- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore

Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main 2024
- MHT CET 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Main Question Paper
- JEE Main Cutoff
- JEE Main Answer Key
- JEE Main Result
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- JEE Advanced Registration
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2023
- CAT 2023 College Predictor
- CMAT 2024 Registration
- TS ICET 2024 Registration
- CMAT Exam Date 2024
- MAH MBA CET Cutoff 2024
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- DNB CET College Predictor
- DNB PDCET College Predictor
- NEET Application Form 2024
- NEET PG Application Form 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
- LSAT India 2024
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top Law Collages in Indore
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
- AIBE 18 Result 2023
- NID DAT Exam
- Pearl Academy Exam
Animation Courses
- Animation Courses in India
- Animation Courses in Bangalore
- Animation Courses in Mumbai
- Animation Courses in Pune
- Animation Courses in Chennai
- Animation Courses in Hyderabad
- Design Colleges in India
- Fashion Design Colleges in Bangalore
- Fashion Design Colleges in Mumbai
- Fashion Design Colleges in Pune
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Hyderabad
- Fashion Design Colleges in India
- Top Design Colleges in India
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission 2024
- UP B.Ed JEE 2024
- DDU Entrance Exam
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET Exam City Intimation Slip 2024
- IGNOU Date Sheet
- CUET Mock Test 2024
- CUET Admit card 2024
- CUET PG Syllabus 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Syllabus 2024
- IGNOU Exam Form 2024
- IGNOU Result
- CUET Courses List 2024
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Access premium articles, webinars, resources to make the best decisions for career, course, exams, scholarships, study abroad and much more with
Plan, Prepare & Make the Best Career Choices
Cyber Crime Essay
The unlawful act of gaining unauthorised access to computer systems or digital devices is known as cybercrime. A detailed grasp of how to stop or recover from cyberattacks is provided by cyber security. Online courses offer guidance on how to avoid, safeguard against, and recover from cybercrime risks. Here are a few sample essays on the topic ‘Cyber Crime’.
100 Words Essay on Cyber Crime
200 words essay on cyber crime, 500 words essay on cyber crime.

Cybercrime is the most discussed problem in the twenty-first century. The usage of cellphones and the internet is increasing dramatically over the world, which is generating questions about consumers' security and privacy. Because of this, it is crucial for all users to understand cybercrime and security. Cybercrime is defined as organised criminal conduct carried out by attackers online. Cybercrime comes in numerous forms, such as fraud, computer viruses, cyberstalking, and others. Due to these, businesses and government organisations are spending more on maintaining and employing professionals in cybercrime.
There are millions and billions of users and websites in the vast community known as cyberspace. People utilise it for a variety of activities including e-commerce, transactions, shopping, movies, music, and video games. Anyone can simply access anything online in the current technological era owing to accessible internet connection. As a result, crime in general and cybercrime in particular have surged dramatically. Additionally, the faster internet connection has greatly boosted the rate of data circulation. All of these problems are responsible as to why cyber security has grown to be a significant issue for society.
The government has created a number of cybercrime-related laws in an effort to curb the spread of the crime and to protect people's interests. These laws also provide defence against cybercrime. Aside from that, the government has established cyber cells in police stations to combat cybercrime as quickly as possible.
Cybercrime is an attack that can be harmful to both an individual and a business. There have been several instances where a cyber attack led to a data leak that caused a significant loss for a business or a person. These cyber-attacks could have negative effects on the country and the business. The countless instances of cyberattacks that have taken place in India and other nations have necessitated increased security measures. There are four main categories of cybercrime, according to a popular definition—hacking, money, privacy, and cyber terrorism.
Cybercrime is a type of crime in which illegal activities are carried out online or using computers. Cybercrime comes in a variety of forms which involves harassing online users. Cybercrime is the most serious and rapidly expanding type of crime in this day and age. Any person's life may be negatively impacted for a very long time by becoming a cyber victim. Cybercrimes have a wide range of repercussions on financial and investment activity in digital organisations.
One typical tactic used by criminals is to lure online users in by creating attractive websites and sending phoney emails purporting to be from banks or other organisations and asking for personal information. It makes it easier for criminals to access a person's bank account and personal data. Due to viruses, mail fraud, account hacking, and software piracy, people have been victims of cybercrimes. They also run into problems with unauthorised access mailing, threats from pornographic emails, and video transmission.
Types of Cyber Crime
Cyberstalking | It is the use of electronic communication to track down a person or to make repeated attempts to get in touch with them in order to foster personal interaction despite their blatant lack of interest. Anyone who monitors the internet, email, or any other form of electronic communication is guilty of stalking.
Phishing | It is a sort of fraud that includes collecting personal data from recipients of emails that seem to be coming from a reliable source, including Customer ID, IPIN, Credit/Debit Card number, Card expiration date, CVV number, etc.
Vishing | It is an attempt when criminals attempt to obtain personal information over the phone, such as Customer ID, Net Banking password, ATM PIN, OTP, Card expiration date, CVV, etc.
Smishing | It is a sort of fraud that employs text messages sent to mobile devices to entice victims into dialling a fake phone number, going to a fake website, or downloading harmful software.
Impersonation And Identity Theft | This includes the dishonest or fraudulent use of another person's electronic signature, password, or other distinctive identification trait.
Virus, Worms, Trojan | A computer virus is a programme designed to infiltrate your computer, corrupt your files and data, and spread itself. Worms are malicious software applications that repeatedly duplicate themselves on local drives, network shares, etc. Trojan is a malicious programme that mimics a legitimate application. Trojans offer unauthorised people and applications access to your computer through a backdoor entry, allowing them to steal sensitive data.
How to Prevent Cyber Crime
Backup every piece of information—data, systems, and considerations—to make it easier for businesses to recover from unforeseen events with the help of prior data.
Pick a firewall that offers protection from viruses, malware, and dishonest hackers.
Never divulge private information to a stranger since they might exploit it for fraud.
To avoid cybercrime, check your security settings—in order to determine if someone has logged into your computer, a cyber firewall analyses your network settings.
Antivirus software aids in identifying potential threats and malware before they infect a computer system. Never use software that has been cracked since it poses a serious risk of data loss or malware attack.
Keep your information protected when accessing untrusted websites—information can readily bypass the data through phishing websites.
Explore Career Options (By Industry)
- Construction
- Entertainment
- Manufacturing
- Information Technology
Data Administrator
Database professionals use software to store and organise data such as financial information, and customer shipping records. Individuals who opt for a career as data administrators ensure that data is available for users and secured from unauthorised sales. DB administrators may work in various types of industries. It may involve computer systems design, service firms, insurance companies, banks and hospitals.
Bio Medical Engineer
The field of biomedical engineering opens up a universe of expert chances. An Individual in the biomedical engineering career path work in the field of engineering as well as medicine, in order to find out solutions to common problems of the two fields. The biomedical engineering job opportunities are to collaborate with doctors and researchers to develop medical systems, equipment, or devices that can solve clinical problems. Here we will be discussing jobs after biomedical engineering, how to get a job in biomedical engineering, biomedical engineering scope, and salary.
Ethical Hacker
A career as ethical hacker involves various challenges and provides lucrative opportunities in the digital era where every giant business and startup owns its cyberspace on the world wide web. Individuals in the ethical hacker career path try to find the vulnerabilities in the cyber system to get its authority. If he or she succeeds in it then he or she gets its illegal authority. Individuals in the ethical hacker career path then steal information or delete the file that could affect the business, functioning, or services of the organization.
GIS officer work on various GIS software to conduct a study and gather spatial and non-spatial information. GIS experts update the GIS data and maintain it. The databases include aerial or satellite imagery, latitudinal and longitudinal coordinates, and manually digitized images of maps. In a career as GIS expert, one is responsible for creating online and mobile maps.
Data Analyst
The invention of the database has given fresh breath to the people involved in the data analytics career path. Analysis refers to splitting up a whole into its individual components for individual analysis. Data analysis is a method through which raw data are processed and transformed into information that would be beneficial for user strategic thinking.
Data are collected and examined to respond to questions, evaluate hypotheses or contradict theories. It is a tool for analyzing, transforming, modeling, and arranging data with useful knowledge, to assist in decision-making and methods, encompassing various strategies, and is used in different fields of business, research, and social science.
Geothermal Engineer
Individuals who opt for a career as geothermal engineers are the professionals involved in the processing of geothermal energy. The responsibilities of geothermal engineers may vary depending on the workplace location. Those who work in fields design facilities to process and distribute geothermal energy. They oversee the functioning of machinery used in the field.
Database Architect
If you are intrigued by the programming world and are interested in developing communications networks then a career as database architect may be a good option for you. Data architect roles and responsibilities include building design models for data communication networks. Wide Area Networks (WANs), local area networks (LANs), and intranets are included in the database networks. It is expected that database architects will have in-depth knowledge of a company's business to develop a network to fulfil the requirements of the organisation. Stay tuned as we look at the larger picture and give you more information on what is db architecture, why you should pursue database architecture, what to expect from such a degree and what your job opportunities will be after graduation. Here, we will be discussing how to become a data architect. Students can visit NIT Trichy , IIT Kharagpur , JMI New Delhi .
Remote Sensing Technician
Individuals who opt for a career as a remote sensing technician possess unique personalities. Remote sensing analysts seem to be rational human beings, they are strong, independent, persistent, sincere, realistic and resourceful. Some of them are analytical as well, which means they are intelligent, introspective and inquisitive.
Remote sensing scientists use remote sensing technology to support scientists in fields such as community planning, flight planning or the management of natural resources. Analysing data collected from aircraft, satellites or ground-based platforms using statistical analysis software, image analysis software or Geographic Information Systems (GIS) is a significant part of their work. Do you want to learn how to become remote sensing technician? There's no need to be concerned; we've devised a simple remote sensing technician career path for you. Scroll through the pages and read.
Budget Analyst
Budget analysis, in a nutshell, entails thoroughly analyzing the details of a financial budget. The budget analysis aims to better understand and manage revenue. Budget analysts assist in the achievement of financial targets, the preservation of profitability, and the pursuit of long-term growth for a business. Budget analysts generally have a bachelor's degree in accounting, finance, economics, or a closely related field. Knowledge of Financial Management is of prime importance in this career.
Underwriter
An underwriter is a person who assesses and evaluates the risk of insurance in his or her field like mortgage, loan, health policy, investment, and so on and so forth. The underwriter career path does involve risks as analysing the risks means finding out if there is a way for the insurance underwriter jobs to recover the money from its clients. If the risk turns out to be too much for the company then in the future it is an underwriter who will be held accountable for it. Therefore, one must carry out his or her job with a lot of attention and diligence.
Finance Executive
Product manager.
A Product Manager is a professional responsible for product planning and marketing. He or she manages the product throughout the Product Life Cycle, gathering and prioritising the product. A product manager job description includes defining the product vision and working closely with team members of other departments to deliver winning products.
Operations Manager
Individuals in the operations manager jobs are responsible for ensuring the efficiency of each department to acquire its optimal goal. They plan the use of resources and distribution of materials. The operations manager's job description includes managing budgets, negotiating contracts, and performing administrative tasks.
Stock Analyst
Individuals who opt for a career as a stock analyst examine the company's investments makes decisions and keep track of financial securities. The nature of such investments will differ from one business to the next. Individuals in the stock analyst career use data mining to forecast a company's profits and revenues, advise clients on whether to buy or sell, participate in seminars, and discussing financial matters with executives and evaluate annual reports.
A Researcher is a professional who is responsible for collecting data and information by reviewing the literature and conducting experiments and surveys. He or she uses various methodological processes to provide accurate data and information that is utilised by academicians and other industry professionals. Here, we will discuss what is a researcher, the researcher's salary, types of researchers.
Welding Engineer
Welding Engineer Job Description: A Welding Engineer work involves managing welding projects and supervising welding teams. He or she is responsible for reviewing welding procedures, processes and documentation. A career as Welding Engineer involves conducting failure analyses and causes on welding issues.
Transportation Planner
A career as Transportation Planner requires technical application of science and technology in engineering, particularly the concepts, equipment and technologies involved in the production of products and services. In fields like land use, infrastructure review, ecological standards and street design, he or she considers issues of health, environment and performance. A Transportation Planner assigns resources for implementing and designing programmes. He or she is responsible for assessing needs, preparing plans and forecasts and compliance with regulations.
Environmental Engineer
Individuals who opt for a career as an environmental engineer are construction professionals who utilise the skills and knowledge of biology, soil science, chemistry and the concept of engineering to design and develop projects that serve as solutions to various environmental problems.
Safety Manager
A Safety Manager is a professional responsible for employee’s safety at work. He or she plans, implements and oversees the company’s employee safety. A Safety Manager ensures compliance and adherence to Occupational Health and Safety (OHS) guidelines.
Conservation Architect
A Conservation Architect is a professional responsible for conserving and restoring buildings or monuments having a historic value. He or she applies techniques to document and stabilise the object’s state without any further damage. A Conservation Architect restores the monuments and heritage buildings to bring them back to their original state.
Structural Engineer
A Structural Engineer designs buildings, bridges, and other related structures. He or she analyzes the structures and makes sure the structures are strong enough to be used by the people. A career as a Structural Engineer requires working in the construction process. It comes under the civil engineering discipline. A Structure Engineer creates structural models with the help of computer-aided design software.
Highway Engineer
Highway Engineer Job Description: A Highway Engineer is a civil engineer who specialises in planning and building thousands of miles of roads that support connectivity and allow transportation across the country. He or she ensures that traffic management schemes are effectively planned concerning economic sustainability and successful implementation.
Field Surveyor
Are you searching for a Field Surveyor Job Description? A Field Surveyor is a professional responsible for conducting field surveys for various places or geographical conditions. He or she collects the required data and information as per the instructions given by senior officials.
Orthotist and Prosthetist
Orthotists and Prosthetists are professionals who provide aid to patients with disabilities. They fix them to artificial limbs (prosthetics) and help them to regain stability. There are times when people lose their limbs in an accident. In some other occasions, they are born without a limb or orthopaedic impairment. Orthotists and prosthetists play a crucial role in their lives with fixing them to assistive devices and provide mobility.
Pathologist
A career in pathology in India is filled with several responsibilities as it is a medical branch and affects human lives. The demand for pathologists has been increasing over the past few years as people are getting more aware of different diseases. Not only that, but an increase in population and lifestyle changes have also contributed to the increase in a pathologist’s demand. The pathology careers provide an extremely huge number of opportunities and if you want to be a part of the medical field you can consider being a pathologist. If you want to know more about a career in pathology in India then continue reading this article.
Veterinary Doctor
Speech therapist, gynaecologist.
Gynaecology can be defined as the study of the female body. The job outlook for gynaecology is excellent since there is evergreen demand for one because of their responsibility of dealing with not only women’s health but also fertility and pregnancy issues. Although most women prefer to have a women obstetrician gynaecologist as their doctor, men also explore a career as a gynaecologist and there are ample amounts of male doctors in the field who are gynaecologists and aid women during delivery and childbirth.
Audiologist
The audiologist career involves audiology professionals who are responsible to treat hearing loss and proactively preventing the relevant damage. Individuals who opt for a career as an audiologist use various testing strategies with the aim to determine if someone has a normal sensitivity to sounds or not. After the identification of hearing loss, a hearing doctor is required to determine which sections of the hearing are affected, to what extent they are affected, and where the wound causing the hearing loss is found. As soon as the hearing loss is identified, the patients are provided with recommendations for interventions and rehabilitation such as hearing aids, cochlear implants, and appropriate medical referrals. While audiology is a branch of science that studies and researches hearing, balance, and related disorders.
An oncologist is a specialised doctor responsible for providing medical care to patients diagnosed with cancer. He or she uses several therapies to control the cancer and its effect on the human body such as chemotherapy, immunotherapy, radiation therapy and biopsy. An oncologist designs a treatment plan based on a pathology report after diagnosing the type of cancer and where it is spreading inside the body.
Are you searching for an ‘Anatomist job description’? An Anatomist is a research professional who applies the laws of biological science to determine the ability of bodies of various living organisms including animals and humans to regenerate the damaged or destroyed organs. If you want to know what does an anatomist do, then read the entire article, where we will answer all your questions.
For an individual who opts for a career as an actor, the primary responsibility is to completely speak to the character he or she is playing and to persuade the crowd that the character is genuine by connecting with them and bringing them into the story. This applies to significant roles and littler parts, as all roles join to make an effective creation. Here in this article, we will discuss how to become an actor in India, actor exams, actor salary in India, and actor jobs.
Individuals who opt for a career as acrobats create and direct original routines for themselves, in addition to developing interpretations of existing routines. The work of circus acrobats can be seen in a variety of performance settings, including circus, reality shows, sports events like the Olympics, movies and commercials. Individuals who opt for a career as acrobats must be prepared to face rejections and intermittent periods of work. The creativity of acrobats may extend to other aspects of the performance. For example, acrobats in the circus may work with gym trainers, celebrities or collaborate with other professionals to enhance such performance elements as costume and or maybe at the teaching end of the career.
Video Game Designer
Career as a video game designer is filled with excitement as well as responsibilities. A video game designer is someone who is involved in the process of creating a game from day one. He or she is responsible for fulfilling duties like designing the character of the game, the several levels involved, plot, art and similar other elements. Individuals who opt for a career as a video game designer may also write the codes for the game using different programming languages.
Depending on the video game designer job description and experience they may also have to lead a team and do the early testing of the game in order to suggest changes and find loopholes.
Radio Jockey
Radio Jockey is an exciting, promising career and a great challenge for music lovers. If you are really interested in a career as radio jockey, then it is very important for an RJ to have an automatic, fun, and friendly personality. If you want to get a job done in this field, a strong command of the language and a good voice are always good things. Apart from this, in order to be a good radio jockey, you will also listen to good radio jockeys so that you can understand their style and later make your own by practicing.
A career as radio jockey has a lot to offer to deserving candidates. If you want to know more about a career as radio jockey, and how to become a radio jockey then continue reading the article.
Choreographer
The word “choreography" actually comes from Greek words that mean “dance writing." Individuals who opt for a career as a choreographer create and direct original dances, in addition to developing interpretations of existing dances. A Choreographer dances and utilises his or her creativity in other aspects of dance performance. For example, he or she may work with the music director to select music or collaborate with other famous choreographers to enhance such performance elements as lighting, costume and set design.
Social Media Manager
A career as social media manager involves implementing the company’s or brand’s marketing plan across all social media channels. Social media managers help in building or improving a brand’s or a company’s website traffic, build brand awareness, create and implement marketing and brand strategy. Social media managers are key to important social communication as well.
Photographer
Photography is considered both a science and an art, an artistic means of expression in which the camera replaces the pen. In a career as a photographer, an individual is hired to capture the moments of public and private events, such as press conferences or weddings, or may also work inside a studio, where people go to get their picture clicked. Photography is divided into many streams each generating numerous career opportunities in photography. With the boom in advertising, media, and the fashion industry, photography has emerged as a lucrative and thrilling career option for many Indian youths.
An individual who is pursuing a career as a producer is responsible for managing the business aspects of production. They are involved in each aspect of production from its inception to deception. Famous movie producers review the script, recommend changes and visualise the story.
They are responsible for overseeing the finance involved in the project and distributing the film for broadcasting on various platforms. A career as a producer is quite fulfilling as well as exhaustive in terms of playing different roles in order for a production to be successful. Famous movie producers are responsible for hiring creative and technical personnel on contract basis.
Copy Writer
In a career as a copywriter, one has to consult with the client and understand the brief well. A career as a copywriter has a lot to offer to deserving candidates. Several new mediums of advertising are opening therefore making it a lucrative career choice. Students can pursue various copywriter courses such as Journalism , Advertising , Marketing Management . Here, we have discussed how to become a freelance copywriter, copywriter career path, how to become a copywriter in India, and copywriting career outlook.
In a career as a vlogger, one generally works for himself or herself. However, once an individual has gained viewership there are several brands and companies that approach them for paid collaboration. It is one of those fields where an individual can earn well while following his or her passion.
Ever since internet costs got reduced the viewership for these types of content has increased on a large scale. Therefore, a career as a vlogger has a lot to offer. If you want to know more about the Vlogger eligibility, roles and responsibilities then continue reading the article.
For publishing books, newspapers, magazines and digital material, editorial and commercial strategies are set by publishers. Individuals in publishing career paths make choices about the markets their businesses will reach and the type of content that their audience will be served. Individuals in book publisher careers collaborate with editorial staff, designers, authors, and freelance contributors who develop and manage the creation of content.
Careers in journalism are filled with excitement as well as responsibilities. One cannot afford to miss out on the details. As it is the small details that provide insights into a story. Depending on those insights a journalist goes about writing a news article. A journalism career can be stressful at times but if you are someone who is passionate about it then it is the right choice for you. If you want to know more about the media field and journalist career then continue reading this article.
Individuals in the editor career path is an unsung hero of the news industry who polishes the language of the news stories provided by stringers, reporters, copywriters and content writers and also news agencies. Individuals who opt for a career as an editor make it more persuasive, concise and clear for readers. In this article, we will discuss the details of the editor's career path such as how to become an editor in India, editor salary in India and editor skills and qualities.
Individuals who opt for a career as a reporter may often be at work on national holidays and festivities. He or she pitches various story ideas and covers news stories in risky situations. Students can pursue a BMC (Bachelor of Mass Communication) , B.M.M. (Bachelor of Mass Media) , or MAJMC (MA in Journalism and Mass Communication) to become a reporter. While we sit at home reporters travel to locations to collect information that carries a news value.
Corporate Executive
Are you searching for a Corporate Executive job description? A Corporate Executive role comes with administrative duties. He or she provides support to the leadership of the organisation. A Corporate Executive fulfils the business purpose and ensures its financial stability. In this article, we are going to discuss how to become corporate executive.
Multimedia Specialist
A multimedia specialist is a media professional who creates, audio, videos, graphic image files, computer animations for multimedia applications. He or she is responsible for planning, producing, and maintaining websites and applications.
Quality Controller
A quality controller plays a crucial role in an organisation. He or she is responsible for performing quality checks on manufactured products. He or she identifies the defects in a product and rejects the product.
A quality controller records detailed information about products with defects and sends it to the supervisor or plant manager to take necessary actions to improve the production process.
Production Manager
A QA Lead is in charge of the QA Team. The role of QA Lead comes with the responsibility of assessing services and products in order to determine that he or she meets the quality standards. He or she develops, implements and manages test plans.
Process Development Engineer
The Process Development Engineers design, implement, manufacture, mine, and other production systems using technical knowledge and expertise in the industry. They use computer modeling software to test technologies and machinery. An individual who is opting career as Process Development Engineer is responsible for developing cost-effective and efficient processes. They also monitor the production process and ensure it functions smoothly and efficiently.
AWS Solution Architect
An AWS Solution Architect is someone who specializes in developing and implementing cloud computing systems. He or she has a good understanding of the various aspects of cloud computing and can confidently deploy and manage their systems. He or she troubleshoots the issues and evaluates the risk from the third party.
Azure Administrator
An Azure Administrator is a professional responsible for implementing, monitoring, and maintaining Azure Solutions. He or she manages cloud infrastructure service instances and various cloud servers as well as sets up public and private cloud systems.
Computer Programmer
Careers in computer programming primarily refer to the systematic act of writing code and moreover include wider computer science areas. The word 'programmer' or 'coder' has entered into practice with the growing number of newly self-taught tech enthusiasts. Computer programming careers involve the use of designs created by software developers and engineers and transforming them into commands that can be implemented by computers. These commands result in regular usage of social media sites, word-processing applications and browsers.
Information Security Manager
Individuals in the information security manager career path involves in overseeing and controlling all aspects of computer security. The IT security manager job description includes planning and carrying out security measures to protect the business data and information from corruption, theft, unauthorised access, and deliberate attack
ITSM Manager
Automation test engineer.
An Automation Test Engineer job involves executing automated test scripts. He or she identifies the project’s problems and troubleshoots them. The role involves documenting the defect using management tools. He or she works with the application team in order to resolve any issues arising during the testing process.
Applications for Admissions are open.

