- Partners Login

- Network Design

What Are RADIUS Servers, and How Does RADIUS Authentication Work?
RADIUS (Remote Authentication Dial-In User Service) is a client-server protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
Internet Service Providers (ISPs) and enterprises widely employ RADIUS for overseeing access to the internet or internal networks, encompassing wireless networks and integrated email services. It accomplishes this by utilizing a RADIUS server, which holds (or is able to access) user credential information and the rules that determine which users can access which networks or services.
Nile Access Service enables authentication and authorization of users and devices across wired and Wi-Fi connectivity by implementing several measures. It uses 802.1X RADIUS and Single Sign-On (SSO) authentication with device profiling for network access to protect assets. It orchestrates dynamic rules that move with users and devices, eliminating the use of virtual LANs (VLAN) and static Access Control Lists (ACLs) for policy enforcement mechanisms.
Additionally, Nile Access Service ensures isolation across all authorized users and IoT devices for added protection. For guest users, their traffic is tunneled to Nile’s point-of-presence (PoP) to protect the network. These measures collectively ensure a secure and efficient authentication and authorization process across both wired and Wi-Fi connectivity.
What are components of a RADIUS server?
RADIUS operates in a client-server model and mainly consists of three key components:
- RADIUS Server : This is the system that hosts the RADIUS software. It receives user connection requests, authenticates the user, and then, based on the configured policies, returns all configuration information necessary for the client to deliver service to the user. The server is also responsible for logging accounting information.
- RADIUS Client : Normally, the RADIUS client is a network access server (NAS). Some examples could be a VPN concentrator, a wireless access point, or a switch. The client is responsible for passing user information to designated RADIUS servers and then acting on the response that is returned.
- RADIUS Proxy : Positioned between the RADIUS client and the RADIUS server, the RADIUS proxy serves as an intermediary. Proxy servers are useful for routing authentication requests to the remote RADIUS server groups for authentication and accounting.
Additional components include:
- User or Supplicant: This is the device or user trying to gain access to resources on the network. The user provides unique credentials to verify their identity during the authentication process.
- Shared Secret: A password or security key used between the RADIUS server and RADIUS clients (or proxies) to secure transmitted information.
- AAA Protocol: This provides Authentication (validates user’s identity), Authorization (defines what a user can do or access) and Accounting (tracks what the user does), forming a core part of the RADIUS protocol.
- RADIUS Attributes: These are specific pieces of information in a RADIUS message, such as username, password, IP address, and connection port. They allow for flexibility and control in dictating user access rules.
- RADIUS Dictionaries: They are collections of vendor-specific attributes (VSAs) that allow RADIUS to carry information specific to vendor products.
How does RADIUS server authentication work?
RADIUS authentication is a method employed to confirm a user’s identity when they endeavor to establish a connection with a network. Here’s how it works:
1. User connection attempt
A user attempts to connect to a network or network resource, such as a VPN or Wi-Fi access point. This device is known as a Network Access Server (NAS), or a RADIUS client.
2. Initiate Access-Request
The NAS, or RADIUS client, sends an “Access-Request” message to the RADIUS server. This request contains identification parameters like the user’s credentials (username and password), the IP address of the RADIUS client, and a port number.
3. RADIUS server verification
The RADIUS server receives this request and checks the user’s provided credentials against a database of authorized users.
4. Send Access-Accept message
If the credentials provided in the access request match a record in the database, the RADIUS server creates an “Access-Accept” message. This typically includes configuration information that the NAS requires to deliver service to the user, such as IP addresses, VLAN assignments, or Quality of Service (QoS) parameters.
5. Dispatch Access-Reject message
If the provided credentials do not align with any records in the database, the RADIUS server sends out an “Access-Reject” message, denying the user access to the network or resource.
6. Request further authentication
The RADIUS server can also dispatch an “Access-Challenge” message, asking for additional identification data, often as part of multi-factor authentication.
