- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore

Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Main Question Paper
- JEE Main Mock Test
- JEE Main Registration
- JEE Main Syllabus
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- GATE 2024 Result
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2023
- CAT 2023 College Predictor
- CMAT 2024 Registration
- TS ICET 2024 Registration
- CMAT Exam Date 2024
- MAH MBA CET Cutoff 2024
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- DNB CET College Predictor
- DNB PDCET College Predictor
- NEET Application Form 2024
- NEET PG Application Form 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
- LSAT India 2024
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top Law Collages in Indore
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
- AIBE 18 Result 2023
- NID DAT Exam
- Pearl Academy Exam
Animation Courses
- Animation Courses in India
- Animation Courses in Bangalore
- Animation Courses in Mumbai
- Animation Courses in Pune
- Animation Courses in Chennai
- Animation Courses in Hyderabad
- Design Colleges in India
- Fashion Design Colleges in Bangalore
- Fashion Design Colleges in Mumbai
- Fashion Design Colleges in Pune
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Hyderabad
- Fashion Design Colleges in India
- Top Design Colleges in India
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission
- UP B.Ed JEE 2024
- DDU Entrance Exam
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET PG Admit Card 2024
- IGNOU Date Sheet
- CUET Mock Test 2024
- CUET Application Form 2024
- CUET PG Syllabus 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Syllabus 2024
- IGNOU Exam Form 2024
- IGNOU Result
- CUET PG Courses 2024
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Access premium articles, webinars, resources to make the best decisions for career, course, exams, scholarships, study abroad and much more with
Plan, Prepare & Make the Best Career Choices
Cyber Security Essay
Cyber security is one of the most important topics in today’s digital world. With technology evolving at an unprecedented pace and more companies going online than ever before, it’s essential that everyone understands the basics of cyber security. Here are some sample essays on cyber security.
- 100 Words Essay On Cyber Security
As a student in today's digital world, it's important to remember the importance of cyber security. Today, almost everything that we do is done online or through the internet, and that means our personal information, like our passwords, banking information, and even our school work, is vulnerable to cyber security threats.
200 Words Essay On Cyber Security
500 words essay on cyber security.

Cyber security is the practice of protecting networks, systems, and programs from digital attacks. These attacks can come from many different sources, including hackers, viruses, and even from other people. In order to stay safe online, it's essential to understand the basics of cyber security. Cyber security is an ever-evolving field, and it's important for school students to stay informed and take the necessary steps to protect themselves online.
School students are the future of our society, and it's important to teach them the importance of cyber security from an early age. Cyber security is an ever-increasing problem in our digital world, and it's up to us to ensure that our students are aware of the risks and dangers that come with the internet.
What Is Cyber Security?
Cyber security is the practice of protecting digital devices and networks from unauthorised access and malicious activities. With the rise of technology and its integration into our lives, cyber security has become an integral part of our lives, and it's important for school students to understand the need for cyber security measures.
How To Protect Yourself From Cyber Crime?
One of the most important ways to protect your devices and networks from cyber threats is to create strong passwords and never share them with anyone else. Passwords are the first line of defence against cyber attacks, and it's important that school students understand how to create and use strong passwords. Additionally, students should be taught to never share personal information online, such as passwords, credit card numbers, and bank account information.
Staying informed is the best way to stay ahead of the latest threats, and it's important for students to stay up-to-date on the latest cyber security news and updates.
Cyber security is the use of antivirus and anti-malware software. These programs are designed to detect and block malicious programs, such as viruses, worms, and Trojans, before they can do any damage to your devices and networks. By teaching our students about the importance of cyber security, we can ensure that they will be better prepared to protect themselves and their devices from cyber threats.
Cyber Security is essential for all those who regularly and frequently use electronic devices. With so much of our sensitive data and documents stored on these gadgets, it is essential to ensure their protection. There are several ways to protect your devices from cyber threats, such as using Antivirus and Antimalware software, and implementing End-User Protection solutions. Taking the necessary steps to secure your devices can help keep your data safe and secure.
Causes Of Cyber Crime
There are many different causes of cybercrime, but most can be categorised into one of three categories:
Personal gain | This is perhaps the most common motivation for cybercrime, as it can be very lucrative. Cybercriminals may engage in activities such as identity theft, phishing scams, and credit card fraud in order to make money.
Revenge or vandalism | Some cybercriminals commit crimes out of a desire for revenge or simply to cause havoc. They may engage in activities such as denial of service attacks, website defacement, or even doxxing (releasing personal information online).
Political or ideological motivations | In some cases, cybercrime is committed for political or ideological reasons. For example, hackers may attack a website in order to protest its content or disrupt its operations.
How To Increase Cyber Security
For school students, cyber security is especially important. Many students use the internet for their studies, making them more vulnerable to cyberattacks. Hackers may try to access school networks, steal student data, or even disrupt classes. It’s important for students to know how to protect themselves from cyber threats. There are some simple steps that you can take to ensure your safety and security.
The first step is to create strong passwords for all of your accounts. Passwords should be hard to guess and should never be shared with anyone. Make sure to use a combination of upper and lowercase letters, numbers, and symbols. It's also important to change your passwords regularly.
Next, you should be sure to protect your personal information. This means making sure that you don't share your passwords or other sensitive information online. Be sure to use an up-to-date antivirus program to scan your computer regularly for malicious software.
Finally, be sure to stay informed about the latest cyber security threats. Keeping up with the news and reading articles on cyber security can help you stay aware of the latest threats and how to protect yourself against them.
By following these tips, you can stay safe online and protect your personal information. Cyber security is an important issue and it's important to take it seriously. If you take the time to learn more about cyber security and make sure you take steps to protect yourself, you can stay safe online and enjoy the benefits of today's digital world.
Explore Career Options (By Industry)
- Construction
- Entertainment
- Manufacturing
- Information Technology
Bio Medical Engineer
The field of biomedical engineering opens up a universe of expert chances. An Individual in the biomedical engineering career path work in the field of engineering as well as medicine, in order to find out solutions to common problems of the two fields. The biomedical engineering job opportunities are to collaborate with doctors and researchers to develop medical systems, equipment, or devices that can solve clinical problems. Here we will be discussing jobs after biomedical engineering, how to get a job in biomedical engineering, biomedical engineering scope, and salary.
Data Administrator
Database professionals use software to store and organise data such as financial information, and customer shipping records. Individuals who opt for a career as data administrators ensure that data is available for users and secured from unauthorised sales. DB administrators may work in various types of industries. It may involve computer systems design, service firms, insurance companies, banks and hospitals.
Ethical Hacker
A career as ethical hacker involves various challenges and provides lucrative opportunities in the digital era where every giant business and startup owns its cyberspace on the world wide web. Individuals in the ethical hacker career path try to find the vulnerabilities in the cyber system to get its authority. If he or she succeeds in it then he or she gets its illegal authority. Individuals in the ethical hacker career path then steal information or delete the file that could affect the business, functioning, or services of the organization.
Data Analyst
The invention of the database has given fresh breath to the people involved in the data analytics career path. Analysis refers to splitting up a whole into its individual components for individual analysis. Data analysis is a method through which raw data are processed and transformed into information that would be beneficial for user strategic thinking.
Data are collected and examined to respond to questions, evaluate hypotheses or contradict theories. It is a tool for analyzing, transforming, modeling, and arranging data with useful knowledge, to assist in decision-making and methods, encompassing various strategies, and is used in different fields of business, research, and social science.
Geothermal Engineer
Individuals who opt for a career as geothermal engineers are the professionals involved in the processing of geothermal energy. The responsibilities of geothermal engineers may vary depending on the workplace location. Those who work in fields design facilities to process and distribute geothermal energy. They oversee the functioning of machinery used in the field.
Remote Sensing Technician
Individuals who opt for a career as a remote sensing technician possess unique personalities. Remote sensing analysts seem to be rational human beings, they are strong, independent, persistent, sincere, realistic and resourceful. Some of them are analytical as well, which means they are intelligent, introspective and inquisitive.
Remote sensing scientists use remote sensing technology to support scientists in fields such as community planning, flight planning or the management of natural resources. Analysing data collected from aircraft, satellites or ground-based platforms using statistical analysis software, image analysis software or Geographic Information Systems (GIS) is a significant part of their work. Do you want to learn how to become remote sensing technician? There's no need to be concerned; we've devised a simple remote sensing technician career path for you. Scroll through the pages and read.
Geotechnical engineer
The role of geotechnical engineer starts with reviewing the projects needed to define the required material properties. The work responsibilities are followed by a site investigation of rock, soil, fault distribution and bedrock properties on and below an area of interest. The investigation is aimed to improve the ground engineering design and determine their engineering properties that include how they will interact with, on or in a proposed construction.
The role of geotechnical engineer in mining includes designing and determining the type of foundations, earthworks, and or pavement subgrades required for the intended man-made structures to be made. Geotechnical engineering jobs are involved in earthen and concrete dam construction projects, working under a range of normal and extreme loading conditions.
Cartographer
How fascinating it is to represent the whole world on just a piece of paper or a sphere. With the help of maps, we are able to represent the real world on a much smaller scale. Individuals who opt for a career as a cartographer are those who make maps. But, cartography is not just limited to maps, it is about a mixture of art , science , and technology. As a cartographer, not only you will create maps but use various geodetic surveys and remote sensing systems to measure, analyse, and create different maps for political, cultural or educational purposes.
Budget Analyst
Budget analysis, in a nutshell, entails thoroughly analyzing the details of a financial budget. The budget analysis aims to better understand and manage revenue. Budget analysts assist in the achievement of financial targets, the preservation of profitability, and the pursuit of long-term growth for a business. Budget analysts generally have a bachelor's degree in accounting, finance, economics, or a closely related field. Knowledge of Financial Management is of prime importance in this career.
Product Manager
A Product Manager is a professional responsible for product planning and marketing. He or she manages the product throughout the Product Life Cycle, gathering and prioritising the product. A product manager job description includes defining the product vision and working closely with team members of other departments to deliver winning products.
Underwriter
An underwriter is a person who assesses and evaluates the risk of insurance in his or her field like mortgage, loan, health policy, investment, and so on and so forth. The underwriter career path does involve risks as analysing the risks means finding out if there is a way for the insurance underwriter jobs to recover the money from its clients. If the risk turns out to be too much for the company then in the future it is an underwriter who will be held accountable for it. Therefore, one must carry out his or her job with a lot of attention and diligence.
Finance Executive
Operations manager.
Individuals in the operations manager jobs are responsible for ensuring the efficiency of each department to acquire its optimal goal. They plan the use of resources and distribution of materials. The operations manager's job description includes managing budgets, negotiating contracts, and performing administrative tasks.
Bank Probationary Officer (PO)
Investment director.
An investment director is a person who helps corporations and individuals manage their finances. They can help them develop a strategy to achieve their goals, including paying off debts and investing in the future. In addition, he or she can help individuals make informed decisions.
Welding Engineer
Welding Engineer Job Description: A Welding Engineer work involves managing welding projects and supervising welding teams. He or she is responsible for reviewing welding procedures, processes and documentation. A career as Welding Engineer involves conducting failure analyses and causes on welding issues.
Transportation Planner
A career as Transportation Planner requires technical application of science and technology in engineering, particularly the concepts, equipment and technologies involved in the production of products and services. In fields like land use, infrastructure review, ecological standards and street design, he or she considers issues of health, environment and performance. A Transportation Planner assigns resources for implementing and designing programmes. He or she is responsible for assessing needs, preparing plans and forecasts and compliance with regulations.
An expert in plumbing is aware of building regulations and safety standards and works to make sure these standards are upheld. Testing pipes for leakage using air pressure and other gauges, and also the ability to construct new pipe systems by cutting, fitting, measuring and threading pipes are some of the other more involved aspects of plumbing. Individuals in the plumber career path are self-employed or work for a small business employing less than ten people, though some might find working for larger entities or the government more desirable.
Construction Manager
Individuals who opt for a career as construction managers have a senior-level management role offered in construction firms. Responsibilities in the construction management career path are assigning tasks to workers, inspecting their work, and coordinating with other professionals including architects, subcontractors, and building services engineers.
Urban Planner
Urban Planning careers revolve around the idea of developing a plan to use the land optimally, without affecting the environment. Urban planning jobs are offered to those candidates who are skilled in making the right use of land to distribute the growing population, to create various communities.
Urban planning careers come with the opportunity to make changes to the existing cities and towns. They identify various community needs and make short and long-term plans accordingly.
Highway Engineer
Highway Engineer Job Description: A Highway Engineer is a civil engineer who specialises in planning and building thousands of miles of roads that support connectivity and allow transportation across the country. He or she ensures that traffic management schemes are effectively planned concerning economic sustainability and successful implementation.
Environmental Engineer
Individuals who opt for a career as an environmental engineer are construction professionals who utilise the skills and knowledge of biology, soil science, chemistry and the concept of engineering to design and develop projects that serve as solutions to various environmental problems.
Naval Architect
A Naval Architect is a professional who designs, produces and repairs safe and sea-worthy surfaces or underwater structures. A Naval Architect stays involved in creating and designing ships, ferries, submarines and yachts with implementation of various principles such as gravity, ideal hull form, buoyancy and stability.
Orthotist and Prosthetist
Orthotists and Prosthetists are professionals who provide aid to patients with disabilities. They fix them to artificial limbs (prosthetics) and help them to regain stability. There are times when people lose their limbs in an accident. In some other occasions, they are born without a limb or orthopaedic impairment. Orthotists and prosthetists play a crucial role in their lives with fixing them to assistive devices and provide mobility.
Veterinary Doctor
Pathologist.
A career in pathology in India is filled with several responsibilities as it is a medical branch and affects human lives. The demand for pathologists has been increasing over the past few years as people are getting more aware of different diseases. Not only that, but an increase in population and lifestyle changes have also contributed to the increase in a pathologist’s demand. The pathology careers provide an extremely huge number of opportunities and if you want to be a part of the medical field you can consider being a pathologist. If you want to know more about a career in pathology in India then continue reading this article.
Speech Therapist
Gynaecologist.
Gynaecology can be defined as the study of the female body. The job outlook for gynaecology is excellent since there is evergreen demand for one because of their responsibility of dealing with not only women’s health but also fertility and pregnancy issues. Although most women prefer to have a women obstetrician gynaecologist as their doctor, men also explore a career as a gynaecologist and there are ample amounts of male doctors in the field who are gynaecologists and aid women during delivery and childbirth.
An oncologist is a specialised doctor responsible for providing medical care to patients diagnosed with cancer. He or she uses several therapies to control the cancer and its effect on the human body such as chemotherapy, immunotherapy, radiation therapy and biopsy. An oncologist designs a treatment plan based on a pathology report after diagnosing the type of cancer and where it is spreading inside the body.
Audiologist
The audiologist career involves audiology professionals who are responsible to treat hearing loss and proactively preventing the relevant damage. Individuals who opt for a career as an audiologist use various testing strategies with the aim to determine if someone has a normal sensitivity to sounds or not. After the identification of hearing loss, a hearing doctor is required to determine which sections of the hearing are affected, to what extent they are affected, and where the wound causing the hearing loss is found. As soon as the hearing loss is identified, the patients are provided with recommendations for interventions and rehabilitation such as hearing aids, cochlear implants, and appropriate medical referrals. While audiology is a branch of science that studies and researches hearing, balance, and related disorders.
Hospital Administrator
The hospital Administrator is in charge of organising and supervising the daily operations of medical services and facilities. This organising includes managing of organisation’s staff and its members in service, budgets, service reports, departmental reporting and taking reminders of patient care and services.
For an individual who opts for a career as an actor, the primary responsibility is to completely speak to the character he or she is playing and to persuade the crowd that the character is genuine by connecting with them and bringing them into the story. This applies to significant roles and littler parts, as all roles join to make an effective creation. Here in this article, we will discuss how to become an actor in India, actor exams, actor salary in India, and actor jobs.
Individuals who opt for a career as acrobats create and direct original routines for themselves, in addition to developing interpretations of existing routines. The work of circus acrobats can be seen in a variety of performance settings, including circus, reality shows, sports events like the Olympics, movies and commercials. Individuals who opt for a career as acrobats must be prepared to face rejections and intermittent periods of work. The creativity of acrobats may extend to other aspects of the performance. For example, acrobats in the circus may work with gym trainers, celebrities or collaborate with other professionals to enhance such performance elements as costume and or maybe at the teaching end of the career.
Video Game Designer
Career as a video game designer is filled with excitement as well as responsibilities. A video game designer is someone who is involved in the process of creating a game from day one. He or she is responsible for fulfilling duties like designing the character of the game, the several levels involved, plot, art and similar other elements. Individuals who opt for a career as a video game designer may also write the codes for the game using different programming languages.
Depending on the video game designer job description and experience they may also have to lead a team and do the early testing of the game in order to suggest changes and find loopholes.
Radio Jockey
Radio Jockey is an exciting, promising career and a great challenge for music lovers. If you are really interested in a career as radio jockey, then it is very important for an RJ to have an automatic, fun, and friendly personality. If you want to get a job done in this field, a strong command of the language and a good voice are always good things. Apart from this, in order to be a good radio jockey, you will also listen to good radio jockeys so that you can understand their style and later make your own by practicing.
A career as radio jockey has a lot to offer to deserving candidates. If you want to know more about a career as radio jockey, and how to become a radio jockey then continue reading the article.
Choreographer
The word “choreography" actually comes from Greek words that mean “dance writing." Individuals who opt for a career as a choreographer create and direct original dances, in addition to developing interpretations of existing dances. A Choreographer dances and utilises his or her creativity in other aspects of dance performance. For example, he or she may work with the music director to select music or collaborate with other famous choreographers to enhance such performance elements as lighting, costume and set design.
Videographer
Multimedia specialist.
A multimedia specialist is a media professional who creates, audio, videos, graphic image files, computer animations for multimedia applications. He or she is responsible for planning, producing, and maintaining websites and applications.
Social Media Manager
A career as social media manager involves implementing the company’s or brand’s marketing plan across all social media channels. Social media managers help in building or improving a brand’s or a company’s website traffic, build brand awareness, create and implement marketing and brand strategy. Social media managers are key to important social communication as well.
Copy Writer
In a career as a copywriter, one has to consult with the client and understand the brief well. A career as a copywriter has a lot to offer to deserving candidates. Several new mediums of advertising are opening therefore making it a lucrative career choice. Students can pursue various copywriter courses such as Journalism , Advertising , Marketing Management . Here, we have discussed how to become a freelance copywriter, copywriter career path, how to become a copywriter in India, and copywriting career outlook.
Careers in journalism are filled with excitement as well as responsibilities. One cannot afford to miss out on the details. As it is the small details that provide insights into a story. Depending on those insights a journalist goes about writing a news article. A journalism career can be stressful at times but if you are someone who is passionate about it then it is the right choice for you. If you want to know more about the media field and journalist career then continue reading this article.
For publishing books, newspapers, magazines and digital material, editorial and commercial strategies are set by publishers. Individuals in publishing career paths make choices about the markets their businesses will reach and the type of content that their audience will be served. Individuals in book publisher careers collaborate with editorial staff, designers, authors, and freelance contributors who develop and manage the creation of content.
In a career as a vlogger, one generally works for himself or herself. However, once an individual has gained viewership there are several brands and companies that approach them for paid collaboration. It is one of those fields where an individual can earn well while following his or her passion.
Ever since internet costs got reduced the viewership for these types of content has increased on a large scale. Therefore, a career as a vlogger has a lot to offer. If you want to know more about the Vlogger eligibility, roles and responsibilities then continue reading the article.
Individuals in the editor career path is an unsung hero of the news industry who polishes the language of the news stories provided by stringers, reporters, copywriters and content writers and also news agencies. Individuals who opt for a career as an editor make it more persuasive, concise and clear for readers. In this article, we will discuss the details of the editor's career path such as how to become an editor in India, editor salary in India and editor skills and qualities.
Linguistic meaning is related to language or Linguistics which is the study of languages. A career as a linguistic meaning, a profession that is based on the scientific study of language, and it's a very broad field with many specialities. Famous linguists work in academia, researching and teaching different areas of language, such as phonetics (sounds), syntax (word order) and semantics (meaning).
Other researchers focus on specialities like computational linguistics, which seeks to better match human and computer language capacities, or applied linguistics, which is concerned with improving language education. Still, others work as language experts for the government, advertising companies, dictionary publishers and various other private enterprises. Some might work from home as freelance linguists. Philologist, phonologist, and dialectician are some of Linguist synonym. Linguists can study French , German , Italian .
Public Relation Executive
Travel journalist.
The career of a travel journalist is full of passion, excitement and responsibility. Journalism as a career could be challenging at times, but if you're someone who has been genuinely enthusiastic about all this, then it is the best decision for you. Travel journalism jobs are all about insightful, artfully written, informative narratives designed to cover the travel industry. Travel Journalist is someone who explores, gathers and presents information as a news article.
Quality Controller
A quality controller plays a crucial role in an organisation. He or she is responsible for performing quality checks on manufactured products. He or she identifies the defects in a product and rejects the product.
A quality controller records detailed information about products with defects and sends it to the supervisor or plant manager to take necessary actions to improve the production process.
Production Manager
Merchandiser.
A QA Lead is in charge of the QA Team. The role of QA Lead comes with the responsibility of assessing services and products in order to determine that he or she meets the quality standards. He or she develops, implements and manages test plans.
Metallurgical Engineer
A metallurgical engineer is a professional who studies and produces materials that bring power to our world. He or she extracts metals from ores and rocks and transforms them into alloys, high-purity metals and other materials used in developing infrastructure, transportation and healthcare equipment.
Azure Administrator
An Azure Administrator is a professional responsible for implementing, monitoring, and maintaining Azure Solutions. He or she manages cloud infrastructure service instances and various cloud servers as well as sets up public and private cloud systems.
AWS Solution Architect
An AWS Solution Architect is someone who specializes in developing and implementing cloud computing systems. He or she has a good understanding of the various aspects of cloud computing and can confidently deploy and manage their systems. He or she troubleshoots the issues and evaluates the risk from the third party.
Computer Programmer
Careers in computer programming primarily refer to the systematic act of writing code and moreover include wider computer science areas. The word 'programmer' or 'coder' has entered into practice with the growing number of newly self-taught tech enthusiasts. Computer programming careers involve the use of designs created by software developers and engineers and transforming them into commands that can be implemented by computers. These commands result in regular usage of social media sites, word-processing applications and browsers.
ITSM Manager
Information security manager.
Individuals in the information security manager career path involves in overseeing and controlling all aspects of computer security. The IT security manager job description includes planning and carrying out security measures to protect the business data and information from corruption, theft, unauthorised access, and deliberate attack
Business Intelligence Developer
Applications for admissions are open..

