota, Eytan Modiano, " Optimal Scheduling of Real-Time Traffic in Wireless Networks with Delayed Feedback ,” Allerton conference on Communication, Control, and Computing, September 2015.
183. Marzieh Parandehgheibi, Eytan Modiano, " Modeling the Impact of Communication Loss on the Power Grid Under Emergency Control ,” IEEE SmartGridComm, Miami, FL, Nov. 2015.
182. Anurag Rai, Chih-ping Li, Georgios Paschos, Eytan Modiano, " Loop-Free Backpressure Routing Using Link-Reversal Algorithms ,” Proceedings of the ACM MobiHoc, July 2015.
181. Longbo Huang, Eytan Modiano, " Optimizing Age of Information in a Multiclass Queueing System ,” Proceedings of IEEE ISIT 2015, Hong Kong, Jun 2015.
180. M. Johnston, E. Modiano, " A New Look at Wireless Scheduling with Delayed Information ,” Proceedings of IEEE ISIT 2015, Hong Kong, June 2015.
179. M. Johnston, E. Modiano, " Scheduling over Time Varying Channels with Hidden State Information ,” Proceedings of IEEE ISIT 2015, Hong Kong, June 2015.
178. M. Johnston and E. Modiano, " Controller Placement for Maximum Throughput Under Delayed CSI ,” IEEE Wiopt, Mombai, India, May 2015.
177. A. Sinha, G. Paschos, C. P. Li, and E. Modiano, " Throughput Optimal Broadcast on Directed Acyclic Graphs ,” IEEE Infocom, Hong Kong, April 2015.
176. J. Zheng and E. Modiano, " Enhancing Network Robustness via Shielding ,” IEEE Design of Reliable Communication Networks, Kansas City, March 2015.
175. H. W. Lee and E. Modiano, " Robust Design of Cognitive Radio Networks ,” Information and Communication Technology Convergence (ICTC), 2014.
174. Greg Kuperman and Eytan Modiano, " Disjoint Path Protection in Multi-Hop Wireless Networks with Interference Constraints ,” IEEE Globecom, Austin, TX, December 2014.
173. Marzieh Parandehgheibi, Eytan Modiano, David Hay, " Mitigating Cascading Failures in Interdependent Power Grids and Communication Networks ,” IEEE Smartgridcomm, Venice, Italy, November 2014.
172. Georgios Paschos and Eytan Modiano, " Throughput optimal routing in overlay networks ,” Allerton conference on Communication, Control, and Computing, September 2014.
171. Nathan Jones, George Paschos, Brooke Shrader, Eytan Modiano, " An overlay architecture for Throughput Optimal Multipath Routing ,” ACM MobiHoc, August 2014.
170. Matt Johnston, Eytan Modiano, Yuri Polyanskiy, " Opportunistic Scheduling with Limited Channel State Information: A Rate Distortion Approach ,” IEEE International Symposium on Information Theory, Honolulu, HI, July 2014.
169. Chih-Ping Li, Georgios Paschos, Eytan Modiano, Leandros Tassiulas, " Dynamic Overload Balancing in Server Farms ,” Networking 2014, Trondheim, Norway, June, 2014.
168. Hulya Seferonglu and Eytan Modiano, " TCP-Aware Backpressure Routing and Scheduling ,” Information Theory and Applications, San Diego, CA, February 2014.
167. Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Delay Stability of Back-Pressure Policies in the presence of Heavy-Tailed Traffic ,” Information Theory and Applications, San Diego, CA, February 2014.
166. Kyu Soeb Kim, Chih-ping Li, Eytan Modiano, " Scheduling Multicast Traffic with Deadlines in Wireless Networks ,” IEEE Infocom, Toronto, CA, April 2014.
165. Georgios Paschos, Chih-ping Li, Eytan Modiano, Kostas Choumas, Thanasis Korakis, " A Demonstration of Multirate Multicast Over an 802.11 Mesh Network ,” IEEE Infocom, Toronto, CA, April 2014.
164. Sebastian Neumayer, Eytan Modiano, " Assessing the Effect of Geographically Correlated Failures on Interconnected Power-Communication Networks ,” IEEE SmartGridComm, 2013.
163. Marzieh Parandehgheibi, Eytan Modiano, " Robustness of Interdependent Networks: The case of communication networks and the power grid ,” IEEE Globecom, December 2013.
162. Matt Johnston, Eytan Modiano, " Optimal Channel Probing in Communication Systems: The Two-Channel Case ,” IEEE Globecom, December 2013.
161. Mihalis Markakis, Eytan Modiano, John N. Tsitsiklis, " Delay Analysis of the Max-Weight Policy under Heavy-Tailed Traffic via Fluid Approximations ,” Allerton Conference, October 2013.
160. Matthew Johnston, Isaac Keslassy, Eytan Modiano, " Channel Probing in Communication Systems: Myopic Policies Are Not Always Optimal ,” IEEE International Symposium on Information Theory, July 2013.
159. Krishna P Jagannathan, Libin Jiang, Palthya Lakshma Naik, Eytan Modiano, " Scheduling Strategies to Mitigate the Impact of Bursty Traffic in Wireless Networks ,” 11th International Symposium on Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks Wiopt 2013, Japan, May 2013. (Winner – Best Paper Award).
158. Hulya Seferoglu and Eytan Modiano, " Diff-Max: Separation of Routing and Scheduling in Backpressure-Based Wireless Networks ,” IEEE Infocom, Turin, Italy, April 2013.
157. Chih-Ping Li, Eytan Modiano, " Receiver-Based Flow Control for Networks in Overload ,” IEEE Infocom, Turin, Italy, April 2013.
156. Nathan Jones, Brooke Shrader, Eytan Modiano, " Distributed CSMA with Pairwise Coding ,” IEEE Infocom, Turin, Italy, April 2013.
155. Greg Kuperman and Eytan Modiano, " Network Protection with Guaranteed Recovery Times using Recovery Domains ,” IEEE Infocom, Turin, Italy, April 2013.
154. Greg Kuperman and Eytan Modiano, " Providing Protection in Multi-Hop Wireless Networks ,” IEEE Infocom, Turin, Italy, April 2013.
153. Greg Kuperman, Eytan Modiano, Aradhana Narula-Tam, " Network Protection with Multiple Availability Guarantees ,” IEEE ICC workshop on New Trends in Optical Networks Survivability, June 2012.
152. Nathaniel Jones, Brooke Shrader, Eytan Modiano, " Optimal Routing and Scheduling for a Simple Network Coding Scheme ,” IEEE Infocom, Orlando, Fl, March, 2012.
151. Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Max-Weight Scheduling in Networks with Heavy-Tailed Traffic ,” IEEE Infocom, Orlando, Fl, March, 2012.
150. Guner Celik and Eytan Modiano, " Scheduling in Networks with Time-Varying Channels and Reconfiguration Delay ,” IEEE Infocom, Orlando, Fl, March, 2012.
149. Sebastian Neumayer, Alon Efrat, Eytan Modiano, " Geographic Max-Flow and Min-cut Under a Circular Disk Failure Model ,” IEEE Infocom (MC), Orlando, Fl, March, 2012.
148. Marzieh Parandehgheibi, Hyang-Won Lee, and Eytan Modiano, " Survivable Paths in Multi-Layer Networks ,” Conference on Information Science and Systems, March, 2012.
147. Greg Kuperman, Eytan Modiano, and Aradhana Narula-Tam, " Partial Protection in Networks with Backup Capacity Sharing ,” Optical Fiber Communications Conference (OFC), Anaheim, CA, March, 2012.
146. Krishna Jagannathan, Libin Jiang, Eytan Modiano, " On Scheduling Algorithms Robust to Heavy-Tailed Traffic ,” Information Theory and Applications (ITA), San Diego, CA, February 2012.
145. M. Johnston, H.W. Lee, E. Modiano, " Robust Network Design for Stochastic Traffic Demands ,” IEEE Globecom, Next Generation Networking Symposium, Houston, TX, December 2011.
144. S. Neumayer, E. Modiano, " Network Reliability Under Random Circular Cuts ,” IEEE Globecom, Optical Networks and Systems Symposium, Houston, TX, December 2011.
143. H.W. Lee, K. Lee, E. Modiano, " Maximizing Reliability in WDM Networks through Lightpath Routing ,” IEEE Globecom, Optical Networks and Systems Symposium, Houston, TX, December 2011.
142. Guner Celik, Sem Borst, Eytan Modiano, Phil Whiting, " Variable Frame Based Max-Weight Algorithms for Networks with Switchover Delay ,” IEEE International Symposium on Information Theory, St. Petersburgh, Russia, August 2011.
141. Krishna Jaganathan, Ishai Menache, Eytan Modiano, and Gil Zussman, " Non-cooperative Spectrum Access - The Dedicated vs. Free Spectrum Choice ,” ACM MOBIHOC'11, May 2011.
140. Krishna Jagannathan, Shie Mannor, Ishai Menache, Eytan Modiano, " A State Action Frequency Approach to Throughput Maximization over Uncertain Wireless Channels ,” IEEE Infocom (Mini-conference), Shanghai, China, April 2011.
139. Guner Celik, Long B. Le, Eytan Modiano, " Scheduling in Parallel Queues with Randomly Varying Connectivity and Switchover Delay ,” IEEE Infocom (Mini-conference), Shanghai, China, April 2011.
138. Gregory Kuperman, Eytan Modiano, Aradhana Narula-Tam, " Analysis and Algorithms for Partial Protection in Mesh Networks ,” IEEE Infocom (Mini-conference), Shanghai, China, April 2011.
137. Matthew Johnston, Hyang-Won Lee, Eytan Modiano, " A Robust Optimization Approach to Backup Network Design with Random Failures ,” IEEE Infocom, Shanghai, China, April 2011.
136. Krishna Jagannathan, Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Queue Length Asymptotics for Generalized Max-Weight Scheduling in the presence of Heavy-Tailed Traffic ,” IEEE Infocom, Shanghai, China, April 2011.
135. Guner Celik and Eytan Modiano, " Dynamic Vehicle Routing for Data Gathering in Wireless Networks ,” In Proc. IEEE CDC'10, Dec. 2010..***
134. Long B. Le, Eytan Modiano, Changhee Joo, and Ness B. Shroff, " Longest-queue-first scheduling under the SINR interference model ,” ACM MobiHoc, September 2010..***
133. Krishna Jagannathan, Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Throughput Optimal Scheduling in the Presence of Heavy-Tailed Traffic ,” Allerton Conference on Communication, Control, and Computing, September 2010..**
132. Delia Ciullo, Guner Celik, Eytan Modiano, " Minimizing Transmission Energy in Sensor Networks via Trajectory Control ,” IEEE Wiopt 2010, Avignon, France, June 2010, (10 pages; CD proceedings – page numbers not available).
131. Sebastian Neumayer and Eytan Modiano, " Network Reliability with Geographically Correlated Failures ,” IEEE Infocom 2010, San Diego, CA, March 2010, (9 pages; CD proceedings – page numbers not available).**
130. Long Le, Eytan Modiano, Ness Shroff, " Optimal Control of Wireless Networks with Finite Buffers ,” IEEE Infocom 2010, San Diego, CA, March 2010, (9 pages; CD proceedings – page numbers not available).
129. Kayi Lee, Hyang-Won Lee, Eytan Modiano, " Reliability in Layered Network with Random Link Failures ,” IEEE Infocom 2010, San Diego, CA, March 2010, (9 pages; CD proceedings – page numbers not available).**
128. Krishna Jagannathan, Eytan Modiano, " The Impact of Queue length Information on Buffer Overflow in Parallel Queues ,” Allerton Conference on Communication, Control, and Computing, September 2009, pgs. 1103 -1110 **
127. Mihalis Markakis, Eytan Modiano, John Tsitsiklis, " Scheduling Policies for Single-Hop with Heavy-Tailed Traffic ,” Allerton Conference on Communication, Control, and Computing, September 2009, pgs. 112 – 120..**
126. Dan Kan, Aradhana Narula-Tam, Eytan Modiano, " Lightpath Routing and Capacity Assignment for Survivable IP-over-WDM Networks ,” DRCN 2009, Alexandria, VA October 2009, pgs. 37 -44..**
125. Mehdi Ansari, Alireza Bayesteh, Eytan Modiano, " Opportunistic Scheduling in Large Scale Wireless Networks ,” IEEE International Symposium on Information Theory, Seoul, Korea, June 2009, pgs. 1624 – 1628.
124. Hyang-Won Lee, Eytan Modiano and Long Bao Le, " Distributed Throughput Maximization in Wireless Networks via Random Power Allocation ,” IEEE Wiopt, Seoul, Korea, June 2009. (9 pages; CD proceedings – page numbers not available).
123. Wajahat Khan, Eytan Modiano, Long Le, " Autonomous Routing Algorithms for Networks with Wide-Spread Failures ,” IEEE MILCOM, Boston, MA, October 2009. (6 pages; CD proceedings – page numbers not available).**
122. Guner Celik and Eytan Modiano, " Random Access Wireless Networks with Controlled Mobility ,” IEEE Med-Hoc-Nets, Haifa, Israel, June 2009, pgs. 8 – 14.**
121. Hyang-Won Lee and Eytan Modiano, " Diverse Routing in Networks with Probabilistic Failures ,” IEEE Infocom, April 2009, pgs. 1035 – 1043.
120. Kayi Lee and Eytan Modiano, " Cross-layer Survivability in WDM-based Networks ,” IEEE Infocom, April 2009, pgs. 1017 -1025..**
119. Krishna Jagannathan, Eytan Modiano, Lizhong Zheng, " On the Trade-off between Control Rate and Congestion in Single Server Systems ,” IEEE Infocom, April 2009, pgs. 271 – 279.**
118. Sebastian Neumayer, Gil Zussman, Rueven Cohen, Eytan Modiano, " Assessing the Vulnerability of the Fiber Infrastructure to Disasters ,” IEEE Infocom, April 2009, pgs. 1566 – 1574.**
117. Long Le, Krishna Jagannathan and Eytan Modiano, " Delay analysis of max-weight scheduling in wireless ad hoc networks ,” Conference on Information Science and Systems, Baltimore, MD, March, 2009, pgs. 389 – 394.**
116. Krishna Jagannathan, Eytan Modiano, Lizhong Zheng, " Effective Resource Allocation in a Queue: How Much Control is Necessary? ,” Allerton Conference on Communication, Control, and Computing, September 2008, pgs. 508 – 515.**
115. Sebastian Neumayer, Gil Zussman, Rueven Cohen, Eytan Modiano, " Assessing the Impact of Geographically Correlated Network Failures ,” IEEE MILCOM, November 2008. (6 pages; CD proceedings – page numbers not available).**
114. Emily Craparo, Jonathan P. How, and Eytan Modiano, " Simultaneous Placement and Assignment for Exploration in Mobile Backbone Networks ,” IEEE conference on Decision and Control (CDC), November 2008, pgs. 1696 – 1701 **
113. Anand Srinivas and Eytan Modiano, " Joint node placement and assignment for throughput optimization in mobile backbone networks ,” IEEE INFOCOM'08, pp. 1130 – 1138, Phoenix, AZ, Apr. 2008, pgs. 1130 – 1138.**
112. Guner Celik, Gil Zussman, Wajahat Khan and Eytan Modiano, " MAC for Networks with Multipacket Reception Capability and Spatially Distributed Nodes ,” IEEE INFOCOM'08, Phoenix, AZ, Apr. 2008, pgs. 1436 – 1444.**
111. Gil Zussman, Andrew Brzezinski, and Eytan Modiano, " Multihop Local Pooling for Distributed Throughput Maximization in Wireless Networks ,” IEEE INFOCOM'08, Phoenix, AZ, Apr. 2008, pgs 1139 – 1147.**
110. Emily Craparo, Jonathan How and Eytan Modiano, " Optimization of Mobile Backbone Networks: Improved Algorithms and Approximation ,” IEEE American Control Conference, Seattle, WA, June 2008, pgs. 2016 – 2021.**
109. Atilla Eryilmaz, Asuman Ozdaglar, Devavrat Shah, Eytan Modiano, " Imperfect Randomized Algorithms for the Optimal Control of Wireless Networks ,” Conference on Information Science and Systems, Princeton, NJ, March, 2008, pgs. 932 – 937.
108. Anand Srinivas and Eytan Modiano, " Optimal Path Planning for Mobile Backbone Networks ,” Conference on Information Science and Systems, Princeton, NJ, March, 2008, pgs. 913 – 918.
107. Kayi Lee and Eytan Modiano, " Cross-layer Survivability in WDM Networks with Multiple Failures ,” IEEE Optical Fiber Communications Conference, San Diego, CA February, 2008 (3 pages; CD proceedings – page numbers not available).
106. Andrew Brzezinski, Gil Zussman and Eytan Modiano, " Local Pooling Conditions for Joint Routing and Scheduling ,” Workshop on Information Theory and Applications, pp. 499 – 506, La Jolla, CA, January, 2008, pgs. 499 – 506.
105. Murtaza Zafer and Eytan Modiano, " Minimum Energy Transmission over a Wireless Fading Channel with Packet Deadlines ,” Proceedings of IEEE Conference on Decision and Control (CDC), New Orleans, LA, December, 2007, pgs. 1148 – 1155.**
104. Atilla Eryilmaz, Asuman Ozdaglar, Eytan Modiano, " Polynomial Complexity Algorithms for Full Utilization of Multi-hop Wireless Networks ,” IEEE Infocom, Anchorage, AK, April, 2007, pgs. 499 – 507.
103. Murtaza Zafer and Eytan Modiano, " Delay Constrained Energy Efficient Data Transmission over a Wireless Fading Channel ,” Workshop on Information Theory and Application, University of California, San Diego, CA, February, 2007, pgs. 289 – 298.**
102. Atilla Eryilmaz, Eytan Modiano, Asuman Ozdaglar, " Randomized Algorithms for Throughput-Optimality and Fairness in Wireless Networks ,” Proceedings of IEEE Conference on Decision and Control (CDC), San Diego, CA, December, 2006, pgs. 1936 – 1941.
101. Anand Srinivas, Gil Zussman, and Eytan Modiano, " Distributed Mobile Disk Cover - A Building Block for Mobile Backbone Networks ,” Proc. Allerton Conf. on Communication, Control, and Computing, Allerton, IL, September 2006, (9 pages; CD proceedings – page numbers not available).**
100. Krishna Jagannathan, Sem Borst, Phil Whiting, Eytan Modiano, " Scheduling of Multi-Antenna Broadcast Systems with Heterogeneous Users ,” Allerton Conference on Communication, Control and Computing, Allerton, IL, September 2006, (10 pages; CD proceedings – page numbers not available).**
99. Andrew Brzezinski, Gil Zussman, and Eytan Modiano, " Enabling Distributed Throughput Maximization in Wireless Mesh Networks - A Partitioning Approach ,” Proceedings of ACM MOBICOM'06, Los Angeles, CA, Sep. 2006, (12 pages; CD proceedings – page numbers not available).**
98. Eytan Modiano, Devavrat Shah, and Gil Zussman, " Maximizing Throughput in Wireless Networks via Gossiping ,” Proc. ACM SIGMETRICS / IFIP Performance'06, Saint-Malo, France, June 2006, (12 pages; CD proceedings – page numbers not available). (best paper award)
97. Anand Srinivas, Gil Zussman, and Eytan Modiano, " Mobile Backbone Networks – Construction and Maintenance ,” Proc. ACM MOBIHOC'06, Florence, Italy, May 2006, (12 pages; CD proceedings – page numbers not available).**
96. Andrew Brzezinski and Eytan Modiano, " Achieving 100% throughput in reconfigurable optical networks ,” IEEE INFOCOM 2006 High-Speed Networking Workshop, Barcelona, Spain, April 2006, (5 pages; CD proceedings – page numbers not available).**
95. Krishna P. Jagannathan, Sem Borst, Phil Whiting, Eytan Modiano, " Efficient scheduling of multi-user multi-antenna systems ,” Proceedings of WiOpt 2006, Boston, MA, April 2006, (8 pages; CD proceedings – page numbers not available).**
94. Andrew Brzezinski and Eytan Modiano, " Greedy weighted matching for scheduling the input-queued switch ,” Conference on Information Sciences and Systems (CISS), Princeton, NJ, March 2006, pgs. 1738 – 1743.**
93. Murtaza Zafer and Eytan Modiano, " Optimal Adaptive Data Transmission over a Fading Channel with Deadline and Power Constraints ,” Conference on Information Sciences and Systems (CISS), Princeton, New Jersey, March 2006, pgs. 931 – 937.**
92. Li-Wei Chen and E. Modiano, " A Geometric Approach to Capacity Provisioning in WDM Networks with Dynamic Traffic ,” Conference on Information Science and Systems (CISS), Princeton, NJ, March, 2006, pgs. 1676 – 1683, **
91. Jun Sun and Eytan Modiano, " Channel Allocation Using Pricing in Satellite Networks ,” Conference on Information Science and Systems (CISS), Princeton, NJ, March, 2006, pgs. 182 – 187.**
90. Jun Sun, Jay Gao, Shervin Shambayatti and Eytan Modiano, " Ka-Band Link Optimization with Rate Adaptation ,” IEEE Aerospace Conference, Big Sky, MN, March, 2006. (7 pages; CD proceedings – page numbers not available).
89. Alessandro Tarello, Eytan Modiano and Jay Gao, " Energy efficient transmission scheduling over Mars proximity links ,” IEEE Aerospace Conference, Big Sky, MN, March, 2006. (10 pages; CD proceedings – page numbers not available).
88. A. Brzezinski and E. Modiano, " RWA decompositions for optimal throughput in reconfigurable optical networks ,” INFORMS Telecommunications Conference, Dallas, TX, March 2006 (3 pages; CD proceedings – page numbers not available).**
87. Li Wei Chen and E. Modiano, " Geometric Capacity Provisioning for Wavelength Switched WDM Networks ,” Workshop on Information Theory and Application, University of California, San Diego, CA, February, 2006. (8 pages; CD proceedings – page numbers not available).**
86. Murtaza Zafer and Eytan Modiano, " Joint Scheduling of Rate-guaranteed and Best-effort Services over a Wireless Channel ,” IEEE Conference on Decision and Control, Seville, Spain, December, 2005, pgs. 6022–6027.**
85. Jun Sun and Eytan Modiano, " Opportunistic Power Allocation for Fading Channels with Non-cooperative Users and Random Access ,” IEEE BroadNets – Wireless Networking Symposium, Boston, MA, October, 2005, pgs. 397–405.**
84. Li Wei Chen and Eytan Modiano, " Uniform vs. Non-uniform Band Switching in WDM Networks ,” IEEE BroadNets-Optical Networking Symposium, Boston, MA, October, 2005, pgs. 219– 228.**
83. Sonia Jain and Eytan Modiano, " Buffer Management Schemes for Enhanced TCP Performance over Satellite Links ,” IEEE MILCOM, Atlantic City, NJ, October 2005 (8 pages; CD proceedings – page numbers not available).**
82. Murtaza Zafer and Eytan Modiano, " Continuous-time Optimal Rate Control for Delay Constrained Data Transmission ,” Allerton Conference on Communications, Control and Computing, Allerton, IL, September, 2005 (10 pages; CD proceedings – page numbers not available).**
81. Alessandro Tarello, Eytan Modiano, Jun Sun, Murtaza Zafer, " Minimum Energy Transmission Scheduling subject to Deadline Constraints ,” IEEE Wiopt, Trentino, Italy, April, 2005, pgs. 67–76. (Winner of best student paper award).**
80. Amir Khandani, Eytan Modiano, Jinane Abounadi, Lizhong Zheng, " Reliability and Route Diversity in Wireless Networks ,” Conference on Information Science and System, Baltimore, MD, March, 2005, (8 pages; CD proceedings – page numbers not available).**
79. Andrew Brzezinski, Iraj Saniee, Indra Widjaja, Eytan Modiano, " Flow Control and Congestion Management for Distributed Scheduling of Burst Transmissions in Time-Domain Wavelength Interleaved Networks ,” IEEE/OSA Optical Fiber Conference (OFC), Anaheim, CA, March, 2005, pgs. WC4-1–WC4-3.
78. Andrew Brzezinski and Eytan Modiano, " Dynamic Reconfiguration and Routing Algorithms for IP-over-WDM Networks with Stochastic Traffic ,” IEEE Infocom 2005, Miami, FL, March, 2005, pgs. 6–11.**
77. Murtaza Zafer and Eytan Modiano, " A Calculus Approach to Minimum Energy Transmission Policies with Quality of Service Guarantees ,” IEEE Infocom 2005, Miami, FL, March, 2005, pgs. 548–559.**
