- Trending Categories

- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary

Characteristics of an Ideal Filter (LPF, HPF, BPF and BRF)
What is a filter.
A filter is a frequency selective network, i.e., it allows the transmission of signals of certain frequencies with no attenuation or with very little attenuation and it rejects all other frequency components.
What is an Ideal Filter?
An ideal filter is a frequency selective network that has very sharp cut-off characteristics, i.e., it transmits the signals of certain specified band of frequencies exactly and totally rejects the signals of frequencies outside this band. Therefore, the phase spectrum of an ideal filter is linear.
Ideal Filter Characteristics
Based on the frequency response characteristics, the ideal filters can be of following types −
Ideal Low-Pass Filter (LPF)
Ideal High-Pass Filter (HPF)
Ideal Band-Pass Filter (BPF)
Ideal Band-Reject Filter (BRF)
Ideal All Pass Filter
Ideal low pass filter (lpf).
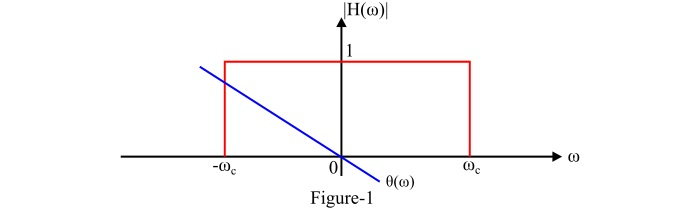
An ideal low pass filter is the one which transmits all the signal of frequencies less than a certain frequency $\mathit{\omega_{c}}$ radians per second without any distortion and blocks all the signals of frequencies above $\mathit{\omega_{c}}$ radians per second. Where, the frequency $\mathit{\omega_{c}}$ radians per second is called the cut-off frequency . The phase function of an ideal low-pass filter is given by $[\mathit{\theta \left(\omega\right)=-\omega t_{d}}]$.
The transfer function of an ideal low-pass filter is given by,
$$\mathrm{\mathit{\left | H\left(\omega\right) \right |=\left\{\begin{matrix} \mathrm{1}\:\:\mathrm{for}\:\left | \omega\ \right|<\omega_{c} \ \mathrm{2} \:\:\mathrm{for}\:\left | \omega\ \right|>\omega_{c} \end{matrix}\right.}}$$
Therefore, the frequency response characteristics of an ideal low-pass filter is a gate or rectangular function and it is shown in Figure-1.
Ideal High Pass Filter (HPF)
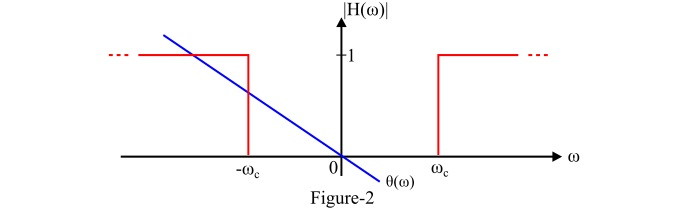
An ideal high pass filter transmits all the signals of frequencies above a certain frequency $\mathit{\omega_{c}}$ radians per second without any distortion and blocks completely all the signals of frequencies below the frequency $\mathit{\omega_{c}}$ radians per second. Here, the frequency $\mathit{\omega_{c}}$ radians per second is called the cut-off frequency . The phase function of an ideal high pass filter is given by,
$$\mathrm{\theta (\omega )=-\omega t_{d}}$$
The transfer function of an ideal high pass filter is given by,
$$\mathrm{\mathit{\left | H\left(\omega\right) \right |=\left\{\begin{matrix} \mathrm{0}\:\:\mathrm{for}\:\left | \omega\ \right|<\omega_{c} \ \mathrm{1} \:\:\mathrm{for}\:\left | \omega\ \right|>\omega_{c} \end{matrix}\right.}}$$
Figure-2 shows the frequency response characteristics of an ideal high pass filter.
Ideal Band Pass Filter (BPF)
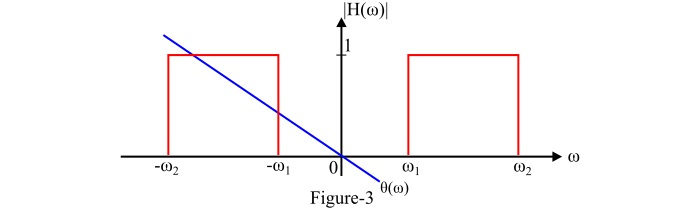
An ideal band pass filter transmits all the signals of frequencies within a certain frequency band $\mathit{\left(\omega _{\mathrm{2}}-\omega_{\mathrm{1}}\right)}$ radians per second without any distortion and completely blocks all the signals of frequencies outside this frequency band.
The frequency band $\mathit{\left(\omega _{\mathrm{2}}-\omega_{\mathrm{1}}\right)}$ is called the bandwidth of the band-pass filter.
The phase function of an ideal band-pass filter for the distortion less transmission is given by,
$$\mathrm{\mathit{\theta\left(\omega\right)=-\omega t_{d}}}$$
And the transfer function of an ideal band-pass filter is given by,
$$\mathrm{\mathit{\left | H\left(\omega\right) \right |=\left\{\begin{matrix} \mathrm{1}\:\:\mathrm{for}\:\left | \omega_{\mathrm{1}}\ \right|<\omega< \left | \omega_{2}\ \right| \\mathrm{0} \:\:\mathrm{for}\:\omega<\left | \omega_{\mathrm{1}}\ \right|\&\:\omega>\left | \omega_{\mathrm{2}}\ \right| \end{matrix}\right.}}$$
The figure-3 shows the frequency response characteristics of an ideal band-pass filter (BPF).
Ideal Band Rejection Filter (BRF)
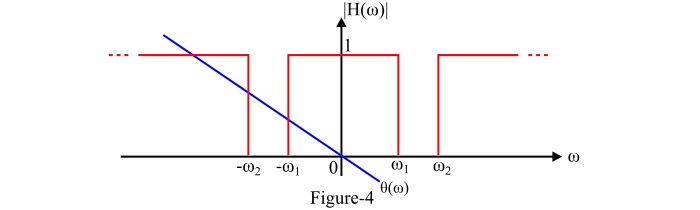
An ideal band rejection filter rejects completely all the signals of frequencies within a frequency band $\mathit{\left(\omega _{\mathrm{2}}-\omega_{\mathrm{1}}\right)}$ radians per second and transmits all the signals of frequencies outside the frequency band without any distortion.
In this case, the frequency band $\mathit{\left(\omega _{\mathrm{2}}-\omega_{\mathrm{1}}\right)}$ is called the rejection band. The Band rejection filter is also called the band stop filter (BSF) or band-elimination filter (BEF). The phase function of an ideal band rejection filter is $\mathit{\theta\left(\omega\right)=-\omega t_{d}}$.
And the transfer function of an ideal band rejection filter is given by,
$$\mathrm{\mathit{\left | H\left(\omega\right) \right |=\left\{\begin{matrix} \mathrm{0}\:\:\mathrm{for}\:\left | \omega_{\mathrm{1}}\ \right|<\omega< \left | \omega_{\mathrm{2}}\ \right| \\mathrm{1} \:\:\mathrm{for}\:\omega<\left | \omega_{\mathrm{1}}\ \right|\&\:\omega>\left | \omega_{\mathrm{2}}\ \right| \end{matrix}\right.}}$$
The figure-4 shows the frequency response characteristics of an ideal band rejection filter.
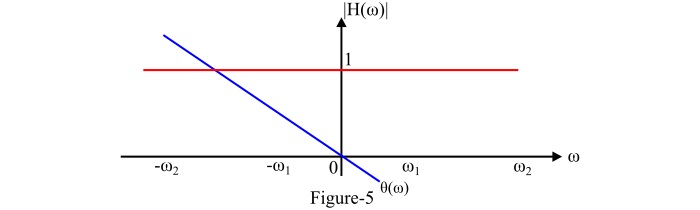
An all pass filter is a frequency selective network which transmits signals of all the frequencies without any distortion. That is, the bandwidth of an all pass filter is infinite as shown in figure-5. The transfer function of an ideal all pass filter is given by,
$$\mathrm{\mathit{\left| H\left(\omega\right)\right |=\left\{\mathrm{1}\:\:\mathrm{for} \:\mathrm{all}\:\omega\right.}}$$
And the phase function of an ideal all pass filter for the distortion less transmission is $\mathit{\theta\left(\omega\right)=-\omega t_{d}}$.
Note - All ideal filters are non-causal systems. Therefore, none of them can be physically realizable.

Related Articles
- State any two characteristics of an ideal fuel?
- What is Ideal Reconstruction Filter?
- Signals and Systems – Filter Characteristics of Linear Systems
- Write any four characteristics of an ideal fuel. What is C.N.G.? Mention its one use.
- Characteristic of an Ideal Digital Electronics Element
- What is an Ideal Transformer?
- What is the full form of BPF?
- (a) What are fuels? Name any two common fuels.(b) State any four characteristics of an ideal fuel(or good fuel).
- What are the qualities of an ideal source of energy?
- Difference between Ideal Transformer and Practical Transformer
- Difference between Ideal Gas and Real Gas
- Characteristics and classification of Gymnosperms
- Why is biogas considered an ideal fuel for domestic use?
- What is an organism and what are its characteristics?
- Characteristics of Network and Electric Circuit
Kickstart Your Career
Get certified by completing the course

Band Reject Filter Circuit:
In this Band Reject Filter Circuit, frequencies are attenuated in the stop band and passed outside it, as shown in Fig. 15.20(b). As with band pass filters, band reject filters can also be classified as (i) wide and (ii) narrow band.
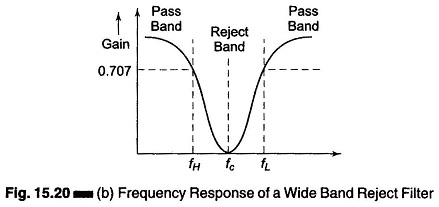
The narrow band reject filter circuit is also called the notch filter . Because of its higher Q which is greater than 10, the bandwidth of the narrow band reject filter is much smaller than that of the wide band reject filter. The band reject filter is also called a band stop or band elimination filter because it eliminates a certain band of frequencies.
Wide Band Reject Filter:
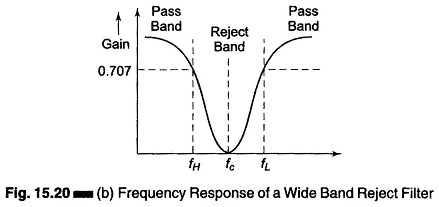
Figure 15.20 (a) shows wide band reject filter circuit using a low pass filter, a high pass filter and a summing amplifier. For a proper band reject response, the low cutoff frequency f L of the high pass filter must be larger than the high cutoff frequency f H of the low pass filter. Also, the pass band gain of both high pass and low pass sections must be equal.
Narrow Band Reject Filter:
The narrow band reject filter, often called the notch filter, is commonly used for the attenuation of a single frequency. For example, it may be necessary to attenuate 60 Hz or 400 Hz noise or hum signals in a circuit. The most commonly used notch filter is the Twin T network, shown in Fig. 15.21(a), which is a passive filter composed of two T shaped networks.
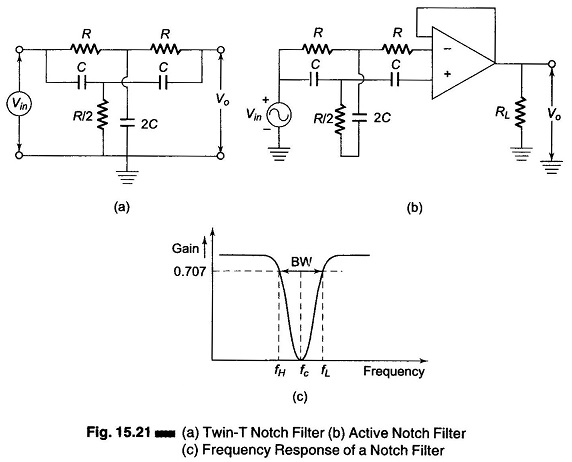
One T network is made up of two resistors and a capacitor , while the other is made of two capacitors and a resistor. The frequency at which maximum attenuation occurs is called the notch-out frequency, given by

Related Posts:
Data transmission, automatic bridge circuit, low pass filter circuits, dual slope integrating type dvm, chopper type dc amplifier voltmeter (microvoltmeter), single channel data acquisition system, fully automatic digital instrument, thermocouple principle and types of thermocouple, classification of printers, strip chart recorder application.

What is a Band Pass Filter? Circuit Diagram, Types, and Applications
In signal processing , filters are one kind of devices used for allowing required frequency components as well as removes unwanted frequency components. Filtering can be defined as; the interfacing signal background noise can be diminished by removing some frequencies. The circuit of the filter can be used for uniting the LPF and HPF properties into an only filter which is termed as a band pass filter. There are different kinds of filters available such as analog/digital, active/passive, linear/nonlinear, time-variant/time invariant. This article discusses an overview of the band pass filter with applications
What is Band Pass Filter?
The definition of the band pass filter is a circuit which permits the signals to flow among two particular frequencies, although divides these signals at other frequencies. These filters are available in different types; some of the BPF- band pass filter design can be done with an external power as well as active components such as integrated circuits, transistors , which are named as an active band pass filter . Similarly, some of the filters use any kind of power source as well as passive components like capacitors and inductors , which are named as a passive band pass filter.
These filters are applicable in wireless transmitters as well as receivers. In a transmitter, a BPF can be used to limit the output signal’s bandwidth toward the minimum necessary level & transmitting data at the preferred speed & form. Similarly, in a receiver, this filter lets the signals in a favored frequency range to be decoded, whereas keeping away from signals at unnecessary frequencies. The signal to noise (S/N) ratio of a receiver can be optimized by a BPF.
Band Pass Filter Circuit
The best example of a band pass filter circuit is the RLC circuit that is shown below. This filter can also be designed by uniting an LPF and HPF. In BPF, Bandpass illustrates a kind of filter otherwise procedure of filtering. It is to be differentiated from passband that refers to the real section of the influenced spectrum. An idyllic bandpass filter doesn’t have gain and attenuation, so it is totally level passband. That will totally attenuate every one of frequencies exterior the passband.

Practically, the bandpass filter is not ideal and doesn’t attenuate every one of frequencies outside the preferred frequency choice totally. Particularly, there is a section just outside the proposed pass band wherever frequencies are attenuated, however not discarded which is called like the filter roll-off, & usually, it is specified in dB of attenuation for every octave otherwise decade of frequency. In general, the filter design looks to build the roll-off as thin as feasible, therefore letting the filter to do the proposed design. Frequently, this can be attained at the expenditure of passband ripple otherwise stopband ripple.
The filter bandwidth can be defined as the dissimilarity among the upper frequency as well as lower frequency. The form factor is the fraction of bandwidths calculated with two dissimilar attenuation values for determining the cut-off frequency, For example., a form factor of 2:1 at 20/2 dB means the bandwidth calculated among frequencies at 20 dB attenuation is double that calculated among frequencies at 2 dB attenuation. Optical BPFs are commonly used in photography as well as lighting work in theatre. These kinds of filters take the outline of a clear colored film otherwise sheet.
Different Types of Band Pass Filters
The categorization of the bandpass filter can be done in two types such as wide bandpass filter as well as narrow band pass filter .
Wide Band Pass Filter
A WBF or wide bandpass filter (WBF) can be formed by dropping low pass as well as high pass segments which is normally a different circuit intended for simple design & act.