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters

Aakash iACST Scholarship Test 2024
Get up to 90% scholarship on NEET, JEE & Foundation courses

Resonance Coaching
Enroll in Resonance Coaching for success in JEE/NEET exams

TOEFL ® Registrations 2024
Thinking of Studying Abroad? Think the TOEFL® test. Register now & Save 10% on English Proficiency Tests with Gift Cards

ALLEN JEE Exam Prep
Start your JEE preparation with ALLEN
NEET 2024 Most scoring concepts
Just Study 32% of the NEET syllabus and Score upto 100% marks
Everything about Education
Latest updates, Exclusive Content, Webinars and more.
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Cetifications
We Appeared in

Essay on Cyber Security
Students are often asked to write an essay on Cyber Security in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Security
Understanding cyber security.
Cyber security is about protecting computers, servers, mobile devices, electronic systems, networks, and data from digital attacks. It’s a critical area as our daily life, economic vitality, and national security rely on a stable, safe, and resilient cyberspace.
The Importance of Cyber Security
Cyber security is important because it helps protect sensitive information, like our personal data and banking details, from being stolen by hackers. It also safeguards against harmful viruses that can damage our devices.
Types of Cyber Threats
Common threats include malware, phishing, and ransomware. Malware is harmful software, phishing tricks people into revealing sensitive information, and ransomware locks users out until they pay a ransom.
Cyber Security Practices
Good practices include using strong passwords, regularly updating software, and not clicking on suspicious links. These can help protect us from cyber threats.
Also check:
- Paragraph on Cyber Security
- Speech on Cyber Security
250 Words Essay on Cyber Security
Introduction to cyber security.
Cybersecurity, a term that has gained paramount importance in the digital age, refers to the practice of protecting internet-connected systems, including hardware, software, and data, from digital attacks. Its significance is amplified by the increasing reliance on technology, which, while offering numerous benefits, also opens up new avenues for potential threats.
The digital landscape is a double-edged sword. On one hand, it facilitates communication, commerce, and innovation. On the other, it provides a fertile ground for cybercriminals to exploit vulnerabilities. Cybersecurity thus becomes crucial in safeguarding sensitive information, preventing unauthorized access, and maintaining system integrity.
Challenges in Cyber Security
However, the complexity and sophistication of cyber threats are growing at an alarming pace. Cybercriminals are using advanced techniques, such as AI and machine learning, to bypass traditional security measures. This necessitates the development of more robust, adaptive cybersecurity strategies.
The Future of Cyber Security
The future of cybersecurity lies in proactive defense mechanisms. By leveraging technologies like AI, predictive analytics, and blockchain, we can anticipate and neutralize threats before they cause harm. Furthermore, fostering a culture of cybersecurity awareness is equally important to empower individuals and organizations against cyber threats.
In conclusion, cybersecurity is a vital aspect of our digital existence. Its importance, challenges, and future prospects underline the need for continuous research, development, and education in this field. As the digital landscape evolves, so too must our approach to cybersecurity.
500 Words Essay on Cyber Security
Cyber security, also known as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, damage, or destruction. In the digital era, the importance of cyber security is growing exponentially due to the increasing reliance on computer systems, the internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices like smartphones and televisions.
The significance of robust cyber security measures cannot be understated. Cyber attacks can lead to serious consequences like identity theft, extortion attempts, deletion of important data, and even the disruption of normal business operations. In more extreme cases, they can lead to the compromise of national security. Hence, cyber security is not just a concern for businesses or governments, but it is a potential threat to all internet users.
Cyber threats can be broadly divided into three categories: Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption; Cyber-attack often involves politically motivated information gathering; and Cyberterrorism is intended to undermine electronic systems to cause panic or fear. Examples of these threats are malware, phishing, ransomware, and social engineering.
Cyber Security Measures
In response to these threats, several cyber security measures are being employed. These include firewalls, intrusion detection systems, anti-virus software, and encryption. Furthermore, organizations are increasingly recognizing the importance of information assurance, where data integrity, confidentiality, and availability are assured.
As technology evolves, so does the complexity and sophistication of cyber threats. Hence, the future of cyber security lies in constant evolution and adaptation. Artificial Intelligence (AI) and Machine Learning (ML) are becoming integral in combating cyber threats. These technologies can learn and adapt to new threats, making them more efficient than traditional security measures.
In conclusion, cyber security is a crucial aspect of our digital lives, and its importance will only increase with time. To ensure a secure digital environment, individuals, organizations, and governments must understand the potential threats and employ robust security measures to counter them. The future of cyber security is promising, with the advent of AI and ML, but the road ahead is challenging, requiring constant vigilance and adaptation to new threats.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Cyber Bullying
- Essay on Customer Service
- Essay on Tourism in Kerala
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Presentations made painless
- Get Premium
127 Cyber Security Essay Topic Ideas & Examples
Inside This Article
With the increasing reliance on technology, cyber security has become a critical concern for individuals, organizations, and governments worldwide. As cyber threats continue to evolve and become more sophisticated, it is essential to stay informed about the latest trends and issues in this field. If you are tasked with writing an essay on cyber security, here are 127 topic ideas and examples to get your creative juices flowing.
The role of artificial intelligence in enhancing cyber security.
The impact of cyber attacks on critical infrastructure.
The ethical considerations of cyber warfare.
The legal frameworks governing cyber security.
The challenges of securing the Internet of Things (IoT) devices.
The role of encryption in protecting sensitive information.
The effectiveness of password policies in preventing cyber attacks.
The psychology behind social engineering attacks.
The impact of cyber attacks on the global economy.
The future of biometrics in cyber security.
The role of cyber insurance in mitigating cyber risks.
The ethics of hacking for the greater good.
The impact of cyber attacks on healthcare systems.
The role of education in raising cyber security awareness.
The challenges of securing cloud computing environments.
The implications of quantum computing on cyber security.
The importance of international cooperation in combating cyber crime.
The role of cyber security in protecting intellectual property.
The impact of cyber attacks on national security.
The challenges of securing critical data in the cloud.
The role of cybersecurity audits in identifying vulnerabilities.
The impact of cyber attacks on the banking and financial sector.
The ethical implications of government surveillance for cyber security purposes.
The role of cybersecurity professionals in addressing the skills gap.
The challenges of securing personal information in the digital age.
The impact of cyber attacks on elections and democratic processes.
The role of user awareness training in preventing cyber attacks.
The implications of data breaches for consumer trust.
The challenges of securing mobile devices in the workplace.
The role of cyber security in protecting personal privacy.
The impact of cyber attacks on small businesses.
The role of cyber security in safeguarding intellectual property in academia.
The challenges of securing critical infrastructure in developing countries.
The ethical considerations of vulnerability disclosure.
The impact of cyber attacks on the transportation sector.
The role of cyber security in protecting children online.
The challenges of securing Internet of Things (IoT) in smart homes.
The implications of cyber attacks on the aviation industry.
The role of cyber security in protecting against ransomware attacks.
The impact of cyber attacks on the entertainment industry.
The challenges of securing e-commerce platforms.
The role of cyber security in preventing identity theft.
The implications of cyber attacks on the energy sector.
The ethical considerations of government backdoor access to encrypted data.
The impact of cyber attacks on the hospitality and tourism industry.
The role of cyber security in protecting sensitive government information.
The challenges of securing online gaming platforms.
The implications of cyber attacks on the media and journalism.
The role of cyber security in protecting against social media threats.
The impact of cyber attacks on the transportation and logistics industry.
The challenges of securing online banking and financial transactions.
The role of cyber security in protecting against insider threats.
The implications of cyber attacks on the education sector.
The ethical considerations of using cyber weapons in warfare.
The impact of cyber attacks on the retail industry.
The role of cyber security in protecting against insider trading.
The challenges of securing online voting systems.
The implications of cyber attacks on the gaming industry.
The role of cyber security in protecting against intellectual property theft.
The impact of cyber attacks on the healthcare and pharmaceutical industry.
The challenges of securing social media platforms.
The ethical considerations of cyber security in autonomous vehicles.
The implications of cyber attacks on the hospitality industry.
The role of cyber security in protecting against credit card fraud.
The impact of cyber attacks on the manufacturing industry.
The challenges of securing online dating platforms.
The implications of cyber attacks on the insurance industry.
The role of cyber security in protecting against corporate espionage.
The impact of cyber attacks on the food and beverage industry.
The challenges of securing online marketplaces.
The implications of cyber attacks on the pharmaceutical industry.
The role of cyber security in protecting against intellectual property infringement.
The impact of cyber attacks on the nonprofit sector.
The challenges of securing online streaming platforms.
The ethical considerations of cyber security in wearable technology.
The implications of cyber attacks on the real estate industry.
The role of cyber security in protecting against medical identity theft.
The impact of cyber attacks on the telecommunications industry.
The challenges of securing online job portals.
The implications of cyber attacks on the automotive industry.
The role of cyber security in protecting against data breaches in the legal sector.
The impact of cyber attacks on the music industry.
The challenges of securing online auction platforms.
The implications of cyber attacks on the construction industry.
The role of cyber security in protecting against online harassment.
The impact of cyber attacks on the advertising and marketing industry.
The challenges of securing online learning platforms.
The implications of cyber attacks on the fashion industry.
The role of cyber security in protecting against online stalking.
The impact of cyber attacks on the sports industry.
The challenges of securing online travel booking platforms.
The implications of cyber attacks on the beauty and cosmetics industry.
The role of cyber security in protecting against online scams.
The impact of cyber attacks on the hospitality and catering industry.
The challenges of securing online dating applications.
The implications of cyber attacks on the healthcare and wellness industry.
The role of cyber security in protecting against online bullying.
The impact of cyber attacks on the entertainment and events industry.
The challenges of securing online food delivery platforms.
The implications of cyber attacks on the fitness and wellness industry.
The role of cyber security in protecting against online fraud.
The impact of cyber attacks on the home services industry.
The challenges of securing online social networking platforms.
The implications of cyber attacks on the pet care industry.
The role of cyber security in protecting against online piracy.
The impact of cyber attacks on the restaurant industry.
The challenges of securing online fashion retail platforms.
The implications of cyber attacks on the healthcare and fitness industry.
The role of cyber security in protecting against online hate speech.
The impact of cyber attacks on the wedding and event planning industry.
The challenges of securing online grocery delivery platforms.
The implications of cyber attacks on the gaming and entertainment industry.
The impact of cyber attacks on the music and entertainment industry.
The challenges of securing online travel and tourism platforms.
The implications of cyber attacks on the beauty and wellness industry.
The role of cyber security in protecting against online identity theft.
The impact of cyber attacks on the fashion and retail industry.
The challenges of securing online health and wellness platforms.
The implications of cyber attacks on the food and beverage industry.
These essay topic ideas cover a broad range of industries and sectors, highlighting the pervasive nature of cyber security threats. Whether you choose to explore the implications of cyber attacks on a specific industry, examine the challenges of securing a particular platform, or discuss the ethical considerations of cyber security, there are endless possibilities for research and analysis in this field. Remember to choose a topic that interests you and aligns with your objectives, ensuring a rewarding and engaging essay-writing experience.
Want to create a presentation now?
Instantly Create A Deck
Let PitchGrade do this for me
Hassle Free
We will create your text and designs for you. Sit back and relax while we do the work.
Explore More Content
- Privacy Policy
- Terms of Service
© 2023 Pitchgrade

Empowering Protection in the Digital Age
The Importance of Cyber Security in Today’s World
- By: Samuel Norris
- Time to read: 24 min.