76. Michael Neely and Eytan Modiano, " Fairness and optimal stochastic control for heterogeneous networks ,” IEEE Infocom 2005, Miami, FL, March, 2005, pgs. 1723 – 1734.**
75. Aradhana Narula-Tam, Thomas G. Macdonald, Eytan Modiano, and Leslie Servi, " A Dynamic Resource Allocation Strategy for Satellite Communications ,” IEEE MILCOM, Monterey, CA, October, 2004, pgs. 1415 – 1421.
74. Li-Wei Chen, Poompat Saengudomlert and Eytan Modiano, " Optimal Waveband Switching in WDM Networks ,” IEEE International Conference on Communication (ICC), Paris, France, June, 2004, pgs. 1604 – 1608.**
73. Michael Neely and Eytan Modiano, " Logarithmic Delay for NxN Packet Switches ,” IEEE Workshop on High performance Switching and Routing (HPSR 2004), Phoenix, AZ, April, 2004, pgs. 3–9.**
72. Li-Wei Chen and Eytan Modiano, " Dynamic Routing and Wavelength Assignment with Optical Bypass using Ring Embeddings ,” IEEE Workshop on High performance Switching and Routing (HPSR 2004), Phoenix, Az, April, 2004, pgs. 119–125.**
71. Randall Berry and Eytan Modiano, " On the Benefits of Tunability in Reducing Electronic Port Counts in WDM/TDM Networks ,” IEEE Infocom, Hong Kong, March 2004, pgs. 1340–1351.
70. Andrew Brzezinski and Eytan Modiano, " A new look at dynamic traffic scheduling in WDM networks with transceiver tuning latency ,” Informs Telecommunications Conference, Boca Raton, FL, March 2004, pgs. 25–26.**
69. Chunmei Liu and Eytan Modiano, " Packet Scheduling with Window Service Constraints ,” Conference on Information Science and System, Princeton, NJ, March, 2004, pgs. 178–184.**
68. Jun Sun, Eytan Modiano, and Lizhong Zheng, " A Novel Auction Algorithm for Fair Allocation of a Wireless Fading Channel ,” Conference on Information Science and System, Princeton, NJ, March, 2004, pgs. 1377–1383.**
67. Murtaza Zafer and Eytan Modiano, " Impact of Interference and Channel Assignment on Blocking Probability in Wireless Networks ,” Conference on Information Science and System, Princeton, NJ, March, 2004, pgs. 430–436.**
66. Chunmei Liu and Eytan Modiano, " An Analysis of TCP over Random Access Satellite Links ,” IEEE Wireless Communications and Networking Conference (WCNC), Atlanta, GA, February, 2004, pgs. 2033–2040..**
65. Randall Berry and Eytan Modiano, " Using tunable optical transceivers for reducing the number of ports in WDM/TDM Networks ,” IEEE/OSA Optical Fiber Conference (OFC), Los Angeles, CA, February, 2004, pgs. 23–27.
64. Aradhana Narula-Tam, Eytan Modiano and Andrew Brzezinski, " Physical Topology Design for Survivable Routiing of Logical Rings in WDM-based Networks ,” IEEE Globecom, San francisco, CA, December, 2003, pgs. 2552–2557.
63. Jun Sun, Lizhong Zheng and Eytan Modiano, " Wireless Channel Allocation Using an Auction Algorithm ,” Allerton Conference on Communications, Control and Computing, October, 2003, pgs. 1114–1123..**
62. Amir Khandani, Jinane Abounadi, Eytan Modiano, Lizhong Zhang, " Cooperative Routing in Wireless Networks ,” Allerton Conference on Communications, Control and Computing, October, 2003, pgs. 1270–1279.**
61. Poompat Saengudomlert, Eytan Modiano and Robert Gallager, " Dynamic Wavelength Assignment for WDM all optical Tree Networks ,” Allerton Conference on Communications, Control and Computing, October, 2003, 915–924.**
60. Aradhana Narula-Tam and Eytan Modiano, " Designing Physical Topologies that Enable Survivable Routing of Logical Rings ,” IEEE Workshop on Design of Reliable Communication Networks (DRCN), October, 2003, pgs. 379–386.
59. Anand Srinivas and Eytan Modiano, " Minimum Energy Disjoint Path Routing in Wireless Ad Hoc Networks ,” ACM Mobicom, San Diego, Ca, September, 2003, pgs. 122–133.**
58. Michael Neely and Eytan Modiano, " Improving Delay in Ad-Hoc Mobile Networks Via Redundant Packet Transfers ,” Conference on Information Science and System, Baltimore, MD, March, 2003 (6 pages; CD proceedings – page numbers not available).**
57. Michael Neely, Eytan Modiano and Charles Rohrs, " Dynamic Power Allocation and Routing for Time Varying Wireless Networks ,” IEEE Infocom 2003, San Francisco, CA, April, 2003, pgs. 745–755.**
56. Alvin Fu, Eytan Modiano, and John Tsitsiklis, " Optimal Energy Allocation for Delay-Constrained Data Transmission over a Time-Varying Channel ,” IEEE Infocom 2003, San Francisco, CA, April, 2003, pgs. 1095–1105.**
55. Poompat Saengudomlert, Eytan Modiano and Rober Gallager, " On-line Routing and Wavelength Assignment for Dynamic Traffic in WDM Ring and Torus Networks ,” IEEE Infocom 2003, San Francisco, CA, April, 2003, pgs. 1805–1815.**
54. Li-Wei Chen and Eytan Modiano, " Efficient Routing and Wavelength Assignment for Reconfigurable WDM Networks with Wavelength Converters ,” IEEE Infocom 2003, San Francisco, CA, April, 2003, pgs. 1785–1794. Selected as one of the best papers of Infocom 2003 for fast track publication in IEEE/ACM Transactions on Networking.**
53. Mike Neely, Jun Sun and Eytan Modiano, " Delay and Complexity Tradeoffs for Dynamic Routing and Power Allocation in a Wireless Network ,” Allerton Conference on Communication, Control, and Computing, Allerton, Illinois, October, 2002, pgs. 157 –159.**
52. Anand Ganti, Eytan Modiano and John Tsitsiklis, " Transmission Scheduling for Multi-Channel Satellite and Wireless Networks ,” Allerton Conference on Communication, Control, and Computing, Allerton, Illinois, October, 2002, pgs. 1318–1327.**
51. Poompat Saengudomlert, Eytan Modiano, and Robert G. Gallager, " Optimal Wavelength Assignment for Uniform All-to-All Traffic in WDM Tree Networks ,” Allerton Conference on Communication, Control, and Computing, Allerton, Illinois, October, 2002, pgs. 528–537.**
50. Hungjen Wang, Eytan Modiano and Muriel Medard, " Partial Path Protection for WDM Networks: End-to-End Recovery Using Local Failure Information ,” IEEE International Symposium on Computer Communications (ISCC), Taormina, Italy, July 2002, pgs. 719–725.**
49. Jun Sun and Eytan Modiano, " Capacity Provisioning and Failure Recovery in Mesh-Torus Networks with Application to Satellite Constellations ,” IEEE International Symposium on Computer Communications (ISCC), Taormina, Italy, July 2002, pgs. 77–84.**
48. Alvin Fu, Eytan Modiano, and John Tsitsiklis, " Optimal Energy Allocation and Admission Control for Communications Satellites ,” IEEE INFOCOM 2002, New York, June, 2002, pgs. 648–656.**
47. Michael Neely, Eytan Modiano and Charles Rohrs, " Power and Server Allocation in a Multi-Beam Satellite with Time Varying Channels ,” IEEE INFOCOM 2002, New York, June, 2002, pgs. 1451–1460..**
46. Mike Neely, Eytan Modiano and Charles Rohrs, " Tradeoffs in Delay Guarantees and Computation Complexity for N x N Packet Switches ,” Conference on Information Science and Systems, Princeton, NJ, March, 2002, pgs. 136–148.**
45. Alvin Fu, Eytan Modiano and John Tsitsiklis, " Transmission Scheduling Over a Fading Channel with Energy and Deadline Constraints ,” Conference on Information Science and System, Princeton, NJ, March, 2002, pgs. 1018–1023.**
44. Chunmei Liu and Eytan Modiano, " On the Interaction of Layered Protocols: The Case of Window Flow Control and ARQ ,” Conference on Information Science and System, Princeton, NJ, March, 2002, pgs. 118–124.**
43. Mike Neely, Eytan Modiano and Charles Rohrs, " Packet Routing over Parallel Time-varying Queues with Application to Satellite and Wireless Networks ,” Conference on Information Science and System, Princeton, NJ, March, 2002, pgs. 360–366.**
42. Ahluwalia Ashwinder, Eytan Modiano and Li Shu, " On the Complexity and Distributed Construction of Energy Efficient Broadcast Trees in Static Ad Hoc Wireless Networks ,” Conference on Information Science and System, Princeton, NJ, March, 2002, pgs. 807–813.**
41. Jun Sun and Eytan Modiano, " Capacity Provisioning and Failure Recovery for Satellite Constellations ,” Conference on Information Science and System, Princeton, NJ, March, 2002, pgs. 1039–1045.**
40. Eytan Modiano, Hungjen Wang, and Muriel Medard, " Partial Path Protection for WDM networks ,” Informs Telecommunications Conference, Boca Raton, FL, March 2002, pgs. 78–79.**
39. Poompat Saengudomlert, Eytan H. Modiano, and Robert G. Gallager, " An On-Line Routing and Wavelength Assignment Algorithm for Dynamic Traffic in a WDM Bidirectional Ring ,” Joint Conference on Information Sciences (JCIS), Durham, North Carolina, March, 2002, pgs. 1331–1334.**
38. Randy Berry and Eytan Modiano, " Switching and Traffic Grooming in WDM Networks ,” Joint Conference on Information Sciences (JCIS), Durham, North Carolina, March, 2002, pgs. 1340–1343.
37. Eytan Modiano, Hungjen Wang, and Muriel Medard, " Using Local Information for WDM Network Protection ,” Joint Conference on Information Sciences (JCIS), Durham, North Carolina, March, 2002, pgs. 1398–1401.**
36. Aradhana Narula-Tam and Eytan Modiano, " Network architectures for supporting survivable WDM rings ,” IEEE/OSA Optical Fiber Conference (OFC) 2002, Anaheim, CA, March, 2002, pgs. 105–107.
35. Michael Neely, Eytan Modiano, Charles Rohrs, " Packet Routing over Parallel Time-Varying Queues with Application to Satellite and Wireless Networks ,” Allerton Conference on Communication, Control, and Computing, Allerton, Illinois, September, 2001, pgs. 1110-1111.**
34. Eytan Modiano and Randy Berry, " The Role of Switching in Reducing Network Port Counts ,” Allerton Conference on Communication, Control, and Computing, Allerton, Illinois, September, 2001, pgs. 376-385.
33. Eytan Modiano, " Resource allocation and congestion control in next generation satellite networks ,” IEEE Gigabit Networking Workshop (GBN 2001), Anchorage, AK, April 2001, (2 page summary-online proceedings).
32. Eytan Modiano and Aradhana Narula-Tam, " Survivable Routing of Logical Topologies in WDM Networks ,” IEEE Infocom 2001, Anchorage, AK, April 2001, pgs. 348–357.
31. Michael Neely and Eytan Modiano, " Convexity and Optimal Load Distribution in Work Conserving */*/1 Queues ,” IEEE Infocom 2001, Anchorage, AK, April 2001, pgs. 1055–1064.
30. Eytan Modiano and Randy Berry, " Using Grooming Cross- Connects to Reduce ADM Costs in Sonet/WDM Ring Networks ,” IEEE/OSA Optical Fiber Conference (OFC) 2001, Anaheim, CA March 2001, pgs. WL1- WL3.
29. Eytan Modiano and Aradhana Narula-Tam, " Designing Survivable Networks Using Effective Rounting and Wavelenght Assignment (RWA) ,” IEEE/OSA Optical Fiber Conference (OFC) 2001, Anaheim, CA March 2001, pgs. TUG5-1 – TUG5– 3.
28. Roop Ganguly and Eytan Modiano, " Distributed Algorithms and Architectures for Optical Flow Switching in WDM networks ,” IEEE International Symposium on Computer Communications (ISCC 2000), Antibes, France, July 2000, pgs. 134–139.
27. Aradhana Narula-Tam, Philip J. Lin and Eytan Modiano, " Wavelength Requirements for Virtual topology Reconfiguration in WDM Ring Networks ,” IEEE International Conference on Communications (ICC 2000), New Orleans, LA, June 2000, pgs. 1650–1654.
26. Eytan Modiano, "Optical Flow Switching for the Next Generation Internet,” IEEE Gigabit Networking Workshop (GBN 2000), Tel-aviv, March 2000 (2 page summary-online proceedings).
25. Aradhana Narula and Eytan Modiano, " Dynamic Reconfiguration in WDM Packet Networks with Wavelength Limitations ,” IEEE/OSA Optical Fiber Conference (OFC) 2000, Baltimore, MD, March, 2000, pgs. 1210–1212.
24. Brett Schein and Eytan Modiano, " Quantifying the benefits of configurability in circuit-switched WDM ring networks ,” IEEE Infocom 2000, Tel Aviv, Israel, April, 2000, pgs.1752–1760..***
23. Aradhana Narula-Tam and Eytan Modiano, " Load Balancing Algorithms for WDM-based IP networks ,” IEEE Infocom 2000, Tel Aviv, Israel, April, 2000, pgs. 1010–1019.
22. Nan Froberg, M. Kuznetsov, E. Modiano, et. al., " The NGI ONRAMP test bed: Regional Access WDM technology for the Next Generation Internet ,” IEEE LEOS ’99, October, 1999, pgs. 230–231.
21. Randy Berry and Eytan Modiano, " Minimizing Electronic Multiplexing Costs for Dynamic Traffic in Unidirectional SONET Ring Networks ,” IEEE International Conference on Communications (ICC ’99), Vancouver, CA, June 1999, pgs. 1724–1730..***
20. Brett Schein and Eytan Modiano, "Increasing Traffic Capacity in WDM Ring Networks via Topology Reconfiguration,” Conference on Information Science and Systems, Baltimore, MD, March 1999, pgs. 201 – 206.
19. Eytan Modiano and Richard Barry, " Design and Analysis of an Asynchronous WDM Local Area Network Using a Master/Slave Scheduler ,” IEEE Infocom ’99, New York, NY, March 1999, pgs. 900–907.
18. Randy Berry and Eytan Modiano, " Grooming Dynamic Traffic in Unidirectional SONET Ring Networks ,” IEEE/OSA Optical Fiber Conference (OFC) ’99, San Diego, CA, February 1999, pgs. 71–73.
17. Angela Chiu and Eytan Modiano, " Reducing Electronic Multiplexing Costs in Unidirectional SONET/WDM Ring Networks Via Efficient Traffic Grooming ,” IEEE Globecom '98, Sydney, Australia, November 1998, pgs. 322–327.
16. Eytan Modiano, " Throughput Analysis of Unscheduled Multicast Transmissions in WDM Broadcast-and-Select Networks ,” IEEE International Symposium on Information Theory, Boston, MA, September 1998, pg. 167.
15. Eytan Modiano and Angela Chiu, "Traffic Grooming Algorithms for Minimizing Electronic Multiplexing Costs in Unidirectional SONET/WDM Ring Networks,” Conference on Information Science and Systems, Princeton, NJ, March 1998, 653–658.
14. Eytan Modiano and Eric Swanson, " An Architecture for Broadband Internet Services over a WDM-based Optical Access Network ,” IEEE Gigabit Networking Workshop (GBN '98), San Francisco, CA, March 1998 (2 page summary-online proceedings).
13. Eytan Modiano, " Unscheduled Multicasts in WDM Broadcast-and-Select Networks ,” IEEE Infocom '98, San Francisco, CA, March 1998, pgs. 86–93.
12. Eytan Modiano, Richard Barry and Eric Swanson, " A Novel Architecture and Medium Access Control (MAC) protocol for WDM Networks ,” IEEE/OSA Optical Fiber Conference (OFC) '98, San Jose, CA, February 1998, pgs. 90–91.
11. Eytan Modiano, " Scheduling Algorithms for Message Transmission Over a Satellite Broadcast System ,” IEEE MILCOM 97, Monterey, CA, November 1997, pgs. 628–634.
10. Eytan Modiano, " Scheduling Packet Transmissions in A Multi-hop Packet Switched Network Based on Message Length ,” IEEE International Conference on Computer Communications and Networks (IC3N) Las Vegas, Nevada, September 1997, pgs. 350–357.
9. Eytan Modiano, "A Simple Algorithm for Optimizing the Packet Size Used in ARQ Protocols Based on Retransmission History,” Conference on Information Science and Systems, Baltimore, MD, March 1997, pgs. 672–677.
8. Eytan Modiano, " A Multi-Channel Random Access Protocol for the CDMA Channel ,” IEEE PIMRC '95, Toronto, Canada, September 1995, pgs. 799–803.
7. Eytan Modiano Jeffrey Wieselthier and Anthony Ephremides, " A Simple Derivation of Queueing Delay in a Tree Network of Discrete-Time Queues with Deterministic Service Times ,” IEEE International Symposium on Information Theory, Trondheim, Norway, June 1994, pg. 372.
6. Eytan Modiano, Jeffrey Wieselthier and Anthony Ephremides, "An Approach for the Analysis of Packet Delay in an Integrated Mobile Radio Network,” Conference on Information Sciences and Systems, Baltimore, MD, March 1993, pgs. 138-139.
5. Eytan Modiano and Anthony Ephremides, " A Method for Delay Analysis of Interacting Queues in Multiple Access Systems ,” IEEE INFOCOM 1993, San Francisco, CA, March 1993, pgs. 447 – 454.
4. Eytan Modiano and Anthony Ephremides, " A Model for the Approximation of Interacting Queues that Arise in Multiple Access Schemes ,” IEEE International Symposium on Information Theory, San Antonio, TX, January 1993, pg. 324.
3. Eytan Modiano and Anthony Ephremides, " Efficient Routing Schemes for Multiple Broadcasts in a Mesh ,” Conference on Information Sciences and Systems, Princeton, NJ, March 1992, pgs. 929 – 934.
2. Eytan Modiano and Anthony Ephremides, " On the Secrecy Complexity of Computing a Binary Function of Non-uniformly Distributed Random Variables ,” IEEE International Symposium on Information Theory, Budapest, Hungary, June 1991, pg. 213.
1. Eytan Modiano and Anthony Ephremides, "Communication Complexity of Secure Distributed Computation in the Presence of Noise,” IEEE International Symposium on Information Theory, San Diego, CA, January 1990, pg. 142.
Book Chapters
- Hyang-Won Lee, Kayi Lee, Eytan Modiano, " Cross-Layer Survivability " in Cross-Layer Design in Optical Networks, Springer, 2013.
- Li-Wei Chen and Eytan Modiano, " Geometric Capacity Provisioning for Wavelength-Switched WDM Networks ," Chapter in Computer Communications and Networks Series: Algorithms for Next Generation Networks, Springer, 2010.
- Amir Khandani, Eytan Modiano, Lizhong Zhang, Jinane Aboundi, " Cooperative Routing in Wireless Networks ," Chapter in Advances in Pervasive Computing and Networking, Kluwer Academic Publishers, 2005.
- Jian-Qiang Hu and Eytan Modiano, " Traffic Grooming in WDM Networks ," Chapter in Emerging Optical Network Technologies, Kluwer Academic Publishers, to appear, 2004.
- Eytan Modiano, " WDM Optical Networks ," Wiley Encyclopedia of Telecommunications (John Proakis, Editor), 2003.
- Eytan Modiano, " Optical Access Networks for the Next Generation Internet ," in Optical WDM Networks: Principles and Practice, Kluwer Academic Prublishers, 2002.
- Eytan Modiano, Richard Barry and Eric Swanson, " A Novel Architecture and Medium Access Control protocol for WDM Networks ," Trends in Optics and Photonics Series (TOPS) volume on Optical Networks and Their Applications, 1998.
- Eytan Modiano and Kai-Yeung Siu, "Network Flow and Congestion Control," Wiley Encyclopedia of Electrical and Electronics Engineering, 1999.
Technical Reports
- Amir Khandani, Eytan Modiano, Jinane Abounadi, Lizhong Zheng, "Reliability and Route Diversity in Wireless Networks, " MIT LIDS Technical Report number 2634, November, 2004.
- Anand Srinivas and Eytan Modiano, "Minimum Energy Disjoint Path Routing in Wireless Ad Hoc Networks, " MIT LIDS Technical Report, P-2559, March, 2003.
- Eytan Modiano and Aradhana Narula-Tam, "Survivable lightpath routing: a new approach to the design of WDM-based networks, " LIDS report 2552, October, 2002.
- Michael Neely, Eytan Modiano and Charles Rohrs, "Packet Routing over Parallel Time-Varying Queues with Application to Satellite and Wireless Networks," LIDS report 2520, September, 2001.
- Jun Sun and Eytan Modiano, "Capacity Provisioning and Failure Recovery in Mesh-Torus Networks with Application to Satellite Constellations," LIDS report 2518, September, 2001.
- Hungjen Wang, Eytan Modiano and Muriel Medard, "Partial Path Protection for WDM Networks: End-to-End Recovery Using Local Failure Information, " LIDS report 2517, Sept. 2001.
- Alvin Fu, Eytan Modiano, and John Tsitsiklis, "Optimal Energy Allocation and Admission Control for Communications Satellites, " LIDS report 2516, September, 2001.
- Michael Neely, Eytan Modiano and Charles Rohrs, "Power and Server Allocation in a Multi-Beam Satellite with Time Varying Channels, " LIDS report 2515, September, 2001.
- Eytan Modiano, "Scheduling Algorithms for Message Transmission Over the GBS Satellite Broadcast System, " Lincoln Laboratory Technical Report Number TR-1035, June 1997.
- Eytan Modiano, "Scheduling Packet Transmissions in A Multi-hop Packet Switched Network Based on Message Length, " Lincoln Laboratory Technical Report number TR-1036, June, 1997.
- Research & Faculty
- Offices & Services
- Information for:
- Faculty & Staff
- News & Events
- Contact & Visit
- About the Department
- Message from the Chair
- Computer Science Major (BS/BA)
- Computer Science Minor
- Data Science and Engineering Minor
- Combined BS (or BA)/MS Degree Program
- Intro Courses
- Special Programs & Opportunities
- Student Groups & Organizations
- Undergraduate Programs
- Undergraduate Research
- Senior Thesis
- Peer Mentors
- Curriculum & Requirements
- MS in Computer Science
- PhD in Computer Science
- Admissions FAQ
- Financial Aid
- Graduate Programs
- Courses Collapse Courses Submenu
- Research Overview
- Research Areas
- Systems and Networking
- Security and Privacy
- Programming Languages
- Artificial Intelligence
- Human-Computer Interaction
- Vision and Graphics
- Groups & Labs
- Affiliated Centers & Institutes
- Industry Partnerships
- Adobe Research Partnership
- Center for Advancing Safety of Machine Intelligence
- Submit a Tech Report
- Tech Reports
- Tenure-Track Faculty
- Faculty of Instruction
- Affiliated Faculty
- Adjunct Faculty
- Postdoctoral Fellows
- PhD Students
- Outgoing PhDs and Postdocs
- Visiting Scholars
- News Archive
- Weekly Bulletin
- Monthly Student Newsletter
- All Public Events
- Seminars, Workshops, & Talks
- Distinguished Lecture Series
- CS Colloquium Series
- CS + X Events
- Tech Talk Series
- Honors & Awards
- External Faculty Awards
- University Awards
- Department Awards
- Student Resources
- Undergraduate Student Resources
- MS Student Resources
- PhD Student Resources
- Student Organization Resources
- Faculty Resources
- Postdoc Resources
- Staff Resources
- Purchasing, Procurement and Vendor Payment
- Expense Reimbursements
- Department Operations and Facilities
- Initiatives
- Student Groups
- CS Faculty Diversity Committee
- Broadening Participation in Computing (BPC) Plan
- Northwestern Engineering
Research / Research Areas Systems and Networking
Systems and Networking is a broad and diverse area of computing research which spans areas including: systems, networks and distributed systems, programming languages and software engineering, compilers, databases and data science, security and cryptography, and mobile and wireless systems.