It is recognized with a number of practical circuits. A bandpass filter with ± 20 dB/ decade can be formed by using the two sections like a 1st order low pass as well as high pass sections can be dropped. Similarly, a bandpass filter with ± 40 dB/ decade can be formed by connecting two second-order filters in series namely low pass and high- pass filter (HPF). This means the order of the bandpass filter (BPF) is ruled with the order of the low pass & high pass filters . The bandpass filter graph is shown below.

A bandpass filter with ± 20 dB/decade can be is composed of a 1st order HPF (high pass filter) . A 1st order LPF (low-pass filter) is shown in the following figure by its frequency response.
Narrow Band Pass Filter
Generally, a narrow bandpass filter uses several feedbacks. This bandpass filter using an op-amp as shown in the following circuit diagram. The main features of this filter mainly include the following.

Another name of this filter is a multiple feedback filter because it includes two feedback lanes
An op-amp is utilized in the inverting mode
The frequency response of this filter is shown in the following figure.

Usually, the designing of this filter can be done for exact values of center frequency (fc) & bandwidth or center frequency & BW. The components of this circuit can be determined by the following relationships. Each of the C1 and C2 capacitors can be taken to C for the simplifications of design calculation.
R1 = Q/2∏ fc CAf R2 =Q/2∏ fc C(2Q2-Af) R3 = Q /∏ fc C
From the above equations, at middle frequency Af denotes the gain, so Af = R3 / 2R1
But, the Af should satisfy this statement Af<2Q2
The multiple feedback filters’ fc (center frequency) can be altered toward a novel frequency fc with no changing the bandwidth or gain. This can be attained just by altering R2 to R2’ so that
R2’ = R2 * ( fc / fc )2
Band Pass Filter Calculator
The following circuit is the passive bandpass filter circuit. By using this circuit we can calculate the passive bandpass filter. The formula for passive bandpass filter calculator is shown below.

For low cut off frequency = 1/2∏R2C2
For high cut off frequency = 1/2∏R1C1
Similarly, we can calculate for active inverting op-amp BPF, and active non-inverting op-amp BPF.
Band Pass Filter Applications
The applications of bandpass filters include the following.
- These filters are extensively applicable to wireless transmitters & receivers .
- This filter can be used to optimize the S/N ratio (signal-to-noise) as well as the compassion of a receiver.
- The main purpose of the filter in the transmitter is to limit the BW of the output signal to the selected band for the communication.
- BPFs are also widely used in optics such as LIDARS , lasers, etc.
- The best application of this filter is audio signal processing, wherever a specific range of sound frequencies is necessary though removing the rest.
- These filters are applicable in sonar, instruments, medical, and Seismology applications
- These filters involve communication systems for choosing a particular signal from a variety of signals.
Therefore, this is all about band-pass filter theory which includes, circuit diagram with working, types of bandpass filters and its applications. From the above information, finally we can conclude that the other fields of applications of these filters include in astronomy, these filters permit only an only section of the range of light into a device. These filters can assist in finding wherever stars recline on the major series, recognizing redshifts, etc. Here is a question for you, what is an active bandpass filter?
Share This Post:

- Electronics
- Communication
- Free Circuits
- Interview Questions
- ECE Projects
- EEE Projects
- Project Ideas
- Resistor Color Code Calculator
- Ohms Law Calculator
- Circuit Design
- Infographics

RF filter types | LPF, HPF, BPF, BSF, active, passive, analog, digital
This page describes gain vs frequency response of RF filter types . There are four types of RF filters viz. lowpass filter (LPF),Highpass filter (HPF),Bandpass filter (BPF) and Bandstop filter (BSF). Filters are categorized into active filter and passive filter. They are also categorized into analog filters and digital filters.
RF Filter definition : The electronic circuit which changes amplitude and phase angle of electrical signal based on frequency is known as frequency filter. The filter which operates on radio frequency is known as RF filter.
Passive Filter Vs Active filter
Based on type of components used in the design of filter there are two types viz. passive filter and active filter. Passive Filter : It uses passive components such as coils or inductors (L), capacitors (C) and resistors (R) in the construction of filter. Hence it is known as passive filter. Active Filter : It uses active components such as operational amplifier in addition to R and C in the construction of the filter. Hence it is known as active filter.
Analog filter Vs Digital filter
Analog Filter : The analog filters are made of discrete components. Digital Filter : The digital filters are usually developed in programming languages which are ported on ASIC, FPGA or DSP or other processors. They perform operation as per algorithm written.

