Security-Assignments.com
Content for an information security management course.
By Drs. Dave Eargle and Anthony Vance
Learn more · Adoption guide

Book and Film List
Reading topics, in-class activities.
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
security-assignments
Repositories.
This organization has no public members. You must be a member to see who’s a part of this organization.
Top languages
Most used topics.
for Education
- Google Classroom
- Google Workspace Admin
- Google Cloud
Easily distribute, analyze, and grade student work with Assignments for your LMS
Assignments is an application for your learning management system (LMS). It helps educators save time grading and guides students to turn in their best work with originality reports — all through the collaborative power of Google Workspace for Education.
- Get started
- Explore originality reports
Bring your favorite tools together within your LMS
Make Google Docs and Google Drive compatible with your LMS
Simplify assignment management with user-friendly Google Workspace productivity tools
Built with the latest Learning Tools Interoperability (LTI) standards for robust security and easy installation in your LMS
Save time distributing and grading classwork
Distribute personalized copies of Google Drive templates and worksheets to students
Grade consistently and transparently with rubrics integrated into student work
Add rich feedback faster using the customizable comment bank
Examine student work to ensure authenticity
Compare student work against hundreds of billions of web pages and over 40 million books with originality reports
Make student-to-student comparisons on your domain-owned repository of past submissions when you sign up for the Teaching and Learning Upgrade or Google Workspace for Education Plus
Allow students to scan their own work for recommended citations up to three times
Trust in high security standards
Protect student privacy — data is owned and managed solely by you and your students
Provide an ad-free experience for all your users
Compatible with LTI version 1.1 or higher and meets rigorous compliance standards
Product demos
Experience google workspace for education in action. explore premium features in detail via step-by-step demos to get a feel for how they work in the classroom..
“Assignments enable faculty to save time on the mundane parts of grading and...spend more time on providing more personalized and relevant feedback to students.” Benjamin Hommerding , Technology Innovationist, St. Norbert College
Classroom users get the best of Assignments built-in
Find all of the same features of Assignments in your existing Classroom environment
- Learn more about Classroom
Explore resources to get up and running
Discover helpful resources to get up to speed on using Assignments and find answers to commonly asked questions.
- Visit Help Center
Get a quick overview of Assignments to help Educators learn how they can use it in their classrooms.
- Download overview
Get started guide
Start using Assignments in your courses with this step-by-step guide for instructors.
- Download guide
Teacher Center Assignments resources
Find educator tools and resources to get started with Assignments.
- Visit Teacher Center
How to use Assignments within your LMS
Watch this brief video on how Educators can use Assignments.
- Watch video
Turn on Assignments in your LMS
Contact your institution’s administrator to turn on Assignments within your LMS.
- Admin setup
Explore a suite of tools for your classroom with Google Workspace for Education
You're now viewing content for a different region..
For content more relevant to your region, we suggest:
Sign up here for updates, insights, resources, and more.

- Comic Books
- Premiere Photos
- Special Event Photos
- Rock/Pop/Etc.
- Soundtracks
- The Dork Side
Home » About
Latest Buzz
EMAIL Questions? Press Releases? Pitches? Scoops? Contact us directly at:
EDITORIAL OFFICE 24307 Magic Mountain Pkwy Suite #210 Valencia, CA 91355
EDITOR A.C. Ferrante
CONTRIBUTING EDITORS Pamela Harland Carl Cortez Peter Brown Paul Zimmerman
STAFF WRITER Abbie Bernstein
CONTRIBUTING WRITERS T.K. Dehn Sean Elliott Emerson Parker Rachel Reitsleff Sue Schneider
COLUMNIST Sonia Mansfield
- Click to share on Facebook (Opens in new window)
- Click to share on Twitter (Opens in new window)
- Click to share on Pinterest (Opens in new window)
- Click to share on Reddit (Opens in new window)
- Click to email a link to a friend (Opens in new window)
- Click to print (Opens in new window)
- Click to share on Tumblr (Opens in new window)

Leave a Comment
XHTML: You can use these tags: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <s> <strike> <strong>
Assignment X Poll
Who is the scariest horror icon?
- Art the Clown from TERRIFIER
- Candyman from CANDYMAN
- Chucky from CHILD'S PLAY
- Freddy Krueger from A NIGHTMARE ON ELM STREET
- Jason from FRIDAY THE 13th
- Jigsaw from SAW
- Leatherface from THE TEXAS CHAINSAW MASSACRE
- Michael Myers from HALLOWEEN
- Norman Bates from PSYCHO
- Pinhead from HELLRAISER
View Results
- Polls Archive
24 ABC American Idol Angel Blu-ray Bones Buffy the Vampire Slayer CBS Dancing With the Stars David Boreanaz Doctor Who DVD DWTS Emily Deschanel Eric Kripke Exclusive exclusive interview Fox Fox Network FX Game of Thrones HBO interview Jared Padalecki Jensen Ackles Michaela Conlin Movie Review Movies Movie Soundtracks NBC Recap review science fiction Season 1 Season 2 Showtime soundtrack Supernatural Syfy TCA television Television Critics Association The CW True Blood TV review
WP Cumulus Flash tag cloud by Roy Tanck requires Flash Player 9 or better.