Nabil Alshurafa
Associate Professor of Preventive Medicine and (by courtesy) Computer Science and Electrical and Computer Engineering
Email Nabil Alshurafa

Fabian Bustamante
Professor of Computer Science
Email Fabian Bustamante

Simone Campanoni
Associate Professor of Computer Science and (by courtesy) Electrical and Computer Engineering
Email Simone Campanoni

Yan Chen
Email Yan Chen

Alok Choudhary
Harold Washington Professor of Electrical and Computer Engineering and Computer Science
Email Alok Choudhary

Christos Dimoulas
Assistant Professor of Computer Science
Email Christos Dimoulas

Peter Dinda
Professor of Computer Science and (by courtesy) Electrical and Computer Engineering
Email Peter Dinda

Robby Findler
Email Robby Findler

Branden Ghena
Assistant Professor of Instruction
Email Branden Ghena

Nikos Hardavellas
Associate Professor of Computer Science
Associate Professor of Electrical and Computer Engineering
Email Nikos Hardavellas

Josiah Hester
Adjunct Associate Professor of Electrical and Computer Engineering
Adjunct Associate Professor of Computer Science
Email Josiah Hester

Russell Joseph
Email Russell Joseph

Aleksandar Kuzmanovic
Email Aleksandar Kuzmanovic

Seda Ogrenci
Professor of Electrical and Computer Engineering
Email Seda Ogrenci

Jennie Rogers
Email Jennie Rogers

Vincent St-Amour
Associate Professor of Instruction
Email Vincent St-Amour

Kate Smith
Email Kate Smith
More in this section
- Engineering Home
- CS Department
Related Links
- Research at McCormick
- Meet our Faculty
- Northwestern Research Overview
Contact Info
Fabian Bustamante Professor Email
Peter Dinda Professor Email
Articles on Networking
Displaying 1 - 20 of 39 articles.

