For enquiries call:
+1-469-442-0620


10 Current Database Research Topic Ideas in 2024
Home Blog Database 10 Current Database Research Topic Ideas in 2024
As we head towards the second half of 2024, the world of technology evolves at a rapid pace. With the rise of AI and blockchain, the demand for data, its management and the need for security increases rapidly. A logical consequence of these changes is the way fields like database security research topics and DBMS research have come up as the need of the hour.
With new technologies and techniques emerging day-by-day, staying up-to-date with the latest trends in database research topics is crucial. Whether you are a student, researcher, or industry professional, we recommend taking our Database Certification courses to stay current with the latest research topics in DBMS.
In this blog post, we will introduce you to 10 current database research topic ideas that are likely to be at the forefront of the field in 2024. From blockchain-based database systems to real-time data processing with in-memory databases, these topics offer a glimpse into the exciting future of database research.
So, get ready to dive into the exciting world of databases and discover the latest developments in database research topics of 2024!
Blurring the Lines between Blockchains and Database Systems
The intersection of blockchain technology and database systems offers fertile new grounds to anyone interested in database research.
As blockchain gains popularity, many thesis topics in DBMS[1] are exploring ways to integrate both fields. This research will yield innovative solutions for data management. Here are 3 ways in which these two technologies are being combined to create powerful new solutions:
Immutable Databases: By leveraging blockchain technology, it’s possible to create databases to be immutable. Once data has been added to such a database, it cannot be modified or deleted. This is particularly useful in situations where data integrity is critical, such as in financial transactions or supply chain management.
Decentralized Databases: Blockchain technology enables the creation of decentralized databases. Here data is stored on a distributed network of computers rather than in a central location. This can help to improve data security and reduce the risk of data loss or corruption.
Smart Contracts: Smart contracts are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. By leveraging blockchain technology, it is possible to create smart contracts that are stored and executed on a decentralized database, making it possible to automate a wide range of business processes.
Childhood Obesity: Data Management
Childhood obesity is a growing public health concern, with rates of obesity among children and adolescents rising around the world. To address this issue, it’s crucial to have access to comprehensive data on childhood obesity. Analyzing information on prevalence, risk factors, and interventions is a popular research topic in DBMS these days.
Effective data management is essential for ensuring that this information is collected, stored, and analyzed in a way that is useful and actionable. This is one of the hottest DBMS research paper topics. In this section, we will explore the topic of childhood obesity data management.
A key challenge to childhood obesity data management is ensuring data consistency. This is difficult as various organizations have varied methods for measuring and defining obesity. For example:
Some may use body mass index (BMI) as a measure of obesity.
Others may use waist circumference or skinfold thickness. Another challenge is ensuring data security and preventing unauthorized access. To protect the privacy and confidentiality of individuals, it is important to ensure appropriate safeguards are in place. This calls for database security research and appropriate application.
Application of Computer Database Technology in Marketing
Leveraging data and analytics allows businesses to gain a competitive advantage in this digitized world today. With the rising demand for data, the use of computer databases in marketing has gained prominence.
The application of database capabilities in marketing has really come into its own as one of the most popular and latest research topics in DBMS[2]. In this section, we will explore how computer database technology is being applied in marketing, and the benefits this research can offer.
Customer Segmentation: Storage and analysis of customer data makes it possible to gain valuable insights. It allows businesses to identify trends in customer behavior, preferences and demographics. This information can be utilized to create highly targeted customer segments. This is how businesses can tailor their marketing efforts to specific groups of customers.
Personalization: Computer databases can be used to store and analyze customer data in real-time. In this way, businesses can personalize their marketing and offers based on individual customer preferences. This can help increase engagement and loyalty among customers, thereby driving greater revenue for businesses.
Predictive Analytics: Advanced analytics techniques such as machine learning and predictive modeling can throw light on patterns in customer behavior. This can even be used to predict their future actions. This information can be used to create more targeted marketing campaigns, and to identify opportunities for cross-selling and upselling.
Database Technology in Sports Competition Information Management
Database technology has revolutionized the way in which sports competition information is managed and analyzed. With the increasing popularity of sports around the world, there is a growing need for effective data management systems that can collect, store, and analyze large volumes of relevant data. Thus, researching database technologies[3] is vital to streamlining operations, improving decision-making, and enhancing the overall quality of events.
Sports organizations can use database technology to collect and manage a wide range of competition-related data such as:
Athlete and team information,
competition schedules and results,
performance metrics, and
spectator feedback.
Collating this data in a distributed database lets sports organizations easily analyze and derive valuable insights. This is emerging as a key DBMS research paper topic.
Database Technology for the Analysis of Spatio-temporal Data
Spatio-temporal data refers to data which has a geographic as well as a temporal component. Meteorological readings, GPS data, and social media content are prime examples of this diverse field. This data can provide valuable insights into patterns and trends across space and time. However, its multidimensional nature makes analysis be super challenging. It’s no surprise that this has become a hot topic for distributed database research[4].
In this section, we will explore how database technology is being used to analyze spatio-temporal data, and the benefits this research offers.
Data Storage and Retrieval: Spatio-temporal data tends to be very high-volume. Advances in database technology are needed to make storage, retrieval and consumption of such information more efficient. A solution to this problem will make such data more available. It will then be easily retrievable and usable by a variety of data analytics tools.
Spatial Indexing: Database technology can create spatial indexes to enable faster queries on spatio-temporal data. This allows analysts to quickly retrieve data for specific geographic locations or areas of interest, and to analyze trends across these areas.
Temporal Querying: Distributed database research can also enable analysts to analyze data over specific time periods. This facilitates the identification of patterns over time. Ultimately, this enhances our understanding of how these patterns evolve over various seasons.
Artificial Intelligence and Database Technology
Artificial intelligence (AI) is another sphere of technology that’s just waiting to be explored. It hints at a wealth of breakthroughs which can change the entire world. It’s unsurprising that the combination of AI with database technology is such a hot topic for database research papers[5] in modern times.
By using AI to analyze data, organizations can identify patterns and relationships that might not be apparent through traditional data analysis methods. In this section, we will explore some of the ways in which AI and database technology are being used together. We’ll also discuss the benefits that this amalgamation can offer.
Predictive Analytics: By analyzing large volumes of organizational and business data, AI can generate predictive models to forecast outcomes. For example, AI can go through customer data stored in a database and predict who is most likely to make a purchase in the near future.
Natural Language Processing: All businesses have huge, untapped wells of valuable information in the form of customer feedback and social media posts. These types of data sources are unstructured, meaning they don’t follow rigid parameters. By using natural language processing (NLP) techniques, AI can extract insights from this data. This helps organizations understand customer sentiment, preferences and needs.
Anomaly Detection: AI can be used to analyze large volumes of data to identify anomalies and outliers. Then, a second round of analysis can be done to pinpoint potential problems or opportunities. For example, AI can analyze sensor data from manufacturing equipment and detect when equipment is operating outside of normal parameters.
Data Collection and Management Techniques of a Qualitative Research Plan
Any qualitative research calls for the collection and management of empirical data. A crucial part of the research process, this step benefits from good database management techniques. Let’s explore some thesis topics in database management systems[6] to ensure the success of a qualitative research plan.
Interviews: This is one of the most common methods of data collection in qualitative research. Interviews can be conducted in person, over the phone, or through video conferencing. A standardized interview guide ensures the data collected is reliable and accurate. Relational databases, with their inherent structure, aid in this process. They are a way to enforce structure onto the interviews’ answers.
Focus Groups: Focus groups involve gathering a small group of people to discuss a particular topic. These generate rich data by allowing participants to share their views in a group setting. It is important to select participants who have knowledge or experience related to the research topic.
Observations: Observations involve observing and recording events in a given setting. These can be conducted openly or covertly, depending on the research objective and setting. To ensure that the data collected is accurate, it is important to develop a detailed observation protocol that outlines what behaviors or events to observe, how to record data, and how to handle ethical issues.
Database Technology in Video Surveillance System
Video surveillance systems are used to monitor and secure public spaces, workplaces, even homes. With the increasing demand for such systems, it’s important to have an efficient and reliable way to store, manage and analyze the data generated. This is where database topics for research paper [7] come in.
By using database technology in video surveillance systems, it is possible to store and manage large amounts of video data efficiently. Database management systems (DBMS) can be used to organize video data in a way that is easily searchable and retrievable. This is particularly important in cases where video footage is needed as evidence in criminal investigations or court cases.
In addition to storage and management, database technology can also be used to analyze video data. For example, machine learning algorithms can be applied to video data to identify patterns and anomalies that may indicate suspicious activity. This can help law enforcement agencies and security personnel to identify and respond to potential threats more quickly and effectively.
Application of Java Technology in Dynamic Web Database Technology
Java technology has proven its flexibility, scalability, and ease of use over the decades. This makes it widely used in the development of dynamic web database applications. In this section, we will explore research topics in DBMS[8] which seek to apply Java technology in databases.
Java Server Pages (JSP): JSP is a Java technology that is used to create dynamic web pages that can interact with databases. It allows developers to embed Java code within HTML scripts, thereby enabling dynamic web pages. These can interact with databases in real-time, and aid in data collection and maintenance.
Java Servlets: Java Servlets are Java classes used to extend the functionality of web servers. They provide a way to handle incoming requests from web browsers and generate dynamic content that can interact with databases.
Java Database Connectivity (JDBC): JDBC is a Java API that provides a standard interface for accessing databases. It allows Java applications to connect to databases. It can SQL queries to enhance, modify or control the backend database. This enables developers to create dynamic web applications.
Online Multi Module Educational Administration System Based on Time Difference Database Technology
With the widespread adoption of remote learning post-COVID, online educational systems are gaining popularity at a rapid pace. A ubiquitous challenge these systems face is managing multiple modules across different time zones. This is one of the latest research topics in database management systems[9].
Time difference database technology is designed to handle time zone differences in online systems. By leveraging this, it’s possible to create a multi-module educational administration system that can handle users from different parts of the world, with different time zones.
This type of system can be especially useful for online universities or other educational institutions that have a global reach:
It makes it possible to schedule classes, assignments and other activities based on the user's time zone, ensuring that everyone can participate in real-time.
In addition to managing time zones, a time difference database system can also help manage student data, course materials, grades, and other important information.
Why is it Important to Study Databases?
Databases are the backbone of many modern technologies and applications, making it essential for professionals in various fields to understand how they work. Whether you're a software developer, data analyst or a business owner, understanding databases is critical to success in today's world. Here are a few reasons why it is important to study databases and more database topics for research paper should be published:
Efficient Data Management
Databases enable the efficient storage, organization, and retrieval of data. By studying databases, you can learn how to design and implement effective data management systems that can help organizations store, analyze, and use data efficiently.
Improved Decision-Making
Data is essential for making informed decisions, and databases provide a reliable source of data for analysis. By understanding databases, you can learn how to retrieve and analyze data to inform business decisions, identify trends, and gain insights.
Career Opportunities
In today's digital age, many career paths require knowledge of databases. By studying databases, you can open up new career opportunities in software development, data analysis, database administration and related fields.
Needless to say, studying databases is essential for anyone who deals with data. Whether you're looking to start a new career or enhance your existing skills, studying databases is a critical step towards success in today's data-driven world.
Final Takeaways
In conclusion, as you are interested in database technology, we hope this blog has given you some insights into the latest research topics in the field. From blockchain to AI, from sports to marketing, there are a plethora of exciting database topics for research papers that will shape the future of database technology.
As technology continues to evolve, it is essential to stay up-to-date with the latest trends in the field of databases. Our curated KnowledgeHut Database Certification Courses will help you stay ahead of the curve and develop new skills.
We hope this blog has inspired you to explore the exciting world of database research in 2024. Stay curious and keep learning!
Frequently Asked Questions (FAQs)
There are several examples of databases, with the five most common ones being:
MySQL : An open-source RDBMS used commonly in web applications.
Microsoft SQL Server : A popular RDBMS used in enterprise environments.
Oracle : A trusted commercial RDBMS famous for its high-scalability and security.
MongoDB : A NoSQL document-oriented database optimized for storing large amounts of unstructured data.
PostgreSQL : An open-source RDBMS offering advanced features like high concurrency and support for multiple data types.
Structured Query Language (SQL) is a high-level language designed to communicate with relational databases. It’s not a database in and of itself. Rather, it’s a language used to create, modify, and retrieve data from relational databases such as MySQL and Oracle.
A primary key is a column (or a set of columns) that uniquely identifies each row in a table. In technical terms, the primary key is a unique identifier of records. It’s used as a reference to establish relationships between various tables.

Spandita Hati
Spandita is a dynamic content writer who holds a master's degree in Forensics but loves to play with words and dabble in digital marketing. Being an avid travel blogger, she values engaging content that attracts, educates and inspires. With extensive experience in SEO tools and technologies, her writing interests are as varied as the articles themselves. In her leisure, she consumes web content and books in equal measure.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Database Batches & Dates
Advancing database security: a comprehensive systematic mapping study of potential challenges
- Original Paper
- Open access
- Published: 17 July 2023
Cite this article
You have full access to this open access article
- Asif Iqbal 1 ,
- Siffat Ullah Khan 1 ,
- Mahmood Niazi 2 , 3 ,
- Mamoona Humayun 4 ,
- Najm Us Sama 5 ,
- Arif Ali Khan 6 &
- Aakash Ahmad 7
2369 Accesses
Explore all metrics
The value of data to a company means that it must be protected. When it comes to safeguarding their local and worldwide databases, businesses face a number of challenges. To systematically review the literature to highlight the difficulties in establishing, implementing, and maintaining secure databases. In order to better understand database system problems, we did a systematic mapping study (SMS). We’ve analyzed 100 research publications from different digital libraries and found 20 issues after adopting inclusion and exclusion criteria. This SMS study aimed to identify the most up-to-date research in database security and the different challenges faced by users/clients using various databases from a software engineering perspective. In total, 20 challenges were identified related to database security. Our results show that “weak authorization system”, “weak access control”, “privacy issues/data leakage”, “lack of NOP security”, and “database attacks” as the most frequently cited critical challenges. Further analyses were performed to show different challenges with respect to different phases of the software development lifecycle, venue of publications, types of database attacks, and active research institutes/universities researching database security. The organizations should implement adequate mitigation strategies to address the identified database challenges. This research will also provide a direction for new research in this area.
Similar content being viewed by others