News | Reviews | Interviews | Columns | Photos | Videos
Movies | Television | Music | Blu-ray/DVD | Books
Supernatural | Buffy the Vampire Slayer | Chuck | Doctor Who | Glee | Fringe | Harry Potter
Scream 4 | Smallville | Spider-Man 4 | Tangled | TRON: Legacy | V

COPYRIGHT © 2010 - 2024, MIDNIGHT PRODUCTIONS, INC. ALL RIGHTS RESERVED. PRIVACY POLICY & TERMS OF USE
You’re viewing a preview of this course. Log in or sign up for full access.
Security Agreements, Pledge Agreements, and Assignments
This preview has ended..
Sign up for free to see the full course.
- Posted by Admin
- On July 21, 2020
- no comments
Create New Scheduled Training Assignment – PSAT (Setup)
Question – How do I create a new Scheduled Training assignment?
- Navigate to Training
- Select Scheduled under Manage Training Assignments
- Choose +Create Assignment
- Enter a unique Name for the new training assignment. This name is used internally to identify the assignment and will not display to the end user. It will appear on reports and on the Scheduled Assignment table for reference.
- The Type defaults to Scheduled .
Note: If you change your mind at this point and you want to add a Duration Assignment , select Duration from the drop-down list. The fields on the page will change accordingly.
- If you are using email notifications, the email will be sent at 12:01 AM Eastern Time on the selected date
- If the start date is today, the assignment notification will go out within 30 minutes of creation
- If you do not want the notification to be sent immediately, set the Start Date in the future
- This is the date that is marked as the deadline for users in their My Training view
- It is also when the Assignment is closed and no further users or groups can be added to it
- There is a 30-day grace period for users to continue taking the assignment after the due date
- Select a Training Assignment notification option from the drop-down list. You can choose to not send a notification, always send the active notification, or select from the list of approved notifications.
- If one of the approved notifications is selected, you have the option to click the Preview Template link to view the template and/or send a test email to a specified email address.
- If you want to create a reminder email(s), see Create Reminder If not, skip this section and go to the Modules section.
- Type all or part of the module name in the Find item by name search box. As you type, modules matching the search criteria entered thus far will begin displaying. To clear contents entered in the box, click the X at the end of the search box.
- If you want all modules in this assignment to be completed prior to any other assignment in the user’s training list, then select the High priority assignment check box. Otherwise, leave it blank. Assignments that are not marked as a high priority will be locked until all high priority ones are completed first.
- Click the + sign next to each module under Available Modules to add it to the Included Modules list on the right. You can also double-click on the module name to add it to the Included Modules list. The number of lessons in each module displays to the right of the module name.
Note: You can only select one module at a time.
You can now preview modules by clicking on the module name blue. The module will open in another browser window where you can page through it. You can also proceed with cloning the module from here.
- If you want the modules to show in a specific completion order, select the Enforce module completion order box, and use your mouse to click on and drag the modules up and down into the appropriate order
- In the Users section, click on the box(es) next to the user(s) you want to add to the assignment
- If you click in the check box next to Email , you can also select or deselect all of your users or select or deselect all users on the specific page.
- Click the Filter icon. When selecting users, there is the ability to filter based on Date Range (when the user was added to the system) or Groups added through Essentials User Management.
- Select one of the existing blue links (Today, Last 7 Days, or Last 30 Days).
- Select a date range using the calendar by clicking on the first date and the last date of the range.
- Enter the date or date range in the text box. If you enter a date in the textbox, use the MMM-DD-YYYY (three-character month abbreviation followed by a hyphen, then the two-digit date followed by a hyphen, and then the four-digit year). For example, May-13-2019. If adding a date range, add a space after the first date in the range followed by a hyphen and then the ending date in the range. For example, May-13-2019 – May 16-2019.
- You can also select or deselect all of your users or select or deselect all users on the specific page once you filter on Groups
- Select +Add to Assignment.
- Click Submit.
- Your assignment will now show in the Manage Training Assignments table.
IFSEC Insider is part of the Informa Markets Division of Informa PLC
- INFORMA PLC
- INVESTOR RELATIONS
IFSEC Insider is operated by a business or businesses owned by Informa PLC and all copyright resides with them. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. Registered in England and Wales. Number 8860726.

- Anticipate London
- Advertise With Us
- Video Surveillance
- Access Control
- Intruder Alarms
- Corporate Security
- Physical Security
- Borders & Infrastructure
- Guarding & security officers
- Cyber Security
- Smart Buildings
- Fire safety news
- Building safety
- Fire protection
- Fire prevention
- Fire extinguishers
- Critical national infrastructure
- Leisure & sport
- Residential
- Installer zone
- IFSEC Interviews
- Influencers hub
- Influencers in fire 2022
- Influencers in security 2022
- The IFSEC Insider Podcast
- IFSEC Insider Influencers in Security & Fire
- Critical Conversations
- IFSEC Directory
- CCTV Technologies Guide
- Control Rooms
- Video Analytics
- Thermal Cameras
- Video Surveillance Manufacturers
- Safe Cities
- Drone Security
- Perimeter Security
- Security Officer
- Fire Safety Manufacturers
- Residential Housing
- IFSEC London
- IFSEC London Exhibitors
- FIREX London
- FIREX Exhibitors
- IFSEC India
- IFSEC Philippines
- IFSEC Southeast Asia
- Security Companies
- Mergers & Acquisitions
- Hanwha Techwin
- Arecont Vision
- The Fire Industry Association (FIA)