Despite appearances, digital networking hasn’t killed the business card – yet
Jane Menzies , University of the Sunshine Coast

Networking: an opportunity or an obstacle for women?
Miryam Martinez Martinez , Universidad CEU San Pablo ; Gabriela Contreras , Radboud University , and Susana González Pérez , Universidad CEU San Pablo
Optus has revealed the cause of the major outage. Could it happen again?
Mark A Gregory , RMIT University

Businesses that address social or environmental problems often struggle to survive: 3 things that can help them
Willie Tafadzwa Chinyamurindi , University of Fort Hare ; Motshedisi Mathibe , University of Pretoria , and Progress Hove-Sibanda , Nelson Mandela University

Here’s what to do when you encounter people with ‘dark personality traits’ at work
Cinthia Beccacece Satornino , University of New Hampshire

Fishing, strip clubs and golf: How male-focused networking in medicine blocks female colleagues from top jobs
Jennifer R. Grandis , University of California, San Francisco

Got $1.2T to invest in roads and other infrastructure? Here’s how to figure out how to spend it wisely
Anna Nagurney , UMass Amherst

Study shows the power of networking in alleviating hardship during COVID-19
Naiema Taliep , University of South Africa and Ghouwa Ismail , University of South Africa

4 ways that volunteering can be good for you
Jennifer A. Jones , University of Florida

How to narrow the gap between what universities produce and what employers expect
Angelo Fynn , University of South Africa

How WhatsApp groups support Nigeria’s nurse graduates
Ademola Johnson Ajuwon , University of the Witwatersrand and Christoph Pimmer , University of Applied Sciences Northwestern Switzerland

How immigrants give American companies a powerful boost against Chinese rivals
Benjamin A.T. Graham , USC Dornsife College of Letters, Arts and Sciences

Research shows networking is painful, but it can be a lot better
Libby (Elizabeth) Sander , Bond University

Internet openness pits collaborative history against competitive future
Lorenzo De Carli , Colorado State University

Access to mobile phones won’t magically fix youth unemployment in Africa
Gina Porter , Durham University and Ariane De Lannoy , University of Cape Town

Unraveling what’s holding back women economists in academia
Michael E. Rose , University of Cape Town

Why the FCC’s proposed internet rules may spell trouble ahead
David Choffnes , Northeastern University

Creating a high-speed internet lane for emergency situations
Nirmala Shenoy , Rochester Institute of Technology ; Erik Golen , Rochester Institute of Technology , and Jennifer Schneider , Rochester Institute of Technology

New research highlights challenges of building networks for employees and entrepreneurs

From communities to territories: towards a Mediterranean coworking network
Raphaël Besson , Université Grenoble Alpes (UGA)
Related Topics
- Cybersecurity
- Internet of Things
- Net neutrality
- Open internet
- Social networks
- Telecommunications
Top contributors
MBA Director & Assistant Professor of Organisational Behaviour, Bond Business School, Bond University
Professor and Eugene M. Isenberg Chair in Integrative Studies, UMass Amherst
Associate Professor, School of Psychology, UNSW Sydney
Associate Professor, Rotterdam School of Management, Erasmus University Rotterdam
Professor, Computer Networking and Telecommunications, University of Salford
Professor, Information Security Group, Royal Holloway University of London
Professor of Theoretical Economics, Queen's University Belfast
Adjunct professor, Universidad CEU San Pablo
Profesora Adjunta Área de Comercialización e Investigación de Mercados, Universidad CEU San Pablo
Assistant Professor, Radboud University
Senior Lecturer in Computer science, Queen Mary University of London
Professor of Cybersecurity, School of Computer Science and Informatics, De Montfort University
Professor of Physics, University of the Witwatersrand
Associate Professor, University of the Free State
Associate Professor of Marketing, Curtin University
- X (Twitter)
- Unfollow topic Follow topic
- Privacy Policy

Home » 300+ Social Media Research Topics
300+ Social Media Research Topics

Social media has become an integral part of our lives, and it has transformed the way we communicate, share information, and interact with each other. As social media platforms continue to evolve and gain popularity, they have also become a rich source of data for researchers. Social media research is a rapidly growing field that encompasses a wide range of topics , from understanding the psychological and social effects of social media to analyzing patterns of user behavior and identifying trends in online conversations. In this era of data-driven decision-making, social media research is more important than ever, as it provides insights into how we use and are influenced by social media. In this post, we will explore some of the most fascinating and relevant social media research topics that are shaping our understanding of this powerful medium.
Social Media Research Topics
Social Media Research Topics are as follows:
- The effects of social media on mental health
- The role of social media in political polarization
- The impact of social media on relationships
- The use of social media by businesses for marketing
- The effects of social media on body image and self-esteem
- The influence of social media on consumer behavior
- The use of social media for education
- The effects of social media on language use and grammar
- The impact of social media on news consumption
- The role of social media in activism and social change
- The use of social media for job seeking and career development
- The effects of social media on sleep patterns
- The influence of social media on adolescent behavior
- The impact of social media on the spread of misinformation
- The use of social media for personal branding
- The effects of social media on political participation
- The influence of social media on fashion trends
- The impact of social media on sports fandom
- The use of social media for mental health support
- The effects of social media on creativity
- The role of social media in cultural exchange
- The impact of social media on language learning
- The use of social media for crisis communication
- The effects of social media on privacy and security
- The influence of social media on diet and exercise behavior
- The impact of social media on travel behavior
- The use of social media for citizen journalism
- The effects of social media on political accountability
- The role of social media in peer pressure
- The impact of social media on romantic relationships
- The use of social media for community building
- The effects of social media on gender identity
- The influence of social media on music consumption
- The impact of social media on academic performance
- The use of social media for social support
- The effects of social media on social skills
- The role of social media in disaster response
- The impact of social media on nostalgia and memory
- The use of social media for charity and philanthropy
- The effects of social media on political polarization in developing countries
- The influence of social media on literary consumption
- The impact of social media on family relationships
- The use of social media for citizen science
- The effects of social media on cultural identity
- The role of social media in promoting healthy behaviors
- The impact of social media on language diversity
- The use of social media for environmental activism
- The effects of social media on attention span
- The influence of social media on art consumption
- The impact of social media on cultural values and norms.
- The impact of social media on mental health
- The impact of social media on mental health.
- The impact of social media on body image and self-esteem.
- The use of social media for political activism and social justice movements.
- The role of social media in promoting cultural diversity and inclusivity.
- The impact of social media on romantic relationships and dating.
- The use of social media for customer service and support.
- The impact of social media on mental health and well-being among young adults.
- The impact of social media on political polarization and partisanship.
- The use of social media for health communication and behavior change.
- The role of social media in shaping public opinion and attitudes towards vaccination.
- The impact of social media on political participation and civic engagement.
- The impact of social media on political polarization and echo chambers.
- The use of social media for political campaigning and the manipulation of public opinion.
- The role of social media in shaping public attitudes towards vaccination and public health.
- The impact of social media on news consumption and trust in journalism.
- The use of social media for promoting sustainable fashion practices and ethical consumption.
- The role of social media in influencing beauty standards and body image.
- The impact of social media on the music industry and the role of social media influencers.
- The use of social media for promoting mental health and well-being among healthcare professionals.
- The role of social media in shaping public attitudes towards gun violence and gun control policies.
- The impact of social media on social activism and advocacy.
- The use of social media for promoting cross-cultural communication and intercultural understanding.
- The role of social media in shaping public attitudes towards climate change and environmental policies.
- The impact of social media on public health during the COVID-19 pandemic.
- The use of social media for promoting financial literacy and access to financial services for low-income individuals.
- The role of social media in shaping public attitudes towards immigration policies and refugee crises.
- The impact of social media on political activism and social movements.
- The use of social media for promoting digital literacy and technology education in developing countries.
- The role of social media in shaping public attitudes towards gender and sexual orientation.
- The impact of social media on consumer behavior in the food and beverage industry.
- The use of social media for promoting mental health and well-being among first responders.
- The role of social media in shaping public attitudes towards racial justice and police brutality.
- The impact of social media on privacy concerns and data security.
- The use of social media for promoting interfaith dialogue and religious tolerance.
- The role of social media in shaping public attitudes towards income inequality and economic justice.
- The impact of social media on the film and television industry and consumer behavior.
- The use of social media for promoting mental health and well-being among military personnel.
- The role of social media in shaping public attitudes towards privacy and data security.
- The impact of social media on the hospitality industry and consumer behavior.
- The use of social media for promoting intergenerational communication and understanding.
- The role of social media in shaping public attitudes towards animal welfare and animal rights.
- The impact of social media on the gaming industry and gamer behavior.
- The use of social media for promoting digital literacy and technology skills among seniors.
- The role of social media in shaping public attitudes towards renewable energy and sustainability.
- The impact of social media on the advertising industry and consumer behavior.
- The use of social media for promoting mental health and well-being among children and adolescents.
- The role of social media in shaping public attitudes towards online privacy and security.
- The impact of social media on the beauty industry and consumer behavior.
- The use of social media for promoting cultural preservation and heritage tourism.
- The role of social media in shaping public attitudes towards criminal justice reform.
- The impact of social media on the automotive industry and consumer behavior.
- The use of social media for promoting mental health and well-being among marginalized communities.
- The role of social media in shaping public attitudes towards sustainable development goals.
- The impact of social media on the fashion industry and consumer behavior.
- The use of social media for promoting intercultural communication in the workplace.
- The role of social media in shaping public attitudes towards mental health policies.
- The impact of social media on the travel industry and sustainable tourism practices.
- The use of social media for health information seeking and patient empowerment.
- The role of social media in promoting environmental activism and sustainable practices.
- The impact of social media on consumer behavior and brand loyalty.
- The use of social media for promoting education and lifelong learning.
- The role of social media in shaping public opinion and attitudes towards mental health issues.
- The impact of social media on the fashion industry and fast fashion practices.
- The use of social media for promoting social entrepreneurship and social innovation.
- The role of social media in shaping public opinion and attitudes towards gun control.
- The impact of social media on the mental health and well-being of adolescents.
- The use of social media for promoting intercultural exchange and understanding.
- The role of social media in shaping public opinion and attitudes towards climate change.
- The impact of social media on political advertising and campaign strategies.
- The use of social media for promoting healthy relationships and communication skills.
- The role of social media in shaping public opinion and attitudes towards police brutality and racial justice.
- The use of social media for promoting financial literacy and personal finance management.
- The role of social media in shaping public opinion and attitudes towards LGBTQ+ rights.
- The impact of social media on the music industry and fan engagement.
- The use of social media for promoting mental health and well-being among marginalized populations.
- The role of social media in shaping public opinion and attitudes towards immigration and border policies.
- The impact of social media on the professional development and networking of journalists.
- The use of social media for promoting community building and social cohesion.
- The role of social media in shaping public opinion and attitudes towards healthcare policies.
- The impact of social media on the food industry and consumer behavior.
- The role of social media in shaping public opinion and attitudes towards gender equality.
- The impact of social media on the sports industry and athlete-fan interactions.
- The use of social media for promoting financial inclusion and access to banking services.
- The role of social media in shaping public opinion and attitudes towards animal welfare.
- The use of social media for promoting mental health and well-being among college students.
- The role of social media in shaping public opinion and attitudes towards privacy and data security.
- The role of social media in shaping public opinion and attitudes towards income inequality and poverty.
- The use of social media for promoting digital literacy and technology skills.
- The role of social media in shaping public opinion and attitudes towards renewable energy.
- The use of social media for promoting mental health and well-being among elderly populations.
- The role of social media in shaping public opinion and attitudes towards online privacy and security.
- The role of social media in shaping public opinion and attitudes towards criminal justice reform.
- The impact of social media on online activism and social movements.
- The use of social media for business-to-business communication and networking.
- The role of social media in promoting civic education and engagement.
- The impact of social media on the fashion industry and sustainable fashion practices.
- The use of social media for promoting cultural diversity and inclusion.
- The role of social media in shaping public opinion and attitudes towards police reform.
- The impact of social media on the mental health and well-being of frontline healthcare workers.
- The use of social media for promoting financial literacy and investment education.
- The role of social media in promoting environmental sustainability and conservation.
- The impact of social media on body image and self-esteem among adolescent girls.
- The use of social media for promoting intercultural dialogue and understanding.
- The role of social media in shaping public opinion and attitudes towards immigration policies and refugees.
- The impact of social media on the professional development and networking of healthcare professionals.
- The use of social media for promoting community resilience and disaster preparedness.
- The role of social media in shaping public opinion and attitudes towards the Black Lives Matter movement.
- The impact of social media on the music industry and artist-fan interactions.
- The use of social media for promoting healthy eating habits and nutrition education.
- The role of social media in promoting mental health and well-being among college students.
- The impact of social media on the entertainment industry and consumer behavior.
- The use of social media for promoting workplace diversity and inclusion.
- The role of social media in shaping public opinion and attitudes towards climate change policies.
- The impact of social media on the travel industry and consumer behavior.
- The use of social media for promoting mental health and well-being among military veterans.
- The role of social media in promoting intergenerational dialogue and understanding.
- The impact of social media on the professional development and networking of educators.
- The use of social media for promoting animal welfare and advocacy.
- The role of social media in shaping public opinion and attitudes towards reproductive rights.
- The impact of social media on the sports industry and fan behavior.
- The use of social media for promoting financial inclusion and literacy among underprivileged populations.
- The role of social media in promoting mental health and well-being among LGBTQ+ populations.
- The impact of social media on the food and beverage industry and consumer behavior.
- The use of social media for promoting interfaith dialogue and understanding.
- The role of social media in shaping public opinion and attitudes towards gun ownership.
- The use of social media for promoting mental health and well-being among caregivers.
- The role of social media in promoting sustainable tourism practices.
- The impact of social media on the gaming industry and gamer culture.
- The use of social media for promoting cultural heritage tourism and preservation.
- The role of social media in shaping public opinion and attitudes towards public transportation policies.
- The use of social media for promoting mental health and well-being among homeless populations.
- The role of social media in promoting mental health and well-being among immigrants and refugees.
- The use of social media for promoting financial literacy and entrepreneurship among youth.
- The use of social media for political mobilization and participation in authoritarian regimes.
- The role of social media in shaping public opinion and attitudes towards immigration policies.
- The impact of social media on the professional development of teachers and educators.
- The use of social media for emergency communication during public health crises.
- The role of social media in promoting LGBTQ+ rights and advocacy.
- The impact of social media on body positivity and self-acceptance among women.
- The use of social media for public diplomacy and international relations.
- The impact of social media on the mental health and well-being of marginalized communities.
- The use of social media for crisis management and disaster response in the corporate sector.
- The role of social media in promoting environmental activism and conservation.
- The impact of social media on the professional development and networking of entrepreneurs.
- The use of social media for medical education and healthcare communication.
- The role of social media in promoting cultural exchange and understanding.
- The impact of social media on social capital and civic engagement among young adults.
- The use of social media for disaster preparedness and community resilience.
- The role of social media in promoting religious pluralism and tolerance.
- The use of social media for promoting healthy lifestyles and wellness.
- The use of social media for fundraising and philanthropy in the non-profit sector.
- The role of social media in promoting interfaith dialogue and understanding.
- The impact of social media on the travel and tourism industry and consumer behavior.
- The use of social media for customer engagement and brand loyalty in the retail sector.
- The impact of social media on the political attitudes and behaviors of young adults.
- The use of social media for promoting gender equality and women’s empowerment.
- The use of social media for promoting animal welfare and adoption.
- The role of social media in promoting mental health and well-being among the elderly.
- The impact of social media on the art industry and artist-fan interactions.
- The use of social media for promoting healthy food choices and nutrition.
- The role of social media in shaping public opinion and attitudes towards income inequality.
- The use of social media for promoting political satire and humor.
- The role of social media in promoting disability rights and advocacy.
- The use of social media for promoting voter registration and participation.
- The role of social media in promoting entrepreneurship and small business development.
- The use of social media for promoting mental health and well-being among incarcerated populations.
- The role of social media in shaping public opinion and attitudes towards gun violence prevention.
- The use of social media for promoting cultural heritage and preservation.
- The impact of social media on mental health and well-being.
- The relationship between social media use and academic performance.
- The use of social media for emergency communication during natural disasters.
- The impact of social media on traditional news media and journalism.
- The role of social media in shaping public opinion and discourse.
- The use of social media for online learning and education.
- The impact of social media on the fashion and beauty industry.
- The use of social media for brand awareness and marketing.
- The impact of social media on privacy and security.
- The use of social media for job searching and recruitment.
- The impact of social media on political polarization and extremism.
- The use of social media for online harassment and cyberbullying.
- The role of social media in promoting environmental awareness and sustainability.
- The impact of social media on youth culture and identity formation.
- The use of social media for travel and tourism marketing.
- The impact of social media on consumer behavior and decision-making.
- The role of social media in shaping beauty standards and body positivity.
- The use of social media for crisis communication and disaster response.
- The impact of social media on the music industry.
- The use of social media for fundraising and philanthropy.
- The role of social media in promoting healthy lifestyles and wellness.
- The impact of social media on sports fandom and fan behavior.
- The use of social media for political lobbying and advocacy.
- The impact of social media on the entertainment industry.
- The use of social media for healthcare communication and patient engagement.
- The role of social media in promoting gender equality and feminism.
- The impact of social media on the restaurant and food industry.
- The use of social media for volunteerism and community service.
- The role of social media in promoting religious tolerance and interfaith dialogue.
- The impact of social media on the art industry.
- The use of social media for political satire and humor.
- The role of social media in promoting disability awareness and advocacy.
- The impact of social media on the real estate industry.
- The use of social media for legal advocacy and justice reform.
- The role of social media in promoting intercultural communication and understanding.
- The impact of social media on the automotive industry.
- The use of social media for pet adoption and animal welfare advocacy.
- The role of social media in promoting mental health and wellness for marginalized communities.
- The impact of social media on the retail industry.
- The use of social media for promoting civic engagement and voter participation.
- The impact of social media on the film and television industry.
- The use of social media for fashion and style inspiration.
- The role of social media in promoting activism for human rights and social issues.
- The effectiveness of social media for political campaigns.
- The role of social media in promoting fake news and misinformation.
- The impact of social media on self-esteem and body image.
- The impact of social media on romantic relationships.
- The use of social media for online activism and social justice movements.
- The impact of social media on traditional news media.
- The impact of social media on interpersonal communication skills.
- The impact of social media on the fashion industry.
- The use of social media for social support and mental health awareness.
- The use of social media for political lobbying and activism.
- The impact of social media on travel and tourism behavior.
- The use of social media for customer feedback and market research.
- The impact of social media on the restaurant industry.
- The role of social media in political activism
- The effect of social media on interpersonal communication
- The relationship between social media use and body image concerns
- The impact of social media on self-esteem
- The role of social media in shaping cultural norms and values
- The use of social media by celebrities and its impact on their image
- The role of social media in building and maintaining personal relationships
- The use of social media for job searching and recruitment
- The impact of social media on children and adolescents
- The use of social media by political candidates during election campaigns
- The role of social media in education
- The impact of social media on political polarization
- The use of social media for news consumption
- The effect of social media on sleep habits
- The use of social media by non-profit organizations for fundraising
- The role of social media in shaping public opinion
- The influence of social media on language and communication patterns
- The use of social media in crisis communication and emergency management
- The role of social media in promoting environmental awareness
- The influence of social media on music preferences
- The impact of social media on body positivity movements
- The role of social media in shaping beauty standards
- The influence of social media on sports fandom
- The use of social media for health promotion and education
- The impact of social media on political participation
- The role of social media in shaping parenting practices
- The influence of social media on food preferences and eating habits
- The use of social media for peer support and mental health advocacy
- The role of social media in shaping religious beliefs and practices
- The influence of social media on humor and comedy
- The use of social media for online activism and social justice advocacy
- The impact of social media on public health awareness campaigns
- The role of social media in promoting cultural diversity and inclusion
- The influence of social media on travel behavior and decision-making
- The use of social media for international diplomacy and relations
- The impact of social media on job satisfaction and employee engagement
- The role of social media in shaping romantic preferences and dating behavior
- The influence of social media on language learning and language use
- The use of social media for political satire and humor
- The impact of social media on social capital and community building
- The role of social media in shaping gender identity and expression
- The influence of social media on fashion and beauty advertising.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