Aakash iACST Scholarship Test 2024
Get up to 90% scholarship on NEET, JEE & Foundation courses

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters

ALLEN NEET Coaching
Ace your NEET preparation with ALLEN Online Programs

SAT® | CollegeBoard
Registeration closing on 19th Apr for SAT® | One Test-Many Universities | 90% discount on registrations fee | Free Practice | Multiple Attempts | no penalty for guessing

TOEFL ® Registrations 2024
Thinking of Studying Abroad? Think the TOEFL® test. Register now & Save 10% on English Proficiency Tests with Gift Cards

Resonance Coaching
Enroll in Resonance Coaching for success in JEE/NEET exams
Everything about Education
Latest updates, Exclusive Content, Webinars and more.
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Cetifications
We Appeared in

25,000+ students realised their study abroad dream with us. Take the first step today
Meet top uk universities from the comfort of your home, here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

- School Education /
✍️Essay on Cybercrime: Free Samples in 100, 200, 300 Words
- Updated on
- Nov 2, 2023

The 21st century is a digital age, where any and every task is done on the internet. All thanks to the developments in technology which have been the main factor to ease human life on earth and maybe on other plants in future. But with the benefits of technology, there are several harmful effects, one of them which has recently gained popularity; Cyber Crime.

Cybercrime has emerged as pervasive and evolved as one of the most dangerous threats to humans. There are several users on the internet who indulge in illegal and criminal activities, using computers and networks. To guide you through this hot debate topic, below we have discussed essays on cybercrime.
Table of Contents
- 1 Essay on Cybercrime in 100 Words
- 2 Essay on Cybercrime in 200 Words
- 3 Essay on Cybercrime in 300 Words
Also Read: Essay on Student Life
Essay on Cybercrime in 100 Words
Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one. Cybercrime often invades a person’s privacy by stealing their personal details, including sensitive data, photos, and communication records, which can be used for blackmailing or any malicious purpose.
There are several governmental and non-government organizations which are working
To tackle cybercrime by raising awareness among the masses, cyber security training, implementing robust security protocols, and enacting comprehensive cybercrime laws.
Essay on Cybercrime in 200 Words
Cybercrime is a criminal activity done online using a computer, network and internet. With the increasing use of the internet and mobile phones, the number of criminal activities has also gained pace. These criminal-minded people steal the personal details of a person, which leads to financial losses and damages the reputation of the victims. Various scams and fraudulent schemes are offered on the internet like online auctions, advance fees, or any investment scam, which are all aimed at deceiving individuals into parting with their money.
Cybercrime is not limited to financial losses or reputational damage, a more discrete term has emerged; cyberbullying. In cyberbullying, a person is harassed, humiliated, or threatened online. This can have severe psychological and emotional consequences. Ethical hackers or white hat hackers can help organizations identify vulnerabilities in their systems before malicious hackers exploit them.
Cybercrime doesn’t have any boundaries and is an international issue and international cooperation is crucial for tracking and prosecuting cybercriminals who operate across borders. To combat cybercrime effectively, a multi-faceted approach is required, involving education, technology, legislation, and international cooperation. As technology continues to advance, our efforts to combat cybercrime must keep pace to protect our increasingly interconnected world.
Also Read – Essay on Winter Season
Essay on Cybercrime in 300 Words
Economists have termed cybercrime as ‘ A Hidden Threat to the Digital World.’ Modern humans are relying on the internet for their day-to-day activities and every macro and micro activity. In this sense, the term cybercrime comes to the front. Cybercrime refers to criminal activities conducted through the use of computers, networks, and the Internet.
Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
The consequences of cybercrime are far-reaching. Financial losses run into 10 digits annually, affecting individuals and organizations alike. Personal privacy is invaded as cybercriminals steal sensitive data, photos, and communication records. In cases of cyberbullying and harassment, victims suffer reputational damages, psychological distress, and emotional trauma, particularly in cases of cyberbullying and harassment.
It’s necessary to look for a multifaceted approach to deal with cybercrime, some of which are.
- Raising public awareness through campaigns where people are informed about the risks of cybercrime and educate them on best practices for online safety.
- Individuals and organizations should implement robust security protocols, regularly update software, and use multi-factor authentication to protect their digital assets.
- Governments should enact and enforce cybercrime laws, providing law enforcement agencies with the resources and expertise needed to prosecute cybercriminals effectively.
- Looking at the global nature of cybercrime, international collaboration is vital. Countries should work together to share threat intelligence and cooperate in the investigation and prosecution of cybercriminals.
- Ethical hackers can help organizations identify and rectify vulnerabilities in their systems before malicious actors exploit them.
Tackling cybercrime requires proactive measures, including education, strong cybersecurity practices, legislation, international cooperation, and the active involvement of ethical hackers.
Related Articles
Cybercrime is an illegal and unethical activity which is done by hackers and fraudsters to gain financial or any other benefits for themselves.
To tackle cybercrime, several measures can be taken. Some of these measures are education and public awareness, research and innovation, ethical hacking, etc.
To write an essay on cybercrime, you need to give details on how it works and the level of danger it poses to humans. Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
For more information about such informative articles, visit our essay writing page and make sure to follow Leverage Edu .
Shiva Tyagi
With an experience of over a year, I've developed a passion for writing blogs on wide range of topics. I am mostly inspired from topics related to social and environmental fields, where you come up with a positive outcome.
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Connect With Us

25,000+ students realised their study abroad dream with us. Take the first step today.

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
January 2024
September 2024
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Have something on your mind?

Make your study abroad dream a reality in January 2022 with
India's Biggest Virtual University Fair

Essex Direct Admission Day
Why attend .

Don't Miss Out
Talk to our experts
1800-120-456-456
- Cyber Crime Essay

Essay on Cyber Crime
Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about cyber crime & security. As a result, thi topic has become the most favorite topic of the examiner and can often be seen asked in the exams. In this view, students must have information on cyber crime and stay prepared to tackle such topics in the essay question in the English paper.
Introduction
Cybercrime is a dangerous attack a company or an individual may face. There are many cases where the cyber attack has brought massive loss to the company and individuals due to the data hack. We live in a technology-driven era, and every piece of information is now fed on computers. Cybercrime involves an attack on computers and digital devices. These cyber-attacks can prove hazardous not just for the organization, but also for the nation. To date, there are many digital attack cases in India and global, pushing for more security measures. These attacks are also affecting the economy of the country if not controlled in the initial stage.