IFSEC Insider
Author Bio ▼
Sign up to free email newsletters
- Enter your email address.. *
- Country/Region --- Please Select --- Afghanistan Albania Algeria American Samoa Andorra Angola Antigua and Barbuda Argentina Armenia Australia Austria Azerbaijan Bahamas Bahrain Bangladesh Barbados Belarus Belgium Belize Benin Bermuda Bhutan Bolivia Bosnia and Herzegovina Botswana Brazil Brunei Bulgaria Burkina Faso Burundi Cambodia Cameroon Canada Cape Verde Cayman Islands Central African Republic Chad Chile China Colombia Comoros Congo, Democratic Republic of the Congo, Republic of the Costa Rica Côte d'Ivoire Croatia Cuba Curaçao Cyprus Czech Republic Denmark Djibouti Dominica Dominican Republic East Timor Ecuador Egypt El Salvador Equatorial Guinea Eritrea Estonia Ethiopia Faroe Islands Fiji Finland France French Polynesia Gabon Gambia Georgia Germany Ghana Greece Greenland Grenada Guam Guatemala Guinea Guinea-Bissau Guyana Haiti Honduras Hungary Iceland India Indonesia Iran Iraq Ireland Israel Italy Jamaica Japan Jordan Kazakhstan Kenya Kiribati North Korea South Korea Kosovo Kuwait Kyrgyzstan Laos Latvia Lebanon Lesotho Liberia Libya Liechtenstein Lithuania Luxembourg Madagascar Malawi Malaysia Maldives Mali Malta Marshall Islands Mauritania Mauritius Mexico Micronesia Moldova Monaco Mongolia Montenegro Morocco Mozambique Myanmar Namibia Nauru Nepal Netherlands New Zealand Nicaragua Niger Nigeria North Macedonia Northern Mariana Islands Norway Oman Pakistan Palau Palestine, State of Panama Papua New Guinea Paraguay Peru Philippines Poland Portugal Puerto Rico Qatar Romania Russia Rwanda Saint Kitts and Nevis Saint Lucia Saint Vincent and the Grenadines Samoa San Marino Sao Tome and Principe Saudi Arabia Senegal Serbia Seychelles Sierra Leone Singapore Sint Maarten Slovakia Slovenia Solomon Islands Somalia South Africa Spain Sri Lanka Sudan Sudan, South Suriname Swaziland Sweden Switzerland Syria Tajikistan Tanzania Thailand Togo Tonga Trinidad and Tobago Tunisia Turkey Turkmenistan Tuvalu Uganda Ukraine United Arab Emirates United Kingdom United States Uruguay Uzbekistan Vanuatu Vatican City Venezuela Vietnam Virgin Islands, British Virgin Islands, U.S. Yemen Zambia Zimbabwe
- I have read, understood and consent to your Privacy Policy .
Transforming security: The role of secure IoT connectivity within fire and security applications
Whitepaper: enhancing security, resilience and efficiency across a range of industries, do your security officers use assignment instructions.