300+ American History Research Paper Topics

500+ Cyber Security Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics
- IEEE CS Standards
- Career Center
- Subscribe to Newsletter
- IEEE Standards
- For Industry Professionals
- For Students
- Launch a New Career
- Membership FAQ
- Membership FAQs
- Membership Grades
- Special Circumstances
- Discounts & Payments
- Distinguished Contributor Recognition
- Grant Programs
- Find a Local Chapter
- Find a Distinguished Visitor
- Find a Speaker on Early Career Topics
- Technical Communities
- Collabratec (Discussion Forum)
- Start a Chapter
- My Subscriptions
- My Referrals
- Computer Magazine
- ComputingEdge Magazine
- Let us help make your event a success. EXPLORE PLANNING SERVICES
- Events Calendar
- Calls for Papers
- Conference Proceedings
- Conference Highlights
- Top 2024 Conferences
- Conference Sponsorship Options
- Conference Planning Services
- Conference Organizer Resources
- Virtual Conference Guide
- Get a Quote
- CPS Dashboard
- CPS Author FAQ
- CPS Organizer FAQ
- Find the latest in advanced computing research. VISIT THE DIGITAL LIBRARY
- Open Access
- Tech News Blog
- Author Guidelines
- Reviewer Information
- Guest Editor Information
- Editor Information
- Editor-in-Chief Information
- Volunteer Opportunities
- Video Library
- Member Benefits
- Institutional Library Subscriptions
- Advertising and Sponsorship
- Code of Ethics
- Educational Webinars
- Online Education
- Certifications
- Industry Webinars & Whitepapers
- Research Reports
- Bodies of Knowledge
- CS for Industry Professionals
- Resource Library
- Newsletters
- Women in Computing
- Digital Library Access
- Organize a Conference
- Run a Publication
- Become a Distinguished Speaker
- Participate in Standards Activities
- Peer Review Content
- Author Resources
- Publish Open Access
- Society Leadership
- Boards & Committees
- Local Chapters
- Governance Resources
- Conference Publishing Services
- Chapter Resources
- About the Board of Governors
- Board of Governors Members
- Diversity & Inclusion
- Open Volunteer Opportunities
- Award Recipients
- Student Scholarships & Awards
- Nominate an Election Candidate
- Nominate a Colleague
- Corporate Partnerships
- Conference Sponsorships & Exhibits
- Advertising
- Recruitment
- Publications
- Education & Career
The 4 Most Important Networking Trends in 2020 and Beyond

In today’s digital world, networking technology is everything. It’s what makes the internet possible. It’s how businesses support sprawling multinational footprints. It’s even stitching together the appliances in our homes into one, smart, convenient fabric. For all of its importance, though, networking technology as a whole doesn’t tend to change much. For example, the internet itself runs on an iteration of a protocol that’s now 40 years old . Most of the developments in networking over that time have revolved around capacity and speed – not capability. As we move into the 2020s, though, there are a number of trends and technologies that are poised to create real change in the world of networking. Here are the four most important ones among them.
Next-Generation Wireless Technology
Without a doubt, the biggest networking technology development of the 2020s is one that’s going to be all around us very soon – the deployment of next-generation wireless networks. In the mobile networking arena, it’s the 5G standard that’s going to rewrite the rules of what’s possible for technology on-the-go. It’s these new cellular networks that are going to unleash the true potential of things like augmented reality and the IoT, as well as bringing us closer to a world filled with “ smart everything “. Indoors, the wireless revolution’s going to be led by Wi-Fi 6, the soon-to-go-mainstream standard that’s making its way into devices right now . It will not only triple the theoretical maximum throughput of its immediate predecessor, but will deliver better indoor signal penetration and support greater device density. In a world where every electrical device is gaining networking capabilities, the effects of Wi-Fi 6 can’t be overstated.
SD-WAN Becoming Common
Over the course of the last decade, cloud providers, SaaS and IaaS solutions, and mobile computing have come to challenge the traditional notion of boundary-driven networking. In the past, corporate and other private networks were animated by the concept of fenced-off access using firewalls and other location-centric controls. Now, as business computing assets have started to spread to remote data centers and mobile systems, a new concept has emerged – software-defined wide area networks (SD-WAN). This new paradigm in networking makes it possible to use a variety of network interconnections to create a private business LAN analog consisting of assets in the cloud, data centers, and branch offices that function like a single, seamless system. More than anything, this is made possible by continued improvements in WAN link bandwidth, which now allow geographically disbursed resources to move data at or near LAN speeds across vast distances. As the 2020s wear on, SD-WAN will come to replace traditional hardware-based onsite networking approaches.
Want More Tech News? Subscribe to ComputingEdge Newsletter Today!
Encryption Everywhere
One of the glaring deficiencies in the internet’s infrastructure has always been a lack of built-in data security and privacy features. That reality is increasing the pressure on website operators, app developers, and networking vendors to take steps to make encryption a part of their platforms as a means of making up for the underlying insecurity of the networks they rely on. And even though the tech media would have you believe that users looking for ways to watch any country’s Netflix is what’s driving the increase in the use of consumer VPN services, it too is a result of the push toward encryption everywhere. In the networking world, the push for encryption everywhere hasn’t gone unnoticed. It has in fact spurred hardware developers toward making encryption at the network layer a standard feature of their hardware going forward. It’s become so important that estimates now believe that the network encryption market will be worth $5.8 billion by 2026 , almost doubling in size in little more than five years.
UCaaS Displacing VoIP, OTT Messaging
One of the biggest results of the explosion of networking technology over the past 40 years is that it has revolutionized the way that we communicate. The internet began by displacing switched telephone networks as the primary means of real-time communication around the globe, and in the years since has spawned myriad ways for people to talk to one another. The result has been a fragmented communications environment that networked systems often struggle to keep up with. Between traffic shaping and prioritization to support VoIP protocols and managing the traffic generated by innumerable over-the-top messaging platforms on computers, tablets, and smartphones, the lack of standardization has been tough to navigate. In the 2020s, though, a trend toward Unified Communications as a Service (UCaaS) solutions aims to reset the landscape and allow network hardware developers to move away from supporting multiple application-specific protocols and specifications.
Connecting the Future
Judging by these and other trends now reshaping the world of networking, the 2020s are going to see the technology landscape in that field change significantly. Many of the longest-held concepts and traditional infrastructures will be replaced with more modern ones that take the needs of next-generation connected devices into account. In many ways, the idea of data networks themselves will be updated to reflect the new reality of border-free, seamless connectivity that we have now come to expect. There’s sure to be plenty of hurdles to overcome and obstacles to the remaking of networking technology as we’ve known it, but one thing is clear: networking technology, which has remained mostly unchanged for much of its history, is due for disruption on several fronts – and it’s coming in more ways than anyone is likely to be able to foresee. It’s going to make it an interesting time to be a networking professional, and that part is certain.
About the Author
Andrej is a digital marketing expert, editor at TechLoot , and a contributing writer for a variety of other technology-focused online publications. He has covered the intersection of marketing and technology for several years and is pursuing an ongoing mission to share his expertise with business leaders and marketing professionals everywhere.
Recommended by IEEE Computer Society

From Data to Discovery: AI’s Revolutionary Impact on Upstream Oil and Gas Transformation

How to Implement Sustainable Innovation in Your Business

Understanding Cloud Native Security

The Role of a Green Data Center for a Sustainable IT Infrastructure

7 Tips for Implementing an Effective Cyber GRC Program

Continuous Deployment: Trends and Predictions for 2024

5 Ways to Save on Database Costs in AWS

Redefining Trust: Cybersecurity Trends and Tactics for 2024
A Nature Research Service

- On-demand Courses
- Work with others
Networking for Researchers
For researchers in the natural sciences who want to gain confidence by improving their networking skills or mentor others through the process
10 experts in networking, including researchers, experienced academic networkers, fellows, networking consultants and communications specialists
8 hours of learning
15-minute bite-sized lessons
4-module course with certificate
About this course
‘Networking for Researchers’ covers the key elements needed to acquire or perfect effective professional networking skills for scientific researchers. In this course you will discover how building a professional network will benefit your research and career, and learn the skills to build and maintain networking connections in a variety of settings, both in-person and online.
What you’ll learn
- The theory behind and the importance of networking, and how to use your research and career goals to guide you to find appropriate networking opportunities
- How to research and prepare key resources to help you build an effective network
- Strategies to approach and connect with potential contacts, and how to follow up – both in person and online
- Strategies for nurturing your networking contacts, and how to leverage them to advance your research and career
Free Sample Why network?
5 lessons 2h
Free Sample Getting ready to network
6 lessons 2h
Free Sample Connect with new networking contacts - in person and online
7 lessons 2h 30m

Free Sample Nurturing and harnessing the power of your network
5 lessons 1h 30m
Free Sample Networking for Researchers: Free sample
No subscription yet? Try this free sample to preview lessons from the course
3 lessons 30m
Start this module
Developed with expert academics and professionals
This course has been created with an international team of experts with a wide range of experience in networking, including:
- Setting career goals
- Evaluating current networks
- Identifying networking opportunities and researching potential contacts
- Studying social networks
- Leveraging networks to advance your research and career
Sarah Blackford
Independent Career Consultant and Honorary Teaching Fellow, Lancaster University
Ben Johnson
Head of Communities & Engagement and Magazine Editor, Nature Medicine
Tanya Menon
Professor of Management & Human Resources, Fisher School of Business, Ohio State University
David Payne
Managing Editor, Careers & Supplements, Springer Nature
Despina Sanoudou
Associate Professor, National & Kapodistrian University of Athens
Advice from experienced presenters
The course also has additional insights through interviews from:
Paige Brown Jarreau
VP of Science Communication, LifeOmic and Co-founder of Lifeology.io
Emma Chapman
Lecturer, University of Nottingham
Head, Laboratory of Tumor Biology and Chair, Department of Pathology, Sackler Faculty of Medicine, Tel Aviv University, Israel
Edmond Sanganyado
Associate Professor, Shantou University and President, Zimbabwe Young Academy of Sciences
Lucy A. Taylor
Junior Research Fellow, Christ Church College and Department of Zoology, University of Oxford
Discover related courses
Getting an academic research position.
Prepare yourself to take your next career step, into either a postdoc or faculty role
Participating in a Collaboration
Build your skills to make a more meaningful contribution to your collaborative projects
Access options
For researchers.
- Register and complete our free course offering , or try a free sample of any of our paid-for courses
- Recommend our courses to your institution, so that we can contact them to discuss becoming a subscriber
For institutions, departments and labs
Find out which of our subscription plans best suits your needs See our subscription plans
Does my institution provide full course access?
When registering, you’ll be asked to select your institution first. If your institution is listed, it has subscribed and provides full access to our on-demand courses catalogue.
My institution isn’t listed!
Select „other“ and register with an individual account. This allows you to access all our free sample course modules, and our entirely free course on peer review. You might also want to recommend our courses to your institution.
I am in charge of purchasing training materials for our lab / department / institution. Buy a subscription
Start this course
Full course access via institutional subscription only. More info
Institutions, departments and labs: Give your research full access to our entire course catalogue
Image Credits
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
5 Networking Tips for Introverts (and Anyone Else)
- Samantha Dewalt