What is Cybercrime?
Cybercrime or attack is defined as the systematic criminal activity occurring digitally
and done by attackers. There are many examples of cybercrime, including fraud,
malware viruses, cyberstalking and others. Due to these, government agencies and
companies are investing more in the maintenance and hiring of cybercrime experts.
Earlier, cybercrime was committed only by individuals or by small groups. However, now a highly complex cybercriminals network work on attacking the system for data
collection.
Three groups of cybercrimes-
This is the form of cyberstalking, trafficking, and grooming. Over the years, this
This type of cybercrime has been taken seriously by law enforcement agencies. It is
now keeping a track over every such attack on an individual.
Similar to the real world where criminals steal the property, in the cyber world,
attackers steal data. Here, the attacker steals a person's bank details and
misuse the credit card for online purchase. By using malicious software, the
attacker attacks the property to disrupt the system of the organization.
These types of crimes are denoted as cyber terrorism. This can be a terror because
the attacker can get hold of essential documents related to government
projects. An enemy nation or terrorist usually makes such attacks. There are
many cases globally where a terrorist hacks government data.
Apart from these, there is a financial crime where the hacker steals the money of the
user account holder. Moreover, they steal company data and finance.
In this type, the computer system of the person is hacked to get personal
information. In many countries, including India, hacking is a punishable act.
It is quite different from ethical hacking. In normal hacking, illegal use
different types of software to enter the system of the target person. Hacker is
then able to monitor every activity done by the person.
This Cybercrime is about violating copyright and downloading music or movies. In
India, many movies before their releases are leaked on the movie download
sites. In other words , theft is also called privacy, which can bring a huge
loss to the organization.
Cyber Stalking
It is online harassment by an individual or a group of people. Normally, these
stalkers target an individual and harass online. There are many cases of
cyberstalking in India, resulting in the target person ending up taking
Malicious Software
These are computer-based cybercrimes where virus-based software is installed in the
target people or organization computers. This is to damage the system and
corrupt the data of the target.
Laws Related to Cybercrime
In India, there are many cybercrime laws enacted to stop this threat. Be it for
the individual or the organization; these laws help to either bring down the
number of cases or eliminate these digital crimes.
Apart from these laws, as an individual, you also need to take steps to stop these
crimes. Like, not providing your login details, installing trust anti-virus
software and keeping your online profile private can help to act against such
Cybercrime is a significant threat that can bring huge loss to the individual and the
organization. It is essential to follow basic online rules to ensure the safety
of self and the organization.
Benefits of Cyber Crime Essay in English provided by Vedantu
The essay on cybercrime provided by Vedantu is prepared by highly qualified teachers which makes it a reliable source of information. This information could be utilized for a variety of reasons. Being a reliable piece of information the essay will benefit everyone curious to know about the topic.
Following are the highlights of its benefits:
Reliable information
Adaptive to the context
Precise language
Fulfills the requirements of the students for english exam questions
Comprehensive and analytical. The article digs in the depth of the issue and analyzes it through a 360 degree perspective.
The essay could also be used by the students for preparing themselves for the essay question in the English paper. This essay is an excellent guide to understand what the examiner is looking for in the exam. Moreover, the topic of cybercrime is quite a recurrent one in the exam. So the students use this essay to deal with the same topic.
The Essay on Cyber Crime is an excellent guide on averting any possibilities of a cyber attack. On today's date, one is mostly on the internet for a variety of reasons. It becomes essential for one to know important tips that can keep one safe from cyberbullies, thieves, or blackmailers. It is also important for one to understand the right course of actions to be taken in an eventuality of such an incident.
Download the cybercrime essay for students in English on the Vedantu website.

FAQs on Cyber Crime Essay
1. How Does Cybercrime Work?
Group of people or an individual commits most of these cyber-crimes. These criminals use a systematic process to hack and commit these acts. These criminal communities share strategies and tools to launch attacks. Some of the cybercrime techniques
Fast Flux - In this method, the hacker moves data quickly among computers in a botnet, making it challenging to find the right source.
Social Engineering - This method includes using lies and manipulation to trick people into revealing their personal information.
Skimmers - This involves installing a skimming tool in an ATM and stealing the information. You may find such skimming devices in ATMs.
There are some digital criminals targeting organizations to steal personal information.
2. How Cybercrime Affects Society?
Cybercrime can hugely affect society. In 2018, the US faced a loss of $600 billion. As consumers are increasingly allowing technologies to get into their lives, cyber attackers are getting better access. Some of the essential information available are-
Personal health data, sleep schedules, and geo-locations Shopping history, account information, and passive conversations noticed voice-controlled devices, Private conversations on social media accounts.
Your entire life is now available on social media, making it vulnerable to hack or cyber-attack. Attackers use different techniques including- installing malware, virus, phishing, cyberstalking, etc. These can certainly bring loss of lives and data for individuals and organizations. For society, this is a significant loss in the long run. One needs to be very careful when presenting himself socially.
3. How to stay secure in times of cybercrime?
Cybercrime is a real threat posing to society. It is the 21st-century version of theft and blackmailing. There are certain ways one should adopt to prevent any possibilities of cybercrime. Do not disclose the banking details to random people or fill the CVV of your debit or credit cards on an unknown and unverified website. Keep your passwords always discrete. The camera of the laptop should always be covered.
4. Where can I get a cybercrime essay?
One can find a good quality cyber crime essay on Vedantu's website. The essay which is prepared by the expert teachers describes everything that one needs to know about cybercrime. It is the one-stop solution for all your requirements on the topic. Their essay is available in PDF format on the website and could be downloaded on any device. One downloaded essay could be used in offline mode too. If one finds it feasible, the printout of the PDF could also be taken out.
Essays About Cyber Crime: Top 5 Examples and 8 Prompts
Cybercrime is a severe issue that threatens user security and safety. To help you with this subject, see our essays about cyber crime examples and prompts.
As its name suggests, cyber crime occurs in the digital space beyond our tangible keyboards, computer monitors, and phone screens. This criminal activity happens offline and online, and although many are affected, only 10% to 12% of the victims report these wrongdoings.
You may have encountered cyber crime in the virtual world as a victim or an almost-target. Most of us have the misfortune of being hacked, phished, spoofed, or attacked with a denial of service. At the same time, you may not know that you’ve committed a cyber crime by pirating software, music, movies, books, and other data.
5 Essay Examples
1. cyber crime essay for students and children by anonymous on toppr.com, 2. cyber crimes and its effects on youth by anonymous on edubirdie.com, 3. cyber crime by luz owens, 4. cyber crime: a threat to society by ankita yadav, 5. essay on cyber crime by anonymous on vedantu.com, 1. the future of cyber crime, 2. the benefits of cyber crime, 3. cyber crime and its impacts on an industry, 4. cyber crime prevention for the average user, 5. mobile protection from cyber crime, 6. the power of strong passwords to combat cyber crime, 7. laws and cyber crime, 8. my personal experience with cyber crime.
“Cyber Crime is not something which we cannot deal with our self. Likewise, with little use of our common sense and logic, we can stop Cyber Crimes from happening.”
The essay begins with cyber crime’s meaning, defining it as an illegal activity to harm others through a computer. The author also discusses the four significant categories of cybercrime: hacking, privacy, financial, and cyber terrorism, and digs into what each type covers.
In the next part of the essay, the writer focuses on cybercrime in India, citing how it’s now a significant concern. So, the government implements cybercrime laws to protect itself and its citizens. You might also be interested in these articles about death penalty .
“Becoming the victim of cyber can have long lasting effects on any one’s life.”
After recognizing cybercrime as the most potent crime today, the author probes its direct connection to the creation of the Internet. Aside from pushing organizations to spend more on their online security to avoid vulnerability, cyber crime also causes lasting effects on its victims’ lives.
The essay provides various instances where criminals exploit unaware individuals through the web. An example is fake emails mimicking legitimate organizations that give criminals access to the victim’s personal information to ruin their financial credibility. Unfortunately, the main targets for these crimes are the youth as they are the most who use the web for their studies.
“In order to diminish cyber crime, all organizations and governments should cooperate, as it has no boundaries.”
Owens compares the new century and the old days when cybercrime didn’t exist. She then describes cyber crime, its different classifications, and how much damage it causes annually. She concedes that this criminal act is difficult to control because most countries don’t have the right laws against it.
Owens also discusses how the youth are more prone to cybercrime exposure because they’re more likely to use technology and be curious. She includes relevant cases and studies that analyze cyber crime, its effects, and how it’s used to the detriment of others.
“Cyber crime is the criminal act which takes place over the internet through computers as tools or targets or other smart devices meant for making our work easier.”
Yadav determines cybercrime as a punishable offense committed via the internet, causing loss to an individual, organization, or government. She lists examples of cybercrime and how everyone falls victim to them, no matter their educational attainment. In her conclusion, Yadav recognizes cybercrime as the most prevalent misdeed today and calls for more severe measures to prevent it.
“Cybercrime or attack is defined as the systematic criminal activity occurring digitally and done by attackers.”
This essay highlights privacy issues connected to the steady rise of smartphones and internet usage. It’s also the reason users should be knowledgeable about cyber crime. The author defines cyber crime and expounds on its adverse effects on individuals, properties, and the government. The author also mentions specific crimes like hacking, theft, and cyberstalking.
Looking for more suggestions? Check out our essays about technology for your next project.
8 Prompts for Essays About Cyber Crime

Cybercrime continuously evolves as more people learn about its potential and countermeasures. Consider this essay prompt if you have several ideas and theories about how cybercrime will adapt to new anti-cybercrime measures.
Don’t forget to research the current state of cybercrime, the capabilities of the criminals that perform it, and the laws made to prevent it. Make sure to include research data and support your theories with relevant studies.
While cybercrime is an umbrella term for illegal acts in cyberspace, it can also lead to positive results. One silver lining example of cybercrime is that it pushes software developers to create more effective protection measures against online attacks. Its rising occurrence among the youth also means that more people are becoming more educated about this issue and can thus actively prevent it from happening.
In this controversial essay topic, discuss the possible benefits of cybercrime. Look into how cybercrime might push technology forwards and improve personal data protection online. Cite relevant case studies and reference platforms with strict security measures, such as Meta .
Whether it’s healthcare, education, or banking, you can always find different and unique cybercrime impacts in various fields. Write an essay about how cyber criminals and their illegal actions can affect a specific industry, depending on your specialty or interest. For example, you can talk about the impacts of cybercrime on students and teachers if you work in the educational field.
One frustrating thing about being an average computer or device user is that you may need more resources to protect yourself from the latest cyber-attacks. With in-depth research and help from field experts, write an essay about how the average Joe can defend himself for a small fee or for free.

Most people spend hours on their smartphones and other mobile devices. Those who use their phones for work, banking, entertainment, and others are always at risk of cyber attacks. For this prompt, research how smartphone users can create a security blanket against cybercrime when they surf the internet, use banking apps, or linger on social media. Tip: If writing an essay sounds like a lot of work, simplify it. Write a simple 5 paragraph essay instead.
If there is one thing cybercriminals hate, it’s a strong and complex password. With this essay prompt, you can discuss creative and memorable ways individuals can create unique passwords.
For example, they can spell their sibling’s name backward and add their favorite number and symbols at the end. Favorite colors, food items, dates, and other things can also work as effective password choices when used with the right symbol, capitalization, and number combinations. There are also helpful apps such as 1password , which creates strong passwords automatically for users.
For this prompt, look for laws worldwide that successfully assist the government in fighting cybercrime. Add your opinion on how your country should adapt these laws and if there are any areas of these proposals you want to change, remove, or improve.
If you’ve had a distressing memory concerning cybercrime, recount the experience in your essay. Tell how it happened and what you did to battle its impact on your life. Similarly, you can also talk about any cybercrime you unintentionally committed and how you worked on stopping yourself from repeating it. Looking for more suggestions? Check out our essays about technology for your next project.

Maria Caballero is a freelance writer who has been writing since high school. She believes that to be a writer doesn't only refer to excellent syntax and semantics but also knowing how to weave words together to communicate to any reader effectively.
View all posts

Essay on Cyber Crime
Students are often asked to write an essay on Cyber Crime in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Crime
Introduction to cyber crime.
Cybercrime refers to illegal activities conducted through the internet. It’s a fast-growing area of crime, with more criminals exploiting the speed, convenience, and anonymity of the internet.
Types of Cyber Crime
There are many types of cybercrimes. These include hacking, where unauthorized access is gained to a computer system, and identity theft, where personal information is stolen and used fraudulently.
Preventing Cyber Crime
Preventing cybercrime is crucial. This can be achieved by using strong, unique passwords, keeping software and systems updated, and being cautious of suspicious emails or websites.
Cybercrime is a significant issue in today’s digital age. Awareness and proper precautions can help in preventing these crimes.
Also check:
- 10 Lines on Cyber Crime
- Paragraph on Cyber Crime
- Speech on Cyber Crime
250 Words Essay on Cyber Crime
Introduction.
Cybercrime, an umbrella term encompassing a variety of offenses committed using digital technology, poses a significant threat to the modern world. As our reliance on technology increases, so does the potential for misuse, leading to a surge in cybercrimes.
The Nature of Cybercrime
Cybercrimes can range from financial theft, identity theft, cyberstalking, to more complex forms like cyber terrorism and cyber warfare. They exploit the anonymity provided by the internet, making them difficult to trace, investigate, and prosecute.
Impact of Cybercrime
The impact of cybercrime extends beyond financial loss. It can cause significant psychological harm to victims, damage reputations, and even pose threats to national security. In a digital world, the effects of cybercrime are far-reaching and potentially devastating.
Preventing Cybercrime
Preventing cybercrime requires a multi-faceted approach. It involves not only technological solutions but also legal and educational measures. A robust cybersecurity infrastructure, stringent laws, and increased public awareness are crucial to mitigating the risk of cybercrime.
In conclusion, as technology advances, so too does the sophistication of cybercrimes. Combating this growing threat requires a comprehensive approach that combines technology, legislation, and education. The fight against cybercrime is a shared responsibility, requiring collective effort from individuals, organizations, and governments alike.
500 Words Essay on Cyber Crime
In the digital age, our reliance on technology has given rise to a new form of criminal activity known as cyber crime. This term encapsulates any illegal activity that utilizes a computer as its primary means of commission. Cyber crime has become a critical concern due to its widespread impact, affecting individuals, businesses, and even nations.
The Different Forms of Cyber Crime
Cyber crime manifests in various forms, each carrying its unique implications. Identity theft, for instance, involves unauthorized access and use of personal information for fraudulent purposes. Another common type, cyberstalking, uses digital tools to harass or threaten individuals. More complex forms of cyber crime include cyberterrorism and cyber warfare, which target national security and infrastructure.
The Impact of Cyber Crime
The impact of cyber crime is far-reaching and multifaceted. On an individual level, victims may face financial loss, emotional distress, and privacy invasion. For businesses, the implications can be devastating, leading to significant financial losses, reputational damage, and loss of customer trust. On a national level, cyber crime can threaten a country’s security, economy, and infrastructure.
Preventing cyber crime requires a multi-pronged approach. On a personal level, individuals must take precautions such as using strong passwords, regularly updating software, and being cautious of suspicious emails or links. Businesses, on the other hand, need robust cybersecurity measures, including firewalls, intrusion detection systems, and regular employee training. Governments must also play their part, enacting robust cyber crime laws and cooperating internationally to apprehend and prosecute cyber criminals.
Legal and Ethical Considerations
The legal landscape surrounding cyber crime is complex and continually evolving. Jurisdictional issues often arise, given the borderless nature of the internet. Ethically, the debate around privacy and security is pertinent. While law enforcement agencies advocate for backdoors into encrypted systems to combat cyber crime, this raises concerns about potential misuse and invasion of privacy.
The Future of Cyber Crime
As technology advances, so does the sophistication of cyber crimes. Future threats could involve artificial intelligence and machine learning, making detection and prevention even more challenging. Therefore, continuous research, development of advanced cybersecurity measures, and international cooperation are imperative to stay a step ahead of cyber criminals.
In conclusion, cyber crime poses a significant threat in the digital age, affecting all aspects of society. A comprehensive understanding of its forms, impacts, prevention strategies, and the associated legal and ethical considerations is crucial for individuals, businesses, and governments alike. As we move further into the digital era, the fight against cyber crime will undoubtedly remain a pressing issue.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Christmas Celebration in School
- Essay on How I Spent My Christmas Vacation
- Essay on My Aim of Life to Become a Bank Manager
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Cyber Crime Essay For Students

Table of Contents
Cyber Crime Essay: In today’s digital age, the internet has become an integral part of our lives. While it offers numerous benefits, it also brings with it a dark side – cybercrime. It is imperative for all individuals to be well-informed about the world of cybercrime, what it is, its types, and its impact. In this article, we have provided you with sample essays on cybercrime of varying lengths to help you get started on your own essay.
What is Cyber Crime?
Cybercrime, simply put, is criminal activity conducted online. It encompasses a wide range of illegal activities that use computers and the internet as tools to commit crimes. These crimes can be broadly categorized into four main types: financial, personal, political, and property crimes.
Fill Out the Form for Expert Academic Guidance!
Please indicate your interest Live Classes Books Test Series Self Learning
Verify OTP Code (required)
I agree to the terms and conditions and privacy policy .
Fill complete details
Target Exam ---
Whether you need a 100-word overview or a more detailed 500-word essay on the topic “Cyber Crime Essay”, we’ve got your back. Refer to the sample essays given below.