Database Security: Attacks and Solutions

Reverse Engineering of Database Security Policies

Automated Generation of Multi-tenant Database Systems Based upon System Design Diagrams
Avoid common mistakes on your manuscript.
1 Introduction
Companies’ databases (DBs) are repositories of their most significant and high-value data. As DB utilization has surged, so has the frequency of attacks on these databases. A DB attack is characterized as an event that jeopardizes a resource by altering or destroying vital data [ 1 , 2 ]. The common goal of DB attacks is to access critical information. Illicitly acquiring sensitive data such as credit card details, banking data, and personal identifiers is another prevalent motive behind DB hacks. In our interconnected global society, several technologies provide avenues for DB attacks to exploit vulnerabilities in DB architecture, as per common understanding [ 1 , 3 , 4 ].
Many enterprises confront challenges like data piracy, data replication, and denial of service attacks. To infiltrate a company’s DBs, cybercriminals scout for system vulnerabilities and exploit them using specialized tools [ 5 , 6 ].
The aspect of security should be prioritized during the development of information systems, particularly DBs. In terms of software development, security concerns must be addressed at every stage of the development cycle [ 7 ]. As illustrated in Fig. 1 , security breaches, including the loss of critical data, have become commonplace in recent years. Given the importance of data security to numerous businesses, a range of measures and methodologies are required to safeguard the DB [ 8 , 9 , 10 ]. A secure DB is designed to react appropriately in the event of a potential DB attack [ 11 ].
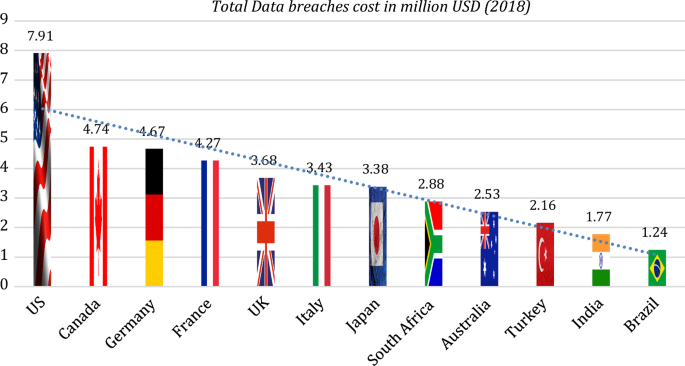
Total data breaches cost in different countries [ 5 ]
In the current world, the impact of cyber-attacks on the commercial landscape must be addressed. To succeed in the globalized environment, businesses must ensure the protection of their vital data. DBs can be safeguarded from unauthorized access [ 12 , 13 , 14 ]. When a DB is outsourced to the cloud, cloud platforms introduce security challenges such as unreliable service providers, malicious cloud employees, data protection, consistency, and scalability. With cloud DBs becoming increasingly susceptible to both external and internal threats, traditional and conventional security measures are insufficient for their protection [ 15 , 16 ].
While extensive work has been done in this field, much of it focuses on a few specific DB platforms or problems, typically explored through standard literature reviews. We aim to provide a more holistic view by conducting a systematic mapping study (SMS) to identify security concerns in DB architecture, development, and maintenance from a software engineering perspective. This SMS will help us identify the ongoing research challenges and priorities.
The following research questions (RQs) will guide our SMS to achieve our study objectives:
RQ1 What is the current state of the art in the development and implementation of secure DBs?
RQ2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
1.1 Paper contribution
The contributions of the intended work are as follows:
The proposed research undertakes a systematic mapping study (SMS) to identify and emphasize the challenges associated with developing and maintaining secure databases.
In addition to showing the difficulties experienced by users using various databases from a software engineering standpoint, our SMS survey sheds light on some of the most current database security studies.
It also highlights the importance of maintaining careful attention to database security and suggests a direction for future research in this field.
1.2 Motivation for the paper
Several research in the literature seeks to give a solution for database security. However, before moving forward with new solutions, it is necessary to synthesize current knowledge to offer security practitioners the most up-to-date information. We must identify the cutting-edge in constructing, implementing, and maintaining dependable databases, as well as security challenges, so BD’s design, development, and maintenance may be secure. The motivation behind this research is to provide in-depth solutions to these problems.
1.3 Paper organization
The remainder of the article is arranged in the following manner.
In Sect. 2 , we discussed the background of DB security, and Sect. 3 , illustrated the research methodology in detail. The results of our conducted SMS are given in Sect. 4 . In Sect. 5 , the Implication of our findings is discussed. Finally, the conclusion and future work are discussed in Sect. 6 . Other supportive information is provided in the rest of the sections at the bottom of this paper.
2 Background
There are a number of studies that look at database security from different angles. In their study [ 17 ], Mai et al. suggest using cloud-based security measures to safeguard power system databases. Using an RSA encryption method, public and private keys are generated for database encryption; a huge prime integer is chosen randomly from the cloud platform’s Simple Storage Service and used as the client key. When the database receives a verification key, it compares it to the public key and private key established by the RSA encryption method. If the database determines that the access is legitimate, it provides feedback on the access. According to the findings of the tests, the database can be protected against threats as the threat situation value is always less than 0.50 once the design technique has been implemented.
A data encryption algorithm was developed by Ibrahim et al., which provides an encryption-based solution for DB security. In this system, information is encrypted using standard ASCII characters. They encrypted all of the data in the database and used three keys to access the primary formula. Numbers and text both work for the data. The suggested formula may restore the data’s original format by combining another coordinator with the aforementioned three keys. In order to achieve a comparable data size to when the data is encrypted at a decent pace, the algorithm prioritizes data size and recording speed [ 18 ].
The article offers a lightweight cryptosystem based on the Rivest Cypher 4 (RC4) algorithm [ 19 ] as a solution to the widespread problem of insecure database transfer between sender and recipient. This cryptosystem safeguards sensitive information by encrypting it before sending it through a network and then decrypting it upon its safe return. Database tables have an encapsulating system that ciphers symbolize hens.
The continual improvements in digitizing have enhanced the prominence of online services. Enterprises must store essential data in corporate DB systems, including bank records, activities, the history of patient paperwork, personal data, agreements, etc. The institutions also must maintain the data’s authenticity, privacy, and availability. Any intrusion in security procedures or data may cause severe economic loss and damage the company’s reputation [ 20 ]. The remarkable development in the deployment of DB’s is the required architecture to cope with information that can be attributed to the rising big data. Every 1.2 years, according to research, the entire quantity of institutional information doubles [ 21 ].
Most of the latest studies provide encryption-based solutions for DB security. However, before proceeding towards these solutions, there is a need to find out the flaws that lead to security breaches.
One or more of the following sources can lead to a security flaw:
Interior Internal origins of attack originate from inside the corporation. Human resources—organization supervisors, admins, workers, and interns—all fall within this category of insiders. Almost all insiders are recognized in a particular way, and just a few IT professionals have significant access levels.
Exterior Exterior attacks originate from entities outside the organization instance, cybercriminals, illegal parties of established ways, and government agencies. Usually, no confidence and trust, or benefit is offered for external sources.
Collaborator Any third party involved in a business connection with the organization, firm, or group is considered a partner in many companies. This significant collection of partners, distributors, vendors, contractual labor, and customers is known as the entire enterprise. There must be some level of confidence and privilege of accessibility or record among colleagues in the entire enterprise; therefore, this is often advised.
2.1 Secure databases
With incredibly high secure data and an expanded online presence, the worries concerning DB security are high at all-time. As more systems are connected and brought online to improve access, the sensitivity towards attacks is also increased, estimated to be about $1.3 million in massive financial losses; these mischievous attacks are also liable for public reputation and client relations with the association [ 21 , 22 ]. All users can boundlessly get information from the DB server in an un-secure DB system. All hosts are allowed to associate with the server from any IP address and link with the DB server, making everyone’s information accessible in the storage engine [ 23 , 24 ].
Hence, the DB system is retained with numerous security mechanisms which contain anticipation of unauthorized access to data from an insider or outsider of an organization. Proper encryption techniques should be applied to secure the DB’s [ 25 ]. The most comprehensive secure DB model is the multilevel model, which allows the arrangement of information according to its privacy and deals with mandatory access control MAC [ 7 ]. DB services are intended to ensure that client DB’s are secure by implementing backup and recovery techniques [ 26 ].
The DB can be protected from the third party, which is not authorized by the procedure called cryptography and utilizing other related techniques. The primary motivation behind DB security is ensuring data privacy from unauthorized outsiders. The essential techniques in DB security are authentication, confidentiality, and integrity, which are utilized to secure the DB’s [ 27 ]. DB construction, in particular, must consider security as the main goal while developing a data system. In this respect, security should be addressed at all stages of the software development process [ 7 , 28 , 29 , 30 ].
2.2 Related work
Various articles examine the importance of security controls from the perspective of software engineering [ 31 ]. For instance, MÁRQUEZ et al. [ 32 ] conducted a systematic survey concentrating on the telemedicine platform’s safety from the software engineering viewpoint. The key focus of this article is investigating how Software development assists in designing a reliable telehealth platform. However, the proposed work is just restricted to, particularly telehealth systems.
Al-Sayid et al. [ 1 ] notably studied the challenges of data stores and proposed DB security issues. To prevent unauthorized access to or alteration of the DB’s critical material, they observed a wide variety of DB security issues. Another research by Zeb focuses on identifying potential attacks on the DB system using a standard research study. Mousa et al. [ 33 ] discover the various risks to DB safety in their analysis through the unstructured research study. Moghadam et al. [ 15 ] did an investigation on cloud servers to figure out all conceivable threats.
Nevertheless, this analysis is solely restricted to the cloud DB environment. The researchers Segundo Toapanta et al. [ 5 ] uncovered real-world examples of cybercrime. Apart from that, their research is restricted to cyberattacks.
The authors in [ 21 ] have suggested an innovative technique for spotting distinct threats to DB systems by assessing the risk for incoming new activities. Their research discovered various harmful attacks that could harm the DB system. The emphasis of their research is only confined to security assessment involving DB’s. Experts in [ 32 ] present a comprehensive mapping analysis, and their observations are only limited to the Telehealth system’s privacy from the software engineering point of view. They did not define the security problems in creating, implementing, and managing safe DB’s. Furthermore, with the rapid development of ICTs, it is essential to be up to date on the most recent developments in this field.
The primary goal of this research is to gain a greater understanding of this topic by conducting a Systematic Mapping Survey to identify the problems in building, managing, and sustaining reliable DB’s.
3 Research methodology
The goal of this study was accomplished by evaluating the current state of DB privacy and suggesting areas that needed further research work. With the SMS, researchers may better connect the data from literary research to a series of questions [ 34 , 35 ]. SMS is a descriptive investigation that involves picking and putting combine all published research articles associated with a particular challenge and gives a broad summery of existing materials relating to the particular questions. In the near future, software engineers will benefit significantly from SMS because it provides a comprehensive overview of the research in the field. Figure 2 outlines the process that was followed to conduct the mapping study.
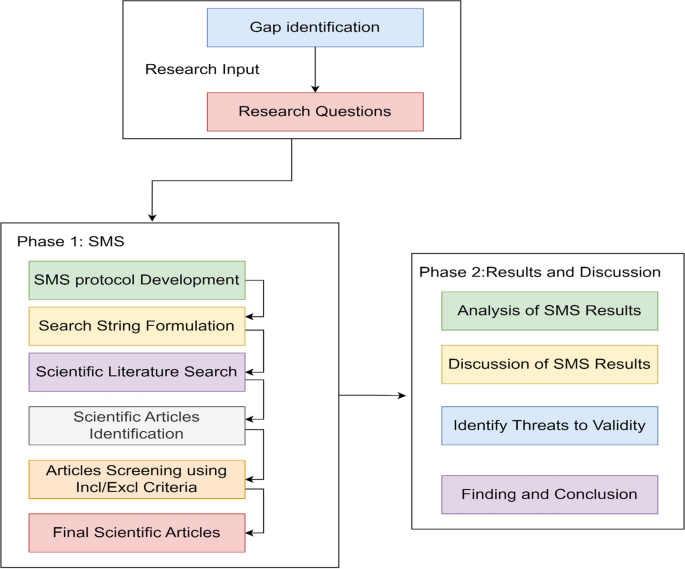
SMS process
3.1 Research questions
Our primary objective is to find the obstacles in planning, creating, and managing data protection. To achieve this objective, relevant study questions have been devised.
RQ 1 What is the current state of the art in the development and implementation of secure DBs?
To address RQ1, we have studied the material depending on the sub-questions mentioned above:
RQ 1.1 n terms of reliable data modeling, development, and maintenance, which stage has received the most attention in the research?
RQ 1.2 What are the primary sites for robust DB design?
RQ 1.3 What are the ongoing research organizations working in robust data modeling?
RQ 1.4 What kinds of DB attacks have been described in the research?
RQ 1.5 According to the research, what are the various categories of DB's?
RQ 1.6 What kinds of DBMS platforms are often employed, as stated in the literature.
RQ 2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
3.2 Search strategy
The scholars in [ 36 , 37 , 38 ] employed the PICO (Population, Intervention, Comparison, and Outcomes) framework to develop a list of terms and then drew search terms from research questions.
Population DB’s and software development in general.
Intervention Security Strategies.
Comparison No assessments proceed for the ongoing investigation.
Outcomes Reliable DB’s.
3.3 Search strings
After several tries, the following two search terms were selected to link the PICO aspects by utilizing Boolean connector (AND):
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database intrusion” OR “Database prevention”) AND (“Security Mechanisms” OR “Security Models” OR “Security methods” OR “Security policies” OR “Security techniques” OR “Security Guidelines”)).
For Science Direct online repository, we compressed the above search term due to space limits. As a result, the accompanying keywords were entered into the ScienceDirect database:
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database prevention”) AND (“Security Mechanisms” OR “Security methods” OR “Security techniques” OR “Security guidelines”)).
3.4 Literature resources
We choose below digital repositories (A to F) to do our SMS and execute the search stings for acquiring publications.
IEEE xplore–B
Springer link–C
AIS electronic library (AiSel)–D
Science direct–E
Wiley online library–F
3.5 Research evaluation criteria
Titles, abstracts, entire readings, and quality assessments were all factors in our selection of research publications. The primary goal of the selection process is to compile an appropriate collection of papers by imposing inclusion and exclusion standards on submissions. We have set the accompanying inclusion and exclusion criteria to perform our SMS effectively. The same inclusion and exclusion criteria have been used in other studies [ 39 , 40 , 41 ]
3.5.1 Inclusion criteria
Only articles that meet one or more of the below criteria were considered for inclusion in our collection.
I1 Research involving the design and implementation of database security measures.
I2 Research that explains how to protect DB’s.
I3 Research the difficulties and dangers of creating, implementing, and maintaining safe DB’s.
I4 Research on the planning, development, and management of reliable DB's included in this category.
3.5.2 Exclusion criteria
The preceding exclusion criteria were considered to find relevant articles.
E1 Publications that are not published in the English language.
E2 No consideration will be given to materials that haven’t been published in any journal, magazine, or conference proceedings, such as unpublished books and grey material.
E3 Books as well as non-peer-reviewed articles, including briefs, proposals, keynotes, evaluations, tutorials, and forum discussions.
E4 Articles that aren’t published in their whole digital.
E5 Publications that don’t meet the inclusion requirements.
E6 Research is only provided as abstracts or PowerPoint slides.
We used the snowballing approach [ 42 , 43 , 44 ] in addition to the previous inclusion/exclusion criteria for our concluding decision. The snowball method was used to choose seven articles from various research repositories. Appendix 1 contains the papers selected using the snowballing approach, from 94 to 100. In the latest research, scholars have employed the same method [ 45 , 46 ].
3.6 Quality evaluation
All articles chosen in the selection have been evaluated for quality. Criteria for quality evaluation include:
To evaluate the papers, we used a three-point Likert scale (yes, partially, no) for every element of the quality evaluation criteria. We awarded each element of quality assessment criteria a score of 2 (yes), 1 (partially), or 0 (no) to achieve notable findings. Including an article in the SMS is permitted if it gained an average standard score of > or = 0.5. Many other scholars [ 45 , 47 , 48 , 49 ] have employed a similar approach. A list of all of the questions from Table 1 is included in the quality ranking.
3.7 Article selection
Employing Afzal et al. tollgate’s technique, we adjusted the key publication selection in our SMS analysis upon executing the search terms (Sect. 3.3 ) and online DB’s (Sect. 3.4 ) [ 50 ]. The five stages of this method are as follows: (Table 2 ).
Stage1 (St-1) Conducting literature searches in digital repositories/DB’s for most relevant articles.
Stage 2 (St-2) A article’s inclusion or removal is based on its title and abstract readings.
Stage 3 (St-3) To determine if an item should be included or not, the introduction and findings must be reviewed.
Stage 4 (St-4) the inclusion and exclusion of data analysis research are based on a full-text review of the research's findings.
In Stage 5 (St-5) most of the original studies that will be included in the SMS study have been vetted and selected for inclusion.
There were 4827 documents collected from the chosen web-based libraries/DB’s by imposing inclusion and exclusion criteria following the initial search string iteration (see Sect. 3.3 ). (Sects. 3.5.1 and 3.5.2 , respectively). The tollgate strategy led to a shortlist of 100 publications that were eventually selected for the research. Quality evaluation criteria were used to evaluate the selected articles (Sect. 3.6 ). Appendix 1 includes a collection of the publications that were ultimately chosen.
3.8 Extracting and synthesizing content
A survey of the articles reviewed is used to obtain the data. In order to address the questions stated in Sect. 3.1 , the entire content of every article has been reviewed, and pertinent data extracted. You can find a precise technique for extracting data in the SMS Protocol.
4 Description of key findings
A comprehensive mapping analysis was used throughout this study to determine current state-of-the-art and privacy issues in data modeling, development, and maintenance. Sections 4.1 , 4.2 , 4.3 , 4.4 , 4.5 and 4.6 contain the facts of our observations.
4.1 The current state of the art
RQ1 has been addressed using the below sub-questions as a reference (Sects. 4.1.1 , 4.1.2 , 4.1.3 , 4.1.4 , 4.1.5 and 4.1.6 ).
4.1.1 Stages in the building of a protected database
RQ 1.1 focuses on a reliable DB’s most frequently studied stages (design, development, and maintenance). As seen in Table 3 , the “design” step was mentioned in most publications at a rate of 27%. There is a 25 percent chance that you’ll hear about the “developing” stage. The “maintenance” stage was only mentioned in 5 of our SMS research findings.
4.1.2 Well-known sources for the building of reliable DB’s
RQ 1.2 is addressed in the second part of this SMS, which concentrates on the location of the papers chosen for this SMS. For venue and provider type analyses, we looked at five repositories, including A, B, C, D, and E. Tables 4 and 5 exhibit the snowballing method, which we refer to as “others.” Several of the papers from these collections were presented at conferences, journals, and workshops/symposia, among other venues. As shown in Table 4 , 45 out of 100 articles were published through the conference venue. Secondly, we found that, with a rate of 37 out of 100, a large percentage of the publications came from the journal channel. Workshops and symposiums accounted for 18% of the articles presented.
Table 4 lists a total of 100 articles spanning a wide range of topics related to DB privacy. This indicates that scholars have devoted a great deal of attention to this topic. “International Journal of Information Security(IJIS)”, “The International Journal on Very Large Data Bases (VLDB)”, “Computers and Security (C&S)”, “Digital Investigation (DI)”, “Journal of Natural Sciences (JNS)” and “Journal of Zhejiang University SCIENCE A (JZUS-A)” were found to be the most popular publications for privacy mechanisms in secure DB designing, as mentioned in Table 5 . We also discovered that the “Annual Computer Security Applications Conference(ACSAC)” and the “International Workshop on Digital Watermarking(IWDW)” are the most often referred articles on the issue of our research. Software engineering and other related domains can benefit greatly from DB privacy studies.
4.1.3 Research institutions participating in the construction of a reliable DB
The institution of the first researcher was utilized to determine and evaluate the highly ongoing researching institutes in the field of protected DB’s. Table 6 shows the findings for RQ 1.3, which reveal that “University of Florida, USA (UOF)” and “CISUC, University of Coimbra, Portugal (UOC)” produced the most research publications on protected DB’s (3 percent, each, out of 100). Ben-Gurion University of the Negev (BGU); RMIT University in Melbourne, Australia; YONSEI University in Seoul; TELECOM Bretagne in Brest, France(ENST); Anna University in Chennai, India (AUC); Huazhong University of Science and Technology in Wuhan (HUST); and George Mason University in Fairfax, Virgin Islands(GMU). BGU has presented two publications for each of the selected research.
4.1.4 The most common kind of DB attacks, according to academic research
RQ 1.4 is concerned with identifying the many kinds of DB attacks that have been recorded. Table 7 shows the three types of incidents: internal, external, and both (internal and external). To effectively understand intrusions, we must combine cyber-attacks with breaches by collaborators. Because both internal and external attacks are mentioned in one article, we refer to this as both (internal and external). Our SMS study’s “Both (Internal & External)” attacks had a rate of 52, according to the assessment in Table 7 . The bulk of the articles in our SMS survey highlighted “External” attacks with a frequency of 35%. In total, 13 papers in our SMS addressed the topic of “internal” attacks.
4.1.5 Database types that have been identified in the literature
To answer RQ 1.5, we must recognize the various DB’s discussed in the literature. Seventeen different DB’s have been documented in the research based on the data we gathered from the articles we included in our SMS. Table 8 shows that of the 100 articles in our SMS survey, 24 papers mentioned the term “Web DB.” Secondly, we found that “Commercial DB” appeared in 11 of the 100 articles in our SMS analysis. According to SMS, “multilevel DB and distributed DB” was mentioned in ten publications.
4.1.6 Kinds of database management systems (DBMS) presented in the research
Data management systems (DBMS) are examined in RQ 1.6. In this research, 11 distinct DBMS types have been documented based on our SMS data, which was gathered from a selection of studies. Most of the articles in our SMS survey mentioned an “Oracle DB system” with a 31 out of 100 rate, as shown in Table 9 . Secondly, “MySQL DB system” was mentioned in most of the publications in our SMS analysis (23 out of 100). Our SMS research found 21 publications that mentioned the term “SQL Server DB system.”
4.2 Issues in databases
As demonstrated in Table 10 and Fig. 3 our existing research into DB privacy has uncovered 20 issues from a pool of 100 studies (see Appendix 1 ).
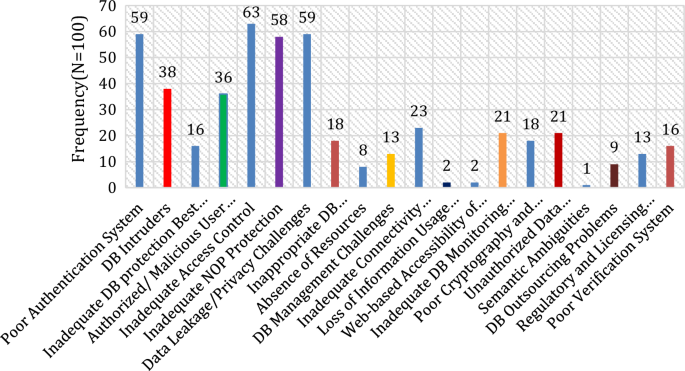
Issues in DB security
CC #1 Poor authentication system An unauthorized individual gains access to a DB, harvests vital information, and allows the hostile attacker to violate the safety of certified DB’s [ 1 , 51 ].
CC #2 Database intruders We are talking about when we say “threat database attacks” Anonymous queries (anomalous query attack), Harmful queries (query flood attack), and Inferential Attacks (polyinstantiation issue, aggregate problem).
CC #3: Inadequate database protection Best Strategies Specifications Engineering, Architectural, Planning, and Development all suffer from the absence of proper security procedures.
CC #4 Authorized/Malicious User Threats An authorized individual, employee, or administrator may collect or disclose critical data [ 52 ].
CC #5 Inadequate access contro Whenever many persons need access to the information, the risk of data fraud and leakage increases. The access should be restricted and regulated [ 1 ]
CC #6 Inadequate NOP protection Inadequate NOP Protection is a shortage of network privacy, operating system privacy, and physical safety.
CC #7 Data leakage/privacy challenges Clients of database systems are increasingly concerned about information security. Attacks on disclosed confidential information, including passwords, emails, and private photographs, triggered this issue. Individuals and database systems cannot stop the propagation of data exploitation and destruction once the content has been leaked [ 53 ].
CC #8 Inappropriate database implementation/configuration/maintenance Numerous DB’s are improperly setup, formatted, and maintained, among the main reasons for database privacy issues [ 54 ].
CC #9 Absence of resources When we talk about a shortage of resources, we are talking about a need of trained employees, a lack of time and budget, a shortage of reliable resources, and an insufficient storage capacity, to name a few things.
CC #10 Database management challenges There are aspects of effectively handling database systems, connectivity, and information at different levels [ 53 ].
CC #11 Inadequate connectivity platforms Presently, the majority of customer, user, and third-party conversations are conducted online. The inclusion of an insecure transmission medium was driven by the Internet’s opportunity to link DB’s [ 1 ].
CC #12 Loss of information usage monitoring Several users are unconcerned regarding their communications but may inadvertently send important information to an unauthorized person or untrustworthy servers. Because of a shortage of supervision of data consumption, they are also lost and destroyed [ 1 ].
CC #13 Web-based accessibility of tools for database attacks Several tools being used for intrusions are accessible in this globally networked domain, allowing intruders to expose weak spots with minimal expertise of the victim DB architecture [ 1 ].
CC #14 Inadequate database monitoring strategy Regulatory risk, discovery, mitigation, and restoration risk are just a few of the dangers posed by a lack of DB auditing [ 1 ].
CC #15 Poor cryptography and anonymization No DB privacy plan, regulation, or technology would be sufficient without cryptography, whether the information is traveling over a network or being kept in the DB system [ 1 ].
CC #16 Unauthorized data alteration/deletion Any type of unauthorized information alteration or deletion can result in substantial economic losses for an organization or corporation [ 55 ].
CC #17 Semantic ambiguities DB issues, including semantic uncertainty, which arises from an absence of semantics or inadequate semantic descriptions, dissemination issues, updating scope constraints, and tuple mistrust, are addressed [ 56 , 57 ].
CC #18: DB outsourcing problems : Because so many DB’s are now being outsourced, there are serious concerns about the data’s accuracy and safety. Clients will have to relinquish management of the information they have outsourced [ 58 , 59 ] .
CC #19 Regulatory and licensing challenges DB’s have many security issues, including policy and licensing concerns. Would the corporation have a consistent and approved policy and licensing from the authorities or organization [ 1 , 60 ]?
#20 Poor verification system A poor verification system allows an attacker to assume the credentials of a legitimate DB and access its data. The invader has a wide range of options for determining the identification of data. Assuming passwords are easy to remember [ 1 ] or using a preset username and password.
4.3 An assessment of database protection issues based on continents
There is much research on various continents in our SMS findings. A comparative analysis of only three continents, i.e., Europe, North America, and Asia, is discussed in this work (See Appendix 2 for more details). We want to find out if these issues are different across continents. We believe that by examining the similarities and distinctions among these problems, we may better prepare ourselves to deal with them on the continent in question. We employed the sequential correlation chi-square test to determine whether there were notable variations among the issues in the three continents listed previously (Martin, 2000). There are many more similarities than distinctions among the issues in the three continents. Poor authentication systems, DB intruders, inadequate DB protection best strategies, and authorized/ malicious user threats are the only major differences found in Table 11 . According to our findings, the most prevalent risks in the three continents are “Inadequate Access Control” (65%, 57%, and 64%), “Inadequate NOP Protection” (59%, 57%, and 60%), “Data Leakage/Privacy Challenges” (49%, 60%, 64%), and “Authorized/Malicious Individuals Threats” (40%, 20%, and 52%). It is not uncommon to see “Authorized/Malicious User Threats,” “Inadequate Access Control,” and “Inadequate NOP Security” across Europe and Asia. Inadequate Connectivity Platforms, Poor Verification Systems, Data Leakage/Privacy Challenges, and Regulatory and Licensing Challenges are some of the problems North American and European clients/users face while creating safe DB’s, as shown in Table 11 . According to our research, the “Poor Verification System” problem affects the most significant number of customers and users in Asia (78 percent). “Data Leakage/Privacy Challenges” is the most common issue faced by European customers and individuals (60 percent). Many customers in North America face “Inadequate Access Control” and “Data Leakage/Privacy Challenges” concerns, respectively (i.e., 64 percent) (Fig. 4 ).
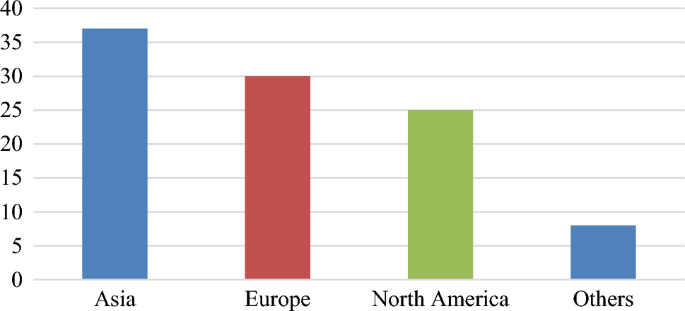
Distribution depending on continents
4.4 Methodological assessment of database privacy issues
Table 12 shows how we divided the different types of difficulties into three distinct approaches. Table 12 shows the three approaches used: tests, Ordinary literature review OLR, and Other/Mixed Approaches as shown in Fig. 5 . Other techniques include writing an experience report, conducting a case study, conducting a survey, and utilizing fuzzy methodologies. When we talk about “many methodologies,” we mean that more than one is employed in a single work. Testing is commonly utilized (39 out of 100 times, according to Table 12 ). The second notable finding in our SMS research is that 31 of the 100 participants used a standard literature review approach. Appendix 2 has further information. Many issues have been revealed by studying the distribution of publications among the three methodologies. Seventeen issues have been detected in relation to OLR, as shown in Table 12 . Two of the Seventeen issues have been mentioned in over 50% of the publications. Inadequate Access Control (74%), and Data Leakage/Privacy Challenges (52%), are two of the most often stated problems. Tests face a total of 18 difficulties. Four of these 18 issues have been quoted more than 50% of the time in at least one of the publications. “Data Leakage/Privacy Challenges—64 percent”, “Inadequate NOP Protection—62 percent”, “Poor Authentication System—56 percent”, and “Inadequate Access Control—56 percent” are among the most often stated difficulties. Other/Mixed Approaches publications have highlighted twenty difficulties. Moreover, half of the publications cited 4 of the 20 issues listed. “Poor Authentication System—73%”, “Inadequate NOP Protection—63%”, “Inadequate Access Control—60%”, and “Data Leakage/Privacy Challenges—60%” are among the most frequently stated problems.
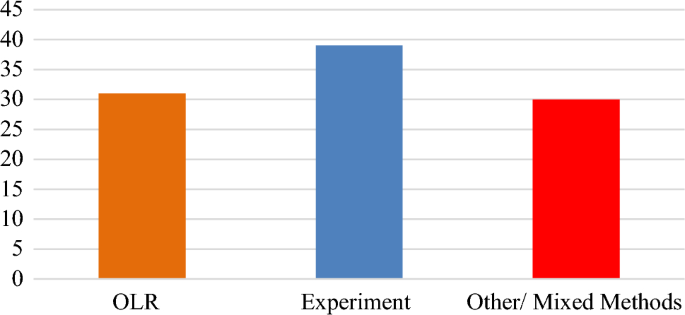
Methodological-based distribution of papers
Table 12 shows that no SMS approach was employed in any studies (n = 0). These findings prove that our study methodology is innovative in this particular field. We performed the Linear-by-Linear Chi-Square test for the earlier research-mentioned techniques and methodologies to establish whether there was a substantial difference between the challenges. “Poor Authentication System” and “Inappropriate DB implementation/configuration/maintenance” are the only notable variances.
4.5 Years-based study of database privacy issues
A comparison of issues over two time periods, 1990–2010 and 2011–2021, is shown in Table 13 and presented in Fig. 6 . More information can be found in Appendix 2 . Within the first phase; we found that 18 issues had been highlighted in the research. Four of the 18 issues have been quoted more than 50% in the publications. Inadequate Access Control (70 percent), Poor Authentication System (65 percent), Inadequate NOP Protection (62 percent), and Data Leakage/Privacy Challenges (52 percent) are the most commonly stated vulnerabilities. Between 1990 and 2010, 70 percent of DB’s had Inadequate Access Control, indicating that designers failed to effectively control access permission throughout implementationcontrol access permission throughout implementation.
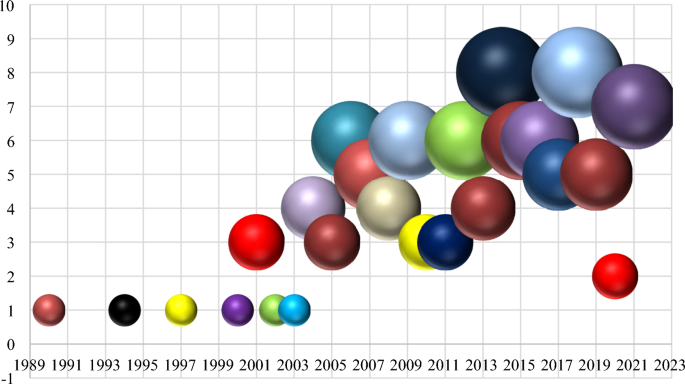
Year-based distribution of publications
Furthermore, admins in an organization are liable for ensuring that data is adequately protected via access permissions. The “Inadequate Access Control” difficulty has dropped to 58 percent in the second period. The literature has revealed 19 problems for the second time period. Four of the 19 obstacles have been referenced in at least half of the publications. “Data Leakage/Privacy Challenges” accounts for 63% of the faults, “Inadequate Access Control” for 58%, “Poor Authentication System” for 55%, and “Inadequate NOP Protection” for 55% of the issues, respectively. We used the Linear-by-Linear Chi-Square analysis and only identified a substantial variation for one problem, “DB Management Challenges, “with a p -value of less than.05.
4.6 Evaluation of articles based on their venue
Table 14 displays a breakdown of the various distribution methods. In addition to Journals, Symposiums, Conferences, and Workshops, we have presented our final articles on extracting data via SMS in various other publications venues as well. Journals, Workshops/Symposiums, and conferences have been classified into three categories for easy study. We found that 45 percent of our comprehensive study of articles was presented at conferences, according to Table 14 and Fig. 7 . Additionally, 37% of the publications in Table 14 were presented in new journals. For further information, please see Appendix 2 at the ending of the study. Many issues have been discovered as a result of distributing papers via these three channels. According to our findings, 18 issues with journals need to be addressed. Four of the 18 challenges have been referenced in at least half of the publications. “Privacy Issues/Data Leakage—84 percent,” “Inadequate Access Control”—59 percent, “Inadequate NOP Protection”—59 percent,” and “Poor Authentication System—54 percent” are the most often stated difficulties. Conferences face a total of 20 obstacles. Three of these 20 difficulties have been quoted more than 50% of the time in at least one publication. “Poor Authentication System—71 percent,” “Inadequate Access Control—69 percent,” and “Inadequate NOP Protection—62 percent” are the most often stated issues. Workshops/Symposiums face a total of 16 difficulties. Two issues have been mentioned in over half of the publications out of the 16 total. “Data Leakage/Privacy Challenges—61 percent” and “Inadequate Access Control—56 percent” are the most commonly reported hurdles. Linear-by-Linear Chi-Squared test has been used to find substantial differences throughout the difficulties. We have found just one big variation between the hurdles “Data Leakage/Privacy Challenges”.
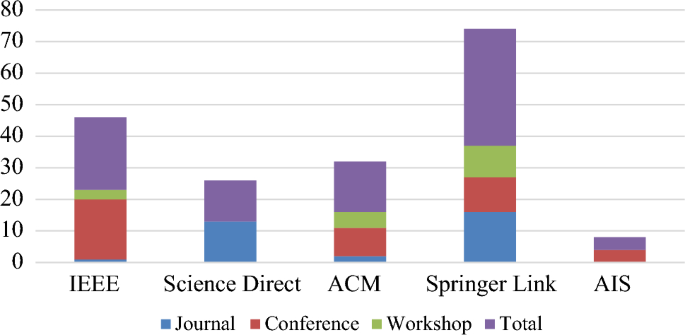
Venue-based distribution of articles
4.7 Comparison with existing studies
A wealth of studies have delved into various aspects of database security. Some of these have centered their attention on securing data transmission from server to client, while others have prioritized the construction of secure databases through secure coding practices. The increasing dependence on geographically dispersed information systems for daily operations might augment productivity and efficiency but simultaneously heightens the risk of security violations. Current security measures ensure data transmission protection, yet a comprehensive security strategy must also encompass mechanisms to enforce diverse access control policies. These policies should consider the content sensitivity, data attributes and traits, and other contextual data such as timing.
The consensus in the field is that effective access control systems should integrate data semantics. Moreover, strategies ensuring data integrity and availability must be customized for databases. Consequently, the database security community has developed an array of strategies and procedures over time to safeguard the privacy, integrity, and accessibility of stored data.
Nonetheless, despite these advancements, fresh challenges persist in the database security landscape. Evolving threats, data access “disintermediation,” and emerging computing paradigms and applications like grid-based computing and on-demand business have all introduced new security demands and innovative contexts where existing methodologies can be employed or extended. Despite a multitude of available solutions, raising awareness about existing security breaches is critical for bolstering database security.
In response, we decided to conduct a Systematic Mapping Study (SMS) on secure databases to offer an up-to-date perspective for both database users and developers. We did not find any comprehensive systematic literature review (SLR) or mapping study on this topic to draw comparisons with. However, we believe this research will offer a strategic roadmap for all database stakeholders.
5 Practical implications of research
The practical implications of this research are manifold and impactful. Initially, the results of this SMS will serve as an invaluable resource for DB privacy professionals and users. By leveraging the insights from this study, experts gain an enhanced understanding of DB privacy issues that need addressing. Consequently, they can prioritize their focus on the most significant security challenges. This, in turn, equips DB users with an awareness of their potential privacy risks. Thus, this study benefits consumers by assisting organizations in developing secure DB systems, mindful of the challenges they face (Table 10 ).
Furthermore, professionals such as DB designers, project managers, and scholars specializing in secure DB design are keen to keep abreast of the latest developments. This research provides DB developers with insights into novel strategies for DB security and the latest advancements in DB technology. Journals such as “VLDB,” “Computers & Security,” “DI,” and “JNS” should be of particular interest to them. Consequently, they would find it beneficial to scrutinize papers available from the “ACSAC” and “IWDW” Conferences and Workshops. The aforementioned venues present optimal resources for studying reliable DB development.
These venues, recognized for their focus on secure DB design, encourage scholars to contribute high-quality academic articles. The outcomes of this study will inform experts’ decision-making processes, providing guidance on where to invest when developing tools and methodologies for safeguarding DB systems. Lastly, it underscores the need for organizations to provide appropriate training for their customers to tackle critical challenges.
Acknowledgements
The authors would like to acknowledge the support provided by the Deanship of Scientific Research via project number DF201007 at King Fahd University of Petroleum and Minerals, Saudi Arabia.
Open Access funding provided by University of Oulu including Oulu University Hospital.
Author information
Authors and affiliations.
Department of Computer Science and IT, Software-Engineering-Research-Group (SERG-UOM), University of Malakand, Chakdara, Pakistan
Asif Iqbal & Siffat Ullah Khan
Information and Computer Science Department, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Mahmood Niazi
Interdisciplinary Research Center for Intelligent Secure Systems, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Department of Information Systems, College of Computer and Information Sciences, Jouf University, Sakaka, 72311, Saudi Arabia
Mamoona Humayun
Faculty of Computer Science and Information Technology, Universiti Malaysia Sarawak, Kota Samarahan, Sarawak, Malaysia
Najm Us Sama
M3S Empirical Software Engineering Research Unit, University of Oulu, Oulu, Finland
Arif Ali Khan
Lancaster University Leipzig, Leipzig, Germany
Aakash Ahmad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Arif Ali Khan .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
See Table 15 .
See Table 16 .
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Iqbal, A., Khan, S.U., Niazi, M. et al. Advancing database security: a comprehensive systematic mapping study of potential challenges. Wireless Netw (2023). https://doi.org/10.1007/s11276-023-03436-z
Download citation
Published : 17 July 2023
DOI : https://doi.org/10.1007/s11276-023-03436-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Database security
- Systematic mapping study
- Secure databases
- Modeling and maintenance of protected databases
- Issues in the development
- Find a journal
- Publish with us
- Track your research
Database Management Systems (DBMS)
Database group website: db.cs.berkeley.edu
Declarative languages and runtime systems
Design and implementation of declarative programming languages with applications to distributed systems, networking, machine learning, metadata management, and interactive visualization; design of query interface for applications.
Scalable data analysis and query processing
Scalable data processing in new settings, including interactive exploration, metadata management, cloud and serverless environments, and machine learning; query processing on compressed, semi-structured, and streaming data; query processing with additional constraints, including fairness, resource utilization, and cost.
Consistency, concurrency, coordination and reliability
Coordination avoidance, consistency and monotonicity analysis; transaction isolation levels and protocols; distributed analytics and data management, geo-replication; fault tolerance and fault injection.
Data storage and physical design
Hot and cold storage; immutable data structures; indexing and data skipping; versioning; new data types; implications of hardware evolution.
Metadata management
Data lineage and versioning; usage tracking and collective intelligence; scalability of metadata management services; metadata representations; reproducibility and debugging of data pipelines.
Systems for machine learning and model management
Distributed machine learning and graph analytics; physical and logical optimization of machine learning pipelines; online model management and maintenance; prediction serving; real-time personalization; latency-accuracy tradeoffs and edge computing for large-scale models; machine learning lifecycle management.
Data cleaning, data transformation, and crowdsourcing
Human-data interaction including interactive transformation, query authoring, and crowdsourcing; machine learning for data cleaning; statistical properties of data cleaning pipelines; end-to-end systems for crowdsourcing.
Interactive data exploration and visualization
Interactive querying and direct manipulation; scalable spreadsheets and data visualization; languages and interfaces for interactive exploration; progressive query visualization; predictive interaction.
Secure data processing
Data processing under homomorphic encryption; data compression and encryption; differential privacy; oblivious data processing; databases in secure hardware enclaves.
Foundations of data management
Optimal trade-offs between storage, quality, latency, and cost, with applications to crowdsourcing, distributed data management, stream data processing, version management; expressiveness, complexity, and completeness of data representations, query languages, and query processing; query processing with fairness constraints.
Research Centers
- EPIC Data lab
- Sky Computing Lab
- Alvin Cheung
- Natacha Crooks
- Joseph Gonzalez
- Joseph M. Hellerstein (coordinator)
- Jiantao Jiao
- Aditya Parameswaran
- Matei Zaharia
- Eric Brewer
- Michael Lustig
- Jelani Nelson
Faculty Awards
- ACM Prize in Computing: Eric Brewer, 2009.
- National Academy of Engineering (NAE) Member: Ion Stoica, 2024. Eric Brewer, 2007.
- American Academy of Arts and Sciences Member: Eric Brewer, 2018.
- Sloan Research Fellow: Aditya Parameswaran, 2020. Alvin Cheung, 2019. Jelani Nelson, 2017. Michael Lustig, 2013. Ion Stoica, 2003. Joseph M. Hellerstein, 1998. Eric Brewer, 1997.
Related Courses
- CS 186. Introduction to Database Systems
- CS 262A. Advanced Topics in Computer Systems
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection

Advances in database systems education: Methods, tools, curricula, and way forward
Muhammad ishaq.
1 Department of Computer Science, National University of Computer and Emerging Sciences, Lahore, Pakistan
2 Department of Computer Science, Virtual University of Pakistan, Lahore, Pakistan
3 Department of Computer Science, University of Management and Technology, Lahore, Pakistan
Muhammad Shoaib Farooq
Muhammad faraz manzoor.
4 Department of Computer Science, Lahore Garrison University, Lahore, Pakistan
Uzma Farooq
Kamran abid.
5 Department of Electrical Engineering, University of the Punjab, Lahore, Pakistan
Mamoun Abu Helou
6 Faculty of Information Technology, Al Istiqlal University, Jericho, Palestine
Associated Data
Not Applicable.
Fundamentals of Database Systems is a core course in computing disciplines as almost all small, medium, large, or enterprise systems essentially require data storage component. Database System Education (DSE) provides the foundation as well as advanced concepts in the area of data modeling and its implementation. The first course in DSE holds a pivotal role in developing students’ interest in this area. Over the years, the researchers have devised several different tools and methods to teach this course effectively, and have also been revisiting the curricula for database systems education. In this study a Systematic Literature Review (SLR) is presented that distills the existing literature pertaining to the DSE to discuss these three perspectives for the first course in database systems. Whereby, this SLR also discusses how the developed teaching and learning assistant tools, teaching and assessment methods and database curricula have evolved over the years due to rapid change in database technology. To this end, more than 65 articles related to DSE published between 1995 and 2022 have been shortlisted through a structured mechanism and have been reviewed to find the answers of the aforementioned objectives. The article also provides useful guidelines to the instructors, and discusses ideas to extend this research from several perspectives. To the best of our knowledge, this is the first research work that presents a broader review about the research conducted in the area of DSE.
Introduction
Database systems play a pivotal role in the successful implementation of the information systems to ensure the smooth running of many different organizations and companies (Etemad & Küpçü, 2018 ; Morien, 2006 ). Therefore, at least one course about the fundamentals of database systems is taught in every computing and information systems degree (Nagataki et al., 2013 ). Database System Education (DSE) is concerned with different aspects of data management while developing software (Park et al., 2017 ). The IEEE/ACM computing curricula guidelines endorse 30–50 dedicated hours for teaching fundamentals of design and implementation of database systems so as to build a very strong theoretical and practical understanding of the DSE topics (Cvetanovic et al., 2010 ).
Practically, most of the universities offer one user-oriented course at undergraduate level that covers topics related to the data modeling and design, querying, and a limited number of hours on theory (Conklin & Heinrichs, 2005 ; Robbert & Ricardo, 2003 ), where it is often debatable whether to utilize a design-first or query-first approach. Furthermore, in order to update the course contents, some recent trends, including big data and the notion of NoSQL should also be introduced in this basic course (Dietrich et al., 2008 ; Garcia-Molina, 2008 ). Whereas, the graduate course is more theoretical and includes topics related to DB architecture, transactions, concurrency, reliability, distribution, parallelism, replication, query optimization, along with some specialized classes.
Researchers have designed a variety of tools for making different concepts of introductory database course more interesting and easier to teach and learn interactively (Brusilovsky et al., 2010 ) either using visual support (Nagataki et al., 2013 ), or with the help of gamification (Fisher & Khine, 2006 ). Similarly, the instructors have been improvising different methods to teach (Abid et al., 2015 ; Domínguez & Jaime, 2010 ) and evaluate (Kawash et al., 2020 ) this theoretical and practical course. Also, the emerging and hot topics such as cloud computing and big data has also created the need to revise the curriculum and methods to teach DSE (Manzoor et al., 2020 ).
The research in database systems education has evolved over the years with respect to modern contents influenced by technological advancements, supportive tools to engage the learners for better learning, and improvisations in teaching and assessment methods. Particularly, in recent years there is a shift from self-describing data-driven systems to a problem-driven paradigm that is the bottom-up approach where data exists before being designed. This mainly relies on scientific, quantitative, and empirical methods for building models, while pushing the boundaries of typical data management by involving mathematics, statistics, data mining, and machine learning, thus opening a multidisciplinary perspective. Hence, it is important to devote a few lectures to introducing the relevance of such advance topics.
Researchers have provided useful review articles on other areas including Introductory Programming Language (Mehmood et al., 2020 ), use of gamification (Obaid et al., 2020 ), research trends in the use of enterprise service bus (Aziz et al., 2020 ), and the role of IoT in agriculture (Farooq et al., 2019 , 2020 ) However, to the best of our knowledge, no such study was found in the area of database systems education. Therefore, this study discusses research work published in different areas of database systems education involving curricula, tools, and approaches that have been proposed to teach an introductory course on database systems in an effective manner. The rest of the article has been structured in the following manner: Sect. 2 presents related work and provides a comparison of the related surveys with this study. Section 3 presents the research methodology for this study. Section 4 analyses the major findings of the literature reviewed in this research and categorizes it into different important aspects. Section 5 represents advices for the instructors and future directions. Lastly, Sect. 6 concludes the article.
Related work
Systematic Literature Reviews have been found to be a very useful artifact for covering and understanding a domain. A number of interesting review studies have been found in different fields (Farooq et al., 2021 ; Ishaq et al., 2021 ). Review articles are generally categorized into narrative or traditional reviews (Abid et al., 2016 ; Ramzan et al., 2019 ), systematic literature review (Naeem et al., 2020 ) and meta reviews or mapping study (Aria & Cuccurullo, 2017 ; Cobo et al., 2012 ; Tehseen et al., 2020 ). This study presents a systematic literature review on database system education.
The database systems education has been discussed from many different perspectives which include teaching and learning methods, curriculum development, and the facilitation of instructors and students by developing different tools. For instance, a number of research articles have been published focusing on developing tools for teaching database systems course (Abut & Ozturk, 1997 ; Connolly et al., 2005 ; Pahl et al., 2004 ). Furthermore, few authors have evaluated the DSE tools by conducting surveys and performing empirical experiments so as to gauge the effectiveness of these tools and their degree of acceptance among important stakeholders, teachers and students (Brusilovsky et al., 2010 ; Nelson & Fatimazahra, 2010 ). On the other hand, some case studies have also been discussed to evaluate the effectiveness of the improvised approaches and developed tools. For example, Regueras et al. ( 2007 ) presented a case study using the QUEST system, in which e-learning strategies are used to teach the database course at undergraduate level, while, Myers and Skinner ( 1997 ) identified the conflicts that arise when theories in text books regarding the development of databases do not work on specific applications.
Another important facet of DSE research focuses on the curriculum design and evolution for database systems, whereby (Alrumaih, 2016 ; Bhogal et al., 2012 ; Cvetanovic et al., 2010 ; Sahami et al., 2011 ) have proposed solutions for improvements in database curriculum for the better understanding of DSE among the students, while also keeping the evolving technology into the perspective. Similarly, Mingyu et al. ( 2017 ) have shared their experience in reforming the DSE curriculum by adding topics related to Big Data. A few authors have also developed and evaluated different tools to help the instructors teaching DSE.
There are further studies which focus on different aspects including specialized tools for specific topics in DSE (Mcintyre et al, 1995 ; Nelson & Fatimazahra, 2010 ). For instance, Mcintyre et al. ( 1995 ) conducted a survey about using state of the art software tools to teach advanced relational database design courses at Cleveland State University. However, the authors did not discuss the DSE curricula and pedagogy in their study. Similarly, a review has been conducted by Nelson and Fatimazahra ( 2010 ) to highlight the fact that the understanding of basic knowledge of database is important for students of the computer science domain as well as those belonging to other domains. They highlighted the issues encountered while teaching the database course in universities and suggested the instructors investigate these difficulties so as to make this course more effective for the students. Although authors have discussed and analyzed the tools to teach database, the tools are yet to be categorized according to different methods and research types within DSE. There also exists an interesting systematic mapping study by Taipalus and Seppänen ( 2020 ) that focuses on teaching SQL which is a specific topic of DSE. Whereby, they categorized the selected primary studies into six categories based on their research types. They utilized directed content analysis, such as, student errors in query formulation, characteristics and presentation of the exercise database, specific or non-specific teaching approach suggestions, patterns and visualization, and easing teacher workload.
Another relevant study that focuses on collaborative learning techniques to teach the database course has been conducted by Martin et al. ( 2013 ) This research discusses collaborative learning techniques and adapted it for the introductory database course at the Barcelona School of Informatics. The motive of the authors was to introduce active learning methods to improve learning and encourage the acquisition of competence. However, the focus of the study was only on a few methods for teaching the course of database systems, while other important perspectives, including database curricula, and tools for teaching DSE were not discussed in this study.
The above discussion shows that a considerable amount of research work has been conducted in the field of DSE to propose various teaching methods; develop and test different supportive tools, techniques, and strategies; and to improve the curricula for DSE. However, to the best of our knowledge, there is no study that puts all these relevant and pertinent aspects together while also classifying and discussing the supporting methods, and techniques. This review is considerably different from previous studies. Table Table1 1 highlights the differences between this study and other relevant studies in the field of DSE using ✓ and – symbol reflecting "included" and "not included" respectively. Therefore, this study aims to conduct a systematic mapping study on DSE that focuses on compiling, classifying, and discussing the existing work related to pedagogy, supporting tools, and curricula.
Comparison with other related research articles
Research methodology
In order to preserve the principal aim of this study, which is to review the research conducted in the area of database systems education, a piece of advice has been collected from existing methods described in various studies (Elberzhager et al., 2012 ; Keele et al., 2007 ; Mushtaq et al., 2017 ) to search for the relevant papers. Thus, proper research objectives were formulated, and based on them appropriate research questions and search strategy were formulated as shown in Fig. 1 .