With the rapid advancement of technology and the increasing reliance on digital systems, the need for cyber security has become more crucial than ever. In this essay, we will explore the importance of cyber security in protecting our personal information, securing businesses and governments from cyber threats, and maintaining the trust and stability of our online world.
The importance of cyber security in protecting personal information

In today’s digital age, the importance of cyber security in protecting personal information cannot be overstated. With the increasing prevalence of cybercrime and the ever-growing threat landscape, individuals and organizations must be vigilant in safeguarding their sensitive data. Cyber security measures are crucial not only to protect personal information from unauthorized access but also to maintain the integrity and confidentiality of data.
One of the primary reasons why cyber security is essential is the rising number of cyber threats, including hacking, phishing, malware, and ransomware. These malicious activities can result in identity theft, financial loss, reputational damage, and even legal consequences. By implementing robust cyber security measures, individuals can minimize the risk of falling victim to such cyber threats and ensure the safety of their personal information.
Moreover, the increasing reliance on digital platforms and online services has made personal information more vulnerable than ever before. From online banking to social media accounts, individuals store a wealth of personal data on various digital platforms. Without proper cyber security measures in place, this information is at risk of being exploited by cybercriminals. Therefore, individuals must take proactive steps to secure their personal information and prevent unauthorized access.
Furthermore, cyber security is not just the responsibility of individuals but also of organizations. Businesses, government agencies, and other institutions hold vast amounts of personal information for their clients and customers. Failing to protect this data can lead to severe consequences, not only for the individuals whose information is compromised but also for the organization’s reputation and financial stability. By investing in robust cyber security measures, organizations can demonstrate their commitment to protecting personal information and build trust with their stakeholders.
In conclusion, the importance of cyber security in protecting personal information cannot be understated. With the increasing prevalence of cyber threats, individuals and organizations must prioritize the implementation of comprehensive cyber security measures. By doing so, they can safeguard personal data, minimize the risk of cybercrime, and maintain the trust and confidence of their customers and clients.
Cyber attacks and their impact on businesses and economies

Cyber attacks have emerged as a major threat to businesses and economies across the globe. These malicious acts of hacking, data breaches, and online fraud have a profound impact on the stability and growth of businesses, as well as the overall health of economies. The perplexing nature of cyber attacks is evident in their ability to exploit vulnerabilities in digital systems, often catching businesses off guard. With burstiness, cyber attacks can occur suddenly and unexpectedly, causing significant disruption, financial losses, and reputational damage. Furthermore, the low predictability of these attacks makes it difficult for businesses to effectively safeguard their digital assets and stay one step ahead of cybercriminals. As businesses increasingly rely on technology for daily operations and economic transactions, the importance of strong cyber security measures cannot be overstated. Implementing robust security protocols, such as firewalls, encryption, and multi-factor authentication, is crucial for businesses to mitigate the risks posed by cyber attacks. Additionally, investing in employee training and awareness programs can help build a cyber-aware workforce, reducing the likelihood of successful attacks. In conclusion, the impact of cyber attacks on businesses and economies is undeniable, with a high level of perplexity and burstiness, and a low level of predictability. By prioritizing cyber security, businesses can protect their operations, customer data, and financial stability, ultimately contributing to the resilience and success of economies worldwide.
The role of cyber security in safeguarding national security

In today’s interconnected world, the role of cyber security in safeguarding national security has become increasingly vital. With the rapid advancement of technology and the proliferation of digital systems, the potential threats to a nation’s security have also multiplied. Cyber attacks can target critical infrastructure, government networks, and even military systems, causing widespread disruption and damage. Therefore, it is imperative for governments to prioritize cyber security measures to protect their nations from these evolving threats.
Cyber security plays a crucial role in safeguarding national security by preventing unauthorized access to sensitive information and networks. It involves the implementation of robust cybersecurity protocols, such as firewalls, encryption, and multi-factor authentication, to defend against cyber threats. By securing networks and systems, governments can ensure the confidentiality, integrity, and availability of critical data, thereby safeguarding national secrets, defense strategies, and citizen information.
Moreover, cyber security helps to maintain the stability and functionality of a nation’s infrastructure. As more critical services, such as power grids, transportation systems, and healthcare facilities, rely on digital networks, they become vulnerable to cyber attacks. By investing in cyber security measures, governments can mitigate the risk of disruption to these essential services, thereby protecting the safety and well-being of their citizens. Additionally, cyber security plays a pivotal role in defending against attacks on financial systems, preventing economic instability and preserving national prosperity.
Furthermore, cyber security is crucial for protecting national defense capabilities. Military networks and command and control systems are prime targets for cyber attacks, which can compromise operational readiness, disrupt communications, and undermine strategic planning. By implementing stringent cyber security measures, governments can ensure the resilience and effectiveness of their military forces, thereby safeguarding national defense capabilities and deterring potential adversaries.
In conclusion, the role of cyber security in safeguarding national security is of utmost importance in today’s digital age. By prioritizing and investing in robust cyber security measures, governments can protect critical infrastructure, defend against cyber attacks, and ensure the confidentiality and integrity of sensitive data. As the threat landscape continues to evolve, it is imperative for nations to stay ahead by continuously enhancing their cyber security capabilities and collaborating with international partners to combat cyber threats.

Click here to preview your posts with PRO themes ››
The evolving threat landscape and the need for stronger cyber security measures

In today’s rapidly evolving digital landscape, the threat of cyber attacks looms larger than ever before. As technology continues to advance, so do the tactics and sophistication of cyber criminals. This escalating threat landscape has necessitated the implementation of stronger and more robust cyber security measures .
Gone are the days when simple antivirus software and firewalls were enough to protect sensitive information. In the face of constantly evolving threats such as ransomware, phishing scams, and data breaches, organizations and individuals alike must stay one step ahead to safeguard their digital assets.
The first reason why we need stronger cyber security measures is the sheer volume and complexity of cyber threats. Cyber criminals are constantly devising new ways to exploit vulnerabilities in software, networks, and even human behavior. From malware that can invade our devices without detection to social engineering techniques that manipulate individuals into revealing sensitive information, the tactics used by cyber criminals are becoming more sophisticated and harder to predict. Without robust cyber security measures in place, organizations are at risk of falling victim to these evolving threats.
Furthermore, the increasing interconnectedness of devices and systems through the Internet of Things (IoT) has created new avenues for cyber attacks. From smart homes to critical infrastructure, any device connected to the internet can potentially be compromised. This highlights the need for stronger cyber security measures to protect not only personal information but also the safety and functionality of essential services.
Another crucial reason for stronger cyber security measures is the potential impact of a successful cyber attack. The consequences can be devastating, both financially and reputationally. Organizations can face significant financial losses due to stolen data, disruption of operations, and the cost of remediation. Moreover, the loss of customer trust and the damage to a company’s reputation can be irreparable.
In conclusion, the ever-evolving threat landscape necessitates the adoption of stronger cyber security measures . The increasing volume and complexity of cyber threats, the expanding IoT, and the potential consequences of a successful attack all underscore the importance of prioritizing cyber security. Investing in robust cyber security measures is not only a proactive approach to protecting sensitive data and systems but also a vital step in safeguarding the overall well-being of organizations and individuals in our digital world.
Cyber security best practices for individuals and organizations

Cyber security is not just a concern for governments and large corporations; it is equally crucial for individuals and small organizations. In today’s digital age, where cyber threats are constantly evolving, implementing best practices is essential to protect sensitive information and maintain data integrity. This article will discuss some of the top cyber security best practices that individuals and organizations should follow.
- Strong and Unique Passwords: One of the simplest yet most effective ways to enhance cyber security is by using strong and unique passwords. Avoid using common passwords or personal information that can be easily guessed. Consider using a password manager to generate and securely store complex passwords.
- Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a second verification step, such as a code sent to your mobile device, in addition to your password.
- Regular Software Updates: Keeping all software and operating systems up to date is crucial. Software updates often include patches for known vulnerabilities, which hackers can exploit. Set up automatic updates to ensure that you are always running the latest versions.
- Secure Wi-Fi Networks: Protect your home or office Wi-Fi network with a strong and unique password. Additionally, consider enabling network encryption, such as WPA2, to secure the communication between devices and the network.
- Employee Training and Awareness: Organizations should prioritize cyber security training and awareness programs for their employees. This helps ensure that everyone understands the importance of following security protocols and recognizes potential threats like phishing emails or suspicious links.
- Regular Data Backups: Regularly backing up important data is crucial in case of a cyber attack or data loss. Store backups on separate devices or in the cloud, and test the restoration process periodically to ensure the data can be recovered.
- Firewalls and Antivirus Software: Install and regularly update firewalls and antivirus software on all devices. These security tools provide an additional layer of protection against malware, viruses, and other cyber threats.
- Secure Web Browsing: Be cautious when browsing the internet. Avoid clicking on suspicious links or downloading files from untrusted sources. Use reputable web browsers and consider using browser extensions that provide additional security features.
By implementing these cyber security best practices, individuals and organizations can significantly reduce the risk of falling victim to cyber attacks and protect sensitive information from unauthorized access. Stay vigilant, stay informed, and stay secure!
The cost of cyber attacks and the value of investing in cyber security
In today’s digital age, the cost of cyber attacks is staggering. The value of investing in cyber security cannot be overstated. Cyber attacks not only lead to significant financial losses for businesses, but also result in reputational damage, legal consequences, and potential customer distrust. It is crucial for organizations to understand the true extent of the impact cyber attacks can have on their bottom line.
The financial cost of cyber attacks is multifaceted. The direct expenses include incident response, recovery, and potential ransom payments. However, the long-term financial repercussions often extend far beyond these immediate costs. Companies may suffer from lost revenue due to downtime, loss of intellectual property, or the need to invest in new security measures to prevent future attacks. Additionally, there are legal expenses and fines that can result from non-compliance with data protection regulations.
Furthermore, the intangible costs of cyber attacks are equally significant. A breach of customer data can lead to a loss of trust and loyalty, impacting customer retention and acquisition. The damage to reputation may result in decreased brand value and a loss of competitive advantage. Rebuilding trust and repairing a damaged reputation can be a time-consuming and expensive process.
Investing in cyber security is essential to mitigate the risks posed by cyber attacks. By implementing robust security measures and proactive monitoring, organizations can greatly reduce the likelihood and impact of successful attacks. The investment in cyber security is not just a cost, but rather an investment in the longevity and resilience of the business.
Cyber security measures include securing networks, implementing strong access controls, regularly updating and patching software, educating employees about security best practices, and conducting regular security audits. By staying ahead of evolving threats and investing in the right technology and expertise, organizations can enhance their ability to detect, respond to, and recover from cyber attacks.
In conclusion, the cost of cyber attacks is not limited to immediate financial losses. The long-term consequences, including reputational damage and legal ramifications, can be equally devastating. Investing in cyber security is not only a smart financial decision, but also a critical step in safeguarding the future of any organization. By understanding the true cost of cyber attacks and the value of investing in cyber security, businesses can make informed decisions to protect themselves and their stakeholders.
The correlation between cyber security and privacy in the digital age
In the fast-paced digital age, the correlation between cyber security and privacy has become increasingly intricate and crucial. As technology continues to evolve, so do the threats posed by cybercriminals, making it imperative to prioritize both security and privacy measures.
Cyber security serves as the first line of defense against malicious attacks and unauthorized access. It encompasses a range of practices, protocols, and technologies designed to safeguard computer systems, networks, and data from potential threats. By implementing robust cyber security measures, individuals and organizations can protect their sensitive information, prevent data breaches, and maintain the confidentiality and integrity of their digital assets.
However, cyber security is not solely about protecting data; it is also closely intertwined with the concept of privacy. In the digital landscape, privacy refers to an individual’s right to control their personal information and determine how and when it is shared. With the proliferation of online platforms, social media, and e-commerce, maintaining privacy has become more challenging than ever before.
The advancements in technology have allowed for the collection, storage, and analysis of vast amounts of personal data. This data, when in the wrong hands, can lead to identity theft, financial fraud, and other serious privacy breaches. Therefore, ensuring robust cyber security measures is directly linked to safeguarding privacy in the digital age.
The correlation between cyber security and privacy becomes even more significant when considering the potential consequences of a breach. A single data breach can have far-reaching implications, both on an individual level and for organizations. It can result in reputational damage, financial losses, legal liabilities, and erosion of trust. Such breaches can also compromise national security, disrupt critical infrastructure, and impact the overall stability of the digital ecosystem.
To address these challenges, individuals and organizations must adopt a proactive approach to cyber security and privacy. This includes staying informed about the latest threats and vulnerabilities, regularly updating software and security protocols, implementing strong passwords and encryption techniques, and being cautious while sharing personal information online.
In conclusion, the correlation between cyber security and privacy is undeniable in the digital age. Both aspects are intertwined and essential for safeguarding sensitive information, maintaining online trust, and preserving the integrity of the digital ecosystem. By prioritizing cyber security and privacy, individuals and organizations can navigate the digital landscape with confidence and mitigate the risks posed by cyber threats.
The role of government in promoting and enforcing cyber security regulations
In today’s digital age, the role of government in promoting and enforcing cyber security regulations is of paramount importance. With the increasing frequency and sophistication of cyber threats, it has become imperative for governments to actively intervene and safeguard their nations’ vital digital infrastructure and sensitive information. This article delves into the reasons why the government plays a crucial role in ensuring cyber security and the impact of their regulations on protecting individuals, businesses, and national security.
First and foremost, the government has the authority and resources to establish robust cyber security regulations that set standards and guidelines for all sectors. By creating a legal framework, they enforce compliance and hold organizations accountable for implementing appropriate security measures. This helps to create a culture of cyber security awareness and ensures that businesses prioritize the protection of valuable data.
Moreover, governments have access to intelligence and information sharing networks that enable them to identify emerging threats and vulnerabilities. By actively monitoring cyber activities, they can proactively respond to potential attacks and prevent major security breaches. This proactive approach not only protects individuals and businesses but also strengthens the overall resilience of the nation’s digital infrastructure.
Additionally, the government plays a vital role in promoting international cooperation and establishing global cyber security standards. Since cyber threats transcend national boundaries, collaboration between governments is essential to address these challenges collectively. By participating in international forums and treaties, governments can foster information exchange, capacity building, and joint efforts to combat cybercrime.
Furthermore, the government’s involvement in cyber security regulations is crucial for national security. Cyber attacks have the potential to disrupt critical infrastructure, compromise defense systems, and even manipulate elections. By establishing stringent regulations and investing in cyber defense capabilities, governments can safeguard their nation’s sovereignty and protect against potential cyber warfare.
However, it is important to strike a balance between promoting cyber security and ensuring individual privacy rights. Governments need to find the right balance between collecting necessary data for security purposes and protecting citizens’ privacy. This requires transparent and accountable governance, with checks and balances in place to prevent misuse of power.
In conclusion, the role of government in promoting and enforcing cyber security regulations is vital in today’s interconnected world. With the increasing complexity and severity of cyber threats, governments need to take proactive measures to protect their nations’ digital assets. By establishing robust regulations, fostering international cooperation, and investing in cyber defense capabilities, governments can create a safe and secure digital environment for individuals, businesses, and national security.
Emerging technologies and their impact on cyber security challenges
In today’s rapidly evolving technological landscape, emerging technologies have brought about immense advancements and opportunities. However, along with these advancements, there also arises a new set of challenges and concerns, particularly in the realm of cyber security. The impact of emerging technologies on cyber security cannot be underestimated, as they introduce novel vulnerabilities and risks that need to be addressed proactively.
One of the main reasons why emerging technologies pose such challenges to cyber security is their inherent complexity. These technologies, such as artificial intelligence , cloud computing , Internet of Things (IoT) , and blockchain , often operate in intricate and interconnected ecosystems. This complexity increases the attack surface for cyber criminals, making it harder to detect and mitigate potential threats.
Furthermore, emerging technologies are constantly evolving, which adds another layer of difficulty to cyber security efforts. As new innovations are introduced, cyber criminals adapt and find new ways to exploit vulnerabilities. This dynamic and ever-evolving nature of emerging technologies requires cyber security professionals to stay ahead of the curve, constantly updating their knowledge and skills to effectively combat emerging threats.
Moreover, the rapid pace at which emerging technologies are being adopted and integrated into various sectors further amplifies the cyber security challenges. Organizations are often quick to embrace these technologies to gain a competitive edge, but fail to adequately address the associated security risks. This creates a gap that cyber criminals can exploit, potentially leading to data breaches, financial losses, and reputational damage.
Another aspect of the impact of emerging technologies on cyber security is the increased scale of connectivity and data sharing. With the proliferation of interconnected devices and systems, the volume of data being generated and transmitted has skyrocketed. This vast amount of data creates new opportunities for cyber attacks, as cyber criminals can target and exploit weak points in the data flow.
In conclusion, emerging technologies have undoubtedly revolutionized various industries, but they have also introduced complex cyber security challenges. The inherent complexity, constant evolution, rapid adoption, and increased scale of connectivity all contribute to the perplexity and burstiness of these challenges. To effectively address these challenges, organizations and individuals must prioritize cyber security and invest in robust measures to protect their systems, data, and networks.
The future of cyber security: trends and predictions
The future of cyber security is an enigmatic landscape that is constantly evolving, filled with both promising advancements and daunting challenges. As technology continues to advance at an unprecedented rate, the need for robust cyber security measures becomes increasingly vital. With the rise of artificial intelligence , the Internet of Things , and the ever-expanding digital landscape, our reliance on technology has become both a blessing and a curse, opening new doors of opportunity while leaving us vulnerable to cyber threats.
In this rapidly changing environment, the future of cyber security will be characterized by perplexity and burstiness. Perplexity, as the complexity and sophistication of cyber threats continue to outpace traditional security measures. Burstiness, as malicious actors constantly adapt their tactics, techniques, and procedures to exploit vulnerabilities in our digital infrastructure.
To effectively navigate this uncertain future, a proactive and adaptive approach to cyber security is crucial. Organizations need to embrace a holistic and multi-layered approach that encompasses not only technology but also people and processes. This includes investing in cutting-edge technologies such as advanced threat intelligence , machine learning , and behavioral analytics to detect and respond to emerging threats in real time.
Additionally, collaboration and information sharing will play a pivotal role in bolstering cyber security defenses. Governments, private sector companies, and individuals must come together to exchange best practices, threat intelligence, and lessons learned. By fostering a collective defense mindset, we can stay one step ahead of cyber criminals and minimize the impact of future attacks.
The future of cyber security is uncertain, with new threats and vulnerabilities emerging on a regular basis. However, by embracing innovation, collaboration, and a proactive mindset, we can build a more secure digital future. It is essential that we invest in research and development, education and awareness, and the cultivation of a skilled cyber security workforce to tackle the challenges that lie ahead. Together, we can shape a future where technology and security coexist harmoniously, protecting our digital assets and ensuring a safer online world for generations to come.
What is cyber security?
Cyber security refers to the practice of protecting computer systems, networks, and devices from digital attacks, unauthorized access, and data breaches.
Why do we need cyber security?
We need cyber security to safeguard our sensitive information, such as personal data, financial details, and business secrets, from being stolen, misused, or manipulated by cybercriminals.
What are the common cyber threats?
Common cyber threats include malware (such as viruses and ransomware), phishing attacks, social engineering, hacking, and denial-of-service (DoS) attacks.
How can cyber security help individuals?
Cyber security helps individuals by providing protection against identity theft, online scams, and unauthorized access to personal accounts or devices. It allows for safe online banking, shopping, and communication.