Sample Essays on Cyber Crime
100-word essay on cyber crime.
Cybercrime, the dark underbelly of the digital world, is on the rise. It encompasses a range of illegal activities conducted through computers and the internet, including hacking, phishing, and online fraud. Cybercriminals exploit vulnerabilities for financial gain or personal satisfaction, causing harm to individuals and organizations. The consequences can be devastating, from financial loss to emotional distress and stolen identities. To combat cybercrime, awareness and vigilance are paramount. Adopting strong passwords, using antivirus software, and practicing safe online behavior are steps we can all take to protect ourselves in this interconnected age. Cybercrime is a threat we must confront in our digital lives.
Cyber Crime Essay: 250 Words
In today’s technology-driven world, where we rely heavily on the internet and digital devices for various aspects of our lives, the threat of cybercrime looms larger than ever. Cybercrime encompasses a wide range of illegal activities carried out in the digital realm, and its impact extends far beyond just financial losses.
Hacking, a prevalent cybercrime, involves malicious individuals gaining unauthorized access to systems, risking sensitive data compromise, leading to dire consequences such as identity theft and financial ruin.
Phishing scams, a common cybercrime, deceive victims into disclosing personal data, enabling criminals to commit theft and fraud with the acquired information.
Online fraud is rampant in the cyber world. Criminals create fake websites or online marketplaces to dupe unsuspecting victims into making payments for goods or services that don’t exist. Victims can lose substantial sums of money in such scams.
To combat cybercrime, prioritize cybersecurity by practicing safe online behavior, updating passwords, and using reliable antivirus software. Keeping software and operating systems up to date is crucial for enhanced protection.
Additionally, organizations and governments need to invest in robust cybersecurity infrastructure and enact stricter regulations to deter cybercriminals. Raising awareness about the risks and consequences of cybercrime is a collective responsibility that can help safeguard our digital world.
In conclusion, cybercrime is a growing menace that affects individuals, businesses, and society as a whole. Understanding the various forms of cybercrime and taking proactive steps to protect ourselves and our digital assets are essential in this interconnected age. Only through collective efforts can we hope to mitigate the ever-present threat of cybercrime.

Cyber Crime Essay: 300 Words
In our increasingly digitized world, cybercrime has emerged as a formidable challenge. Cybercrime refers to criminal activities carried out through computer networks and the internet, encompassing a wide range of illicit actions that exploit vulnerabilities in our interconnected systems.
One prevalent form of cybercrime is hacking, where individuals or groups gain unauthorized access to computer systems or networks, often with malicious intent. Hacked systems can lead to data breaches, identity theft, and financial losses for individuals and organizations alike.
Phishing is another common cybercrime tactic, where scammers impersonate legitimate entities to trick individuals into revealing sensitive information, such as login credentials or credit card details. These deceptive schemes can result in severe financial and personal consequences for victims.
Online fraud, including various scams and schemes, poses significant risks. It includes activities like advance-fee fraud, Ponzi schemes, and online auction fraud. Victims may suffer substantial financial losses, and recovery can be challenging.
Cyberbullying and online harassment are personal cybercrimes that target individuals through hurtful, threatening, or offensive online behavior. These acts can have profound psychological and emotional effects on victims.
To combat cybercrime, individuals and organizations must prioritize cybersecurity. This involves using strong, unique passwords, enabling two-factor authentication, and keeping software and antivirus programs up to date. Cybersecurity awareness and education are crucial to recognizing and avoiding potential threats.
Governments and law enforcement agencies worldwide are also working to combat cybercrime by strengthening legislation and collaborating on international cybercrime investigations. However, prevention starts with individual responsibility and vigilance.
In conclusion, cybercrime is an evolving threat that affects us all in the digital age. As technology advances, so do the methods employed by cybercriminals. Staying informed, practicing safe online behavior, and implementing robust cybersecurity measures are essential steps to protect ourselves and our digital assets from the growing menace of cybercrime.
500-Word Essay on Cyber Crime:
In our increasingly interconnected world, where digital technology permeates every aspect of our lives, the threat of cybercrime has become a pressing concern. Cybercrime encompasses a wide range of illicit activities that occur in the digital realm, using computers, networks, and the internet as tools for criminal intent. This essay explores the evolving landscape of cybercrime, its various forms, the consequences it brings, and the measures individuals and organizations can take to combat this growing menace.
The Landscape of Cybercrime
Cybercrime is a multifaceted problem, constantly evolving as technology advances. It includes various forms, such as hacking, phishing, identity theft, online fraud, cyberbullying, and more. The motives behind cybercrime can be financial gain, political agenda, personal vendettas, or even thrill-seeking.
Hacking is one of the most prevalent forms of cybercrime. It involves unauthorized access to computer systems, networks, or data. Hackers exploit vulnerabilities to steal sensitive information, disrupt services, or distribute malware.
Phishing, on the other hand, is a deceitful practice where cybercriminals impersonate legitimate entities to trick individuals into revealing personal information or login credentials. This information is then used for malicious purposes, such as identity theft or financial fraud.
Identity theft is a pervasive cybercrime, with victims experiencing devastating consequences. Cybercriminals use stolen personal information to open fraudulent accounts, apply for loans, or engage in criminal activities, often leaving the victim to deal with the legal and financial fallout.
Online fraud includes various scams and schemes, such as Ponzi schemes, fake online marketplaces, and investment fraud. Victims of online fraud can lose substantial sums of money, often with little hope of recovery.
The social impact of cybercrime is also significant. Cyberbullying and online harassment have become increasingly common, especially among young people. The anonymity provided by the internet allows perpetrators to engage in hurtful behavior, leading to emotional and psychological distress for the victims.
The Consequences of Cybercrime
The consequences of cybercrime are far-reaching and extend beyond financial losses. Individuals can experience emotional distress, anxiety, and a loss of trust in online interactions. Businesses and organizations face significant financial and reputational damage when data breaches occur. Governments grapple with the challenge of protecting national security and critical infrastructure from cyberattacks.
Solutions and Prevention
To combat cybercrime effectively, individuals, organizations, and governments must work together and adopt proactive measures. Here are some key steps:
- Cybersecurity Awareness : Raising awareness about the risks of cybercrime is essential. Individuals should educate themselves about online threats and practice safe online behavior.
- Strong Passwords : Using strong, unique passwords for each online account is crucial. Employing password managers can help manage and generate complex passwords.
- Antivirus Software : Reliable antivirus and anti-malware software can detect and block malicious threats.
- Regular Software Updates : Keeping software, operating systems, and applications up to date is essential to patch security vulnerabilities.
- Two-Factor Authentication : Enable two-factor authentication (2FA) wherever possible to add an extra layer of security to your accounts.
- Secure Data Handling : Exercise caution when sharing personal information online. Only provide sensitive data on trusted websites.
- Cybersecurity Training : Organizations should invest in cybersecurity training for their employees to recognize and respond to threats effectively.
- Legal Frameworks : Governments need to enact and enforce comprehensive cybersecurity laws and regulations to deter cybercriminals.
- International Collaboration : Cybercrime often crosses international borders, so international collaboration among governments and law enforcement agencies is crucial.
The threat of cybercrime is an ever-growing challenge in our digital age. As technology advances, so do the methods and sophistication of cybercriminals. To effectively combat cybercrime, individuals, organizations, and governments must prioritize cybersecurity through awareness, education, and the implementation of robust security measures. Only by working together can we hope to mitigate the risks and consequences of cybercrime and ensure a safer digital future for all.
Check Other Essays:
FAQs on Cyber Crime Essay
What is cyber crime in short essay.
Cybercrime refers to criminal activities carried out using computers or the internet. Examples include online fraud, hacking, identity theft, and cyberbullying. These crimes can have serious consequences, such as financial loss, personal harm, or damage to one's reputation. To combat cybercrime, individuals must stay vigilant and follow online safety practices.
What is cyber security in 100 words?
Cybersecurity is the practice of safeguarding digital systems, networks, and data from a wide range of cyber threats and unauthorized access. It involves implementing measures and technologies to protect information integrity, confidentiality, and availability. Cybersecurity encompasses various aspects, including the use of strong passwords, encryption, firewalls, antivirus software, and intrusion detection systems. It is essential in today's interconnected world to mitigate the risks of data breaches, hacking, malware attacks, and other malicious activities that can lead to financial losses, reputational damage, and the compromise of personal and sensitive information. Cybersecurity is an ongoing effort to maintain the security and resilience of digital environments.
Is cyber crime bad?
Yes, cybercrime is bad as it can result in financial loss, emotional distress, and harm to individuals and organizations.
What are the causes of cybercrime?
The causes of cybercrime include technological vulnerabilities, lack of cybersecurity awareness, financial motivations, and anonymity provided by the internet.
Related content
Talk to our academic expert!
Language --- English Hindi Marathi Tamil Telugu Malayalam
Get access to free Mock Test and Master Class
Register to Get Free Mock Test and Study Material
Offer Ends in 5:00
Cybercrime: Victimization, Perpetration, and Techniques
- Published: 10 November 2021
- Volume 46 , pages 837–842, ( 2021 )
Cite this article
- James Hawdon ORCID: orcid.org/0000-0002-0273-2227 1
10k Accesses
4 Citations
5 Altmetric
Explore all metrics
Avoid common mistakes on your manuscript.
The creation of the World Wide Web revolutionized communication. At the turn of the twenty-first century, roughly 413 million people used the internet (Roser & Ortiz-Ospina, 2015 ). A mere 21 years later, nearly 4.7 billion people, or about 60% of the world’s population, actively use the internet (We Are Social, & DataReportal, & Hootsuite, 2021 ). The pace of innovation in information technology, from the introduction of email in the 1960s to the rise of multiple social media platforms in the early 2000s to the rise of the Internet of Things (Iot) and 5 g, has been astonishing. It is now almost inconceivable to imagine life without access to the internet. Yet the IT revolution, like all technological revolutions, has been a dual-edge sword. Indeed, the internet’s many benefits and drawbacks have been discussed in numerous forums, and these discussions will undoubtedly continue as long as we remain dependent on this technology. This special edition of the American Journal of Criminal Justice contributes to those discussions by considering one of the drawbacks: cybercime.
Cybercrime, or the use of computer technology or online networks to commit crimes, ranges from fraud and identity theft to threats and intimidation. Cybercrime and its many manifestations has clearly increased over the past 20 years. For example, cybercrime costs increased from approximately $3 trillion in 2015 to more than $6 trillion in 2021, and these are expected to increase to over $10.5 trillion by 2025 (Morgan, 2020 ). In the U.S. alone, approximately 23 percent of households experience some sort of cybercrime annually (Reinhart, 2018 ; Hawdon et al., 2020 ). Indeed, in the same way that larceny characterized the twentieth century, cybercrime is characterizing the twenty-first century (Albanese, 2005 ). And these facts just reflect the economic costs of cybercrime and do not account for the non-monetary harms caused by cyberviolence. Cyberstalking, online sexual exploitation, cyber-harassment and bullying, threats of violence, and online violent extremism are also commonly committed acts of cyberviolence (FBI, 2021 ).
In many ways, it is unsurprising that cybercrime has increased in recent years. As technology becomes more sophisticated, so do cybercriminals, and cybercriminals now target individuals, businesses, healthcare facilities, educational institutions, and governments. As more people engage in an ever-increasing variety of online activities and more businesses conduct their affairs online, it is predictable that there would be a rise in cybercrime. To use the familiar language of Routine Activity Theory (Cohen & Felson, 1979 ), we have a lot more suitable targets in insufficiently guarded space being victimized by an increasing number motivated offenders. It is also unsurprising that there is a growing body of literature dedicated to cybercrime as scholars scramble to understand the ever-evolving phenomena. Entire journals are now dedicated to its study, and new academic disciplines have been created to try to prevent it. While our understanding of cybercrime has accumulated quickly and impressively, there is so much about cybercrime that we still do not know. This special issue of the A merican Journal of Criminal Justice offers nine new articles to help fill that knowledge gap.
The articles included in this issue reflect three broad areas of cybercrime research: cybercrime victimization, cybercrime perpetration, and techniques and facilitators of cybercrime. While there is some overlap, the issue includes three papers focused on each of these three areas.
The first area covered in the special issue focuses on cybercrime victimization. This area has generated the most research to date. In part because victims of cybercrime are relatively easy to find, considerable research has been conducted on cybervictimization across a variety of cybercrimes. Three of the articles in this special issue focus on cybervictimization, and they add to the literature in interesting ways by providing cross-national perspectives, building on theoretical traditions, or providing systematic summaries of the state of field at this time.
The first article in this section by Michelle Wright and a team of colleagues investigates how adolescent from China, Cyprus, the Czech Republic, India, Japan, and the United States explain being a victim of cyberbully. The investigation compares if how adolescents explain victimization varies by setting (private vs. public), medium (offline vs cyber), and severity and if cultural differences alter these relationships. Their findings suggest the need for prevention and intervention efforts to consider the role of setting, medium, severity, and cultural values if they are to be successful.
The second paper focusing on victimization builds on the frequent finding that problematic social media use is associated with negative life experiences and provides empirical support for a theoretical link between problematic social media use and cybervictimization. The analysis, conducted by colleagues Eetu Marttila, Aki Koivula, and Pekka Räsänen, is framed in Routine Activity Theory/Lifestyle-Exposure Theory. The results indicate that not only is problematic social media use strongly correlated with cybervictimization in a between-subject analysis, but within-subject analyses also reveal that problematic social media use has a cumulative effect on victimization.
The third paper bridges research on cybercrime victimization and cybercrime perpetration and provides a glimpse at the state of knowledge about a specific form of cyberviolence. Catherine Marcum and George Higgins conduct a systematic review of literature investigating both offending and victimization of cyberstalking, cyberdating abuse, and interpersonal electronic surveillance. Using a number of electronic databases, the authors focus on 31 studies to identify correlates of involvement in these cybercrimes. Victims are disproportionately female. Other correlates of victimization include overall social media use, risky online behavior, and negative external factors such as being attached to abusive peers. Correlates of perpetration provide support for a number of leading criminological theories as perpetrators tend to have low levels of self-control, associate with delinquent peers, and have low levels of parental supervision. As more research is conducted, there is a great need for more systematic literature reviews so we can begin to better refine our understanding and identify the theoretical approaches that provide the most insight into the world of cybercrime.
There are another three articles included in this special issue that focus on cybercrime perpetration. All three articles test traditional criminological theories and find support for them. In the first, Adam Bossler uses Sykes and Matza’s ( 1957 ) techniques of neutralization to examine the effects of techniques of neutralization on college students’ willingness to commit cybercrime, specifically hacking websites to deface them or compromise foreign and domestic financial and government targets. An overall techniques of neutralization scale significantly predicts being willing to commit cyberattacks even after controlling for other relevant factors. In addition to the theoretical implications of finding strong support for Sykes and Matza’s framework, the findings also have implications for situational crime prevention efforts aimed at removing excuses for offenders.
In another article focusing on perpetration, Thomas Dearden and Katalin Parti use a national online sample of 1,109 participants and find strong support for social learning theory as measures of both online and offline social learning correlate with a measure of cyber-offending. However, the authors also argue that self-control will interact with social learning variables to further influence the likelihood of cyber-offending. Overall, they find that both social learning and self-control, individually and as an interaction, are good predictors of cyber-offending.
In the final article dedicated to investigating the perpetration of cybercrime, Ashley Reichelmann and Matthew Costello use a nationally representative sample to explore how various dimensions of American national identity relate to producing online hate materials. The analysis reveals that higher levels of salience and public self-regard are weakly related to producing online hate. However, the findings suggest that understanding the nuances of “what it means to be American” is important for fully understanding the phenomenon of cyberhate, especially in this polarizing time when what it means to “be American” is frequently questioned.
Another three articles deal with perpetrating cybercrimes or “pseudo-cybercrimes,” but their focus is on how these crimes are committed. That is, the investigations deal with using the Dark Web or the surface web to make illegal or pseudo-legal purchases of illegal or quasi-legal substances. In the first paper in the section, Eric Jardine provides a crime script for purchasing drugs on the Dark Web. The script involves four generic stages (i.e. Informational Accumulation; Account Formation; Market Exchange; Delivery/Receipt) and provides an opportunity to review known law enforcement interventions that have effectively targeted each stage of the script to reduce the use of these online markets. The paper highlights numerous steps that law enforcement could take to effectively reduce the illegal selling and purchasing of drugs on the Dark Web.
Next, Robert Perdue engages in green criminology and focuses on the illegal trade of endangered species. Noting that regulating this trade is a critical, and very difficult, challenge for conservationists and law enforcement agents, Perdue examines the role the Internet plays in critically endangered plant transactions, but instead of focusing on the Dark Web, he investigates eBay to understand the extent to which such trades occur in plain sight. He finds that nearly a third of the critically endangered plant species examined were for sale in some form on eBay. Yet, despite the evidence that there is a high degree of open trading in these species, the complexity of the international legal frameworks regulating these transactions makes it difficult to ascertain their legality. Nevertheless, at least a subset of these sales are probably unlawful.
Finally, J. Mitchell Miller and Holly Ventura Miller provide insight into the computer-facilitated gray market of pseudo-legal marijuana sales in Los Vegas, Nevada. The ethnographic study reveals how various cannabis products are illegally diverted from legal markets to the gray market, and how brokers use the Internet in clever ways to advertise their products and services to a public that is likely unaware that they are engaging in illegal activities by skirting the regulations and tight control of the legal market.
Taken together, these three papers highlight the tremendous difficulties with regulating e-commerce. While the Dark Web provides an environment to conduct illegal transactions with minimal risk, it turns out that the Dark Web may be unnecessary for many illegal cyber-purchases. Given the surface web is convenient, widely available, and scarcely policed, many cybercriminals simply commit their crimes in the open. Using the language of Routine Activity Theory again, the internet—Dark or Surface—is an environment largely devoid of capable guardians.
As a whole, I believe these nine papers speak to the current state and future promise of cybercriminology. Currently, we are building a large body of empirical studies that speak to patterns of victimization and perpetration. With respect to victimization, we have learned a lot about who is likely to be victimized and how the patterns of victimization vary by type of cybercrime. We also have a good understanding of the activities that increase the likelihood of victimization, the emotional and financial costs of being a victim, and how people view victims depending on the setting and type of victimization. The body of evidence supporting a slightly modified version of Routine Activity Theory/Lifestyle-Exposure Theory is increasingly impressive, and the papers by Marttila, Koivula, and Räsänen as well as the article by Marcum and Higgins offer additional support for aspects of this theoretical approach.
Similarly, our understanding of cybercrime perpetration has expanded exponentially in recent years. While finding samples of cybercriminals is always a challenge, the growing body of evidence suggests that the behavior of cybercriminals is largely explained by the same set of factors that can account for the behavior of more traditional criminals. That is, cybercriminals tend to have low levels of self and social control, are largely unsupervised, experience strains, and learn the how, when, and why of their crimes from their associates. The papers in this issue offer additional support for techniques of neutralization, social learning theory, and self-control theory. While there are nuanced differences in how some criminogenic factors play out in the virtual and offline worlds, our existing theories appear to be robust as many of our theories apply to both online and offline criminal behavior. A number of the differences that exist largely relate to the asynchronous nature of many online interactions. The fact that online interactions can occur synchronously as well as asynchronously expands our networks and provide additional opportunities for others beyond our immediate environment to influence us and for us to commit crimes. The full ramifications of these changes in social networks, criminogenic forces, and criminal opportunities are not understood; however, we understand these far better today than we did even just a few years ago.
We also have a far greater understanding of the techniques of committing cybercrimes. We know considerably more about the use of the Dark Web to find and purchase illegal goods and services, and we have learned that the Surface Web plays a significant role in computer-dependent crimes. Moreover, as the article by Miller and Miller highlights, information technology has helped blur the line between legal, pseudo-legal, and illegal behaviors. What work in this area really highlights is how difficult it is to monitor and police the internet. While there is certainly social control exercised on the internet, there are limits to the effectiveness of this control (see Hawdon et al., 2017 ). Yet, by understanding the patterns of victimization, the underlying causes of perpetration, and the techniques that facilitate cybercrime, we become better armed in designing strategies to prevent it, defend against it, mitigate its adverse effects, and prosecute those who commit it. All of the articles included in this issue further that understanding.
The Special Issue
The process of selecting the articles for this special issue was perhaps unusual but also rather intensive. The process began by me inviting a group of scholars to submit manuscripts for the special issue. I selected these scholars because I knew of their work and was confident they would submit quality papers that covered a wide range of topics in the area of cybercrime. After discussing their planned submissions with the authors to assure there would be good topic coverage, the authors submitted their paper. An anonymous scholar and I reviewed these initial submissions (the anonymous scholar served as a typical double-blind reviewer). Each contributing author also reviewed one or two of the included articles. Authors then revised their work based on the reviewers’ comments and resubmitted the papers. Each contributing author was then asked to read all nine revised papers. Then, the authors and I took advantage of the brief pause in the COVID-19 pandemic and gathered for a two-day workshop in Asheville, North Carolina as part of the Center for Peace Studies and Violence Prevention’s annual research workshop program. The lone exception to this was our Finnish colleagues who were unable to get a special visa to visit the U.S. at that time. These colleagues joined the workshop via Zoom. The authors/workshop participants then discussed and provided feedback on all of the articles. The authors then made final revisions to their papers based on these discussions. Thus, these papers have been through three rounds of revisions. As the editor of the special edition, I am proud of the finished product.
Albanese, J. S. (2005). Fraud: The characteristic crime of the 21st Century. Trends in Organized Crime, 8 , 5–16.
Article Google Scholar
Cohen, L. E., & Felson, M. (1979). Social change and crime rate trends: A routine activity approach. American Sociological Review, 44 (4), 588–608.
Federal Bureau of Investigation. (2021). 2020 Internet crime report . U.S. Government Printing Office.
Google Scholar
Hawdon, J., Costello, C., Ratliff, T., Hall, L., & Middleton, J. (2017). Conflict management styles and cybervictimization: An extension of routine activity theory. Sociological Spectrum, 37 (4), 250–266.
Hawdon, J., Parti, K., & Dearden, T. E. (2020). Cybercrime in America amid COVID-19: The initial results from a natural experiment. American Journal of Criminal Justice, 45 , 546–562.
Morgan, S. (2020). Cybercrime to cost the World $10.5 Trillion Annually by 2025. Cybercrime Magazine , November 13, 2020. https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
Reinhart, R. J. (2018). One in four Americans have experienced cybercrime. Gallup Politics . https://news.gallup.com/poll/245336/one-four-americans-experienced-cybercrime.aspx
Roser, M. H. R. & Ortiz-Ospina, E. (2015). "Internet". Published online at OurWorldInData.org. Retrieved from: ' https://ourworldindata.org/internet ' [Online Resource]
Sykes, G. M., & Matza, D. (1957). Techniques of neutralization: A theory of delinquency. American Sociological Review, 22 (6), 664–670.
We Are Social, & DataReportal, & Hootsuite. (2021). Global digital population as of January 2021 (in billions) [Graph]. In Statista . Retrieved September 24, 2021, from https://www.statista.com/statistics/617136/digital-population-worldwide/
Download references
Author information
Authors and affiliations.
Virginia Tech, Blacksburg, VA, USA
James Hawdon
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to James Hawdon .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Hawdon, J. Cybercrime: Victimization, Perpetration, and Techniques. Am J Crim Just 46 , 837–842 (2021). https://doi.org/10.1007/s12103-021-09652-7
Download citation
Received : 03 July 2021
Accepted : 03 August 2021
Published : 10 November 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s12103-021-09652-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Find a journal
- Publish with us
- Track your research
Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