Research objectives
The Following are the research objectives of this study:
- i. To find high quality research work in DSE.
- ii. To categorize different aspects of DSE covered by other researchers in the field.
- iii. To provide a thorough discussion of the existing work in this study to provide useful information in the form of evolution, teaching guidelines, and future research directions of the instructors.
Research questions
In order to fulfill the research objectives, some relevant research questions have been formulated. These questions along with their motivations have been presented in Table Table2 2 .
Study selection results
Search strategy
The Following search string used to find relevant articles to conduct this study. “Database” AND (“System” OR “Management”) AND (“Education*” OR “Train*” OR “Tech*” OR “Learn*” OR “Guide*” OR “Curricul*”).
Articles have been taken from different sources i.e. IEEE, Springer, ACM, Science Direct and other well-known journals and conferences such as Wiley Online Library, PLOS and ArXiv. The planning for search to find the primary study in the field of DSE is a vital task.
Study selection
A total of 29,370 initial studies were found. These articles went through a selection process, and two authors were designated to shortlist the articles based on the defined inclusion criteria as shown in Fig. 2 . Their conflicts were resolved by involving a third author; while the inclusion/exclusion criteria were also refined after resolving the conflicts as shown in Table Table3. 3 . Cohen’s Kappa coefficient 0.89 was observed between the two authors who selected the articles, which reflects almost perfect agreement between them (Landis & Koch, 1977 ). While, the number of papers in different stages of the selection process for all involved portals has been presented in Table Table4 4 .

Selection criteria
Title based search: Papers that are irrelevant based on their title are manually excluded in the first stage. At this stage, there was a large portion of irrelevant papers. Only 609 papers remained after this stage.
Abstract based search: At this stage, abstracts of the selected papers in the previous stage are studied and the papers are categorized for the analysis along with research approach. After this stage only 152 papers were left.
Full text based analysis: Empirical quality of the selected articles in the previous stage is evaluated at this stage. The analysis of full text of the article has been conducted. The total of 70 papers were extracted from 152 papers for primary study. Following questions are defined for the conduction of final data extraction.
Quality assessment criteria
Following are the criteria used to assess the quality of the selected primary studies. This quality assessment was conducted by two authors as explained above.
- The study focuses on curricula, tools, approach, or assessments in DSE, the possible answers were Yes (1), No (0)
- The study presents a solution to the problem in DSE, the possible answers to this question were Yes (1), Partially (0.5), No (0)
- The study focuses on empirical results, Yes (1), No (0)
Score pattern of publication channels
Almost 50.00% of papers had scored more than average and 33.33% of papers had scored between the average range i.e., 2.50–3.50. Some articles with the score below 2.50 have also been included in this study as they present some useful information and were published in education-based journals. Also, these studies discuss important demography and technology based aspects that are directly related to DSE.
Threats to validity
The validity of this study could be influenced by the following factors during the literature of this publication.
Construct validity
In this study this validity identifies the primary study for research (Elberzhager et al., 2012 ). To ensure that many primary studies have been included in this literature two authors have proposed possible search keywords in multiple repetitions. Search string is comprised of different terms related to DS and education. Though, list might be incomplete, count of final papers found can be changed by the alternative terms (Ampatzoglou et al., 2013 ). IEEE digital library, Science direct, ACM digital library, Wiley Online Library, PLOS, ArXiv and Google scholar are the main libraries where search is done. We believe according to the statistics of search engines of literature the most research can be found on these digital libraries (Garousi et al., 2013 ). Researchers also searched related papers in main DS research sites (VLDB, ICDM, EDBT) in order to minimize the risk of missing important publication.
Including the papers that does not belong to top journals or conferences may reduce the quality of primary studies in this research but it indicates that the representativeness of the primary studies is improved. However, certain papers which were not from the top publication sources are included because of their relativeness wisth the literature, even though they reduce the average score for primary studies. It also reduces the possibility of alteration of results which might have caused by the improper handling of duplicate papers. Some cases of duplications were found which were inspected later whether they were the same study or not. The two authors who have conducted the search has taken the final decision to the select the papers. If there is no agreement between then there must be discussion until an agreement is reached.
Internal validity
This validity deals with extraction and data analysis (Elberzhager et al., 2012 ). Two authors carried out the data extraction and primary studies classification. While the conflicts between them were resolved by involving a third author. The Kappa coefficient was 0.89, according to Landis and Koch ( 1977 ), this value indicates almost perfect level of agreement between the authors that reduces this threat significantly.
Conclusion validity
This threat deals with the identification of improper results which may cause the improper conclusions. In this case this threat deals with the factors like missing studies and wrong data extraction (Ampatzoglou et al., 2013 ). The objective of this is to limit these factors so that other authors can perform study and produce the proper conclusions (Elberzhager et al., 2012 ).
Interpretation of results might be affected by the selection and classification of primary studies and analyzing the selected study. Previous section has clearly described each step performed in primary study selection and data extraction activity to minimize this threat. The traceability between the result and data extracted was supported through the different charts. In our point of view, slight difference based on the publication selection and misclassification would not alter the main results.
External validity
This threat deals with the simplification of this research (Mateo et al., 2012 ). The results of this study were only considered that related to the DSE filed and validation of the conclusions extracted from this study only concerns the DSE context. The selected study representativeness was not affected because there was no restriction on time to find the published research. Therefore, this external validity threat is not valid in the context of this research. DS researchers can take search string and the paper classification scheme represented in this study as an initial point and more papers can be searched and categorized according to this scheme.
Analysis of compiled research articles
This section presents the analysis of the compiled research articles carefully selected for this study. It presents the findings with respect to the research questions described in Table Table2 2 .
Selection results
A total of 70 papers were identified and analyzed for the answers of RQs described above. Table Table6 6 represents a list of the nominated papers with detail of the classification results and their quality assessment scores.
Classification and quality assessment of selected articles
RQ1.Categorization of research work in DSE field
The analysis in this study reveals that the literature can be categorized as: Tools: any additional application that helps instructors in teaching and students in learning. Methods: any improvisation aimed at improving pedagogy or cognition. Curriculum: refers to the course content domains and their relative importance in a degree program, as shown in Fig. 3 .

Taxonomy of DSE study types
Most of the articles provide a solution by gathering the data and also prove the novelty of their research through results. These papers are categorized as experiments w.r.t. their research types. Whereas, some of them case study papers which are used to generate an in depth, multifaceted understanding of a complex issue in its real-life context, while few others are review studies analyzing the previously used approaches. On the other hand, a majority of included articles have evaluated their results with the help of experiments, while others conducted reviews to establish an opinion as shown in Fig. 4 .

Cross Mapping of DSE study type and research Types
Educational tools, especially those related to technology, are making their place in market faster than ever before (Calderon et al., 2011 ). The transition to active learning approaches, with the learner more engaged in the process rather than passively taking in information, necessitates a variety of tools to help ensure success. As with most educational initiatives, time should be taken to consider the goals of the activity, the type of learners, and the tools needed to meet the goals. Constant reassessment of tools is important to discover innovation and reforms that improve teaching and learning (Irby & Wilkerson, 2003 ). For this purpose, various type of educational tools such as, interactive, web-based and game based have been introduced to aid the instructors in order to explain the topic in more effective way.
The inclusion of technology into the classroom may help learners to compete in the competitive market when approaching the start of their career. It is important for the instructors to acknowledge that the students are more interested in using technology to learn database course instead of merely being taught traditional theory, project, and practice-based methods of teaching (Adams et al., 2004 ). Keeping these aspects in view many authors have done significant research which includes web-based and interactive tools to help the learners gain better understanding of basic database concepts.
Great research has been conducted with the focus of students learning. In this study we have discussed the students learning supportive with two major finding’s objectives i.e., tools which prove to be more helpful than other tools. Whereas, proposed tools with same outcome as traditional classroom environment. Such as, Abut and Ozturk ( 1997 ) proposed an interactive classroom environment to conduct database classes. The online tools such as electronic “Whiteboard”, electronic textbooks, advance telecommunication networks and few other resources such as Matlab and World Wide Web were the main highlights of their proposed smart classroom. Also, Pahl et al. ( 2004 ) presented an interactive multimedia-based system for the knowledge and skill oriented Web-based education of database course students. The authors had differentiated their proposed classroom environment from traditional classroom-based approach by using tool mediated independent learning and training in an authentic setting. On the other hand, some authors have also evaluated the educational tools based on their usage and impact on students’ learning. For example, Brusilovsky et al. ( 2010 )s evaluated the technical and conceptual difficulties of using several interactive educational tools in the context of a single course. A combined Exploratorium has been presented for database courses and an experimental platform, which delivers modified access to numerous types of interactive learning activities.
Also, Taipalus and Perälä ( 2019 ) investigated the types of errors that are persistent in writing SQL by the students. The authors also contemplated the errors while mapping them onto different query concepts. Moreover, Abelló Gamazo et al. ( 2016 ) presented a software tool for the e-assessment of relational database skills named LearnSQL. The proposed software allows the automatic and efficient e-learning and e-assessment of relational database skills. Apart from these, Yue ( 2013 ) proposed the database tool named Sakila as a unified platform to support instructions and multiple assignments of a graduate database course for five semesters. According to this study, students find this tool more useful and interesting than the highly simplified databases developed by the instructor, or obtained from textbook. On the other hand, authors have proposed tools with the main objective to help the student’s grip on the topic by addressing the pedagogical problems in using the educational tools. Connolly et al. ( 2005 ) discussed some of the pedagogical problems sustaining the development of a constructive learning environment using problem-based learning, a simulation game and interactive visualizations to help teach database analysis and design. Also, Yau and Karim ( 2003 ) proposed smart classroom with prevalent computing technology which will facilitate collaborative learning among the learners. The major aim of this smart classroom is to improve the quality of interaction between the instructors and students during lecture.
Student satisfaction is also an important factor for the educational tools to more effective. While it supports in students learning process it should also be flexible to achieve the student’s confidence by making it as per student’s needs (Brusilovsky et al., 2010 ; Connolly et al., 2005 ; Pahl et al., 2004 ). Also, Cvetanovic et al. ( 2010 ) has proposed a web-based educational system named ADVICE. The proposed solution helps the students to reduce the gap between DBMS, theory and its practice. On the other hand, authors have enhanced the already existing educational tools in the traditional classroom environment to addressed the student’s concerns (Nelson & Fatimazahra, 2010 ; Regueras et al., 2007 ) Table Table7 7 .
Tools: Adopted in DSE and their impacts
Hands on database development is the main concern in most of the institute as well as in industry. However, tools assisting the students in database development and query writing is still major concern especially in SQL (Brusilovsky et al., 2010 ; Nagataki et al., 2013 ).
Student’s grades reflect their conceptual clarity and database development skills. They are also important to secure jobs and scholarships after passing out, which is why it is important to have the educational learning tools to help the students to perform well in the exams (Cvetanovic et al., 2010 ; Taipalus et al., 2018 ). While, few authors (Wang et al., 2010 ) proposed Metube which is a variation of YouTube. Subsequently, existing educational tools needs to be upgraded or replaced by the more suitable assessment oriented interactive tools to attend challenging students needs (Pahl et al., 2004 ; Yuelan et al., 2011 ).
One other objective of developing the educational tools is to increase the interaction between the students and the instructors. In the modern era, almost every institute follows the student centered learning(SCL). In SCL the interaction between students and instructor increases with most of the interaction involves from the students. In order to support SCL the educational based interactive and web-based tools need to assign more roles to students than the instructors (Abbasi et al., 2016 ; Taipalus & Perälä, 2019 ; Yau & Karim, 2003 ).
Theory versus practice is still one of the main issues in DSE teaching methods. The traditional teaching method supports theory first and then the concepts learned in the theoretical lectures implemented in the lab. Whereas, others think that it is better to start by teaching how to write query, which should be followed by teaching the design principles for database, while a limited amount of credit hours are also allocated for the general database theory topics. This part of the article discusses different trends of teaching and learning style along with curriculum and assessments methods discussed in DSE literature.
A variety of teaching methods have been designed, experimented, and evaluated by different researchers (Yuelan et al., 2011 ; Chen et al., 2012 ; Connolly & Begg, 2006 ). Some authors have reformed teaching methods based on the requirements of modern way of delivering lectures such as Yuelan et al. ( 2011 ) reform teaching method by using various approaches e.g. a) Modern ways of education: includes multimedia sound, animation, and simulating the process and working of database systems to motivate and inspire the students. b) Project driven approach: aims to make the students familiar with system operations by implementing a project. c) Strengthening the experimental aspects: to help the students get a strong grip on the basic knowledge of database and also enable them to adopt a self-learning ability. d) Improving the traditional assessment method: the students should turn in their research and development work as the content of the exam, so that they can solve their problem on their own.
The main aim of any teaching method is to make student learn the subject effectively. Student must show interest in order to gain something from the lectures delivered by the instructors. For this, teaching methods should be interactive and interesting enough to develop the interest of the students in the subject. Students can show interest in the subject by asking more relative questions or completing the home task and assignments on time. Authors have proposed few teaching methods to make topic more interesting such as, Chen et al. ( 2012 ) proposed a scaffold concept mapping strategy, which considers a student’s prior knowledge, and provides flexible learning aids (scaffolding and fading) for reading and drawing concept maps. Also, Connolly & Begg (200s6) examined different problems in database analysis and design teaching, and proposed a teaching approach driven by principles found in the constructivist epistemology to overcome these problems. This constructivist approach is based on the cognitive apprenticeship model and project-based learning. Similarly, Domínguez & Jaime ( 2010 ) proposed an active method for database design through practical tasks development in a face-to-face course. They analyzed results of five academic years using quasi experimental. The first three years a traditional strategy was followed and a course management system was used as material repository. On the other hand, Dietrich and Urban ( 1996 ) have described the use of cooperative group learning concepts in support of an undergraduate database management course. They have designed the project deliverables in such a way that students develop skills for database implementation. Similarly, Zhang et al. ( 2018 ) have discussed several effective classroom teaching measures from the aspects of the innovation of teaching content, teaching methods, teaching evaluation and assessment methods. They have practiced the various teaching measures by implementing the database technologies and applications in Qinghai University. Moreover, Hou and Chen ( 2010 ) proposed a new teaching method based on blending learning theory, which merges traditional and constructivist methods. They adopted the method by applying the blending learning theory on Access Database programming course teaching.
Problem solving skills is a key aspect to any type of learning at any age. Student must possess this skill to tackle the hurdles in institute and also in industry. Create mind and innovative students find various and unique ways to solve the daily task which is why they are more likeable to secure good grades and jobs. Authors have been working to introduce teaching methods to develop problem solving skills in the students(Al-Shuaily, 2012 ; Cai & Gao, 2019 ; Martinez-González & Duffing, 2007 ; Gudivada et al., 2007 ). For instance, Al-Shuaily ( 2012 ) has explored four cognitive factors such as i) Novices’ ability in understanding, ii) Novices’ ability to translate, iii) Novice’s ability to write, iv) Novices’ skills that might influence SQL teaching, and learning methods and approaches. Also, Cai and Gao ( 2019 ) have reformed the teaching method in the database course of two higher education institutes in China. Skills and knowledge, innovation ability, and data abstraction were the main objective of their study. Similarly, Martinez-González and Duffing ( 2007 ) analyzed the impact of convergence of European Union (EU) in different universities across Europe. According to their study, these institutes need to restructure their degree program and teaching methodologies. Moreover, Gudivada et al. ( 2007 ) proposed a student’s learning method to work with the large datasets. they have used the Amazon Web Services API and.NET/C# application to extract a subset of the product database to enhance student learning in a relational database course.
On the other hand, authors have also evaluated the traditional teaching methods to enhance the problem-solving skills among the students(Eaglestone & Nunes, 2004 ; Wang & Chen, 2014 ; Efendiouglu & Yelken, 2010 ) Such as, Eaglestone and Nunes ( 2004 ) shared their experiences of delivering a database design course at Sheffield University and discussed some of the issues they faced, regarding teaching, learning and assessments. Likewise, Wang and Chen ( 2014 ) summarized the problems mainly in teaching of the traditional database theory and application. According to the authors the teaching method is outdated and does not focus on the important combination of theory and practice. Moreover, Efendiouglu and Yelken ( 2010 ) investigated the effects of two different methods Programmed Instruction (PI) and Meaningful Learning (ML) on primary school teacher candidates’ academic achievements and attitudes toward computer-based education, and to define their views on these methods. The results show that PI is not favoured for teaching applications because of its behavioural structure Table Table8 8 .
Methods: Teaching approaches adopted in DSE
Students become creative and innovative when the try to study on their own and also from different resources rather than curriculum books only. In the modern era, there are various resources available on both online and offline platforms. Modern teaching methods must emphasize on making the students independent from the curriculum books and educate them to learn independently(Amadio et al., 2003 ; Cai & Gao, 2019 ; Martin et al., 2013 ). Also, in the work of Kawash et al. ( 2020 ) proposed he group study-based learning approach called Graded Group Activities (GGAs). In this method students team up in order to take the exam as a group. On the other hand, few studies have emphasized on course content to prepare students for the final exams such as, Zheng and Dong ( 2011 ) have discussed the issues of computer science teaching with particular focus on database systems, where different characteristics of the course, teaching content and suggestions to teach this course effectively have been presented.
As technology is evolving at rapid speed, so students need to have practical experience from the start. Basic theoretical concepts of database are important but they are of no use without its implementation in real world projects. Most of the students study in the institutes with the aim of only clearing the exams with the help of theoretical knowledge and very few students want to have practical experience(Wang & Chen, 2014 ; Zheng & Dong, 2011 ). To reduce the gap between the theory and its implementation, authors have proposed teaching methods to develop the student’s interest in the real-world projects (Naik & Gajjar, 2021 ; Svahnberg et al., 2008 ; Taipalus et al., 2018 ). Moreover, Juxiang and Zhihong ( 2012 ) have proposed that the teaching organization starts from application scenarios, and associate database theoretical knowledge with the process from analysis, modeling to establishing database application. Also, Svahnberg et al. ( 2008 ) explained that in particular conditions, there is a possibility to use students as subjects for experimental studies in DSE and influencing them by providing responses that are in line with industrial practice.
On the other hand, Nelson et al. ( 2003 ) evaluated the different teaching methods used to teach different modules of database in the School of Computing and Technology at the University of Sunder- land. They outlined suggestions for changes to the database curriculum to further integrate research and state-of-the-art systems in databases.
- III. Curriculum
Database curriculum has been revisited many times in the form of guidelines that not only present the contents but also suggest approximate time to cover different topics. According to the ACM curriculum guidelines (Lunt et al., 2008 ) for the undergraduate programs in computer science, the overall coverage time for this course is 46.50 h distributed in such a way that 11 h is the total coverage time for the core topics such as, Information Models (4 core hours), Database Systems (3 core hours) and Data Modeling (4 course hours). Whereas, the remaining hours are allocated for elective topics such as Indexing, Relational Databases, Query Languages, Relational Database Design, Transaction Processing, Distributed Databases, Physical Database Design, Data Mining, Information Storage and Retrieval, Hypermedia, Multimedia Systems, and Digital Libraries(Marshall, 2012 ). While, according to the ACM curriculum guidelines ( 2013 ) for undergraduate programs in computer science, this course should be completed in 15 weeks with two and half hour lecture per week and lab session of four hours per week on average (Brady et al., 2004 ). Thus, the revised version emphasizes on the practice based learning with the help of lab component. Numerous organizations have exerted efforts in this field to classify DSE (Dietrich et al., 2008 ). DSE model curricula, bodies of knowledge (BOKs), and some standardization aspects in this field are discussed below:
Model curricula
There are standard bodies who set the curriculum guidelines for teaching undergraduate degree programs in computing disciplines. Curricula which include the guidelines to teach database are: Computer Engineering Curricula (CEC) (Meier et al., 2008 ), Information Technology Curricula (ITC) (Alrumaih, 2016 ), Computing Curriculum Software Engineering (CCSE) (Meyer, 2001 ), Cyber Security Curricula (CSC) (Brady et al., 2004 ; Bishop et al., 2017 ).
Bodies of knowledge (BOK)
A BOK includes the set of thoughts and activities related to the professional area, while in model curriculum set of guidelines are given to address the education issues (Sahami et al., 2011 ). Database body of Knowledge comprises of (a) The Data Management Body of Knowledge (DM- BOK), (b) Software Engineering Education Knowledge (SEEK) (Sobel, 2003 ) (Sobel, 2003 ), and (c) The SE body of knowledge (SWEBOK) (Swebok Evolution: IEEE Computer Society n.d. ).
Apart from the model curricula, and bodies of knowledge, there also exist some standards related to the database and its different modules: ISO/IEC 9075–1:2016 (Computing Curricula, 1991 ), ISO/IEC 10,026–1: 1998 (Suryn, 2003 ).
We also utilize advices from some studies (Elberzhager et al., 2012 ; Keele et al., 2007 ) to search for relevant papers. In order to conduct this systematic study, it is essential to formulate the primary research questions (Mushtaq et al., 2017 ). Since the data management techniques and software are evolving rapidly, the database curriculum should also be updated accordingly to meet these new requirements. Some authors have described ways of updating the content of courses to keep pace with specific developments in the field and others have developed new database curricula to keep up with the new data management techniques.
Furthermore, some authors have suggested updates for the database curriculum based on the continuously evolving technology and introduction of big data. For instance Bhogal et al. ( 2012 ) have shown that database curricula need to be updated and modernized, which can be achieved by extending the current database concepts that cover the strategies to handle the ever changing user requirements and how database technology has evolved to meet the requirements. Likewise, Picciano ( 2012 ) examines the evolving world of big data and analytics in American higher education. According to the author, the “data driven” decision making method should be used to help the institutes evaluate strategies that can improve retention and update the curriculum that has big data basic concepts and applications, since data driven decision making has already entered in the big data and learning analytic era. Furthermore, Marshall ( 2011 ) presented the challenges faced when developing a curriculum for a Computer Science degree program in the South African context that is earmarked for international recognition. According to the author, the Curricula needs to adhere both to the policy and content requirements in order to be rated as being of a particular quality.
Similarly, some studies (Abourezq & Idrissi, 2016 ; Mingyu et al., 2017 ) described big data influence from a social perspective and also proceeded with the gaps in database curriculum of computer science, especially, in the big data era and discovers the teaching improvements in practical and theoretical teaching mode, teaching content and teaching practice platform in database curriculum. Also Silva et al. ( 2016 ) propose teaching SQL as a general language that can be used in a wide range of database systems from traditional relational database management systems to big data systems.
On the other hand, different authors have developed a database curriculum based on the different academic background of students. Such as, Dean and Milani ( 1995 ) have recommended changes in computer science curricula based on the practice in United Stated Military Academy (USMA). They emphasized greatly on the practical demonstration of the topic rather than the theoretical explanation. Especially, for the non-computer science major students. Furthermore, Urban and Dietrich ( 2001 ) described the development of a second course on database systems for undergraduates, preparing students for the advanced database concepts that they will exercise in the industry. They also shared their experience with teaching the course, elaborating on the topics and assignments. Also, Andersson et al. ( 2019 ) proposed variations in core topics of database management course for the students with the engineering background. Moreover, Dietrich et al. ( 2014 ) described two animations developed with images and color that visually and dynamically introduce fundamental relational database concepts and querying to students of many majors. The goal is that the educators, in diverse academic disciplines, should be able to incorporate these animations in their existing courses to meet their pedagogical needs.
The information systems have evolved into large scale distributed systems that store and process a huge amount of data across different servers, and process them using different distributed data processing frameworks. This evolution has given birth to new paradigms in database systems domain termed as NoSQL and Big Data systems, which significantly deviate from conventional relational and distributed database management systems. It is pertinent to mention that in order to offer a sustainable and practical CS education, these new paradigms and methodologies as shown in Fig. 5 should be included into database education (Kleiner, 2015 ). Tables Tables9 9 and and10 10 shows the summarized findings of the curriculum based reviewed studies. This section also proposed appropriate text book based on the theory, project, and practice-based teaching methodology as shown in Table Table9. 9 . The proposed books are selected purely on the bases of their usage in top universities around the world such as, Massachusetts Institute of Technology, Stanford University, Harvard University, University of Oxford, University of Cambridge and, University of Singapore and the coverage of core topics mentioned in the database curriculum.

Concepts in Database Systems Education (Kleiner, 2015 )
Recommended text books for DSE
Curriculum: Findings of Reviewed Literature
RQ.2 Evolution of DSE research
This section discusses the evolution of database while focusing the DSE over the past 25 years as shown in Fig. 6 .

Evolution of DSE studies
This study shows that there is significant increase in research in DSE after 2004 with 78% of the selected papers are published after 2004. The main reason of this outcome is that some of the papers are published in well-recognized channels like IEEE Transactions on Education, ACM Transactions on Computing Education, International Conference on Computer Science and Education (ICCSE), and Teaching, Learning and Assessment of Database (TLAD) workshop. It is also evident that several of these papers were published before 2004 and only a few articles were published during late 1990s. This is because of the fact that DSE started to gain interest after the introduction of Body of Knowledge and DSE standards. The data intensive scientific discovery has been discussed as the fourth paradigm (Hey et al., 2009 ): where the first involves empirical science and observations; second contains theoretical science and mathematically driven insights; third considers computational science and simulation driven insights; while the fourth involves data driven insights of modern scientific research.
Over the past few decades, students have gone from attending one-room class to having the world at their fingertips, and it is a great challenge for the instructors to develop the interest of students in learning database. This challenge has led to the development of the different types of interactive tools to help the instructors teach DSE in this technology oriented era. Keeping the importance of interactive tools in DSE in perspective, various authors have proposed different interactive tools over the years, such as during 1995–2003, when different authors proposed various interactive tools. Some studies (Abut & Ozturk, 1997 ; Mcintyre et al., 1995 ) introduced state of the art interactive tools to teach and enhance the collaborative learning among the students. Similarly, during 2004–2005 more interactive tools in the field of DSE were proposed such as Pahl et al. ( 2004 ), Connolly et al. ( 2005 ) introduced multimedia system based interactive model and game based collaborative learning environment.
The Internet has started to become more common in the first decade of the twenty-first century and its positive impact on the education sector was undeniable. Cost effective, student teacher peer interaction, keeping in touch with the latest information were the main reasons which made the instructors employ web-based tools to teach database in the education sector. Due to this spike in the demand of web-based tools, authors also started to introduce new instruments to assist with teaching database. In 2007 Regueras et al. ( 2007 ) proposed an e-learning tool named QUEST with a feedback module to help the students to learn from their mistakes. Similarly, in 2010, multiple authors have proposed and evaluated various web-based tools. Cvetanovic et al. ( 2010 ) proposed ADVICE with the functionality to monitor student’s progress, while, few authors (Wang et al., 2010 ) proposed Metube which is a variation of YouTube. Furthermore, Nelson and Fatimazahra ( 2010 ) evaluated different web-based tools to highlight the complexities of using these web-based instruments.
Technology has changed the teaching methods in the education sector but technology cannot replace teachers, and despite the amount of time most students spend online, virtual learning will never recreate the teacher-student bond. In the modern era, innovation in technology used in educational sectors is not meant to replace the instructors or teaching methods.
During the 1990s some studies (Dietrich & Urban, 1996 ; Urban & Dietrich, 1997 ) proposed learning and teaching methods respectively keeping the evolving technology in view. The highlight of their work was project deliverables and assignments where students progressively advanced to a step-by-step extension, from a tutorial exercise and then attempting more difficult extension of assignment.
During 2002–2007 various authors have discussed a number of teaching and learning methods to keep up the pace with the ever changing database technology, such as Connolly and Begg ( 2006 ) proposing a constructive approach to teach database analysis and design. Similarly, Prince and Felder ( 2006 ) reviewed the effectiveness of inquiry learning, problem based learning, project-based learning, case-based teaching, discovery learning, and just-in-time teaching. Also, McIntyre et al. (Mcintyre et al., 1995 ) brought to light the impact of convergence of European Union (EU) in different universities across Europe. They suggested a reconstruction of teaching and learning methodologies in order to effectively teach database.
During 2008–2013 more work had been done to address the different methods of teaching and learning in the field of DSE, like the work of Dominguez and Jaime ( 2010 ) who proposed an active learning approach. The focus of their study was to develop the interest of students in designing and developing databases. Also, Zheng and Dong ( 2011 ) have highlighted various characteristics of the database course and its teaching content. Similarly, Yuelan et al. ( 2011 ) have reformed database teaching methods. The main focus of their study were the Modern ways of education, project driven approach, strengthening the experimental aspects, and improving the traditional assessment method. Likewise, Al-Shuaily ( 2012 ) has explored 4 cognitive factors that can affect the learning process of database. The main focus of their study was to facilitate the students in learning SQL. Subsequently, Chen et al. ( 2012 ) also proposed scaffolding-based concept mapping strategy. This strategy helps the students to better understand database management courses. Correspondingly, Martin et al. ( 2013 ) discussed various collaborative learning techniques in the field of DSE while keeping database as an introductory course.
In the years between 2014 and 2021, research in the field of DSE increased, which was the main reason that the most of teaching, learning and assessment methods were proposed and discussed during this period. Rashid and Al-Radhy ( 2014 ) discussed the issues of traditional teaching, learning, assessing methods of database courses at different universities in Kurdistan and the main focus of their study being reformation issues, such as absence of teaching determination and contradiction between content and theory. Similarly, Wang and Chen ( 2014 ) summarized the main problems in teaching the traditional database theory and its application. Curriculum assessment mode was the main focus of their study. Eaglestone and Nunes ( 2004 ) shared their experiences of delivering a databases design course at Sheffield University. Their focus of study included was to teach the database design module to a diverse group of students from different backgrounds. Rashid ( 2015 ) discussed some important features of database courses, whereby reforming the conventional teaching, learning, and assessing strategies of database courses at universities were the main focus of this study. Kui et al. ( 2018 ) reformed the teaching mode of database courses based on flipped classroom. Initiative learning of database courses was their main focus in this study. Similarly, Zhang et al. ( 2018 ) discussed several effective classroom teaching measures. The main focus of their study was teaching content, teaching methods, teaching evaluation and assessment methods. Cai and Gao ( 2019 ) also carried out the teaching reforms in the database course of liberal arts. Diversified teaching modes, such as flipping classroom, case oriented teaching and task oriented were the focus of their study. Teaching Kawash et al. ( 2020 ) proposed a learning approach called Graded Group Activities (GGAs). Their main focus of the study was reforming learning and assessment method.
Database course covers several topics that range from data modeling to data implementation and examination. Over the years, various authors have given their suggestions to update these topics in database curriculum to meet the requirements of modern technologies. On the other hand, authors have also proposed a new curriculum for the students of different academic backgrounds and different areas. These reformations in curriculum helped the students in their preparation, practically and theoretically, and enabled them to compete in the competitive market after graduation.
During 2003 and 2006 authors have proposed various suggestions to update and develop computer science curriculum across different universities. Robbert and Ricardo ( 2003 ) evaluated three reviews from 1999 to 2002 that were given to the groups of educators. The focus of their study was to highlight the trends that occurred in database curriculum. Also, Calero et al. ( 2003 ) proposed a first draft for this Database Body of Knowledge (DBBOK). Database (DB), Database Design (DBD), Database Administration (DBAd), Database Application (DBAp) and Advance Databases (ADVDB) were the main focus of their study. Furthermore, Conklin and Heinrichs (Conklin & Heinrichs, 2005 ) compared the content included in 13 database textbooks and the main focus of their study was IS 2002, CC2001, and CC2004 model curricula.
The years from 2007 and 2011, authors managed to developed various database curricula, like Luo et al. ( 2008 ) developed curricula in Zhejiang University City College. The aim of their study to nurture students to be qualified computer scientists. Likewise, Dietrich et al. ( 2008 ) proposed the techniques to assess the development of an advanced database course. The purpose behind the addition of an advanced database course at undergraduate level was to prepare the students to respond to industrial requirements. Also, Marshall ( 2011 ) developed a new database curriculum for Computer Science degree program in the South African context.
During 2012 and 2021 various authors suggested updates for the database curriculum such as Bhogal et al. ( 2012 ) who suggested updating and modernizing the database curriculum. Data management and data analytics were the focus of their study. Similarly, Picciano ( 2012 ) examined the curriculum in the higher level of American education. The focus of their study was big data and analytics. Also, Zhanquan et al. ( 2016 ) proposed the design for the course content and teaching methods in the classroom. Massive Open Online Courses (MOOCs) were the focus of their study. Likewise, Mingyu et al. ( 2017 ) suggested updating the database curriculum while keeping new technology concerning the database in perspective. The focus of their study was big data.
The above discussion clearly shows that the SQL is most discussed topic in the literature where more than 25% of the studies have discussed it in the previous decade as shown in Fig. 7 . It is pertinent to mention that other SQL databases such as Oracle, MS access are discussed under the SQL banner (Chen et al., 2012 ; Hou & Chen, 2010 ; Wang & Chen, 2014 ). It is mainly because of its ability to handle data in a relational database management system and direct implementation of database theoretical concepts. Also, other database topics such as transaction management, application programming etc. are also the main highlights of the topics discussed in the literature.