LPF | Low Pass Filter
A LPF permits all the lower frequencies of a signal upto desired cutoff frequency to pass through with little or no attenuation. All the frequencies above the cutoff frequency are attenuated.
HPF | High Pass Filter
A HPF permits all the higher frequencies of a signal from defined cutoff frequency with little or no attenuation. All the frequencies below the cutoff frequency are attenuated.
BPF | Band Pass Filter
A BPF permits signals within specific frequency bands to pass through. All the signal frequencies below and above the passband are attenuated or blocked.
BSF | Band Stop Filter
The BSF suppress specific frequency range and permits all other frequencies which are in lower and higher range.
Refer LPF vs HPF vs BPF vs BSF>> and All Pass Filter basics and types>> for more information.
RF Filter Related Links
RF Filter calculator Microstrip based RF Filter design RF filter manufacturers RF filter applications RF filter selection guide RF filter terminologies
RF RELATED LINKS
stripline basics and types Microstrip line variants Slotline basics and types Finline basics CPW(Coplanar Waveguide) basics Types and basics of coaxial line Types and basics of transmission line RF Terms -Useful for RF design and testing. RF -This page describes what is RF
RF and Wireless Terminologies
Dive into BPF: a list of reading material
Sep 1, 2016 • Quentin Monnet
What is BPF?
Dive into the bytecode, about other components related or based on ebpf, about flow dissectors, about p4 and bpf, from the kernel, from package iproute2, from bcc set of tools, other examples, manual pages, bpf code in the kernel, xdp hooks code, bpf logic in bcc, code to manage bpf with tc, bpf utilities, other interesting chunks, llvm backend, running in userspace, commit logs, errors at compilation time, errors at load and run time, and still more.
~ Updated 2019-01-10 ~
BPF, as in B erkeley P acket F ilter, was initially conceived in 1992 so as to provide a way to filter packets and to avoid useless packet copies from kernel to userspace. It initially consisted in a simple bytecode that is injected from userspace into the kernel, where it is checked by a verifier—to prevent kernel crashes or security issues—and attached to a socket, then run on each received packet. It was ported to Linux a couple of years later, and used for a small number of applications (tcpdump for example). The simplicity of the language as well as the existence of an in-kernel Just-In-Time (JIT) compiling machine for BPF were factors for the excellent performances of this tool.
Then in 2013, Alexei Starovoitov completely reshaped it, started to add new functionalities and to improve the performances of BPF. This new version is designated as eBPF (for “extended BPF”), while the former becomes cBPF (“classic” BPF). New features such as maps and tail calls appeared. The JIT machines were rewritten. The new language is even closer to native machine language than cBPF was. And also, new attach points in the kernel have been created.
Thanks to those new hooks, eBPF programs can be designed for a variety of use cases, that divide into two fields of applications. One of them is the domain of kernel tracing and event monitoring. BPF programs can be attached to kprobes and they compare with other tracing methods, with many advantages (and sometimes some drawbacks).
The other application domain remains network programming. In addition to socket filter, eBPF programs can be attached to tc (Linux traffic control tool) ingress or egress interfaces and perform a variety of packet processing tasks, in an efficient way. This opens new perspectives in the domain.
And eBPF performances are further leveraged through the technologies developed for the IO Visor project: new hooks have also been added for XDP (“eXpress Data Path”), a new fast path recently added to the kernel. XDP works in conjunction with the Linux stack, and relies on BPF to perform very fast packet processing.
Even some projects such as P4, Open vSwitch, consider or started to approach BPF. Some others, such as CETH, Cilium, are entirely based on it. BPF is buzzing, so we can expect a lot of tools and projects to orbit around it soon…
As for me: some of my work (including for BEBA ) is closely related to eBPF, and several future articles on this site will focus on this topic. Logically, I wanted to somehow introduce BPF on this blog before going down to the details—I mean, a real introduction, more developed on BPF functionalities that the brief abstract provided in first section: What are BPF maps? Tail calls? What do the internals look like? And so on. But there are a lot of presentations on this topic available on the web already, and I do not wish to create “yet another BPF introduction” that would come as a duplicate of existing documents.
So instead, here is what we will do. After all, I spent some time reading and learning about BPF, and while doing so, I gathered a fair amount of material about BPF: introductions, documentation, but also tutorials or examples. There is a lot to read, but in order to read it, one has to find it first. Therefore, as an attempt to help people who wish to learn and use BPF, the present article introduces a list of resources. These are various kinds of readings, that hopefully will help you dive into the mechanics of this kernel bytecode.
Generic presentations
The documents linked below provide a generic overview of BPF, or of some closely related topics. If you are very new to BPF, you can try picking a couple of presentation among the first ones and reading the ones you like most. If you know eBPF already, you probably want to target specific topics instead, lower down in the list.
Generic presentations about eBPF:
A brief introduction to XDP and eBPF (Diego Pino García, January 2019): An excellent and accessible introduction providing context, history, and details about the functioning of eBPF.
Introduction to eBPF in Red Hat Enterprise Linux 7 (Stanislav Kozina, January 2019): Focusing on the eBPF features arriving in Red Hat.
Toward Flexible and Efficient In-Kernel Network Function Chaining with IO Visor (Fulvio Risso, HPSR 2018, Bucharest, June 2018): A generic introduction to BPF, XDP, IO Visor, bcc and other components.
A thorough introduction to eBPF (Matt Flemming, on LWN.net, December 2017): A well-written and accessible introduction providing an overview of eBPF subsystem components.
Making the Kernel’s Networking Data Path Programmable with BPF and XDP (Daniel Borkmann, OSSNA17, Los Angeles, September 2017): One of the best set of slides available to understand quickly all the basics about eBPF and XDP (mostly for network processing).
The BSD Packet Filter (Suchakra Sharma, June 2017): A very nice introduction, mostly about the tracing aspects.
BPF: tracing and more (Brendan Gregg, January 2017): Mostly about the tracing use cases.
Linux BPF Superpowers (Brendan Gregg, March 2016): With a first part on the use of flame graphs .
IO Visor (Brenden Blanco, SCaLE 14x, January 2016): Also introduces IO Visor project .
eBPF on the Mainframe (Michael Holzheu, LinuxCon, Dublin, October 2015)
New (and Exciting!) Developments in Linux Tracing (Elena Zannoni, LinuxCon, Japan, 2015)
BPF — in-kernel virtual machine (Alexei Starovoitov, February 2015): Presentation by the author of eBPF.
Extending extended BPF (Jonathan Corbet, July 2014)
BPF internals :
- Advanced programmability and recent updates with tc’s cls_bpf (netdev 1.2, Tokyo, October 2016): Daniel provides details on eBPF, its use for tunneling and encapsulation, direct packet access, and other features.
- cls_bpf/eBPF updates since netdev 1.1 (netdev 1.2, Tokyo, October 2016, part of this tc workshop )
- On getting tc classifier fully programmable with cls_bpf (netdev 1.1, Sevilla, February 2016): After introducing eBPF, this presentation provides insights on many internal BPF mechanisms (map management, tail calls, verifier). A must-read! For the most ambitious, the full paper is available here .
- Linux tc and eBPF (fosdem16, Brussels, Belgium, January 2016)
- eBPF and XDP walkthrough and recent updates (fosdem17, Brussels, Belgium, February 2017)
These presentations are probably one of the best sources of documentation to understand the design and implementation of internal mechanisms of eBPF.
The IO Visor blog has some interesting technical articles about BPF. Some of them contain a bit of marketing talks.
As of early 2019, there are more and more presentations being done around multiple aspects of BPF. One nice example is the BPF track that was held in parallel to the Linux Plumbers Conference in late 2018 (and should be held again on coming years), where lots of topics related to eBPF development or use cases were presented.
Kernel tracing : summing up all existing methods, including BPF:
Meet-cute between eBPF and Kerne Tracing (Viller Hsiao, July 2016): Kprobes, uprobes, ftrace
Linux Kernel Tracing (Viller Hsiao, July 2016): Systemtap, Kernelshark, trace-cmd, LTTng, perf-tool, ftrace, hist-trigger, perf, function tracer, tracepoint, kprobe/uprobe…
Regarding event tracing and monitoring , Brendan Gregg uses eBPF a lot and does an excellent job at documenting some of his use cases. If you are in kernel tracing, you should see his blog articles related to eBPF or to flame graphs. Most of it are accessible from this article or by browsing his blog.
Introducing BPF, but also presenting generic concepts of Linux networking :
Linux Networking Explained (Thomas Graf, LinuxCon, Toronto, August 2016)
Kernel Networking Walkthrough (Thomas Graf, LinuxCon, Seattle, August 2015)
Hardware offload :
- eBPF with tc or XDP supports hardware offload, starting with Linux kernel version 4.9 and introduced by Netronome. Here is a presentation about this feature: eBPF/XDP hardware offload to SmartNICs (Jakub Kicinski and Nic Viljoen, netdev 1.2, Tokyo, October 2016)
- An updated version was presented on year later: Comprehensive XDP offload—Handling the edge cases (Jakub Kicinski and Nic Viljoen, netdev 2.2, Seoul, November 2017)
- I presented a shorter but updated version at FOSDEM 2018: The Challenges of XDP Hardware Offload (Quentin Monnet, FOSDEM’18, Brussels, February 2018)
About cBPF :
The BSD Packet Filter: A New Architecture for User-level Packet Capture (Steven McCanne and Van Jacobson, 1992): The original paper about (classic) BPF.
The FreeBSD manual page about BPF is a useful resource to understand cBPF programs.
Daniel Borkmann realized at least two presentations on cBPF, one in 2013 on mmap, BPF and Netsniff-NG , and a very complete one in 2014 on tc and cls_bpf .
On Cloudflare’s blog, Marek Majkowski presented his use of BPF bytecode with the xt_bpf module for iptables . It is worth mentioning that eBPF is also supported by this module, starting with Linux kernel 4.10 (I do not know of any talk or article about this, though).
Libpcap filters syntax
The eXpress Data Path (Diego Pino García, January 2019): Probably one of the most accessible introduction to XDP, providing sample code to show how one can easily process packets.
XDP overview on the IO Visor website.
eXpress Data Path (XDP) (Tom Herbert, Alexei Starovoitov, March 2016): The first presentation about XDP.
BoF - What Can BPF Do For You? (Brenden Blanco, LinuxCon, Toronto, August 2016).
- ip routing drop: ~3.6 million packets per second (Mpps)
- tc (with clsact qdisc) drop using BPF: ~4.2 Mpps
- XDP drop using BPF: 20 Mpps (<10 % CPU utilization)
- XDP forward (on port on which the packet was received) with rewrite: 10 Mpps
(Tests performed with the mlx4 driver).
- XDP − eXpress Data Path, Intro and future use-cases (September 2016): “Linux Kernel’s fight against DPDK” . Future plans (as of this writing) for XDP and comparison with DPDK.
- Network Performance Workshop (netdev 1.2, Tokyo, October 2016): Additional hints about XDP internals and expected evolution.
- XDP – eXpress Data Path, Used for DDoS protection (OpenSourceDays, March 2017): Contains details and use cases about XDP, with benchmark results , and code snippets for benchmarking as well as for basic DDoS protection with eBPF/XDP (based on an IP blacklisting scheme).
- Memory vs. Networking, Provoking and fixing memory bottlenecks (LSF Memory Management Summit, March 2017): Provides a lot of details about current memory issues faced by XDP developers. Do not start with this one, but if you already know XDP and want to see how it really works on the page allocation side, this is a very helpful resource.
- XDP for the Rest of Us (netdev 2.1, Montreal, April 2017), with Andy Gospodarek: How to get started with eBPF and XDP for normal humans. This presentation was also summarized by Julia Evans on her blog .
- XDP for the Rest of Us … second edition (netdev 2.2, Seoul, November 2017), same authors: Revised version of the talk, with new contents.
- XDP now with REDIRECT (LLC, Lund (Sweden), May 2018): Update on XDP, and in particular on the redirect actions (redirecting packets to other interfaces or other CPUs, with or without the use of eBPF maps for better performance).
(Jesper also created and tries to extend some documentation about eBPF and XDP, see related section .)
XDP workshop — Introduction, experience, and future development (Tom Herbert, netdev 1.2, Tokyo, October 2016) — as of this writing, only the video is available, I don’t know if the slides will be added.
High Speed Packet Filtering on Linux (Gilberto Bertin, DEF CON 25, Las Vegas, July 2017) — an excellent introduction to state-of-the-art packet filtering on Linux, oriented towards DDoS protection, talking about packet processing in the kernel, kernel bypass, XDP and eBPF.
AF_XDP is a new Linux socket type using eBPF filters to drive packets to user space at really high speed. Some of it is already in the kernel. There are a couple of presentations about the mechanism, such as Fast Packet Processing in Linux with AF_XDP (Björn Töpel and Magnus Karlsson, FOSDEM 2018, Brussels, February 2018).
A full-length article describing the details of XDP is available, dating from December 2018. It is called The eXpress Data Path: Fast Programmable Packet Processing in the Operating System Kernel and was written by Toke Høiland-Jørgensen, Jesper Dangaard Brouer, Daniel Borkmann, John Fastabend, Tom Herbert, David Ahern and David Miller, all being essential eBPF and XDP contributors.
- As eBPF support is coming to Red Hat, engineers from the company publish interesting content about it. Here is an article on Achieving high-performance, low-latency networking with XDP (Part I) , from Paolo Abeni (December 2018).
bpfilter is a new Linux mechanism trying to leverage eBPF programs to offer a replacement for netfilter, while remaining compatible with the iptables user utility. Here is a high-level post by Thomas Graf about the motivations behind this project, and there is my own presentation on the topic.
Are you wondering why your fresh Linux install has BPF programs running, although you do not remember attaching any? Starting with version 235 (think Ubuntu 18.04), systemd itself uses BPF programs, in particular for IP traffic accounting and access control.
P4 on the Edge (John Fastabend, May 2016): Presents the use of P4 , a description language for packet processing, with BPF to create high-performance programmable switches.
If you like audio presentations, there is an associated OvS Orbit episode (#11), called P4 on the Edge , dating from August 2016. OvS Orbit are interviews realized by Ben Pfaff, who is one of the core maintainers of Open vSwitch. In this case, John Fastabend is interviewed.
P4, EBPF and Linux TC Offload (Dinan Gunawardena and Jakub Kicinski, August 2016): Another presentation on P4 , with some elements related to eBPF hardware offload on Netronome’s NFP (Network Flow Processor) architecture.
- Cilium: Networking & Security for Containers with BPF & XDP , also featuring a load balancer use case (Linux Plumbers conference, Santa Fe, November 2016)
- Cilium: Networking & Security for Containers with BPF & XDP (Docker Distributed Systems Summit, October 2016 — video )
- Cilium: Fast IPv6 container Networking with BPF and XDP (LinuxCon, Toronto, August 2016)
- Cilium: BPF & XDP for containers (fosdem17, Brussels, Belgium, February 2017)
A good deal of contents is repeated between the different presentations; if in doubt, just pick the most recent one. Daniel Borkmann has also written a generic introduction to Cilium as a guest author on Google Open Source blog.
There are also podcasts about Cilium : an OvS Orbit episode (#4) , in which Ben Pfaff interviews Thomas Graf (May 2016), and another podcast by Ivan Pepelnjak , still with Thomas Graf about eBPF, P4, XDP and Cilium (October 2016).
- Offloading OVS Flow Processing using eBPF (William (Cheng-Chun) Tu, OvS conference, San Jose, November 2016)
- Coupling the Flexibility of OVN with the Efficiency of IOVisor (Fulvio Risso, Matteo Bertrone and Mauricio Vasquez Bernal, OvS conference, San Jose, November 2016)
These use cases for eBPF seem to be only at the stage of proposals (nothing merge to OvS main branch) as far as I know, but it will be very interesting to see what comes out of it.
XDP is envisioned to be of great help for protection against Distributed Denial-of-Service (DDoS) attacks. More and more presentations focus on this. For example, the talks from people from Cloudflare ( XDP in practice: integrating XDP in our DDoS mitigation pipeline ) or from Facebook ( Droplet: DDoS countermeasures powered by BPF + XDP ) at the netdev 2.1 conference in Montreal, Canada, in April 2017, present such use cases.
Katran is an open source layer four (L4) load-balancer built by Facebook on top of XDP. There is a presentation in this post , and the code is available on GitHub .
Kubernetes can interact in a number of ways with eBPF. There is and interesting article about Using eBPF in Kubernetes that explains how existing products (Cilium, Weave Scope) leverage eBPF to work with Kubernetes, or more generically describing what interactions with eBPF are interesting in the context of container deployment.
CETH for XDP (Yan Chan and Yunsong Lu, Linux Meetup, Santa Clara, July 2016): CETH stands for Common Ethernet Driver Framework for faster network I/O, a technology initiated by Mellanox.
The VALE switch , another virtual switch that can be used in conjunction with the netmap framework, has a BPF extension module .
- eBPF and XDP section of Suricata documentation
- SEPTun-Mark-II ( Suricata Extreme Performance Tuning guide - Mark II ), published by Michal Purzynski and Peter Manev in March 2018
- A blog post introducing the feature , published by Éric Leblond in September 2016
- The adventures of a Suricate in eBPF land , a talk on the subject (Éric Leblond, netdev 1.2, Tokyo, October 2016)
- eBPF and XDP seen from the eyes of a meerkat a more recent talk (Éric Leblond, Kernel Recipes, Paris, September 2017)
The project claims to attain excellent performances when using driver-native XDP.
InKeV: In-Kernel Distributed Network Virtualization for DCN (Z. Ahmed, M. H. Alizai and A. A. Syed, SIGCOMM, August 2016): InKeV is an eBPF-based datapath architecture for virtual networks, targeting data center networks. It was initiated by PLUMgrid, and claims to achieve better performances than OvS-based OpenStack solutions.
gobpf - utilizing eBPF from Go (Michael Schubert, fosdem17, Brussels, Belgium, February 2017): A “library to create, load and use eBPF programs from Go”
ply is a small but flexible open source dynamic tracer for Linux, with some features similar to the bcc tools, but with a simpler language inspired by awk and DTrace, written by Tobias Waldekranz.
BPFtrace is also a tool for tracing, again with its own DSL. It is flexible enough to be envisioned as a Linux replacement for DTrace and SystemTap. It was created by Alastair Robertson and Brendan Gregg.
BPFd is a project trying to leverage the flexibility of the bcc tools to trace and debug remote targets, and in particular devices running with Android. adeb is related, and provides a Linux shell environment for that purpose.
It is not to be confused with bpfd , small letters, which claims to be a container-aware framework for running BPF tracers with rules on Linux as a daemon.
Could DPDK one day work in concert with BPF? It looks likely that the AF_XDP mechanism introduced in the kernel will be used to drive packets to user space and to feed them to applications using the framework. However, there were also some discussions for replicating the eBPF interpreter and JIT compiler in DPDK itself . They did not seem to lead to the inclusion on the feature at this time.
Even if it does not make it to the core of DPDK, eBPF, and in particular AF_XDP, using XDP programs to redirect packets to user space sockets, can be used to create a poll-mode driver (PMD) for DPDK .
Sysdig , a tool for universal system visibility with native support for containers , now supports eBPF as an instrumentation back end .
The user file system FUSE is also considering using eBPF for improved performance. This was the topic of a presentation at the Linux Foundation Open Source Summit 2017 , and a related page on the ExtFUSE project is available.
In order to help with measuring power consumption for servers, the DEEP-mon tool is using eBPF programs for in-kernel aggregation of data.
- If you read my previous article, you might be interested in this talk I gave about implementing the OpenState interface with eBPF , for stateful packet processing, at fosdem17.
Documentation
Once you managed to get a broad idea of what BPF is, you can put aside generic presentations and start diving into the documentation. Below are the most complete documents about BPF specifications and functioning. Pick the one you need and read them carefully!