Home — Essay Samples — Law, Crime & Punishment — Internet Privacy — Cyber Crime And Internet Privacy
Cyber Crime and Internet Privacy
- Categories: Cyber Crimes Internet Internet Privacy
About this sample

Words: 761 |
Published: Oct 2, 2020
Words: 761 | Pages: 2 | 4 min read
Table of contents
Introduction, identity theft, future protection.

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Dr. Karlyna PhD
Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
2 pages / 742 words
5 pages / 2327 words
3 pages / 1155 words
1 pages / 482 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Internet Privacy
With the rise of technology and the internet, children today have access to an unprecedented amount of information at their fingertips. This has sparked a debate among educators and parents about whether the internet is making [...]
The internet has become an integral part of our daily lives. With the rise of search engines like Google, accessing information has never been easier. However, as we become increasingly reliant on these tools, there is a growing [...]
The widespread use of the internet and the prevalence of digital content have revolutionized the way we consume and share information. However, this digital era has also brought about challenges in protecting the rights of [...]
Should there be a legal age limit for social media is a question that has gained significant prominence in our digital age. As the influence of social media continues to grow, concerns about its impact on young users' [...]
In the modern interconnected world, where the internet serves as both a conduit for information and a platform for social interaction, the issue of internet privacy has become paramount with the increase of new technology [...]
Cyber security or information technology security are the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation. There are four types of security [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Internet Crimes: Cyberstalking Essay
Introduction, cyberstalking, location and pursue of victims, laws and other methods of preventing cyberstalking, effects of cyber stalking, identify theft, laws and other methods of curbing internet identity theft.
How would a person feel if he or she wakes up one morning to find his or her identity stolen along with their money? Why would someone ever think of doing such a thing? It is noteworthy that criminals engage in different types of Internet crimes. As a result, there are plenty of criminals out there that would have no sympathy for their victims. Unfortunately, there are many places criminals can locate their victims without their knowledge.
Although social networking websites such as Facebook, MySpace and Tweeter have become very popular, these websites have also become the preferred places for criminals to find and hunt new victims. As these sites give criminals the opportunity to stalk, locate, probably pursue their victims and in some cases steal their identities.
Cyberstalking is considered a form of Internet crime that occurs when an individual’s safety, personal life, and freedom are taken away by anonymous methods or covert, then pursued and monitored, causing paranoia and fear. This is done by use of any forms of online, Internet or communication using a computer. Thus, it is performed by a group of individuals or an individual not known to the victim (Bocij, 8).
Cyberstalking is rather a new trend. With the declining price, thus augmented the accessibility of online services and computers, more persons are acquiring computers and accessing the Internet. This eventually increases susceptibility to abuse by Internet criminals such as stalkers (Bocij, 9). It is noteworthy that underage children have also fallen victim of cyberstalking. As a result, the criminals might use the children to commit such crimes on their behalf.
Cyberstalkers meet their victims in electronic mail, online chat sessions, communication board, and debate sites. Also, this crime has acquired many forms such as sending of the obscene or frightening e-mail, abuse in chat rooms, posting offensive messages on communication boards, transfer of electronic viruses, tracing and monitoring of an individual’s Internet activity, and identity theft.
Cyberstalking in children involves exposing them to pornography sites. Hence, Cyberstalking is a horrifying occurrence for victims (Siegel, 448).
Many cyberstalking activities develop into off-line stalking as the stalker can locate the victim. They achieve this by use of the personal information posted on the Internet sites by the victims (Jaishankar, 549). This is because; in most online chat rooms, the victims post their actual details on their profile page.
These include their real names, cellular phone numbers, physical address, and details of their family members. As a result, a victim may receive offensive and excessive phone calls, damage to property, intimidating or pornographic mail, trespass, and physical attack (Jaishankar, 549).
Cyber Stalkers use their technological links to pursue their victims through a variety of ways that are not restricted to; phony claims, obsessive monitoring, bootlegging of the victim’s unique ideas, gathering information for potential assault, soliciting for sexual activities and cracking computer access codes to hack or get IP address (Jaishankar, 549).
It is noteworthy that cyberstalking incidents are on the rise; above all, the victims themselves fan these indecent activities as they keep responding, to the numerous messages and attention they receive from these criminals. Thus, the stalkers develop an interest in the victims thereby continuing to pursue them (Jaishankar, 549).
It is noteworthy that personal information is becoming readily accessible to many people, who use the Internet and other sophisticated technology; thus, state legislators are dealing with the trouble of stalkers who pester and intimidate their victims over the Internet. Stalking laws and other statutes illegalizing stalking deeds presently in effect in many states may by now deal with this crime (Bocij, 163).
States have started to address the use of electronic equipment for stalking purposes by implementing conditions barring such action in both anti-stalking and harassment legislation. Furthermore, few states, such as Arizona, Alabama, Illinois, New York, Connecticut, Hawaii, and New Hampshire have added ban against any form of irritating electronic contact in harassment laws.
Similarly, Oklahoma, Alaska, Wyoming, and lately, California, have included electronically converse messages as demeanor comprising stalking in their laws that fight anti-stalking. However, some states have enacted both laws (Bocij, 163). Similarly, other states have put in place laws that forbid all internet crimes. Thus, identity theft is constituted in these laws.
Recent federal law has established measures to deal with cyberstalking, as well. For example, the act protecting women against the violence that was enacted in 2000 placed cyberstalking as a constituent of federal laws. Similarly, other federal legislation that deals with cyberstalking has been set up lately, but no such actions have yet been endorsed. Consequently, there is a deficiency of legislation at the federal level to address this crime, leaving the bulk of legislative embargo against cyberstalking at the state level (Bocij, 163).
Apart from the laws enacted, there are other methods of preventing cyberstalking. These are the Internet user based solutions and Internet provider based solutions. Internet user based solutions involve Internet users who employ chat rooms to communicate with strangers. Thus, such Internet users should seize from posting their actual details on the profile pages. Above all, information like names, phone number, physical address, and family information should be confidential, thus only given to the people one knows (Pittaro, 2007).
Internet provider based solutions involve Internet users purchasing soft wares from Internet providers. It is notable that these soft wares are used to block redundant electronic contact. It is thus advisable to seek help from the Internet provider. As a result, there exist online agreement policies restricting such misuse of service (Pittaro, 2007).
Victims experience emotional and physical instabilities in life, as well as a mental disturbance. Some of these include fear for one’s safety, anxiety, hyper vigilance, and nightmares. As a result, the victims might consider seeking professional assistance like counseling. Also, family and friends support is needed.
Identity theft is a crime that occurs when one’s details are stolen and used without his consent. As a result, it can be used to commit a crime or steal money from the victim. Personal details are used when individuals want to access certain services.
Thus, with such information, a criminal can steal money from the victims without their knowledge, whereby they can run up their victims existing credit card account (May, 10). It is evident that these activities take place without the victim’s knowledge. At times, these criminals can go as far as wiping out their victim’s bank accounts by authorizing electronic transactions in their victim’s name (May, 10).
The Internet is providing avenues through which these criminals can access an individual’s personal information. Hence, they accomplish this by using online chat sessions and soft wares that crash key loggers on the computer, thus transmitting personal details stored in the computers. Online businesses store clients personal details on their web sites. As a result, such details are easily accessed by criminals.
These Internet criminals may set up a counterfeit organization website to trick the clients into submitting their personal information. Further more, these are information which the legitimate organization already possesses.
Internet identity theft has discouraged individuals from engaging in online monetary transactions as they consider it an unsafe mode of fiscal transaction basing on the recent cases of Internet identity theft (May, 10).
Identity fraud has become rampant in the United States, as a result, in 1998, there was the ratification of the Identity Theft and Assumption Deterrence Act (ITADA) meant to bring justice to the criminals and protection of the victim. More often, Internet identity theft constitutes online transactions, and criminals are always unknown. Thus, tracing of the criminals is tedious but not impossible.
The ITADA considers Internet identity theft as it comes with a 30-year jail sentence. Two states of Wisconsin and California have established a privacy protection office that encourages citizens to seize from engaging in identity theft and help victims recover.
States have enacted laws that deal with identity theft; similarly, in some, identity theft is dealt with in the attorney generals office. Essentially, Identity theft laws are quite new. Thus more amendments are required (May, 13).
Other than the laws enacted to fight identity theft, users must also take care of themselves. As everyone is susceptible to Internet identity theft, the same way, an individual walks along dangerous back streets in town with their wallet. The only difference is that one can not physically see Internet criminals. Thus, the best way to avoid these criminals is for Internet users to apply caution when submitting their details to people and organizations online.
Clients who bank online are advised to employ protection devices that detect any attempts to use their password. Thus, there are banks that offer free downloadable detection devices to clients.
Above all, those who purchase goods online must first confirm the security mark displayed on the screen before submitting their account details. As a result, the use of a debit card is preferred when making online, fiscal transactions. Hence, even when criminals get hold of the information, their expenditure is limited. As a result, they can not put an individual into debt.
It is advisable for individuals to open a different account for transacting online purchases and maintain the other account other functions. This will prevent hackers from accessing details of the other accounts as they are not anywhere on the Internet. Most importantly, one should not engage in online monetary transactions that raise doubts. This is considered the best way to curb Internet criminals (May, 23).
There is no professional and truthful company that will ever ask for clients’ information via an electronic mail. Thus, Individuals are supposed to think before passing over personal details to any company on the Internet (May, 23). After all, the relevant banks or companies already have the details if one uses pay pal. It is recommended that the internet users delete all the cache in their computers. Also, temporary internet files should be deleted, as criminals use them as to getting ways to hack into computers.
Internet users are advised to make sure; they include those people they trust as friends in the online chat rooms. Furthermore, individuals should not leave their computers unattended to or with strangers. As this will make the criminals access their personal information. Above all, Individuals are also advised not to tolerate the criminals in the chat rooms. Also, the Internet connection should always be terminated when not in use as leaving the connection in idle mode will make hackers gain remote access to computers.
Cyberstalking is a crime on the rampage in the United States. Thus, many citizens fall victim, resulting in psychological trauma and fear. On the other hand, identity theft has also taken a new course, with criminals upgrading their means of conducting fraud. As a result, citizens may lose money and acquire debts. Hence, the rising cases of cyberstalking and identity theft have made different states enact laws that fight this crime.
Since the enactment of laws to fight internet crimes, it has been noted that these crimes have reduced significantly. However, there are some criminals who continue to engage in this vise. It is so sad and disappointing as children have also fallen victims of these internet crimes. It is noteworthy that criminals exploit them without their knowledge.
Bocij, Paul. Cyber stalking: harassment in the Internet age and how to protect your family . New York: Greenwood Publishing Group, 2004 Pp 8-177.
Jaishankar, K. International Perspectives on Crime and Justice . London. Cambridge scholars publishing. 2009 Pp 549.
May, Johnny. Johnny May’s Guide to Preventing Identity Theft . Security Resources Unlimited, LLC, 2004 Pp 10-27.
Pittaro, Michael. Cyber stalking : an analysis of online harassment and intimidation . Open access. 2007. Web.
Siegel, Larry. Criminology. California: Cengage Learning, 2008 Pp 448.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2022, May 2). Internet Crimes: Cyberstalking. https://ivypanda.com/essays/internet-crimes/
"Internet Crimes: Cyberstalking." IvyPanda , 2 May 2022, ivypanda.com/essays/internet-crimes/.
IvyPanda . (2022) 'Internet Crimes: Cyberstalking'. 2 May.
IvyPanda . 2022. "Internet Crimes: Cyberstalking." May 2, 2022. https://ivypanda.com/essays/internet-crimes/.
1. IvyPanda . "Internet Crimes: Cyberstalking." May 2, 2022. https://ivypanda.com/essays/internet-crimes/.
Bibliography
IvyPanda . "Internet Crimes: Cyberstalking." May 2, 2022. https://ivypanda.com/essays/internet-crimes/.
- Victimization of Individuals Online: Cyber-Stalking and Prostitution
- The Effects of Cyber-Bullying and Cyber-Stalking on the Society
- Cyberstalking and Cyberbullying Laws in Kentucky
- Ethical Issues Associated with Social Media
- Cybercrime and Law Enforcement Challenges
- Social Networking Threats for Children
- Cyber Law, Cyber Compliance and Information Assurance
- Bullying and Cyberbullying in Modern Society
- Psychological Disorders Problem
- What Is Stalking?
- American Police Community Relations
- Criminal Justice Workplace Management
- Organizational Behavior Concepts in the Criminal Justice
- Criminology: Critique of the Current Rehabilitation Options
- Prisons and Jails: Learning the Difference