Evolution of Database topics discussed in literature
Research synthesis, advice for instructors, and way forward
This section presents the synthesized information extracted after reading and analyzing the research articles considered in this study. To this end, it firstly contextualizes the tools and methods to help the instructors find suitable tools and methods for their settings. Similarly, developments in curriculum design have also been discussed. Subsequently, general advice for instructors have been discussed. Lastly, promising future research directions for developing new tools, methods, and for revising the curriculum have also been discussed in this section.
Methods, tools, and curriculum
Methods and tools.
Web-based tools proposed by Cvetanovic et al. ( 2010 ) and Wang et al. ( 2010 ) have been quite useful, as they are growing increasingly pertinent as online mode of education is prevalent all around the globe during COVID-19. On the other hand, interactive tools and smart class room methodology has also been used successfully to develop the interest of students in database class. (Brusilovsky et al., 2010 ; Connolly et al., 2005 ; Pahl et al., 2004 ; Canedo et al., 2021 ; Ko et al., 2021 ).
One of the most promising combination of methodology and tool has been proposed by Cvetanovic et al. ( 2010 ), whereby they developed a tool named ADVICE that helps students learn and implement database concepts while using project centric methodology, while a game based collaborative learning environment was proposed by Connolly et al. ( 2005 ) that involves a methodology comprising of modeling, articulation, feedback, and exploration. As a whole, project centric teaching (Connolly & Begg, 2006 ; Domínguez & Jaime, 2010 ) and teaching database design and problem solving skills Wang and Chen ( 2014 ), are two successful approaches for DSE. Whereas, other studies (Urban & Dietrich, 1997 ) proposed teaching methods that are more inclined towards practicing database concepts. While a topic specific approach has been proposed by Abbasi et al. ( 2016 ), Taipalus et al. ( 2018 ) and Silva et al. ( 2016 ) to teach and learn SQL. On the other hand, Cai and Gao ( 2019 ) developed a teaching method for students who do not have a computer science background. Lastly, some useful ways for defining assessments for DSE have been proposed by Kawash et al. ( 2020 ) and Zhang et al. ( 2018 ).
Curriculum of database adopted by various institutes around the world does not address how to teach the database course to the students who do not have a strong computer science background. Such as Marshall ( 2012 ), Luo et al. ( 2008 ) and Zhanquan et al. ( 2016 ) have proposed the updates in current database curriculum for the students who are not from computer science background. While Abid et al. ( 2015 ) proposed a combined course content and various methodologies that can be used for teaching database systems course. On the other hand, current database curriculum does not include the topics related to latest technologies in database domain. This factor was discussed by many other studies as well (Bhogal et al., 2012 ; Mehmood et al., 2020 ; Picciano, 2012 ).
Guidelines for instructors
The major conclusion of this study are the suggestions based on the impact and importance for instructors who are teaching DSE. Furthermore, an overview of productivity of every method can be provided by the empirical studies. These instructions are for instructors which are the focal audience of this study. These suggestions are subjective opinions after literature analysis in form of guidelines according to the authors and their meaning and purpose were maintained. According to the literature reviewed, various issues have been found in this section. Some other issues were also found, but those were not relevant to DSE. Following are some suggestions that provide interesting information:
Project centric and applied approach
- To inculcate database development skills for the students, basic elements of database development need to be incorporated into teaching and learning at all levels including undergraduate studies (Bakar et al., 2011 ). To fulfill this objective, instructors should also improve the data quality in DSE by assigning the projects and assignments to the students where they can assess, measure and improve the data quality using already deployed databases. They should demonstrate that the quality of data is determined not only by the effective design of a database, but also through the perception of the end user (Mathieu & Khalil, 1997 )
- The gap between the database course theory and industrial practice is big. Fresh graduate students find it difficult to cope up with the industrial pressure because of the contrast between what they have been taught in institutes and its application in industry (Allsopp et al., 2006 ). Involve top performers from classes in industrial projects so that they are able to acquiring sufficient knowledge and practice, especially for post graduate courses. There must be some other activities in which industry practitioners come and present the real projects and also share their industrial experiences with the students. The gap between theoretical and the practical sides of database has been identified by Myers and Skinner ( 1997 ). In order to build practical DS concepts, instructors should provide the students an accurate view of reality and proper tools.
Importance of software development standards and impact of DB in software success
- They should have the strategies, ability and skills that can align the DSE course with the contemporary Global Software Development (GSD) (Akbar & Safdar, 2015 ; Damian et al., 2006 ).
- Enable the students to explain the approaches to problem solving, development tools and methodologies. Also, the DS courses are usually taught in normal lecture format. The result of this method is that students cannot see the influence on the success or failure of projects because they do not realize the importance of DS activities.
Pedagogy and the use of education technology
- Some studies have shown that teaching through play and practical activities helps to improve the knowledge and learning outcome of students (Dicheva et al., 2015 ).
- Interactive classrooms can help the instructors to deliver their lecture in a more effective way by using virtual white board, digital textbooks, and data over network(Abut & Ozturk, 1997 ). We suggest that in order to follow the new concept of smart classroom, instructors should use the experience of Yau and Karim ( 2003 ) which benefits in cooperative learning among students and can also be adopted in DSE.
- The instructors also need to update themselves with full spectrum of technology in education, in general, and for DSE, in particular. This is becoming more imperative as during COVID the world is relying strongly on the use of technology, particularly in education sector.
Periodic Curriculum Revision
- There is also a need to revisit the existing series of courses periodically, so that they are able to offer the following benefits: (a) include the modern day database system concepts; (b) can be offered as a specialization track; (c) a specialized undergraduate degree program may also be designed.
DSE: Way forward
This research combines a significant work done on DSE at one place, thus providing a point to find better ways forward in order to improvise different possible dimensions for improving the teaching process of a database system course in future. This section discusses technology, methods, and modifications in curriculum would most impact the delivery of lectures in coming years.
Several tools have already been developed for effective teaching and learning in database systems. However, there is a great room for developing new tools. Recent rise of the notion of “serious games” is marking its success in several domains. Majority of the research work discussed in this review revolves around web-based tools. The success of serious games invites researchers to explore this new paradigm of developing useful tools for learning and practice database systems concepts.
Likewise, due to COVID-19 the world is setting up new norms, which are expected to affect the methods of teaching as well. This invites the researchers to design, develop, and test flexible tools for online teaching in a more interactive manner. At the same time, it is also imperative to devise new techniques for assessments, especially conducting online exams at massive scale. Moreover, the researchers can implement the idea of instructional design in web-based teaching in which an online classroom can be designed around the learners’ unique backgrounds and effectively delivering the concepts that are considered to be highly important by the instructors.
The teaching, learning and assessment methods discussed in this study can help the instructors to improve their methods in order to teach the database system course in a better way. It is noticed that only 16% of authors have the assessment methods as their focus of study, which clearly highlights that there is still plenty of work needed to be done in this particular domain. Assessment techniques in the database course will help the learners to learn from their mistakes. Also, instructors must realize that there is a massive gap between database theory and practice which can only be reduced with maximum practice and real world database projects.
Similarly, the technology is continuously influencing the development and expansion of modern education, whereas the instructors’ abilities to teach using online platforms are critical to the quality of online education.
In the same way, the ideas like flipped classroom in which students have to prepare the lesson prior to the class can be implemented on web-based teaching. This ensures that the class time can be used for further discussion of the lesson, share ideas and allow students to interact in a dynamic learning environment.
The increasing impact of big data systems, and data science and its anticipated impact on the job market invites the researchers to revisit the fundamental course of database systems as well. There is a need to extend the boundaries of existing contents by including the concepts related to distributed big data systems data storage, processing, and transaction management, with possible glimpse of modern tools and technologies.
As a whole, an interesting and long term extension is to establish a generic and comprehensive framework that engages all the stakeholders with the support of technology to make the teaching, learning, practicing, and assessing easier and more effective.
This SLR presents review on the research work published in the area of database system education, with particular focus on teaching the first course in database systems. The study was carried out by systematically selecting research papers published between 1995 and 2021. Based on the study, a high level categorization presents a taxonomy of the published under the heads of Tools, Methods, and Curriculum. All the selected articles were evaluated on the basis of a quality criteria. Several methods have been developed to effectively teach the database course. These methods focus on improving learning experience, improve student satisfaction, improve students’ course performance, or support the instructors. Similarly, many tools have been developed, whereby some tools are topic based, while others are general purpose tools that apply for whole course. Similarly, the curriculum development activities have also been discussed, where some guidelines provided by ACM/IEEE along with certain standards have been discussed. Apart from this, the evolution in these three areas has also been presented which shows that the researchers have been presenting many different teaching methods throughout the selected period; however, there is a decrease in research articles that address the curriculum and tools in the past five years. Besides, some guidelines for the instructors have also been shared. Also, this SLR proposes a way forward in DSE by emphasizing on the tools: that need to be developed to facilitate instructors and students especially post Covid-19 era, methods: to be adopted by the instructors to close the gap between the theory and practical, Database curricula update after the introduction of emerging technologies such as big data and data science. We also urge that the recognized publication venues for database research including VLDB, ICDM, EDBT should also consider publishing articles related to DSE. The study also highlights the importance of reviving the curricula, tools, and methodologies to cater for recent advancements in the field of database systems.
Data availability
Code availability, declarations.
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
- Abbasi, S., Kazi, H., Khowaja, K., Abelló Gamazo, A., Burgués Illa, X., Casany Guerrero, M. J., Martin Escofet, C., Quer, C., Rodriguez González, M. E., Romero Moral, Ó., Urpi Tubella, A., Abid, A., Farooq, M. S., Raza, I., Farooq, U., Abid, K., Hussain, N., Abid, K., Ahmad, F., …, Yatim, N. F. M. (2016). Research trends in enterprise service bus (ESB) applications: A systematic mapping study. Journal of Informetrics, 27 (1), 217–220.
- Abbasi, S., Kazi, H., & Khowaja, K. (2017). A systematic review of learning object oriented programming through serious games and programming approaches. 2017 4th IEEE International Conference on Engineering Technologies and Applied Sciences (ICETAS) , 1–6.
- Abelló Gamazo A, Burgués Illa X, Casany Guerrero MJ, Martin Escofet C, Quer C, Rodriguez González ME, Romero Moral Ó, Urpi Tubella A. A software tool for E-assessment of relational database skills. International Journal of Engineering Education. 2016; 32 (3A):1289–1312. [ Google Scholar ]
- Abid A, Farooq MS, Raza I, Farooq U, Abid K. Variants of teaching first course in database systems. Bulletin of Education and Research. 2015; 37 (2):9–25. [ Google Scholar ]
- Abid A, Hussain N, Abid K, Ahmad F, Farooq MS, Farooq U, Khan SA, Khan YD, Naeem MA, Sabir N. A survey on search results diversification techniques. Neural Computing and Applications. 2016; 27 (5):1207–1229. [ Google Scholar ]
- Abourezq, M., & Idrissi, A. (2016). Database-as-a-service for big data: An overview. International Journal of Advanced Computer Science and Applications (IJACSA) , 7 (1).
- Abut, H., & Ozturk, Y. (1997). Interactive classroom for DSP/communication courses. 1997 IEEE International Conference on Acoustics, Speech, and Signal Processing , 1 , 15–18.
- Adams ES, Granger M, Goelman D, Ricardo C. Managing the introductory database course: What goes in and what comes out? ACM SIGCSE Bulletin. 2004; 36 (1):497–498. [ Google Scholar ]
- Akbar, R., & Safdar, S. (2015). A short review of global software development (gsd) and latest software development trends. 2015 International Conference on Computer, Communications, and Control Technology (I4CT) , 314–317.
- Allsopp DH, DeMarie D, Alvarez-McHatton P, Doone E. Bridging the gap between theory and practice: Connecting courses with field experiences. Teacher Education Quarterly. 2006; 33 (1):19–35. [ Google Scholar ]
- Alrumaih, H. (2016). ACM/IEEE-CS information technology curriculum 2017: status report. Proceedings of the 1st National Computing Colleges Conference (NC3 2016) .
- Al-Shuaily, H. (2012). Analyzing the influence of SQL teaching and learning methods and approaches. 10 Th International Workshop on the Teaching, Learning and Assessment of Databases , 3.
- Amadio, W., Riyami, B., Mansouri, K., Poirier, F., Ramzan, M., Abid, A., Khan, H. U., Awan, S. M., Ismail, A., Ahmed, M., Ilyas, M., Mahmood, A., Hey, A. J. G., Tansley, S., Tolle, K. M., others, Tehseen, R., Farooq, M. S., Abid, A., …, Fatimazahra, E. (2003). The fourth paradigm: data-intensive scientific discovery. Innovation in Teaching and Learning in Information and Computer Sciences , 1 (1), 823–828. https://www.iso.org/standard/27614.html
- Amadio, W. (2003). The dilemma of Team Learning: An assessment from the SQL programming classroom . 823–828.
- Ampatzoglou A, Charalampidou S, Stamelos I. Research state of the art on GoF design patterns: A mapping study. Journal of Systems and Software. 2013; 86 (7):1945–1964. [ Google Scholar ]
- Andersson C, Kroisandt G, Logofatu D. Including active learning in an online database management course for industrial engineering students. IEEE Global Engineering Education Conference (EDUCON) 2019; 2019 :217–220. [ Google Scholar ]
- Aria M, Cuccurullo C. bibliometrix: An R-tool for comprehensive science mapping analysis. Journal of Informetrics. 2017; 11 (4):959–975. [ Google Scholar ]
- Aziz O, Farooq MS, Abid A, Saher R, Aslam N. Research trends in enterprise service bus (ESB) applications: A systematic mapping study. IEEE Access. 2020; 8 :31180–31197. [ Google Scholar ]
- Bakar MA, Jailani N, Shukur Z, Yatim NFM. Final year supervision management system as a tool for monitoring computer science projects. Procedia-Social and Behavioral Sciences. 2011; 18 :273–281. [ Google Scholar ]
- Beecham S, Baddoo N, Hall T, Robinson H, Sharp H. Motivation in Software Engineering: A systematic literature review. Information and Software Technology. 2008; 50 (9–10):860–878. [ Google Scholar ]
- Bhogal, J. K., Cox, S., & Maitland, K. (2012). Roadmap for Modernizing Database Curricula. 10 Th International Workshop on the Teaching, Learning and Assessment of Databases , 73.
- Bishop, M., Burley, D., Buck, S., Ekstrom, J. J., Futcher, L., Gibson, D., ... & Parrish, A. (2017, May). Cybersecurity curricular guidelines . In IFIP World Conference on Information Security Education (pp. 3–13). Cham: Springer.
- Brady A, Bruce K, Noonan R, Tucker A, Walker H. The 2003 model curriculum for a liberal arts degree in computer science: preliminary report. ACM SIGCSE Bulletin. 2004; 36 (1):282–283. [ Google Scholar ]
- Brusilovsky P, Sosnovsky S, Lee DH, Yudelson M, Zadorozhny V, Zhou X. An open integrated exploratorium for database courses. AcM SIGcSE Bulletin. 2008; 40 (3):22–26. [ Google Scholar ]
- Brusilovsky P, Sosnovsky S, Yudelson MV, Lee DH, Zadorozhny V, Zhou X. Learning SQL programming with interactive tools: From integration to personalization. ACM Transactions on Computing Education (TOCE) 2010; 9 (4):1–15. [ Google Scholar ]
- Cai, Y., & Gao, T. (2019). Teaching Reform in Database Course for Liberal Arts Majors under the Background of" Internet Plus". 2018 6th International Education, Economics, Social Science, Arts, Sports and Management Engineering Conference (IEESASM 2018) , 208–213.
- Calderon KR, Vij RS, Mattana J, Jhaveri KD. Innovative teaching tools in nephrology. Kidney International. 2011; 79 (8):797–799. [ PubMed ] [ Google Scholar ]
- Calero C, Piattini M, Ruiz F. Towards a database body of knowledge: A study from Spain. ACM SIGMOD Record. 2003; 32 (2):48–53. [ Google Scholar ]
- Canedo, E. D., Bandeira, I. N., & Costa, P. H. T. (2021). Challenges of database systems teaching amidst the Covid-19 pandemic. In 2021 IEEE Frontiers in Education Conference (FIE) (pp. 1–9). IEEE.
- Chen H-H, Chen Y-J, Chen K-J. The design and effect of a scaffolded concept mapping strategy on learning performance in an undergraduate database course. IEEE Transactions on Education. 2012; 56 (3):300–307. [ Google Scholar ]
- Cobo MJ, López-Herrera AG, Herrera-Viedma E, Herrera F. SciMAT: A new science mapping analysis software tool. Journal of the American Society for Information Science and Technology. 2012; 63 (8):1609–1630. [ Google Scholar ]
- Conklin M, Heinrichs L. In search of the right database text. Journal of Computing Sciences in Colleges. 2005; 21 (2):305–312. [ Google Scholar ]
- Connolly, T. M., & Begg, C. E. (2006). A constructivist-based approach to teaching database analysis and design. Journal of Information Systems Education , 17 (1).
- Connolly, T. M., Stansfield, M., & McLellan, E. (2005). An online games-based collaborative learning environment to teach database design. Web-Based Education: Proceedings of the Fourth IASTED International Conference(WBE-2005) .
- Curricula Computing. (1991). Report of the ACM/IEEE-CS Joint Curriculum Task Force. Technical Report . New York: Association for Computing Machinery.
- Cvetanovic M, Radivojevic Z, Blagojevic V, Bojovic M. ADVICE—Educational system for teaching database courses. IEEE Transactions on Education. 2010; 54 (3):398–409. [ Google Scholar ]
- Damian, D., Hadwin, A., & Al-Ani, B. (2006). Instructional design and assessment strategies for teaching global software development: a framework. Proceedings of the 28th International Conference on Software Engineering , 685–690.
- Dean, T. J., & Milani, W. G. (1995). Transforming a database systems and design course for non computer science majors. Proceedings Frontiers in Education 1995 25th Annual Conference. Engineering Education for the 21st Century , 2 , 4b2--17.
- Dicheva, D., Dichev, C., Agre, G., & Angelova, G. (2015). Gamification in education: A systematic mapping study. Journal of Educational Technology \& Society , 18 (3), 75–88.
- Dietrich SW, Urban SD, Haag S. Developing advanced courses for undergraduates: A case study in databases. IEEE Transactions on Education. 2008; 51 (1):138–144. [ Google Scholar ]
- Dietrich SW, Goelman D, Borror CM, Crook SM. An animated introduction to relational databases for many majors. IEEE Transactions on Education. 2014; 58 (2):81–89. [ Google Scholar ]
- Dietrich, S. W., & Urban, S. D. (1996). Database theory in practice: learning from cooperative group projects. Proceedings of the Twenty-Seventh SIGCSE Technical Symposium on Computer Science Education , 112–116.
- Dominguez, C., & Jaime, A. (2010). Database design learning: A project-based approach organized through a course management system. Computers \& Education , 55 (3), 1312–1320.
- Eaglestone, B., & Nunes, M. B. (2004). Pragmatics and practicalities of teaching and learning in the quicksand of database syllabuses. Journal of Innovations in Teaching and Learning for Information and Computer Sciences , 3 (1).
- Efendiouglu A, Yelken TY. Programmed instruction versus meaningful learning theory in teaching basic structured query language (SQL) in computer lesson. Computers & Education. 2010; 55 (3):1287–1299. [ Google Scholar ]
- Elberzhager F, Münch J, Nha VTN. A systematic mapping study on the combination of static and dynamic quality assurance techniques. Information and Software Technology. 2012; 54 (1):1–15. [ Google Scholar ]
- Etemad M, Küpçü A. Verifiable database outsourcing supporting join. Journal of Network and Computer Applications. 2018; 115 :1–19. [ Google Scholar ]
- Farooq MS, Riaz S, Abid A, Abid K, Naeem MA. A Survey on the role of IoT in agriculture for the implementation of smart farming. IEEE Access. 2019; 7 :156237–156271. [ Google Scholar ]
- Farooq MS, Riaz S, Abid A, Umer T, Zikria YB. Role of IoT technology in agriculture: A systematic literature review. Electronics. 2020; 9 (2):319. [ Google Scholar ]
- Farooq U, Rahim MSM, Sabir N, Hussain A, Abid A. Advances in machine translation for sign language: Approaches, limitations, and challenges. Neural Computing and Applications. 2021; 33 (21):14357–14399. [ Google Scholar ]
- Fisher, D., & Khine, M. S. (2006). Contemporary approaches to research on learning environments: Worldviews . World Scientific.
- Garcia-Molina, H. (2008). Database systems: the complete book . Pearson Education India.
- Garousi V, Mesbah A, Betin-Can A, Mirshokraie S. A systematic mapping study of web application testing. Information and Software Technology. 2013; 55 (8):1374–1396. [ Google Scholar ]
- Gudivada, V. N., Nandigam, J., & Tao, Y. (2007). Enhancing student learning in database courses with large data sets. 2007 37th Annual Frontiers In Education Conference-Global Engineering: Knowledge Without Borders, Opportunities Without Passports , S2D--13.
- Hey, A. J. G., Tansley, S., Tolle, K. M., & others. (2009). The fourth paradigm: data-intensive scientific discovery (Vol. 1). Microsoft research Redmond, WA.
- Holliday, M. A., & Wang, J. Z. (2009). A multimedia database project and the evolution of the database course. 2009 39th IEEE Frontiers in Education Conference , 1–6.
- Hou, S., & Chen, S. (2010). Research on applying the theory of Blending Learning on Access Database Programming Course teaching. 2010 2nd International Conference on Education Technology and Computer , 3 , V3--396.
- Irby DM, Wilkerson L. Educational innovations in academic medicine and environmental trends. Journal of General Internal Medicine. 2003; 18 (5):370–376. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Ishaq K, Zin NAM, Rosdi F, Jehanghir M, Ishaq S, Abid A. Mobile-assisted and gamification-based language learning: A systematic literature review. PeerJ Computer Science. 2021; 7 :e496. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Joint Task Force on Computing Curricula, A. F. C. M. (acm), & Society, I. C. (2013). Computer science curricula 2013: Curriculum guidelines for undergraduate degree programs in computer science . New York, NY, USA: Association for Computing Machinery.
- Juxiang R, Zhihong N. Taking database design as trunk line of database courses. Fourth International Conference on Computational and Information Sciences. 2012; 2012 :767–769. [ Google Scholar ]
- Kawash, J., Jarada, T., & Moshirpour, M. (2020). Group exams as learning tools: Evidence from an undergraduate database course. Proceedings of the 51st ACM Technical Symposium on Computer Science Education , 626–632.
- Keele, S., et al. (2007). Guidelines for performing systematic literature reviews in software engineering .
- Kleiner, C. (2015). New Concepts in Database System Education: Experiences and Ideas. Proceedings of the 46th ACM Technical Symposium on Computer Science Education , 698.
- Ko J, Paek S, Park S, Park J. A news big data analysis of issues in higher education in Korea amid the COVID-19 pandemic. Sustainability. 2021; 13 (13):7347. [ Google Scholar ]
- Kui, X., Du, H., Zhong, P., & Liu, W. (2018). Research and application of flipped classroom in database course. 2018 13th International Conference on Computer Science \& Education (ICCSE) , 1–5.
- Landis, J. R., & Koch, G. G. (1977). The measurement of observer agreement for categorical data. Biometrics , 159–174. [ PubMed ]
- Lunt, B., Ekstrom, J., Gorka, S., Hislop, G., Kamali, R., Lawson, E., ... & Reichgelt, H. (2008). Curriculum guidelines for undergraduate degree programs in information technology . ACM.
- Luo, R., Wu, M., Zhu, Y., & Shen, Y. (2008). Exploration of Curriculum Structures and Educational Models of Database Applications. 2008 The 9th International Conference for Young Computer Scientists , 2664–2668.
- Luxton-Reilly, A., Albluwi, I., Becker, B. A., Giannakos, M., Kumar, A. N., Ott, L., Paterson, J., Scott, M. J., Sheard, J., & Szabo, C. (2018). Introductory programming: a systematic literature review. Proceedings Companion of the 23rd Annual ACM Conference on Innovation and Technology in Computer Science Education , 55–106.
- Manzoor MF, Abid A, Farooq MS, Nawaz NA, Farooq U. Resource allocation techniques in cloud computing: A review and future directions. Elektronika Ir Elektrotechnika. 2020; 26 (6):40–51. doi: 10.5755/j01.eie.26.6.25865. [ CrossRef ] [ Google Scholar ]
- Marshall, L. (2011). Developing a computer science curriculum in the South African context. CSERC , 9–19.
- Marshall, L. (2012). A comparison of the core aspects of the acm/ieee computer science curriculum 2013 strawman report with the specified core of cc2001 and cs2008 review. Proceedings of Second Computer Science Education Research Conference , 29–34.
- Martin C, Urpi T, Casany MJ, Illa XB, Quer C, Rodriguez ME, Abello A. Improving learning in a database course using collaborative learning techniques. The International Journal of Engineering Education. 2013; 29 (4):986–997. [ Google Scholar ]
- Martinez-González MM, Duffing G. Teaching databases in compliance with the European dimension of higher education: Best practices for better competences. Education and Information Technologies. 2007; 12 (4):211–228. [ Google Scholar ]
- Mateo PR, Usaola MP, Alemán JLF. Validating second-order mutation at system level. IEEE Transactions on Software Engineering. 2012; 39 (4):570–587. [ Google Scholar ]
- Mathieu, R. G., & Khalil, O. (1997). Teaching Data Quality in the Undergraduate Database Course. IQ , 249–266.
- Mcintyre, D. R., Pu, H.-C., & Wolff, F. G. (1995). Use of software tools in teaching relational database design. Computers \& Education , 24 (4), 279–286.
- Mehmood E, Abid A, Farooq MS, Nawaz NA. Curriculum, teaching and learning, and assessments for introductory programming course. IEEE Access. 2020; 8 :125961–125981. [ Google Scholar ]
- Meier, R., Barnicki, S. L., Barnekow, W., & Durant, E. (2008). Work in progress-Year 2 results from a balanced, freshman-first computer engineering curriculum. In 38th Annual Frontiers in Education Conference (pp. S1F-17). IEEE.
- Meyer B. Software engineering in the academy. Computer. 2001; 34 (5):28–35. [ Google Scholar ]
- Mingyu, L., Jianping, J., Yi, Z., & Cuili, Z. (2017). Research on the teaching reform of database curriculum major in computer in big data era. 2017 12th International Conference on Computer Science and Education (ICCSE) , 570–573.
- Morien, R. I. (2006). A Critical Evaluation Database Textbooks, Curriculum and Educational Outcomes. Director , 7 .
- Mushtaq Z, Rasool G, Shehzad B. Multilingual source code analysis: A systematic literature review. IEEE Access. 2017; 5 :11307–11336. [ Google Scholar ]
- Myers M, Skinner P. The gap between theory and practice: A database application case study. Journal of International Information Management. 1997; 6 (1):5. [ Google Scholar ]
- Naeem A, Farooq MS, Khelifi A, Abid A. Malignant melanoma classification using deep learning: Datasets, performance measurements, challenges and opportunities. IEEE Access. 2020; 8 :110575–110597. [ Google Scholar ]
- Nagataki, H., Nakano, Y., Nobe, M., Tohyama, T., & Kanemune, S. (2013). A visual learning tool for database operation. Proceedings of the 8th Workshop in Primary and Secondary Computing Education , 39–40.
- Naik, S., & Gajjar, K. (2021). Applying and Evaluating Engagement and Application-Based Learning and Education (ENABLE): A Student-Centered Learning Pedagogy for the Course Database Management System. Journal of Education , 00220574211032319.
- Nelson, D., Stirk, S., Patience, S., & Green, C. (2003). An evaluation of a diverse database teaching curriculum and the impact of research. 1st LTSN Workshop on Teaching, Learning and Assessment of Databases, Coventry .
- Nelson D, Fatimazahra E. Review of Contributions to the Teaching, Learning and Assessment of Databases (TLAD) Workshops. Innovation in Teaching and Learning in Information and Computer Sciences. 2010; 9 (1):78–86. [ Google Scholar ]
- Obaid I, Farooq MS, Abid A. Gamification for recruitment and job training: Model, taxonomy, and challenges. IEEE Access. 2020; 8 :65164–65178. [ Google Scholar ]
- Pahl C, Barrett R, Kenny C. Supporting active database learning and training through interactive multimedia. ACM SIGCSE Bulletin. 2004; 36 (3):27–31. [ Google Scholar ]
- Park, Y., Tajik, A. S., Cafarella, M., & Mozafari, B. (2017). Database learning: Toward a database that becomes smarter every time. Proceedings of the 2017 ACM International Conference on Management of Data , 587–602.
- Picciano AG. The evolution of big data and learning analytics in American higher education. Journal of Asynchronous Learning Networks. 2012; 16 (3):9–20. [ Google Scholar ]
- Prince MJ, Felder RM. Inductive teaching and learning methods: Definitions, comparisons, and research bases. Journal of Engineering Education. 2006; 95 (2):123–138. [ Google Scholar ]
- Ramzan M, Abid A, Khan HU, Awan SM, Ismail A, Ahmed M, Ilyas M, Mahmood A. A review on state-of-the-art violence detection techniques. IEEE Access. 2019; 7 :107560–107575. [ Google Scholar ]
- Rashid, T. A., & Al-Radhy, R. S. (2014). Transformations to issues in teaching, learning, and assessing methods in databases courses. 2014 IEEE International Conference on Teaching, Assessment and Learning for Engineering (TALE) , 252–256.
- Rashid, T. (2015). Investigation of instructing reforms in databases. International Journal of Scientific \& Engineering Research , 6 (8), 64–72.
- Regueras, L. M., Verdú, E., Verdú, M. J., Pérez, M. A., & De Castro, J. P. (2007). E-learning strategies to support databases courses: a case study. First International Conference on Technology, Training and Communication .
- Robbert MA, Ricardo CM. Trends in the evolution of the database curriculum. ACM SIGCSE Bulletin. 2003; 35 (3):139–143. [ Google Scholar ]
- Sahami, M., Guzdial, M., McGettrick, A., & Roach, S. (2011). Setting the stage for computing curricula 2013: computer science--report from the ACM/IEEE-CS joint task force. Proceedings of the 42nd ACM Technical Symposium on Computer Science Education , 161–162.
- Sciore E. SimpleDB: A simple java-based multiuser syst for teaching database internals. ACM SIGCSE Bulletin. 2007; 39 (1):561–565. [ Google Scholar ]
- Shebaro B. Using active learning strategies in teaching introductory database courses. Journal of Computing Sciences in Colleges. 2018; 33 (4):28–36. [ Google Scholar ]
- Sibia, N., & Liut, M. (2022, June). The Positive Effects of using Reflective Prompts in a Database Course. In 1st International Workshop on Data Systems Education (pp. 32–37).
- Silva, Y. N., Almeida, I., & Queiroz, M. (2016). SQL: From traditional databases to big data. Proceedings of the 47th ACM Technical Symposium on Computing Science Education , 413–418.
- Sobel, A. E. K. (2003). Computing Curricula--Software Engineering Volume. Proc. of the Final Draft of the Software Engineering Education Knowledge (SEEK) .
- Suryn, W., Abran, A., & April, A. (2003). ISO/IEC SQuaRE: The second generation of standards for software product quality .
- Svahnberg, M., Aurum, A., & Wohlin, C. (2008). Using students as subjects-an empirical evaluation. Proceedings of the Second ACM-IEEE International Symposium on Empirical Software Engineering and Measurement , 288–290.
- Swebok evolution: IEEE Computer Society. (n.d.). In IEEE Computer Society SWEBOK Evolution Comments . Retrieved March 24, 2021 https://www.computer.org/volunteering/boards-and-committees/professional-educational-activities/software-engineering-committee/swebok-evolution
- Taipalus T, Seppänen V. SQL education: A systematic mapping study and future research agenda. ACM Transactions on Computing Education (TOCE) 2020; 20 (3):1–33. [ Google Scholar ]
- Taipalus T, Siponen M, Vartiainen T. Errors and complications in SQL query formulation. ACM Transactions on Computing Education (TOCE) 2018; 18 (3):1–29. [ Google Scholar ]
- Taipalus, T., & Perälä, P. (2019). What to expect and what to focus on in SQL query teaching. Proceedings of the 50th ACM Technical Symposium on Computer Science Education , 198–203.
- Tehseen R, Farooq MS, Abid A. Earthquake prediction using expert systems: A systematic mapping study. Sustainability. 2020; 12 (6):2420. [ Google Scholar ]
- Urban, S. D., & Dietrich, S. W. (2001). Advanced database concepts for undergraduates: experience with teaching a second course. Proceedings of the Thirty-Second SIGCSE Technical Symposium on Computer Science Education , 357–361.
- Urban SD, Dietrich SW. Integrating the practical use of a database product into a theoretical curriculum. ACM SIGCSE Bulletin. 1997; 29 (1):121–125. [ Google Scholar ]
- Wang, J., & Chen, H. (2014). Research and practice on the teaching reform of database course. International Conference on Education Reform and Modern Management, ERMM .
- Wang, J. Z., Davis, T. A., Westall, J. M., & Srimani, P. K. (2010). Undergraduate database instruction with MeTube. Proceedings of the Fifteenth Annual Conference on Innovation and Technology in Computer Science Education , 279–283.
- Yau, G., & Karim, S. W. (2003). Smart classroom: Enhancing collaborative learning using pervasive computing technology. II American Society… .
- Yue K-B. Using a semi-realistic database to support a database course. Journal of Information Systems Education. 2013; 24 (4):327. [ Google Scholar ]
- Yuelan L, Yiwei L, Yuyan H, Yuefan L. Study on teaching methods of database application courses. Procedia Engineering. 2011; 15 :5425–5428. [ Google Scholar ]
- Zhang, X., Wang, X., Liu, Z., Xue, W., & ZHU, X. (2018). The Exploration and Practice on the Classroom Teaching Reform of the Database Technologies Course in colleges. 2018 3rd International Conference on Modern Management, Education Technology, and Social Science (MMETSS 2018) , 320–323.
- Zhanquan W, Zeping Y, Chunhua G, Fazhi Z, Weibin G. Research of database curriculum construction under the environment of massive open online courses. International Journal of Educational and Pedagogical Sciences. 2016; 10 (12):3873–3877. [ Google Scholar ]
- Zheng, Y., & Dong, J. (2011). Teaching reform and practice of database principles. 2011 6th International Conference on Computer Science \& Education (ICCSE) , 1460–1462.
Information
- Eugene Wu (Instructor) OH: TBA 421 Mudd
- Class: Th 2-4PM
- Syllabus & FAQ
- Reviews Wiki
- Req: W4111 Intro to DB
- Pref: W4112 DB Impl
- Ugrads OK; see Prof Wu
- Proposal 5%
- Paper Draft 10%
- Demo/Poster 10%
- Participation 10% <!–
- Paper Reviews 10%
- Assignments 15% –>
Data management systems are the corner-stone of modern applications, businesses, and science (including data). If you were excited by the topics in 4111, this graduate level course in database systems research will be a deep dive into classic and modern database systems research. Topics will range from classic database system design, modern optimizations in single-machine and multi-machine settings, data cleaning and quality, and application-oriented databases. This semester’s theme will look at how learning has affected many classic data management systems challenges, and also how data management systems support and extends ML needs.
See FAQ for difference between 6113 and the other database courses.
- Class: Th 2-4PM in 829 Mudd
- Instructor: Eugene Wu , OH: Thurs 12-1PM 421 Mudd
- Syllabus & FAQ , Slack , Project , Papers
- Prereqs: W4111 Intro to DB (required), W4112 DB Implementations (recommended). Ugrads OK; see Prof Wu
- Discussion Prep 30%
- Class participation 30%
- Project 40%: Final Presentation 10% , Paper 30%
Recent Announcements
Tentative schedule.
Course design inspired by
- Cal’s CS286
- Waterloo’s CS848
- Colin Raffel’s Role playing seminar
- Carl Vondrick’s self supervision graduate seminar
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Databases articles from across Nature Portfolio
A database is one or more sets of data, for example numbers, characters and images, bundled together with software that enables data to be added, removed or retrieved. Databases can be used to store research data, for example in protein databases and genetic databases, and they organise data into standard formats so that information can readily be obtained.
In an exoplanet atmosphere far, far away
JWST collects vast amounts of information about exoplanets light years away from Earth. Back home, the measured optical constants of laboratory aerosols are critically input parameters in models to interpret the observational results.
- Ella Sciamma-O’Brien
- Thomas Drant
- Nicholas Wogan

Related Subjects
- Genetic databases
- Protein databases
Latest Research and Reviews
The Arctic Plant Aboveground Biomass Synthesis Dataset
- Logan T. Berner
- Kathleen M. Orndahl
- Scott J. Goetz
Real-world evidence of constipation and laxative use in the Korean population with chronic kidney disease from a common data model
- Joon Ho Song
A comprehensive DNA barcoding reference database for Plecoptera of Switzerland
- Laurent Vuataz
- Jean-Paul Reding
- Jean-Luc Gattolliat
EUPRO - A reference database on project-based R&D collaboration networks
- Thomas Scherngell
- Michael Barber
- Xheneta Bilalli Shkodra
MCSdb, a database of proteins residing in membrane contact sites
- Xianrun Pan

Decoding chromatin states by proteomic profiling of nucleosome readers
A multidimensional proteomics analysis of the interactions between around 2,000 nuclear proteins and over 80 modified dinucleosomes representing promoter, enhancer and heterochromatin states provides insights into how chromatin states are decoded by chromatin readers.
- Saulius Lukauskas
- Andrey Tvardovskiy
- Till Bartke
News and Comment
Cosmic recipe book updated.