Why is cyber security important for businesses?
Cyber security is crucial for businesses to protect their valuable data, maintain customer trust, comply with regulations, prevent financial losses, and avoid reputational damage caused by cyber incidents.
What are some best practices for cyber security?
Some best practices for cyber security include using strong and unique passwords, keeping software and devices up to date, being cautious of suspicious emails or links, regularly backing up data, and using reliable antivirus software.
Is cyber security a constant concern?
Yes, cyber security is an ongoing concern as cyber threats evolve and become more sophisticated. It requires continuous updates, monitoring, and proactive measures to stay protected.
Can individuals contribute to cyber security?
Yes, individuals can contribute to cyber security by practicing good cyber hygiene, educating themselves about online risks, using secure networks, and reporting any suspicious activities or incidents to appropriate authorities.
In conclusion, cyber security is crucial in today’s digital age. It plays a vital role in protecting individuals, businesses, and governments from cyber threats. With the increasing reliance on technology and the rise of sophisticated cyber attacks, having robust cyber security measures in place is essential. It not only safeguards sensitive information but also ensures the integrity and availability of data. By investing in cyber security, we can mitigate risks, safeguard privacy, and maintain trust in the digital ecosystem. Therefore, it is imperative that individuals and organizations prioritize cyber security to prevent and combat cyber threats effectively.
Related Posts

The Significance of Cyber Security Training
In today’s digital world, cyber security training has become crucial. With increasing cyber threats, organizations need to ensure their employees are equipped with the necessary skills to detect and prevent attacks. Training helps create awareness about potential risks, teaches best practices, and promotes a culture of security. It empowers individuals to safeguard sensitive data, mitigate threats, and contribute to a safe online environment.

The Importance of Cyber Security
Cyber security is more important than ever in today’s digital age. With the increasing number of cyber threats and attacks, it is crucial for individuals and businesses to protect their sensitive data. From financial transactions to personal information, cyber security ensures confidentiality, integrity, and availability. Learn why cyber security matters and how it impacts our daily lives.

Understanding Cyber Security Month: Importance and Impact
October is designated as Cyber Security Month, an annual campaign to raise awareness about the importance of online safety. Throughout the month, various organizations and individuals come together to promote cybersecurity practices and educate the public on how to protect themselves from cyber threats. Stay tuned for exciting events, informative resources, and practical tips to enhance your digital security this Cyber Security Month!
Home — Essay Samples — Information Science and Technology — Computers — Cyber Security
Essays on Cyber Security
Choosing a topic, types of essays, example thesis statements, example paragraphs, cyber security personal statement, target breach case study, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
Social Networking and Online Communication
Brief history of cyber security, cyber crimes and cyber security in modern world, cybersecurity and risk management, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Effects of Social Media on Cybercrime
The importance of cybersecurity: department of justice, yahoo and jp morgan chase, the history and concept of cyber security, impact realisation of cyber warfare, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Fundamental Steps of Cyber Security
Statement of purpose (information technology and cyber security), data mining and machine learning methods for cyber security intrusion detection, best ways to have secure coding at your company, the issue of digital security risks and its types, a survey on android malwares and their detection techniques, the notions of cyber-warriors in social media, human error, the weakest link in cybersecurity, digital crime and digital terrorism: the future of technology, general data protection regulation, cyber bullying, its effects and ways to stop, cyber crimes, cyber terrorism as a major security challenge, the most damaging hackers' attacks in history, malware classification using machine learning, national security and its need for technological advancement, international cybercrime law: past, present, future perspectives, the future of cyber security: what we can expect, research on cyberwarfare: cyberattacks, experiments, and future predictions, the role of information security, relevant topics.
- Digital Era
- Computer Science
- Virtual Reality
- Artificial Intelligence
- 5G Technology
- Disadvantages of Technology
- Negative Impact of Technology
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Skip to main content
India’s Largest Career Transformation Portal
Essay on Cyber Security for Students in English [500 Words]
January 3, 2021 by Sandeep
Essay on Cyber Security: The data, networks and other important confidential information present online needs to be protected from prospective hackers and hacker groups to prevent them from leakage. Cyber security acts and rules are enacted and enforced in situations where there is a cyber-crime on the spot. Accessing data in an unauthorized way, destruction of information, using data without permission, introducing malicious software and viruses to extract data are some of the common cyber crimes taking place worldwide.
Essay on Cyber Security 500 Words in English
Below we have provided Cyber Security Essay in English, suitable for class 6, 7, 8, 9 and 10.
“If you spend more on coffee than on IT, you will be hacked.” ~ Richard Clarke
The world is now one global digital village with all of its population and cultures connected. India has the second-largest internet-using population in the world, with more than 400 million users. Cybersecurity is the protection of computer systems from damage to their hardware, software and electronic data. It is also a measure to prevent thefts, disruption of data and misleading of services. The need for cybersecurity has drastically increased because of the huge reliance on wireless networks and the internet .
Need for Cyber Security
It is estimated that on average, companies spend more than 400 billion dollars on cybersecurity. While many choose to protect their systems, others do not invest in cybersecurity to keep their costs down. Following are some reasons why you should invest in cybersecurity now more than ever-:
The cost of a security breach can be very high for a company. It not only causes financial damage but affects the reputation of the firm as well. Clients or customers upon knowing that a breach has happened would think that the company has a flawed security system and would hence like to take their business elsewhere. People who illegally enter into your electronic systems are known as hackers.
The number of hackers in the world has increased, and so has their level of sophistication. When even Deloitte, the largest cybersecurity consultant company in the world was not able to protect itself from a cyber-attack, think of how easy it would be for a hacker to enter your cell phones. The easy availability of hacking tools on the internet has made cyber attacks an even stronger possibility. These tools are getting more updated and superior day by day, and so are the people using them.
Cyber Crime
Cybercrime is any criminal or illegal activity that takes place on or through the internet. There are various types of cybercrimes-: Many innocent individuals, mostly women, are victims of cyberstalking. It is a type of sexual harassment that involves sending messages and emails online. The content of these messages and emails may be threatening and even provocative.
Phishing is another very common type of cyber-attack. In this, identical emails are sent to a very large number of people. The cyber attacker poses as a trustworthy entity of an institution and tries to obtain sensitive information from you like your bank details, credit card details and passwords.
Email bombing and spamming have also been in use for a long time now. Email bombing happens when a cyber attacker sends thousands of emails to the same email addresses through the help of bots. The emails sent are mostly meaningless and use up lots of internet bandwidth. Because of receiving such heavy traffic in the account at once, the email accounts of many people are crashed, and then they fail to access them. Through email spamming, people are sent inappropriate links, fake news and attachments that when clicked on, inject viruses in the computer .
Benefits of Cyber Security
Individuals and companies are always on the risk of cyber-attacks. No one is safe from them in the current world. Hence, it is advisable to have a cyber security plan or some sort of protection software. The advantages of having a cybersecurity solution are as follows-:
The major advantage to companies is that cybersecurity helps in protecting their business. Small companies and newer businesses are more prone to such breaches, and hence, having a cybersecurity plan can save the company its resources in more than one way. It allows employees to work and surf freely without any threats and does not let work productivity diminish. Cybersecurity also helps the company’s website from shutting down by getting electronically infected. The crashing of the website can cause e-commerce giants to lose a lot of revenue and transactions.
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
Student Essays
Essays-Paragraphs-Speeches
Essay On Cyber Security | Importance, Risks & Challenges
The Cyber security is the need of today’s time. The world is getting on increasingly digital. Here in point, there comes the needs for us to strengthen our cyber security to face possible risk and cyber challenges. Here is the short essay in point that discusses the meaning, importance, risks, challenges and ways to deal with cyber security in today’s world. This essay is helpful for both children and students.
List of Topics
Essay on Cyber Security, its Meaning & Importance
Defining Cyber Security
Cyber security can be defined as the protection of systems, networks and data within cyberspace. Defending against losses, compromises, or attacks using preventative measures is the goal of cyber security
Meaning & Importance of Cyber Security in Modern World
Cybersecurity is a complex issue that cuts across multiple domains and requires multi-dimensional, multi-layered initiatives and responses. Since it involves various ministries and departments, it has proved to be a challenge for governments. In the absence of tangible perpetrators, the threat spectrum is diffused and varied, making it difficult to formulate a suitable response.
The goal of cybersecurity is to prevent unauthorized or unattended access, destruction, and changes to data, networks, programs, and other information. Security threats and cyber-attacks have made cybersecurity a very important issue in the modern world. There are many companies that develop software for data protection.
Using this software, the data will be protected. In addition to protecting information, cybersecurity helps to protect our system from virus attacks. The U.S. and China have the most internet users, followed by India.
Classification/Types of Cyber Security
Cyber security can be classified into two broad categories;
- Cyber crime
Cyber Warfare
Cyber crime.
Criminal activities using computers or networked devices are known as cybercrime. Most cybercrimes are performed by cybercriminals for financial gain, but other cybercrimes are undertaken to damage or disable computers or devices, while others use computers or networks to spread malicious software, illegal information or images. It causes frustration, anger & Loneliness among the victims.
In addition to its financial effects, cybercrime can involve many different types of profit-driven criminal activity, such as ransomware attacks, email and internet fraud, and identity fraud, as well as attempts to steal financial account, credit card or other payment card information.
How to Boost Cyber Security & Prevent Cyber crime
Although it may not be possible to eliminate cybercrime completely and ensure complete internet security, businesses can reduce their exposure to it by implementing an effective cybersecurity strategy that employs a defense-in-depth approach to securing systems, networks, and data.
The following steps can help reduce cybercrime risks:
- Create a clear policy and procedure for the business and its employees;
- Prepare plans for managing cybersecurity incidents;
- Provide an overview of the systems and data protection measures in place;
- Install two-factor authentication (2FA) keys or use two-factor authentication apps;
- When possible, enable 2FA for every online account;
- Verify verbally the authenticity of requests to send money by talking to a financial manager;
- Set up intrusion detection systems (IDS) to flag emails with extensions similar to company emails;
- Analyze each email request for a transfer of funds to determine if it is different from the norm;
- In order to prevent security breaches, employees should be continuously trained on cybersecurity procedures;
- Maintain all software release updates and patches on websites, endpoint devices, and systems; and
- Data and information should be backed up regularly to avoid data breaches and ransomware attacks.
Cyberwarfare is the use of computers and the networks that connect them to wage war against other states. Government and military networks are usually attacked in cyberwar in order to disrupt, destroy, or deny their use. Cyberspace is made up of computers and their networks. Almost every aspect of modern society depends on cyberspace, and developing countries are becoming more reliant on it each year.
From critical infrastructure to financial institutions and commerce to national security, almost everything modern society relies on cyberspace to function. Cyber attacks do share some similarities with other criminal attacks in that they produce the same result.
The role of cybersecurity in today’s world is growing due to the high penetration of the internet. Cybersecurity is becoming an increasingly dangerous issue to the security of a country. Among the citizens as well as the government, awareness of updated network and system security settings and the use of proper anti-virus should be spread so that your networking and system settings remain virus-free and secure.
Short Essay on Cyber Security & its Importance today
Cybersecurity is an effort to keep electronic gadgets such as laptops, smartphones, and tablets away from hackers and data thieves. It is always detrimental to the end user.
Nowadays, everyone needs to have proper cybersecurity with the increasing use of electronic gadgets. It ensures the protection of our private data and official and personal documents. Cyber Security is essential to ensure the safety and privacy of our data. When Cyber Security is not implemented, anyone can steal, misuse, and abuse our data without our authorization.
Keeping our data and important documents secure when using electronic gadgets is extremely important for all people who use them regularly and frequently. Cyber security has grave impact upon the mental health of youth. It has been the leading cause of frustration, depression , anger and uncertainty. Cyber Security is provided in many ways, some of which are Antivirus, Antimalware, End-User Protection, etc.
It is important to update your system software regularly. Choose a strong password when enabling security on your gadgets. Also, avoid clicking on uncertain and suspicious links. Keeping our devices secure with the help of the tools discussed above is crucial in the current digital world.
Related Posts:
![Essay on Secularism [ Features, Importance, Challenges ] Essay on Secularism [ Features, Importance, Challenges ]](https://mystudentsessays.com/wp-content/plugins/contextual-related-posts/default.png)
Reader Interactions
August 14, 2021 at 3:18 pm
How to writena book in this website?
August 16, 2021 at 5:01 am
Yes! You can get your post Published with us. For more contact us at the given email at contact Us page
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Kaspersky Premium
- Kaspersky Plus
- Kaspersky Standard
- Kaspersky Safe Kids
- Kaspersky Password Manager
- Renew Licence
- Trials & Downloads
- Small Business
- Medium Business
- Find a reseller
- Find a distributor
- Partnership with Kaspersky
- Get to know us
- Company overview
- Transparency
- Corporate News
- Awards & Recognitions
- Top 3 Rankings
- Press center
- Sponsorships
- Policy blog
What is Cyber Security?

Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
· Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
· Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
· Information security protects the integrity and privacy of data, both in storage and in transit.
· Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
· Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
· End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.

The scale of the cyber threat
The global cyber threat continues to evolve at a rapid pace, with a rising number of data breaches each year. A report by RiskBased Security revealed that a shocking 7.9 billion records have been exposed by data breaches in the first nine months of 2019 alone. This figure is more than double (112%) the number of records exposed in the same period in 2018.
Medical services, retailers and public entities experienced the most breaches, with malicious criminals responsible for most incidents. Some of these sectors are more appealing to cybercriminals because they collect financial and medical data, but all businesses that use networks can be targeted for customer data, corporate espionage, or customer attacks.
With the scale of the cyber threat set to continue to rise, global spending on cybersecurity solutions is naturally increasing. Gartner predicts cybersecurity spending will reach $188.3 billion in 2023 and surpass $260 billion globally by 2026. Governments across the globe have responded to the rising cyber threat with guidance to help organizations implement effective cyber-security practices.
In the U.S., the National Institute of Standards and Technology (NIST) has created a cyber-security framework . To combat the proliferation of malicious code and aid in early detection, the framework recommends continuous, real-time monitoring of all electronic resources.
The importance of system monitoring is echoed in the “ 10 steps to cyber security ”, guidance provided by the U.K. government’s National Cyber Security Centre. In Australia, The Australian Cyber Security Centre (ACSC) regularly publishes guidance on how organizations can counter the latest cyber-security threats.
Types of cyber threats
The threats countered by cyber-security are three-fold:
1. Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption.
2. Cyber-attack often involves politically motivated information gathering.
3. Cyberterrorism is intended to undermine electronic systems to cause panic or fear.
So, how do malicious actors gain control of computer systems? Here are some common methods used to threaten cyber-security:
Malware means malicious software. One of the most common cyber threats, malware is software that a cybercriminal or hacker has created to disrupt or damage a legitimate user’s computer. Often spread via an unsolicited email attachment or legitimate-looking download, malware may be used by cybercriminals to make money or in politically motivated cyber-attacks.
There are a number of different types of malware, including:
· Virus: A self-replicating program that attaches itself to clean file and spreads throughout a computer system, infecting files with malicious code.
· Trojans : A type of malware that is disguised as legitimate software. Cybercriminals trick users into uploading Trojans onto their computer where they cause damage or collect data.
· Spyware: A program that secretly records what a user does, so that cybercriminals can make use of this information. For example, spyware could capture credit card details.
· Ransomware: Malware which locks down a user’s files and data, with the threat of erasing it unless a ransom is paid.
· Adware: Advertising software which can be used to spread malware.
· Botnets: Networks of malware infected computers which cybercriminals use to perform tasks online without the user’s permission.
SQL injection
An SQL (structured language query) injection is a type of cyber-attack used to take control of and steal data from a database. Cybercriminals exploit vulnerabilities in data-driven applications to insert malicious code into a databased via a malicious SQL statement. This gives them access to the sensitive information contained in the database.
Phishing is when cybercriminals target victims with emails that appear to be from a legitimate company asking for sensitive information. Phishing attacks are often used to dupe people into handing over credit card data and other personal information.
Man-in-the-middle attack
A man-in-the-middle attack is a type of cyber threat where a cybercriminal intercepts communication between two individuals in order to steal data. For example, on an unsecure WiFi network, an attacker could intercept data being passed from the victim’s device and the network.
Denial-of-service attack
A denial-of-service attack is where cybercriminals prevent a computer system from fulfilling legitimate requests by overwhelming the networks and servers with traffic. This renders the system unusable, preventing an organization from carrying out vital functions.
Latest cyber threats
What are the latest cyber threats that individuals and organizations need to guard against? Here are some of the most recent cyber threats that the U.K., U.S., and Australian governments have reported on.
Dridex malware
In December 2019, the U.S. Department of Justice (DoJ) charged the leader of an organized cyber-criminal group for their part in a global Dridex malware attack . This malicious campaign affected the public, government, infrastructure and business worldwide.
Dridex is a financial trojan with a range of capabilities. Affecting victims since 2014, it infects computers though phishing emails or existing malware. Capable of stealing passwords, banking details and personal data which can be used in fraudulent transactions, it has caused massive financial losses amounting to hundreds of millions.
In response to the Dridex attacks, the U.K.’s National Cyber Security Centre advises the public to “ensure devices are patched, anti-virus is turned on and up to date and files are backed up”.
Romance scams
In February 2020, the FBI warned U.S. citizens to be aware of confidence fraud that cybercriminals commit using dating sites, chat rooms and apps. Perpetrators take advantage of people seeking new partners, duping victims into giving away personal data.
The FBI reports that romance cyber threats affected 114 victims in New Mexico in 2019, with financial losses amounting to $1.6 million.
Emotet malware
In late 2019, The Australian Cyber Security Centre warned national organizations about a widespread global cyber threat from Emotet malware.
Emotet is a sophisticated trojan that can steal data and also load other malware. Emotet thrives on unsophisticated password: a reminder of the importance of creating a secure password to guard against cyber threats.
End-user protection
End-user protection or endpoint security is a crucial aspect of cyber security. After all, it is often an individual (the end-user) who accidentally uploads malware or another form of cyber threat to their desktop, laptop or mobile device.
So, how do cyber-security measures protect end users and systems? First, cyber-security relies on cryptographic protocols to encrypt emails, files, and other critical data. This not only protects information in transit, but also guards against loss or theft.
In addition, end-user security software scans computers for pieces of malicious code, quarantines this code, and then removes it from the machine. Security programs can even detect and remove malicious code hidden in Master Boot Record (MBR) and are designed to encrypt or wipe data from computer’s hard drive.
Electronic security protocols also focus on real-time malware detection . Many use heuristic and behavioral analysis to monitor the behavior of a program and its code to defend against viruses or Trojans that change their shape with each execution (polymorphic and metamorphic malware). Security programs can confine potentially malicious programs to a virtual bubble separate from a user's network to analyze their behavior and learn how to better detect new infections.
Security programs continue to evolve new defenses as cyber-security professionals identify new threats and new ways to combat them. To make the most of end-user security software, employees need to be educated about how to use it. Crucially, keeping it running and updating it frequently ensures that it can protect users against the latest cyber threats.
Cyber safety tips - protect yourself against cyberattacks
How can businesses and individuals guard against cyber threats? Here are our top cyber safety tips:
1. Update your software and operating system: This means you benefit from the latest security patches.
2. Use anti-virus software: Security solutions like Kaspersky Total Security will detect and removes threats. Keep your software updated for the best level of protection.
3. Use strong passwords: Ensure your passwords are not easily guessable.
4. Do not open email attachments from unknown senders: These could be infected with malware.
5. Do not click on links in emails from unknown senders or unfamiliar websites: This is a common way that malware is spread.
6. Avoid using unsecure WiFi networks in public places: Unsecure networks leave you vulnerable to man-in-the-middle attacks.
Kaspersky Endpoint Security received three AV-TEST awards for the best performance, protection, and usability for a corporate endpoint security product in 2021 . In all tests Kaspersky Endpoint Security showed outstanding performance, protection, and usability for businesses.
Related Articles:
- What is Cybercrime: Risks and Prevention
- How to Avoid Most Types of Cybercrime
- Internet of Things Security Threats
- What is Spam and a Phishing Scams
Related Products and Services:
· Cyber Security for your Home Devices
· Small Business Cyber Security
· Advanced Endpoint Security for SMBs
· Corporate Cyber Security Services
· Cyber Security Awareness Training for Employees
· Enterprise Cyber Security for Industries
Related articles
174 Cybersecurity Essay Topics & Research Questions to Write About
Are you looking for cybersecurity essay topics? Check out our extensive list of trending titles and interesting cyber security essay examples! You can use these ideas for your project, presentation, thesis, or research paper. And our questions for debates can also be used as cyber security argumentative essay topics!
🏆 Best Essay Topics on Cybersecurity
✍️ cybersecurity essay topics for college, 👍 good cybersecurity research topics & essay examples, 🎓 most interesting cybersecurity paper topics, 💡 trending cybersecurity topics to write about, ❓ cybersecurity research questions, 🖥️ cybersecurity topics for presentation, 🗣️ cybersecurity debate topics.
- Cybersecurity in Amazon Business and Its Industry
- Cyber Security: The Nature and Scope of Cybercrime
- PEST Factors and PEST Analysis in Cybersecurity Industry
- Cyber Security Challenges for Business
- Cyber Security at Ports: Advantages and Disadvantages
- Equifax Case Study: Cybersecurity Measures
- Literature Review of Articles on Cyber Security of Young Children
- Cybersecurity and Protection in Healthcare Studying the topic of cybersecurity in healthcare is a valuable source for creating the best ways to protect against hacker attacks.
- Cybersecurity for Amazon Web Services Infrastructure This paper gives a detailed description of the best strategies and initiatives to maintain the security of data and services that reside on Amazon Web Services infrastructure.
- Blue Team Con: Cybersecurity Conference Blue Team Con is a conference performed yearly for cybersecurity specialists, working with companies directly to ensure the safety of their assets, students, and entrepreneurs.
- Cybersecurity in Cruise Ship Industry Even though cruise ships are equipped with the most advanced technologies, they remain vulnerable to cyberattacks that may lead to economic, political, and social damages.
- Baiting in Cybersecurity: Realization and Prevention A type of cyber-attack such as baiting is part of social engineering. It is a term that refers to looting users’ data or compromising the integrity of an IT infrastructure.
- Ethics in Cybersecurity and Software Engineering Ethical philosophy as a whole implies a search for definitions and mechanisms for the systematic distinction between right and wrong.
- The Future of Computers and Cybersecurity The cybersecurity sector is almost always changing in response to hackers’ shifting habits and new threats. Therefore, the future of cybersecurity is almost impossible to predict.
- The Need for Cybersecurity Data Science It is critical to explore how data science helps cybersecurity defense strategies and understand its importance.
- Public-Private Partnerships for Election Systems Cybersecurity The paper explores the public-private partnership and explains benefits for businesses, costs, and risks, and offers a recommendation for companies.
- Cyber Security: Policy, Processes and Practices There are potential challenges associated with cyber security. Increased internet connections and applications require robust measures for the management of cyber security.
- Cybersecurity: The Role in Business The human factor plays a considerable role in the reliability of cybersecurity, as both user error and abuse of access-related privileges represent cyber threats.
- Cybersecurity in Healthcare Organizations Data breaches in healthcare facilities greatly impact patients, and they may lose confidence in the healthcare system.
- Confidentiality in Cybersecurity Confidentiality is one of the major concepts that contribute to the security of users online as well as their personal data used in online activities.
- Cybersecurity in the Energy Sector Cybersecurity is protecting cyberspace, the infrastructure that stores and transfers information, from malicious cyberattacks.
- Island Banking Services: Cybersecurity Strategy and Implementation Plan This paper aims to describe the cybersecurity strategy and its implementation plan for Island Banking Services that is a firm that works in Financial Transactions Processing.
- Cyber Security Management and Policy Cyber security threats should be a concern for any company and especially for businesses that employ a large number of people and collect substantial quantities of data.
- Sifers-Grayson Company: Cybersecurity Incident The business impact of the cybersecurity incident should be analyzed from the perspectives of operational efforts and transformations.
- Cybersecurity of Central Institutions The issue of cybersecurity acquires the top priority and should be given significant attention to guarantee the effective functioning of central institutions.
- Blockchain Technology and Cybersecurity Blockchain-related technologies are innately safer for businesses. At the same time, small businesses do not benefit from technology as much as large-scale ones.
- Cyber Security in Business Organizations The most dangerous crime associated with technology is the emergence of hackers, who steal organizations’ information for financial benefits.
- Cybersecurity Threats to the Energy Sector The modern era of global technologies creates a two-fold situation. On the one hand, new advanced digital technologies are emerging to automate energy production.
- Cybersecurity and Its Importance in Schools Cybersecurity is becoming important for schools due to the ever-increasing number of risks, the typology of which is becoming more extensive and diverse.
- Cybersecurity Threats America Faces This paper analyzes the articles on engaging consumers in cyber security, the cyber frontier and digital pitfalls in the global south, and the cybersecurity workforce gap.
- Store My Bits International Company’s Cybersecurity Risk Analysis The paper gives full details of the plan for mitigating and addressing viruses problems associated with modern technologies and the Internet.
- Russia-Ukraine War as Cybersecurity Challenge This paper will address the most pressing topic of recent weeks, namely the war that Russia has launched against Ukraine, and touch on a severe aspect related to cybersecurity.
- The Internet of Things Cybersecurity Improvement Act This research paper discusses the Internet of Things Cybersecurity Improvement Act and what it means for the public and the government.
- Statistics for an IT Project Manager and in Cybersecurity Statistical analysis as the means of managing a vast amount of data represents an untapped potential for any IT manager.
- Cybersecurity and Crimes as Advanced Persistent Threat The purpose of this article is to introduce the features, attack process, and methods and techniques used by advanced persistent threat attackers to carry out attacks.
- Cyber Security Process and Technology The management should also consider updating the computer’s software regularly to enhance protection from stalkers.
- Cyber Security Breaches and Ransomware Attacks This research paper attempts to describe ransomware as a complex malware and its characteristics, it also discusses the factors, detection, and prevention of malicious software.
- Innovation in the Cybersecurity Industry This paper explains the role of innovation in the cybersecurity industry and identifies the major developers related to inventions.
- Researching of Cybersecurity and Cybercrime The paper will discuss the technology transfer processes followed by the funding sources for technologies in the cybersecurity field
- Integrating NIST’s Cybersecurity Framework With IT Governance Frameworks An Information Security Management System (ISMS) is a primary asset responsible for an organization’s cybersecurity.
- Local Government’s New Policy on Cybersecurity The paper argues the local government has the obligation to ensure that the information of the residents remains safe and confidential.
- National Cybersecurity Protection and the Role of CISA The federal government with the help of the Cybersecurity and ISA has put in place strategies and policies to protect the country from ICT-related national threats.
- Contemporary Global Marketing and Cyber Security The article discusses cyber security issues in the context of business and marketing. The security market had grown over the years within global marketing.
- Cyber Security Awareness Employee Training This paper aims to provide cyber security awareness employee training, discussing good cyber security habits, password guidance, phishing attacks and how to prevent them.
- Cybersecurity Workforce Crisis in State Governments Cybersecurity is one of the most vital fields in computing. This research has been conducted to highlight the cybersecurity challenges facing state governments.
- Speed as Important Factor in Cyber Security Enterprise organizations have a lot to handle in the era when cyberattacks have become not just a tangible threat but a lived reality.
- Cybersecurity Awareness and Training in Business Environment Cybersecurity refers to protecting systems linked to the Internet, including software, data, and hardware, from online threats.
- Drone Technology Cybersecurity and Information Systems The purpose of this document is to discuss drone technology, applications, cybersecurity, and information systems.
- Cybersecurity: The Current War of Today Cybersecurity laws in the United States have continued to be modified over time to meet new challenges, but there are difficulties in completely securing information.
- The Need of Cybersecurity in Healthcare Industry The purpose of this point paper is to explain the importance of implementing cybersecurity strategies for healthcare organizations.
- Cybersecurity Threats to the Non-Executive Director The essay will elaborate on the most major digital threats that non-executives face while being on their computers and provide practical strategies for preventing them.
- Raising Employee Cybersecurity Awareness Sufficient information that could empower employees to identify cyber vulnerabilities is readily available online, it can be disseminated freely or added to instructions.
- “How COVID-19 Is Dramatically Changing Cybersecurity” by Deo The article “How Covid-19 is dramatically changing cybersecurity” by TATA Consultancy Services delivers a detailed overview of the risks large companies face.
- Cyber Security Is Not a New Issue The issue of cybersecurity should be given significant attention to preserve the existing order and guarantee the effective functioning of central institutions.
- Cybersecurity – Threat Modeling to Predict Attacks Over the last decade, the field of cybersecurity has faced dramatic changes, and cyber-threats have become more severe.
- Cybersecurity Strategic Plan and the Best Practices in the Healthcare Sector Technology is changing at a rate that most institutions cannot keep pace with; hence, introducing a large that makes organizations susceptible to cyber breaches.
- Software Piracy at Kaspersky Cybersecurity Company Software piracy is an urgent contemporary problem that manifests itself both locally in relation to an individual organization and globally.
- Mayo Clinic’s Cybersecurity Risk Analysis The purpose of this paper is to analyze internal and external threats to Mayo Clinic’s Personal Healthcare Information (PHI).
- Cybersecurity Issues of Healthcare Organizations The paper aims at analyzing the article describing a potential implementation of unified cybersecurity standards for healthcare organizations.
- Cybersecurity of Healthcare Technologies In the world of fast-developing technologies, there are many opportunities and threats to health care. Cybersecurity threats need to be addressed as soon as they emerge.
- Medical Device Cybersecurity in Practice The breach of medical device security can lead to the loss of vital data, personal records of the patients, and the flawed operation of the devices.
- US Health and Human Services’ Cyber Security This report focuses on the security challenges of the U.S. Department of Health and Human Services and studies the activities carried out by HHS on information security.
- Mandiant Cyber Security Company’s Leadership Style Mandiant Cyber Security Company, renowned for forensic expertise and computer security programs, was founded in America by Kevin Mandia in early 2004.
- Unified Cybersecurity Standards in Healthcare Medical staff needs to improve their informatics skills to use the equipment efficiently. Attacks on servers and systems will increase.
- Changes Smartphones Are Making in Cybersecurity
- Cybersecurity for Digital Financial Service
- Multidisciplinary Approach Within the Cybersecurity Discourse
- Cybersecurity Challenges and Compliance Issues Within the U.S. Healthcare Sector
- Cybersecurity and Law Enforcement
- Takeaways From the Ocie Cybersecurity Initiative Risk
- Cybersecurity for American Government
- Cybersecurity and Risk Management
- The Cybersecurity and Cyber Warfare in India
- Government Cybersecurity Regulation Assignment
- Cybersecurity for Critical Infrastructure Protection
- Ethics, Legal, and Compliance Issues in Cybersecurity
- Cybersecurity and the Threat to National Security
- Attack-Prevention and Damage-Control Investments in Cybersecurity
- Cybersecurity in an Open and Decentralized Network
- Cybersecurity and Risk Behaviour on Mobile Individual Consumers in Spain
- Cybersecurity Policies and Solutions in Yemen
- Parallel and Distributed Computing for Cybersecurity
- Cybersecurity and Organizational Change Concept Map
- National Cybersecurity Policies and Regulations
- Cybersecurity and Cyberwarfare Critical Thinking
- Architecture for Managing Knowledge on Cybersecurity in Sub-Saharan Africa
- Modeling Multivariate Cybersecurity Risks
- Computer Networks and Cybersecurity
- Innovation Dynamics and Capability in Open Collaborative Cyber Communities: Implications for Cybersecurity
- Cybersecurity and Financial Stability: Risks and Resilience
- Current Practice Analysis for It Control and Security, Cybersecurity
- Cybersecurity Reaches New Heights in Georgia
- The Issues Surrounding Our Cybersecurity
- When Considering Cybersecurity, What Are the Roles and Responsibilities of an Organization?
- Government Cybersecurity Regulation
- Some Cybersecurity Strategies Indian Enterprises Should Look Into
- Cybersecurity and Financial Stability
- Cyber Risk: Why Cybersecurity Is Important?
- National Cybersecurity Profile Brazil
- Technology and the Impact on Cybersecurity
- Dealing With Cybersecurity Threats Posed by Globalized Information Technology Suppliers
- Fed Records Show Dozens of Cybersecurity Breaches
- Benefits of President Obama’s Cybersecurity Internet Policy
- Emerging Cybersecurity Technologies
- Most Important Cybersecurity Vulnerability Facing It Managers Computer Science
- Emerging Technologies That Impact the Cybersecurity Field
- Internet Surfers and Cybersecurity
- Improving Cybersecurity Using Nist Framework
- Global Cybersecurity Industry Analysis and Forecast to 2023
- Cybersecurity Research Meets Science and Technology Studies
- Cybersecurity and National Policy
- Cyber Crime: Cybersecurity for Cyberspace
- Small Business Cybersecurity and the Public Cloud
- New Concepts for Cybersecurity in Port Communication Networks
- Cybersecurity Gets Dumber Each Day
- Cybersecurity, Capital Allocations, and Management Control Systems
- Personal Statement About Cybersecurity
- Current Cybersecurity Policy Issues for the Protection
- Free Cybersecurity, Economic Progress, and Economic Security in Private Business
- Cybersecurity and the World Today
- Why Should Computer Scientists Care About Cybersecurity?
- Enacting Expertise: Ritual and Risk in Cybersecurity
- Muddling Through Cybersecurity: Insights From the U.S. Healthcare Industry
- Global Cybersecurity: New Directions in Theory and Methods
- What Are the Most Common Cybersecurity Problems in Enterprises?
- How Can Cybersecurity Policy Be Improved?
- Why Is Cybersecurity Important in Today’s World?
- Is Cybersecurity Part of Risk Management?
- What Is the Relationship Between Cybersecurity and Risk Management?
- How to Create an Effective Cybersecurity Policy?
- Why Is Cybersecurity Important for Small Businesses?
- Is Machine Learning Important in Cybersecurity?
- What Are the Major Cybersecurity Risks?
- Does Cybersecurity Affect Mental Health?
- Why Is Risk Management Important in Cybersecurity?
- How Does Cybersecurity Affect the World?
- Does Cybersecurity Require Coding?
- What Is Risk Assessment in Cybersecurity?
- Why Is Cybersecurity Important for National Security?
- How Hard Is It to Learn Cybersecurity?
- What Computer Language Is Used for Cybersecurity?
- Is Cybersecurity a Good Career in the Long Term?
- Which Country Topped Global Cybersecurity?
- Do Small Businesses Need Cybersecurity?
- What Are the Common Types of Cybersecurity Attacks?
- How Does Technology Affect Cybersecurity?
- What Are the Three Cybersecurity Strategies?
- Will Cybersecurity Ever Be Automated?
- How Is Data Science Used in Cyber Security?
- What Are the Current Computer and Cybersecurity Trends in the Near Future?
- How Is Machine Learning Used in Cybersecurity?
- What Will Cybersecurity Look Like 10 Years From Now?
- Is Cybersecurity or Data Analytics Better?
- Will Artificial Intelligence Replace Cybersecurity Jobs?
- The Latest Trends in Cyber Attacks.
- The Basics of Encryption and Its Role in Cybersecurity.
- The Impact of Data Breaches on Businesses and Individuals.
- Cybersecurity Best Practices for Remote Work.
- Ethical Hacking: The Importance of Penetration Testing.
- The Dark Web as the Hidden World of Cybercriminals.
- Social Engineering: How Hackers Exploit Human Psychology.
- Ways to Protect Patient Data in Healthcare Organizations.
- The Role of Blockchain Technology in Improving Cybersecurity.
- Cybersecurity Challenges Related to Artificial Intelligence.
- Should the Government Have Access to Encrypted Communications?
- Who Is Responsible for Cybersecurity: Government, Companies, or Individuals?
- Should Companies Be Liable for Data Breaches Resulting from Negligence?
- Is Biometric Authentication Secure Enough?
- Should the Regulations on the Collection and Use of Personal Data Be Stricter?
- Should Cybersecurity Training Be Mandatory for All Employees?
- Is the “Zero Trust” Strategy in Cybersecurity Justified?
- Should Governments Be Allowed to Engage in Cyber Espionage?
- Should Companies Be Required to Disclose All Data Breaches?
- Is There a Need for a Global Ban of Cyber Warfare?
Cite this post
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2022, March 1). 174 Cybersecurity Essay Topics & Research Questions to Write About. https://studycorgi.com/ideas/cybersecurity-essay-topics/
"174 Cybersecurity Essay Topics & Research Questions to Write About." StudyCorgi , 1 Mar. 2022, studycorgi.com/ideas/cybersecurity-essay-topics/.
StudyCorgi . (2022) '174 Cybersecurity Essay Topics & Research Questions to Write About'. 1 March.
1. StudyCorgi . "174 Cybersecurity Essay Topics & Research Questions to Write About." March 1, 2022. https://studycorgi.com/ideas/cybersecurity-essay-topics/.
Bibliography
StudyCorgi . "174 Cybersecurity Essay Topics & Research Questions to Write About." March 1, 2022. https://studycorgi.com/ideas/cybersecurity-essay-topics/.
StudyCorgi . 2022. "174 Cybersecurity Essay Topics & Research Questions to Write About." March 1, 2022. https://studycorgi.com/ideas/cybersecurity-essay-topics/.
These essay examples and topics on Cybersecurity were carefully selected by the StudyCorgi editorial team. They meet our highest standards in terms of grammar, punctuation, style, and fact accuracy. Please ensure you properly reference the materials if you’re using them to write your assignment.
This essay topic collection was updated on December 27, 2023 .
Cyber Crime Essay for Students and Children
500+ words essay on cyber crime.
Cyber Crime Essay – Everybody thinks that only stealing someone’s private data is Cyber Crime. But in defining terms we can say that ‘Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone’s data or trying to harm them using a computer.
Besides, it is an illegal activity that involves a series of issues ranging from theft to using your system or IP address as a tool for committing a crime.