World-first “Cybercrime Index” ranks countries by cybercrime threat level
Following three years of intensive research, an international team of researchers have compiled the first ever ‘World Cybercrime Index’, which identifies the globe’s key cybercrime hotspots by ranking the most significant sources of cybercrime at a national level.
The Index, published today in the journal PLOS ONE , shows that a relatively small number of countries house the greatest cybercriminal threat. Russia tops the list, followed by Ukraine, China, the USA, Nigeria, and Romania. The UK comes in at number eight.

‘The research that underpins the Index will help remove the veil of anonymity around cybercriminal offenders, and we hope that it will aid the fight against the growing threat of profit-driven cybercrime,’ Dr Bruce said.
‘We now have a deeper understanding of the geography of cybercrime, and how different countries specialise in different types of cybercrime.’
‘By continuing to collect this data, we’ll be able to monitor the emergence of any new hotspots and it is possible early interventions could be made in at-risk countries before a serious cybercrime problem even develops.’
The data that underpins the Index was gathered through a survey of 92 leading cybercrime experts from around the world who are involved in cybercrime intelligence gathering and investigations. The survey asked the experts to consider five major categories of cybercrime*, nominate the countries that they consider to be the most significant sources of each of these types of cybercrime, and then rank each country according to the impact, professionalism, and technical skill of its cybercriminals.

Co-author Associate Professor Jonathan Lusthaus , from the University of Oxford’s Department of Sociology and Oxford School of Global and Area Studies, said cybercrime has largely been an invisible phenomenon because offenders often mask their physical locations by hiding behind fake profiles and technical protections.
'Due to the illicit and anonymous nature of their activities, cybercriminals cannot be easily accessed or reliably surveyed. They are actively hiding. If you try to use technical data to map their location, you will also fail, as cybercriminals bounce their attacks around internet infrastructure across the world. The best means we have to draw a picture of where these offenders are actually located is to survey those whose job it is to track these people,' Dr Lusthaus said.
Figuring out why some countries are cybercrime hotspots, and others aren't, is the next stage of the research. There are existing theories about why some countries have become hubs of cybercriminal activity - for example, that a technically skilled workforce with few employment opportunities may turn to illicit activity to make ends meet - which we'll be able to test against our global data set. Dr Miranda Bruce Department of Sociology, University of Oxford and UNSW Canberra
Co-author of the study, Professor Federico Varese from Sciences Po in France, said the World Cybercrime Index is the first step in a broader aim to understand the local dimensions of cybercrime production across the world.
‘We are hoping to expand the study so that we can determine whether national characteristics like educational attainment, internet penetration, GDP, or levels of corruption are associated with cybercrime. Many people think that cybercrime is global and fluid, but this study supports the view that, much like forms of organised crime, it is embedded within particular contexts,’ Professor Varese said.
The World Cybercrime Index has been developed as a joint partnership between the University of Oxford and UNSW and has also been funded by CRIMGOV , a European Union-supported project based at the University of Oxford and Sciences Po. The other co-authors of the study include Professor Ridhi Kashyap from the University of Oxford and Professor Nigel Phair from Monash University.
The study ‘Mapping the global geography of cybercrime with the World Cybercrime Index’ has been published in the journal PLOS ONE .
*The five major categories of cybercrime assessed by the study were:
1. Technical products/services (e.g. malware coding, botnet access, access to compromised systems, tool production).
2. Attacks and extortion (e.g. denial-of-service attacks, ransomware).
3. Data/identity theft (e.g. hacking, phishing, account compromises, credit card comprises).
4. Scams (e.g. advance fee fraud, business email compromise, online auction fraud).
5. Cashing out/money laundering (e.g. credit card fraud, money mules, illicit virtual currency platforms).
DISCOVER MORE
- Support Oxford's research
- Partner with Oxford on research
- Study at Oxford
- Research jobs at Oxford
You can view all news or browse by category
Essay on Cyber Crime
Cyber crime is the result of technological advancements. It is a dangerous crime involving the use of internet and computers. Cybercrime is undetectable at the initial phase but comes to notice with the consequences. Through this, the illegal transfer of data and information is made, which is of confidential value to an individual or a group.
Short and Long Essays on Cyber Crime in English
Essay on Cyber Crime for students of class 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11 and class 12 in English in 100, 150, 200, 250, 300, 500 words. Also find short Cyber Crime essay 10 lines.
Cyber Crime Essay 10 Lines (100 – 150 Words)
1) The crime done with the help of a computer network is termed as cybercrime.
2) Cybercrime can harm your privacy and security.
3) Cybercrime is an illegal act that tends to hack your private data.
4) Cybercriminals try to gain money through illegal methods.
5) Phishing, DoS attack, spoofing, etc are some common cybercrimes.
6) With the increasing use of the internet, cybercrimes are on the rise.
7) Cybercrime makes the victim helpless by stealing their money and credentials.
8) One should be conscious while using the internet.
9) Cybercrimes can affect a person, an organization, or even the government.
10) Cybercrime is the misuse of advanced technologies.
Essay 1 (250 Words) – Cyber Crime: A Threat to Society
Introduction
Crime is a word used for wrong deed or offence, but when it comes to cybercrime then, it can be defined as a crime done by internet to cause an immeasurable loss to the individual, organization, or the government. Cyber crime is a punishable offence committed by cyber criminals .
Cyber Crime – A Threat to Society
Cyber crime is the criminal act which takes place over the internet through computers as tools or targets or other smart devices meant for making our work easier. The hacker or criminals are having various motives of the crime. They may be involved to cause a loss to an individual, some organization or government.
Several examples of cyber crime include frauds, identity theft, cyberstalking, creating and sending malware like viruses for destroying the systems or steal the data to make money. People involved in such activities find them as an easy way of making money. Even many of the well-educated and knowledge full persons are involved in such activities. Instead of using their mind in a positive way they employ themselves in cyber crime activities. Day by day this is becoming a great threat to our society and nation.
Cybercrime is the most prevailing crime in the present scenario, done through the internet. It causes a severe loss to the victim. Therefore some of the measures should be taken by us to avoid such crimes. The vigilant behaviour and following the safety protocols are only helping aids which can reduce the occurrence of cybercrime.
Essay 2 (400 Words) – Cyber Crime: Classification and Impacts
Man has been innovative and inventive by nature, since early ages. The different needs gave rise to new devices, tools, and technologies. Technology is also a discovery of man for making work easier. The advancement in technology is useful on one side and on the other side has some devastating effects. Cybercrime is also a negative aspect of these technological developments. The individual, organization and groups are involved in committing such criminal activities.
Classification of Cyber Crimes
- Crime Against an Individual – Crime committed against an individual by use of an individual’s credit card details, confidential data and sending of spam emails. This crime is mainly done for making money.
- Crime Against an Organization – This is done against a firm, company or organization to get unauthorized access to the data. This is done either to reveal the important data and employee details of the company or for money-making.
- Crime Against Government – This is the crime against the nation, by getting access to the national data and records. This crime is of main concern as it concerned with the safety of the people of the nation.
Impacts of Cyber Crime
Cyber crime has ruined up the lives of many. The people involved in cyber crime are called hackers.
- If we discuss on an individual level, the people affected with this are still trying to adjust the loss. Some have opted to commit suicide. The ultimate loss of money and any data which is confidential make the person helpless and left out in a painful situation.
- On an organization level, the loss is made by stealing the data of the company or destroying the system by malware so that it may not work till the terms and conditions of the criminal get fulfilled. The companies are at a greater loss as their strategies and important data is stolen and leaked out.
- The government is also the victim of this offence. Much confidential data is leaked as the result of cyber crime at the government level, risking the nation’s sovereignty. This is a serious issue as it may happen that the lives of people of the nation are threatened and frightened. The loss can be economical too. Many lakh and crore have been lost from the nation because of these cyber crimes.
Cyber crime is an offence related to the use of the internet. It is dealt with some important information to be leaked in public or money-making in an easy way. Therefore we should be practicing some safety measures and security applications to prevent the crime.
Essay 3 (500 – 600 Words) – Cyber Crime
Cybercrime can be mentioned as illicit use of the internet and computers. The computers are either the target of the crimes or used as a weapon for the crime. These crimes have become a common part of our daily lives. Each and every day one or the other person is becoming the victim of cybercrime. Internet is accessed by a number of people at the same time for various purposes, these hackers make their way out of these opportunities.
Different Types of Cyber Crimes
- Phishing – This involves obtaining the personal information of the user by sending spam emails or by means of phishing website which resembles the same as authorized website.
- Identity Theft – This involves getting the information about credit or debit cards or bank details, further unwanted money can be easily deducted after the information is hacked.
- Malware Attacks – Malware is the hostile software which is designed to damage the computer or systems. This is done to access meaningful information or for doing some crime by using that system.
- ATM Frauds – The ATM machine is totally hacked in this crime. The criminals have developed the way to access both the data on the card along with the pin, further they are successful in making the duplicate of the cards and use the same to withdraw money.
- Cyber Stalking – The criminal is involved in following the person through online measures. They can even send malware to damage the systems to get the exact information. It involves harassment of the user.
- Pornography – The act of presenting sexual activity containing video, through pornographic websites.
- Spoofing – In this, an email is received and appears to be from some authentic source, but it is not the same. It is corrupted.
- Piracy – It is unauthorized access to the information which is confidential. Many of the times the government websites are hacked and files are pirated containing important data.
The First National Conference on National Crime Investigation and Crime Forensics
- Our nation India, for the first time had a national conference on national crime investigation held in New Delhi at headquarters of CBI (Central Bureau of Investigation) on 4 and 5 September 2019.
- The main motive of the conference was to create a common platform for the investigators, forensic teams and other officials involved to discuss various methods and ways to tackle the cyber-related crimes. The conference was of 2 days i.e. 4th and 5th September.
Cyber Crime Awareness
Different security measures should be followed to be safe from the dreadful act of cyber crime.
- Strong passwords should be used. The password must be a complex one, could not be possible to guess.
- Use antivirus programmes to keep the system free of malware.
- Continuously update the system.
- Be vigilant and use the presence of mind to avoid identity thefts.
- Make your children aware of the internet, so that they can state any misuse or harassment if they are going through.
- Maintain privacy settings over social media.
Cyber Security
Cyber security is saving our system, network, devices, and programmes from the attack of malicious software. Thus the illegal accessing of data can be stopped.
Importance – The information regarding any important issue of the nation or any data which is meant to be used personally, if gets shared will create several problems. Therefore if there will be a security check imposed at several levels, the information and important data can be saved from leaking.
Types of Cyber Security
- Network Security – Protects the network from being attacked by malware and thus using a secure network .
- Cloud security – Meant for safeguarding the data in the cloud resources .
- Information security – Helps in protecting the data from unauthorized or illegal access.
- End-user security – The user should be conscious of while inserting any external devices in the system, opening any mail or links.
- Application security – helps in keeping the system and software free of any threat .
Cyber crime is spreading its arms day by day. The most appropriate way of being safe from becoming the victim of its ill effects is following security measures. There are various ways by which we can protect our confidential information from being leaked. We should always focus on awareness as – ‘Prevention is better than cure’, especially when the cure is not available.
FAQs: Frequently Asked Questions
Ans . Cybercrime started in the world in the 1970s.
Ans . Ian Murphy was the first cybercriminal in the world.
Ans . Karuppannan Jaishankar is regarded as the father of Cyber criminology.
Ans . The Yahoo v. Akash Arora case was the first cybercrime case in India that happened in 1999.
Ans . The United States of America has the highest number of cybercrimes in the world.
Related Posts
Essay on digital india, cashless india essay, essay on child is father of the man, essay on causes, effects and prevention of corona virus, essay on dr. sarvepalli radhakrishnan, durga puja essay, essay on summer vacation, essay on my plans for summer vacation, essay on holiday, leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

- Follow UNSW on LinkedIn
- Follow UNSW on Instagram
- Follow UNSW on Facebook
- Follow UNSW on WeChat
- Follow UNSW on TikTok