‘All of Us’ genetics chart stirs unease over controversial depiction of race
Debate over figure connecting genes, race and ethnicity reignites concerns among geneticists about how to represent human diversity.
The All of Us Research Program is an opportunity to enhance the diversity of US biomedical research
The All of Us Research Program has prioritized the enrollment of people from backgrounds that are historically under-represented in medical research to bring precision medicine to the full diversity of the US population and to improve health outcomes for all.
- Diana W. Bianchi
- Patricia Flatley Brennan
- Joshua C. Denny
Missing centenarians are an international concern
- Ivan Lozada-Martinez
- Juan-Manuel Anaya

Effects of regulatory variants across pig tissues
The Farm Animal GTEx project introduces a new resource for pigs, in which they map genetic variation to differences in gene expression across thousands of samples.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
67 Data Management Essay Topics & Database Research Topics
🏆 best database research topics, ✍️ data management essay topics for college, 🎓 most interesting database topics for research paper, 💡 simple data management systems essay topics.
- Data Assets Management of LuLu Hypermarkets System
- Database Management Systems’ Major Capabilities
- Relational Database Management Systems in Business
- Deli Depot Case Study: Data Analysis Management Reporting
- Big Data Opportunities in Green Supply Chain Management
- Technology-Assisted Reviews of Data in a Document Management System
- Why Open-Source Software Will (Or Will Not) Soon Dominate the Field of Database Management Tools
- Object-Oriented and Database Management Systems Tradeoffs The paper suggests using the hybrid database system as it contains fewer flaws by fusing the strengths of both RDBMS and OODBMS technologies.
- Data Storage Management Solutions: Losses of Personal Data The term data refers to a collection of facts about anything. As it is often said, processed data results to information and he who has information has power.
- Childhood Obesity: Data Management The use of electronic health records (EHR) is regarded as one of the effective ways to treat obesity in the population.
- Health Data Management: Sharing and Saving Patient Data One of the ways to facilitate achieving the idealized environment of data sharing is developing the methods of accessing health-related information.
- Big Data Management Research This paper will present a literature review of three articles that examine text mining methods for quantitative analysis.
- Electronic Health Record Database and Data Management Progress in modern medicine has resulted in the amount of information related to the health of patients to grow exponentially.
- Data Management and Financial Strategies By adopting comprehensive supply chain management, businesses can maximize the three main streams in the supply chain— information flow, product flow, and money flow.
- Policy on People Data Management Law No. (13) of 2016 is a data protection legislation that applies to all public institutions and private organizations across Qatar.
- The Choice of a Medical Data Management System The choice of a medical data management system is critically important for any organization providing healthcare services.
- Data Analytics and Its Application to Management The role of the collection of data and its subsequent analysis in the industry is as big as ever. Specifically, it pertains to the managerial field.
- Modern Data Management and Organization Strategies Today, with a shrinking focus on data and analytics, a proper data management strategy is imperative to meeting business goals.
- Data Collection and Management Techniques for a Qualitative Research Plan To conduct complete qualitative research and present a cohesive qualitative research plan, it is necessary to match the structure and topic of the study.
- Database Management and Machine Learning Machine learning is used in science, business, industry, healthcare, education, etc. The possibilities of using machine learning technologies are constantly expanding.
- Data Management in a Medium-Sized Business This paper will use a medium-sized business data management offering highly specialized, high-quality business development education services as an example.
- Data Collection and Management Techniques of a Qualitative Research Plan This research paper recommends interview method in the collection of data and the application of NVivo statistical software in the management of data.
- Big Data Fraud Management The growth of eCommerce systems has led to an increase in online transactions using credit cards and other methods of payment services.
- Information Technology-Based Data Management in Retail The following paper discusses the specificities of data management and identifies the most apparent ethical considerations using retail as an example.
- Data Management, Networking and Enterprise Software Enterprise software is often created “in-house” and thus has a far higher cost as compared to simply buying the software solution from another company.
- EHR Database Management: Diabetes Prevention The data needed to prevent diabetes is usually collected throughout regular screenings conducted whenever a patient refers to a hospital, as well as by using various lab tests.
- Big Data Usage in Supply Chain Management This paper gives a summary of the research that was conducted to understand the unique issues surrounding the use of big data in the supply chain.
- Adopting Electronic Data Management in the Health Care Industry
- Distributed Operating System and Infrastructure for Scientific Data Management
- Advanced Drill Data Management Solutions Market: Growth and Forecast
- The Changing Role of Data Management in Clinical Trials
- Business Rules and Their Relationship to Effective Data Management
- Class Enterprise Data Management and Administration
- Developing Highly Scalable and Autonomic Data Management
- Cloud Computing: Installation and Maintenance of Energy Efficient Data Management
- Exploring, Mapping, and Data Management Integration of Habitable Environments in Astrobiology
- Data Management: Data Warehousing and Data Mining
- Efficient Algorithmic Techniques for Several Multidimensional Geometric Data Management and Analysis Problems
- Data Management for Photovoltaic Power Plants Operation and Maintenance
- Elderly Patients and Falls: Adverse Trends and Data Management
- Data Management for Pre- and Post-Release Workforce Services
- Epidemiological Data Management During an Outbreak of Ebola Virus Disease
- Dealing With Identifier Variables in Data Management and Analysis
- How Data Mining, Data Warehousing, and On-Line Transactional Databases Are Helping Solve the Data Management Predicament
- Improving the New Data Management Technologies and Leverage
- Integrated Process and Data Management for Healthcare Applications
- Making Data Management Manageable: A Risk Assessment Activity for Managing Research Data
- The Use of Temporal Database in the Data Management System
- Multi-Cloud Data Management Using Shamir’s Secret Sharing and Quantum Byzantine Agreement Schemes
- Data Management Is More Than Just Managing Data
- Is Effective Data Management a Key Driver of Business Success?
- National Data Centre and Financial Statistics Office: A Conceptual Design for Public Data Management
- Big Data Management and Relevance of Big Data to E-Business
- Redefining the Data Management Strategy: A Way to Leverage the Huge Chunk of Data
- Structured Data Management Software Market in Taiwan
- Towards Effective GML Data Management: Framework and Prototype
- Data Management in Cloud Environments
- Digital Communication: Enterprise Data Management
- The Impact of Big Data on Data Management Functions
- Analysis of Data Management Strategies at Tesco
- The Best Data Management Tools Overview
- What Is Data Management and Why Is It Important
- Data Management and Use: Governance in the 21st Century
- What Is Data Management and How Do Businesses Use It?
- The Difference Between Data Management and Data Governance
- Types of Data Management Systems for Data-First Marketing Strategies and Success
- Reasons Why Data Management Leads to Business Success
Cite this post
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2022, June 5). 67 Data Management Essay Topics & Database Research Topics. https://studycorgi.com/ideas/data-management-essay-topics/
"67 Data Management Essay Topics & Database Research Topics." StudyCorgi , 5 June 2022, studycorgi.com/ideas/data-management-essay-topics/.
StudyCorgi . (2022) '67 Data Management Essay Topics & Database Research Topics'. 5 June.
1. StudyCorgi . "67 Data Management Essay Topics & Database Research Topics." June 5, 2022. https://studycorgi.com/ideas/data-management-essay-topics/.
Bibliography
StudyCorgi . "67 Data Management Essay Topics & Database Research Topics." June 5, 2022. https://studycorgi.com/ideas/data-management-essay-topics/.
StudyCorgi . 2022. "67 Data Management Essay Topics & Database Research Topics." June 5, 2022. https://studycorgi.com/ideas/data-management-essay-topics/.
These essay examples and topics on Data Management were carefully selected by the StudyCorgi editorial team. They meet our highest standards in terms of grammar, punctuation, style, and fact accuracy. Please ensure you properly reference the materials if you’re using them to write your assignment.
This essay topic collection was updated on December 27, 2023 .
database security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
NETWORK DATABASE SECURITY WITH INTELLECTUAL ACCESS SUPERVISION USING OUTLIER DETECTION TECHNIQUES
Comparison of performance rot13 and caesar cipher method for registration database of vessels berthed at p.t. samudera indonesia.
Database security is a very important aspect of an information system. A general information is onlyintended for certain groups. Therefore, it is very important for a company to prevent database leakage sothat the information contained in it does not fall to unauthorized people. Cryptographic technique is an alternative solution that can be used in database security. One way to maintain the security of the database is to use encryption techniques. The method used to secure the database is encryption using the ROTI3 and Caesar Cipher methods. Both of these methods have advantages in processing speed. For thisreason, the author will compare the use of the two algorithms above in terms of the encryption and decryption process time
A Novel Framework for Efficient Multiple Signature on Certificate with Database Security
Abstract PKI gives undeniable degree of safety by transferring the key pair framework among the clients. By constructing, a PKI we combine digital identities with the digital signatures, which give an end-to-end trust model. Basically, PKI is an attempt, which can simulate the real-world human analyzation of identity and reliability in a computerized fashion. In any case, the existing applications are centered on a tight trust model which makes them inadequate as an overall device for trust examination. After years of research, development and deployment, PKI still facing strong technical and organizational challenges such as attacks against Certificate Authorities (CA). CAs are the primitive component of PKIs which plays powerful role in the PKI model. CA must be diligent, creditable and legitimate. In any case, a technocrat who picks up control on a CA can use CA's certificate to issue bogus certificate and impersonate any site, such as - DigiNotar, GobalSign, Comodo and DigiCert Malaysia. In this paper we proposed an approach to reduce the damage of compromised CA/CA’s key by imposing Multiple Signatures (MS) after verifying/authenticating user’s information. One single compromised CA is not able to issue a certificate to any domain as multiple signatures are required. Private key and other perceptive information are stored in the form of object/blob. Without knowing the structure of class no one can access the object and object output stream. Proposed MS achieve better performance over existing MS schemes and control fraudulent certificate issuance with more database security. The proposed scheme also avoids MITM attack against CA who is issuing certificate to whom which is using the following parameters such as identity of Sender, Receiver, Timestamp and Aadhar number.
A guiding framework for enhancing database security in state-owned universities in Zimbabwe
Technique for evaluating the security of relational databases based on the enhanced clements–hoffman model.
Obtaining convincing evidence of database security, as the basic corporate resource, is extremely important. However, in order to verify the conclusions about the degree of security, it must be measured. To solve this challenge, the authors of the paper enhanced the Clements–Hoffman model, determined the integral security metric and, on this basis, developed a technique for evaluating the security of relational databases. The essence of improving the Clements–Hoffmann model is to expand it by including a set of object vulnerabilities. Vulnerability is considered as a separate objectively existing category. This makes it possible to evaluate both the likelihood of an unwanted incident and the database security as a whole more adequately. The technique for evaluating the main components of the security barriers and the database security as a whole, proposed by the authors, is based on the theory of fuzzy sets and risk. As an integral metric of database security, the reciprocal of the total residual risk is used, the constituent components of which are presented in the form of certain linguistic variables. In accordance with the developed technique, the authors presented the results of a quantitative evaluation of the effectiveness of the protection of databases built on the basis of the schema with the universal basis of relations and designed in accordance with the traditional technology of relational databases.
Hybrid Security Approach for Database Security using Diffusion based cryptography and Diffie-Hellman key exchange Algorithm
Application of network database security technology based on big data technology, database security in a dynamic it world.
Databases are vulnerable. Public statements by Target, Home Depot, and Anthem following their extremely advertised data breaches are each uniform and succinct on how their breaches unfolded: unauthorized access to those systems that ultimately led to the extraction of sensitive information. A comprehensive strategy to secure a database is over data security. Usually, security events will be related to the later action: illegitimate access to data confidentiality damage, injury to the integrity of knowledge, loss of data accessibility (Discover). Loss of privacy of data, creating them accessible to others without a right of access is not visible within the database and does not need changes deductible database. This paper addresses these events to confirm database security.
A Review of Database Security Concepts, Risks, and Problems
Currently, data production is as quick as possible; however, databases are collections of well-organized data that can be accessed, maintained, and updated quickly. Database systems are critical to your company because they convey data about sales transactions, product inventories, customer profiles, and marketing activities. To accomplish data manipulation and maintenance activities the Database Management System considered. Databases differ because their conclusions based on countless rules about what an invulnerable database constitutes. As a result, database protection seekers encounter difficulties in terms of a fantastic figure selection to maintain their database security. The main goal of this study is to identify the risk and how we can secure databases, encrypt sensitive data, modify system databases, and update database systems, as well as to evaluate some of the methods to handle these problems in security databases. However, because information plays such an important role in any organization, understanding the security risk and preventing it from occurring in any database system require a high level of knowledge. As a result, through this paper, all necessary information for any organization has been explained; in addition, also a new technological tool that plays an essential role in database security was discussed.
Database protection model based on security system with full overlap
Security is one of the most important characteristics of the quality of information systems in general and databases, as their main component, in particular. Therefore, the presence of an information protection system, as a complex of software, technical, cryptographic, organizational and other methods, means and measures that ensure the integrity, confidentiality, authenticity and availability of information in conditions of exposure to natural or artificial threats, is an integral feature of almost any modern information system and database. At the same time, in order to be able to verify the conclusions about the degree of security, it must be measured in some way. The paper considers a database security model based on a full overlap security model (a covered security system), which is traditionally considered the basis for a formal description of security systems. Thanks to expanding the Clements-Hoffman model by including a set of vulnerabilities (as a separately objectively existing category necessary to describe a weakness of an asset or control that can be exploited by one or more threats), which makes it possible to assess more adequately the likelihood of an unwanted incident (threat realization) in a two-factor model (in which one of the factors reflects the motivational component of the threat, and the second takes into account the existing vulnerabilities); a defined integral indicator of database security (as a value inverse to the total residual risk, the constituent components of which are represented in the form of the corresponding linguistic variables); the developed technique for assessing the main components of security barriers and the security of the database as a whole, based on the theory of fuzzy sets and risk, it becomes possible to use the developed model to conduct a quantitative assessment of the security of the analyzed database.
Export Citation Format
Share document.
iNetTutor.com
Online Programming Lessons, Tutorials and Capstone Project guide
40 List of DBMS Project Topics and Ideas
Introduction
A Capstone project is the last project of an IT degree program. It is made up of one or more research projects in which students create prototypes, services, and/or products. The projects are organized around an issue that needs to be handled in real-world scenarios. When IT departments want to test new ideas or concepts that will be adopted into their daily operations, they implement these capstone projects within their services.
In this article, our team has compiled a list of Database Management System Project Topics and Ideas. The capstone projects listed below will assist future researchers in deciding which capstone project idea to pursue. Future researchers may find the information in this page useful in coming up with unique capstone project ideas.
- Telemedicine Online Platform Database Design
“Telemedicine Online Platform” is designed to allow doctors to deliver clinical support to patients remotely. Doctors can communicate with their patients in real-time for consultations, diagnoses, monitoring, and medical supply prescriptions. The project will be developed using the SDLC method by the researchers. The researchers will also compile a sample of hospital doctors and patients who will act as study participants. A panel of IT specialists will review, test, and assess the project.
- Virtual and Remote Guidance Counselling System Database Design
Counseling is a vital component of a person’s life since it aids in the improvement of interpersonal relationships. Humans must cease ignoring this issue because it is essential for the development of mental wellness. The capstone project “Virtual and Remote Guidance Counselling System,” which covers the gap in giving counseling in stressful situations, was built for this reason. It answers to the requirement to fill in the gaps in the traditional technique and make it more effective and immersive in this way.
- COVID-19 Facilities Management Information System Database Design
COVID – 19 has put people in fear due to its capability of transmission when exposed to the virus. The health sectors and the government provide isolation facilities for COVID-19 patients to mitigate the spread and transmission of the virus. However, proper communication for the availability of the facilities is inefficient resulting to surge of patients in just one facility and some are transferred multiple times due to unavailability. The COVID-19 respondents must have an advance tools to manage the COVID-19 facilities where respondents can easily look for available facilities to cater more patients.
- Document Tracking System Database Design
The capstone project, “Document Tracking System” is purposely designed for companies and organizations that allow them to electronically store and track documents. The system will track the in/out of the documents across different departments. The typical way of tracking documents is done using the manual approach. The staff will call or personally ask for updates about the documents which are time-consuming and inefficient.
- Face Recognition Application Database Design
Technology has grown so fast; it changes the way we do our daily tasks. Technology has made our daily lives easier. The capstone project, entitled “Face Recognition Attendance System” is designed to automate checking and recording of students’ attendance during school events using face recognition technology. The system will work by storing the student’s information along with their photographs in a server and the system will detect the faces of the students during school events and match it and verify to record the presence or absence of the student.
- Digital Wallet Solution Database Design
The capstone project, named “Digital Wallet Solution,” is intended to allow people to store money online and make payments online. The digital wallet transactions accept a variety of currencies and provide a variety of payment gateways via which the user can pay for products and services. The system allows users to conduct secure and convenient online financial transactions. It will speed up payment and other financial processes, reducing the amount of time and effort required to complete them.
- Virtual Online Tour Application Database Design
The usage of technology is an advantage in the business industry, especially during this challenging pandemic. It allows businesses to continue to operate beyond physicality. The capstone project entitled “Virtual Online Tour Application” is designed as a platform to streamline virtual tours for clients. Any business industry can use the system to accommodate and provide their clients with a virtual experience of their business. For example, the tourist industry and real estate agencies can use the system to provide a virtual tour to their clients about the tourist locations and designs of properties, respectively.
- Invoice Management System Database Design
The researchers will create a system that will make it easier for companies to manage and keep track of their invoice information. The company’s sales records, payables, and total invoice records will all be electronically managed using this project. Technology is highly used for business operations and transactions automation. The capstone project, entitled “Invoice Management System” is designed to automate the management of the company’s invoice records. The said project will help companies to have an organized, accurate, and reliable record that will help them track their sales and finances.
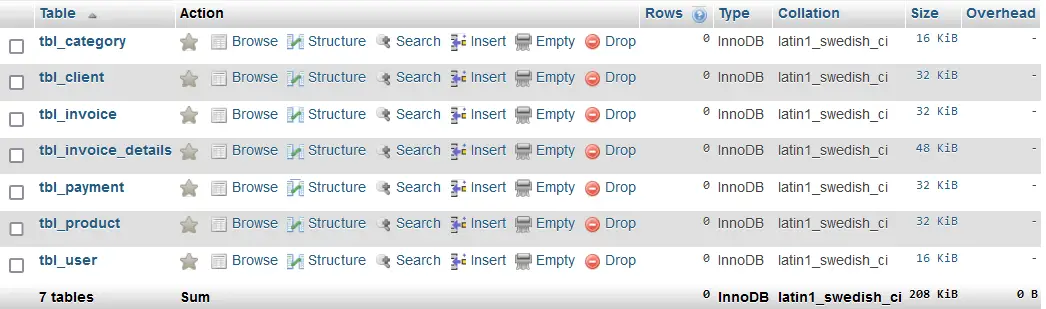
- Vehicle Repair and Maintenance Management System Database Design
Information Technology has become an integral part of any kind of business in terms of automating business operations and transactions. The capstone project, entitled “Vehicle Repair and Maintenance Management System” is designed for vehicle repair and maintenance management automation. The said project will automate the vehicle garage’s operations and daily transactions. The system will automate operations such as managing vehicle repair and maintenance records, invoice records, customer records, transaction records, billing and payment records, and transaction records.
- Transcribe Medical Database Design
Information technology has made everything easier and simpler, including transcribing the medical diagnosis of patients. The capstone project, entitled “Medical Transcription Platform,” is designed to allow medical transcriptionists to transcribe audio of medical consultations and diagnose patients in a centralized manner. A medical transcriptionist is vital to keep accurate and credible medical records of patients and can be used by other doctors to know the patients’ medical history. The said project will serve as a platform where transcribed medical audios are stored for safekeeping and easy retrieval.
- Multi-branch Travel Agency and Booking System Database Design
The capstone project, entitled “Multi-Branch Travel Agency and Booking System,” is designed as a centralized platform wherein multiple travel agency branches are registered to ease and simplify inquiries and booking of travels and tour packages by clients. The said project will allow travel agencies to operate a business in an easy, fast manner considering the convenience and safety of their clients. The system will enable travel agencies and their clients to have a seamless online transaction.
- Pharmacy Stocks Management Database Design
The capstone project “Pharmacy Stocks Management System” allows pharmacies to manage and monitor their stocks of drugs electronically. The Pharmacy Stocks Management System will automate inventory to help ensure that the pharmacy has enough stock of medications and supplies to serve the needs of the patients.
- Loan Management with SMS Database Design
The capstone project entitled “ Loan Management System with SMS ” is an online platform that allows members to apply and request loan. In addition, they can also monitor their balance in their respective dashboard. Management of cooperative will review first the application for approval or disapproval of the request. Notification will be send through the SMS or short messaging service feature of the system.
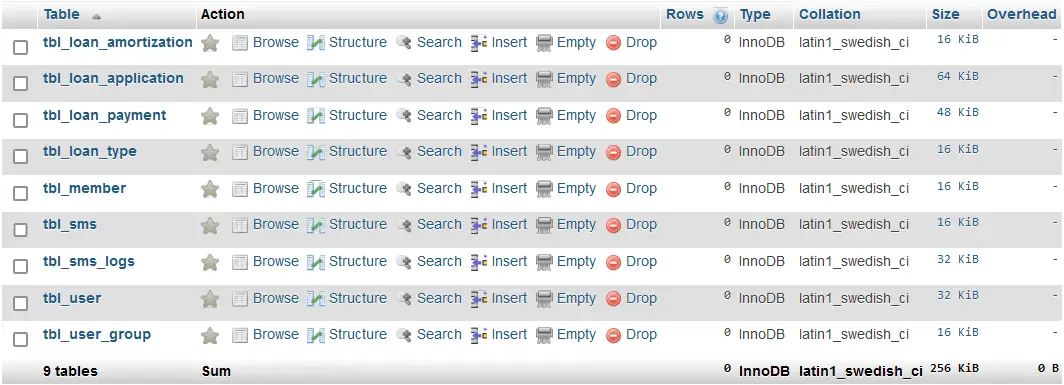
- Service Call Management System Database Design
The capstone project, entitled ” Service Call Management System,” is designed to transform service calls to a centralized platform. The said project would allow clients to log in and lodge calls to the tech support if they encountered issues and difficulties with their purchased products. The tech support team will diagnose the issue and provide them with the necessary actions to perform via a call to solve the problem and achieve satisfaction.
- File Management with Approval Process Database Design
The File Management System provides a platform for submitting, approving, storing, and retrieving files. Specifically, the capstone project is for the file management of various business organizations. This is quite beneficial in the management and organization of the files of every department. Installation of the system on an intranet is possible, as is uploading the system to a live server, from which the platform can be viewed online and through the use of a browser.
- Beauty Parlor Management System Database Design
The capstone project entitled “Beauty Parlour Management System” is an example of transactional processing system that focuses on the records and process of a beauty parlour. This online application will help the management to keep and manage their transactions in an organize, fast and efficient manner.
- Exam Management System Database Design
Information technology plays a significant role in the teaching and learning process of teachers and students, respectively. IT offers a more efficient and convenient way for teachers and students to learn and assess learnings. The capstone project, “Exam Management System,” is designed to allow electronic management of all the information about the exam questions, courses and subjects, and teachers and students. The said project is an all-in-one platform for student exam management.
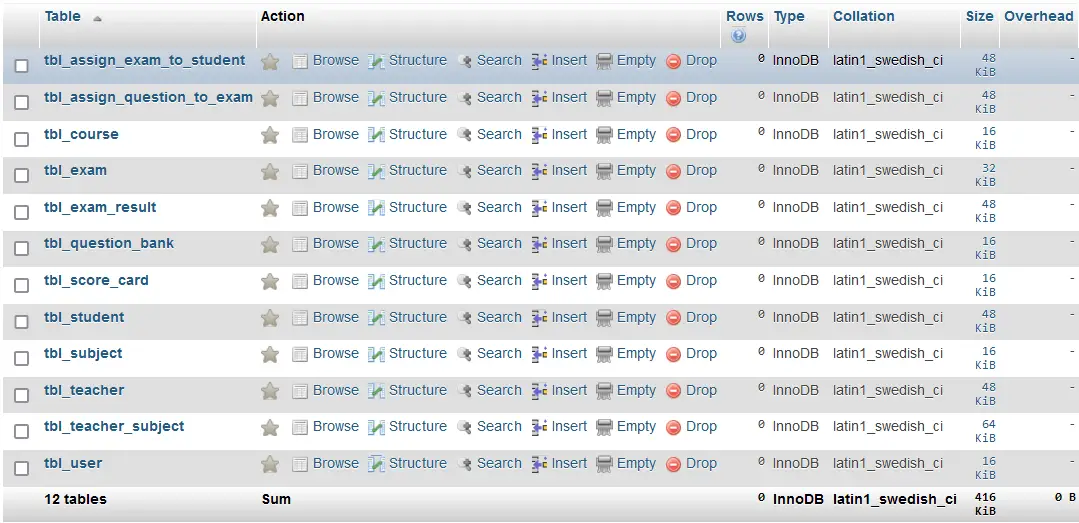
- Student and Faculty Clearance Database Design
The capstone project, entitled “Student and Faculty Clearance System,” is designed to automate students and faculty clearance processes. The approach is intended to make the clearance procedure easier while also guaranteeing that approvals are accurate and complete. The project works by giving every Department involved access to the application. The proposed scheme can eliminate the specified challenges, streamline the process, and verify the integrity and correctness of the data.
- Vehicle Parking Management System Database Design
The capstone project entitled “ Vehicle Parking Management System ” is an online platform that allows vehicle owners to request or reserve a slot for parking space. Management can accept and decline the request of reservation. In addition, payment option is also part of the system feature but is limited to on-site payment.
- Hospital Resources and Room Utilization Database Design
The capstone project, “Hospital Resources and Room Utilization Management System” is a system designed to streamline the process of managing hospital resources and room utilization. The said project is critical especially now that we are facing a pandemic, there is a need for efficient management of hospital resources and room management. The management efficiency will prevent a shortage in supplies and overcrowding of patients in the hospitals.
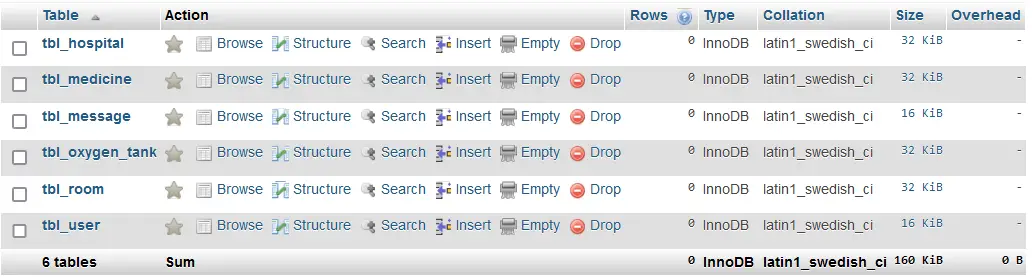
- Church Event Management System Database Design
The capstone project entitled “Church Event Management System” is designed to be used by church organizations in creating and managing different church events. The conventional method of managing church events is done manually where members of organizations will face difficulties due to physical barriers and time constraints.
- CrowdFunding Platform Database Design
Business financing is critical for new business ventures. In this study, the researchers concentrate on designing and developing a business financing platform that is effective for new startups. This capstone project, entitled “Crowdfunding Platform” is a website that allows entrepreneurs to campaign their new business venture to attract investors and crowdfund.
- Vehicle Franchising and Drivers Offense Software Database Design
The proposed software will be used to electronically process and manage vehicle and franchising and driver’s offenses. The proposed software will eliminate the manual method which involves a lot of paper works and consumes valuable amount of time. The proposed project will serve as a centralized platform was recording and paying for the offenses committed by the drivers will be processed. The system will quicken the process of completing transaction between the enforcers and the drivers. Vehicle franchising and managing driver offenses will be easy, fast and convenient using the system.
- Student Tracking Performance Database Design
The capstone project entitled “Student Academic Performance Tracking and Monitoring System” allows academic institutions to monitor and gather data about the academic performance of students where decisions are derived to further improve the students learning outcomes. Tracking and monitoring student’s performance serves a vital role in providing information that is used to assist students, teachers, administrators, and policymakers in making decisions that will further improve the academic performance of students.
- Webinar Course Management System Database Design
The capstone project, entitled “Webinar Course Management System,” is designed to automate managing webinar courses. The project aims to eliminate the current method, which is inefficient and inconvenient for parties involved in the webinar. A software development life cycle (SDLC) technique will be used by the researchers in order to build this project. They will gather a sample size of participating webinar members and facilitators to serve as respondents of the study.
- Online Birth Certificate Processing System with SMS Notification Database Design
The capstone project, “Online Birth Certificate Processing System with SMS Notification “ is an IT-based solution that aims to automate the process of requesting, verifying, and approving inquiries for original birth records. The system will eliminate the traditional method and transition the birth certificate processing into an easy, convenient, and efficient manner. The researchers will develop the project following the Software Development Life Cycle (SDLC) technique.
- Food Donation Services Database Design
Information technology plays a significant role in automating the operations of many companies to boost efficiency. One of these is the automation of food donation and distribution management. “Food Donation Services,” the capstone project, is intended to serve as a platform for facilitating transactions between food groups, donors, and recipients. Food banks will be able to respond to various food donations and food assistance requests in a timely and effective manner as a result of the project.
- COVID Profiling Database Design
The capstone project “City COVID-19 Profiling System with Decision Support” is designed to automate the process of profiling COVID-19 patients. The project will empower local health officers in electronically recording and managing COVID-19 patient information such as symptoms, travel history, and other critical details needed to identify patients. Manual profiling is prone to human mistakes, necessitates a lot of paperwork, and needs too much time and effort from the employees.
- Evacuation Center Database Design
Calamities can have a significant impact on society. It may result in an enormous number of people being evacuated. The local government unit assigned evacuation centers to provide temporary shelter for people during disasters. Evacuation centers are provided to give temporary shelter for the people during and after a calamity. Evacuation centers can be churches, sports stadium community centers, and much more that are capable to provide emergency shelter.
- QR Code Fare Payment System Database Design
The capstone project, “QR Code Fare Payment System” is designed to automate the procedure of paying for a fare when riding a vehicle. Passengers will register in the system to receive their own QR code, which they will use to pay for their fares by scanning in the system’s QR code scanning page. The project will enable cashless fare payment.
- Web Based Psychopathology Diagnosis System Database Design
The capstone project entitled “Web-Based Psychopathology Diagnosis System” is designed for patients and medical staff in the field of psychopathology. The system will be a centralized platform to be used by patients and psychopathologists for consultations. The said project will also keep all the records electronically. Mental health is important. Each individual must give importance to their mental health by paying attention to it and seek medical advice if symptoms of mental disorders and unusual behavior occur.
- Service Marketplace System Database Design
The capstone project, “Services Marketplace System” is designed to serve as a centralized platform for marketing and inquiring about different services. The system will serve as a platform where different service providers and customers will have an automated transaction. Technology made it easier for people to accomplish daily tasks and activities. In the conventional method, customers avail themselves of services by visiting the shop that offers their desired services personally.