A new study reveals the make-or-break factors for developing networking skills.
Even if you’re an introvert who dreads the notion of networking, you can develop your skills to get out there and do it. Research by the Lehigh@NasdaqCenter, a partnership between Lehigh University and the Nasdaq Entrepreneurial Center, identified make-or-break factors for developing networking skills. They include: the ability to adapt your thinking swiftly in response to changing situations; combating a tendency to focus more on avoiding errors and negative results and instead striving for positive outcomes; consciously trying to have faith in your networking prowess; being persistent; and focusing more on the future.
Professionals who are extroverts are better equipped than introverts to form social connections, right? After all, they’re outgoing and more comfortable talking with strangers.
- Willy Das is a research scientist at the Lehigh@NasdaqCenter , an exclusive education-industry partnership between Lehigh University and the Nasdaq Entrepreneurial Center.
- Samantha Dewalt is managing director of the Lehigh@NasdaqCenter , an exclusive education-industry partnership between Lehigh University and the Nasdaq Entrepreneurial Center.
Partner Center
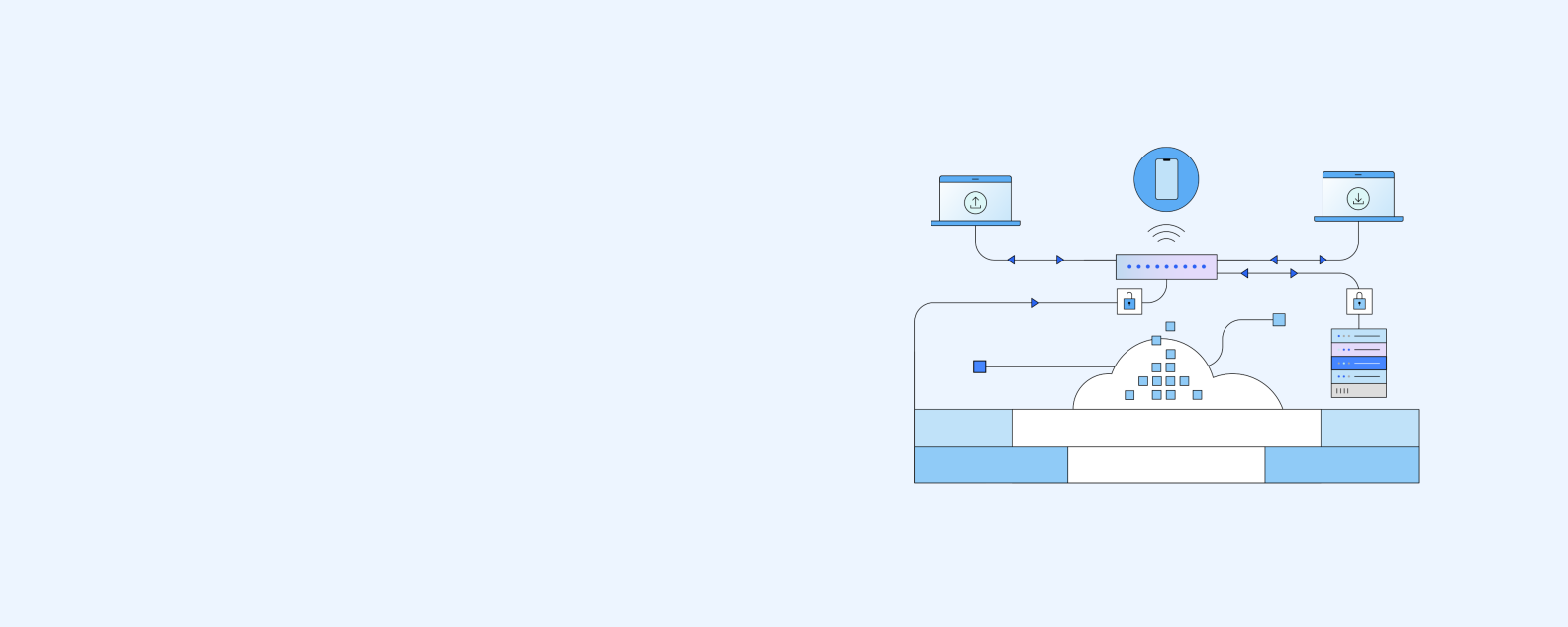
A computer network comprises two or more computers that are connected—either by cables (wired) or wifi (wireless)—with the purpose of transmitting, exchanging, or sharing data and resources.
You build a computer network by using hardware (for example, routers, switches, access points, and cables) and software (for example, operating systems or business applications).
Geographic location often defines a computer network. For example, a LAN (local area network) connects computers in a defined physical space, like an office building, whereas a WAN (wide area network) can connect computers across continents. The internet is the largest example of a WAN, connecting billions of computers worldwide.
You can further define a computer network by the protocols it uses to communicate, the physical arrangement of its components, how it controls traffic, and its purpose.
Computer networks enable communication for every business, entertainment, and research purpose. The internet, online search, email, audio and video sharing, online commerce, live-streaming, and social networks all exist because of computer networks.
Read how desktop as a service (DaaS) enables enterprises to achieve the same level of performance and security as deploying the applications on premises.
Register for the guide on app modernization
As networking needs evolved, so did the computer network types that serve those needs. Here are the most common and widely used computer network types:
LAN (local area network): A LAN connects computers over a relatively short distance, allowing them to share data, files, and resources. For example, a LAN may connect all the computers in an office building, school, or hospital. Typically, LANs are privately owned and managed.
WLAN (wireless local area network): A WLAN is just like a LAN but connections between devices on the network are made wirelessly.
WAN (wide area network): As the name implies, a WAN connects computers over a wide area, such as from region to region or even continent to continent. The internet is the largest WAN, connecting billions of computers worldwide. You will typically see collective or distributed ownership models for WAN management.
MAN (metropolitan area network): MANs are typically larger than LANs but smaller than WANs. Cities and government entities typically own and manage MANs.
PAN (personal area network): A PAN serves one person. For example, if you have an iPhone and a Mac, it’s likely you’ve set up a PAN that shares and syncs content—text messages, emails, photos, and more—across both devices.
SAN (storage area network): A SAN is a specialized network that provides access to block-level storage—shared network or cloud storage. To the user, it looks, and works like a storage drive that’s physically attached to a computer. (For more information on how a SAN works with block storage, see Block Storage: A Complete Guide ).
CAN (campus area network): A CAN is also known as a corporate area network. A CAN is larger than a LAN but smaller than a WAN. CANs serve sites such as colleges, universities, and business campuses.
VPN (virtual private network): A VPN is a secure, point-to-point connection between two network end points (see ‘nodes’ below). A VPN establishes an encrypted channel that keeps a user’s identity and access credentials, as well as any data transferred, inaccessible to hackers.
The following are some common terms to know when discussing computer networking:
IP address : An IP address is a unique number assigned to every device connected to a network that uses the Internet Protocol for communication. Each IP address identifies the device’s host network and the location of the device on the host network. When one device sends data to another, the data includes a ‘header’ that includes the IP address of the sending device and the IP address of the destination device.
Nodes : A node is a connection point inside a network that can receive, send, create, or store data. Each node requires you to provide some form of identification to receive access, like an IP address. A few examples of nodes include computers, printers, modems, bridges, and switches. A node is essentially any network device that can recognize, process, and transmit information to any other network node.
Routers : A router is a physical or virtual device that sends information that is contained in data packets between networks. Routers analyze data within the packets to determine the best way for the information to reach its ultimate destination. Routers forward data packets until they reach their destination node.
Switches : A switch is a device that connects other devices and manages node-to-node communication within a network, ensuring that data packets reach their ultimate destination. While a router sends information between networks, a switch sends information between nodes in a single network. When discussing computer networks, ‘switching’ refers to how data is transferred between devices in a network. The three main types of switching are as follows:
Circuit switching , which establishes a dedicated communication path between nodes in a network. This dedicated path assures the full bandwidth is available during the transmission, meaning that no other traffic can travel along that path.
Packet switching involves breaking down data into independent components that are called packets, which because of their small size, make fewer demands on the network. The packets travel through the network to their end destination.
Message switching sends a message in its entirety from the source node, traveling from switch to switch until it reaches its destination node.
Ports : A port identifies a specific connection between network devices. Each port is identified by a number. If you think of an IP address as comparable to the address of a hotel, then ports are the suites or room numbers within that hotel. Computers use port numbers to determine which application, service, or process should receive specific messages.
Network cable types : The most common network cable types are Ethernet twisted pair, coaxial, and fiber optic. The choice of cable type depends on the size of the network, the arrangement of network elements, and the physical distance between devices.
The wired or wireless connection of two or more computers for the purpose of sharing data and resources form a computer network. Today, nearly every digital device belongs to a computer network.
In an office setting, you and your colleagues may share access to a printer or to a group messaging system. The computing network that allows this is likely a LAN or local area network that permits your department to share resources.
A city government might manage a city-wide network of surveillance cameras that monitor traffic flow and incidents. This network would be part of a MAN or metropolitan area network that allows city emergency personnel to respond to traffic accidents, advise drivers of alternate travel routes. And even send traffic tickets to drivers who run red lights.
The Weather Company worked to create a peer-to-peer mesh network that allows mobile devices to communicate directly with other mobile devices without requiring wifi or cellular connectivity. The Mesh Network Alerts project allows the delivery of life-saving weather information to billions of people, even without an internet connection.
The internet is actually a network of networks that connects billions of digital devices worldwide. Standard protocols allow communication between these devices. Those protocols include the hypertext transfer protocol (the ‘http’ in front of all website addresses). Internet protocols (or IP addresses) are the unique identifying numbers that are required of every device that accesses the internet. IP addresses are comparable to your mailing address, providing unique location information so that information can be delivered correctly.
Internet Service Providers (ISPs) and Network Service Providers (NSPs) provide the infrastructure that allows the transmission of packets of data or information over the internet. Every bit of information that is sent over the internet doesn’t go to every device connected to the internet. It’s the combination of protocols and infrastructure that tells information exactly where to go.
Computer networks connect nodes like computers, routers, and switches by using cables, fiber optics, or wireless signals. These connections allow devices in a network to communicate and share information and resources.
Networks follow protocols, which define how communications are sent and received. These protocols allow devices to communicate. Each device on a network uses an Internet Protocol or IP address, a string of numbers that uniquely identifies a device and allows other devices to recognize it.
Routers are virtual or physical devices that facilitate communications between different networks. Routers analyze information to determine the best way for data to reach its ultimate destination. Switches connect devices and manage node-to-node communication inside a network, ensuring that bundles of information traveling across the network reach their ultimate destination.
Computer network architecture defines the physical and logical framework of a computer network. It outlines how computers are organized in the network and what tasks are assigned to those computers. Network architecture components include hardware, software, transmission media (wired or wireless), network topology, and communications protocols.
Main types of network architecture
There are two types of network architecture: peer-to-peer (P2P) and client/server . In P2P architecture, two or more computers are connected as “peers,” meaning that they have equal power and privileges on the network. A P2P network does not require a central server for coordination. Instead, each computer on the network acts as both a client (a computer that needs to access a service) and a server (a computer that serves the needs of the client accessing a service). Each peer makes some of its resources available to the network, sharing storage, memory, bandwidth, and processing power.
In a client/server network, a central server or group of servers manage resources and deliver services to client devices in the network. The clients in the network communicate with other clients through the server. Unlike the P2P model, clients in a client/server architecture don’t share their resources. This architecture type is sometimes called a tiered model because it's designed with multiple levels or tiers.
Network topology
Network topology refers to how the nodes and links in a network are arranged. A network node is a device that can send, receive, store, or forward data. A network link connects nodes and may be either cabled or wireless links.
Understanding topology types provides the basis for building a successful network. There are several topologies but the most common are bus, ring, star, and mesh:
A bus network topology is when every network node is directly connected to a main cable.
In a ring topology , nodes are connected in a loop, so each device has exactly two neighbors. Adjacent pairs are connected directly; nonadjacent pairs are connected indirectly through multiple nodes.
In a star network topology , all nodes are connected to a single, central hub and each node is indirectly connected through that hub.
A mesh topology is defined by overlapping connections between nodes. You can create a full mesh topology, where every node in the network is connected to every other node. You can also create partial mesh topology in which only some nodes are connected to each other and some are connected to the nodes with which they exchange the most data. Full mesh topology can be expensive and time-consuming to run, which is why it's often reserved for networks that require high redundancy. Partial mesh provides less redundancy but is more cost-effective and simpler to run.
Computer network security protects the integrity of information that is contained by a network and controls who access that information. Network security policies balance the need to provide service to users with the need to control access to information.
There are many entry points to a network. These entry points include the hardware and software that comprise the network itself as well as the devices used to access the network, like computers, smartphones, and tablets. Because of these entry points, network security requires using several defense methods. Defenses may include firewalls—devices that monitor network traffic and prevent access to parts of the network based on security rules.
Processes for authenticating users with user IDs and passwords provide another layer of security. Security includes isolating network data so that proprietary or personal information is harder to access than less critical information. Other network security measures include ensuring hardware and software updates and patches are performed regularly. This educates network users about their role in security processes, and staying aware of external threats executed by hackers and other malicious actors. Network threats constantly evolve, which makes network security a never-ending process.
The use of public cloud also requires updates to security procedures to ensure continued safety and access. A secure cloud demands a secure underlying network.
Read about the top five considerations for securing the public cloud.
As noted above, a mesh network is a topology type in which the nodes of a computer network connect to as many other nodes as possible. In this topology, nodes cooperate to efficiently route data to its destination. This topology provides greater fault tolerance because if one node fails, there are many other nodes that can transmit data. Mesh networks self-configure and self-organize, searching for the fastest, most reliable path on which to send information.
Type of mesh networks:
There are two types of mesh networks—full mesh and partial mesh.
- In a full mesh topology , every network node connects to every other network node, providing the highest level of fault tolerance. However, it costs more to run. In a partial mesh topology, only some nodes connect, typically those that exchange data most frequently.
- A wireless mesh network may consist of tens to hundreds of nodes. This type of network connects to users over access points spread across a large area.
Load balancers efficiently distribute tasks, workloads, and network traffic across available servers. Think of load balancers like air traffic control at an airport. The load balancer observes all traffic coming into a network and directs it toward the router or server that is best equipped to manage it. The objectives of load balancing are to avoid resource overload, optimize available resources, improve response times, and maximize throughput.
For a complete overview of load balancers, see Load Balancing: A Complete Guide .
A content delivery network (CDN) is a distributed server network that delivers temporarily stored, or cached, copies of website content to users based on the user’s geographic location. A CDN stores this content in distributed locations and serves it to users as a way to reduce the distance between your website visitors and your website server. Having cached content closer to your end users allows you to serve content faster and helps websites better reach a global audience. CDNs protect against traffic surges, reduce latency, decrease bandwidth consumption, accelerate load times. And lessen the impact of hacks and attacks by introducing a layer between the end user and your website infrastructure.
Live-streaming media, on-demand media, gaming companies, application creators, e-commerce sites—as digital consumption increases, more content owners turn to CDNs to better serve content consumers.
Avoid network traffic jams and decrease latency by keeping your data closer to your users with Akamai’s content delivery network on IBM Cloud®.
IBM Cloud® Load Balancers enable you to balance traffic among servers to improve uptime and performance.
Gain more control of your cloud infrastructure and protect your servers and network.
IBM Hybrid Cloud Mesh offers simple, secure, and predictable application-centric connectivity.
Learn how load balancing optimizes website and application performance.
An introduction to content delivery networks and how they improve customer satisfaction by optimizing website and mobile app performance.
Answers to pressing questions from IT architects on public cloud security.
IBM NS1 Connect provides fast, secure connections to users anywhere in the world with premium DNS and advanced, customizable traffic steering. NS1 Connect’s always-on, API-first architecture enables your IT teams to more efficiently monitor networks, deploy changes and conduct routine maintenance.
Research Topics & Ideas: CompSci & IT
50+ Computer Science Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a computer science-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software engineering.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the CompSci domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: CompSci Research Topics
- Algorithms & data structures
- Artificial intelligence ( AI )
- Computer networking
- Database systems
- Human-computer interaction
- Information security (IS)
- Software engineering
- Examples of CompSci dissertation & theses
Topics/Ideas: Algorithms & Data Structures
- An analysis of neural network algorithms’ accuracy for processing consumer purchase patterns
- A systematic review of the impact of graph algorithms on data analysis and discovery in social media network analysis
- An evaluation of machine learning algorithms used for recommender systems in streaming services
- A review of approximation algorithm approaches for solving NP-hard problems
- An analysis of parallel algorithms for high-performance computing of genomic data
- The influence of data structures on optimal algorithm design and performance in Fintech
- A Survey of algorithms applied in internet of things (IoT) systems in supply-chain management
- A comparison of streaming algorithm performance for the detection of elephant flows
- A systematic review and evaluation of machine learning algorithms used in facial pattern recognition
- Exploring the performance of a decision tree-based approach for optimizing stock purchase decisions
- Assessing the importance of complete and representative training datasets in Agricultural machine learning based decision making.
- A Comparison of Deep learning algorithms performance for structured and unstructured datasets with “rare cases”
- A systematic review of noise reduction best practices for machine learning algorithms in geoinformatics.
- Exploring the feasibility of applying information theory to feature extraction in retail datasets.
- Assessing the use case of neural network algorithms for image analysis in biodiversity assessment
Topics & Ideas: Artificial Intelligence (AI)
- Applying deep learning algorithms for speech recognition in speech-impaired children
- A review of the impact of artificial intelligence on decision-making processes in stock valuation
- An evaluation of reinforcement learning algorithms used in the production of video games
- An exploration of key developments in natural language processing and how they impacted the evolution of Chabots.
- An analysis of the ethical and social implications of artificial intelligence-based automated marking
- The influence of large-scale GIS datasets on artificial intelligence and machine learning developments
- An examination of the use of artificial intelligence in orthopaedic surgery
- The impact of explainable artificial intelligence (XAI) on transparency and trust in supply chain management
- An evaluation of the role of artificial intelligence in financial forecasting and risk management in cryptocurrency
- A meta-analysis of deep learning algorithm performance in predicting and cyber attacks in schools