World-first Cybercrime Index ranks countries by cybercrime threat level
Photo: terovesalainen - stock.adobe.com
The new index shows where cyber criminals are, and the impact they are having.
An international team of researchers has compiled the first ever World Cybercrime Index, which identifies the globe’s key cybercrime hotspots by ranking the most significant sources of cybercrime at a national level.
The Index, released today after three years of intensive research, shows that a relatively small number of countries house the greatest cybercriminal threat. Russia tops the list, followed by Ukraine, China, the USA, Nigeria, and Romania. Australia comes in at number 34.
Co-author of the study, Dr Miranda Bruce from UNSW Canberra and the University of Oxford, said the study will enable the public and private sectors to focus their resources on key cybercrime hubs and spend less time and funds on cybercrime countermeasures in countries where the problem is not as significant.
“The research that underpins the Index will help remove the veil of anonymity around cybercriminal offenders, and we hope that it will aid the fight against the growing threat of profit-driven cybercrime,” Dr Bruce said.
“We now have a deeper understanding of the geography of cybercrime, and how different countries specialise in different types of cybercrime.
“By continuing to collect this data, we’ll be able to monitor the emergence of any new hotspots and it’s possible early interventions could be made in at-risk countries before a serious cybercrime problem even develops.
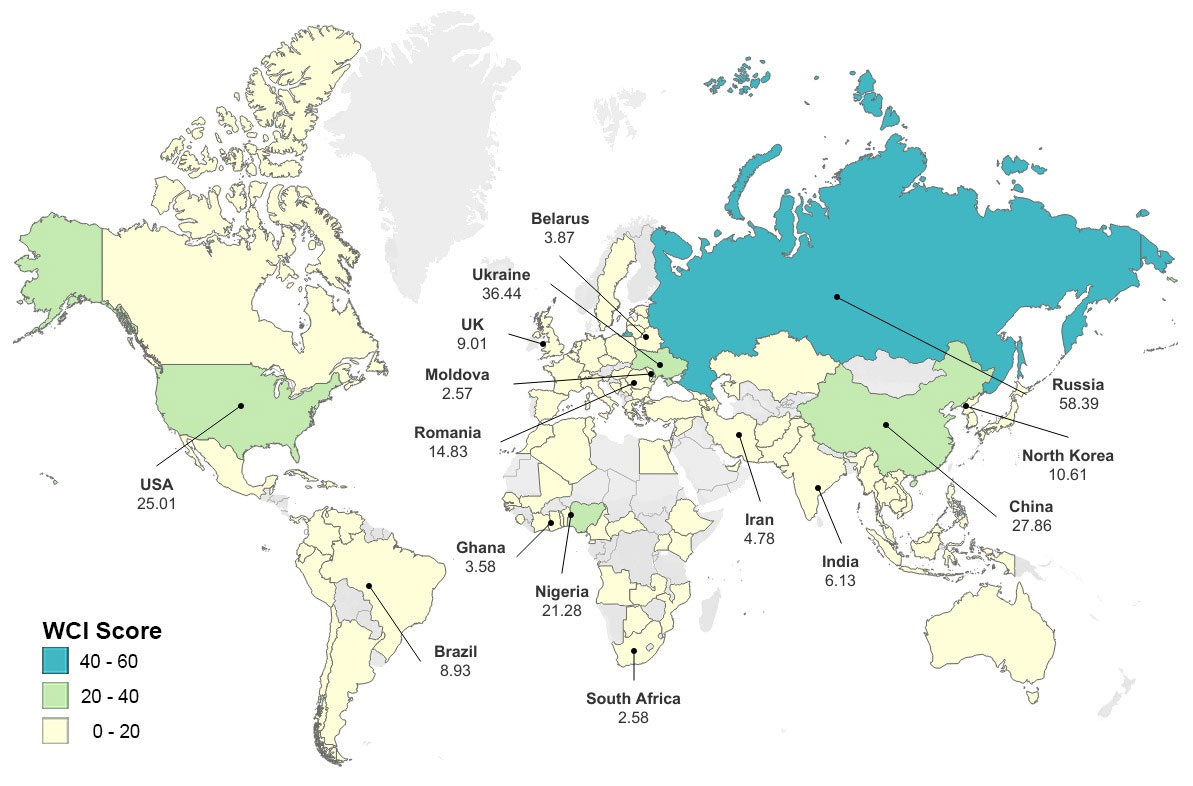
“For the first time we have reliable data on the location of cybercriminals, and we also have a way to measure their impact. Government agencies and private enterprises tasked with tackling cybercrime now have a much better understanding of the scale of the problem in their own backyard.
“Up until now, you had to be an experienced cybercrime investigator to know where cybercriminals actually live, but now we can share that information with the public, governments and businesses. It means that we now have a much clearer picture of the extent of the problem and can target our efforts in the right direction.”
The data that underpins the Index was gathered through a survey of 92 leading cybercrime experts from around the world who are involved in cybercrime intelligence gathering and investigations. The survey asked the experts to consider five major categories of cybercrime, nominate the countries that they consider to be the most significant sources of each of these types of cybercrime, and then rank each country according to the impact, professionalism, and technical skill of its cybercriminals.
Locating the cybercriminals
Another co-author of the study, Associate Professor Jonathan Lusthaus from the University of Oxford in the UK, said cybercrime has largely been an invisible phenomenon because offenders often mask their physical locations by hiding behind fake profiles and highly technical protections.
“Due to the illicit and anonymous nature of their activities, cybercriminals cannot be easily accessed or reliably surveyed. They are actively hiding. If you try to use technical data to map their location, you will also fail, as cybercriminals bounce their attacks around internet infrastructure across the world. The best means we have to draw a picture of where these offenders are actually located is to survey those whose job it is to track these people,” Dr Lusthaus said.
Government agencies and private enterprises tasked with tackling cybercrime now have a much better understanding of the scale of the problem in their own backyard. Dr Miranda Bruce
Joint author of the study, Professor Federico Varese from Sciences Po in France, said the World Cybercrime Index is the first step in a broader aim to understand the local dimensions of cybercrime production across the world.
“We are hoping to expand the study so that we can determine whether national characteristics like educational attainment, Internet penetration, GDP or levels of corruption are associated with cybercrime. Many people think that cybercrime is global and fluid, but this study supports the view that, much like forms of organised crime, it is embedded within particular contexts,” Professor Varese said.
The World Cybercrime Index has been developed as a joint partnership between the University of Oxford and UNSW and has also been funded by CRIMGOV , a European Union-supported project based at the University of Oxford and Sciences Po. The other co-authors of the study include Professor Ridhi Kashyap, from the University of Oxford and Professor Nigel Phair from Monash University.
‘ Mapping the global geography of cybercrime with the World Cybercrime Index ’ is available online now.
Media enquiries
For more information on this story or to arrange interviews, please contact:
Dr Miranda Bruce
For media support in Australia:
Damon Whittock, UNSW Canberra
Phone: +61 (0)404 489 376
Email: [email protected]
For media support in the UK:
Dr Caroline Wood, University of Oxford
Phone: +44 01865 280534
Email: [email protected]

Share this story
- Share this page on Email
- Share this page on Facebook
- Share this page on Twitter
- Share this page on LinkedIn
- Share this page on WhatsApp
- Share this page on FacebookMessenger
- Share this page on WeChat
- Share this page on Copy
Related stories

Cracking the code: why people fall for scams

The $500 million ATO fraud highlights flaws in the myGov ID system. Here's how to keep your data safe

Australia needs a robust cybersecurity overhaul – not whack-a-mole bans on apps like TikTok

Australia should adopt 'gold standard' in data laws after Optus leak
- Share full article
Advertisement
Subscriber-only Newsletter
Ross Douthat
Is the internet the enemy of progress.

By Ross Douthat
Opinion Columnist
It’s unusual when you find a strong dose of pessimism about the future of technological progress highlighted by one of the world’s leading techno-optimists. But if you follow the combative venture capitalist Marc Andreessen on X, you would have seen him giving wide circulation to this passage from Michael Crichton’s 1995 “Jurassic Park” sequel “The Lost World,” in which Crichton’s ever-prescient Dr. Ian Malcolm warns that the internet will put an end to human progress:
“It means the end of innovation,” Malcolm said. “This idea that the whole world is wired together is mass death. Every biologist knows that small groups in isolation evolve fastest. You put a thousand birds on an ocean island and they’ll evolve very fast. You put ten thousand on a big continent, and their evolution slows down … And everybody on Earth knows that innovation only occurs in small groups. Put three people on a committee and they may get something done. Ten people, and it gets harder. Thirty people, and nothing happens. Thirty million, it becomes impossible. That’s the effect of mass media — it keeps anything from happening. Mass media swamps diversity. It makes every place the same. Bangkok or Tokyo or London: there’s a McDonald’s on one corner, a Benetton on another, a Gap across the street. Regional differences vanish. All differences vanish. In a mass-media world, there’s less of everything except the top ten books, records, movies, ideas. People worry about losing species diversity in the rain forest. But what about intellectual diversity — our most necessary resource? That’s disappearing faster than trees. But we haven’t figured that out, so now we’re planning to put five billion people together in cyberspace. And it’ll freeze the entire species … Everyone will think the same thing at the same time. Global uniformity.”
This is the kind of quotation I would normally highlight at the end of this newsletter, in my “This Week in Decadence” feature. But it’s 29 years old, written when the true internet era was still just a gleam in Al Gore’s eye.
And as prophecies go, it’s pretty impressive — up there with Malcolm’s rather more famous prediction about just how bad things would get in John Hammond’s amusement park. The quote doesn’t capture everything about the current age (more on the prophecy’s limits in a moment), but it predicted quite a lot: the popular styles that seem stuck on repeat ; the mid-list musicians and novelists disappearing amid the dominance of megastars; the dwindling interest in new music as the algorithm steers everyone to the Beatles; the “ age of average ” in everything from art and architecture to hotel décor , auto design and Instagram looks.
You could further argue that the passage predicted the Great Stagnation that Tyler Cowen identified in 2011, the productivity slowdown and disappointing economic growth that followed the initial 1990s-era internet boom. You could say that it predicted the remarkable ideological groupthink of the liberal Western leadership class over the same period, the rise of Davos Man and then the heightened elite conformism of the woke era. Finally, you could say that it predicted the striking phenomenon of birthrates declining globally, not just locally, in nearly every country and region touched by the iPhone version of modernity.
This last point is central to the updating of the Malcolm/Crichton thesis offered recently by the George Mason University professor Robin Hanson. Writing for Quillette, he argues that globalization and homogenization have reduced cultural competition in roughly the way that the “Lost World” passage describes. Instead of a bevy of cultural models competing the way private-sector firms do and dying off quickly if they don’t adapt successfully, globalization gives us a tendency toward “macro culture” — a few large-scale cultural models, or maybe eventually even just a global monoculture. This has initial benefits but long-term drawbacks:
The recent big jump in the size of macro cultures has boosted within -culture innovation, powering peace, trade and fast-growing wealth. As a result, our few huge cultures today suffer much less from famine, disease or war. But because of these effects, we should expect to now get much less selection of cultures, and thus less long-run innovation. It’s not just that we’re forgoing opportunities to improve our macro cultures. Selection may also be too weak — at least in the short run — to cancel the mistakes of cultural drift. Shouldn’t we expect that macro cultures, when selection is weak, will drift into dysfunction just as firm cultures do?
This kind of maladaptive cultural drift, Hanson argues, is what’s happening with below-replacement fertility. For a variety of social and economic reasons, the developed world has converged on a reproductive model that’s already leading to rapid population aging and could lead — with South Korea as the blinking-red indicator light — to outright population collapse. This all but guarantees that technological and economic progress will slow down, but Hanson goes further and argues that depopulation may turn the world over to “insular cultures like Mennonites, Amish, and Haredim,” which by “doubling every two decades,” he writes, “look on track to replace our mainline civilization in a few centuries.”
For him, this is basically a fall-of-Rome scenario, with insular religious minorities playing the role of the early Christians and the rest of us cast in the role of the decadent Roman elites. And Hanson suggests that it’s extremely difficult for a culture that’s become universal but also maladaptive to escape this kind of fate, to get back to dynamism without first going through a crackup or collapse that yields more competition in the wreckage.
Now let’s consider the alternative to this kind of pessimism. When he posted the Ian Malcolm quotation, Andreessen did not endorse it; rather, he caveated it, saying that Crichton “was right about this. But also wrong. The internet is also the land of a million shards, cultures, cults.” Meaning that while there is a powerful tendency toward cultural homogenization and global uniformity, the online era also allows for more of Hanson’s within-culture innovation, if you know where to look for it: more conformism at the center, maybe, but more ferment at the fringe; more debilitating groupthink but also more eccentricity and radical experiments.
To develop this argument, you might say that while Crichton’s character got a lot of big things right, his prophecy underestimated the human tendency to react against stagnation and decadence once it begins to set in.
So the past decade or so has delivered polarization and division as well as incurious conformism, with populist rebellions and socialist revivals and extreme-outsider ideas coming into fashion rather than everyone thinking the same thing at the same time — and these have been mediated and encouraged by the same internet that’s encouraged homogeneity.
Outside the West, there are now various explicit attempts to escape the universal politics of global liberalism — the various visions of what Bruno Maçães calls “ civilization states ” in China and India and Russia, the quest for non-Western models of 21st-century development and power. Some of these paths are grim and tyrannical, but they aren’t just seeking sameness and convergence. For good or ill, they’re aiming at the strong cultural competition that Hanson thinks we need.
Meanwhile within the Western world, America, at least, has slipped somewhat free from the Great Stagnation. For all its flaws, Silicon Valley remains an exceptional culture, the American South and West are booming, the artificial intelligence breakthroughs are real, however uncertain their consequences. There are forms of spiritual ferment ( charismatic revivals , pagan experiments, the neo-traditionalism of younger Christians) at work even as the old Christian institutions continue to decline. Even American cinema is showing a few big bright spots after its Covid-era diminishment.
If the rule of a globalized, digitally united world is maladaptive conformity, in other words, you can also see some notable exceptions — enough of them, maybe, to say that we aren’t just waiting for the Amish to take over, that Andreessen’s plethora of shards, cultures and cults will suffice to deliver renewal from within.
What makes me a bit less optimistic than the venture capitalist is my sense that it’s hard for the shards and subcultures to scale up. On the largest scale, the alternatives to the globalized macro culture often seem to be either fake or failing: Russia is a gangster state, not a civilizational alternative; China is plunging into the low-fertility future faster than the West, and so on.
But on the smaller scale, the smallness is the problem. You can have a micro culture that resists the macro culture, an exceptionalism in one town, one region, one college, one very online community, but if we aren’t going to just sink into civilizational old age, at some point this nonconformism has to break out and actually change the world. You need your weird art scenesters to reshape the movie business, your trads to build cathedrals as well as home-school co-ops, your high-fertility exceptions to retain their fecundity while adding more non-zealous normies to their ranks, your populists and radicals to actually govern effectively, not just gripe and critique. And so far, we have only scanty models of this happening.
(This issue applies to the Amish and Mennonites as well. I don’t think insular religious subcultures could take over the West the way Christians took over the Roman Empire, because their current success depends on their insularity. To exert real influence of the kind the early Christians gained, they would have to shed some of that separatism, and once they did so, they would immediately be subject to the same homogenizing forces as everyone else.)
I also worry — and this is a running disagreement I’ve had with Andreessen — that the pull of online reality and headset-mediated simulations almost automatically carries us toward a variation on the Crichton dystopia, a version of stagnation that’s sustained by the illusion of exploration, an age of fundamental conformity disguised by the personal tailoring of everyone’s private holodeck.
Andreessen often worries , and reasonably so, about how A.I. could be co-opted by a culture of conformity, deployed as a tool of ideological groupthink , the chat prompt’s minders herding everyone into the same narrow zone of speech and thought. But A.I. also seems like it could carry us more organically into a future of personalized illusions, comfortable numbness, simulated relationships and precision-guided digital addictions just as easily as into a future of A.I.-enabled artistic masterpieces, cancer cures, self-driving cars and Mars expeditions.
I think there’s hope of escape from the Crichton prophecy. But if we don’t escape, these will be the terms of our imprisonment: a wired-together environment that freezes us in place while being so perpetually stimulating and distracting that only the dropouts and the despairing notice what’s really going on.
Razib Khan on how cities make and break civilizations.
Alexandra Walsham on early modern atheism .
Michael Brendan Dougherty on the inescapable 1990s .
Josh Dzieza on the World Wide Web in the depths of the sea .
Ruxandra Teslo on a proposed cure for cavities .
Tyler Cowen interviews Peter Thiel.
Advertisements for Myself
I’ll be speaking at Flagler College in St. Augustine, Fla., this coming Tuesday, April 23, at 7 p.m., on the future of the Catholic Church. The event is free and open to the public.
Ross Douthat has been an Opinion columnist for The Times since 2009. He is the author, most recently, of “The Deep Places: A Memoir of Illness and Discovery.” @ DouthatNYT • Facebook
Watch CBS News
Criminal exploits of Scattered Spider earn respect of Russian ransomware hackers
By Bill Whitaker , Aliza Chasan , Graham Messick, Jack Weingart
April 14, 2024 / 7:32 PM EDT / CBS News
In the shadowy corners of the dark web, young hackers from the U.S., U.K., and Canada met and teamed up with Russian ransomware hackers, becoming powerful partners in crime.
In the last year, ransomware hackers have targeted hospitals, pharmaceuticals, tech companies, and even Las Vegas' biggest hotels and casinos. Bryan Vorndran, the FBI's top cyber official, called ransomware an "enormous problem," and says no sector, company, or type of organization is off limits to hackers. There are estimates that global losses from ransom payments exceed $1 billion a year.
"Any way you look at the numbers, it's a problem for the global economy, and for the U.S. economy, and for the security of the United States," Vorndran said.
Scattered Spider hackers
A loose-knit group of predominantly native-English speaking hackers, called Scattered Spider by the FBI, are behind some of the recent ransomware attacks, Vorndran said. The group is also known as Star Fraud, UNC3944, and Octo Tempest. Scattered Spider hackers are considered experts in social engineering.
"Part of their success is because they are fluent in Western culture. They know how our society works," said Allison Nixon, chief research officer with the cybersecurity firm Unit 221B. "They know what to say to get someone to do something."