As the managing director of a security consultancy business, and having worked in the security sector for 20 years now, I’ve seen many changes within the industry.
With the relatively recent introduction of the Security Industry Authority’s Approved Contractor Scheme (ACS), a standard has at long last been set. That standard has been much needed in the security sector.
In particular, the ACS has highlighted the importance of processes and documents in your business. It has made this mandatory in some cases, for example when it comes to site assignment instructions.
I have long held the belief that site assignment instruction booklets are one of the most important documents a security officer has access to while on duty (if not the most important). During my time working with all sizes of security company, I have come across many variations of site assignment instructions. There have been the two-page documents scribbled all over as practices have altered, all the way up to vast tomes designed to impress clients rather than aid the officer.
The feedback I have received about assignment instructions when speaking to officers has surprised me. In some cases, such little importance is given to these documents that certain security officers don’t even know what they are, and why they should be used.
On the other hand, we have officers who are frustrated as their limited assignment instructions document does not aid them in their job. At the other end of the scale, I’ve met with officers who are baffled by a 100-page collective that bears little relevance to their job and duties.
In our experience, assignment instructions are a constant reference for the security officer and every bit as important as his or her licence and uniform. Having passed Basic Job Training, the assignment instructions become a familiar document which includes such important information as duties for the security staff, client details and emergency procedures.
Advantages of detailed instructions
The advantages to having detailed but concise assignment instructions are far-reaching:
- it’s one of the requirements of the SIA’s Approved Contractor Scheme
- Security officers are more confident in their job, and have a standard against which they can work
- they portray a professional image to clients
- the guarding company’s processes are more structured
- it’s good indication to your insurers that you’re trading correctly
However, when producing your assignment instructions you’ll find that it’s time-consuming and very often difficult to know what to include. The instructions we’ve developed are easily adaptable and contain information approved by a qualified assessor
Roberta Minty is Managing Director of the Total Training Consultancy.
You certainly make the importance of assignment instructions obvious. In addition, I like how you point out that these documents can be a source of confusion. If the document is too extensive, or not extensive enough, a company can end up paying for security service that they are not using to it’s full potential. http://www.goldshieldsecurity.com/brooklyn-ny-security-officers-and-fire-guards.htm
How long legally do site security assignment instructions last, ie need renewing and signing by security staff ?
The British Standards say they must be reviewed upon any change or at least annually
- CRM Asignment Help
- MBA Assignment Help
- Statistics Assignment Help
- Market Analysis Assignment Help
- Business Development Assignment Help
- 4p of Marketing Assignment Help
- Pricing Strategy Assignment Help
- Operations Management Assignment Help
- Corporate Strategy Assignment Help
- Change Management Assignment Help
- Supply Chain Management Assignment Help
- Human Resource Assignment Help
- Management Assignment Help
- Marketing Assignment Help
- Strategy Assignment Help
- Operation Assignment Help
- Marketing Research Assignment Help
- Strategic Marketing Assignment Help
- Project Management Assignment Help
- Strategic Management Assignment Help
- Marketing Management Assignment Help
- Business Assignment Help
- Business Ethics Assignment Help
- Consumer Behavior Assignment Help
- Conflict Management Assignment Help
- Business Statistics Assignment Help
- Managerial Economics Assignment Help
- Project Risk Management Assignment Help
- Nursing Assignment Help
- Clinical Reasoning Cycle
- Nursing Resume Writing
- Medical Assignment Help
- Financial Accounting Assignment Help
- Financial Services Assignment Help
- Finance Planning Assignment Help
- Finance Assignment Help
- Forex Assignment Help
- Behavioral Finance Assignment Help
- Personal Finance Assignment Help
- Capital Budgeting Assignment Help
- Corporate Finance Planning Assignment Help
- Financial Statement Analysis Assignment Help
- Accounting Assignment Help
- Solve My Accounting Paper
- Taxation Assignment Help
- Cost Accounting Assignment Help
- Managerial Accounting Assignment Help
- Business Accounting Assignment Help
- Activity-Based Accounting Assignment Help
- Economics Assignment Help
- Microeconomics Assignment Help
- Econometrics Assignment Help
- IT Management Assignment Help
- Robotics Assignment Help
- Business Intelligence Assignment Help
- Information Technology Assignment Help
- Database Assignment Help
- Data Mining Assignment Help
- Data Structure Assignment Help
- Computer Network Assignment Help
- Operating System Assignment Help
- Data Flow Diagram Assignment Help
- UML Diagram Assignment Help
- Solidworks Assignment Help
- Cookery Assignment Help
- R Studio Assignment Help
- Law Assignment Help
- Law Assignment Sample
- Criminology Assignment Help
- Taxation Law Assignment Help
- Constitutional Law Assignment Help
- Business Law Assignment Help
- Consumer Law Assignment Help
- Employment Law Assignment Help
- Commercial Law Assignment Help
- Criminal Law Assignment Help
- Environmental Law Assignment Help
- Contract Law Assignment Help
- Company Law Assignment Help
- Corp. Governance Law Assignment Help
- Science Assignment Help
- Physics Assignment Help
- Chemistry Assignment Help
- Sports Science Assignment Help
- Chemical Engineering Assignment Help
- Biology Assignment Help
- Bioinformatics Assignment Help
- Biochemistry Assignment Help
- Biotechnology Assignment Help
- Anthropology Assignment Help
- Paleontology Assignment Help
- Engineering Assignment Help
- Autocad Assignment Help
- Mechanical Assignment Help
- Fluid Mechanics Assignment Help
- Civil Engineering Assignment Help
- Electrical Engineering Assignment Help
- Ansys Assignment Help
- Humanities Assignment Help
- Sociology Assignment Help
- Philosophy Assignment Help
- English Assignment Help
- Geography Assignment Help
- History Assignment Help
- Agroecology Assignment Help
- Psychology Assignment Help
- Social Science Assignment Help
- Public Relations Assignment Help
- Political Science Assignment Help
- Mass Communication Assignment Help
- Auditing Assignment Help
- Dissertation Writing Help
- Sociology Dissertation Help
- Marketing Dissertation Help
- Biology Dissertation Help
- Nursing Dissertation Help
- MATLAB Dissertation Help
- Law Dissertation Help
- Geography Dissertation Help
- English Dissertation Help
- Architecture Dissertation Help
- Doctoral Dissertation Help
- Dissertation Statistics Help
- Academic Dissertation Help
- Cheap Dissertation Help