Types of Cyber Crime
Speaking in a broadway we can say that Cyber Crime are categorized into four major types. These are Financial, Privacy, Hacking, and Cyber Terrorism.
The financial crime they steal the money of user or account holders. Likewise, they also stole data of companies which can lead to financial crimes. Also, transactions are heavily risked because of them. Every year hackers stole lakhs and crores of rupees of businessmen and government.
Privacy crime includes stealing your private data which you do not want to share with the world. Moreover, due to it, the people suffer a lot and some even commit suicide because of their data’s misuse.
In, hacking they intentional deface a website to cause damage or loss to the public or owner. Apart from that, they destroy or make changes in the existing websites to diminish its value.
Modern-day terrorism has grown way beyond what it was 10-20 years ago. But cyber terrorism is not just related to terrorists or terrorist organizations. But to threat some person or property to the level of creating fear is also Cyber Terrorism.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Crime in India
Web world or cyberspace is a massive community of millions and billions of users and websites. Also, people access it for different uses like shopping, movies, music, video games, transactions, and e-commerce, etc.

In this Age of Technology and easy access to the internet, anyone can easily reach it. Because of this fast pace growth from the previous decade. Besides, the internet has opened a world of information on which anyone can connect.
Due to, this the rate of crime especially the rate of Cyber Crime has increased much fold. Moreover, the rate of circulation of data is also increased much fold due to the higher speed of internet. Above all, due to all these issues, the Cybersecurity has become a major concern for society.
Laws related to Cyber Crimes
To stop the spread of Cyber Crime and to safeguard the interest of people the government has made several laws related to Cyber Crimes. Also, these laws serve as protection against Cyber Crime. Apart from that, the government has also introduced cyber cells in police stations to counter the problem of Cyber Crime as fast as they can.
Ways of stopping Cyber Crime
Cyber Crime is not something which we cannot deal with our self. Likewise, with little use of our common sense and logic, we can stop Cyber Crimes from happening.
To conclude, we can say that Cyber Crime is a dangerous offense to someone’s privacy or any material. Also, we can avoid Cyber Crime by following some basic logical things and using our common sense. Above all, Cyber Crime is a violation of not only law but of human rights too.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [{ “@type”: “Question”, “name”: “What is the main cause of Cyber Crime?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The greed for quick money and the desire to get famous quickly are the two main reasons of Cyber Crime. Also, most of the targets of Cyber Crime banks, businessman, financial firms, etc.” } }, { “@type”: “Question”, “name”: “What is the punishment of Cyber Crime in India?”, “acceptedAnswer”: { “@type”: “Answer”, “text”:”If the person is found guilty then there are several punishments based on the level of crime. A simple crime can cost you a fine while a bigger crime can lead you to jail.”} }] }
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


Cyber Safety Review Board finds Microsoft security culture ‘inadequate,’ calls for accountability
M icrosoft comes under intense scrutiny and pointed criticism in a 34-page report released Tuesday by the Cyber Safety Review Board (CSRB) , a group created by the U.S. Secretary of Homeland Security in 2021 to review major cybersecurity incidents.
The report focuses on a high-profile incident in May and June 2023, when the Chinese hacking group known as Storm-0558 is believed to have compromised the Microsoft Exchange Online mailboxes of more than 500 people and 22 organizations worldwide, including senior U.S. government officials.
The CSRB report takes Microsoft to task for its security culture, describing it as “inadequate” and saying it “requires an overhaul, particularly in light of the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations.”
The report also criticizes Microsoft’s public communications, noting that the company waited until last month to correct a September 2023 blog post about the root cause of the breach after repeated questions from the board.
At the conclusion of CSRB’s review, the report said, Microsoft still didn’t know exactly how Storm-0558 obtained the critical 2016 Microsoft Services Account (MSA) signing key that was used in the 2023 intrusion.
At one point, the report says Microsoft’s leaders need to consider refocusing its product development, prioritizing security features over new product features, effectively reviving the spirit of the “Trustworthy Computing” initiative that Microsoft co-founder Bill Gates famously instituted in 2002.
The CSRB report reads, in part:
“The Board concludes that Microsoft has drifted away from this ethos and needs to restore it immediately as a top corporate priority. The Board is aware of Microsoft’s recent changes to its security leadership and the ‘Secure Future Initiative’ that it announced in November 2023. The Board believes that these and other security-related efforts should be overseen directly and closely by Microsoft’s CEO and its Board of Directors, and that all senior leaders should be held accountable for implementing all necessary changes with utmost urgency.”
Asked for comment on the report, a Microsoft spokesperson gave this statement:
“We appreciate the work of the CSRB to investigate the impact of well-resourced nation state threat actors who operate continuously and without meaningful deterrence. As we announced in our Secure Future Initiative , recent events have demonstrated a need to adopt a new culture of engineering security in our own networks. While no organization is immune to cyberattack from well-resourced adversaries, we have mobilized our engineering teams to identify and mitigate legacy infrastructure, improve processes, and enforce security benchmarks. Our security engineers continue to harden all our systems against attack and implement even more robust sensors and logs to help us detect and repel the cyber-armies of our adversaries.”
The statement added that Microsoft “will also review the final report for additional recommendations.”
Read the full report here .