Scattered Spider is just one of many illicit hacking groups, all part of a sprawling collection of online criminals calling themselves "the Community," or "the Com" for short, Nixon said. She describes it as a new, but surprisingly disruptive online subculture. Members of the Com have hacked into companies like Microsoft, Nvidia and Electronic Arts, among others.
The number of people involved has exploded since 2018 from only a few hundred to thousands, Nixon said.
"They connect over the internet. Social spaces where people hang out. Gaming servers," Nixon said. "It's almost analogous to, like, maybe the back alley where the bad kids hang out but on the internet."
Those involved are largely males under the age of 25, though Nixon said teens as young as 13 have also been involved in pulling off major crimes.
- Infiltrating ransomware gangs on the dark web
Members communicate on messaging apps like Telegram – their chatter a toxic stew of racism and sexism. They often boast about the money they've scammed and how menacing they are.
"There are these toxic online spaces where young people can socialize and mingle with criminals and gang members," Nixon said. "And the end result of all of this is this online subculture has formed that glorifies crime, that measures one's personal worth by how much harm they can cause the world."
Hackers team up
Scattered Spider is one of the most sophisticated offshoots of the Com. Their criminal exploits have caught the attention of cybersecurity companies and earned the respect of other criminal hackers, including one of the most notorious Russian ransomware gangs, BlackCat, also known as ALPHV, who saw the young, native-English-speaking Westerners as a potential "force multiplier" for their ransomware attacks.
"Historically speaking, Russian cyber criminals did not like working with Western cyber criminals," Nixon said. "There was not only a language barrier, but also they kinda looked down on them and viewed them as unprofessional."
Scattered Spider uses its English and social engineering skills to break into companies and other entities. BlackCat provides its experience, platform and its malware, which has been used in some of the most consequential ransomware attacks in recent history.
Cybersecurity researchers believe that BlackCat is made up of former members of the Russian cybercriminal hacking group DarkSide/BlackMatter, which was responsible for the 2021 attack on Colonial Pipeline that caused gas shortages up and down the East Coast. And according to an FBI advisory, "Many of the developers and money launderers for BlackCat/ALPHV are linked to DarkSide/BlackMatter, indicating they have extensive networks and experience with ransomware operations."

"It's called rebranding," said Jon DiMaggio, who is chief security strategist for cybersecurity company Analyst1. DiMaggio investigates ransomware and the relationships between different cybercriminal groups.
"With the ransomware as a service model, you have that core gang that's the service provider that is providing all these resources and attack services to make their job easy. And then you have the hackers who are the contractors that work for them," said DiMaggio.
Long-established Russian gangs, like BlackCat, offer their services — including the latest malware and experience negotiating ransoms and laundering money — to affiliate hacking groups, like Scattered Spider. If a victim pays a ransom, the funds are split.
Ransomware attacks bring companies to knees
Scattered Spider and BlackCat both claimed credit for the September 2023 ransomware attack on MGM Resorts , which cost the hotel and casino giant more than $100 million. It disrupted operations at a dozen of the most renowned hotels and casinos on the Las Vegas Strip: including MGM Grand, Aria, Mandalay Bay, New York-New York and the Bellagio.
Anthony Curtis, who publishes the "Las Vegas Advisor," was in an MGM property during the ransomware attack. He says people were left dumbfounded as thousands of slot machines suddenly stopped functioning properly.
"So all of a sudden now people are going 'How do I get my money? What's wrong?' And the people were sitting there waiting and couldn't get paid," Curtis said.
As a result of the cyberattack, elevators were malfunctioning, parking gates froze, and digital door keys wouldn't work. As computers went down, reservations locked up and lines backed up at the front desks.
"Anything that required technology was not working," Curtis said.
MGM Resorts declined a request for an interview, but at a conference a month after the hack, CEO and President Bill Hornbuckle admitted the disruptions were devastating.
"For the next four or five days with 36,000 hotel rooms and some regional properties, we were completely in the dark," Hornbuckle said at the conference.
The hackers demanded $30 million to unlock MGM's data. The company refused, but they still paid a price – an estimated $100 million in lost revenue, plus millions more to rebuild their servers.
Hackers got inside MGM's network using social engineering. They zeroed in on an employee, gathering information from the dark web and open sources, like LinkedIn. Next, a smooth-talking hacker impersonated the employee and called the MGM tech help desk. The hacker convinced tech support to reset his password. With that, the hacker was inside MGM's computers and unleashed destructive malware.
Curtis said it was the cyber criminals' version of an "Ocean's Eleven" heist.
"These hackers were able to turn the tables," Curtis said. "The casinos have their systems. They have their protections. They have their experts. They have their security. These guys are better."

Later, MGM's biggest competitor, Caesars , admitted it also suffered a social engineering attack around the same time. It's suspected it was by the same group. Caesars reportedly paid a $15 million ransom and did not suffer any disruptions.
"From an FBI perspective, our position is we recommend a ransom not be paid," Vorndran said. "But we understand it's a business decision during a time of crisis."
He declined to say if any arrests had been made in the Las Vegas cases.
Worries for future
Ransomware hacks have been growing more costly and disruptive every year and cyber security researchers fear it's going to get worse.
The Russian government provides a safe haven for Russian ransomware gangs, said DiMaggio. He added that as long as the hackers don't target organizations in Russia, they don't get prosecuted.
"It's crazy, right? That's how it works though," DiMaggio said.
The most successful Russian gangs are run like legitimate companies with easy-to-navigate online platforms. The leadership are people in their 30s and 40s, DiMaggio said. They often have a financial background.
"There are people that specialize in developing malware and ransomware, and they're in very high demand," DiMaggio said.
Russian ransomware has become such a threat that the elite cyber warriors at the National Security Agency have joined the fight. Rob Joyce, who was the NSA's director of cybersecurity before retiring last month, said the Colonial Pipeline attack was a wakeup call.
"It caused us to step back and decide that we had to put more resources into this foreign threat," Joyce said. "That's the value NSA can bring is, we can identify people, specific people involved in some of these activities."
The NSA helped identify the Russian hacker responsible for the Colonial Pipeline attack. And in January 2022, after months of negotiations, Russia arrested him and other accomplices. But it all came undone five weeks later.

"Following the Ukraine invasion, those people were let out of jail," Joyce said.
And now, Russian hackers have teamed up with the young native-English speaking hackers of Scattered Spider. The FBI's Vorndran calls it an evolution of cybercrime.
"I think that it's important to know that we are against a very capable set of adversaries, they're very good at their work," he said. "We're also very good at our work."
In January, the FBI arrested a 19-year-old from Florida named Noah Urban on charges of stealing $800,000 in cryptocurrency. Urban has pleaded not guilty. Cyber investigators have tied him to Scattered Spider, but so far not to the casino heist. The Scattered Spider hackers who did pull off the attack on MGM are still online – hiding in plain sight – in unholy alliance with Russian hackers. Nixon calls what happened in Las Vegas a harbinger.
"The level of cybercrime has risen to the point where it feels overwhelming," she said. "And every year it gets worse. And it feels like as defenders, it's almost like we're winning every battle and losing the war."

Bill Whitaker is an award-winning journalist and 60 Minutes correspondent who has covered major news stories, domestically and across the globe, for more than four decades with CBS News.
More from CBS News

Tiny piece of technology roiling U.S. tensions with China, Russia

Kevin Hart's journey from stand-up sets in bowling alleys to global tours

Researchers examine painful history of Nazi camps built on British soil

Victims of Nazi concentration camps built on British island being counted

IMAGES
VIDEO
COMMENTS
500+ Words Essay on Cyber Crime. Cyber Crime Essay- Everybody thinks that only stealing someone's private data is Cyber Crime.But in defining terms we can say that 'Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone's data or trying to harm them using a computer.
100 Words Essay on Cyber Crime. Cybercrime is the most discussed problem in the twenty-first century. The usage of cellphones and the internet is increasing dramatically over the world, which is generating questions about consumers' security and privacy. Because of this, it is crucial for all users to understand cybercrime and security.
To tackle cybercrime by raising awareness among the masses, cyber security training, implementing robust security protocols, and enacting comprehensive cybercrime laws. Essay on Cybercrime in 200 Words. Cybercrime is a criminal activity done online using a computer, network and internet.
Essay on Cyber Crime. Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about ...
116 CyberCrime Topics & Essay Samples. Updated: Mar 2nd, 2024. 9 min. If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper. We will write. a custom essay specifically for you by our professional experts. 809 writers online.
When any crime is committed over the Internet it is referred to as a cyber crime. Cyber crimes have become a real threat today and are quite different from old-school crimes, such as robbing, mugging or stealing. ... To conclude the essay, cyber crime has become great threat to mankind. Protection against cybercrime is a vital part for social ...
8 Prompts for Essays About Cyber Crime. 1. The Future of Cyber Crime. In your essay, research the current state of cybercrime, the capabilities of the criminals that perform it, and the laws made to prevent it. Cybercrime continuously evolves as more people learn about its potential and countermeasures.
Cyber Crime Essay: A crime that involves a network and a computer is known as computer-oriented crime or cybercrime. Such a crime affects the security of everything, might be a person, institution or even a nation. ... It has been recorded that in 2018 The Internet Crime Complaint Sector received 351,937 complaints alone. Sine, everything you ...
2. Proliferation and Commercialization (1990s-2000s) Explosion of Malware: Malicious software, including viruses, worms, and trojans, became more prevalent in the 1990s. Commercial Exploitation: Cyber Crime became increasingly profit-driven with the advent of financial fraud, identity theft, and the rise of the cyber black market. 3.
Speech on Cyber Crime; 250 Words Essay on Cyber Crime Introduction. Cybercrime, an umbrella term encompassing a variety of offenses committed using digital technology, poses a significant threat to the modern world. As our reliance on technology increases, so does the potential for misuse, leading to a surge in cybercrimes. The Nature of Cybercrime
Effects of Cyber Crime on Social Media. 2 pages / 933 words. The issue of cyber Crime has risen rapidly as a result of increased access to computers in the recent years compared to the past. Cyber Crime refers to criminal activities, which are carried out by the use of computers or the internet.
Types of cybercrime. Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense ...
100-Word Essay on Cyber Crime. Cybercrime, the dark underbelly of the digital world, is on the rise. It encompasses a range of illegal activities conducted through computers and the internet, including hacking, phishing, and online fraud. Cybercriminals exploit vulnerabilities for financial gain or personal satisfaction, causing harm to ...
Cybercrime, or the use of computer technology or online networks to commit crimes, ranges from fraud and identity theft to threats and intimidation. Cybercrime and its many manifestations has clearly increased over the past 20 years. For example, cybercrime costs increased from approximately $3 trillion in 2015 to more than $6 trillion in 2021 ...
Cybercrime - against individuals, corporates, etc.and Cyberwarfare - against a state. Cyber Crime. Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime.
The accessibility and efficiency of the Internet and information technologies in supporting the infrastructure of societal institutions also fosters the development of cybercrime and deviant subcultures. Cybercrime is crime that is mediated by networked technology (Wall, Citation 2007). Old crimes such as theft, fraud, and harassment find new ...
Abstract. The Internet is a resource that connects people from all over the world. In most parts of the world, the internet is free. With free internet, however, there comes a price. A lot of data from the internet is stored onto a local server, so it is vulnerable to hackers. Without proper knowledge and education, people are bound to lose ...
It is widely accepted that cybercrime is highly prevalent and increasing. A recent report suggests that Internet Service Providers (ISPs) record around 80 billion automated scans daily by online perpetrators with the aim of identifying targets for cybercrime (Lewis, 2018), and in the year ending September 2019, 1 million 'computer misuse' crimes were reportedly committed against households ...
This essay focuses on the development and future of Internet law in the light of Internet related crimes, together with case law, and discusses how the historical traditions of law are ill-equipped to deal with the modern concepts associated with cyber-law. The first section of this essay discusses the growth of EU legislation surrounding the ...
This chapter covers the definitions, types, and intrusions of e-crimes. It has also focused on the laws against e-crimes in different countries. Cybersecurity and searching methods to get secured ...
Cyberstalking. Cyberstalking is considered a form of Internet crime that occurs when an individual's safety, personal life, and freedom are taken away by anonymous methods or covert, then pursued and monitored, causing paranoia and fear. This is done by use of any forms of online, Internet or communication using a computer.
The study 'Mapping the global geography of cybercrime with the World Cybercrime Index' has been published in the journal PLOS ONE. *The five major categories of cybercrime assessed by the study were: 1. Technical products/services (e.g. malware coding, botnet access, access to compromised systems, tool production). 2.
Essay 1 (250 Words) - Cyber Crime: A Threat to Society. Introduction. Crime is a word used for wrong deed or offence, but when it comes to cybercrime then, it can be defined as a crime done by internet to cause an immeasurable loss to the individual, organization, or the government. Cyber crime is a punishable offence committed by cyber ...
Cyber Crime Essay. Cyber Crime is described as criminal activity committed via use of electronic communications with respect to cyber fraud or identity theft through phishing and spoofing. There are many other forms of cyber-crime also such as harassment, pornography etc. via use of information technology. 729 Words.
Joint author of the study, Professor Federico Varese from Sciences Po in France, said the World Cybercrime Index is the first step in a broader aim to understand the local dimensions of cybercrime production across the world. "We are hoping to expand the study so that we can determine whether national characteristics like educational attainment, Internet penetration, GDP or levels of ...
Overall, the article concludes that their effective use can significantly enhance cyber fraud prevention while promoting sustainable and secure development. Cyber fraud is an emerging issue somewhere it prohibits the essential trust of society, as it is essential to ensure protection and promote sustainability and security. AI and blockchain technologies offer advanced defense strategies and ...
Cybersecurity investigators worry ransomware attacks may worsen as young, native-English speaking hackers in the U.S., U.K. and Canada team up with Russian hackers.
By Ross Douthat. Opinion Columnist. It's unusual when you find a strong dose of pessimism about the future of technological progress highlighted by one of the world's leading techno-optimists ...
Police have taken down a gang accused of using a technology service that helped criminals use fraudulent text messages to steal from victims. They have arrested 37 people worldwide and are ...
Young hackers in the U.S., U.K., and Canada, all part of a loose-knit group called Scattered Spider, are working with a notorious Russian ransomware gang to attack Western companies.