- Fish Catch System Database Design
The capstone project, entitled “Fish Catch Monitoring System” will automate the process of recording and monitoring fish catches. The said project is intended to be used by fisherman and fish markets to accurately record fish catches and will also keep the records electronically safe and secure.
- Complaints Handling Management System Free Template Database Design
The capstone project, “Complaint Handling Management System” is a system designed to help educational institutions to handle and manage complaints electronically. The system will improve the response time of the school’s management in addressing the complaints of the students, parents, staff, and other stakeholders.
- Senior Citizen Information System Free Template Database Design
The system will replace the manual method of managing information and records of the senior citizen to an electronic one. The system will serve as a repository of the record of the senior citizen within the scope of a specific local government unit. By using the system, paper works will be lessened and human errors in file handling will be avoided. The system is efficient enough to aid in managing and keeping the records of the senior citizens in the different barangay.
- Online and SMS-Based Salary Notification Database Design
The “Online and SMS Based Salary Notification” is a capstone project intended to be used by companies and employees to automate the process of notifying salary details. The application will work by allowing the designated company encoder to encode details of salary and the employees to log in to his/her account in the application and have access to the details of his/her salary. One of the beauties of being employed is being paid. Employers manage the employee’s salary and are responsible to discuss with the employees the system of the salary and deductions.
- Maternal Records Management Database Design
The capstone project, “Maternal Records Management System” is a system that automates the process of recording and keeping maternal records. The said project will allow maternity clinics to track and monitor their patients’ records from pregnancy to their baby’s immunization records.
- Online Complaint Management System Database Design
Online Complaint Management System is a capstone project that is design to serve as a platform to address complaints and resolve disputes. The system provides an online way of resolving problems faced by the public or people within the organization. The system will make complaints easier to coordinate, monitor, track and resolve.
- Online Donation Database Design
The capstone project , “Online Donation Platform for DSWD” is an online platform for giving and asking donations in the Department of Social Welfare and Development (DSWD). The system will be managed by the staffs of the DSWD to verify donors and legible beneficiaries electronically. The system will have an SMS feature to notify the donors and beneficiaries about the status of their request.
- OJT Timesheet Monitoring System using QR Code Database Design
The capstone project, “OJT Timesheet Monitoring System using QR Code” allows employer to automate timesheet of each trainee for easy monitoring. The system will be used by the on-the-job trainees to serve as their daily time in and out using the QR code generated by the system. The entire system will be managed by the administrator.
Technology is attributed with driving change in a wide range of enterprises and institutions. Because of information technology, the world has altered dramatically. It is difficult to imagine an industry or organization that has not benefited from technology advances. In these businesses, the most common role of IT has been to automate numerous procedures and transactions in order to increase efficiency and improve people’s overall experience and satisfaction. The aforementioned capstone project ideas will be useful in a range of sectors. It will aid in enhancing operational efficiency as well as the services provided to the project’s users.
You may visit our Facebook page for more information, inquiries, and comments. Please subscribe also to our YouTube Channel to receive free capstone projects resources and computer programming tutorials.
Hire our team to do the project.
Related Topics and Articles:
- List of Completed Capstone Projects with Source code
- 27 Free Capstone Project Ideas and Tutorials
- 16 Lists of Free Capstone Project Ideas in Flutter
- 39 Capstone Project Ideas for IT Related Courses
- 50+ Free Download Web Based System Template in Bootstrap
- COVID-19 Capstone and Research Free Project Ideas 2022
- Capstone Project Ideas for IT and IS January 2022
- Capstone Project Ideas for IT and IS December 2021
- IT and IS Capstone Project Free Resources November 2021
- List of 45 IT Capstone Project on Crime and Disaster Management
Post navigation
- QR Code Generator in PHP Free Source code and Tutorial
Similar Articles
Mysql tutorial – mysql delete command, mysql tutorial – the group by clause, mysql alter command.
Database Search
What is Database Search?
Harvard Library licenses hundreds of online databases, giving you access to academic and news articles, books, journals, primary sources, streaming media, and much more.
The contents of these databases are only partially included in HOLLIS. To make sure you're really seeing everything, you need to search in multiple places. Use Database Search to identify and connect to the best databases for your topic.
In addition to digital content, you will find specialized search engines used in specific scholarly domains.
Related Services & Tools
Reference management. Clean and simple.
The top list of academic research databases

2. Web of Science
5. ieee xplore, 6. sciencedirect, 7. directory of open access journals (doaj), get the most out of your academic research database, frequently asked questions about academic research databases, related articles.
Whether you are writing a thesis , dissertation, or research paper it is a key task to survey prior literature and research findings. More likely than not, you will be looking for trusted resources, most likely peer-reviewed research articles.
Academic research databases make it easy to locate the literature you are looking for. We have compiled the top list of trusted academic resources to help you get started with your research:
Scopus is one of the two big commercial, bibliographic databases that cover scholarly literature from almost any discipline. Besides searching for research articles, Scopus also provides academic journal rankings, author profiles, and an h-index calculator .
- Coverage: 90.6 million core records
- References: N/A
- Discipline: Multidisciplinary
- Access options: Limited free preview, full access by institutional subscription only
- Provider: Elsevier
Web of Science also known as Web of Knowledge is the second big bibliographic database. Usually, academic institutions provide either access to Web of Science or Scopus on their campus network for free.
- Coverage: approx. 100 million items
- References: 1.4 billion
- Access options: institutional subscription only
- Provider: Clarivate (formerly Thomson Reuters)
PubMed is the number one resource for anyone looking for literature in medicine or biological sciences. PubMed stores abstracts and bibliographic details of more than 30 million papers and provides full text links to the publisher sites or links to the free PDF on PubMed Central (PMC) .
- Coverage: approx. 35 million items
- Discipline: Medicine and Biological Sciences
- Access options: free
- Provider: NIH
For education sciences, ERIC is the number one destination. ERIC stands for Education Resources Information Center, and is a database that specifically hosts education-related literature.
- Coverage: approx. 1.6 million items
- Discipline: Education
- Provider: U.S. Department of Education
IEEE Xplore is the leading academic database in the field of engineering and computer science. It's not only journal articles, but also conference papers, standards and books that can be search for.
- Coverage: approx. 6 million items
- Discipline: Engineering
- Provider: IEEE (Institute of Electrical and Electronics Engineers)
ScienceDirect is the gateway to the millions of academic articles published by Elsevier, 1.4 million of which are open access. Journals and books can be searched via a single interface.
- Coverage: approx. 19.5 million items
The DOAJ is an open-access academic database that can be accessed and searched for free.
- Coverage: over 8 million records
- Provider: DOAJ
JSTOR is another great resource to find research papers. Any article published before 1924 in the United States is available for free and JSTOR also offers scholarships for independent researchers.
- Coverage: more than 12 million items
- Provider: ITHAKA
Start using a reference manager like Paperpile to save, organize, and cite your references. Paperpile integrates with PubMed and many popular databases, so you can save references and PDFs directly to your library using the Paperpile buttons:
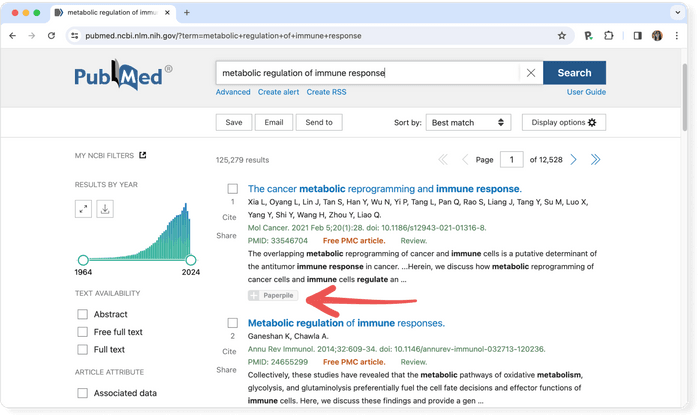
Scopus is one of the two big commercial, bibliographic databases that cover scholarly literature from almost any discipline. Beside searching for research articles, Scopus also provides academic journal rankings, author profiles, and an h-index calculator .
PubMed is the number one resource for anyone looking for literature in medicine or biological sciences. PubMed stores abstracts and bibliographic details of more than 30 million papers and provides full text links to the publisher sites or links to the free PDF on PubMed Central (PMC)

Choose Your Test
Sat / act prep online guides and tips, 113 great research paper topics.
General Education

One of the hardest parts of writing a research paper can be just finding a good topic to write about. Fortunately we've done the hard work for you and have compiled a list of 113 interesting research paper topics. They've been organized into ten categories and cover a wide range of subjects so you can easily find the best topic for you.
In addition to the list of good research topics, we've included advice on what makes a good research paper topic and how you can use your topic to start writing a great paper.
What Makes a Good Research Paper Topic?
Not all research paper topics are created equal, and you want to make sure you choose a great topic before you start writing. Below are the three most important factors to consider to make sure you choose the best research paper topics.
#1: It's Something You're Interested In
A paper is always easier to write if you're interested in the topic, and you'll be more motivated to do in-depth research and write a paper that really covers the entire subject. Even if a certain research paper topic is getting a lot of buzz right now or other people seem interested in writing about it, don't feel tempted to make it your topic unless you genuinely have some sort of interest in it as well.
#2: There's Enough Information to Write a Paper
Even if you come up with the absolute best research paper topic and you're so excited to write about it, you won't be able to produce a good paper if there isn't enough research about the topic. This can happen for very specific or specialized topics, as well as topics that are too new to have enough research done on them at the moment. Easy research paper topics will always be topics with enough information to write a full-length paper.
Trying to write a research paper on a topic that doesn't have much research on it is incredibly hard, so before you decide on a topic, do a bit of preliminary searching and make sure you'll have all the information you need to write your paper.
#3: It Fits Your Teacher's Guidelines
Don't get so carried away looking at lists of research paper topics that you forget any requirements or restrictions your teacher may have put on research topic ideas. If you're writing a research paper on a health-related topic, deciding to write about the impact of rap on the music scene probably won't be allowed, but there may be some sort of leeway. For example, if you're really interested in current events but your teacher wants you to write a research paper on a history topic, you may be able to choose a topic that fits both categories, like exploring the relationship between the US and North Korea. No matter what, always get your research paper topic approved by your teacher first before you begin writing.
113 Good Research Paper Topics
Below are 113 good research topics to help you get you started on your paper. We've organized them into ten categories to make it easier to find the type of research paper topics you're looking for.
Arts/Culture
- Discuss the main differences in art from the Italian Renaissance and the Northern Renaissance .
- Analyze the impact a famous artist had on the world.
- How is sexism portrayed in different types of media (music, film, video games, etc.)? Has the amount/type of sexism changed over the years?
- How has the music of slaves brought over from Africa shaped modern American music?
- How has rap music evolved in the past decade?
- How has the portrayal of minorities in the media changed?

Current Events
- What have been the impacts of China's one child policy?
- How have the goals of feminists changed over the decades?
- How has the Trump presidency changed international relations?
- Analyze the history of the relationship between the United States and North Korea.
- What factors contributed to the current decline in the rate of unemployment?
- What have been the impacts of states which have increased their minimum wage?
- How do US immigration laws compare to immigration laws of other countries?
- How have the US's immigration laws changed in the past few years/decades?
- How has the Black Lives Matter movement affected discussions and view about racism in the US?
- What impact has the Affordable Care Act had on healthcare in the US?
- What factors contributed to the UK deciding to leave the EU (Brexit)?
- What factors contributed to China becoming an economic power?
- Discuss the history of Bitcoin or other cryptocurrencies (some of which tokenize the S&P 500 Index on the blockchain) .
- Do students in schools that eliminate grades do better in college and their careers?
- Do students from wealthier backgrounds score higher on standardized tests?
- Do students who receive free meals at school get higher grades compared to when they weren't receiving a free meal?
- Do students who attend charter schools score higher on standardized tests than students in public schools?
- Do students learn better in same-sex classrooms?
- How does giving each student access to an iPad or laptop affect their studies?
- What are the benefits and drawbacks of the Montessori Method ?
- Do children who attend preschool do better in school later on?
- What was the impact of the No Child Left Behind act?
- How does the US education system compare to education systems in other countries?
- What impact does mandatory physical education classes have on students' health?
- Which methods are most effective at reducing bullying in schools?
- Do homeschoolers who attend college do as well as students who attended traditional schools?
- Does offering tenure increase or decrease quality of teaching?
- How does college debt affect future life choices of students?
- Should graduate students be able to form unions?

- What are different ways to lower gun-related deaths in the US?
- How and why have divorce rates changed over time?
- Is affirmative action still necessary in education and/or the workplace?
- Should physician-assisted suicide be legal?
- How has stem cell research impacted the medical field?
- How can human trafficking be reduced in the United States/world?
- Should people be able to donate organs in exchange for money?
- Which types of juvenile punishment have proven most effective at preventing future crimes?
- Has the increase in US airport security made passengers safer?
- Analyze the immigration policies of certain countries and how they are similar and different from one another.
- Several states have legalized recreational marijuana. What positive and negative impacts have they experienced as a result?
- Do tariffs increase the number of domestic jobs?
- Which prison reforms have proven most effective?
- Should governments be able to censor certain information on the internet?
- Which methods/programs have been most effective at reducing teen pregnancy?
- What are the benefits and drawbacks of the Keto diet?
- How effective are different exercise regimes for losing weight and maintaining weight loss?
- How do the healthcare plans of various countries differ from each other?
- What are the most effective ways to treat depression ?
- What are the pros and cons of genetically modified foods?
- Which methods are most effective for improving memory?
- What can be done to lower healthcare costs in the US?
- What factors contributed to the current opioid crisis?
- Analyze the history and impact of the HIV/AIDS epidemic .
- Are low-carbohydrate or low-fat diets more effective for weight loss?
- How much exercise should the average adult be getting each week?
- Which methods are most effective to get parents to vaccinate their children?
- What are the pros and cons of clean needle programs?
- How does stress affect the body?
- Discuss the history of the conflict between Israel and the Palestinians.
- What were the causes and effects of the Salem Witch Trials?
- Who was responsible for the Iran-Contra situation?
- How has New Orleans and the government's response to natural disasters changed since Hurricane Katrina?
- What events led to the fall of the Roman Empire?
- What were the impacts of British rule in India ?
- Was the atomic bombing of Hiroshima and Nagasaki necessary?
- What were the successes and failures of the women's suffrage movement in the United States?
- What were the causes of the Civil War?
- How did Abraham Lincoln's assassination impact the country and reconstruction after the Civil War?
- Which factors contributed to the colonies winning the American Revolution?
- What caused Hitler's rise to power?
- Discuss how a specific invention impacted history.
- What led to Cleopatra's fall as ruler of Egypt?
- How has Japan changed and evolved over the centuries?
- What were the causes of the Rwandan genocide ?

- Why did Martin Luther decide to split with the Catholic Church?
- Analyze the history and impact of a well-known cult (Jonestown, Manson family, etc.)
- How did the sexual abuse scandal impact how people view the Catholic Church?
- How has the Catholic church's power changed over the past decades/centuries?
- What are the causes behind the rise in atheism/ agnosticism in the United States?
- What were the influences in Siddhartha's life resulted in him becoming the Buddha?
- How has media portrayal of Islam/Muslims changed since September 11th?
Science/Environment
- How has the earth's climate changed in the past few decades?
- How has the use and elimination of DDT affected bird populations in the US?
- Analyze how the number and severity of natural disasters have increased in the past few decades.
- Analyze deforestation rates in a certain area or globally over a period of time.
- How have past oil spills changed regulations and cleanup methods?
- How has the Flint water crisis changed water regulation safety?
- What are the pros and cons of fracking?
- What impact has the Paris Climate Agreement had so far?
- What have NASA's biggest successes and failures been?
- How can we improve access to clean water around the world?
- Does ecotourism actually have a positive impact on the environment?
- Should the US rely on nuclear energy more?
- What can be done to save amphibian species currently at risk of extinction?
- What impact has climate change had on coral reefs?
- How are black holes created?
- Are teens who spend more time on social media more likely to suffer anxiety and/or depression?
- How will the loss of net neutrality affect internet users?
- Analyze the history and progress of self-driving vehicles.
- How has the use of drones changed surveillance and warfare methods?
- Has social media made people more or less connected?
- What progress has currently been made with artificial intelligence ?
- Do smartphones increase or decrease workplace productivity?
- What are the most effective ways to use technology in the classroom?
- How is Google search affecting our intelligence?
- When is the best age for a child to begin owning a smartphone?
- Has frequent texting reduced teen literacy rates?

How to Write a Great Research Paper
Even great research paper topics won't give you a great research paper if you don't hone your topic before and during the writing process. Follow these three tips to turn good research paper topics into great papers.
#1: Figure Out Your Thesis Early
Before you start writing a single word of your paper, you first need to know what your thesis will be. Your thesis is a statement that explains what you intend to prove/show in your paper. Every sentence in your research paper will relate back to your thesis, so you don't want to start writing without it!
As some examples, if you're writing a research paper on if students learn better in same-sex classrooms, your thesis might be "Research has shown that elementary-age students in same-sex classrooms score higher on standardized tests and report feeling more comfortable in the classroom."
If you're writing a paper on the causes of the Civil War, your thesis might be "While the dispute between the North and South over slavery is the most well-known cause of the Civil War, other key causes include differences in the economies of the North and South, states' rights, and territorial expansion."
#2: Back Every Statement Up With Research
Remember, this is a research paper you're writing, so you'll need to use lots of research to make your points. Every statement you give must be backed up with research, properly cited the way your teacher requested. You're allowed to include opinions of your own, but they must also be supported by the research you give.
#3: Do Your Research Before You Begin Writing
You don't want to start writing your research paper and then learn that there isn't enough research to back up the points you're making, or, even worse, that the research contradicts the points you're trying to make!
Get most of your research on your good research topics done before you begin writing. Then use the research you've collected to create a rough outline of what your paper will cover and the key points you're going to make. This will help keep your paper clear and organized, and it'll ensure you have enough research to produce a strong paper.
What's Next?
Are you also learning about dynamic equilibrium in your science class? We break this sometimes tricky concept down so it's easy to understand in our complete guide to dynamic equilibrium .
Thinking about becoming a nurse practitioner? Nurse practitioners have one of the fastest growing careers in the country, and we have all the information you need to know about what to expect from nurse practitioner school .
Want to know the fastest and easiest ways to convert between Fahrenheit and Celsius? We've got you covered! Check out our guide to the best ways to convert Celsius to Fahrenheit (or vice versa).
Need more help with this topic? Check out Tutorbase!
Our vetted tutor database includes a range of experienced educators who can help you polish an essay for English or explain how derivatives work for Calculus. You can use dozens of filters and search criteria to find the perfect person for your needs.
These recommendations are based solely on our knowledge and experience. If you purchase an item through one of our links, PrepScholar may receive a commission.

Christine graduated from Michigan State University with degrees in Environmental Biology and Geography and received her Master's from Duke University. In high school she scored in the 99th percentile on the SAT and was named a National Merit Finalist. She has taught English and biology in several countries.
Student and Parent Forum
Our new student and parent forum, at ExpertHub.PrepScholar.com , allow you to interact with your peers and the PrepScholar staff. See how other students and parents are navigating high school, college, and the college admissions process. Ask questions; get answers.

Ask a Question Below
Have any questions about this article or other topics? Ask below and we'll reply!
Improve With Our Famous Guides
- For All Students
The 5 Strategies You Must Be Using to Improve 160+ SAT Points
How to Get a Perfect 1600, by a Perfect Scorer
Series: How to Get 800 on Each SAT Section:
Score 800 on SAT Math
Score 800 on SAT Reading
Score 800 on SAT Writing
Series: How to Get to 600 on Each SAT Section:
Score 600 on SAT Math
Score 600 on SAT Reading
Score 600 on SAT Writing
Free Complete Official SAT Practice Tests
What SAT Target Score Should You Be Aiming For?
15 Strategies to Improve Your SAT Essay
The 5 Strategies You Must Be Using to Improve 4+ ACT Points
How to Get a Perfect 36 ACT, by a Perfect Scorer
Series: How to Get 36 on Each ACT Section:
36 on ACT English
36 on ACT Math
36 on ACT Reading
36 on ACT Science
Series: How to Get to 24 on Each ACT Section:
24 on ACT English
24 on ACT Math
24 on ACT Reading
24 on ACT Science
What ACT target score should you be aiming for?
ACT Vocabulary You Must Know
ACT Writing: 15 Tips to Raise Your Essay Score
How to Get Into Harvard and the Ivy League
How to Get a Perfect 4.0 GPA
How to Write an Amazing College Essay
What Exactly Are Colleges Looking For?
Is the ACT easier than the SAT? A Comprehensive Guide
Should you retake your SAT or ACT?
When should you take the SAT or ACT?
Stay Informed
Get the latest articles and test prep tips!
Looking for Graduate School Test Prep?
Check out our top-rated graduate blogs here:
GRE Online Prep Blog
GMAT Online Prep Blog
TOEFL Online Prep Blog
Holly R. "I am absolutely overjoyed and cannot thank you enough for helping me!”
- How It Works
- PhD thesis writing
- Master thesis writing
- Bachelor thesis writing
- Dissertation writing service
- Dissertation abstract writing
- Thesis proposal writing
- Thesis editing service
- Thesis proofreading service
- Thesis formatting service
- Coursework writing service
- Research paper writing service
- Architecture thesis writing
- Computer science thesis writing
- Engineering thesis writing
- History thesis writing
- MBA thesis writing
- Nursing dissertation writing
- Psychology dissertation writing
- Sociology thesis writing
- Statistics dissertation writing
- Buy dissertation online
- Write my dissertation
- Cheap thesis
- Cheap dissertation
- Custom dissertation
- Dissertation help
- Pay for thesis
- Pay for dissertation
- Senior thesis
- Write my thesis
214 Best Big Data Research Topics for Your Thesis Paper