The specification of BPF (both classic and extended versions) can be found within the documentation of the Linux kernel, and in particular in file linux/Documentation/networking/filter.txt . The use of BPF as well as its internals are documented there. Also, this is where you can find information about errors thrown by the verifier when loading BPF code fails. Can be helpful to troubleshoot obscure error messages.
Also in the kernel tree, there is a document about frequent Questions & Answers on eBPF design in file linux/Documentation/bpf/bpf_design_QA.rst .
… But the kernel documentation is dense and not especially easy to read. If you look for a simple description of eBPF language, head for its summarized description on the IO Visor GitHub repository instead.
By the way, the IO Visor project gathered a lot of resources about BPF . Mostly, it is split between the documentation directory of its bcc repository, and the whole content of the bpf-docs repository , both on GitHub. Note the existence of this excellent BPF reference guide containing a detailed description of BPF C and bcc Python helpers.
To hack with BPF, there are some essential Linux manual pages . The first one is the bpf(2) man page about the bpf() system call , which is used to manage BPF programs and maps from userspace. It also contains a description of BPF advanced features (program types, maps and so on). The second one is mostly addressed to people wanting to attach BPF programs to tc interface: it is the tc-bpf(8) man page , which is a reference for using BPF with tc , and includes some example commands and samples of code. The eBPF helper functions, those white-listed functions that can be called from within an eBPF program, have been documented in the kernel source file that can be automatically converted into a bpf-helpers(7) manual page (see the relevant Makefile ).
Jesper Dangaard Brouer initiated an attempt to update eBPF Linux documentation , including the different kinds of maps . He has a draft to which contributions are welcome. Once ready, this document should be merged into the man pages and into kernel documentation.
The Cilium project also has an excellent BPF and XDP Reference Guide , written by core eBPF developers, that should prove immensely useful to any eBPF developer.
- bpf.h and you…
- Contextually speaking…
- BPF Verifier Overview
The last one is possibly the best existing summary about the verifier at this date.
Ferris Ellis started a blog post series about eBPF . As I write this paragraph, the first article is out, with some historical background and future expectations for eBPF. Next posts should be more technical, and look promising.
- A list of BPF features per kernel version is available in bcc repository. Useful is you want to know the minimal kernel version that is required to run a given feature. I contributed and added the links to the commits that introduced each feature, so you can also easily access the commit logs from there.
When using BPF for networking purposes in conjunction with tc, the Linux tool for t raffic c ontrol, one may wish to gather information about tc’s generic functioning. Here are a couple of resources about it.
It is difficult to find simple tutorials about QoS on Linux . The two links I have are long and quite dense, but if you can find the time to read it you will learn nearly everything there is to know about tc (nothing about BPF, though). There they are: Traffic Control HOWTO (Martin A. Brown, 2006) , and the Linux Advanced Routing & Traffic Control HOWTO (“LARTC”) (Bert Hubert & al., 2002) .
tc manual pages may not be up-to-date on your system, since several of them have been added lately. If you cannot find the documentation for a particular queuing discipline (qdisc), class or filter, it may be worth checking the latest manual pages for tc components .
Some additional material can be found within the files of iproute2 package itself: the package contains some documentation , including some files that helped me understand better the functioning of tc’s actions . Edit: While still available from the Git history, these files have been deleted from iproute2 in October 2017.
Not exactly documentation: there was a workshop about several tc features (including filtering, BPF, tc offload, …) organized by Jamal Hadi Salim during the netdev 1.2 conference (October 2016).
Bonus information—If you use tc a lot, here are some good news: I wrote a bash completion function for this tool, and it is now shipped with package iproute2 coming with kernel version 4.6 and higher!
Some work-in-progress documentation (including specifications) for XDP started by Jesper Dangaard Brouer, but meant to be a collaborative work. Under progress (September 2016): you should expect it to change, and maybe to be moved at some point (Jesper called for contribution , if you feel like improving it).
The BPF and XDP Reference Guide from Cilium project… Well, the name says it all.
- LWN has an excellent article about Writing network flow dissectors in BPF , contributed by Marta Rybczyńska in September 2018.
P4 is a language used to specify the behavior of a switch. It can be compiled for a number of hardware or software targets. As you may have guessed, one of these targets is BPF… The support is only partial: some P4 features cannot be translated towards BPF, and in a similar way there are things that BPF can do but that would not be possible to express with P4. Anyway, the documentation related to P4 use with BPF used to be hidden in bcc repository . This changed with P4_16 version, the p4c reference compiler including a backend for eBPF .
There is also an interesting presentation from Jamal Hadi Salim, presenting a number of points from tc from which P4 could maybe get some inspiration: What P4 Can Learn From Linux Traffic Control Architecture .
Brendan Gregg has initiated excellent tutorials intended for people who want to use bcc tools for tracing and monitoring events in the kernel. The first tutorial about using bcc itself comes with many steps to understand how to use the existing tools, while the one intended for Python developers focuses on developing new tools, across seventeen “lessons”.
Lorenza Fontana has made a tutorial to explain how to Load XDP programs using the ip (iproute2) command .
If you are unfamiliar to kernel compiling, Diego Pino García has a blog entry on How to build a kernel with [AF-]XDP support .
Sasha Goldshtein also has some Linux Tracing Workshops Materials involving the use of several BPF tools for tracing.
Another post by Jean-Tiare Le Bigot provides a detailed (and instructive!) example of using perf and eBPF to setup a low-level tracer for ping requests and replies.
Few tutorials exist for network-related eBPF use cases. There are some interesting documents, including an eBPF Offload Starting Guide , on the Open NFP platform operated by Netronome. Other than these, the talks from Jesper and Andy, XDP for the Rest of Us (and its second edition ), are probably one of the best ways to get started with XDP.
If you really focus on hardware offload for eBPF, Netronome (my employer as I edit this text) is the only vendor to propose it at the moment. Besides their Open-NFP platform, the best source of information is their support platform: https://help.netronome.com . You will find there video tutorials from David Beckett explaining how to run and offload XDP programs, user guides, and other materials… including the firmware for the Agilio SmartNICs required to perform eBPF offload!
It is always nice to have examples. To see how things really work. But BPF program samples are scattered across several projects, so I listed all the ones I know of. The examples do not always use the same helpers (for instance, tc and bcc both have their own set of helpers to make it easier to write BPF programs in C language).
The kernel contains examples for most types of program: filters to bind to sockets or to tc interfaces, event tracing/monitoring, and even XDP. You can find these examples under the linux/samples/bpf/ directory.
Nowadays, most examples are added under linux/tools/testing/selftests/bpf as unit tests. This includes tests for hardware offload or for libbpf.
Some additional tests regarding BPF with tc can be found in the kernel suite of tests for tc itself, under linux/tools/testing/selftests/tc-tests .
Jesper Dangaard Brouer also maintains a specific set of samples in his prototype-kernel repository. They are very similar to those from the kernel, but can be compiled outside of the kernel infrastructure (Makefiles and headers).
Also do not forget to have a look to the logs related to the (git) commits that introduced a particular feature, they may contain some detailed example of the feature.
The iproute2 package provide several examples as well. They are obviously oriented towards network programming, since the programs are to be attached to tc ingress or egress interfaces. The examples dwell under the iproute2/examples/bpf/ directory.
Many examples are provided with bcc :
Some are networking example programs, under the associated directory. They include socket filters, tc filters, and a XDP program.
The tracing directory include a lot of example tracing programs . The tutorials mentioned earlier are based on these. These programs cover a wide range of event monitoring functions, and some of them are production-oriented. Note that on certain Linux distributions (at least for Debian, Ubuntu, Fedora, Arch Linux), these programs have been packaged and can be “easily” installed by typing e.g. # apt install bcc-tools , but as of this writing (and except for Arch Linux), this first requires to set up IO Visor’s own package repository.
There are also some examples using Lua as a different BPF back-end (that is, BPF programs are written with Lua instead of a subset of C, allowing to use the same language for front-end and back-end), in the third directory.
Of course, bcc tools themselves are interesting example use cases for eBPF programs.
Some other BPF programs are emerging here and there. Have a look at the different projects based on or using eBPF, mentioned above, and search their code to find how they inject programs into the kernel.
Netronome also has a GitHub repository with some samples XDP demo applications , some of them for hardware offload only, others for both driver and offloaded XDP.
While bcc is generally the easiest way to inject and run a BPF program in the kernel, attaching programs to tc interfaces can also be performed by the tc tool itself. So if you intend to use BPF with tc , you can find some example invocations in the tc-bpf(8) manual page .
Sometimes, BPF documentation or examples are not enough, and you may have no other solution that to display the code in your favorite text editor (which should be Vim of course) and to read it. Or you may want to hack into the code so as to patch or add features to the machine. So here are a few pointers to the relevant files, finding the functions you want is up to you!
The file linux/include/linux/bpf.h and its counterpart linux/include/uapi/bpf.h contain definitions related to eBPF, to be used respectively in the kernel and to interface with userspace programs.
On the same pattern, files linux/include/linux/filter.h and linux/include/uapi/filter.h contain information used to run the BPF programs .
The main pieces of code related to BPF are under linux/kernel/bpf/ directory. The different operations permitted by the system call , such as program loading or map management, are implemented in file syscall.c , while core.c contains the interpreter . The other files have self-explanatory names: verifier.c contains the verifier (no kidding), arraymap.c the code used to interact with maps of type array, and so on.
Several functions as well as the helpers related to networking (with tc, XDP…) and available to the user, are implemented in linux/net/core/filter.c . It also contains the code to migrate cBPF bytecode to eBPF (since all cBPF programs are now translated to eBPF in the kernel before being run).
Function and helpers related to event tracing are in linux/kernel/trace/bpf_trace.c instead.
The JIT compilers are under the directory of their respective architectures, such as file linux/arch/x86/net/bpf_jit_comp.c for x86. Exception is made for JIT compilers used for hardware offload, they sit in their driver, see for instance linux/drivers/net/ethernet/netronome/nfp/bpf/jit.c for Netronome NFP cards.
You will find the code related to the BPF components of tc in the linux/net/sched/ directory, and in particular in files act_bpf.c (action) and cls_bpf.c (filter).
I have not used seccomp-BPF much, but you should find the code in linux/kernel/seccomp.c , and some example use cases can be found in linux/tools/testing/selftests/seccomp/seccomp_bpf.c .
Once loaded into the in-kernel BPF virtual machine, XDP programs are hooked from userspace into the kernel network path thanks to a Netlink command. On reception, the function dev_change_xdp_fd() in file linux/net/core/dev.c is called and sets a XDP hook. Such hooks are located in the drivers of supported NICs. For example, the nfp driver used for Netronome hardware has hooks implemented in files under the drivers/net/ethernet/netronome/nfp/ directory. File nfp_net_common.c receives Netlink commands and calls nfp_net_xdp_setup() , which in turns calls for instance nfp_net_xdp_setup_drv() to install the program.
One can find the code for the bcc set of tools on the bcc GitHub repository . The Python code , including the BPF class, is initiated in file bcc/src/python/bcc/__init__.py . But most of the interesting stuff—to my opinion—such as loading the BPF program into the kernel, happens in the libbcc C library .
The code related to BPF in tc comes with the iproute2 package, of course. Some of it is under the iproute2/tc/ directory. The files f_bpf.c and m_bpf.c (and e_bpf.c) are used respectively to handle BPF filters and actions (and tc exec command, whatever this may be). File q_clsact.c defines the clsact qdisc especially created for BPF. But most of the BPF userspace logic is implemented in iproute2/lib/bpf.c library, so this is probably where you should head to if you want to mess up with BPF and tc (it was moved from file iproute2/tc/tc_bpf.c, where you may find the same code in older versions of the package).
The kernel also ships the sources of three tools ( bpf_asm.c , bpf_dbg.c , bpf_jit_disasm.c ) related to BPF, under the linux/tools/net/ (until Linux 4.14) or linux/tools/bpf/ directory depending on your version:
- bpf_asm is a minimal cBPF assembler.
- bpf_dbg is a small debugger for cBPF programs.
- bpf_jit_disasm is generic for both BPF flavors and could be highly useful for JIT debugging.
- bpftool is a generic utility written by Jakub Kicinski, and that can be used to interact with eBPF programs and maps from userspace, for example to show, dump, load, pin programs, or to show, create, pin, update, delete maps. It can also attach and detach programs to cgroups, and has JSON support. It keeps getting more and more features, and is expected to be the go-to tool for eBPF introspection and simple management.
Read the comments at the top of the source files to get an overview of their usage.
Other essential files to work with eBPF are the two userspace libraries from the kernel tree, that can be used to manage eBPF programs or maps from external programs. The functions are accessible through headers bpf.h and libbpf.h (higher level) from directory linux/tools/lib/bpf/ . The tool bpftool heavily relies on those libraries, for example.
If you are interested the use of less common languages with BPF, bcc contains a P4 compiler for BPF targets as well as a Lua front-end that can be used as alternatives to the C subset and (in the case of Lua) to the Python tools.
The BPF backend used by clang / LLVM for compiling C into eBPF was added to the LLVM sources in this commit (and can also be accessed on the GitHub mirror ).
As far as I know there are at least two eBPF userspace implementations. The first one, uBPF , is written in C. It contains an interpreter, a JIT compiler for x86_64 architecture, an assembler and a disassembler.
The code of uBPF seems to have been reused to produce a generic implementation , that claims to support FreeBSD kernel, FreeBSD userspace, Linux kernel, Linux userspace and MacOSX userspace. It is used for the BPF extension module for VALE switch .
The other userspace implementation is my own work: rbpf , based on uBPF, but written in Rust. The interpreter and JIT-compiler work (both under Linux, only the interpreter for MacOSX and Windows), there may be more in the future.
As stated earlier, do not hesitate to have a look at the commit log that introduced a particular BPF feature if you want to have more information about it. You can search the logs in many places, such as on git.kernel.org , on GitHub , or on your local repository if you have cloned it. If you are not familiar with git, try things like git blame <file> to see what commit introduced a particular line of code, then git show <commit> to have details (or search by keyword in git log results, but this may be tedious). See also the list of eBPF features per kernel version on bcc repository, that links to relevant commits.
Troubleshooting
The enthusiasm about eBPF is quite recent, and so far I have not found a lot of resources intending to help with troubleshooting. So here are the few I have, augmented with my own recollection of pitfalls encountered while working with BPF.
Make sure you have a recent enough version of the Linux kernel (see also this document ).
If you compiled the kernel yourself: make sure you installed correctly all components, including kernel image, headers and libc.
When using the bcc shell function provided by tc-bpf man page (to compile C code into BPF): I once had to add includes to the header for the clang call:
(seems fixed as of today).
For other problems with bcc , do not forget to have a look at the FAQ of the tool set.
If you downloaded the examples from the iproute2 package in a version that does not exactly match your kernel, some errors can be triggered by the headers included in the files. The example snippets indeed assume that the same version of iproute2 package and kernel headers are installed on the system. If this is not the case, download the correct version of iproute2, or edit the path of included files in the examples to point to the headers included in iproute2 (some problems may or may not occur at runtime, depending on the features in use).
To load a program with tc, make sure you use a tc binary coming from an iproute2 version equivalent to the kernel in use.
To load a program with bcc, make sure you have bcc installed on the system (just downloading the sources to run the Python script is not enough).
With tc, if the BPF program does not return the expected values, check that you called it in the correct fashion: filter, or action, or filter with “direct-action” mode.
With tc still, note that actions cannot be attached directly to qdiscs or interfaces without the use of a filter.
The errors thrown by the in-kernel verifier may be hard to interpret. The kernel documentation may help, so may the reference guide or, as a last resort, the source code (see above) (good luck!). For this kind of errors it is also important to keep in mind that the verifier does not run the program. If you get an error about an invalid memory access or about uninitialized data, it does not mean that these problems actually occurred (or sometimes, that they can possibly occur at all). It means that your program is written in such a way that the verifier estimates that such errors could happen, and therefore it rejects the program.
Note that tc tool has a verbose mode, and that it works well with BPF: try appending verbose at the end of your command line.
bcc also has verbose options: the BPF class has a debug argument that can take any combination of the three flags DEBUG_LLVM_IR , DEBUG_BPF and DEBUG_PREPROCESSOR (see details in the source file ). It even embeds some facilities to print output messages for debugging the code.
LLVM v4.0+ embeds a disassembler for eBPF programs. So if you compile your program with clang, adding the -g flag for compiling enables you to later dump your program in the rather human-friendly format used by the kernel verifier. To proceed to the dump, use:
Working with maps? You want to have a look at bpf-map , a very userful tool in Go created for the Cilium project, that can be used to dump the contents of kernel eBPF maps. There also exists a clone in Rust.
There is an old bpf tag on StackOverflow , but as of this writing it has been hardly used—ever (and there is nearly nothing related to the new eBPF version). If you are a reader from the Future though, you may want to check whether there has been more activity on this side.
Completion in Vim for working with eBPF and bcc. Yes, someone worked on it.
In case you would like to easily test XDP , there is a Vagrant setup available. You can also test bcc in a Docker container .
Wondering where the development and activities around BPF occur? Well, the kernel patches always end up on the netdev mailing list (related to the Linux kernel networking stack development, check also bpf_devel_QA.rst from the kernel documentation): search for “BPF” or “XDP” keywords. Since April 2017, there is also a mailing list specially dedicated to XDP programming (both for architecture or for asking for help). Many discussions and debates also occur on the IO Visor mailing list , since BPF is at the heart of the project. If you only want to keep informed from time to time, there is also an @IOVisor Twitter account .
And come back on this blog from time to time to see if they are new articles about BPF !
Special thanks to Daniel Borkmann for the numerous additional documents he pointed to me so that I could complete this collection.