7. Begin accounting process
Once the user is authenticated and access is granted, the RADIUS server may initiate an accounting process. This could involve recording the user’s network connection duration to track data usage for billing purposes.
How does accounting for RADIUS authentication work?
Accounting in a RADIUS server functions as a way of tracking resource usage for auditing, billing, and statistical purposes. It establishes a record of what resources users are accessing when they are accessing them, and from where, and generates that information into a log.
Here’s a general look at how it works:
1. User service initiation
When a user starts a service, such as a network session, the Network Access Server (NAS), acting as a RADIUS client, dispatches an Accounting Start (or Accounting-On) packet to the RADIUS server. This contains details like user identity, the requested service, the NAS IP address, and a distinct session identifier, among others.
2. Acknowledgment of session start
The RADIUS server confirms the receipt of the start packet by sending back an Accounting Response. The session is now officially initiated, and its specifics are recorded on the server.
3. Periodic session updates
For the duration of the session, especially longer ones, the NAS might dispatch periodic updates through Accounting Interim (or Accounting-Alive) packets. These inform the RADIUS server that the session is still active and offer updated session statistics. The RADIUS server acknowledges these updates similarly to the initial packet.
4. Session termination
If the user concludes the session or if it’s ended due to other reasons (e.g., timeouts), the NAS sends the RADIUS server an Accounting Stop (or Accounting-Off) packet. This signifies the session’s end and provides the concluding session stats, like its total duration and the data sent and received.
5. Acknowledgment of session end
In response, the RADIUS server sends an Accounting-Response, and the concluding details of the session are recorded on the server.
Using these logs, network administrators can keep track of individual resource usage, identify trends, make better-informed decisions regarding resource allocation, and even bill users based on the resources they consumed during the session. The server could also raise security alerts based on anomalies in the logs – for example, if a user’s consumption is unexpectedly high or if a user is logging in from a new or strange location.
How are RADIUS servers used?
RADIUS servers are used in several ways for authentication, authorization, and accounting processes in network systems. Here are some key uses:
Network access authentication
RADIUS servers are crucial in authenticating network access, whether for a corporate network or an ISP. They validate the provided credentials for system access. For instance, when an employee tries to connect to a company’s intranet, the RADIUS server ensures the entered credentials match the company’s records.
RADIUS servers are frequently utilized to authenticate users aiming to access services or a network via a Virtual Private Network (VPN). By merging a RADIUS server with the VPN, the same authentication and usage policies can be applied to VPN users as local network users. For example, a remote worker connecting to the company’s internal resources via VPN would be authenticated through the RADIUS server before gaining access.
Wireless networks
RADIUS servers are a staple in wireless networks to verify wireless users. This is especially true for enterprise Wi-Fi networks where logging in with a username and password is mandatory. Students trying to connect to the campus Wi-Fi would be authenticated on a college campus through a RADIUS server, ensuring only registered students and staff have access.
Accounting services
RADIUS servers can monitor the use of network services for distinct users. This information is valuable for billing, keeping track of resource utilization, and strategizing capacity planning. For example, a managed service provider might use a RADIUS server to determine how much bandwidth a particular customer has consumed in a billing cycle.
Authorization services
Beyond authentication, RADIUS servers offer authorization services. Once a user is authenticated, the server verifies the services the user can use and allocates the appropriate rights. In a company setting, after an employee logs in, the RADIUS server might determine that they only have access to certain parts of the network based on their role.
Centralizing authentication management
RADIUS servers are harnessed to centralize authentication management. This particularly benefits expansive networks with many Access Points (APs) or Network Access Servers (NAS). On a large college campus network, having a centralized RADIUS server helps manage the myriad of access points across classrooms, libraries, and dormitories, ensuring consistent access rules.
Internet service providers (ISPs)
ISPs frequently employ RADIUS servers to oversee connections for DSL, wireless, and other types of network access. For instance, when a user tries to connect to their home broadband, the ISP’s RADIUS server verifies their credentials before allowing the connection.
How does RADIUS work with Wi-Fi?