- Dissertation Help Online
- Dissertation Proofreading Services
- Do My Dissertation
- Business Report Writing
- Programming Assignment Help
- Java Programming Assignment Help
- C Programming Assignment Help
- PHP Assignment Help
- Python Assignment Help
- Perl Assignment Help
- SAS Assignment Help
- Web Designing Assignment Help
- Android App Assignment Help
- JavaScript Assignment Help
- Linux Assignment Help
- Mathematics Assignment Help
- Geometry Assignment Help
- Arithmetic Assignment Help
- Trigonometry Assignment Help
- Calculus Assignment Help
- Arts Architecture Assignment Help
- Arts Assignment Help
- Case Study Assignment Help
- History Case Study
- Case Study Writing Services
- Write My Case Study For Me
- Business Law Case Study
- Civil Law Case Study Help
- Marketing Case Study Help
- Nursing Case Study Help
- ZARA Case Study
- Amazon Case Study
- Apple Case Study
- Coursework Assignment Help
- Finance Coursework Help
- Coursework Writing Services
- Marketing Coursework Help
- Maths Coursework Help
- Chemistry Coursework Help
- English Coursework Help
- Do My Coursework
- Custom Coursework Writing Service
- Thesis Writing Help
- Thesis Help Online
- Write my thesis for me
- CDR Writing Services
- CDR Engineers Australia
- CDR Report Writers
- Homework help
- Algebra Homework Help
- Psychology Homework Help
- Statistics Homework Help
- English Homework Help
- CPM homework help
- Do My Homework For Me
- Online Exam Help
- Pay Someone to Do My Homework
- Do My Math Homework
- Macroeconomics Homework Help
- Jiskha Homework Help
- Research Paper Help
- Edit my paper
- Research Paper Writing Service
- Write My Paper For Me
- Buy Term Papers Online
- Buy College Papers
- Paper Writing Services
- Research Proposal Help
- Proofread My Paper
- Report Writing Help
- Story Writing Help
- Grant Writing Help
- DCU Assignment Cover Sheet Help Ireland
- CHCDIV001 Assessment Answers
- BSBWOR203 Assessment Answers
- CHC33015 Assessment Answers
- CHCCCS015 Assessment Answers
- CHCECE018 Assessment Answers
- CHCLEG001 Assessment Answers
- CHCPRP001 Assessment Answers
- CHCPRT001 Assessment Answers
- HLTAAP001 Assessment Answers
- HLTINF001 Assessment Answers
- HLTWHS001 Assessment Answers
- SITXCOM005 Assessment Answers
- SITXFSA001 Assessment Answers
- BSBMED301 Assessment Answers
- BSBWOR502 Assessment Answers
- CHCAGE001 Assessment Answers
- CHCCCS011 Assessment Answers
- CHCCOM003 Assessment Answers
- CHCCOM005 Assessment Answers
- CHCDIV002 Assessment Answers
- CHCECE001 Assessment Answers
- CHCECE017 Assessment Answers
- CHCECE023 Assessment Answers
- CHCPRP003 Assessment Answers
- HLTWHS003 Assessment Answers
- SITXWHS001 Assessment Answers
- BSBCMM401 Assessment Answers
- BSBDIV501 Assessment Answers
- BSBSUS401 Assessment Answers
- BSBWOR501 Assessment Answers
- CHCAGE005 Assessment Answers
- CHCDIS002 Assessment Answers
- CHCECE002 Assessment Answers
- CHCECE007 Assessment Answers
- CHCECE025 Assessment Answers
- CHCECE026 Assessment Answers
- CHCLEG003 Assessment Answers
- HLTAID003 Assessment Answers
- SITXHRM002 Assessment Answers
- Elevator Speech
- Maid Of Honor Speech
- Problem Solutions Speech
- Award Presentation Speech
- Tropicana Speech Topics
- Write My Assignment
- Personal Statement Writing
- Narrative Writing help
- Academic Writing Service
- Resume Writing Services
- Assignment Writing Tips
- Writing Assignment for University
- Custom Assignment Writing Service
- Assignment Provider
- Assignment Assistance
- Solve My Assignment
- Pay For Assignment Help
- Assignment Help Online
- HND Assignment Help
- SPSS Assignment Help
- Buy Assignments Online
- Assignment Paper Help
- Assignment Cover Page
- Urgent Assignment Help
- Perdisco Assignment Help
- Make My Assignment
- College Assignment Help
- Get Assignment Help
- Cheap Assignment Help
- Assignment Help Tutors
- TAFE Assignment Help
- Study Help Online
- Do My Assignment
- Do Assignment For Me
- My Assignment Help
- All Assignment Help
- Academic Assignment Help
- Student Assignment Help
- University Assignment Help
- Instant Assignment Help
- Powerpoint Presentation Service
- Last Minute Assignment Help
- World No 1 Assignment Help Company
- Mentorship Assignment Help
- Legit Essay
- Essay Writing Services
- Essay Outline Help
- Descriptive Essay Help
- History Essay Help
- Research Essay Help
- English Essay Writing
- Literature Essay Help
- Essay Writer for Australia
- Online Custom Essay Help
- Essay Writing Help
- Custom Essay Help
- Essay Help Online
- Writing Essay Papers
- Essay Homework Help
- Professional Essay Writer
- Illustration Essay Help
- Scholarship Essay Help
- Need Help Writing Essay
- Plagiarism Free Essays
- Write My Essay
- Response Essay Writing Help
- Essay Assistance
- Essay Typer
- APA Reference Generator
- Harvard Reference Generator
- Vancouver Reference Generator
- Oscola Referencing Generator
- Deakin Referencing Generator
- Griffith Referencing Tool
- Turabian Citation Generator
- UTS Referencing Generator
- Swinburne Referencing Tool
- AGLC Referencing Generator
- AMA Referencing Generator
- MLA Referencing Generator
- CSE Citation Generator
- ASA Referencing
- Oxford Referencing Generator
- LaTrobe Referencing Tool
- ACS Citation Generator
- APSA Citation Generator
- Central Queensland University
- Holmes Institute
- Monash University
- Torrens University
- Victoria University
- Federation University
- Griffith University
- Deakin University
- Murdoch University
- The University of Sydney
- The London College
- Ulster University
- University of derby
- University of West London
- Bath Spa University
- University of Warwick
- Newcastle University
- Anglia Ruskin University
- University of Northampton
- The University of Manchester
- University of Michigan
- University of Chicago
- University of Pennsylvania
- Cornell University
- Georgia Institute of Technology
- National University
- University of Florida
- University of Minnesota
- Help University
- INTI International University
- Universiti Sains Malaysia
- Universiti Teknologi Malaysia
- University of Malaya
- ERC Institute
- Nanyang Technological University
- Singapore Institute of Management
- Singapore Institute of Technology
- United Kingdom
- Jobs near Deakin University
- Jobs Near CQUniversity
- Jobs Near La Trobe University
- Jobs Near Monash University
- Jobs Near Torrens University
- Jobs Near Cornell University
- Jobs Near National University
- Jobs Near University of Chicago
- Jobs Near University of Florida
- Jobs Near University of Michigan
- Jobs Near Bath Spa University
- Jobs Near Coventry University
- Jobs Near Newcastle University
- Jobs Near University of Bolton
- Jobs Near university of derby
- Search Assignments
- Connect Seniors
- Essay Rewriter
- Knowledge Series
- Conclusion Generator
- GPA Calculator
- Factoring Calculator
- Plagiarism Checker
- Word Page Counter
- Paraphrasing Tool
- Living Calculator
- Quadratic Equation
- Algebra Calculator
- Integral Calculator
- Chemical Balancer
- Equation Solver
- Fraction Calculator
- Slope Calculator
- Fisher Equation
- Summary Generator
- Essay Topic Generator
- Alphabetizer
- Case Converter
- Antiderivative Calculator
- Kinematics Calculator
- Truth Table Generator
- Financial Calculator
- Reflection calculator
- Projectile Motion Calculator
- Paper Checker
- Inverse Function Calculator