ChucK Class Library Reference
/ basic filter ugens, filterbasic.
Basic filter unit generators.
inherits : UGen : Object
Constructors.
FilterBasic ()
Default constructor for FilterBasic.
member functions
float Q ( float val)
Set filter resonance.
Get filter resonance.
float freq ( float val)
Set filter cutoff/center frequency.
float freq ()
Get filter cutoff/center frequency.
void set ( float freq, float Q)
Set filter frequency and resonance at the same time.

inherits : FilterBasic : UGen : Object
- filter/lpf.ck
- filter/rlpf.ck
Default constructor for LPF.
Set filter cutoff frequency.
Get filter cutoff frequency.
- filter/hpf.ck
- filter/rhpf.ck
Default constructor for HPF.
- filter/bpf.ck
Default constructor for BPF.
Set filter center frequency.
Get filter frequency and resonance at the same time.
- filter/brf.ck
Default constructor for BRF.
Get filter center frequency.
- basic/wind.ck
- basic/moe.ck
Default constructor for BiQuad.
float a0 ( float value)
Set filter coefficient.
float a0 ()
Get filter coefficient.
float a1 ( float value)
float a1 ()
float a2 ( float value)
float a2 ()
float b0 ( float value)
float b0 ()
float b1 ( float value)
float b1 ()
float b2 ( float value)
float b2 ()
int eqzs ( int value)
Enable equal-gain zeroes.
int norm ( int value)
Toggle normalization.
int norm ()
Get normalization setting.
float pfreq ( float freq)
Set resonance frequency (poles).
float pfreq ()
Get resonance frequency (poles).
float prad ( float value)
Set Pole radius (values greater than 1 will be unstable).
float prad ()
Get pole radius.
float pregain ( float level)
Set pregain.
float pregain ()
Get pregain.
float zfreq ( float freq)
Set notch frequency.
float zfreq ()
Get notch frequency.
float zrad ( float value)
Set zero radius.
float zrad ()
Get zero radius.
- filter/resonz.ck
Default constructor for ResonZ.
- deep/follower.ck
Default constructor for OnePole.
float pole ( float value)
Set pole position along real axis of z-plane.
float pole ()
Get pole position along real axis of z-plane.
- deep/plu.ck
- deep/plu2.ck
- deep/plu3.ck
Default constructor for OneZero.
float zero ( float value)
Set zero position.
float zero ()
Get zero position.
- shred/powerup.ck
Default constructor for TwoPole.
float freq ( float value)
Set filter resonance frequency.
Get filter resonance frequency.
Set filter normalization.
Get filter normalization.
float radius ( float value)
Set filter radius resonance.
float radius ()
Get filter radius resonance.
- deep/chant.ck
- deep/say-chu.ck
Default constructor for TwoZero.
Set filter notch frequency.
Get filter notch frequency.
Set filter notch radius.
Get filter notch radius.
- filter/dcblocker.ck
- stk/flute.ck
- analysis/tracking/pitch-track.ck
- analysis/tracking/pitch-third.ck
- analysis/tracking/pitch-fifth.ck
- analysis/tracking/pitch-seventh.ck
- analysis/tracking/Tracking.ck
PoleZero ()
Default constructor for PoleZero.
float allpass ( float value)
Set allpass filter with given coefficient.
float allpass ()
Get allpass filter with given coefficient.
float blockZero ( float value)
Set DC blocking filter with given pole position.
float blockZero ()
Get DC blocking filter with given pole position.
Learn how UpToDate can help you.
Select the option that best describes you
- Medical Professional
- Resident, Fellow, or Student
- Hospital or Institution
- Group Practice
- Patient or Caregiver
- Find in topic
RELATED TOPICS
INTRODUCTION
This topic will review the etiologies, diagnosis, and treatment of patients with BPF. The diagnosis and management of tracheoesophageal and alveolopleural fistula are discussed separately. (See "Tracheo- and broncho-esophageal fistulas in adults" and "Alveolopleural fistula and prolonged air leak in adults" .)
Lung resection — BPF ( picture 1 ) is most commonly encountered after lung resection surgery (pneumonectomy, lobectomy, segmentectomy), with a frequency ranging from 1.5 to 4.5 percent after pneumonectomy and 0.5 to 1 percent after lobectomy and sublobar resection [ 1 ]. Several risk factors are associated with BPF in the postoperative setting [ 2-6 ]:
● Right-sided surgery
An official website of the United States government
The .gov means it's official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you're on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
- Browse Titles
NCBI Bookshelf. A service of the National Library of Medicine, National Institutes of Health.
StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2024 Jan-.