Topics & Ideas: Networking
- An analysis of the impact of 5G technology on internet penetration in rural Tanzania
- Assessing the role of software-defined networking (SDN) in modern cloud-based computing
- A critical analysis of network security and privacy concerns associated with Industry 4.0 investment in healthcare.
- Exploring the influence of cloud computing on security risks in fintech.
- An examination of the use of network function virtualization (NFV) in telecom networks in Southern America
- Assessing the impact of edge computing on network architecture and design in IoT-based manufacturing
- An evaluation of the challenges and opportunities in 6G wireless network adoption
- The role of network congestion control algorithms in improving network performance on streaming platforms
- An analysis of network coding-based approaches for data security
- Assessing the impact of network topology on network performance and reliability in IoT-based workspaces

Topics & Ideas: Database Systems
- An analysis of big data management systems and technologies used in B2B marketing
- The impact of NoSQL databases on data management and analysis in smart cities
- An evaluation of the security and privacy concerns of cloud-based databases in financial organisations
- Exploring the role of data warehousing and business intelligence in global consultancies
- An analysis of the use of graph databases for data modelling and analysis in recommendation systems
- The influence of the Internet of Things (IoT) on database design and management in the retail grocery industry
- An examination of the challenges and opportunities of distributed databases in supply chain management
- Assessing the impact of data compression algorithms on database performance and scalability in cloud computing
- An evaluation of the use of in-memory databases for real-time data processing in patient monitoring
- Comparing the effects of database tuning and optimization approaches in improving database performance and efficiency in omnichannel retailing
Topics & Ideas: Human-Computer Interaction
- An analysis of the impact of mobile technology on human-computer interaction prevalence in adolescent men
- An exploration of how artificial intelligence is changing human-computer interaction patterns in children
- An evaluation of the usability and accessibility of web-based systems for CRM in the fast fashion retail sector
- Assessing the influence of virtual and augmented reality on consumer purchasing patterns
- An examination of the use of gesture-based interfaces in architecture
- Exploring the impact of ease of use in wearable technology on geriatric user
- Evaluating the ramifications of gamification in the Metaverse
- A systematic review of user experience (UX) design advances associated with Augmented Reality
- A comparison of natural language processing algorithms automation of customer response Comparing end-user perceptions of natural language processing algorithms for automated customer response
- Analysing the impact of voice-based interfaces on purchase practices in the fast food industry

Topics & Ideas: Information Security
- A bibliometric review of current trends in cryptography for secure communication
- An analysis of secure multi-party computation protocols and their applications in cloud-based computing
- An investigation of the security of blockchain technology in patient health record tracking
- A comparative study of symmetric and asymmetric encryption algorithms for instant text messaging
- A systematic review of secure data storage solutions used for cloud computing in the fintech industry
- An analysis of intrusion detection and prevention systems used in the healthcare sector
- Assessing security best practices for IoT devices in political offices
- An investigation into the role social media played in shifting regulations related to privacy and the protection of personal data
- A comparative study of digital signature schemes adoption in property transfers
- An assessment of the security of secure wireless communication systems used in tertiary institutions
Topics & Ideas: Software Engineering
- A study of agile software development methodologies and their impact on project success in pharmacology
- Investigating the impacts of software refactoring techniques and tools in blockchain-based developments
- A study of the impact of DevOps practices on software development and delivery in the healthcare sector
- An analysis of software architecture patterns and their impact on the maintainability and scalability of cloud-based offerings
- A study of the impact of artificial intelligence and machine learning on software engineering practices in the education sector
- An investigation of software testing techniques and methodologies for subscription-based offerings
- A review of software security practices and techniques for protecting against phishing attacks from social media
- An analysis of the impact of cloud computing on the rate of software development and deployment in the manufacturing sector
- Exploring the impact of software development outsourcing on project success in multinational contexts
- An investigation into the effect of poor software documentation on app success in the retail sector
CompSci & IT Dissertations/Theses
While the ideas we’ve presented above are a decent starting point for finding a CompSci-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various CompSci-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- An array-based optimization framework for query processing and data analytics (Chen, 2021)
- Dynamic Object Partitioning and replication for cooperative cache (Asad, 2021)
- Embedding constructural documentation in unit tests (Nassif, 2019)
- PLASA | Programming Language for Synchronous Agents (Kilaru, 2019)
- Healthcare Data Authentication using Deep Neural Network (Sekar, 2020)
- Virtual Reality System for Planetary Surface Visualization and Analysis (Quach, 2019)
- Artificial neural networks to predict share prices on the Johannesburg stock exchange (Pyon, 2021)
- Predicting household poverty with machine learning methods: the case of Malawi (Chinyama, 2022)
- Investigating user experience and bias mitigation of the multi-modal retrieval of historical data (Singh, 2021)
- Detection of HTTPS malware traffic without decryption (Nyathi, 2022)
- Redefining privacy: case study of smart health applications (Al-Zyoud, 2019)
- A state-based approach to context modeling and computing (Yue, 2019)
- A Novel Cooperative Intrusion Detection System for Mobile Ad Hoc Networks (Solomon, 2019)
- HRSB-Tree for Spatio-Temporal Aggregates over Moving Regions (Paduri, 2019)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Fast-Track Your Research Topic
If you’re still feeling a bit unsure about how to find a research topic for your Computer Science dissertation or research project, check out our Topic Kickstarter service.
You Might Also Like:

Investigating the impacts of software refactoring techniques and tools in blockchain-based developments.
Steps on getting this project topic
I want to work with this topic, am requesting materials to guide.
Information Technology -MSc program
It’s really interesting but how can I have access to the materials to guide me through my work?
That’s my problem also.
Investigating the impacts of software refactoring techniques and tools in blockchain-based developments is in my favour. May i get the proper material about that ?
BLOCKCHAIN TECHNOLOGY
I NEED TOPIC
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
share this!
April 26, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
Researchers propose framework for future network systems
by Engineering
In a new study published in Engineering , Wu Jiangxing's research team unveils a theoretical framework that could revolutionize the landscape of network systems and architectures.
The paper titled "Theoretical Framework for a Polymorphic Network Environment," addresses a fundamental challenge in network design—achieving global scalability while accommodating the diverse needs of evolving services.
For decades, the quest for an ideal network capable of seamlessly scaling across various dimensions has remained elusive. The team, however, has identified a critical barrier known as the "impossible service-level agreement (S), multiplexity (M), and variousness (V) triangle" dilemma, which highlights the inherent limitations of traditional unimorphic network systems.
These systems struggle to adapt to the growing complexity of services and application scenarios while maintaining global scalability throughout the network's life cycle.
To overcome this challenge, the researchers propose a paradigm shift in network development—an approach they term the polymorphic network environment (PNE). At the core of this framework lies the separation of application network systems from the underlying infrastructure environment.
By leveraging core technologies such as network elementization and dynamic resource aggregation, the PNE enables the creation of a versatile "network of networks" capable of accommodating diverse service requirements.
Through extensive theoretical analysis and environment testing, the team demonstrates the viability of the PNE model. Results indicate that the framework not only supports multiple application network modalities simultaneously but also aligns with technical and economic constraints, thus paving the way for scalable and adaptable network architectures.
This study challenges the conventional wisdom surrounding network design and offers a promising path towards achieving the elusive goal of an ideal network system. The PNE not only addresses the limitations of current approaches but also lays the foundation for a more flexible and resilient network infrastructure.
Looking ahead, the team aims to further refine the PNE framework and explore key techniques such as elemental extraction and flexible resource scheduling. By doing so, they seek to unlock the full potential of polymorphic network systems and usher in a new era of connectivity and innovation.
The publication of this paper marks a significant milestone in the field of network engineering, with implications that extend far beyond academia. As society becomes increasingly reliant on interconnected systems, the development of scalable and adaptable networks is more crucial than ever. With the PNE, researchers are one step closer to realizing this vision.
Explore further
Feedback to editors

A strategy to boost the efficiency of perovskite/organic solar cells
11 hours ago
Computer scientists unveil novel attacks on cybersecurity
Apr 27, 2024

Proof of concept study shows path to easier recycling of solar modules
Apr 26, 2024

New circuit boards can be repeatedly recycled

Researchers develop an automated benchmark for language-based task planners

Built-in bionic computing: Researchers develop method to control pneumatic artificial muscles

Custom-made catalyst leads to longer-lasting and more sustainable green hydrogen production

Researchers outline path forward for tandem solar cells

Researcher develop high-performance amorphous p-type oxide semiconductor

Scientists create new atomic clock that is both ultra-precise and sturdy
Related stories.

Technological breakthrough may be key to overcoming current 5G network limitations
Aug 8, 2023

National roaming can increase resilience of Dutch mobile networks
Apr 17, 2024

Building a template for the future 6G network
Oct 1, 2021
A graphical diagnostics tool for high-speed railway internet connectivity
Nov 27, 2023

Researchers offer future 6G network concept
Dec 29, 2021

Researchers use AI to make mobile networks more efficient
Oct 31, 2023
Recommended for you

Study explores why human-inspired machines can be perceived as eerie
Apr 25, 2024

Adobe's VideoGigaGAN uses AI to make blurry videos sharp and clear

Engineers uncover key to efficient and stable organic solar cells
Let us know if there is a problem with our content.
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Tech Xplore in any form.
Your Privacy
This site uses cookies to assist with navigation, analyse your use of our services, collect data for ads personalisation and provide content from third parties. By using our site, you acknowledge that you have read and understand our Privacy Policy and Terms of Use .
E-mail newsletter
- Skip to main content
- Skip to search
- Skip to footer
Products and Services

Cisco certifications
Get that career in IT. Earn that promotion. Stand out in your field.
A little over 30 years ago, in a routing and switching room at Cisco, a dream was born...
Today, Cisco certifications are the gold standard in IT training. We’ve certified more than 4 million people so far. In the next 30 years, we aim to train over 10 million more people in our pledge to close the IT skills gap and reshape diversity in the tech industry.
of organizations surveyed use technical certifications to make hiring decisions.
of employers believe IT certifications are a reliable predictor of a successful employee.
of employers associate IT certification holders with increased quality and value of work contribution.
Networking Academy is a great start for students
Learn from anywhere, anytime with self-paced courses or take instructor-led courses from academies across the globe. Earn digital badges and prepare for industry-recognized certifications in topics like cybersecurity, networking, and Python.
Certifications for all levels and technologies
Popular certifications.

Cisco Certified Networking Associate (CCNA)
The network is the heartbeat of the digital future, and companies need trusted specialists to manage their systems. With a CCNA certification, you could be the right person for the job.

CyberOps Associate
The cybersecurity field is booming, and so is the IT job market. Be head and shoulders above other job-seekers with a CyberOps certification.

Professional
Cisco Certified DevNet Professional
Prove you have the skills to develop and maintain applications built on Cisco platforms.

Cisco Certified Networking Professional (CCNP) Enterprise
Prepare to configure, troubleshoot, and manage the networks of the largest companies in the world.
Collaboration
Power the dynamic global workforce.
Meet the challenges of today and tomorrow to build and maintain secure infrastructures that boost productivity for a worldwide workforce.

Cisco Certified Network Professional (CCNP) Collaboration
Proves you have what it takes to build the solutions that empower our evolving collaboration technologies.

Cisco Certified Internetwork Expert (CCIE) Collaboration
Become a technical leader by validating your end-to-end lifecycle skills in complex collaboration solutions.
Protect the digital landscape
As the cybersecurity field grows, companies of all sizes need experts to design and run their security operations. From attack prevention to daily threat monitoring, there’s a role for every career goal. Become your organization’s greatest security asset — we’ll show you how.

Cisco Certified Support Technician (CCST) Cybersecurity
A great place to start if you’re new to the security field. This certification validates your skills and knowledge of entry-level concepts.
Cisco Certified CyberOps Associate
Tests the day-to-day, tactical knowledge and skills Security Operations Center teams need to detect and respond to cybersecurity threats.

Cisco Certified CyberOps Professional
Elevates your skills to address nuanced security challenges.
Data Center
Drive the data tech transformation.
Technology advances generate more data than ever before. Optimize the applications and infrastructure that connect what matters most to any business — its people, systems, and data.

Cisco Certified Network Professional (CCNP) Data Center
Proves that you can run the data centers of today and tomorrow. Core technologies include network, computing, storage, automation, and security.

Cisco Certified Internetwork Expert (CCIE) Data Center
Distinguishes you as a leader in data center technologies. This certification validates your skills in the end-to-end lifecycle for the most complex data center network infrastructures.
Get your license to design as a leader in complex network solutions
Show the world you’ve got what it takes be an elite designer of IT solutions.

Cisco Certified Design Expert (CCDE)
Be armed with the breadth of knowledge and skills to navigate the waters of complex IT projects in network architecture and design.
Harness the power of applications and automation
Now more than ever, streamlining network operations is a must for any business. Become a vital member of today’s IT with expertise in all phases of network automation.

Cisco Certified DevNet Associate
Validates that you can automate workflows across network, security, collaboration, and computing infrastructures.
Showcases the skills you need to develop and maintain applications built on Cisco platforms, securely and at scale.

Cisco Certified DevNet Expert
Validates your expert knowledge and proficiency in network automation, programmability, and secure automation tools.
Manage the world’s largest networks
The only constant in IT is change — and enterprise network technologies are evolving rapidly. Stay ahead of the curve by proving your skills in maintaining and managing today’s most complex networks.

Cisco Certified Support Technician (CCST) Networking
Validates your skills and knowledge of entry-level networking concepts and topics.
Cisco Certified Network Associate (CCNA)
Demonstrates skills and knowledge in a broad range of fundamentals for the latest networking technologies, software development skills, and job roles.
Cisco Certified Network Professional (CCNP) Enterprise
Tests your skills in the ever-changing landscape of enterprise network technologies.

Cisco Certified Internetwork Expert (CCIE) Enterprise Infrastructure
Validates your ability to maximize the potential of enterprise infrastructure solutions.
Cisco Certified Internetwork Expert (CCIE) Enterprise Wireless
Proves your ability to maximize the potential of enterprise wireless solutions.
It’s time to expand your multicloud expertise
Show the world you have what it takes to deploy, secure, manage, and monitor complex public and private multicloud networks.
Cisco Certified Specialist - Enterprise Network Assurance
Demonstrate your knowledge of network assurance design and implementation leveraging platforms and architecture, data collection, implementation, data analysis, insights and alerts.
Cisco Certified Specialist - Cloud Connectivity
Certify that you can design and implement cloud connectivity, including architecture models, IPsec, and Software-Defined Wide Area Network (SD-WAN) solutions.
Cisco Certified Specialist - Secure Cloud Access
Certify your knowledge of designing and implementing secure architectures, users and devices, networks, applications, data, and more.
Build security and resilience
Secure and protect the on-premises and cloud network infrastructures that organizations rely on.