Cyber Security Assignment
Task: Assessment 1: individual problem-solving task 1 Problem-Solving Task 1 Details
Learning outcomes In this assignment, you will be focusing on the following unit learning outcome (ULO):
ULO2: Assess security risks, threats and vulnerabilities to the organisation and implement appropriate information security protection mechanisms by analysing requirements, plans and IT security policies.
This ULO will contribute to three of your Deakin graduate learning outcomes (GLOs) in the form of discipline knowledge (GLO1), critical thinking (GLO4) and problem solving (GLO5).
Brief description of assessment task This task requires you to demonstrate the ability to conduct an investigation of security management issues in corporate organisations based on the background information provided below and write a report.
In your report, you will be required to follow prescribed procedures to evaluate risk levels and the potential impact of threats and vulnerabilities on a hypothetical organisation. You will be assessed on your ability to identify and prioritise the security risks, threats and vulnerabilities to an organisation.
Background information In Course 1 of SIT763 you looked at the Cyber Security and SMEs (Small and Medium Sized enterprises).
In light of this, your security company has been hired by a government body to undertake a security review in relation to SMEs.
This body would like you to write a consultancy paper about cyber security risks. Your report should address the following:
- What common cyber security risks, threats and vulnerabilities do SMEs face?
- Based on what we’ve covered so far and your additional research of the literature, what solutions do you propose?
Your task is to assess common security risks, threats and vulnerabilities to a SME and implement appropriate information security protection mechanisms by analysing requirements, plans and IT security policies.
You may also want to reflect on how cyber security issues relating to SMEs are unique
SIT763: IT Securty Management To prepare your report, you should conduct your research using a variety of sources (including those provided in your prescribed reading list) and reference them.
What do I do now?
- Start collecting and researching information
- Think creatively.
- Develop the report in Microsoft Word format
- Look at the assessment rubric and the unit learning outcomes to ensure that you understand what you are being assessed (and marked) on.
- The problem-solving task should be between 1000-1500 words (not including references).
Assessment 1: individual problem-solving task 1 Executive summary and description of a SME Protecting the sensitive data from the hackers needs to be the major priority for businesses of all sizes whether they are small, medium or large enterprises. The threats come in the form of phishing and malware which seeks to infiltrate the corporate network and extract data. The report focuses on security management issues in SMEs and provides an evaluation of risks levels and potential impact of the threats and different vulnerabilities. A hypothetical organisation needs to consider the high-quality services offered to the customers and protecting their data. The clients want to ensure that their information is secured where SMEs focus on ensuring the team members being informed about the current trends of cybersecurity. The assessment is based on developing better plans and IT security policies and proper training of the employees will help in protecting the organisation from the cyber-attacks.
Subscribe our YouTube channel for more related videos
Cyber security risk assessment
Risks: It is the major loss or the damage in SMEs when the threat tends to exploit a vulnerability. Some of the possibilities include the financial loss with disruption in business, privacy, or reputation, with major legal implications that can include the loss of life as well.
- Unprecedented attacks: the valuable information resides in the different sources which grows with time. IoT create unprecedented attacks (Webb et al., 2017).
- Cyber espionage where the SMEs try to store their data in cloud (either in private, public or hybrid cloud technologies), there is a possibility of major loss of data.
- The data privacy and security are at stake when the confidential data is put on the cloud.
- Internet of Things (IoT) leakage where the real time data collection becomes important. It is important to monitor the traffic and collect the information of patients. The attackers make use of automated programs mainly to locate IoT devices and attackers tend to attempt to connect to the device through default credentials only.
- There are internal attacks which the small business face today. These can be phishing and spear phishing, malware or the spyware or maybe with the actions of disgruntled employee.
- The worms and virus are categorized as threats that tend to harm the organisation mainly through the exposure to the automated attack which is opposed to perpetrations by humans (Tuna et al., 2017).
Vulnerabilities For SMEs, it refers to the weakness of asset that could be exploited mainly by attackers. For example, if an employee leaves the organisation and his account is not disabled to their access to external accounts, change logins or removing their name from company credit card, then this can lead to the problem of intentional or unintentional threats. The vulnerabilities are mainly due to the automated attackers.There is another possibility in SMEs that they are not able to run antivirus and antimalware software which leads to vulnerability to infections. This fails to routinely update the operating systems or application software with remains of vulnerability to software problems (Baskerville et al., 2018). The user behaviour tends to create opportunities for attackers and system administrator tends to surf the web from account on corporate station could become a victim of the “drive-by” infection of the malicious software mainly.
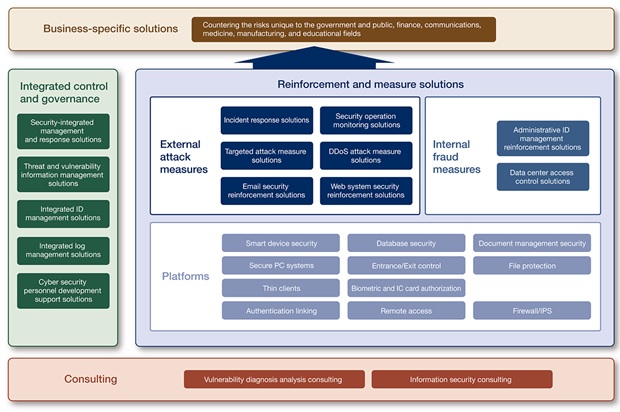
Security strategy Cyber security strategy for SMEs that may include Technical: A proper handling of the external attack measures and internal fraud measures like the DDoS attack measure, web system security reinforcement solution, security operation monitoring solutions, administrative ID management reinforcement solutions could help in handling the technical approach. The firewall, and the IPS is the best platform to authenticate the link and secure the database system. For the security of the system, there are smart device security, a control over the entrance and exist, biometric and IC card authorisation that help in detecting any wrong activity. A proper backup of the system can be an effective measure for the system security (Martellini et al., 2017).