StatPearls [Internet].
Bronchopleural fistula.
Irim Salik ; Rishik Vashisht ; Apolonia E. Abramowicz .
Affiliations
Last Update: May 1, 2023 .
- Continuing Education Activity
Bronchopleural fistula (BPF) is a sinus tract between the main stem, lobar, or segmental bronchus and the pleural space. Treatment for BPF ranges from medical management to bronchoscopic procedures for critically ill patients and surgical intervention for those deemed at the highest risk. This activity describes the epidemiology, pathophysiology, causes, evaluation, and management of bronchopleural fistula. It explains the role of an interprofessional team in the evaluation and management of patients with bronchopleural fistula.
- Describe the risk factors for bronchopleural fistulas.
- Outline the diagnostic techniques of patients with bronchopleural fistulas.
- Explain the conservative and invasive treatment options for the management of patients with bronchopleural fistulas.
- Review the interplay among the interprofessional team in diagnosing, treating, and rehabilitation of patients with bronchopleural fistula.
- Introduction
Bronchopleural fistula (BPF) is a sinus tract between the main stem, lobar, or segmental bronchus and the pleural space. It can be a potentially catastrophic complication following pneumonectomy or other pulmonary resection. Morbidity ranges between 25% and 71%, and diagnosis and management is often a challenge for physicians. [1] Other common causes of BPF include pulmonary infection causing necrosis, persistent spontaneous pneumothorax, chemotherapy or radiotherapy from malignancy, and tuberculosis.
Treatment for BPF ranges from medical management to bronchoscopic procedures for critically ill patients and surgical intervention for those deemed at the highest risk. There is a lack of consensus regarding optimal management due to varying therapeutic success. Varoli et al. described the time of onset following surgical intervention to classify fistulas as early (1 to 7 days), intermediate (8 to 30 days), or late (more than 30 days). [2] Although fistulas almost always occur within three months after surgery BPF following pleuropulmonary infection can occur at any point. [3]
The most common risk factors associated with bronchopleural fistula (BPF) in the postoperative setting include right-sided pneumonectomy and right lower lobectomy. The fistula is commonly found on the stump beside the residual lobe due to the increased risk of ischemic necrosis or the pooling of secretions leading to bacterial overgrowth and colonization. The increased risk of BPF associated with right pneumonectomy is due to the more extensive resection required. [4] [5] [6] [7]
Other causes include: [8]
- Chemotherapy and radiation therapy
- Lobectomy-right, bi-lobectomy, and lower lobectomy
- Diabetes mellitus
- Heavy smoking and chronic obstructive pulmonary disease
- Bullous lung disease
- Spontaneous pneumothorax or other parenchymal abnormalities
- Low nutritional status or poor wound healing
- Previous ipsilateral thoracotomy
- A large diameter bronchial stump (greater than 25 mm)
- Extensive lymph node dissection
- Age older than 60 years
- Corticosteroid use
- Leukocytosis
- Tracheostomy
- Bronchoscopy for sputum suctioning/mucous
- Residual tumor in the resection margins
- Tightness of the individual sutures
- Excessive peribronchial and paratracheal dissection
- Prolonged postoperative mechanical ventilation
- Tuberculosis
- Hemophilus influenza
- Streptococcus viridans
- Staphylococcus aureus
- Pseudomonas aeruginosa
- Klebsiella pneumoniae
- Pneumococcus
- Non-hemolytic streptococcus
- Aspergillus
- Histoplasma capsulatum
- Gastroesophageal reflux disease with Barrett esophagus
- Boerhaave syndrome
- Broncholithiasis
- Lung cancer
- Thyroid cancer
- Esophageal cancer
- Thoracic trauma with tracheobronchial tree disruption
- Bougie intubation
- Necrotizing lung disease associated with radiation or chemotherapy
- Acute respiratory distress syndrome (ARDS): Especially in patients requiring ventilation with high airway pressures
- Ventilator-induced barotrauma
- Overzealous manual ventilation
- Central line placement
- Epidemiology
Bronchopleural fistula (BPF) is most commonly encountered after lung resection surgery (pneumonectomy, lobectomy, segmentectomy), with a frequency ranging from 4.5% to 20% after pneumonectomy and 0.5% to 1% after lobectomy. [9]
- Pathophysiology
Postoperative bronchopleural fistula (BPF) may be classified as acute, subacute, and chronic. The acute form is caused by surgical dehiscence and requires prompt surgical intervention. When acute, BPF can be life-threatening due to tension pneumothorax or asphyxiation from pulmonary flooding. Patients present with sudden appearance of dyspnea, hypotension, subcutaneous emphysema, cough with expectoration of purulent fluid, tracheal or mediastinal shift, persistent air leak, and a reduction or disappearance of pleural effusion on the chest radiograph. The subacute and chronic forms are primarily related to infection and are often seen in immunocompromised or debilitated patients with multiple comorbidities. The subacute presentation is more insidious and is characterized by wasting, malaise, and fever. The chronic form is associated with an infectious process and fibrosis of the pleural space. [10]
A BPF can occur any time during the postoperative period but more often occurs within 8 to 12 days after surgery. If seen within the first four postoperative days, the BPF is likely secondary to a mechanical failure of bronchial stump closure and requires reexploration. A BPF may also occur after suppurative pneumonia, massive pulmonary infarction, or spontaneously. Empyema may occur alone or may be associated with a BPF. A BPF can occur without associated empyema, and the fluid in the pleural space in these cases is sterile. Displacement of the mediastinum to the opposite side occurs because of air on the operative side. Clearing of fluid from the pleural space and coughing up of fluid and blood suggest a BPF. The sudden reappearance of air in an obliterated space suggests either a BPF or a gas-forming infectious process. If a fistula appears in nonsurgical cases or in delayed postoperative period, the diagnosis should be suspected when fever, productive cough, and new or increasing air-fluid levels are seen on the chest radiograph in the pleural space. Esophagotracheal fistulas are associated with coughing and dyspnea during eating and drinking. [10] Nonresolving pneumonia should be endoscopically investigated.
- History and Physical
Patients with bronchopleural fistula (BPF) can present with symptoms that range from acute symptoms of tension pneumothorax to subacute symptoms of empyema. Most patients present in the first two weeks following lung resection. BPF should be suspected in the postoperative lung resection patient who presents with sudden onset of dyspnea, chest pain, hemodynamic instability, and subcutaneous emphysema. Symptoms may be less abrupt in those in whom the chest tube is still in place, and a large persistent or new air leak through the chest tube drainage system may be the only sign present. [11] Examination findings are typically nonspecific but may reveal reduced air entry on the affected side and tracheal deviation if tension pneumothorax is present.
Patients who present in the late postoperative period (more than 14 days), or patients with BPF from other causes including infection or malignancy, present with symptoms and signs of empyema. These include fever, malaise, muscle wasting, cough with purulent sputum, reduced air entry, and dullness to percussion on the affected side. When the BPF is associated with empyema that is not adequately drained, the infection can erode through the chest wall, and a pleurocutaneous opening with drainage of mucopurulent material may be seen; it is known as empyema necessitans.
Persistent air leak after pulmonary injury may represent either disruption of a bronchus or rupture of an overdistended alveolus. Several methods have been used to diagnose bronchopleural fistulas (BPFs), including the instillation of methylene blue into the pleural space and bronchography. [12] In addition, small metallic probes introduced through the working channel of the bronchoscope, and changes in gas concentration in the cavity of pneumonectomy after inhaling different concentrations of oxygen and N2O are also useful. [13] Bronchoscopic exploration allows proper evaluation of the stump and attempts to localize the fistula. It also helps exclude tuberculosis or other infectious etiologies and allows the introduction of sealants into the fistulous tract. While a large BPF is more likely to be seen on bronchoscopy, sequential balloon occlusion of the bronchi is sometimes used, particularly for the localization of a smaller or segmental BPF. The diagnosis of BPF is made using a combination of clinical, radiographic, and bronchoscopic findings that confirm an air leak from a major, lobar, or segmental bronchus to the pleural space. Although there are no specific laboratory findings, some patients with an infected pleural space may exhibit leukocytosis or elevated erythrocyte sedimentation rate.
Radiological features that suggest the presence or the development of a BPF include an increase in the intrapleural airspace, the appearance of a new air-fluid level, changes in an already present air-fluid level, development of tension pneumothorax, and a drop in the air-fluid level exceeding 2 cm. [14] With computed tomography (CT), apart from the demonstration of pneumothorax, pneumomediastinum, and underlying lung pathology, there may be evidence of actual fistulous communication in some patients. [15] In those who have not undergone lung resection, features of the underlying etiology such as malignancy may be demonstrated via CT with a cavitating mass and air-fluid levels.
Using standard and thin section non-contrast CT scans, Westcott and Volpe. could demonstrate a fistula in 10 out of 20 patients. [15] In almost all of these cases, the fistulous tract was located peripherally, and in only one case was there an air-leak in the setting of lung resection. Three-dimensional reconstruction using the spiral technique has also been used successfully to demonstrate BPF in its entirety. [16] The return of continuous bubbles suggests the presence of BPF during bronchial washing. A bronchoscope with inflation of a balloon-tipped catheter into selected airways can aid in localization, as balloon occlusion decreases or eliminates an air leak. Capnography can be used to identify the bronchial segment related to BPF. End-tidal carbon dioxide is measured by connecting a capnograph to a polyethylene catheter and has a reported sensitivity of 83% and a specificity of 100% in the diagnosis of BPF. [17]
Several authors have tried to localize a BPF using radiolabeled aerosol inhalation with planar and single-photon emission tomography (SPECT) imaging. [18] These imaging modalities require substantial time and a patient’s cooperation.This technique has been criticized because the aerosol tends to deposit in areas of turbulence and may lead to false-positive results in patients with obstructive airways. In addition, the estimation of the size of the BPF may be inaccurate as it is an indirect measurement from the kinetics of tracer gas during different phases of the study. [19]
Computed tomography bronchography (CTB) has been utilized in the diagnosis of a difficult BPF. Following bronchoscopy, Sarkar et al. injected 20 to 30 mL of a water-based nonionic low osmolar iodinated contrast medium iohexol at the suspected fistula site either through a catheter or directly through the working channel of the bronchoscope. [20] CT was performed immediately with a targeted reconstruction of images in different planes. The fistula was easily visualized using standard axial and sagittal sections.
- Treatment / Management
First-line therapy should address any immediate, life-threatening conditions, for example, endobronchial contamination, pulmonary flooding, and tension pneumothorax. Since most bronchopleural fistulas (BPFs) occur early in the postoperative period and are not infected, patients can undergo surgical repair with excellent success. Bronchoscopic approaches have variable success rates and are appropriate for those who are not suitable for surgical intervention.
The patient should be placed with the affected side dependent, and adequate pleural drainage is performed. The first intervention for BPF should be drainage of air and fluid from the pleural space by chest tube thoracostomy. Pleural fluid should be sent for complete blood cell count (CBC), pH, total protein, lactate dehydrogenase, glucose, cytology, triglycerides, gram stain, and culture to assess for pleural infection. Although integral for drainage, the chest tube itself can function as a foreign body and predispose to infection at the insertion site and in the pleural space. In patients who are mechanically ventilated, the chest tube can be used to add positive intrapleural pressure during the expiratory phase or occlusion during the inspiratory phase. These interventions aim to decrease the air leak during expiration to maintain positive end-expiratory pressure (PEEP) and to decrease BPF flow during inspiration. The chest tube can also be used to apply sclerosing agents, such as talc and bleomycin, to promote pleurodesis. Broad-spectrum intravenous antibiotics against gram-positive, gram-negative, and anaerobic microorganisms should be given to all patients until gram stain, cultures, and sensitivities are available. Postural drainage can be initiated after specimens have been obtained, as long as a patient can expectorate, chest cavity, and chest tube drainage is less than 30 mL per day, and there is concomitant pleural irrigation. [21]
Suture reclosure of the bronchial stump with vascularized flap coverage is curative for the fistula presenting acutely, normally less than two weeks after surgery. [22] In most cases, a video-assisted thoracoscopic surgical (VATS) approach is performed, but rarely a thoracotomy is needed. Surgical closure of the fistula is done by an anterior, trans-pericardial approach thoracotomy with muscle flap to fill the pleural space or with a muscle flap coverage of the fistula with a limited thoracoplasty. Patients who present with a BPF developing late or those who develop the fistula as a complication of suppurative pleuropulmonary diseases are initially managed medically. Medical management includes dependent drainage and reduction of the pleural space, antibiotic treatment, nutritional supplementation, and adequate ventilator management. [23]
The disease course is more complicated for patients with BPF who are mechanically ventilated. Maintaining airway pressures at or below the critical opening pressure of the fistula to promote healing, but yet provide adequate alveolar ventilation for sufficient gas exchange can present a significant challenge. Air-leaks through bronchopleural fistulae may range from less than 1 to 16 L per minute. Adverse effects of BPF in mechanically-ventilated patients include incomplete lung expansion, loss of effective tidal volume, or positive end-expiratory pressure, inability to remove carbon dioxide, and prolonged ventilatory support. The large air leak via BPF can also result in auto-triggering of the ventilator, leading to severe hyperventilation and inappropriately large doses of sedatives and/or neuromuscular blockers administered to reduce spontaneous respiration. [24] Mean airway pressure should be reduced as much as possible, including minimal PEEP, low peak airway pressures, and reducing the proportion of minute ventilation provided by the ventilator. Intermittent mandatory ventilation modes with low tidal volumes, respiratory rates, and shorter inspiratory times are appropriate.
Other techniques described to decrease an air leak include independent lung ventilation with two ventilators, differential lung ventilation, and high-frequency jet ventilation (HFJV). [25] Selective intubation of the unaffected lung, the use of double-lumen tube intubation with differential lung ventilation, or the use of independent lung ventilation and patient positioning are all advocated. HFJV with permissive hypercapnia avoids the need for a double-lumen tube (DLT) or single lumen tube with a bronchial blocker. HFJV avoids barotrauma to the unaffected lung and decreases the air leak. If HFJV is not available, BPF is one of the strict indications for split lung ventilation. A DLT is preferred because it allows physiologic separation of the lungs if an air leak becomes severe enough to require varied ventilator modes or settings for each lung. According to the airway device used, low-frequency jet ventilation or low tidal volume ventilation is applied during resection. ECMO, either veno-venous or veno-arterial, is another alternative strategy for gas exchange. [25]
Methods to limit airflow across BPFs include direct closure, decortication, thoracoplasty, omental or muscle transposition, and completion pneumonectomy. [26] Localization and size of the fistula may be the decisive factors in choosing between surgical and endoscopic procedures. If a patient is severely debilitated or life expectancy is limited, palliation can sometimes be provided by a surgically created pleurocutaneous tract to vent the pleural space on a permanent or temporary basis. [27] Patients should be assessed and treated for potential empyema. The development of post-pneumonectomy empyema (PPE) occurs at a rate between 2% and 16%. In the setting of PPE, BPFs are present in approximately 60% to 80% of patients and carry a high mortality rate ranging from 21% to 71%. [28]
Patients with BPF from causes other than lung resection, including malignancy and infection, are treated with bronchoscopic methods because the bronchial stump is affected by disease, and stump revision is not feasible. Bronchoscopic management is primarily useful for temporary fistula closure but can be used as a bridge to curative surgery if the underlying cause is reversible. A flexible bronchoscope provides superior and precise access to a greater portion of the bronchial tree than the rigid bronchoscope. Outcomes are variable with rates of successful closure ranging from 30% to 80%. [29] Bronchoscopic intervention is a viable first option in small bronchopleural fistulas that are less than 5 mm in diameter. Endoscopic closure of a BPF is of lower cost, has a reduced rate of trauma, and can be performed in critically ill patients. The BPF can be closed endoscopically if there is no evidence of infection in the pleural cavity.
In patients with BPFs equal to 8 mm, fistula closure with airway stents, coils, or Amplatzer devices is a viable option. The largest case series of 31 patients with BPF reported that the Amplatzer device was effective in 96% of cases, lasting for up to 18 months. [30] Silicone and covered metallic stents for BPF closure involving the central airway have also been described. [31] Angiographic coils, alone or in combination with other occlusive materials, can also successfully treat BPF. Occlusive agents act first as a plug mechanically sealing the leak and later induce an inflammatory process with mucosal proliferation and fibrosis, creating a permanent seal. Fistula repair also occurs by the organization of granulation tissue.
There are several case series and reports of patients with BPF who were treated with occlusive materials, none of which have been compared. Bronchoscopic placement of glutaraldehyde sterilized lead shot, gel foam and tetracycline, autologous blood patch, fibrin glue, gelatin-resorcinol mixture, oxidized regenerated cellulose, albumin-glutaraldehyde tissue adhesive, cryoprecipitate fibrin glue and NN-butyl 2-cyanoacrylate has been attempted at the fistula site. [32] [33] [34] [35] [36] [37]
The 2 component fibrin cryoprecipitate glue (calcium gluconate and cryoprecipitate along with topical thrombin [1000 IU/mL]) is delivered at the fistula site through a double lumen catheter inserted into the operative channel of the bronchoscope, creating a fibrin clot that occludes the fistula. Small BPFs can be occluded using an endobronchial injection of ethanol, polidocanol, and tetracycline followed by autologous blood. [38]
Although not often utilized, argon plasma coagulation and neodymium-doped yttrium aluminum garnet (Nd:YAG) laser have been described for patients with small BPFs. Transplanted bone marrow-derived mesenchymal stem cells and dehydrated amniotic membrane allograft have been reported as successful in BPF closure. [39] [40]
Patients should be monitored after fistula closure for clinical symptoms of recurrence, chest tube output of air, and with imaging of the chest. Patients with a sealed fistula should not have an air leak, and imaging should demonstrate stability or resolution of air in the pleural space. Repeat bronchoscopy is not routine and only performed if fistula recurrence or a complication is suspected. If valves or stents are used, a chest CT scan and bronchoscopy are repeated at six weeks to assess for complications. For patients who fail surgical or bronchoscopic intervention, options include repeat surgery, an alternate bronchoscopic method, or in rare cases, an open window thoracostomy such as Eloesser flap thoracostomy or a Claggett window. [29]
- Differential Diagnosis
In patients who have had a pneumonectomy, acute findings of tension pneumothorax are essentially pathognomonic for bronchopleural fistula (BPF). Although other conditions such as postoperative tension chylothorax or hemorrhage into the pleural space may also cause the findings of tension pneumothorax, the affected hemithorax should fill with fluid rather than air. Tension pneumothorax may also be due to a displaced or obstructed chest tube; ensuring a patent chest tube while imaging is being obtained may distinguish this phenomenon from true BPF. In patients who present with empyema, BPF is likely if the effusion contains air, and there is an air leak after chest tube placement. The culture of the effusion may help distinguish anaerobic infection from BPF. Bronchoscopic findings of a bronchial defect will distinguish BPF from other etiologies.
A BPF can cause significant morbidity, prolonged hospitalization, and mortality. Mortality rates vary between 18% to 67%. [41] The most common cause of death is aspiration pneumonia and subsequent acute respiratory distress syndrome or development of tension pneumothorax. [23] Pierson et al. reported their experience with all cases of mechanical ventilation at a major trauma center for four years. [42] They found that 39 of the 1700 patients receiving mechanical ventilation had BPFs lasting at least 24 hours. Overall mortality in these 39 patients was 67%, and Pierson et al. found that mortality was higher when BPF developed late rather than early in the illness (94% versus 45%). [42] Patients with large air leaks also had significant mortality compared to smaller leaks. They concluded that BPF during mechanical ventilation identifies patients with high mortality, but that unmanageable respiratory acidosis from this complication is rare. Reports using omental and thoracic flaps have shown decreased mortality. [43] [44] Sirbu et al. found the mortality rate of BPF patients to be 27.2% (6 of 22 patients). [45]
- Pearls and Other Issues
- BPF is most commonly encountered after pulmonary resection (pneumonectomy, lobectomy, segmentectomy) with a frequency ranging from 4.5% to 20% after pneumonectomy and 0.5% to 1% after lobectomy.
- Patients with BPF can present with symptoms that range from acute symptoms of tension pneumothorax to subacute symptoms of empyema or a new or persistent air leak via a chest tube.
- Clinical, radiographic, and bronchoscopic findings that confirm an air leak from a bronchus to the pleural space are used to diagnose a BPF.
- BPFs do not typically spontaneously undergo closure and almost always require some surgical or bronchoscopic intervention.
- All patients with a BPF should have a chest tube placed to drain air. In cases of an empyema, infected pleural fluid should be drained, and antibiotics should be initiated. In all cases, a patient's comorbidities and nutritional status should be optimized.
- For most postoperative lung resection patients with BPF who are good surgical candidates, surgical repair is a definitive therapy with excellent success if spontaneous closure is unlikely.
- Bronchoscopic fistula closure is appropriate for patients with BPF who are poor surgical candidates, those who need a bridge to surgery, or patients with BPF due to advanced malignancy.
- Bronchoscopic approaches have variable success rates but are typically more successful in those with small fistulas of less than 8 mm.
- Following fistula closure, patients should be monitored for clinical symptoms of recurrence with chest tube output and chest imaging.
- For patients who fail surgical or bronchoscopic intervention, options include repeat surgery, an alternate bronchoscopic method, or an open window thoracostomy such as Eloesser flap thoracostomy or a Claggett window.
- Enhancing Healthcare Team Outcomes
BPF is one of the most severe complications after thoracic surgery, and no effective prophylactic procedure is available. Evidence for buttressing the bronchial stump leading to a reduction in the incidence of a bronchopleural fistula is conflicting. Level 1b evidence exists that an intercostal flap reduces the risk of BPF in people with diabetes. Thoracic surgeons should consider coverage of the bronchial stump by an intercostal muscle pedicle flap in patients at high risk of BPF.
In a prospective randomized controlled trial of pneumonectomy patients with diabetes mellitus, Sfyridis et al. reported that intercostal muscle flap coverage was effective. [46] Sfyridis et al. performed a randomized controlled trial on 70 patients with diabetes undergoing pneumonectomy. [46] Patients were randomized 1:1 to either intercostal muscle flap reinforcement or no flap coverage; results revealed a significant reduction in BPF risk and empyema in patients with a flap.
Deschamps et al. analyzed 713 pneumonectomy patients. [47] Univariate analysis revealed bronchial stump reinforcement was associated with an increased incidence of BPF. Surgeons utilized multiple techniques for flap coverage - including a combination of muscle flaps, parietal pleura, and pericardium, serratus anterior, and latissimus dorsi. Hamad et al. report a series of 50 patients undergoing bronchial stump coverage with pericardium following extrapleural pneumonectomy for malignant mesothelioma. [48] Although two patients died secondary to cardiac complications, leading to 4% perioperative mortality, there were no cases of BPF. Lastly, Lardinois et al. conducted a non-randomized comparison study of 26 patients undergoing either intercostal muscle or diaphragm flaps (DF). [49] Thirty-day mortality was zero in both groups. There was a higher incidence of complications, including pneumonia, atelectasis, herniation, and BPF in the DF group, 38% versus 8% in the intercostal muscle flap group. Both methods were deemed effective by the authors.
An interprofessional team of the thoracic surgeon, intensivist, and critical care nurse will improve outcomes. Providers must be vigilant for signs and symptoms described above. Rapid recognition and treatment will decrease mortality and morbidity. Specialty trained nurses monitor patients and report status changes back to the team. [Level 5]
- Review Questions
- Access free multiple choice questions on this topic.
- Comment on this article.
Disclosure: Irim Salik declares no relevant financial relationships with ineligible companies.
Disclosure: Rishik Vashisht declares no relevant financial relationships with ineligible companies.
Disclosure: Apolonia Abramowicz declares no relevant financial relationships with ineligible companies.
This book is distributed under the terms of the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0) ( http://creativecommons.org/licenses/by-nc-nd/4.0/ ), which permits others to distribute the work, provided that the article is not altered or used commercially. You are not required to obtain permission to distribute this article, provided that you credit the author and journal.
- Cite this Page Salik I, Vashisht R, Abramowicz AE. Bronchopleural Fistula. [Updated 2023 May 1]. In: StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2024 Jan-.
In this Page
Bulk download.
- Bulk download StatPearls data from FTP
Related information
- PMC PubMed Central citations
- PubMed Links to PubMed
Similar articles in PubMed
- Therapeutic closure of bronchopleural fistulas using ethanol. [Ther Adv Respir Dis. 2021] Therapeutic closure of bronchopleural fistulas using ethanol. Abramian O, Rosenheck J, Taddeo-Kolman D, Bowen F, Boujaoude Z, Abouzgheib W. Ther Adv Respir Dis. 2021 Jan-Dec; 15:17534666211044411.
- Conservative management of postoperative bronchopleural fistulas. [J Thorac Cardiovasc Surg. 2013] Conservative management of postoperative bronchopleural fistulas. Boudaya MS, Smadhi H, Zribi H, Mohamed J, Ammar J, Mestiri T, Kilani T. J Thorac Cardiovasc Surg. 2013 Sep; 146(3):575-9. Epub 2013 Jun 28.
- [Omentum Transplantation in Thorax to Cover Bronchial Stump as Treatment of Bronchopleural Fistula After Pulmonary Resection: Report of 6 Cases' Experience]. [Zhongguo Fei Ai Za Zhi. 2018] [Omentum Transplantation in Thorax to Cover Bronchial Stump as Treatment of Bronchopleural Fistula After Pulmonary Resection: Report of 6 Cases' Experience]. Yang X, Yang X, Xie T, Hu B, Li Q. Zhongguo Fei Ai Za Zhi. 2018 Mar 20; 21(3):235-238.
- Review Bronchopleural fistulas: an overview of the problem with special focus on endoscopic management. [Chest. 2005] Review Bronchopleural fistulas: an overview of the problem with special focus on endoscopic management. Lois M, Noppen M. Chest. 2005 Dec; 128(6):3955-65.
- Review Does postoperative mechanical ventilation predispose to bronchopleural fistula formation in patients undergoing pneumonectomy? [Interact Cardiovasc Thorac Sur...] Review Does postoperative mechanical ventilation predispose to bronchopleural fistula formation in patients undergoing pneumonectomy? Toufektzian L, Patris V, Sepsas E, Konstantinou M. Interact Cardiovasc Thorac Surg. 2015 Sep; 21(3):379-82. Epub 2015 Jun 11.
Recent Activity
- Bronchopleural Fistula - StatPearls Bronchopleural Fistula - StatPearls
Your browsing activity is empty.
Activity recording is turned off.
Turn recording back on
Connect with NLM
National Library of Medicine 8600 Rockville Pike Bethesda, MD 20894
Web Policies FOIA HHS Vulnerability Disclosure
Help Accessibility Careers
Help | Advanced Search
Computer Science > Cryptography and Security
Title: brf: ebpf runtime fuzzer.
Abstract: The eBPF technology in the Linux kernel has been widely adopted for different applications, such as networking, tracing, and security, thanks to the programmability it provides. By allowing user-supplied eBPF programs to be executed directly in the kernel, it greatly increases the flexibility and efficiency of deploying customized logic. However, eBPF also introduces a new and wide attack surface: malicious eBPF programs may try to exploit the vulnerabilities in the eBPF subsystem in the kernel. Fuzzing is a promising technique to find such vulnerabilities. Unfortunately, our experiments with the state-of-the-art kernel fuzzer, Syzkaller, shows that it cannot effectively fuzz the eBPF runtime, those components that are in charge of executing an eBPF program, for two reasons. First, the eBPF verifier (which is tasked with verifying the safety of eBPF programs) rejects many fuzzing inputs because (1) they do not comply with its required semantics or (2) they miss some dependencies, i.e., other syscalls that need to be issued before the program is loaded. Second, Syzkaller fails to attach and trigger the execution of eBPF programs most of the times. This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem. Our experiments show, in 48-hour fuzzing sessions, BRF can successfully execute 8x more eBPF programs compared to Syzkaller. Moreover, eBPF programs generated by BRF are much more expressive than Syzkaller's. As a result, BRF achieves 101% higher code coverage. Finally, BRF has so far managed to find 4 vulnerabilities (some of them have been assigned CVE numbers) in the eBPF runtime, proving its effectiveness.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Open Access is an initiative that aims to make scientific research freely available to all. To date our community has made over 100 million downloads. It’s based on principles of collaboration, unobstructed discovery, and, most importantly, scientific progression. As PhD students, we found it difficult to access the research we needed, so we decided to create a new Open Access publisher that levels the playing field for scientists across the world. How? By making research easy to access, and puts the academic needs of the researchers before the business interests of publishers.
We are a community of more than 103,000 authors and editors from 3,291 institutions spanning 160 countries, including Nobel Prize winners and some of the world’s most-cited researchers. Publishing on IntechOpen allows authors to earn citations and find new collaborators, meaning more people see your work not only from your own field of study, but from other related fields too.
Brief introduction to this section that descibes Open Access especially from an IntechOpen perspective
Want to get in touch? Contact our London head office or media team here
Our team is growing all the time, so we’re always on the lookout for smart people who want to help us reshape the world of scientific publishing.
Home > Books > Diseases of Pleura
Bronchopleural Fistula: Causes, Diagnoses and Management
Submitted: 19 February 2019 Reviewed: 18 June 2019 Published: 06 August 2019
DOI: 10.5772/intechopen.88127
Cite this chapter
There are two ways to cite this chapter:
From the Edited Volume
Diseases of Pleura
Edited by Jelena Stojšić
To purchase hard copies of this book, please contact the representative in India: CBS Publishers & Distributors Pvt. Ltd. www.cbspd.com | [email protected]
Chapter metrics overview
1,677 Chapter Downloads
Impact of this chapter
Total Chapter Downloads on intechopen.com
Total Chapter Views on intechopen.com
Overall attention for this chapters
Bronchopleural fistula (BPF) is a pathological communication between the bronchial tree and pleural space. This clinical condition, which has high mortality and morbidity, is one of the major therapeutic challenges for clinicians even today. BPF may result from a lung neoplasm, necrotizing pneumonia, empyema, blunt and penetrating lung injuries, and a complication of surgical procedures. Lung resection is the most common cause of BPF, and this chapter will focus more on this topic. Frequency ranges from 4.5 to 20% after pneumonectomy and from 0.5 to 1% after lobectomy. Several risk factors have been defined in the development of postoperative BPF; preoperative radiotherapy, pulmonary infection, diabetes, right pneumonectomy, a long bronchial stump, residual cancer at the stump (R1 and R2 resection), and the need for postoperative ventilation (especially with high PEEP). BPFs are divided, based on the time elapsed since surgery, into early or late fistula. This grouping is important in management of patient treatment. In early BPF, surgical treatment is generally the preferred treatment modality, whereas in late BPF, conservative approach is preferred. The management of BPF is still one of the most complex challenges encountered by the thoracic surgeons; so prevention is the best way to manage postoperative BPF.
- bronchopleural fistula
- complication
- lung resection
Author Information
Güntuğ batıhan *.
- Department of Thoracic Surgery, Dr Suat Seren Chest Diseases and Surgery Medical Practice and Research Center, University of Health Sciences, Izmir, Turkey
Kenan Can Ceylan
*Address all correspondence to: [email protected]
1. Introduction
Bronchopleural fistula (BPF) has been defined as a direct communication between the bronchus and pleural cavity. Some authors have grouped BPFs as central and peripheral according to their locations [ 1 ]. While a central BPF defines connection between pleura and tracheobronchial three, a peripheral BPF defines connection between the pleura and airway distal to segmental bronchi or lung parenchyma. In literature, the term of “alveolopleural fistula” is also used to describe peripheral BPFs.
Nonsurgical conditions like trauma, chronic necrotizing pneumonia, empyema, radiotherapy, bulla, or cyst rupture can cause BPF, but the most common cause is lung resection. Frequency ranges from 4.5 to 20% after pneumonectomy and from 0.5 to 1% after lobectomy. BPF-related mortality ranges from 18 to 71% in the literature [ 2 , 3 , 4 ]. Because of high morbidity and mortality rates, it is important to define risk factors and apply preventative methods especially in groups of risky patients.
Many authors have divided postoperative BPFs into two groups according to time of onset. There is no consensus about these definitions in the literature, but generally, early BPF was defined as fistula occurring within 30 days after the initial operation. Late BPF was defined as fistulas occurring after more than 30 days. It is established that early BPFs are most commonly associated with a failure in surgical technique and mostly, it can be repaired with reoperation [ 1 , 3 , 5 ].
Late BPFs are typically secondary to patient-related factors and almost always coexist with empyema, and it usually required complex, long-term, and exhausting treatment process for both the patient and the surgeon.
2. Risk factors
BPF is most commonly encountered after lung resections; therefore, establishing risk factors is important to prevent patients from this highly mortal complication.
Numerous risk factors have been associated with BPF development in the literature [ 3 , 4 , 5 , 6 ]. We divided these risk factors into three groups: patient-related factors, surgeon-related factors, and anatomic factors.
Age (>60), gender (male), neoadjuvant radiation therapy, diabetes mellitus, malnutrition, smoking, chronic steroid/immunosuppressive usage, and need for postoperative mechanic ventilation can be classified as a patient-related risk factor. Induction chemotherapy has been cited as a risk factor for postpneumonectomy BPF but there is not any increased risk for bronchoplastic procedures.
A large number of studies have reported an increased risk for BPF due to postoperative mechanical ventilation usage after pneumonectomy. Therefore, to prevent bronchial stump from barotrauma extubation must be achieved at the earliest time after surgery.
A low forced expiratory volume in 1 second and low carbon monoxide diffusing capacity were also defined as risk factors for postoperative BPF occurrence.
According to cadaveric studies, presence of two left-sided and one right-sided bronchial artery supply is the most common configuration.
While the left main bronchus is protected under the aortic arch and surrounded by mediastinal tissue, the right bronchial stump has no such coverage.
The right main bronchus is wider, and more vertical than the left main bronchus. This condition facilitates secretion retention on the right main bronchial stump.
Early BPFs are usually related with technical failure during surgery. The most common causes of this condition are poorly secured knots, stapler misfiring, and high anastomotic tension. Other surgeon-related risk factors are extensive mediastinal lymphadenectomy and peribronchial dissection, long bronchial stump and not coverage the bronchial stump with viable tissue.
3. Clinical presentations and diagnosis
The size and the time of occurrence of the BPF are major determinants of the clinical presentation but, patients often have infection-related symptoms like: fever, cough with serosanguinous or purulent sputum, night sweats, and chills.
Expectoration and respiratory symptoms typically worsen with the patient lying on the side opposite to the one involving the fistula. Flooding of the infected contents of the pleural space to the contralateral lung can lead to severe pneumonia or respiratory distress syndrome.
If the patient has a chest tube massive and prolonged air leakage would be an important clinical clue for BPF.
White blood cell count and systemic inflammation markers are often elevated.
Chest radiogram often revealed a decrease in the fluid level and enlargement in the ipsilateral pleural cavity. Due to the contamination of the contralateral lung by the infected content of the pleural cavity, parenchymal infiltration can be seen.
Computed tomography of the chest can depict mediastinal emphysema, parenchymal infiltration, and enlargement of the pleural cavity, but its success at demonstrating the presence of the BPF is controversial. By the imaging of the continuation of a bronchus or the lung parenchyma to the pleural space, definitive diagnosis of the fistula can be made ( Figures 1 and 2 ). Westcott et al. reported sensitivity of the chest CT as 50% at demonstrating the presence of the peripheral BPFs. Seo et al. reported that chest CT succeed to demonstrate direct or indirect signs of BPF 86% of the patients with central, and 100% of the patients with peripheral BPFs [ 7 , 8 ].