Finding an ideal big data research topic can take you a long time. Big data, IoT, and robotics have evolved. The future generations will be immersed in major technologies that will make work easier. Work that was done by 10 people will now be done by one person or a machine. This is amazing because, in as much as there will be job loss, more jobs will be created. It is a win-win for everyone.
Big data is a major topic that is being embraced globally. Data science and analytics are helping institutions, governments, and the private sector. We will share with you the best big data research topics.
On top of that, we can offer you the best writing tips to ensure you prosper well in your academics. As students in the university, you need to do proper research to get top grades. Hence, you can consult us if in need of research paper writing services.
Big Data Analytics Research Topics for your Research Project
Are you looking for an ideal big data analytics research topic? Once you choose a topic, consult your professor to evaluate whether it is a great topic. This will help you to get good grades.
- Which are the best tools and software for big data processing?
- Evaluate the security issues that face big data.
- An analysis of large-scale data for social networks globally.
- The influence of big data storage systems.
- The best platforms for big data computing.
- The relation between business intelligence and big data analytics.
- The importance of semantics and visualization of big data.
- Analysis of big data technologies for businesses.
- The common methods used for machine learning in big data.
- The difference between self-turning and symmetrical spectral clustering.
- The importance of information-based clustering.
- Evaluate the hierarchical clustering and density-based clustering application.
- How is data mining used to analyze transaction data?
- The major importance of dependency modeling.
- The influence of probabilistic classification in data mining.
Interesting Big Data Analytics Topics
Who said big data had to be boring? Here are some interesting big data analytics topics that you can try. They are based on how some phenomena are done to make the world a better place.
- Discuss the privacy issues in big data.
- Evaluate the storage systems of scalable in big data.
- The best big data processing software and tools.
- Data mining tools and techniques are popularly used.
- Evaluate the scalable architectures for parallel data processing.
- The major natural language processing methods.
- Which are the best big data tools and deployment platforms?
- The best algorithms for data visualization.
- Analyze the anomaly detection in cloud servers
- The scrutiny normally done for the recruitment of big data job profiles.
- The malicious user detection in big data collection.
- Learning long-term dependencies via the Fourier recurrent units.
- Nomadic computing for big data analytics.
- The elementary estimators for graphical models.
- The memory-efficient kernel approximation.
Big Data Latest Research Topics
Do you know the latest research topics at the moment? These 15 topics will help you to dive into interesting research. You may even build on research done by other scholars.
- Evaluate the data mining process.
- The influence of the various dimension reduction methods and techniques.
- The best data classification methods.
- The simple linear regression modeling methods.
- Evaluate the logistic regression modeling.
- What are the commonly used theorems?
- The influence of cluster analysis methods in big data.
- The importance of smoothing methods analysis in big data.
- How is fraud detection done through AI?
- Analyze the use of GIS and spatial data.
- How important is artificial intelligence in the modern world?
- What is agile data science?
- Analyze the behavioral analytics process.
- Semantic analytics distribution.
- How is domain knowledge important in data analysis?
Big Data Debate Topics
If you want to prosper in the field of big data, you need to try even hard topics. These big data debate topics are interesting and will help you to get a better understanding.
- The difference between big data analytics and traditional data analytics methods.
- Why do you think the organization should think beyond the Hadoop hype?
- Does the size of the data matter more than how recent the data is?
- Is it true that bigger data are not always better?
- The debate of privacy and personalization in maintaining ethics in big data.
- The relation between data science and privacy.
- Do you think data science is a rebranding of statistics?
- Who delivers better results between data scientists and domain experts?
- According to your view, is data science dead?
- Do you think analytics teams need to be centralized or decentralized?
- The best methods to resource an analytics team.
- The best business case for investing in analytics.
- The societal implications of the use of predictive analytics within Education.
- Is there a need for greater control to prevent experimentation on social media users without their consent?
- How is the government using big data; for the improvement of public statistics or to control the population?
University Dissertation Topics on Big Data
Are you doing your Masters or Ph.D. and wondering the best dissertation topic or thesis to do? Why not try any of these? They are interesting and based on various phenomena. While doing the research ensure you relate the phenomenon with the current modern society.
- The machine learning algorithms are used for fall recognition.
- The divergence and convergence of the internet of things.
- The reliable data movements using bandwidth provision strategies.
- How is big data analytics using artificial neural networks in cloud gaming?
- How is Twitter accounts classification done using network-based features?
- How is online anomaly detection done in the cloud collaborative environment?
- Evaluate the public transportation insights provided by big data.
- Evaluate the paradigm for cancer patients using the nursing EHR to predict the outcome.
- Discuss the current data lossless compression in the smart grid.
- How does online advertising traffic prediction helps in boosting businesses?
- How is the hyperspectral classification done using the multiple kernel learning paradigm?
- The analysis of large data sets downloaded from websites.
- How does social media data help advertising companies globally?
- Which are the systems recognizing and enforcing ownership of data records?
- The alternate possibilities emerging for edge computing.
The Best Big Data Analysis Research Topics and Essays
There are a lot of issues that are associated with big data. Here are some of the research topics that you can use in your essays. These topics are ideal whether in high school or college.
- The various errors and uncertainty in making data decisions.
- The application of big data on tourism.
- The automation innovation with big data or related technology
- The business models of big data ecosystems.
- Privacy awareness in the era of big data and machine learning.
- The data privacy for big automotive data.
- How is traffic managed in defined data center networks?
- Big data analytics for fault detection.
- The need for machine learning with big data.
- The innovative big data processing used in health care institutions.
- The money normalization and extraction from texts.
- How is text categorization done in AI?
- The opportunistic development of data-driven interactive applications.
- The use of data science and big data towards personalized medicine.
- The programming and optimization of big data applications.
The Latest Big Data Research Topics for your Research Proposal
Doing a research proposal can be hard at first unless you choose an ideal topic. If you are just diving into the big data field, you can use any of these topics to get a deeper understanding.
- The data-centric network of things.
- Big data management using artificial intelligence supply chain.
- The big data analytics for maintenance.
- The high confidence network predictions for big biological data.
- The performance optimization techniques and tools for data-intensive computation platforms.
- The predictive modeling in the legal context.
- Analysis of large data sets in life sciences.
- How to understand the mobility and transport modal disparities sing emerging data sources?
- How do you think data analytics can support asset management decisions?
- An analysis of travel patterns for cellular network data.
- The data-driven strategic planning for citywide building retrofitting.
- How is money normalization done in data analytics?
- Major techniques used in data mining.
- The big data adaptation and analytics of cloud computing.
- The predictive data maintenance for fault diagnosis.
Interesting Research Topics on A/B Testing In Big Data
A/B testing topics are different from the normal big data topics. However, you use an almost similar methodology to find the reasons behind the issues. These topics are interesting and will help you to get a deeper understanding.
- How is ultra-targeted marketing done?
- The transition of A/B testing from digital to offline.
- How can big data and A/B testing be done to win an election?
- Evaluate the use of A/B testing on big data
- Evaluate A/B testing as a randomized control experiment.
- How does A/B testing work?
- The mistakes to avoid while conducting the A/B testing.
- The most ideal time to use A/B testing.
- The best way to interpret results for an A/B test.
- The major principles of A/B tests.
- Evaluate the cluster randomization in big data
- The best way to analyze A/B test results and the statistical significance.
- How is A/B testing used in boosting businesses?
- The importance of data analysis in conversion research
- The importance of A/B testing in data science.
Amazing Research Topics on Big Data and Local Governments
Governments are now using big data to make the lives of the citizens better. This is in the government and the various institutions. They are based on real-life experiences and making the world better.
- Assess the benefits and barriers of big data in the public sector.
- The best approach to smart city data ecosystems.
- The big analytics used for policymaking.
- Evaluate the smart technology and emergence algorithm bureaucracy.
- Evaluate the use of citizen scoring in public services.
- An analysis of the government administrative data globally.
- The public values are found in the era of big data.
- Public engagement on local government data use.
- Data analytics use in policymaking.
- How are algorithms used in public sector decision-making?
- The democratic governance in the big data era.
- The best business model innovation to be used in sustainable organizations.
- How does the government use the collected data from various sources?
- The role of big data for smart cities.
- How does big data play a role in policymaking?
Easy Research Topics on Big Data
Who said big data topics had to be hard? Here are some of the easiest research topics. They are based on data management, research, and data retention. Pick one and try it!
- Who uses big data analytics?
- Evaluate structure machine learning.
- Explain the whole deep learning process.
- Which are the best ways to manage platforms for enterprise analytics?
- Which are the new technologies used in data management?
- What is the importance of data retention?
- The best way to work with images is when doing research.
- The best way to promote research outreach is through data management.
- The best way to source and manage external data.
- Does machine learning improve the quality of data?
- Describe the security technologies that can be used in data protection.
- Evaluate token-based authentication and its importance.
- How can poor data security lead to the loss of information?
- How to determine secure data.
- What is the importance of centralized key management?
Unique IoT and Big Data Research Topics
Internet of Things has evolved and many devices are now using it. There are smart devices, smart cities, smart locks, and much more. Things can now be controlled by the touch of a button.
- Evaluate the 5G networks and IoT.
- Analyze the use of Artificial intelligence in the modern world.
- How do ultra-power IoT technologies work?
- Evaluate the adaptive systems and models at runtime.
- How have smart cities and smart environments improved the living space?
- The importance of the IoT-based supply chains.
- How does smart agriculture influence water management?
- The internet applications naming and identifiers.
- How does the smart grid influence energy management?
- Which are the best design principles for IoT application development?
- The best human-device interactions for the Internet of Things.
- The relation between urban dynamics and crowdsourcing services.
- The best wireless sensor network for IoT security.
- The best intrusion detection in IoT.
- The importance of big data on the Internet of Things.
Big Data Database Research Topics You Should Try
Big data is broad and interesting. These big data database research topics will put you in a better place in your research. You also get to evaluate the roles of various phenomena.
- The best cloud computing platforms for big data analytics.
- The parallel programming techniques for big data processing.
- The importance of big data models and algorithms in research.
- Evaluate the role of big data analytics for smart healthcare.
- How is big data analytics used in business intelligence?
- The best machine learning methods for big data.
- Evaluate the Hadoop programming in big data analytics.
- What is privacy-preserving to big data analytics?
- The best tools for massive big data processing
- IoT deployment in Governments and Internet service providers.
- How will IoT be used for future internet architectures?
- How does big data close the gap between research and implementation?
- What are the cross-layer attacks in IoT?
- The influence of big data and smart city planning in society.
- Why do you think user access control is important?
Big Data Scala Research Topics
Scala is a programming language that is used in data management. It is closely related to other data programming languages. Here are some of the best scala questions that you can research.
- Which are the most used languages in big data?
- How is scala used in big data research?
- Is scala better than Java in big data?
- How is scala a concise programming language?
- How does the scala language stream process in real-time?
- Which are the various libraries for data science and data analysis?
- How does scala allow imperative programming in data collection?
- Evaluate how scala includes a useful REPL for interaction.
- Evaluate scala’s IDE support.
- The data catalog reference model.
- Evaluate the basics of data management and its influence on research.
- Discuss the behavioral analytics process.
- What can you term as the experience economy?
- The difference between agile data science and scala language.
- Explain the graph analytics process.
Independent Research Topics for Big Data
These independent research topics for big data are based on the various technologies and how they are related. Big data will greatly be important for modern society.
- The biggest investment is in big data analysis.
- How are multi-cloud and hybrid settings deep roots?
- Why do you think machine learning will be in focus for a long while?
- Discuss in-memory computing.
- What is the difference between edge computing and in-memory computing?
- The relation between the Internet of things and big data.
- How will digital transformation make the world a better place?
- How does data analysis help in social network optimization?
- How will complex big data be essential for future enterprises?
- Compare the various big data frameworks.
- The best way to gather and monitor traffic information using the CCTV images
- Evaluate the hierarchical structure of groups and clusters in the decision tree.
- Which are the 3D mapping techniques for live streaming data.
- How does machine learning help to improve data analysis?
- Evaluate DataStream management in task allocation.
- How is big data provisioned through edge computing?
- The model-based clustering of texts.
- The best ways to manage big data.
- The use of machine learning in big data.
Is Your Big Data Thesis Giving You Problems?
These are some of the best topics that you can use to prosper in your studies. Not only are they easy to research but also reflect on real-time issues. Whether in University or college, you need to put enough effort into your studies to prosper. However, if you have time constraints, we can provide professional writing help. Are you looking for online expert writers? Look no further, we will provide quality work at a cheap price.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Comment * Error message
Name * Error message
Email * Error message
Save my name, email, and website in this browser for the next time I comment.
As Putin continues killing civilians, bombing kindergartens, and threatening WWIII, Ukraine fights for the world's peaceful future.
Ukraine Live Updates
77 Data Management Essay Topic Ideas & Examples
🏆 best data management topic ideas & essay examples, 🔎 good research topics about data management, 📝 most interesting data management topics to write about.
- Toyota Corporation Data Resource Management Other than utilizing the knowledge and experience that the employees have, there is the need to use available information to grow and develop knowledge and expertise in employees.
- DNP Project Development: Data Management Plan With the help of this questionnaire, the researcher proves the appropriateness of the participants to the project. The results of this intervention depend on nurses and their willingness to learn something new and meditate. We will write a custom essay specifically for you by our professional experts 808 writers online Learn More
- Data Management in the Healthcare Industry The problem is in the fact that the computer software for managing the data and the used databases are not effective today because of the necessity to operate significant amounts of the information and share […]
- The British Library: Big Data Management The British Library needs the use of big data to keep track of user searches. Thus, the company uses big data to manage resources and meet searchers’ needs.
- Impact of Big Data Analytics on Risk Management Second, BDA permits the users to capture, analyze and store vast amounts of data enabling firms to have a corporate database essential in handling their resources according to business priorities.
- Big Data Analytics in Logistics Management This discussion post will argue that the use of big data warehouses and predictive analytics is the optimal application in logistics management and can ensure customers’ demands are met at the right quality, price, place, […]
- Application of Big Data Analytics in Logistics Management Logistics is an excellent use case for data due to the complicated and dynamic of this industry and the intricate structure of the supply chain.
- Data Breach Management in Business The second step is working to identify the extent and source of the breach, and this will be done through a forensic team that will investigate the issue and gives us answers.
- Data Management and Cybersecurity Namely, the principal standard of the HIPAA, as well as the concept of cybersecurity, have proven to factor into some of the key aspects of my professional and personal life.
- Cloud Technology for Data Management With exponential growth in smart device users, there is an increase in the volume of data generated from various smart devices, which differs according to all the fundamental V’s used to classify it as big […]
- Data Breach Management for an External Audience The relevance of the topic of the following White Paper is determined by the aggravation of information security problems in the context of the intensive improvement of technologies and data protection tools.
- Data Management at Three Big Worldwide Hospitals Out of the three hospitals only NYU Center and Mount Sinai Hospital have stroke care registries. In the effectiveness of surgical care NYU Hospital Center, Lenox Hill hospital, and Mount Sinai Hospital registered scores of […]
- Qualitative Data Organization and Management Another relevant strategy in terms of data management concerns the data volume and the inability to analyze it with no third-party assistance.
- Data Communication and Management Issues Because it operates at the data-link and network layers, it can be implemented as a basis network that offers services to a standard that has a network layer.3.
- Data Integrity and Management According to the guidelines published by Medicines and Healthcare products Regulatory Agency, the universal, suitable for any type of research data, integrity requirements consist of the following points: Establishing data criticality and inherent integrity risk…[with] […]
- Cleveland State University: Data Management Plan Encryption will be applied to files containing sensitive information to ensure safe electronic transfer of data. As earlier mentioned, information sharing will have to adhere to the data protection Act and GDPR policies.
- Big Data Management in the Healthcare Sector Big data in healthcare is a collective term used to refer to the process of collecting, analysing, leverage, and make sense of complex and immense patient and clinical data in a way that traditional data […]
- Big Data Management: Looker, IBM, Oracle and SAS Looker is one of the companies that provide superior systems for guiding companies to benefit from the concept of Big Data.
- MIT Libraries: Data Management Plan Evaluation After the completion of a project or research, it is recommended to keep data for three more years while ensuring safety and accessibility.
- Risk and Internal Data Management This system will ensure that the response to the disaster or incident and that communication of the information to the relevant stakeholders is done simultaneously.
- Data Management in School Technologies Data is destroyed primarily to free up space for new data, to protect the customer or the patient, and upon request.
- Data Management Plan: Processing and Storing Information The Internet of Food and Farm 2020 data management plan provides all the necessary details on how the information created and gathered throughout the project will be processed and stored.
- Issues of Data Management in Technology After a careful analysis of the websites of many recruitment agencies, I settled on two that suffice for this assignment. I can argue that there are ethical technological advancements that can be used to lower […]
- Virgin Mobile Company: Human Resource Data Management The collection of HR and L&D data is of paramount importance for any organisation for two primary reasons: it proves the company’s compliance with certain regulations, and it ensures effective planning and development of the […]
- Cockpit Data Management Solutions: Strengths/Flaws The Cockpit Data Management Solutions system has been designed to ensure fast and efficient use and performance of tasks, as is the goal of most information systems.
- Effective Business Planning: HR and Data Management One of the most valuable reasons to promote the participation of HR in the business planning is the relation between the construction of executable plan and consideration of the special skills and knowledge possessed by […]
- Big Data Management at Carrolls Irish Gifts It is necessary to note that the stakeholders of the systems’ implementation will be the company’s employees and its customers. In the first place, it is possible to evaluate tangible benefits of the use of […]
- Company Metadata and Master Data Management Metadata can be used in describing digital data in a specific discipline, and by relating the information and the context of the data files.
- Data Warehousing as an Information Management Tool The array of data stored in the warehouse allows the management to focus on the company as a whole instead of focusing on an organization in terms of departments.
- Organizational Information Management: Data Warehousing Warehoused data is used to support decision making; the stored information is used for further analysis and identification of trends and variations in a given phenomenon.
- Impact of Virtualization Technologies on Data Management in Organizations The workforce that this firm would require for the management of the data and maintenance of the hardware will be reduced.
- The Hewlett Packard Company Data Management Evidently, from the case analysis, the processing and exchange of information at the HP Company occurred from various processing points as opposed to single repository and processing unit.
- Data Storage: Ethical and Legal Issues in Terms of Management Illegal access of information over the internet can arguably be said to be the most disturbing and biggest challenge that has come along with the internet.
- Financial Implications of the Data Management Problem In spite of the fact the advantages of using the modern approaches to collecting and storing the data are obvious, there are a lot of challenges for developing the tendency of changing the traditional approaches […]
- Ethical and Legal Implications of the Data Management Problem To avoid the ethical and legal conflicts based on the choice of the effective usage of the necessary information to care the patient and the issues of confidentiality and privacy, it is necessary to provide […]
- Data Management Challenges in Healthcare The data management problem within the healthcare industry can be resolved only using the complex approach based on the effective plan which includes such important components as the implementation of electronic health records, the orientation […]
- Club IT’s Data Management The central issue inherent in data management, particularly in the case of Club IT, is that the data will be coming in from multiple sources and rapidly.
- Collaborative Data Management for Longitudinal Studies
- Is It Time to Revisit Your Data Management Strategy
- Redefining the Data Management Strategy: A Way to Leverage the Huge Chunk of Data
- The Concept of Data Management Arose in the 1980s
- Exploring Data Management Support Needs of Bioengineering and Biomedical Research Faculty
- GML Data Management: Framework and Prototype
- Epidemiological Data Management during an Outbreak of Ebola Virus
- Data Management Platform Provides as a Centralized System for Collecting and Analyzing Data
- Data Management Integration of Habitable Environments
- Database Data Management Issues in Amazon
- Efficient Algorithmic Techniques for Several Multidimensional Geometric Data Management
- Data Management in Excel: Data Analysis and Calculation
- From Data Management to Decision Making for Empowerment
- Data Management Across the Continuum Assignment
- Academic Institution Undergoing Audit to Improve Data Management
- Adopting Electronic Data Management in the Health Care Industry
- Data Management and Communication for Open Computational Neuroscience
- Dealing With Identifier Variables in Data Management and Analysis
- Improving the New Data Management Technologies and Leverage
- Integrated Process and Data Management for Healthcare Applications
- Data Manager Must-Have Resume Skills and Keywords
- Exploring Data Management Support Needs of Bioengineering
- Dealing with Identifier Variables in Data Managements
- Autonomic Data Management: The Ability to Manage Itself Automatically Without a Team
- Data Management for Conceptual Design and Findings of Market-Research Projects
- Online Data Management System for On-Farm Trials
- Automated Record for Data Management System
- Data Management Strategy: A Way to Leverage The Huge Chun
- Enterprise Data Management: Strategy and Governance
- Data Management Challenges and Solutions for the Modern Organization
- National Data Centre and Financial Statistics Office: A Conceptual Design for Public Data Management
- Data Management Practices for Collaborative Research
- Distributed Operating System and Infrastructure for Scientific Data Management
- How Data Management Tools and Applications Can Help
- Define Roles and Assign Responsibilities for Data Management
- Data Management for Workforce Services: Optimize the Productivity of Employees
- Evolution of Data Management Systems and Their Security
- Data Management Software Provides: Microsoft MySQL, PostgreSQL, Microsoft Access, or Oracle
- Data Management for Photovoltaic Power Plants Operation
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, March 2). 77 Data Management Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/data-management-essay-topics/
"77 Data Management Essay Topic Ideas & Examples." IvyPanda , 2 Mar. 2024, ivypanda.com/essays/topic/data-management-essay-topics/.
IvyPanda . (2024) '77 Data Management Essay Topic Ideas & Examples'. 2 March.
IvyPanda . 2024. "77 Data Management Essay Topic Ideas & Examples." March 2, 2024. https://ivypanda.com/essays/topic/data-management-essay-topics/.
1. IvyPanda . "77 Data Management Essay Topic Ideas & Examples." March 2, 2024. https://ivypanda.com/essays/topic/data-management-essay-topics/.
Bibliography
IvyPanda . "77 Data Management Essay Topic Ideas & Examples." March 2, 2024. https://ivypanda.com/essays/topic/data-management-essay-topics/.
- Business Intelligence Research Topics
- Computers Essay Ideas
- Information Management Paper Topics
- Machine Learning Ideas
- Data Mining Titles
- Digital Transformation Topics
- Encryption Essay Titles
- Hacking Essay Topics
- Process Management Questions
- Security Management Essay Ideas
- Quality Assurance Questions
- Auditing Paper Topics
- Agile Project Management Research Topics
- Corporate Strategy Paper Topics
- SAT BootCamp
- SAT MasterClass
- SAT Private Tutoring
- SAT Proctored Practice Test
- ACT Private Tutoring
- Academic Subjects
- College Essay Workshop
- Academic Writing Workshop
- AP English FRQ BootCamp
- 1:1 College Essay Help
- Online Instruction
- Free Resources
500 Good Research Paper Topics
Bonus Material: Essential essay checklist
Writing a research paper for a class and not sure how to start?
One of the most important steps to creating a great paper is finding a good topic!
Here’s a hand-drafted list from a Princeton grad who has helped professors at Harvard and Yale edit their papers for publication and taught college writing at the University of Notre Dame and .
What’s more, we give you some foolproof formulas for creating your own paper topic to fit the requirements of your class.
Using these simple formulas, we’ve helped hundreds of students turn a B- paper topic into an A+ paper topic.
Keep reading for our list of 500 vetted research paper topics and our magic formulas for creating your own topic!
Of course, if you want help learning to write research papers tailored to your individual needs, check out our one-on-one writing coaching or academic writing workshop . Set up a free consultation to see how we can help you learn to write A+ papers!
Jump to paper topics in:
European & Mediterranean History
African history, asian history, history of the pre-columbian americas.
- Latin American History
History of Science
Politics & public policy, education & education policy, political theory, science policy.
- Health Sciences & Psychology

What is a research paper?
In order to write a good research paper, it’s important to know what it is!
In general, we can divide academic writing into three broad categories:
- Analytical: analyze the tools an author uses to make their point
- Research: delve deeply into a research topic and share your findings
- Persuasive : argue a specific and nuanced position backed by evidence
What’s the difference between an analytical paper and a research paper? For an analytical paper, it’s okay to just use one or two sources (a book, poem, work of art, piece of music, etc.) and examine them in detail. For a research paper, however, the expectation is that you do, well . . . research .

The depth of research that you’re expected to do will depend on your age and the type of class you’re taking.
In elementary or middle school, a “research paper” might mean finding information from a few general books or encyclopedias in your school library.
In high school, your teachers might expect you to start using information from academic articles and more specific books. You might use encyclopedias and general works as a starting point, but you’ll be expected to go beyond them and do more work to synthesize information from different perspectives or different types of sources. You may also be expected to do “primary research,” where you study the source material yourself, instead of synthesizing what other people have written about the source material.
In college, you’ll be required to use academic journals and scholarly books, and your professors will now expect that you be more critical of these secondary sources, noticing the methodology and perspectives of whatever articles and books you’re using.
In more advanced college courses, you’ll be expected to do more exhaustive surveys of the existing literature on a topic. You’ll need to conduct primary research that makes an original contribution to the field—the kind that could be published in a journal article itself.
For a walkthrough of the 12 essential steps to writing a good paper, check out our step-by-step guide .

Working on a research paper? Grab our free checklist to make sure your essay has everything it needs to earn an A grade.
Get the essential essay checklist
What makes a good research paper topic?
One of the most important features of a research paper topic is that it has a clear, narrow focus.
For example, your teacher may assign you to write a research paper related to the US Revolutionary War. Does that mean that your topic should be “the US Revolutionary War”?
Definitely not! There’s no way to craft a good paper with in-depth research with such a broad topic. (Unless you’re in elementary or middle school, in which case it’s okay to have a more general topic for your research paper.)
Instead, you need to find a more specific topic within this broader one. There are endless ways that you can make this narrower! Some ideas generated from this one broader topic might be:
- Causes of the US Revolutionary War
- Changes in military strategy during the Revolutionary War
- The experiences of Loyalists to England who remained in the American colonies during the Revolutionary War
- How the Revolutionary War was pivotal for the career of Alexander Hamilton
- The role of alliances with France during the US Revolutionary War
- The experiences of people of color during the Revolutionary War
- How George Washington’s previous military career paved the way for his leadership in the Revolutionary War
- The main types of weaponry during the Revolutionary War
- Changes in clothing and fashion over the courses of the Revolutionary War
- How Valley Forge was a key moment in the Revolutionary War
- How women contributed to the Revolutionary War
- What happened in Amherst, Massachusetts during the Revolutionary War
- Field medicine during the Revolutionary War
- How the Battle of Saratoga was a turning point in the Revolutionary War
- How different opinions about the Revolutionary War were reflected in poetry written during that time
- Debates over abolition during the Revolutionary War
- The importance of supply chains during the Revolutionary War
- Reactions to the US Revolutionary war in Europe
- How the US Revolutionary war impacted political theory in England and France
- Similarities and differences between the US Revolutionary War and the French Revolution
- Famous paintings inspired by the US Revolutionary War
- Different ways that the US Revolutionary War has been depicted in modern contemporary culture
- The appropriation of the “Boston Tea Party” by US politicians in the 2010s
This list could go on forever!

In fact, any of these topics could become even more specific. For example, check out the evolution of this topic:
- Economic causes of the Revolutionary war
- The way that tax policies helped lead to the Revolutionary War
- How tax laws enacted 1763–1775 helped lead to the Revolutionary War
- How the tax-free status of the British East India Company helped lead to the Revolutionary War
- How the 1773 tax-free status of the British East India Company helped lead to the Revolutionary War, as reflected in letters written 1767–1775
- How the 1773 tax-free status of the British East India Company helped lead to the Revolutionary War, as reflected in letters written by members of the Sons of Liberty 1767–1775
As you advance in your educational career, you’ll need to make your topic more and more specific. Steps 1–3 of this topic might be okay in high school, but for a college research paper steps 4–7 would be more appropriate!
As you craft your research paper topic, you should also keep in mind the availability of research materials on your subject. There are millions of topics that would make interesting research papers, but for which you yourself might not be able to investigate with the primary and secondary sources to which you have access.
Access to research materials might look like:
- To the best of our knowledge, the sources exist somewhere
- The source isn’t behind a paywall (or you or your school can pay for it)
- Your school or local library has a copy of the source
- Your school or local library can order a copy of the source for you
- The source is in a language that you speak
- The source has been published already (there’s tons of amazing research that hasn’t been published yet, a frustrating problem!)
- You can access the archive, museum, or database where the primary source is held—this might mean online access or travel! To access a source in an archive or museum you’ll often need permission, which often requires a letter of support from your school.
If you’re not sure about access to source materials, talk to a librarian! They’re professionals for this question.
Finally, pick a research topic that interests you! Given that there are unlimited research topics in the world and many ways to adapt a broad topic, there should absolutely be a way to modify a research topic to fit your interests.

Want help learning to write an amazing research paper? Work one-on-one with an experienced Ivy-League tutor to improve your writing skills or sign up for our bestselling academic writing workshop .
Insider tips to generate your own research paper topic
Use these formulas to generate your own research paper topics:
- How did X change over a period of time (year, decade, century)?
- What is the impact (or consequences) of X?
- What led to X?
- What is the role of X in Y?
- How did X influence Y?
- How did X become Y?
- How was X different from Y?
- How is X an example of Y?
- How did X affect Y?
- What were some reactions to X?
- What are the most effective policies to produce X result?
- What are some risks of X?
- How is our current understanding of X incorrect? (advanced)
- What happens if we look at X through the lens of Y theory or perspective? (advanced)
A good research paper topic often starts with the question words—why, how, what, who, and where. Remember to make it as specific as possible!

Good research paper topics
These research paper topics have been vetted by a Princeton grad and academic book editor!
- How did European rivalries (British vs French) impact North American history?
- What was the role of British and French alliances with indigneous tribes during the Seven Years’ War?
- Reactions to the 1754 Albany Congress among North American intellectual figures
- How the Albany Plan served as a model for future attempts at union among the North American colonies
- How did different religious identities (Calvinist, Catholic, etc.) play a role in the aftermath of the Seven Years’ War?
- What were the consequences of the 1763 Treaty of Paris?
- How did the Seven Years’ War impact British debt and colonial economics?
- What were some causes of the US Revolutionary War?
- How did military strategy change during the Revolutionary War?
- What were the experiences of Loyalists to England who remained in the American colonies during the Revolutionary War?
- How was the Revolutionary War pivotal for the career of Alexander Hamilton?
- What was the role of alliances with France during the US Revolutionary War?
- What were the experiences of people of color during the Revolutionary War?
- How did George Washington’s previous military career pave the way for his leadership in the Revolutionary War?
- What were the main types of weaponry during the Revolutionary War? How did that affect the options for military strategies?
- How did clothing and fashion change over the courses of the Revolutionary War?
- How was Valley Forge a key moment in the Revolutionary War?
- How did women contribute to the Revolutionary War?
- What happened in Amherst, Massachusetts (or any other specific location) during the Revolutionary War?
- What was field medicine like during the Revolutionary War?
- How was the Battle of Saratoga a turning point in the Revolutionary War?
- How were different opinions about the Revolutionary War reflected in poetry written during that time?
- What were the debates over abolition during the Revolutionary War?
- What was the role of supply chains during the Revolutionary War?
- What were reactions to the US Revolutionary war like in Europe? What does that tell us about politics in England, France, the Netherlands, etc?
- How did the US Revolutionary war impact political theory in England and France?
- What are similarities and differences between the US Revolutionary War and the French Revolution?
- What are some famous paintings inspired by the US Revolutionary War? What do differences between these paintings tell us about how the artists who created them saw the war?
- What are some different ways that the US Revolutionary War has been depicted in modern contemporary culture? What does that tell us?
- How was the story of the “Boston Tea Party” appropriated by US politicians in the 2010s, and why?
- What was the difference between the Federalists and the Jeffersonians?
- How did the 1797 XYZ Affair lead to the Quasi-War with France?
- How were loans from European countries and companies (France, Spain, Dutch bankers) key to the early US?
- What were reactions to the Constitutional Convention of 1787?
- Why did the US remain neutral during the French Revolution?
- How did the Alien and Sedition acts contribute to the election of Thomas Jefferson as president?
- What was the US’s reaction to the Haitian revolution? Why did the US not recognize Haitian independence until 1862?
- What were the reactions to John Jay’s Treaty of 1794?
- How have the remarks made by George Washington in his Farewell Address inspired isolationist policies?
- How did interpretations of the Monroe Doctrine change over the decades since its creation?
- How did the Roosevelt Corollary and Lodge Corollary change and expand the Monroe Doctrine?
- How did the presence of US companies like the United Fruit Company affect US military interventions in Latin America?
- How was the Monroe Doctrine invoked in the Cuban Missile Crisis of 1962?
- How was US culture shaped by the Cold War?
- How did ecology play a role in the rise of Ancient Egypt?
- How did water management technologies impact Ancient Egypt?
- How did bureaucracies function in Ancient Egypt?
- How did Egyptian art influence Ancient Greek art?
- Who could be a citizen in Athens in the 5th century BCE? What does this tell us about classical Athenian society?
- What was the impact of the Peloponnesian War?
- What was the impact of Alexander the Great’s attempt to create an empire?
- How does the way that Alexander the Great is represented in art demonstrate conceptions about the relationship between the human and the divine?
- Was there a conception of race in the ancient world? How were these ideas different from our own modern conceptions of race?
- What was the role of debt slavery in the Roman republic? How were these policies ended, and what is the significance of the end of debt slavery? What kinds of slavery remained?
- To what degree does the movie Gladiator accurately the Roman Empire in 176–192 CE?
- What was the role of slavery in managing the large latifundia ?
- How and why did the emperor Constantine I adopt Christianity?
- How did patterns of urbanism in the latter Roman empire change? What does this tell us about challenges being faced at that time?
- What do reactions to the Byzantine empress Theodora tell us about ideas of gender in 6th-century Byzantium?
- How did scientific advancements in Islamic Spain influence the rest of Europe?
- What was the relationship between Muslim, Christian, and Jewish populations in Islamic Spain? How does this compare to the experience of Muslim and Jewish populations in Christian Spain?
- How did medieval troubadour poetry represent a new idea of romantic relationships?
- What are similarities and differences between medieval troubadour poetry and lyric poetry in Ancient Greece?
- What do letters between women and popes tell us about gender, power, and religion in medieval Europe?
- In what ways was Hildegard of Bingen groundbreaking for her time?
- Who produced beer in medieval England, and what does this tell us about society?
- How did the adoption of hops affect the production and distribution of beer?
- How did beer production allow some women a way to be financially independent?
- How was clothing used to mark religious and cultural identities in 15th- and 16th-century Spain?
- How did print culture change relationships and courting in Georgian England?
- How did churches function as social gathering spaces in Georgian England?
- To what degree is Netflix’s Bridgerton series historically accurate?
- How did ideas of love change in the 18th century? How did philosophy play a role in this?
- When were Valentine cards first commercially available? What does that show us about cultural ideas of love and courtship?
- What were the consequences of the desertification of the Sahara?
- How did trade links on the Red Sea influence Nubian culture?
- How did Carthage build power in Northern Africa around 600–500 BCE?
- What was the impact of the Mercenary War (241–238 BCE) in Carthage?
- How did the Roman province of Africa play a key role in financing the Roman Empire?
- What were the consequences of the Donatist division in the 300s in Northern Africa?
- What was the impact of the large-scale movement of Bedouins from the Arabian peninsula into the Maghreb?
- How was Mande society organized in the Mali Empire?
- What was the role of the book trade in Timbuktu? What does this tell us about culture and learning in the Mali Empire?
- How did Aksum use trade to build wealth and power?
- What do Nok terracotta sculptures tell us about Nok culture?
- How did the Luba Empire create a centralized political system? How did the idea of spiritual kins ( balopwe ) play a role in this system?
- How did tax collection work in the Lunda empire?
- What does it mean to say that the Ajuran Empire was a hydraulic empire? How did control over water resources allow the Ajuran Empire to build and consolidate power?
- What is the significance of diplomatic ties between the Somai Ajuran Empire and Ming dynasty China?
- How did the tribute system in the Kingdom of Kongo help to stimulate interregional trade?
- What was the impact of the introduction of maize and cassava to the Kingdom of Kongo?
- How did women wield influence in the Kingdom of Benin?
- How did the Industrial Revolution in Europe help lead to the Scramble for Africa 1878–1898?
- What were the consequences of the Second Boer War?
- What happened in the Year of Africa (1960)?
- How did the Han dynasty consolidate power in frontier regions?
- How and why did the Han dynasty nationalize the private salt and iron industries in 117 BCE?
- What are the earliest records of papermaking, and what is the significance of this invention?
- What was the role of Daoist religious societies in rebellions at the end of the Han dynasty (Yellow Turban Rebellion, Five Pecks of Rice Rebellion)?
- What do tomb paintings tell us about ancient Chinese society?
- What was the impact of the Sui dynasty’s standardization and re-unification of the coinage?
- What was the role of standardized testing in Sui dynasty and Tang dynasty China?
- Why is the Tang dynasty often regarded as a golden age of cosmopolitan culture in Chinese history?
- What was the role of slavery in imperial China?
- How did the rise of jiedushi (regional military governments) undermine the civil-service system? What were the consequences of this?
- How did Tang dynasty China exert power over Japan and Korea?
- What was the Three Departments and Six Ministries system in imperial China and how did it work?
- What does the appearance of Inca, Maya, and Aztec goods in North America (Utah, Canada) and the appearance of goods from the Great Lakes region in Maya and Aztec ruins tell us about trade in the Pre-Columbian Americas?
- How did celebration of maize play a central role in Mesoamerican cultures?
- How did the Aztec empire use relationships with client city-states to establish power? How did the Aztec empire use taxation to exert power?
- How did the luxury good trade impact Aztec political power?
- How did the building of roads play a key role in the Aztec empire?
- How and why has archaeology played a pivotal role in expanding our understanding of the pre-Columbian Americas?
- What are some common misconceptions about the Americas in the year 1491? Why do these misconceptions exist?
Latin American History (post-1492)
- How and why did the Spanish appropriate Aztec sites of significance (e.g. Mexico City at the site of Tenochtitlan)?
- What were reactions among Latin American intellectuals (e.g. Luis María Drago, Alejandro Álvarez and Baltasar Brum) to the Monroe Doctrine?
- How was the US’s involvement in the Venezuela Crisis of 1902–1903 a pivotal turning point in the relationship between the US and Latin American countries?
- What were the effects of the US’s involvement in the Cuban War for Independence?
- How did the Roosevelt Corollary of 1904 benefit the US?
- How did Simon Bolivar’s time in Europe affect his ideas about Latin American independence?
- How did 19th century academic societies play a role in the advancement of scientific discoveries? Who was excluded from these societies?
- How was music connected to the sciences in medieval thinking?
- When was the concept of zero first used, and how was it instrumental for advancements in math?
- What role did Islamic Spain play in the spread of scientific advancements in medieval Europe?
- What role has translation between languages played in the development of sciences?
- Why were Galileo’s ideas about astronomy controversial at the time?
- What was the connection between art and advancements in human anatomy?
- Why were Darwin’s ideas about natural selection controversial at the time?
- To what degree does the film Master and Commander accurately depict the voyages of Charles Darwin?
- How did the discovery of quinine and other medical innovations help to facilitate the European colonization of Africa?
- How and why was the internet invented?
- Does Virgil’s Aeneid celebrate the new Roman Empire or subvert it?
- Why was the poet Ovid exiled from Rome?
- What are the pagan influences in Beowulf ? What are the Christian elements in Beowulf ? What does that tell us about late Anglo-Saxon England?
- How does Chaucer’s Canterbury Tales reflect gender roles in late medieval England?
- How does Dante’s Inferno draw on book IV of Virgil’s Aeneid ?
- How are gender roles presented and subverted in Shakespeare’s plays?
- To what degree did Henry David Thoreau live out the ideals he described in Walden in his own life?
- How did the serialized publication of novels affect the way that they were written?
- Does Dickens’ novel A Tale of Two Cities accurately portray the French Revolution?
- How did 18th-century novels propagate the idea of marrying for love?
- What did contemporary readers think about Jane Austen and her novels?
- To what degree do Jane Austen’s novels reflect economic realities for women in Regency England? What do they leave out?
- How did Lord Byron’s personal life affect his poetry?
- What do we know about the romantic life of Emily Dickinson?
- What were the religious movements that influenced the writer George Eliot, and how do those influences appear in her novels?
- In what ways were Walt Whitman’s writings new or different?
- How did British poets react to the horrors of Word War I?
- What do Tolkien’s letters reveal about the ways in which the two world wars influenced his writings?
- How did the friendship between CS Lewis and Tolkien affect their respective writings?
- What are the arguments for and against Catalonian independence from Spain?
- What are the arguments for and against Scottish independence from the United Kingdom?
- What are some risks of contact sports, especially for children?
- What are the most effective policies for combating childhood obesity?
- What are the most effective policies for reducing gun violence?
- Which countries have the longest life expectancy and why?
- What are some differences between the healthcare system in the US and in European countries? Which country has the most similar system to the US?
- What policies for parental leave exist in different countries? What are some effects of these policies?
- Has the drinking age in the US always been 21? What have been some different policies, and what were some consequences of them?
- What is the debate around museum artifacts like the Elgin Marbles in London or the Benin Bronzes in Berlin?
- How have politicians attempted to control population growth in different countries, either directly or indirectly? What have been some effects of these policies?
- Which countries have the most gender parity reflected in national governments? How have they accomplished this?
- How has public funding of K-12 education changed since the 1930s in the US?
- How has public funding of higher education changed in the US?
- What is early childhood education like in different countries?
- What are some effects of free or reduced-cost meals in schools?
- How does access to menstrual products affect education outcomes for girls in different countries?
- What was the impact of Rousseau’s writings on education?
- How did Plato’s ideal forms of government reflect contemporary Athenian concerns about the unruly masses ( demos )?
- How did Aristotle justify slavery?
- How has wealth inequality increased in recent decades?
- How is inflation calculated, and what are the implications of this methodology?
- How have genetically-engineered crops changed the way that the planet feeds itself?
- How has animal testing changed since 2000?
- How is animal testing regulated differently in different countries?
Health Sciences and Psychology
- How do different societies reflect the natural circadian rhythms of the human body?
- How does secondhand smoke affect the human body?
- How does lack of sleep affect the body?
- How does stress affect the body?
- What are some ways to reduce stress?
- How have cancer treatments changed in the past 30 years?
- Why is it hard to find a “cure” for cancer?
- How has the Human Genome Project changed medical science?
- How were the Covid vaccines developed so quickly? What is the difference between the various Covid vaccines that have been developed?
Ready to start working on your research paper?
Our Ivy-League tutors can provide one-on-one writing coaching . Get expert help in selecting a topic that fits your assignment, finding research sources, creating an outline, drafting your paper, and revising for clarity.
Our writing coaches have helped students turn B- papers to A+ papers with just a few sessions together. We have experience working with students of all ages and writing abilities, from middle school students to college students at the nation’s top universities. What’s more, we’ll teach you how to write so that it’s easier the next time around!
A few times per year we also offer our bestselling academic writing workshop . Save your spot here !
Related posts
99 Great Handpicked Ideas for Argumentative Essays 12 Essential Steps for Writing an Argumentative Essay The 13 SAT and ACT Grammar Rules to Know 16 Essential Literary Devices to Know

Emily graduated summa cum laude from Princeton University and holds an MA from the University of Notre Dame. She was a National Merit Scholar and has won numerous academic prizes and fellowships. A veteran of the publishing industry, she has helped professors at Harvard, Yale, and Princeton revise their books and articles. Over the last decade, Emily has successfully mentored hundreds of students in all aspects of the college admissions process, including the SAT, ACT, and college application essay.
CHECK OUT THESE RELATED POSTS

The Hardest Digital SAT Reading Questions
March 10, 2024
Check out the hardest reading comprehension questions you might see on the digital SAT, along with a guide on how to approach …

Can Chat GPT Write your College Essay?
February 21, 2024
Writing your college application essays? More and more students are trying to see if ChatGPT can help with their Common App essays. In this guide, we’ll break down how to use ChatGPT, if it’s actually helpful, and …

PSAT to digital SAT Score Conversion
February 19, 2024
Want to use your PSAT score to predict how you’ll do on the SAT? Our post uses the most updated date to help you convert your PSAT score into an SAT score.