- Mobile Site
- Staff Directory
- Advertise with Ars
Filter by topic
- Biz & IT
- Gaming & Culture
Front page layout
NIGHTMARE SUPPLY CHAIN ATTACK SCENARIO —
What we know about the xz utils backdoor that almost infected the world, malicious updates made to a ubiquitous tool were a few weeks away from going mainstream..
Dan Goodin - Apr 1, 2024 6:55 am UTC

On Friday, a lone Microsoft developer rocked the world when he revealed a backdoor had been intentionally planted in xz Utils, an open source data compression utility available on almost all installations of Linux and other Unix-like operating systems. The person or people behind this project likely spent years on it. They were likely very close to seeing the backdoor update merged into Debian and Red Hat, the two biggest distributions of Linux, when an eagle-eyed software developer spotted something fishy.
Further Reading
Researchers have spent the weekend gathering clues. Here's what we know so far.
What is xz Utils?
xz Utils is nearly ubiquitous in Linux. It provides lossless data compression on virtually all Unix-like operating systems, including Linux. xz Utils provides critical functions for compressing and decompressing data during all kinds of operations. xz Utils also supports the legacy .lzma format, making this component even more crucial.
What happened?
Andres Freund, a developer and engineer working on Microsoft’s PostgreSQL offerings, was recently troubleshooting performance problems a Debian system was experiencing with SSH, the most widely used protocol for remotely logging in to devices over the Internet. Specifically, SSH logins were consuming too many CPU cycles and were generating errors with valgrind , a utility for monitoring computer memory.
Through sheer luck and Freund’s careful eye, he eventually discovered the problems were the result of updates that had been made to xz Utils. On Friday, Freund took to the Open Source Security List to disclose the updates were the result of someone intentionally planting a backdoor in the compression software.
It's hard to overstate the complexity of the social engineering and the inner workings of the backdoor. Thomas Roccia, a researcher at Microsoft, published a graphic on Mastodon that helps visualize the sprawling extent of the nearly successful endeavor to spread a backdoor with a reach that would have dwarfed the SolarWinds event from 2020.
What does the backdoor do?
Malicious code added to xz Utils versions 5.6.0 and 5.6.1 modified the way the software functions. The backdoor manipulated sshd, the executable file used to make remote SSH connections. Anyone in possession of a predetermined encryption key could stash any code of their choice in an SSH login certificate, upload it, and execute it on the backdoored device. No one has actually seen code uploaded, so it's not known what code the attacker planned to run. In theory, the code could allow for just about anything, including stealing encryption keys or installing malware.
Wait, how can a compression utility manipulate a process as security sensitive as SSH?
Any library can tamper with the inner workings of any executable it is linked against. Often, the developer of the executable will establish a link to a library that's needed for it to work properly. OpenSSH, the most popular sshd implementation, doesn’t link the liblzma library, but Debian and many other Linux distributions add a patch to link sshd to systemd , a program that loads a variety of services during the system bootup. Systemd, in turn, links to liblzma, and this allows xz Utils to exert control over sshd.
How did this backdoor come to be?
It would appear that this backdoor was years in the making. In 2021, someone with the username JiaT75 made their first known commit to an open source project. In retrospect, the change to the libarchive project is suspicious, because it replaced the safe_fprint funcion with a variant that has long been recognized as less secure. No one noticed at the time.
The following year, JiaT75 submitted a patch over the xz Utils mailing list, and, almost immediately, a never-before-seen participant named Jigar Kumar joined the discussion and argued that Lasse Collin, the longtime maintainer of xz Utils, hadn’t been updating the software often or fast enough. Kumar, with the support of Dennis Ens and several other people who had never had a presence on the list, pressured Collin to bring on an additional developer to maintain the project.
In January 2023, JiaT75 made their first commit to xz Utils. In the months following, JiaT75, who used the name Jia Tan, became increasingly involved in xz Utils affairs. For instance, Tan replaced Collins' contact information with their own on oss-fuzz, a project that scans open source software for vulnerabilities that can be exploited. Tan also requested that oss-fuzz disable the ifunc function during testing, a change that prevented it from detecting the malicious changes Tan would soon make to xz Utils.
In February of this year, Tan issued commits for versions 5.6.0 and 5.6.1 of xz Utils. The updates implemented the backdoor. In the following weeks, Tan or others appealed to developers of Ubuntu, Red Hat, and Debian to merge the updates into their OSes. Eventually, one of the two updates made its way into the following releases, according to security firm Tenable:
There’s more about Tan and the timeline here .
reader comments
Promoted comments.
It should be noted that the attack only works because Debian and Redhat added functionality to sshd that is not present in it as distributed by its developers. The extra functionality adds systemd interaction, which requires libsystemd which requires liblzma, a component of the (compromised) xz package. One should be wary of distributions adding functionality. Often it increases the attack surface, not only because of the modifications/additions themselves, but also by adding dependencies.
So a prime reason this became potentially exploitable is libsystemd in OpenSSH. Need I say more.
The prime reason is a very well funded and capable attacker looked for a way in. if not xz or systemd then they would have attacked via the next candidate weak point.
"This developer persona has touched dozens of other pieces of open-source software in the past few years.". Well, I guess the Opensource community have some codes to review. Maybe the xz incident is only the tips of the iceberg.
Channel Ars Technica
- Election 2024
- Entertainment
- Newsletters
- Photography
- Personal Finance
- AP Buyline Personal Finance
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Election Results
- Delegate Tracker
- AP & Elections
- March Madness
- AP Top 25 Poll
- Movie reviews
- Book reviews
- Personal finance
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
AT&T says a data breach leaked millions of customers’ information online. Were you affected?
FILE - The sign in front of an AT&T retail store is seen in Miami, July 18, 2019. The theft of sensitive information belonging to millions of AT&T’s current and former customers has been recently discovered online, the telecommunications giant said Saturday, March 30, 2024. In an announcement addressing the data breach, AT&T said that a dataset found on the dark web contains information including some Social Security numbers and passcodes for about 7.6 million current account holders and 65.4 million former account holders. (AP Photo/Lynne Sladky, File)
- Copy Link copied
NEW YORK (AP) — The theft of sensitive information belonging to millions of AT&T’s current and former customers has been recently discovered online, the telecommunications giant said this weekend.
In a Saturday announcement addressing the data breach, AT&T said that a dataset found on the “dark web” contains information including some Social Security numbers and passcodes for about 7.6 million current account holders and 65.4 million former account holders.
Whether the data “originated from AT&T or one of its vendors” is still unknown, the Dallas-based company noted — adding that it had launched an investigation into the incident. AT&T has also begun notifying customers whose personal information was compromised.
Here’s what you need to know.
WHAT INFORMATION WAS COMPROMISED IN THIS BREACH?
Although varying by each customer and account, AT&T says that information involved in this breach included Social Security numbers and passcodes — which, unlike passwords, are numerical PINS that are typically four digits long.
Full names, email addresses, mailing address, phone numbers, dates of birth and AT&T account numbers may have also been compromised. The impacted data is from 2019 or earlier and does not appear to include financial information or call history, the company said.
HOW DO I KNOW IF I WAS AFFECTED?
Consumers impacted by this breach should be receiving an email or letter directly from AT&T about the incident. The email notices began going out on Saturday, an AT&T spokesperson confirmed to The Associated Press.
WHAT ACTION HAS AT&T TAKEN?
Beyond these notifications, AT&T said that it had already reset the passcodes of current users. The company added that it would pay for credit monitoring services where applicable.
AT&T also said that it “launched a robust investigation” with internal and external cybersecurity experts to investigate the situation further.
HAS AT&T SEEN DATA BREACHES LIKE THIS BEFORE?
AT&T has seen several data breaches that range in size and impact over the years .
While the company says the data in this latest breach surfaced on a hacking forum nearly two weeks ago, it closely resembles a similar breach that surfaced in 2021 but which AT&T never acknowledged, cybersecurity researcher Troy Hunt told the AP Saturday.
“If they assess this and they made the wrong call on it, and we’ve had a course of years pass without them being able to notify impacted customers,” then it’s likely the company will soon face class action lawsuits, said Hunt, founder of an Australia-based website that warns people when their personal information has been exposed.
A spokesperson for AT&T declined to comment further when asked about these similarities Sunday.
HOW CAN I PROTECT MYSELF GOING FORWARD?
Avoiding data breaches entirely can be tricky in our ever-digitized world, but consumers can take some steps to help protect themselves going forward.
The basics include creating hard-to-guess passwords and using multifactor authentication when possible. If you receive a notice about a breach, it’s good idea to change your password and monitor account activity for any suspicious transactions. You’ll also want to visit a company’s official website for reliable contact information — as scammers sometimes try to take advantage of news like data breaches to gain your trust through look-alike phishing emails or phone calls.
In addition, the Federal Trade Commission notes that nationwide credit bureaus — such as Equifax, Experian and TransUnion — offer free credit freezes and fraud alerts that consumers can set up to help protect themselves from identity theft and other malicious activity.
AP Reporter Matt O’Brien contributed to this report from Providence, Rhode Island.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Press Releases
Cyber Safety Review Board Releases Report on Microsoft Online Exchange Incident from Summer 2023
WASHINGTON – Today, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board’s (CSRB) findings and recommendations following its independent review of the Summer 2023 Microsoft Exchange Online intrusion . The review detailed operational and strategic decisions that led to the intrusion and recommended specific practices for industry and government to implement to ensure an intrusion of this magnitude does not happen again. Secretary of Homeland Security Alejandro N. Mayorkas received the CSRB report from the Board and delivered it to President Biden. This is the third review completed by the CSRB since the Board was announced in February 2022. “Individuals and organizations across the country rely on cloud services every day, and the security of this technology has never been more important,” said Secretary Mayorkas. “Nation-state actors continue to grow more sophisticated in their ability to compromise cloud service systems. Public-private partnerships like the CSRB are critical in our efforts to mitigate the serious cyber threat these nation-state actors pose. The Department of Homeland Security appreciates the Board’s comprehensive review and report of the Storm-0558 incident. Implementation of the Board’s recommendations will enhance our cybersecurity for years to come.” The CSRB provides a unique forum for leading government and industry experts to review significant cybersecurity events and provide independent, strategic, and actionable recommendations to the President, the Secretary, and the Director of the Cybersecurity and Infrastructure Security Agency (CISA) to better protect our nation. The Board is made up of cybersecurity leaders from the private sector and senior officials from DHS, CISA, the Defense Department, the National Security Agency, the Department of Justice, the Federal Bureau of Investigation, the Office of the National Cyber Director, and the Federal Chief Information Officer. In August 2023, DHS announced that the CSRB would assess the recent Microsoft Exchange Online intrusion, initially reported in July 2023, and conduct a broader review of issues relating to cloud-based identity and authentication infrastructure affecting applicable cloud service providers (CSP) and their customers. The CSRB obtained data from and conducted interviews with 20 organizations and experts including cybersecurity companies, technology companies, law enforcement organizations, security researchers, academics, as well as several impacted organizations. The inclusive review process developed actionable findings and recommendations. As a result of the CSRB’s recommendations, CISA plans to convene major CSPs to develop cloud security practices aligned with the CSRB recommendations and a process for CSPs to regularly attest and demonstrate alignment. “DHS is committed to efforts that meaningfully improve cybersecurity resilience and preparedness for our nation, and the work of the CSRB is reflective of our determination and dedication to this cause,” said CISA Director Jen Easterly . “I am confident that the findings and recommendations from the Board’s report will catalyze action to reduce risk to the critical infrastructure Americans rely on every day.” The CSRB’s review found that the intrusion by Storm-0558, a hacking group assessed to be affiliated with the People’s Republic of China, was preventable. It identified a series of Microsoft operational and strategic decisions that collectively pointed to a corporate culture that deprioritized enterprise security investments and rigorous risk management, at odds with the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations. The Board recommends that Microsoft develop and publicly share a plan with specific timelines to make fundamental, security-focused reforms across the company and its suite of products. Microsoft fully cooperated with the Board’s review. “Cloud computing is some of the most critical infrastructure we have, as it hosts sensitive data and powers business operations across our economy,” said DHS Under Secretary of Policy and CSRB Chair Robert Silvers. “It is imperative that cloud service providers prioritize security and build it in by design. The Board has become the authoritative organization for conducting fact-finding and issuing recommendations in the wake of major cyber incidents, receiving extensive industry and expert input in each of its three reviews to date. We appreciate Microsoft’s full cooperation in the course of the Board’s seven-month, independent review. We also appreciate the input received from 19 additional companies, government agencies, and individual experts.” “The threat actor responsible for this brazen intrusion has been tracked by industry for over two decades and has been linked to 2009 Operation Aurora and 2011 RSA SecureID compromises,” said CSRB Acting Deputy Chair Dmitri Alperovitch . “This People’s Republic of China affiliated group of hackers has the capability and intent to compromise identity systems to access sensitive data, including emails of individuals of interest to the Chinese government. Cloud service providers must urgently implement these recommendations to protect their customers against this and other persistent and pernicious threats from nation-state actors.” The CSRB recommends specific actions to all cloud service providers and government partners to improve security and build resilience against the types of attacks conducted by Storm-0558 and associated groups. Select recommendations include:
- Cloud Service Provider Cybersecurity Practices: Cloud service providers should implement modern control mechanisms and baseline practices, informed by a rigorous threat model, across their digital identity and credential systems to substantially reduce the risk of system-level compromise.
- Audit Logging Norms: Cloud service providers should adopt a minimum standard for default audit logging in cloud services to enable the detection, prevention, and investigation of intrusions as a baseline and routine service offering without additional charge.
- Digital Identity Standards and Guidance: Cloud service providers should implement emerging digital identity standards to secure cloud services against prevailing threat vectors. Relevant standards bodies should refine, update, and incorporate these standards to address digital identity risks commonly exploited in the modern threat landscape.
- Cloud Service Provider Transparency: Cloud service providers should adopt incident and vulnerability disclosure practices to maximize transparency across and between their customers, stakeholders, and the United States government.
- Victim Notification Processes: Cloud service providers should develop more effective victim notification and support mechanisms to drive information-sharing efforts and amplify pertinent information for investigating, remediating, and recovering from cybersecurity incidents.
- Security Standards and Compliance Frameworks: The United States government should update the Federal Risk Authorization Management Program and supporting frameworks and establish a process for conducting discretionary special reviews of the program’s authorized Cloud Service Offerings following especially high-impact situations. The National Institute of Standards and Technology should also incorporate feedback about observed threats and incidents related to cloud provider security.
As directed by President Biden through Executive Order 14028 Improving the Nation’s Cybersecurity, Secretary Mayorkas established the CSRB in February 2022. The Board’s investigations are conducted independently, and its conclusions are independently reached. DHS and the CSRB are committed to transparency and will, whenever possible, release public versions of CSRB reports, consistent with applicable law and the need to protect sensitive information from disclosure. To read the full report, visit Report on Microsoft Online Exchange Incident from Summer 2023 .
- Cybersecurity
- Secretary of Homeland Security
- Cyber Incident
- Cybersecurity and Infrastructure Security Agency (CISA)
- Secretary Alejandro Mayorkas
Cyber-Security Threats and Their Control Essay
Cyber-security menaces are the risks of encountering a cyber-attack, a hostile attempt by an institution or a person to interfere with a person or institution’s system. Advanced Persistent Threats (APT) is the most harmful class of cyber-security threats that propagates when hackers extract essential data from a prohibited network without being discovered for a prolonged period. It attacks when cybercriminals install malware on the organization’s system to help them protect their tracks. The act’s success needs experienced hackers and a spy to gather information from the plotted corporation. By employing threat intelligence techniques in a firm, the security team can identify and manage the objection.
Distributed Denial of Service (DDoS) is the second threat that increases when the perpetrators attempt to jeopardize online systems by overwhelming them with data. The attack occurs when multiple devices are functioning jointly to strike one target. Skilled individuals and the power of botnets consisting of settled computers can aid in a successful offense. By establishing high levels of network security such as, Artificial Intelligence (AI) or antivirus and anti-malware software can be used to prevent suspicious behavior.
Man-in-the-Middle is the third cybercrime committed by assailants through the customers’ servers to retrieve data without their knowledge. The crime propagates when the perpetrators intercept an existing conversation between a user and a system and operate as the legitimate participants. The MitM can be successful when the cybercriminals reach their final stage successfully to satisfy their desires. Avoiding public and insecure internet connections, which ushers the spreading of documents of the altered code to customers’ can assist in exterminating the threat.
Social engineering is the fourth cyber-security threat that relies on verified connection between the assailants and targets, which proposes an influence to submit their sensitive information. The crisis continues to propagate because the victims remain to accept the attackers’ quick decisions. The offense becomes victorious when the attackers deceive the corporation employees’ to deliver the credentials. Firms should use safety strategies such as, raising security awareness to its workers and staff to minimize the increasing invasions.
Password attack is the least destructive cyber-security risk that breeds when people reuse their exposed passwords repeatedly. It attacks when the hacker resembles numerous passwords to discover the valid one. It requires advanced hackers to retrieve the information of an individual or an organization’s password database. The creation of robust passwords is an appropriate way to prevent the concern.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2023, March 17). Cyber-Security Threats and Their Control. https://ivypanda.com/essays/cyber-security-threats-and-their-control/
"Cyber-Security Threats and Their Control." IvyPanda , 17 Mar. 2023, ivypanda.com/essays/cyber-security-threats-and-their-control/.
IvyPanda . (2023) 'Cyber-Security Threats and Their Control'. 17 March.
IvyPanda . 2023. "Cyber-Security Threats and Their Control." March 17, 2023. https://ivypanda.com/essays/cyber-security-threats-and-their-control/.
1. IvyPanda . "Cyber-Security Threats and Their Control." March 17, 2023. https://ivypanda.com/essays/cyber-security-threats-and-their-control/.
Bibliography
IvyPanda . "Cyber-Security Threats and Their Control." March 17, 2023. https://ivypanda.com/essays/cyber-security-threats-and-their-control/.
- Exterminating Bugs in Franz Kafka’s "The Metamorphosis"
- Organizational Vulnerability
- VPN Security Vulnerabilities
- Computer Sciences Technology and HTTPS Hacking Protection
- Various Types of Cybercrime
- Management: Information Technology - Information Assurance
- Data Protection: Securing Information System
- Wireless Networks Investigation Challenges
- Cyber Crimes: Court - United States vs. Ancheta
- Foot-in-the-door and Door-in-the-face Technique
- Simple Local Area Networks (LAN): Data Protection
- ReliaQuest: Information Technology Security
- Cybersecurity and Geopolitics Relationship
- Cybersecurity and Corporations' Input to It
- Cybersecurity and Corporations' Role
share this!
March 25, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
Introducing safety and security civilization: A new paradigm for global safety science
by Maximum Academic Press
Safety science literature and terminology reveal a limited array of concepts to describe the comprehensive characteristics of system safety and security, including terms such as safety culture and risk. Despite these efforts, the rapid evolution of safety science outpaces the adequacy of these concepts, signaling a pressing need for new, meaningful general concepts.
To that end, Emergency Management Science and Technology has published research titled "Why should safety and security civilization (SSC) be a new concept of safety and security science?" The paper aims to define SSC rigorously, demonstrating its importance and potential to become a cornerstone concept in safety science, similar to safety culture yet distinct in its broader applicability and deeper integration of safety and civilization aspects.
In exploring the origins and development of safety culture, the author proposes the introduction of "Safety and Security Civilization" (SSC) as a pivotal new concept that could encapsulate the entire spectrum of safety and security at any given time or place. Initial searches indicate that while discussions on safety civilization exist, they lack the comprehensive and unified approach proposed for SSC.
The paper introduces and describes the concept of Safety and Security Civilization (SSC). Narrow and broad definitions of SSC and its connotations are given separately. "Safety and Security Civilization" is a multidimensional and inclusive term designed to encapsulate all safety and security issues within the framework of civilization. SSC is presented as a comprehensive concept that intertwines with various aspects of human life, including political stability , social fairness, economic development , technological innovation , and environmental protection.
The concept stretches to encompass both traditional and non-traditional security issues, advocating for a balanced approach that nurtures social harmony, technological advancement , and international cooperation for a safer global society. SSC is an advanced part of a broader security culture that can be used as a guide to building a safety culture.
SSC could pave the way for innovative theoretical frameworks, enhance interdisciplinary collaboration, and stimulate the development of forward-thinking safety and security solutions by offering a new lens through which to view safety and security issues .
In conclusion, this paper not only contributes to the theoretical expansion of safety science but also provides practical pathways for improving safety standards and promoting a culture of security that aligns with the evolving demands of modern civilization.
Provided by Maximum Academic Press
Explore further
Feedback to editors