Left sided BPF is seen in the Chest CT. BPF may not always be as clear as this CT image.

Another chest CT image shows right sided BPF. Chest CT also allows the examination of the remaining lung for possible pneumonic infiltrations and metastases.
In the presence of clinical or radiological suspicion of BPF, bronchoscopy must be applied to examine the bronchial stump. Presence of pleural fluid leakage or/and air bubbling in the bronchial stump is pathognomonic ( Figures 3 and 4 ).

Bronchoscope view of the left-sided BPF (arrow) (Asterix shows the main carina). In bronchoscopy, the fistula patency may not always be clearly seen. Air bubbles originating from the stump of the bronchus may be the only sign of the BPF.

Bronchoscope view of the right-sided BPF (arrow) (Asterix shows the main carina).
Reconstruction of 2-dimensional, helical CT images provides noninvasive intraluminal evaluation of the bronchus named as “virtual bronchoscopy” [ 9 ]. This technique can provide additional benefits, especially, planning endobronchial instrumentation, but it is not an essential diagnostic method of fistula.
Less frequently 133 xenon or 99 technetium ventilation scintigraphy can be used to identify BPF by visualization of the radioactive isotopes in the empty pleural cavity. Mark et al. used 99 technetium ventilation scintigraphy in 28 postpneumonectomy patients for the detection of BPF and reported sensitivity of 78% and a specificity of 100% [ 10 , 11 ]. Although, this is a noninvasive diagnostic procedure, it is not practical and easy-to-use, and has no additional benefit to the detection of underlying lung disease.
4. Management
The management of the BPF needs prolonged hospitalization, complex surgical procedures, and close follow-up, but first step in the treatment is management of the life-threatening conditions like sepsis, tension pneumothorax, and respiratory failure. Protection of the contralateral lung from aspiration of the pleural fluid is important to reduce the risk of pneumonia and respiratory failure. Therefore, chest tube must be applied to ensure the drainage of the pleural cavity. Broad spectrum antibiotic therapy against Gram-Positive, Gram-Negative, and anaerobic microorganisms must be initiated, and it should be tailored based on the results of culture-antibiograms.
Early BPFs are mostly associated with failure in the surgical technique. Repairment of the bronchial stump with re-operation is the best treatment modality in these patients.
Patients with late BPF mostly have poor medical condition and major surgical approaches cannot be applied. Conservative treatment modalities like drainage and reduction of the pleural space, pleural irrigation, antibiotics, and nutritional supplementation. Boudaya et al. reported their experience with conservative management of postresectional BPF in 17 patients and BPF is successfully closed in 16 patients [ 12 ].
Various endoscopic techniques for the control of small BPFs have been reported, especially in patients with poor condition. Sealants, fibrin glue, coils, and endobronchial silicon or metal stents have been used to treat small BPFs (ranging from 0.8 to 1.0 mm). Dutau et al. used self-expanding metal stents in seven patients with large fistulas (>6 mm) and reported improvement in patients’ respiratory parameters in early postoperative period [ 13 ].
4.1 Surgical interventions for infection control
Besides conservative treatments, several surgical procedures to treat BPFs have been defined in the literature. Main objectives in these surgical interventions are debridement of the pleural space, minimizing the residual pleural cavity, closure of the fistula, and reinforcement of the bronchial stump with autologous tissue.
Medical condition of the patient
Time of onset of the fistula
Size and localization of the fistula
State of the pleural cavity
4.1.1 Video-assisted thoracoscopic surgery (VATS)
In the presence of pleural infection together with the fistula, tube-thoracostomy must be applied in all cases. Pleural irrigation with antibiotic and povidone-iodine solutions is suggested in sterilization of the infected postpneumonectomy pleural cavity but this treatment modality alone cannot provide sufficient debridement, especially in patients with late fistulas and cause prolong hospitalization.
VATS is a useful method to obtain drainage and debridement of the infected pleural cavity. Single port is usually sufficient in most cases; material and debris can be safely removed with surgical instruments and in the presence of small BPFs (<3 mm) fibrine glue can be applied. Hollaus et al. applied videothoracoscopic debridement in nine patients and defined it as an efficient method to treat postpneumonectomy empyema [ 14 ]. Gossot et al. reported series of 11 patients with postpneumonectomy empyema. These 11 patients underwent videothoracoscopic debridement and 8 of 11 patients discharged without need of additional surgical procedures [ 15 ]. These similar studies have shown that VATS is a feasible option for treatment in select patients with PPE and small BPF.
4.1.2 Open window thoracostomy
Segmental resection of 2–3 ribs
Creation of a skin flap (Muscle should be preserved if possible)
Marsupialization of the cavity
With this procedure, epithelialized thoracostomy window is obtained and effective drainage is ensured.
After this operation, the wound is packed at least daily with gauze moistened with normal saline. Granulation tissue in the wound begins to form over time and when the pleural space is clean closure of the window can be considered.
It is very important to have a good cooperation with patient and relatives for this treatment modality and they should be informed that this treatment procedure may require several weeks.
4.1.3 Clagett procedure
Clagett and Geraci described a two-step treatment technique for the management of postpneumonectomy empyema in 1963 [ 18 ]. Step 1 contains the open window thoracostomy to drain the septic cavity. Step 2 contains obliteration of the pleural cavity with antibiotic solution. Pairolero and Arnold has modified this procedure and described transposition of a well-vascularized extrathoracic muscle as an intermediate step [ 19 ]. With this modification, further reinforcement of the bronchial stump was ensured.
Clagett procedure shows a success rate (OWT closed without PPE recurrence) of 61–89% with a mortality rate between 0 and 24% in the literature.
4.2 Surgically closure of a bronchopleural fistula
Large BPF can cause loss in the tidal volume, aspiration of infected pleural fluid, and respiratory distress. Therefore, bronchial defect must be controlled, especially in patients with large fistulas, for this purpose, two major approaches were defined in the literature.
4.2.1 Transpleural approach
Transpleural approach is the most common method to closure of the BPF ( Figure 5 ). First, BPF must be identified. By careful dissection, bronchus must be mobilized as close to the carina as possible to provide adequate length. Aggressive dissection and devascularization of the proximal bronchus should be avoided because of the risk of failure of the repair and recurrence of BPF. Stapler devices can be used if there is a sufficient length in the bronchial stump. Manual suturation also can be applied above the BPF. After repairment, bronchial stump must be buttressed with well-vascularized tissue such as extrathoracic muscle, omentum, or diaphragm flap.

Image of the left thoracic cavity of the patient with BPF and empyema. Pleural debris and plaques covering the chest wall are seen (Asterix). Infected vascular stumps also are seen (arrow).
4.2.2 Transsternal transpericardial approach
In some cases, surgical management of BPF may be challenging through a lateral transpleural approach. Presence of short bronchial stumps, left-sided BPF, necrotic bronchial stumps and/or history of prior BPF closures via thoracotomy are the main reasons that make transpleural approach difficult. In these cases, transsternal transpericardial approach would be a good alternative to transpleural approach [ 20 , 21 ]. This approach provides work in healthy, inflammation-free planes. Therefore, in this technique, isolation of the airway is easier and safer than others. Biggest benefit of this technique is that it provides the opportunity to work in a healthy plane. Retraction of the superior vena cava and aorta laterally provide sufficient exposure to make a successful repairment. It is also possible to achieve transpericardial approach by anterior thoracic incision with division of multiple costal cartilages which was described by Padhi and Lynn [ 22 ]. This approach was found to be a difficult and complicated compared to transsternal approach. Therefore, transsternal transpericardial approach has become more widely used among surgeons in the repairment of BPF.
4.2.3 Thoracoplasty
One of the major concerns in the treatment of the BPF is obliteration of the persistent space after control of pleural infection. Thoracoplasty is originally considered as a treatment for active tuberculosis but this procedure is also functional for obliterate pleural space with the viable tissue of the chest wall in the cases of BPF. This is achieved by resection of multiple ribs. Traditional thoracoplasty requires removal of the first 11 ribs periosteum, and intercostal muscles with associated neurovascular bundles. After removal of these structures, skin and thoracic muscles fill the pleural cavity. As can be expected, this procedure has high mortality and morbidity rates and is now abandoned. Removing fewer than five ribs named as “tailored” thoracoplasty is still in use especially in the treatment of chronic BPFs [ 23 , 24 ].
It would be rational to use these treatment modalities in combination to deal with space problem. Tailored thoracoplasty, muscle transposition, omentoplasty, and diaphragm flabs can be used and combined with each other. Clinical condition and performance status of the patient are also important for selection of the best method in the treatment of BPF.
5. Bronchoscopic management of BPF
Various endoscopic techniques like bronchoscopic application of sealants, fibrin glue, silver nitrate cautery, coils, and endobronchial stents for the control of small BPFs have been reported [ 25 , 26 , 27 , 28 , 29 ]. There is no consensus on which method is most effective for BPF closure. We use endoscopic techniques only for the patients with poor clinical condition and not for proper major surgical intervention. Proper technique must be selected depending on the length of the bronchial stump, the location, and size of the fistula ( Figures 6 and 7 ).

Image of the customized (closed in one side with a stapler) silicone stent.

Left-sided BPF was closed with customized silicone stent. After this procedure, air drainage from the chest tube was decreased and respiratory condition of the patient was improved.
We often prefer metallic J-stents and silicon Y-stents ( Figure 8 ). The most seen complication of these stents is migration and occlusion with secretion. Migration and occlusion of the stent can cause severe respiratory distress. Retention of the secretion can also cause contamination of the remaining lung and resulted in severe pneumonia.

Bronchoscope image of the right-sided BPF. It was closed with self-expandable metallic stent.
Despite these complications, in selected patients, endobronchial stents can reduce air leakage and prevent remaining lung from contamination with pleural fluid.
6. Prevention of bronchopleural fistula in pulmonary resection-bronchial stump coverage
To prevent postpneumonectomy bronchopleural fistula, coverage of the bronchial stump is recommended, especially for patients with high risk of BPF.
Pedicled intercostal and extrathoracic muscles, diaphragm, pericardium, pericardial fat pad, and pleura can be used to make a flap to coverage the bronchial stump [ 30 , 31 , 32 ]. There is no consensus for best bronchial stump coverage method and related techniques with several complications were defined in the literature. Diaphragm flaps can cause visceral herniation. The pedicled intercostal muscle flap is useful method for coverage of the bronchial stump but developing heterotopic ossification can cause severe problems. Omentum is a great tissue to promote re-vascularization and healing of the bronchial stump but it requires the opening of the abdominal cavity [ 33 ]. Pericardial fat pad coverage appears to be safe and feasible when compared with other coverage techniques ( Figures 9 and 10 ). It can be applied without risk of additional comorbidity and composes a mechanical barrier between bronchial stump and pleural cavity.