Policy For the SMEs, the improved cyber security requires a spectrum of defence that builds an approach of prevention control and compliance (Allodi et al., 2017). The cyber resilience includes internal cyber capability, strong governance and proposed a policy for Critical Infrastructure Resilience in July 2015. The strategy stated that the health, safety and prosperity are depending upon certain infrastructure.
Human In SMEs, the company should keep their employees informed of the trends of cybersecurity and performing regular threat assessments to determine the approach to protect the system and handling the penetration testing that involves the modelling with real world threats. It is important to ensure that the network security antivirus can protect the system, with a data recovery plan in the event of vulnerability being exploited. The risks also need to be assessed which includes the stakeholder perspectives, designating the central group of employees for risk management and determining funding levels for implementing better policies and related controls (Fu et al., 2017).
Governance solutions. The Privacy and Data Protection Deputy Commissioner handles the information privacy with protective data security (Alassafi et al., 2017). The functions include handling of issuing of protective data security standards and law enforcement data security standards. The development of national cyber defence capabilities is set in regard to broad based collective defence. There is a need to ensure of proper information exchange and cooperation with NATO, and other partners for joint cyber security capabilities, and training opportunities. In cyber security, the digital technology sector and innovation is considered to be the major driving force for a better economic growth, productivity and competitiveness (Deshpande et al., 2017). The digital technology will help in driving innovation and lead to the development of advanced capabilities with growing economy.
Summary The information technology risks are assessed and measured depending upon the training opportunities given to the people. SMEs needs to ensure the enhancement fight against cybercrime that tends to reduce trust in digital services. The enhancement of detection of cybercrime with law enforcement and raising public awareness could help in preventing cyber threats. The users of e-services are directed to secured solutions and promoting international cooperation against cybercrime (Sadeghi et al., 2017). It is advisable for the people, to change their passwords as soon as they login to the new device. To avoid the large scale cyber incidents, the technological risks pertain to high level of knowledge and risks awareness in developing a state, society and economy. For the SMEs, a standard regulation or an industry framework is important with better information security and oversight responsibilities. A proper integrated control and governance is will help through companywide control and maintaining the security levels as well.
References Alassafi, M.O., Hussain, R.K., Ghashgari, G., Walters, R.J. and Wills, G.B., 2017. Security in organisations: governance, risks and vulnerabilities in moving to the cloud. In Enterprise Security (pp. 241-258). Springer, Cham.
Allodi, L. and Massacci, F., 2017. Security Events and Vulnerability Data for Cybersecurity Risk Estimation. Risk Analysis, 37(8), pp.1606-1627.
Baskerville, R., Rowe, F. and Wolff, F.C., 2018. Integration of information systems and cybersecurity countermeasures: An exposure to risk perspective. ACM SIGMIS Database: the DATABASE for Advances in Information Systems, 49(1), pp.33-52.
Deshpande, V.M., Nair, D.M.K. and Shah, D., 2017. Major Web Application Threats for Data Privacy & Security–Detection, Analysis and Mitigation Strategies. under review in International Journal of Scientific Research in Science and Technology PRINT ISSN, pp.2395-6011.
Martellini, M., Abaimov, S., Gaycken, S. and Wilson, C., 2017. Vulnerabilities and Security Issues. In Information Security of Highly Critical Wireless Networks (pp. 11-15). Springer, Cham.
Sadeghi, A., Jabbari, M., Alidoosti, A. and Rezaeian, M., 2017. Vulnerability and Security Risk Assessment of a Thermal Power Plant Using SVA Technique. Journal of Integrated Security Science, 1(1).
Tuna, G., Kogias, D.G., Gungor, V.C., Gezer, C., Ta?k?n, E. and Ayday, E., 2017. A survey on information security threats and solutions for machine to machine (M2M) communications. Journal of Parallel and Distributed Computing, 109, pp.142-154.
Webb, T. and Dayal, S., 2017. Building the wall: Addressing cybersecurity risks in medical devices in the USA and Australia. Computer Law & Security Review, 33(4), pp.559-563.
CHECK THE PRICE FOR YOUR PROJECT
Number of pages/words you require, choose your assignment deadline, related samples.
- (coit11226) system testing assignment on testing of software systems
- (BN201)IT assignment on the topic, Maslow's Hierarchy of Needs
- Cyber Security assignment identifying exploring strategies IT vulnerabilities can be detected and solves
- (MITS5004) IT Security Assignment: Critical Analysis of two Security ToolsHydra and Nmap
- (4CI018) IT Management Assignment: Can Graduates of BSc (Hons) Computer-Networking Course Accomplish Employability at Apple?
- IT Management Assignment: Case Analysis On Organisational Change For ITIL Implementation
- Digital Marketing Assignment Campaign Planning For The Sanchaya
- Digital Marketing Assignment: SEMrush- Online Visibility Management Platform
- (MIS609) Netflix Case Study: Data Analytics for Organisational Decision-Making
- (MIS603) Microservices Architecture Assignment: Application Of MSA On Amazon.com
- (MIS603) Microservices Architecture Assignment: Application Of MSA On Netflix
- (PROJ6009) Business Process Management Assignment Analyzing Role Of BPM Within KFC
- (MIS500) Business Research Assignment Evaluating The Social & Digital Media Of Nike
- (MIS500) Business Research Assignment Analysing The Social & Digital Media Of Adidas
- (BMG880) Data Analytics Assignment: Case Analysis Of Netflix Dataset
- (BUSM4742) Design Thinking Solutions For The Issues Encounter By Financial Institution
- (MBA632) Knowledge Management Assignment: Implementation Of Information Technology In The Operation of ZARA
- (BUSM4742) Data Analysis Assignment: Reimagining The Bank Of Tomorrow
- Risk Assessment Report On Finance System Of University of San Diego
- Digital Transformation Assignment Analyzing Issues Encounter by NHS services
- Big Data Assignment Discussing Cloud Security Threats in Case of Global Entertainments (GE)
- Information Security Assignment: Information Classification & Handling Policy for University of Hertfordshire
- (MIS610) Supply Chain Management Assignment: Implementation of Blockchain Technology at CareMart
- (HI6008) Business Research Assignment: Significance of Mobile Computing on Companies
- Digital Transformation Assignment: Impact of Digitalisation on Entrepreneurship’s Opportunity in Indian Telecom Industry