Study reports that age is the driving force in changing how stars move within galaxies
3 hours ago

Newly hatched chicks can instantly recognize objects with vision, even if they've only ever experienced them by touch
5 hours ago

A return to roots: Lab builds its first stellarator in 50 years and opens the door for research into new plasma physics
6 hours ago

A new estimate of US soil organic carbon to improve Earth system models

New research uses coaxial 'dish' antenna to scan for dark matter
7 hours ago

'Unheard of in structural biology': New enzyme models reveal disease insights
Transmitting entanglement between light and matter in the metropolitan network of Barcelona

These plants evolved in Florida millions of years ago. They may be gone in decades.

Focusing ultra-intense lasers to a single wavelength
8 hours ago
Classical optical neural network exhibits 'quantum speedup'
Relevant physicsforums posts, what are your favorite disco "classics".
11 hours ago
How did ‘concern’ semantically shift to mean ‘commercial enterprise' ?
14 hours ago
Wars of the Roses (Lancaster, Red Rose - York, White Rose), 1455-1487
16 hours ago
Interesting anecdotes in the history of physics?
17 hours ago
Cover songs versus the original track, which ones are better?
Apr 1, 2024
Metal, Rock, Instrumental Rock and Fusion
More from Art, Music, History, and Linguistics
Related Stories

Study highlights emergence of new safety and security science disciplines
Jul 3, 2023

Improving miner problems with safety research
Mar 13, 2024

Identifying research priorities for security and safety threats in the Arctic and the North-Atlantic
Sep 15, 2022

Violence and abuse among fan culture growing concern for soccer, new research finds
Jan 16, 2024

1 in 5 US teachers feel carrying gun to class would make schools safer. More than half disagree, finds survey
May 31, 2023
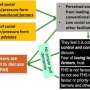
Farmers urged to be inquisitive about farm health and safety
Jul 5, 2023
Recommended for you

Characterizing social networks by the company they keep
12 hours ago

Song lyrics have become simpler and more repetitive since 1980, study finds
Mar 28, 2024

Low resting heart rate in women is associated with criminal offending, unintentional injuries
Mar 27, 2024
Your emotional reaction to climate change may impact the policies you support, study finds

Survey study shows workers with more flexibility and job security have better mental health
Mar 26, 2024

We have revealed a unique time capsule of Australia's first coastal people from 50,000 years ago
Mar 25, 2024
Let us know if there is a problem with our content
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Phys.org in any form.
Newsletter sign up
Get weekly and/or daily updates delivered to your inbox. You can unsubscribe at any time and we'll never share your details to third parties.
More information Privacy policy
Donate and enjoy an ad-free experience
We keep our content available to everyone. Consider supporting Science X's mission by getting a premium account.
E-mail newsletter
AT&T says leaked data set impacts about 73 million current, former account holders

The Reuters Daily Briefing newsletter provides all the news you need to start your day. Sign up here.
Reporting by Gursimran Kaur in Bengaluru; Editing by Leslie Adler
Our Standards: The Thomson Reuters Trust Principles. , opens new tab

Singtel rules out selling Australian unit Optus
Singapore Telecommunications (Singtel) , Southeast Asia's largest telecom operator, reiterated on Wednesday that there was no "impending deal" to divest its Australian telecom unit Optus.

U.S. private equity firm Clayton Dubilier & Rice (CD&R) said on Tuesday it had agreed to acquire a majority ownership position in information technology provider Presidio from UK-based BC Partners.

IMAGES
VIDEO
COMMENTS
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data.
200 Words Essay On Cyber Security. School students are the future of our society, and it's important to teach them the importance of cyber security from an early age. Cyber security is an ever-increasing problem in our digital world, and it's up to us to ensure that our students are aware of the risks and dangers that come with the internet.
our national security depends on a strong cyber culture. To stay ahead of the threat, cybersecurity needs to be steeped into the national consciousness through education, sustained messaging and increased cooperation among businesses and government. My research examines the vulnerabilities, and cites case studies, national policy ...
250 Words Essay on Cyber Security Introduction to Cyber Security. Cybersecurity, a term that has gained paramount importance in the digital age, refers to the practice of protecting internet-connected systems, including hardware, software, and data, from digital attacks. Its significance is amplified by the increasing reliance on technology ...
Cyber security may also be referred to as information technology security." (Lord, 2019). Which is an important part of networking and business security that is required to ensure our security in all aspects of our daily lives. Cybersecurity is important due to the amount of sensitive information that is stored on many different computer ...
Published: Jan 16, 2024. Inside This Article. 127 Cyber Security Essay Topic Ideas & Examples. With the increasing reliance on technology, cyber security has become a critical concern for individuals, organizations, and governments worldwide. As cyber threats continue to evolve and become more sophisticated, it is essential to stay informed ...
Cybersecurity Necessity and Benefits. Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender's cognitive state, possibilities for automation, and an attacker's subjective traits. Cybersecurity Incident Response and Risk Minimization.
Long Essay on Cyber Security is usually given to classes 7, 8, 9, and 10. The main definition of cyber security is protecting networks, data, programs, and other information from unattended or unauthorized access, change, or destruction. Around the globe nowadays, cyber security is very vital because of some cyber-attacks and cyber-attacks.
15 Cyber Security Essay Topics. In the following section, you will find unique ideas for your essay on cyber security. Choose the most appropriate one and create your outstanding paper. Don't forget to compose a catchy introduction, a clear thesis statement, and a dynamic conclusion. You can get more ideas by using our topic generator. Or ...
Learn why cyber security is crucial in today's digital age and how it protects our sensitive information from hackers and cyber attacks. Explore the importance of implementing effective cyber security measures and the potential risks and consequences of neglecting them. Discover the role of cyber security in safeguarding personal privacy, business operations, and national security.
Brief History of Cyber Security. 2 pages / 836 words. Cyber security or information technology security are the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation. There are four types of security controls access, flow, inference, and cryptographic complement each ...
Cyber Safety is implemented in various organizations to protect data. This protection is known as information security. Primarily, information security is deployed in areas where digital data is stored and is highly vulnerable to attacks. This includes information systems, apps, and websites. Following the understanding of what Cyber Safety is ...
Essay on Cyber Security: The data, networks and other important confidential information present online needs to be protected from prospective hackers and hacker groups to prevent them from leakage. Cyber security acts and rules are enacted and enforced in situations where there is a cyber-crime on the spot. Accessing data in an unauthorized way, destruction of information, using data without ...
Short Essay on Cyber Security & its Importance today. Cybersecurity is an effort to keep electronic gadgets such as laptops, smartphones, and tablets away from hackers and data thieves. ... Cyber Security is essential to ensure the safety and privacy of our data. When Cyber Security is not implemented, anyone can steal, misuse, and abuse our ...
In addition, five scenarios can be considered for cyber warfare: (1) Government-sponsored cyber espionage to gather information to plan future cyber-attacks, (2) a cyber-attack aimed at laying the groundwork for any unrest and popular uprising, (3) Cyber-attack aimed at disabling equipment and facilitating physical aggression, (4) Cyber-attack as a complement to physical aggression, and (5 ...
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common ...
Abstract. Advanced cyber attacks that target both public and private sectors at the international level have provoked an increase in research and funding for the establishment of novel cyber security technologies. We will write a custom essay on your topic. 809 writers online.
Confidentiality is one of the major concepts that contribute to the security of users online as well as their personal data used in online activities. Cybersecurity in the Energy Sector. Cybersecurity is protecting cyberspace, the infrastructure that stores and transfers information, from malicious cyberattacks.
Cyber Security Essay. [online]. ... The approach of the organizations towards their security mechanism does not help the organization to ensure the safety and also the methodology incorporated by the organization for securing the data and system is questionable as the efficiency of the system less and the cost of operations are at the higher ...
Cite This Essay. Download. The internet is a no man's land. The whole world has melted into a global village as the internet permeates offices, homes, and mobiles. Cyber security is the practice of protecting networks technological systems, and programs from data breaching, digital attacks, data infringement, and unauthorized access.
500+ Words Essay on Cyber Crime. Cyber Crime Essay- Everybody thinks that only stealing someone's private data is Cyber Crime.But in defining terms we can say that 'Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone's data or trying to harm them using a computer.
Cyber stores or E-commerce transactions face greater e-transaction security risks due to insufficient internet safety from cybercriminals, Not only is hacking a huge risk for all online merchants, but accepting a fraudulent payment also comes at the cost of having to refund the charges. ... Cyber Security Threat Analysis Essay. (2023, October ...
Microsoft comes under intense scrutiny and pointed criticism in a 34-page report released Tuesday by the Cyber Safety Review Board (CSRB), a group created by the U.S. Secretary of Homeland ...
What does the backdoor do? Malicious code added to xz Utils versions 5.6.0 and 5.6.1 modified the way the software functions. The backdoor manipulated sshd, the executable file used to make remote ...
NEW YORK (AP) — The theft of sensitive information belonging to millions of AT&T's current and former customers has been recently discovered online, the telecommunications giant said this weekend.. In a Saturday announcement addressing the data breach, AT&T said that a dataset found on the "dark web" contains information including some Social Security numbers and passcodes for about 7. ...
WASHINGTON - Today, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board's (CSRB) findings and recommendations following its independent review of the Summer 2023 Microsoft Exchange Online intrusion.The review detailed operational and strategic decisions that led to the intrusion and recommended specific practices for industry and government to implement to ...
Social engineering is the fourth cyber-security threat that relies on verified connection between the assailants and targets, which proposes an influence to submit their sensitive information. The crisis continues to propagate because the victims remain to accept the attackers' quick decisions. The offense becomes victorious when the ...
A healthcare-industry hack shows the need for autonomous databases and operating systems.
The connotation of safety and security civilization (SSC). Credit: Emergency Management Science and Technology (2023). DOI: 10.48130/EMST-2023-0014
Telecom company AT&T said on Saturday that it is investigating a data set released on the "dark web" about two weeks ago, and said that its preliminary analysis shows it has impacted approximately ...