Your Guide to Writing a Letter of Continued Interest to Colleges
February 13, 2024
Deferred or waitlisted from your dream school? You can still increase your chances of admission by writing a letter of continued interest, which …

SAT Math: What You Need to Know
February 8, 2024
There are two math sections on the SAT. Your performance on these contributes to 50% of your SAT composite score. Find strategies, SAT Math content, and more in this detailed post!

5 Digital SAT Reading Tips for a Top Score
February 1, 2024
What do you need to know to earn a high score on SAT Reading? We've got the expert answers and the strategies right here.

Digital SAT Score Range Breakdown
Wondering about what the SAT score range is, or what it means? Want to know how to put your score in context? In this guide, we’ll cover what the SAT score range is, how to interpret …

Guide to Digital SAT Scoring
Add excerpt here. Can reuse meta description.

What’s on the SAT in 2024?
January 23, 2024
Our comprehensive guide breaks down all content areas you need to know for the most recent version of the SAT, including math concepts, grammar, and …

12 SAT Grammar Rules for a Perfect Score
On the digital SAT, grammar questions make up almost a quarter of your total Reading and Writing score. In this post, we break down every grammar concept you need to know…
Privacy Preference Center
Privacy preferences.
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
- Working with sources
How to Find Sources | Scholarly Articles, Books, Etc.
Published on June 13, 2022 by Eoghan Ryan . Revised on May 31, 2023.
It’s important to know how to find relevant sources when writing a research paper , literature review , or systematic review .
The types of sources you need will depend on the stage you are at in the research process , but all sources that you use should be credible , up to date, and relevant to your research topic.
There are three main places to look for sources to use in your research:
Research databases
- Your institution’s library
- Other online resources
Table of contents
Library resources, other online sources, other interesting articles, frequently asked questions about finding sources.
You can search for scholarly sources online using databases and search engines like Google Scholar . These provide a range of search functions that can help you to find the most relevant sources.
If you are searching for a specific article or book, include the title or the author’s name. Alternatively, if you’re just looking for sources related to your research problem , you can search using keywords. In this case, it’s important to have a clear understanding of the scope of your project and of the most relevant keywords.
Databases can be general (interdisciplinary) or subject-specific.
- You can use subject-specific databases to ensure that the results are relevant to your field.
- When using a general database or search engine, you can still filter results by selecting specific subjects or disciplines.
Example: JSTOR discipline search filter

Check the table below to find a database that’s relevant to your research.
Google Scholar
To get started, you might also try Google Scholar , an academic search engine that can help you find relevant books and articles. Its “Cited by” function lets you see the number of times a source has been cited. This can tell you something about a source’s credibility and importance to the field.
Example: Google Scholar “Cited by” function
Boolean operators
Boolean operators can also help to narrow or expand your search.
Boolean operators are words and symbols like AND , OR , and NOT that you can use to include or exclude keywords to refine your results. For example, a search for “Nietzsche NOT nihilism” will provide results that include the word “Nietzsche” but exclude results that contain the word “nihilism.”
Many databases and search engines have an advanced search function that allows you to refine results in a similar way without typing the Boolean operators manually.
Example: Project Muse advanced search

The only proofreading tool specialized in correcting academic writing - try for free!
The academic proofreading tool has been trained on 1000s of academic texts and by native English editors. Making it the most accurate and reliable proofreading tool for students.
Try for free
You can find helpful print sources in your institution’s library. These include:
- Journal articles
- Encyclopedias
- Newspapers and magazines
Make sure that the sources you consult are appropriate to your research.
You can find these sources using your institution’s library database. This will allow you to explore the library’s catalog and to search relevant keywords. You can refine your results using Boolean operators .
Once you have found a relevant print source in the library:
- Consider what books are beside it. This can be a great way to find related sources, especially when you’ve found a secondary or tertiary source instead of a primary source .
- Consult the index and bibliography to find the bibliographic information of other relevant sources.
You can consult popular online sources to learn more about your topic. These include:
- Crowdsourced encyclopedias like Wikipedia
You can find these sources using search engines. To refine your search, use Boolean operators in combination with relevant keywords.
However, exercise caution when using online sources. Consider what kinds of sources are appropriate for your research and make sure the sites are credible .
Look for sites with trusted domain extensions:
- URLs that end with .edu are educational resources.
- URLs that end with .gov are government-related resources.
- DOIs often indicate that an article is published in a peer-reviewed , scientific article.
Other sites can still be used, but you should evaluate them carefully and consider alternatives.
If you want to know more about ChatGPT, AI tools , citation , and plagiarism , make sure to check out some of our other articles with explanations and examples.
- ChatGPT vs human editor
- ChatGPT citations
- Is ChatGPT trustworthy?
- Using ChatGPT for your studies
- What is ChatGPT?
- Chicago style
- Paraphrasing
Plagiarism
- Types of plagiarism
- Self-plagiarism
- Avoiding plagiarism
- Academic integrity
- Consequences of plagiarism
- Common knowledge
You can find sources online using databases and search engines like Google Scholar . Use Boolean operators or advanced search functions to narrow or expand your search.
For print sources, you can use your institution’s library database. This will allow you to explore the library’s catalog and to search relevant keywords.
It is important to find credible sources and use those that you can be sure are sufficiently scholarly .
- Consult your institute’s library to find out what books, journals, research databases, and other types of sources they provide access to.
- Look for books published by respected academic publishing houses and university presses, as these are typically considered trustworthy sources.
- Look for journals that use a peer review process. This means that experts in the field assess the quality and credibility of an article before it is published.
When searching for sources in databases, think of specific keywords that are relevant to your topic , and consider variations on them or synonyms that might be relevant.
Once you have a clear idea of your research parameters and key terms, choose a database that is relevant to your research (e.g., Medline, JSTOR, Project MUSE).
Find out if the database has a “subject search” option. This can help to refine your search. Use Boolean operators to combine your keywords, exclude specific search terms, and search exact phrases to find the most relevant sources.
There are many types of sources commonly used in research. These include:
You’ll likely use a variety of these sources throughout the research process , and the kinds of sources you use will depend on your research topic and goals.
Scholarly sources are written by experts in their field and are typically subjected to peer review . They are intended for a scholarly audience, include a full bibliography, and use scholarly or technical language. For these reasons, they are typically considered credible sources .
Popular sources like magazines and news articles are typically written by journalists. These types of sources usually don’t include a bibliography and are written for a popular, rather than academic, audience. They are not always reliable and may be written from a biased or uninformed perspective, but they can still be cited in some contexts.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
Ryan, E. (2023, May 31). How to Find Sources | Scholarly Articles, Books, Etc.. Scribbr. Retrieved March 20, 2024, from https://www.scribbr.com/working-with-sources/finding-sources/
Is this article helpful?

Eoghan Ryan
Other students also liked, types of sources explained | examples & tips, primary vs. secondary sources | difference & examples, boolean operators | quick guide, examples & tips, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”
Robert L. Bogomolny Library
What's happening at the library and items of interest to the UB community
Using Databases to Find a Research Paper Topic
It’s almost mid-semester and you still haven’t picked a topic for your research paper. No worries! The RLB Library has a few tips and tools that can help you find a topic.
Your topic can be on something you’d like to learn more about, or about an issue that is relevant today. It helps to choose a topic that is broad enough to allow research on several aspects of an issue, but not too broad that you find yourself going off on tangents. The topic should be interesting to you and perhaps meaningful in some way to today’s society. In addition, you should be able to support your ideas with research from appropriate sources.
A good way to look for topics is to read lots of stuff in the general subject areas that interest you. The RLB Library has tools for you to find reading material online. These tools include:
1. Research Starters
Go to the Library’s homepage library.ubalt.edu and type in some keywords in the gray box under the “library search” tab. For example, the keyword “inflation” will result in a “Research Starter” display at the top of the search results. Research Starters are a good way to get an overview of a topic. Clicking on “more” will take you to a detailed article on the topic.
2. Credo Reference
This database is another great place to read background information on many topics. You can access Credo Reference by going to the library homepage and clicking on “Databases” beneath the search box. When you get to the list of A-Z Databases, click on the letter C and scroll down for “Credo Reference.”
In Credo Reference, you can browse by subjects. On the right side there are useful “Research Quick Tips.” You can also use “mind maps” to explore related concepts.
3. Academic OneFile (Gale)
This database includes a Topic Finder. When you input a search term, a diagram appears with “tiles” that you can click on to narrow your search and pull up relevant articles. You can access Academic OneFile through the A-Z Databases list under “A.”
4. Opposing Viewpoints (Gale in Context)
If you are interested in contemporary issues, the database Opposing Viewpoints is a good starting point to read about current social issues, with articles exploring contrasting viewpoints. This database can also be accessed from the A-Z Databases list under “O.”
In summary, finding a topic for your research paper or project can be made easier by reading background material. The four resources mentioned above can help you find those background articles that point you to an interesting and compelling topic. But don’t procrastinate! You need to set aside time to read. Ask a Librarian if you want more information on the research process or on how to pick a good topic.
**For a really good tutorial demonstrating how to find a topic, check out this video from NC State University Libraries.**
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Asset Demand and Real Interest Rates
Understanding factors that drive asset demand is central to explaining movements in long-term real interest rates. In this paper, we begin by documenting that much of the increase in the demand for assets in the US in the 30 years prior to Covid represented greater desire to hold assets by households of given age and income levels. For example, if we focus on the 55-64 age group, its wealth-to-income ratio increased by 45-55%, depending on whether housing is included or not. We then develop a model of asset demands which combines retirement motives and inter-temporal substitution motives to quantitatively explore different factors that may have contributed to such an increase. Our findings suggest that decreasing interest rates likely led to a substantial increase in demand for retirement wealth. We also explore some of the across group heterogeneity and show how social security may explain why the lowest income groups did not follow the general trend. Finally, we discuss macroeconomic implications of long-run asset demands that are a decreasing function of interest rates.
This paper benefited from comments and discussions on a previous paper titled “Gazing at r*: A Hysteresis Perspective”. We thank Sushant Acharya, Tom Carter, Martin Eichenbaum, Jordi Galí, Mark Gertler, Narayana Kocherlakota, Oleksiy Kryvtsov, Guillaume Rocheteau, Ludwig Straub, John Williams and especially Steve Cecchetti, Marcus Hagedorn, Jean-Baptiste Michau, Tim Willems, and Christopher Winter for detailed comments that have lead us to reorient the analysis in the paper's earlier incarnation “Gazing at r*” away from intriguing macroeconomic implications (such as multiple steady state real interest rates) and towards a more quantitative analysis of the observed changes in within-group asset holdings in this paper. We also thank seminar and conference participants at the Bank of Canada, 2022 NBER Summer Institute, 2022 Paris School of Economics Macro Days, 2022 Vienna Macroeconomics Workshop, Swiss National Bank 2022 Annual Research Conference, CEF 2022, the University of California, at Irvine, International Finance Corporation, University College London, Oxford University and the University of Victoria for comments. This paper has benefited from financial support through the Bank of Canada. The views expressed herein are those of the authors and do not necessarily represent the views of the Bank of Canada, International Finance Corporation (IFC), IFC management, the World Bank Group, or the National Bureau of Economic Research.
MARC RIS BibTeΧ
Download Citation Data
More from NBER
In addition to working papers , the NBER disseminates affiliates’ latest findings through a range of free periodicals — the NBER Reporter , the NBER Digest , the Bulletin on Retirement and Disability , the Bulletin on Health , and the Bulletin on Entrepreneurship — as well as online conference reports , video lectures , and interviews .

You are viewing this page in an unauthorized frame window.
This is a potential security issue, you are being redirected to https://nvd.nist.gov
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Information Technology Laboratory
National vulnerability database.
- Vulnerabilities
NIST is currently working to establish a consortium to address challenges in the NVD program and develop improved tools and methods. You will temporarily see delays in analysis efforts during this transition. We apologize for the inconvenience and ask for your patience as we work to improve the NVD program.
Weakness Enumeration
Change history, cve modified by cert/cc 3/16/2024 12:15:07 pm, new cve received by nist 3/15/2024 2:15:08 pm.
Read our research on: TikTok | Podcasts | Election 2024
Regions & Countries
5 facts about religion and americans’ views of donald trump.

For most of the last decade, observers have been trying to understand why so many highly religious Americans have a favorable view of Donald Trump, asking how values voters can support a candidate who has been divorced twice, married three times and found liable for sexual abuse . Is Trump viewed most positively by those who might be described as “Christians in name only” – people who identify as Christians but aren’t actually religious?
The latest Pew Research Center survey sheds light on these and related questions. Here are five facts about religion and views of Trump, based on our survey of 12,693 U.S. adults conducted Feb. 13-25.
Pew Research Center conducted this analysis to explore the connection between religion and views of Donald Trump.
For this analysis, we surveyed 12,693 respondents from Feb. 13 to 25, 2024. Most of the respondents (10,642) are members of the Center’s American Trends Panel, an online survey panel recruited through national random sampling of residential addresses, which gives nearly all U.S. adults a chance of selection.
The remaining respondents (2,051) are members of three other panels, the Ipsos KnowledgePanel, the NORC AmeriSpeak panel and the SSRS opinion panel. All three are national survey panels recruited through random sampling (not “opt-in” polls). We used these additional panels to ensure that the survey would have enough Jewish and Muslim respondents to be able to report on their views.
The survey is weighted to be representative of the U.S. adult population by gender, race, ethnicity, partisan affiliation, education, religious affiliation and other categories.
For more, refer to the ATP’s methodology and the methodology for this survey .
Among religious groups, White evangelical Protestants continue to have the most positive opinion of Trump. Overall, two-thirds of White evangelical Protestants say they have a favorable view of the former president, including 30% who have a very favorable opinion of him.
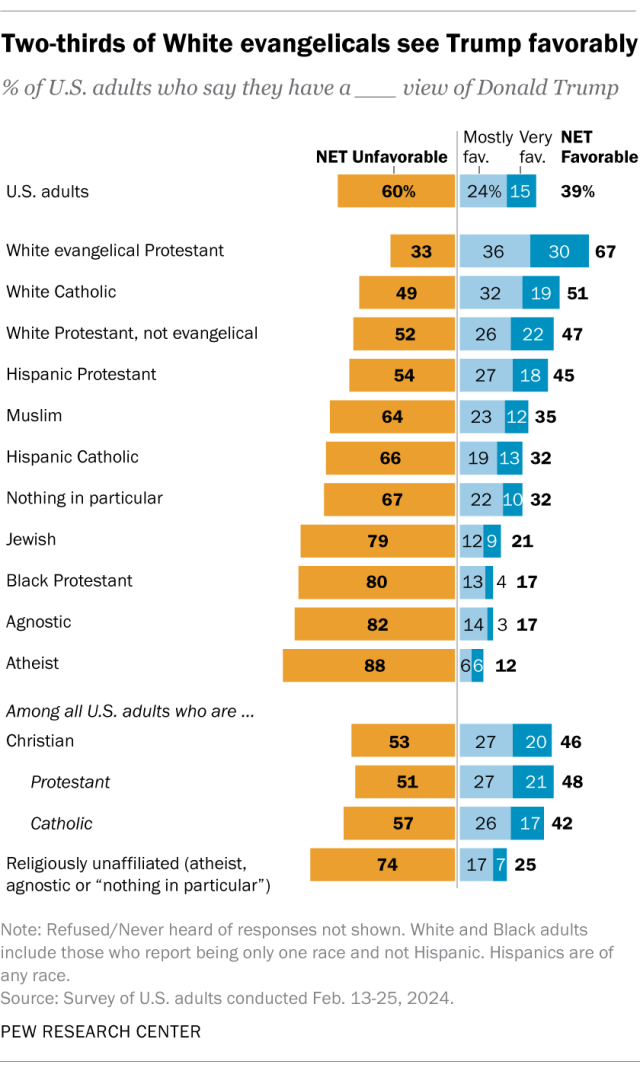
Roughly half of White Catholics (51%) express positive views of Trump, as do 47% of White nonevangelical Protestants and 45% of Hispanic Protestants.
But in every other U.S. religious group large enough to be analyzed in this survey, large majorities have unfavorable opinions of Trump, including:
- 88% of atheists
- 82% of agnostics
- 80% of Black Protestants
- 79% of Jewish Americans
These religious patterns largely reflect partisan differences . Most White evangelicals tend to vote for Republicans, as do smaller majorities of White Catholics and White nonevangelical Protestants. By contrast, most atheists, agnostics, Black Protestants and Jews tend to vote for Democrats.
Trump’s favorability rating is similar among Christians who attend church regularly and those who don’t. Some observers have pointed out that Trump’s political base consists largely of people who call themselves Christians but don’t go to church. However, our survey shows that Christians who regularly go to church express equally favorable views of Trump as those who don’t often attend religious services.
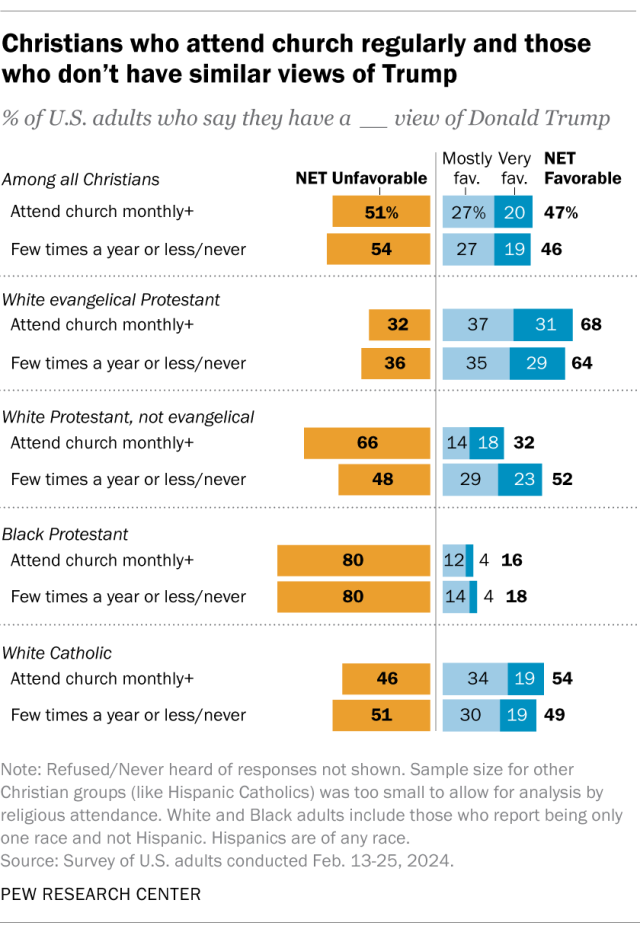
Among Christians as a whole, 47% of those who attend church at least monthly say they have a favorable view of the former president. That’s on par with the 46% of non-church-attending Christians who say the same.
Among White evangelical Protestants, 68% of regular churchgoers have a positive view of Trump – similar to the 64% among White evangelicals who don’t attend church regularly.
The only exception to this pattern is among White Protestants who do not identify as born-again or evangelical. In this group, Trump is viewed more favorably by those who don’t attend church regularly than by those who do (52% vs. 32%).
Many of the people who view Trump favorably don’t go to religious services regularly – but very few are nonreligious. Overall, 64% of respondents who have a favorable view of Trump say they attend religious services a few times a year or less often, while 35% say they go to services at least once or twice a month. (Among all respondents, 69% say they attend religious services a few times a year or less, while 30% go at least monthly.)
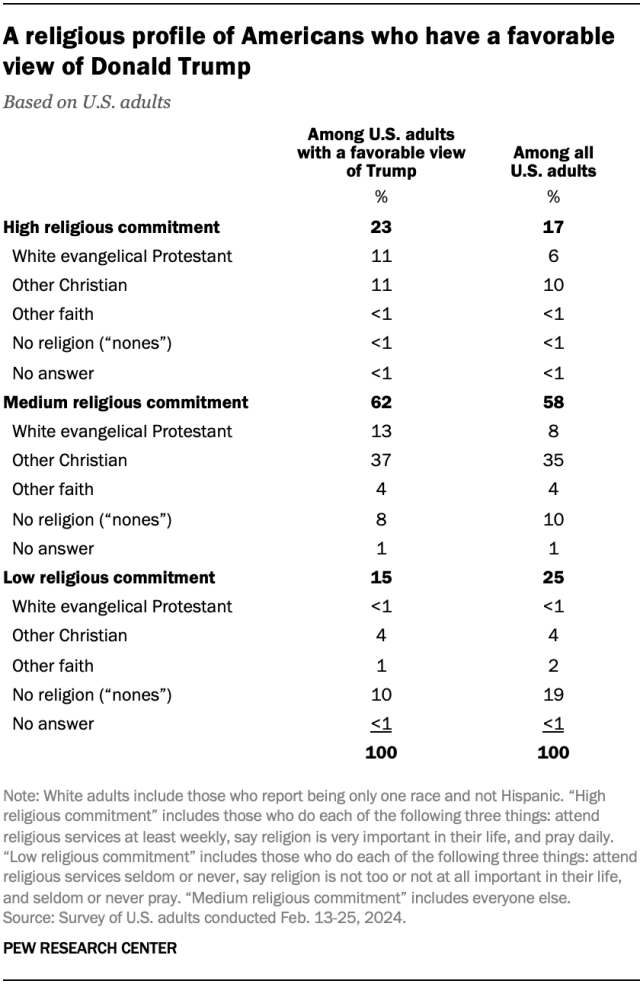
Religious attendance is just one way of looking at religious commitment. Another common way we measure it is to combine survey questions about attendance at religious services, how often people pray and how important religion is to them.
U.S. adults who attend religious services at least weekly, pray daily and say religion is very important in their lives are categorized as highly religious. Those who seldom or never attend services, seldom or never pray and say religion is not too important or not at all important in their lives are counted as having low religious commitment. Everyone else is counted as having medium religious commitment.
Looked at this way, 23% of U.S. adults with a favorable view of Trump are highly religious, including 11% who are highly religious White evangelical Protestants.
Another 62% of Americans with a favorable view of Trump have medium levels of religious commitment, including 13% who are White evangelicals.
Just 15% of people with a favorable view of Trump have low levels of religious commitment. By far the biggest subgroup within this category is religious “nones” – people who describe their religious identity as atheist, agnostic or “nothing in particular.” Overall, 18% of people with a positive view of Trump are religious “nones,” including 10% who are “nones” with low levels of religiousness.
Very few of the people who have a positive view of Trump are White evangelical Protestants with a low level of religiousness. Indeed, self-described White evangelical Protestants who are not religiously observant account for less than 1% of the overall U.S. population. Even if a candidate wanted to form a coalition rooted in support from nonreligious evangelicals, there just aren’t enough of them to be a national political base.
Most people who view Trump positively don’t think he is especially religious himself. But many think he stands up for people with religious beliefs like theirs. Just 8% of people who have a positive view of Trump think he is very religious, while 51% think he is somewhat religious and 38% say he is not too or not at all religious .
But 51% of those with a favorable view of Trump think he stands up for people with religious beliefs like their own, including 24% who think he does this a great deal and 27% who say he does this quite a bit.
Among White evangelical Protestants with a favorable view of Trump, just 9% view him as very religious. But roughly two-thirds think he does a great deal (32%) or quite a bit (35%) to stand up for people with religious beliefs like theirs.
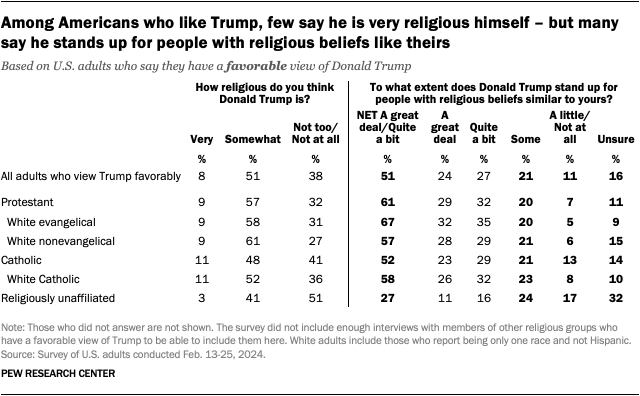
Religious “nones” who are culturally Christian view Trump a bit more positively than religious “nones” who aren’t.
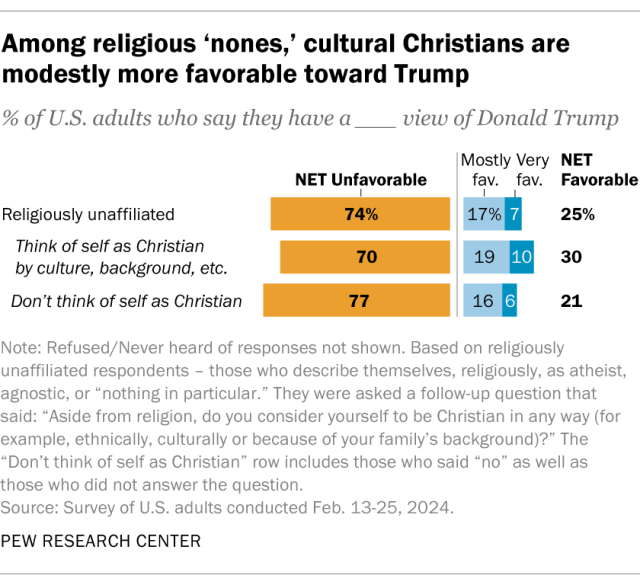
One way to measure for differences between “cultural” and “practicing” Christians is to compare Christians who do and don’t do go to church regularly, as we did above. Another is to look at religiously unaffiliated respondents, or “nones” – people who describe themselves, religiously, as atheist, agnostic, or “nothing in particular.” In our new survey, we asked these Americans whether they think of themselves as Christians “aside from religion … for example ethnically, culturally or because of your family’s background.”
Religious “nones” who identify as culturally Christian have a modestly more favorable opinion of Trump than “nones” who do not identify as Christian in any way. Still, large majorities in both groups express negative views of the former president.

Sign up for our weekly newsletter
Fresh data delivered Saturday mornings
Two-thirds of Republicans want Trump to retain major political role; 44% want him to run again in 2024
A partisan chasm in views of trump’s legacy, how america changed during donald trump’s presidency, trump’s approval ratings so far are unusually stable – and deeply partisan, most americans don’t see trump as religious; fewer than half say they think he’s christian, most popular.
About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .

COMMENTS
Mariya Valerevna Stupina. Feb 2024. Zilani Kaluba. Mayumbo Nyirenda. Explore the latest full-text research PDFs, articles, conference papers, preprints and more on DATABASE MANAGEMENT SYSTEMS ...
This is where database topics for research paper [7] come in. By using database technology in video surveillance systems, it is possible to store and manage large amounts of video data efficiently. Database management systems (DBMS) can be used to organize video data in a way that is easily searchable and retrievable. This is particularly ...
Several database management system performance comparisons have been conducted and published as both vendor white-papers as well as in scientific fora. The approaches and reporting in such studies have been criticized in previous literature. In this study, we systematically surveyed 117 DBMS performance comparison studies.
This SMS study aimed to identify the most up-to-date research in database security and the different challenges faced by users/clients using various databases from a software engineering perspective. In total, 20 challenges were identified related to database security. ... 13 papers in our SMS addressed the topic of "internal" attacks ...
Faculty and students at Berkeley have repeatedly defined and redefined the broad field of data management, combining deep intellectual impact with the birth of multi-billion dollar industries, including relational databases, RAID storage, scalable Internet search, and big data analytics. Berkeley also gave birth to many of the most widely-used ...
Also, other database topics such as transaction management, application programming etc. are also the main highlights of the topics discussed in the literature. ... The study was carried out by systematically selecting research papers published between 1995 and 2021. Based on the study, a high level categorization presents a taxonomy of the ...
If you were excited by the topics in 4111, this graduate level course in database systems research will be a deep dive into classic and modern database systems research. Topics will range from classic database system design, modern optimizations in single-machine and multi-machine settings, data cleaning and quality, and application-oriented ...
Atom. RSS Feed. A database is one or more sets of data, for example numbers, characters and images, bundled together with software that enables data to be added, removed or retrieved. Databases ...
Find here ideas on DBMS security and design other database topics for research papers. Free essays. Search for: Close and clear the search form. Search. Topic Ideas. Topic Ideas. Business . Commerce Innovation Marketing Negotiation Product Marketing. Education .
One way to maintain the security of the database is to use encryption techniques. The method used to secure the database is encryption using the ROTI3 and Caesar Cipher methods. Both of these methods have advantages in processing speed. For thisreason, the author will compare the use of the two algorithms above in terms of the encryption and ...
Technology made it easier for people to accomplish daily tasks and activities. In the conventional method, customers avail themselves of services by visiting the shop that offers their desired services personally. 40 List of DBMS Project Topics and Ideas. Fish Catch System Database Design.
The contents of these databases are only partially included in HOLLIS. To make sure you're really seeing everything, you need to search in multiple places. Use Database Search to identify and connect to the best databases for your topic. In addition to digital content, you will find specialized search engines used in specific scholarly domains.
Get 30 days free. 1. Scopus. Scopus is one of the two big commercial, bibliographic databases that cover scholarly literature from almost any discipline. Besides searching for research articles, Scopus also provides academic journal rankings, author profiles, and an h-index calculator. Coverage: 90.6 million core records. References: N/A.
113 Great Research Paper Topics. One of the hardest parts of writing a research paper can be just finding a good topic to write about. Fortunately we've done the hard work for you and have compiled a list of 113 interesting research paper topics. They've been organized into ten categories and cover a wide range of subjects so you can easily ...
These 15 topics will help you to dive into interesting research. You may even build on research done by other scholars. Evaluate the data mining process. The influence of the various dimension reduction methods and techniques. The best data classification methods. The simple linear regression modeling methods.
MIT Libraries: Data Management Plan Evaluation. After the completion of a project or research, it is recommended to keep data for three more years while ensuring safety and accessibility. Big Data Management: Looker, IBM, Oracle and SAS. Looker is one of the companies that provide superior systems for guiding companies to benefit from the ...
Keep reading for our list of 500 vetted research paper topics and our magic formulas for creating your own topic! Of course, if you want help learning to write research papers tailored to your individual needs, check out our one-on-one writing coaching or academic writing workshop.
Research databases. You can search for scholarly sources online using databases and search engines like Google Scholar. These provide a range of search functions that can help you to find the most relevant sources. If you are searching for a specific article or book, include the title or the author's name. Alternatively, if you're just ...
Such related data are called a database. A database system is an integrated collection of related files, along with details of the interpretation of the data contained therein. Basically, the ...
This database can also be accessed from the A-Z Databases list under "O." In summary, finding a topic for your research paper or project can be made easier by reading background material. The four resources mentioned above can help you find those background articles that point you to an interesting and compelling topic. But don't ...
We use detailed location information from the Longitudinal Employer-Household Dynamics (LEHD) database to develop new evidence on the effects of spatial mismatch on the relative earnings of Black workers in large US cities. We classify workplaces by the size of the pay premiums they offer in a two ...
This paper shows the importance of technological synergies among heterogeneous firms for aggregate fluctuations. First, we document six novel empirical facts using microdata that suggest the existence of important technological synergies between trading firms, the presence of positive assortative matching among firms, and their evolution during the business cycle.
From magazine articles to peer-reviewed papers and case laws, Google Scholar can provide cutting-edge research for free. It's one of Google's lesser-known search tools—but it's invaluable if you ...
Understanding factors that drive asset demand is central to explaining movements in long-term real interest rates. In this paper, we begin by documenting that much of the increase in the demand for assets in the US in the 30 years prior to Covid represented greater desire to hold assets by households of given age and income levels.
Publications and Databases. APA Publishing products and resources that support research, education, practice and general wellbeing. ... We especially seek papers that address the following topics, though other areas of focus are welcome: ... Research papers we seek to include encompass case studies, qualitative studies, and empirical studies (e ...
References to Advisories, Solutions, and Tools. By selecting these links, you will be leaving NIST webspace. We have provided these links to other web sites because they may have information that would be of interest to you.
Aim: To offer an overall picture of the research published regarding the different aspects of death and dying during the COVID-19 pandemic in journals covering the field of nursing in the Scopus database. Design: bibliometric analysis. Methods: The metadata obtained were exported from Scopus for subsequent analysis through Bibliometrix. Using the VOSviewer co-word analysis function, the ...
In the realm of Database Management Systems (DBMS), course curriculum covers several topics that range from data modeling to data implementation and examination.
Among religious groups, White evangelical Protestants continue to have the most positive opinion of Trump. Overall, two-thirds of White evangelical Protestants say they have a favorable view of the former president, including 30% who have a very favorable opinion of him.. Roughly half of White Catholics (51%) express positive views of Trump, as do 47% of White nonevangelical Protestants and 45 ...
Law and Human Behavior is a multidisciplinary forum for manuscripts examining the interface between human behavior and the law, the legal system, and the legal process. Although pure legal analysis falls outside the scope of the journal, Law and Human Behavior publishes compelling conceptual (methodological and theoretical) and empirical papers, and strongly encourages authors to situate their ...