Looking for Your Assignment?

FREE PARAPHRASING TOOL

FREE PLAGIARISM CHECKER

FREE ESSAY TYPER TOOL
Other assignment services.
- SCM Assignment Help
- HRM Assignment Help
- Dissertation Assignment Help
- Marketing Analysis Assignment Help
- Corporate Finance Assignment Help

FREE WORD COUNT AND PAGE CALCULATOR

QUESTION BANK
ESCALATION EMAIL
To get answer.
Please Fill the following Details
Thank you !
We have sent you an email with the required document.

IMAGES
VIDEO
COMMENTS
Security labs for a university course, "Information Security Management." Authors Dave Eargle and Anthony Vance. Security-Assignments.com. Labs Tutorials Projects In-class Activities Cases Books and Films Store Dark Mode. Security-Assignments.com. Content for an information security management course. ...
Security assignments sometimes use the term "absolute" to make clear they are intended to be legal assignments. However, the terminology used is not decisive. An assignment will not be "absolute ...
What if my security assignment isn't unconditional? Your security assignment will not be a 'legal assignment', but instead you are likely to have what's called an 'equitable assignment'. The main ...
security-assignments.github.io Public. Shell 4 3 4 2 Updated 2 weeks ago. pentest-humbleify Public. 3 1 0 0 Updated on Jul 25, 2023. public-quiz-assets Public. 0 0 0 0 Updated on Jan 17, 2022. paypal-create-order Public. Python 0 0 0 0 Updated on Dec 30, 2021. paypal-webhook Public.
Easily distribute, analyze, and grade student work with Assignments for your LMS. Assignments is an application for your learning management system (LMS). It helps educators save time grading and guides students to turn in their best work with originality reports — all through the collaborative power of Google Workspace for Education.
Examples of Security Assignments in a sentence. Important Security Assignments (present) Shopping Plaza, Private Properties or equivalent 2 MarksBanks, Govt.. Any Responsible Person(s) receiving a citation for an Unruly Gathering requiring Increased Response shall be assessed a Police Service Fee for Special Security Assignments relating to the Unruly Gathering as provided §10-13-7(C).
Internet security is a vast area that keeps on developing each day. Students get relevant assignments to check their ability to prevent the risks of stealing sensitive information by malware. If this task is too challenging, you may hire a professional writer and get the best Internet security assignment help at AssignmentBro.
The Pop Culture Entertainment Magazine for Movies, TV, DVD, Blu-ray, Video Games, Books, Comics and Technology
Contact us directly at: [email protected] EDITORIAL OFFICE 24307 Magic Mountain Pkwy Suite #210 Valencia, CA 91355 PHONE 661-222-7744 STAFF EDITOR IN CHIEF Anthony C. Ferrante EXECUTIVE ED ...
Materials. A look at security instruments like security agreements, pledge agreements, and assignments. A discussion about the purpose of security instruments and their important provisions is also included.
Navigate to Training. Select Scheduled under Manage Training Assignments. Choose +Create Assignment. Enter a unique Name for the new training assignment. This name is used internally to identify the assignment and will not display to the end user. It will appear on reports and on the Scheduled Assignment table for reference.
Security Assignment means the Assignment of Sublease (Trust No. 117-A) dated as of July 10, 1995 between Lessor, as assignor, and Head Lessor, as assignee. Sample 1. Based on 4 documents. Security Assignment means a first assignment of the Borrower 's rights in respect of Insurances and all benefits thereof (including the right to receive ...
In our experience, assignment instructions are a constant reference for the security officer and every bit as important as his or her licence and uniform. Having passed Basic Job Training, the assignment instructions become a familiar document which includes such important information as duties for the security staff, client details and ...
Cyber Security Assignment. Question. Task: Assessment 1: individual problem-solving task 1. Problem-Solving Task 1 Details. Learning outcomes. In this assignment, you will be focusing on the following unit learning outcome (ULO): ULO2: Assess security risks, threats and vulnerabilities to the organisation and implement appropriate information ...
Security Assignment. Assignment of the Rights to be Assigned by the Assignor to the Assignee to secure the Secured Claim. Sample 1 Sample 2. Security Assignment. The Additional Chargor, as continuing security for the payment of the Secured Obligations, assigns absolutely by way of security with full title guarantee to the UK Security Trustee ...
View CYBER SECURITY - CSI6199 ASSIGNMENT 1.docx from MGM 430.30 at New England Institute Of Technology. CYBER SECURITY - CSI6199 ASSIGNMENT 1 Student name: Student id: Contents CYBER SECURITY.1 1.
Security Assignment 1.Docx-1 - Free download as Word Doc (.doc / .docx), PDF File (.pdf), Text File (.txt) or read online for free. Scribd is the world's largest social reading and publishing site.