Pericardial fat pad (Asterix) is very useful material to coverage of the bronchial stump. It is dissected from surrounding tissues by preserving the vascular pedicle. Once the fat pad has been mobilized, it is then rotated over the hilum to cover the bronchial staple line (arrows).

The view of the thoracic cavity after coverage of the left main bronchial stump.
7. Conclusion
In modern thoracic surgery, bronchopleural fistula is still associated with significant morbidity and mortality. Treatment techniques have evolved and there are many options to use in patients with BPF, therefore surgeon must evaluate clinical status of the patient, the size, and location of the BPF and the status of the pleural cavity to select the treatment method that will show the most benefit.
It is important to remember that the best treatment is to prevent the disease. Therefore, rigorous surgical technique and bronchial stump coverage are the main steps in the treatment.
Conflict of interest
The authors declare no conflict of interest.
Appendices and nomenclature
- 1. Okuda M, Go T, Yokomise H. Risk factor of bronchopleural fistula after general thoracic surgery: Review article. General Thoracic and Cardiovascular Surgery. Dec 2017; 65 (12):679-685. DOI: 10.1007/s11748-017-0846-1. [Epub 2017 Oct 12]
- 2. Deschamps C, Bernard A, Nichols FC 3rd, et al. Empyema and bronchopleural fistula after pneumonectomy: Factors affecting incidence. The Annals of Thoracic Surgery. 2001; 72 :243-247 [discussion: 248]
- 3. Pforr A, Pages PB, Baste JM, et al. A predictive score for bronchopleural fistula established using the French database EPITHOR. The Annals of Thoracic Surgery. 2016; 101 :287-293
- 4. Wright CD, Wain JC, Mathisen DJ, et al. Postpneumonectomy bronchopleural fistula after sutured bronchial closure: Incidence, risk factors, and management. The Journal of Thoracic and Cardiovascular Surgery. 1996; 112 :1367-1371
- 5. Asamura H, Naruke T, Tsuchiya R, et al. Bronchopleural fistulas associated with lung cancer operations. Univariate and multivariate analysis of risk factors, management, and outcome. The Journal of Thoracic and Cardiovascular Surgery. 1992; 104 :1456-1464
- 6. Martin J, Ginsberg RJ, Abolhoda A, et al. Morbidity and mortality after neoadjuvant therapy for lung cancer: The risks of right pneumonectomy. The Annals of Thoracic Surgery. 2001; 72 :1149-1154
- 7. Wescott JL, Volpe JP. Peripheral bronchopleural fistula: CT evaluation in 20 patients with pneumonia, emphyema, or postoperative air leak. Radiology. 1995; 196 :175-181
- 8. Seo H, Kim TJ, Jin KN, Lee KW. Multi-detector row computed tomography evaluation of bronchopleural fistula: Correlation with clinical, bronchoscopic, and surgical findings. Journal of Computer Assisted Tomography. 2010; 34 :13-18
- 9. Gaur P, Dunne R, Colson Y, Gill R. Bronchopleural fistula and the role of contemporary imaging. The Journal of Thoracic and Cardiovascular Surgery. 2013; 148 . DOI: 10.1016/j.jtcvs.2013.11.009
- 10. Nielsen KR, Blake LM, Mark JB, DeCampli W, McDougall IR. Localization of bronchopleural fistula using ventilation scintigraphy. Journal of Nuclear Medicine. 1994; 35 :867-869
- 11. Raja S, Rice TW, Neumann DR, Saha GB, Khandekar S, MacIntyre WJ, et al. Scintigraphic detection of post-pneumonectomy bronchopleural fistulae. European Journal of Nuclear Medicine. 1999; 26 :215-219
- 12. Boudaya MS, Smadhi H, Zribi H, et al. Conservative management of postoperative bronchopleural fistulas. The Journal of Thoracic and Cardiovascular Surgery. 2013; 146 :575-579
- 13. Dutau H, Breen DP, Gomez C, et al. The integrated place of tracheobronchial stents in the multidisciplinary management of large post-pneumonectomy fistulas: Our experience using a novel customised conical self-expandable metallic stent. European Journal of Cardio-Thoracic Surgery. 2011; 39 :185-189. DOI: 10.1016/j.ejcts.2010.05.020
- 14. Hollaus PH, Lax F, Wurnig PN, et al. Videothoracoscopic debridement of the postpneumonectomy space in empyema. The European Journal of Cardio-Thoracic Surgery. 1999; 16 :283-286
- 15. Gossot D, Stern JB, Galetta D, et al. Thoracoscopic management of postpneumonectomy empyema. The Annals of Thoracic Surgery. 2004; 78 :273-276
- 16. Robinson S. The treatment of chronic non-tuberculous empyema. Surgery, Gynecology & Obstetrics. 1916; 64
- 17. Eloesser L. An operation for tuberculous empyema. Surgery, Gynecology & Obstetrics. 1935; 60 :1096-1097
- 18. Clagett OT, Geraci JE. A procedure for the management of postpneumonectomy empyema. The Journal of Thoracic and Cardiovascular Surgery. 1963; 45 :141-145
- 19. Pairolero PC, Arnold PG, Trastek VF, et al. Postpneumonectomy empyema. The role of intrathoracic muscle transposition. The Journal of Thoracic and Cardiovascular Surgery. 1990; 99 :958-966 [discussion: 966-8]
- 20. Deschamps C, Allen MS, Miller DL, et al. Management of postpneumonectomy empyema and bronchopleural fistula. Seminars in Thoracic and Cardiovascular Surgery. 2001; 13 :13-19
- 21. Abruzzini P. Trattamento chirurgico delle fistole del bronco principale consecutive a pneumonectomia per tubercolosi. Chirur Torac. 1961; 14 :165-171
- 22. Padhi RK, Lynn RB. The management of bronchopleural fistulas. The Journal of Thoracic and Cardiovascular Surgery. 1960; 39 :385-393
- 23. Goldstraw P. Treatment of postpneumonectomy empyema: The case for fenestration. Thorax. 1979; 34 :740-745
- 24. Estlander JA. Sur le resection des cotes dans l’empyeme chronique. The Medico-Chirurgical Review. 1891; 8 :885-888
- 25. Lois M, Noppen M. Bronchopleural fistulas: An overview of the problem with special focus on endoscopic management. Chest. 2005; 128 :3955-3965
- 26. Jones NC, Kirk AJ, Edwards RD. Bronchopleural fistula treated with a covered wallstent. The Annals of Thoracic Surgery. 2006; 81 :364. DOI: 10.1016/j.athoracsur.2004.09.054
- 27. Klotz LV, Gesierich W, Schott-Hildebrand S, et al. Endobronchial closure of bronchopleural fistula using Amplatzer device. Journal of Thoracic Disease. 2015; 7 :1478-1482
- 28. Hamid UI, Jones JM. Closure of a bronchopleural fistula using glue. Interactive Cardiovascular and Thoracic Surgery. 2011; 13 :117-118. DOI: 10.1510/icvts.2011.270397
- 29. Amaral B, Feijó S. Fistula of the stump: A novel approach with a “stapled” stent. Journal of Bronchology and Interventional Pulmonology. 2015; 22 :365-366. DOI: 10.1097/LBR.0000000000000172
- 30. Klepetko W, Taghavi S, Pereszlenyi A, et al. Impact of different coverage techniques on incidence of postpneumonectomy stump fistula. European Journal of Cardio-Thoracic Surgery. 1999; 15 :758-763
- 31. Anderson TM, Miller JI Jr. Use of pleura, azygos vein, pericardium, and muscle flaps in tracheobronchial surgery. The Annals of Thoracic Surgery. 1995; 60 :729-733
- 32. Anderson TM, Miller JI Jr. Surgical technique and application of pericardial fat pad and pericardiophrenic grafts. The Annals of Thoracic Surgery. 1995; 59 :1590-1591
- 33. Okumura Y, Takeda S, Asada H, et al. Surgical results for chronic empyema using omental pedicled flap: Long-term follow-up study. The Annals of Thoracic Surgery. 2005; 79 :1857-1861. DOI: 10.1016/j.athoracsur.2005.01.001
© 2019 The Author(s). Licensee IntechOpen. This chapter is distributed under the terms of the Creative Commons Attribution 3.0 License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Continue reading from the same book
Published: 04 March 2020
By Alberto Sandri, Alessandro Maraschi, Matteo Gaglia...
981 downloads
By Jelena Stojšić
924 downloads
By Vita Dolzan and Alenka Franko
1024 downloads
Subscribe to the PwC Newsletter
Join the community, edit social preview.

Add a new code entry for this paper
Remove a code repository from this paper, mark the official implementation from paper authors, add a new evaluation result row, remove a task, add a method, remove a method, edit datasets, brf: ebpf runtime fuzzer.
15 May 2023 · Hsin-Wei Hung , Ardalan Amiri Sani · Edit social preview
The eBPF technology in the Linux kernel has been widely adopted for different applications, such as networking, tracing, and security, thanks to the programmability it provides. By allowing user-supplied eBPF programs to be executed directly in the kernel, it greatly increases the flexibility and efficiency of deploying customized logic. However, eBPF also introduces a new and wide attack surface: malicious eBPF programs may try to exploit the vulnerabilities in the eBPF subsystem in the kernel. Fuzzing is a promising technique to find such vulnerabilities. Unfortunately, our experiments with the state-of-the-art kernel fuzzer, Syzkaller, shows that it cannot effectively fuzz the eBPF runtime, those components that are in charge of executing an eBPF program, for two reasons. First, the eBPF verifier (which is tasked with verifying the safety of eBPF programs) rejects many fuzzing inputs because (1) they do not comply with its required semantics or (2) they miss some dependencies, i.e., other syscalls that need to be issued before the program is loaded. Second, Syzkaller fails to attach and trigger the execution of eBPF programs most of the times. This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem. Our experiments show, in 48-hour fuzzing sessions, BRF can successfully execute 8x more eBPF programs compared to Syzkaller. Moreover, eBPF programs generated by BRF are much more expressive than Syzkaller's. As a result, BRF achieves 101% higher code coverage. Finally, BRF has so far managed to find 4 vulnerabilities (some of them have been assigned CVE numbers) in the eBPF runtime, proving its effectiveness.
Code Edit Add Remove Mark official
Datasets edit.

IMAGES
VIDEO
COMMENTS
In this case, the frequency band (ω2 −ω1) ( ω 2 − ω 1) is called the rejection band. The Band rejection filter is also called the band stop filter (BSF) or band-elimination filter (BEF). The phase function of an ideal band rejection filter is θ(ω) = −ωtd θ ( ω) = − ω t d. And the transfer function of an ideal band rejection ...
The de nition of \ideal" depends on your application. Let's start with the task of lowpass ltering. Let's de ne an ideal lowpass lter, Y (!) = LI (!)X(!), as follows: (X(!) where !L is some cuto frequency that we choose. For example, to de-noise a speech signal we might choose !L = 2 2400=Fs, because most speech energy is below 2400Hz.
What is active filter, types of active filters using op-amp (Active RC filters) - Low pass filter, High pass filter, Wide band pass filter, Narrow band pass ...
The narrow band reject filter, often called the notch filter, is commonly used for the attenuation of a single frequency. For example, it may be necessary to attenuate 60 Hz or 400 Hz noise or hum signals in a circuit. The most commonly used notch filter is the Twin T network, shown in Fig. 15.21 (a), which is a passive filter composed of two ...
The formula for passive bandpass filter calculator is shown below. Passive Band Pass Filter Calculator. For low cut off frequency = 1/2∏R2C2. For high cut off frequency = 1/2∏R1C1. Similarly, we can calculate for active inverting op-amp BPF, and active non-inverting op-amp BPF.
There are four types of RF filters viz. lowpass filter (LPF),Highpass filter (HPF),Bandpass filter (BPF) and Bandstop filter (BSF). Filters are categorized into active filter and passive filter. They are also categorized into analog filters and digital filters. The electronic circuit which changes amplitude and phase angle of electrical signal ...
This is the seventh lecture on Electric circuits for Electrical engineering. It is about Filters - LOW PASS FILTERS, HIGH PASS FILTERS, BANDPASS FILTERS, BA...
Calculation of Transfer Function/Gain/Cutoff Frequency and Frequency Response
Once loaded into the in-kernel BPF virtual machine, XDP programs are hooked from userspace into the kernel network path thanks to a Netlink command. On reception, the function dev_change_xdp_fd () in file linux/net/core/dev.c is called and sets a XDP hook. Such hooks are located in the drivers of supported NICs.
The algorithm has a simple implementation involving N+1 spatial filterings, where N is the approximation order. We give a detailed analysis of the filtering accuracy that can be achieved by the proposed approximation in relation to the target bilateral filter. This allows us to estimate the order N required to obtain a given accuracy.
BPF. BRF. BiQuad. ResonZ. OnePole. OneZero. TwoPole. TwoZero. PoleZero. Basic filter unit generators. FilterBasic inherits: UGen: Object. ... BRF Default constructor for BRF. member functions. float Q (float val) Set filter resonance. float Q Get filter resonance. float freq (float val) Set filter center frequency.
INTRODUCTION. A pathologic connection between the main stem, lobar, or segmental bronchus and the pleural space is termed bronchopleural fistula (BPF). It is a source of morbidity and mortality in patients, particularly those who undergo lung resection. This topic will review the etiologies, diagnosis, and treatment of patients with BPF.
This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies re-quired by the verifier and the eBPF subsystem. Our experi-ments show, in 48-hour fuzzing sessions, BRF can success-fully execute 8 more eBPF programs compared to Syzkaller. Moreover, eBPF programs generated by BRF are much more
All-solid-state tunable lasers have been widely used in many fields including multi-photon microscopy, time-resolved photoluminescence, atomic physics, and so on owing to their broadband output spectrum range, good beam quality, and low noise. To cover the broad fluorescent line of the laser crystal as much as possible, a birefringent filter (BRF) is always the most popular candidate for ...
Bronchopleural fistula (BPF) is a sinus tract between the main stem, lobar, or segmental bronchus and the pleural space. It can be a potentially catastrophic complication following pneumonectomy or other pulmonary resection. Morbidity ranges between 25% and 71%, and diagnosis and management is often a challenge for physicians.[1] Other common causes of BPF include pulmonary infection causing ...
About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features NFL Sunday Ticket Press Copyright ...
This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem. Our experiments show, in 48-hour ...
Work Status & BPFs - Free download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. SAP BPC Work Status Business Process Flow
Second, Syzkaller fails to attach and trigger the execution of eBPF programs most of the times. This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem. Our experiments show, in 48-hour fuzzing sessions, BRF can successfully execute 8x more eBPF ...
Bronchopleural fistula (BPF) is a pathological communication between the bronchial tree and pleural space. This clinical condition, which has high mortality and morbidity, is one of the major therapeutic challenges for clinicians even today. BPF may result from a lung neoplasm, necrotizing pneumonia, empyema, blunt and penetrating lung injuries, and a complication of surgical procedures.
Filters in Network Theory
This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem, proving its effectiveness. The eBPF technology in the Linux kernel has been widely adopted for different applications, such as networking, tracing, and security, thanks to the programmability it provides.
Second, Syzkaller fails to attach and trigger the execution of eBPF programs most of the times. This paper introduces the BPF Runtime Fuzzer (BRF), a fuzzer that can satisfy the semantics and dependencies required by the verifier and the eBPF subsystem. Our experiments show, in 48-hour fuzzing sessions, BRF can successfully execute 8x more eBPF ...