Cisco Certified Network Professional (CCNP) Security
Proves you can step into any security environment and protect the networks and data that clients rely on.

Cisco Certified Internetwork Expert (CCIE) Security
Proves your skills with complex security solutions.
Service Provider
Propel next-gen networking solutions.
Revolutionize IT infrastructure for businesses worldwide. Stay ahead of emerging technologies, and master strategic network design skills to provide unparalleled services to clients.

Cisco Certified Network Professional (CCNP) Service Provider
Proves your ability to configure, verify, and optimize next-gen service provider IP network infrastructures.

Cisco Certified Internetwork Expert (CCIE) Service Provider
Proves your skills with complex service provider network solutions.
Additional certifications
Consider additional certification possibilities.
Check out these additional training programs to get certified. You might discover your perfect match!
AppDynamics
Whether you’ve been tasked with implementing AppDynamics software or are responsible for setting up a monitoring dashboard, you’re sure to find certifications that align with your role.
Cisco Certified Technician (CCT)
Cisco Certified Technicians have the skills to diagnose, restore, repair, and replace critical Cisco networking and system devices at customer sites. Technicians work closely with the Cisco Technical Assistance Center (TAC) to quickly and efficiently resolve support incidents.
Cisco Customer Experience
Cisco Customer Experience training and exams prepare you for key roles in services or subscription-based organizations. These exams validate your skills in accelerating time to value and ensuring your customers achieve their business goals by implementing, adopting, expanding, and renewing your software and service subscriptions.
Cisco Meraki Solutions
Cisco Meraki Solutions are sweeping the world, with over 2.5 million active networks in more than 190 countries. But who can run these new networks? You can. The Cisco Meraki Solutions Specialist certification validates your ability to design, implement, and operate Meraki technologies.
Land your dream role
Whether you’re interested in servers and hardware, network security, or software development, your dream role is out there - and a certification can help pave the way.
In-demand roles in tech
Network engineer.
Apply a range of technologies to connect, secure, and automate complex networks.
Systems engineer
Be the expert behind any project that optimizes systems for an organization.
CyberOps analyst
Continuously assess network security and look for ways to ensure security measures are well-planned and in place.

Showcase your unique skill set
Every professional- and expert-level exam now earns a Specialist certification. Specialist certifications help to showcase your unique skill set by validating your expertise in the areas that matter to you, from Enterprise to DevNet and everything between.
Certification Success Stories
Ccna moved elvin up the career ladder.

"Passing that CCNA exam triggered a chain of events I could never have predicted. First, I was a student, then a teacher, then a Cisco instructor, and I eventually became a Cisco VIP"
Elvin Arias Soto, CloudOps engineer
CCNA, CCDP, CCDA, CCNP, CCIE
Certifications give Kevin instant credibility at work

"People always want to know who they're talking to. They want to know if you’re qualified. Certifications give you instant credibility."
Kevin Brown, CyberOps analyst
CCNA, CyberOps Associate
Ben made a career change with a Cisco certification

"I chose to pursue Cisco certifications because I knew it would put me in the best position to start a career in networking."
Ben Harting, Configuration Engineer
Engage with a vibrant learning community of peers and experts
The Cisco Learning Network Community is more than just an online platform - it’s your global study group. Connect with peers, learn from experts, and access a wealth of resources that empower your learning journey.
- Frontiers in Network Physiology
- Networks in the Cardiovascular System
- Research Topics
Network Physiology: Insights into the Cardiovascular System, Vol II
Total Downloads
Total Views and Downloads
About this Research Topic
This Research Topic is the second volume of the Network Physiology: Insights into the Cardiovascular System collection. Other titles in the Insights in Frontiers in Network Physiology series can be found ...
Keywords : cardiovascular system, network physiology
Important Note : All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements. Frontiers reserves the right to guide an out-of-scope manuscript to a more suitable section or journal at any stage of peer review.
Topic Editors
Topic coordinators, recent articles, submission deadlines, participating journals.
Manuscripts can be submitted to this Research Topic via the following journals:
total views
- Demographics
No records found
total views article views downloads topic views
Top countries
Top referring sites, about frontiers research topics.
With their unique mixes of varied contributions from Original Research to Review Articles, Research Topics unify the most influential researchers, the latest key findings and historical advances in a hot research area! Find out more on how to host your own Frontiers Research Topic or contribute to one as an author.
- Visit the University of Nebraska–Lincoln
- Apply to the University of Nebraska–Lincoln
- Give to the University of Nebraska–Lincoln
Search Form
Nebraska on-farm research network releases 2023 research results publication.

The Nebraska On-Farm Research Network (NOFRN) is placing research results into producers’ hands through its 2023 Research Results book — a publication that highlights findings from approximately 80 on-farm research studies conducted in Nebraska during the 2023 growing season.
"The research results in this book equip producers with the tools to harness local insights, enabling them to make well-informed decisions that optimize both productivity and profitability on their own operation" said Taylor Lexow, NOFRN Project Coordinator.
Studies in the 2023 Research Results book cover various topics, including crop production, fertility and soil management, non-traditional products, cover crops, crop protection and equipment. The 2023 publication, along with publications from previous years, is now available on the NOFRN’s website.
With planting season upon us, now is the time to dig deeper into agricultural practices and determine what best fits the needs of every operation. Download a copy of the 2023 Research Results book today from the NOFRN site .
For more information about the 2023 Research Results book or the NOFRN, please contact Taylor Lexow at 402-245-2222 .
About the NOFRN
The Nebraska On-Farm Research Network (NOFRN) is a program of Nebraska Extension that partners with farmers to evaluate agricultural practices and provide innovative solutions that impact farm productivity, profitability and sustainability. It is supported by the Nebraska Corn Board, the Nebraska Corn Growers Association, the Nebraska Soybean Checkoff and the Nebraska Dry Bean Commission. To learn more about the NOFRN, visit its website .
2023 Research Results Book
Online Master of Science in Agronomy
With a focus on industry applications and research, the online program is designed with maximum flexibility for today's working professionals.

Network model unifies recency and central tendency biases
Researchers uncover interrelation between short-term history and contraction bias.
Neuroscientists have revealed that recency bias in working memory naturally leads to central tendency bias, the phenomenon where people's (and animals') judgements are biased towards the average of previous observations. Their findings may hint at why the phenomenon is so ubiquitous.
Researchers in the Akrami Lab at the Sainsbury Wellcome Centre at UCL and the Clopath Lab at Imperial College London developed a network model with a working memory module and another accounting for sensory histories. The study, published in eLife , describes how the model shows neural circuits can give rise to both recency and central tendency biases at the same time through a single mechanism.
"Psychologists first observed the central tendency bias over a century ago, but it was assumed to be a separate phenomenon to recency. Our results imply that these two biases are more related than previously thought," said Vezha Boboeva, Senior Research Fellow at the Sainsbury Wellcome Centre and first author on the paper.
Central tendency bias, also known as contraction bias, is a ubiquitous phenomenon. Imagine you are shown a bar of a given length and asked to reproduce that same bar, recalled from your memory. What we tend to do is to misremember the length, based on the bar's size, recalling longer bars as shorter and shorter bars as longer. Therefore, we judge the length of the bar as closer to the mean of the range than it is in reality. The phenomenon also occurs in other animals, including non-human primates and rodents, and happens with other modalities too, such as sound amplitudes and frequencies. This bias is believed to be a brain strategy for processing the statistical patterns of sensory information, formulated through Bayesian computation.
Recency bias, also known as short-term history bias, occurs when you fail to remember a given stimulus because the memory from the previous stimulus is still lingering in your mind.
To understand the neural processes that underpin both central tendency and recency biases, neuroscientists at SWC and Imperial College London studied the phenomena in a neural network model, highly inspired by prior results from rodents and human working memory experiments.
"My previous postdoctoral research showed that deactivating the posterior parietal cortex (PPC) attenuated contraction bias in rats performing a working memory task. We also saw that biases due to lingering memories of previous trials were reduced when PPC was deactivated, suggesting that these two mechanisms may be linked to each other," explained Athena Akrami, Group Leader at SWC and corresponding author on the paper.
Building on this research, Boboeva and team developed a network model that replicated the previous experimental findings. In the model, short-term history effects occur due to inputs from the PPC that has a slower integration timescale as well as firing rate adaptation.
"The model shows that once you make working memory errors because of such lingering memories, contraction bias emerges naturally, without the need to make any other assumption about the average of the sensory history," explained Boboeva.
Importantly, this new unifying model made specific predictions on how sensory statistics affect performance. The researchers used online tools to test and verify these predictions by running psychophysics experiments with human participants. The next steps are to test the model predictions about the neural dynamics by reanalysing the existing datasets and collecting new neural datal.
This research was funded by BBSRC BB/N013956/1, BB/N019008/1, Wellcome Trust 200790/Z/16/Z, Simons Foundation 564408, EPSRC EP/R035806/1, Gatsby Charitable Foundation GAT3755 and Wellcome Trust 219627/Z/19/Z.
- Brain-Computer Interfaces
- Intelligence
- Developmental Biology
- Animal Learning and Intelligence
- Behavioral Science
- Confirmation bias
- Cognitive bias
- Double blind
- Social cognition
- Anchoring bias in decision-making
- List of cognitive biases
- Memory-prediction framework
- Domestication
Story Source:
Materials provided by Sainsbury Wellcome Centre . Note: Content may be edited for style and length.
Journal Reference :
- Vezha Boboeva, Alberto Pezzotta, Claudia Clopath, Athena Akrami. Unifying network model links recency and central tendency biases in working memory . eLife , 2024; 12 DOI: 10.7554/eLife.86725.3
Cite This Page :
Explore More
- Mice Given Mouse-Rat Brains Can Smell Again
- New Circuit Boards Can Be Repeatedly Recycled
- Collisions of Neutron Stars and Black Holes
- Advance in Heart Regenerative Therapy
- Bioluminescence in Animals 540 Million Years Ago
- Profound Link Between Diet and Brain Health
- Loneliness Runs Deep Among Parents
- Food in Sight? The Liver Is Ready!
- Acid Reflux Drugs and Risk of Migraine
- Do Cells Have a Hidden Communication System?
Trending Topics
Strange & offbeat.

IMAGES
VIDEO
COMMENTS
This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network ...
Generally, networking is defined as the computing devices that exchange information and share ideas among individuals or groups of devices or users using either wired or wireless connection. Let us see the latest topics in networking, Latest Research Topics in Networking. Secure and control sensitive data also in cloud environment (any)
A Better Approach to Networking. by. Christie Hunter Arscott. November 04, 2022. PM Images/Getty Images. Summary. Meeting strangers — especially in the context of work — is uncomfortable for ...
Ghost-USB-Honeypot project. This effort, focused on nixing malware like Flame that spreads from computer to computer via USB storage drives, got its start based on research from Sebastian Poeplau ...
2022 Computer Networking Dissertation Topics. Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT. Objectives: To evaluate the factors affecting the network security of IoT devices. To determine the methods for increasing data integrity in M2M communication against physical tampering ...
Thus, inter-networking and uncertainty management are important challenges of emerging networking that deserve attention from the research community. We describe research that touch on both topics. First, we consider a model of data-optical inter-networking, where routes connecting end-points in data domains are concatenation of segments in the ...
Our research combines building and deploying novel networking systems at unprecedented scale, with recent work focusing on fundamental questions around data center architecture, cloud virtual networking, and wide-area network interconnects. We helped pioneer the use of Software Defined Networking, the application of ML to networking, and the ...
6. Eytan Modiano, "Random Algorithms for Scheduling Multicast Traffic in WDM Broadcast-and-Select Networks," IEEE Transactions on Networking, July, 1999. 5. Eytan Modiano and Richard Barry, "Architectural Considerations in the Design of WDM-based Optical Access Networks," Computer Networks, February 1999.
Systems and Networking. Systems and Networking is a broad and diverse area of computing research which spans areas including: systems, networks and distributed systems, programming languages and software engineering, compilers, databases and data science, security and cryptography, and mobile and wireless systems.
B5G & 6G Oriented Optical Wireless Communication and Networking Techniques. An innovative journal that explores the critical branches of contemporary telecommunications in our hyper-connected world, from the physical layer to cross-layer and networking design, performance ...
Jennifer R. Grandis, University of California, San Francisco. By surveying over 100 people in academic medicine, a researcher found that women are consistently excluded from important networking ...
Social Media Research Topics are as follows: The effects of social media on mental health. The role of social media in political polarization. The impact of social media on relationships. The use of social media by businesses for marketing. The effects of social media on body image and self-esteem.
Nonetheless, networking is a crucial research skill for students and early career researchers, who likely find it the most intimidating. There are several benefits to research networking. It is a great way to start new collaborations, share research, learn about funding opportunities, and connect with journal editors and reviewers 2. Networking ...
The 4 Most Important Networking Trends in 2020 and Beyond. In today's digital world, networking technology is everything. It's what makes the internet possible. It's how businesses support sprawling multinational footprints. It's even stitching together the appliances in our homes into one, smart, convenient fabric.
This course is typically offered in the spring quarter. Topics Include. Architectural principles: naming, addressing, routing; congestion control, traffic management, QoS. Wireless and mobility. Overlay networks and virtualization. Network security. Switching and routing. Content distribution. Proposals for future Internet structures.
Focus on learning. Adopt a "promotion mindset" and concentrate on the positives, and you're more likely to perceive networking as an opportunity for discovery rather than a chore. Identify ...
About this course. 'Networking for Researchers' covers the key elements needed to acquire or perfect effective professional networking skills for scientific researchers. In this course you will discover how building a professional network will benefit your research and career, and learn the skills to build and maintain networking ...
Join ResearchGate to discover and stay up-to-date with the latest research from leading experts in Computer Networking and many other scientific topics. Join for free ResearchGate iOS App
Advanced Topic A Renaissance of Network Research and Data. Since the 1960s, network analysis has blossomed. New research and methods have flourished and social networking has developed a new prominence in mainstream culture. Despite early challenges, in the past several decades a healthy and growing subfield has reemerged around social network ...
Research by the Lehigh@NasdaqCenter, a partnership between Lehigh University and the Nasdaq Entrepreneurial Center, identified make-or-break factors for developing networking skills.
TCP termination process. There's a lot more to TCP Protocol. Research more to know more about it. 6. UDP ( User Datagram Protocol ): UDP is a Transport Layer Protocol that works on top of IP.
What is networking? A computer network comprises two or more computers that are connected—either by cables (wired) or wifi (wireless)—with the purpose of transmitting, exchanging, or sharing data and resources. You build a computer network by using hardware (for example, routers, switches, access points, and cables) and software (for ...
If you've landed on this post, chances are you're looking for a computer science-related research topic, but aren't sure where to start. Here, we'll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software ...
Network hardware and physical appliances, such as routers, switches, gateways, hubs and bridges, serve as the vital foundation of network infrastructure. Common network protocols and more emergent network software also play major roles in any architecture. While networking has shifted to software-centric principles, see how traditional network ...
The paper titled "Theoretical Framework for a Polymorphic Network Environment," addresses a fundamental challenge in network design—achieving global scalability while accommodating the diverse needs of evolving services.. For decades, the quest for an ideal network capable of seamlessly scaling across various dimensions has remained elusive.
(SACRAMENTO) The Food and Drug Administration announced Tuesday that samples of pasteurized milk taken from grocery store shelves had tested positive for bird flu, also known as Highly Pathogenic Avian Influenza (HPAI) or H5N1.On Thursday, the agency announced that one in five milk samples nationwide showed genetic traces of the virus. Milk samples from areas with infected herds were more ...
Earn digital badges and prepare for industry-recognized certifications in topics like cybersecurity, networking, and Python. Visit Cisco Networking Academy. Certifications for all levels and technologies Popular certifications ... The Cisco Learning Network Community is more than just an online platform - it's your global study group. Connect ...
This Research Topic is the second volume of the Network Physiology: Insights into the Cardiovascular System collection. Other titles in the Insights in Frontiers in Network Physiology series can be found here.We are now entering the third decade of the 21st Century, and, especially in the last years, the achievements made by scientists have been exceptional, leading to major advancements in ...
Studies in the 2023 Research Results book cover various topics, including crop production, fertility and soil management, non-traditional products, cover crops, crop protection and equipment. ... The Nebraska On-Farm Research Network (NOFRN) is a program of Nebraska Extension that partners with farmers to evaluate agricultural practices and ...
Building on this research, Boboeva and team developed a network model that replicated the previous experimental findings. In the model, short-term history effects occur due to inputs from the PPC ...