RADIUS can be used to enhance the security of a Wi-Fi network by providing centralized Authentication, Authorization, and Accounting (AAA) management.
Here’s how it works:
1. User credential input
When users try to connect to the Wi-Fi network, they are prompted to input their unique credentials, usually a username and password.
2. Forwarding of credentials to the RADIUS server
The Wi-Fi access point, acting as the RADIUS client, securely transfers these credentials to the RADIUS server. This transmission is typically encrypted to avert unauthorized interception.
3. RADIUS server credential verification
The RADIUS server cross-references these credentials with its database. This database could operate independently, or be a segment of a larger user directory like LDAP or Active Directory.
4. Authorization rule check
Upon confirming a match for the user’s credentials in the database, the RADIUS server scrutinizes the authorization guidelines applicable to that user. These rules can set limitations based on various factors such as time of day, access point location, and device type.
5. Dispatching access confirmation
If the user fulfills the authentication requirements and abides by the authorization rules, the RADIUS server sends an affirmation message to the Wi-Fi access point. This communication can also include specific settings tailored for the user, such as an allocated IP address or a session time limit.
6. Granting user access
Following the directives from the RADIUS server, the Wi-Fi access point then permits the user to access the network.
7. Logging user session details
Throughout and post the user’s session, pertinent data, like the session’s duration or the volume of data exchanged, might be documented by the RADIUS server. This data can be vital for administrative purposes, including billing.
This process enables robust, centralized control over network access and ensures a high level of security for your Wi-Fi network. It’s often used in enterprise or large-scale environments where many users need to connect to the network across multiple access points.
Important to note, Nile Access Service enables zero trust isolation for authorized users and IoT devices by extending zero trust networking to campus and branch environments. This model isolates every user and device by default while enforcing zero trust policies to prevent threats from spreading. This approach significantly reduces the attack surface across the LAN, and completely eliminates the proliferation of malware that might have infected an end user mobile device or an IoT device.
What is the difference between LDAP and RADIUS?
LDAP and RADIUS are both protocols used for network security, particularly for user authentication and access control. However, they serve different functions and are typically used in different contexts.
LDAP (Lightweight Directory Access Protocol)
LDAP is a protocol used to access and maintain distributed directory information services over a network. Directory services are software applications that store, organize, and provide access to information in a computer network’s directory. It’s used to query and update items like usernames, passwords, phone numbers, and other user or object attributes in a structured and hierarchical way. LDAP servers store “directory entries” in a tree-like structure called Directory Information Tree (DIT). Some common usage scenarios for LDAP include email programs pulling up contact data from the server, organizations maintaining employee information on an LDAP server, etc.
RADIUS (Remote Authentication Dial-In User Service)
RADIUS is a network protocol used for remote user authentication, authorization, and accounting. It’s typically used in scenarios involving network access control, like VPN user authentication or wireless network access control. RADIUS servers receive user connection requests, authenticate the user, and then return configuration information necessary for the client device to deliver service to the user. RADIUS is generally used in combination with a network access server (NAS) and can serve as a backend to an LDAP directory by consulting the directory to evaluate RADIUS authentication requests. In most cases, enterprises use RADIUS to authenticate, authorize, and account for user access to networks and networked services like VPN or Wi-Fi connections In summary, LDAP is mainly used to manage user information and simplify access to this information, while RADIUS is used to control network access.
LDAP is often used as a backend database for RADIUS. They can also work together – for example, a RADIUS server could use an LDAP server to check the username and password for a given user.
Can RADIUS be cloud-based?
Cloud-based RADIUS servers provide the necessary network infrastructure mechanisms for remote access to a network, including access points, firewalls, and VPN concentrators. Instead of housing this infrastructure on-site, organizations can host their RADIUS servers in the cloud, allowing for increased scalability, streamlined user management, and decreased on-site hardware costs.
Cloud-hosted RADIUS servers manage and authenticate user data transfers and network protocols. Opting for cloud RADIUS services helps businesses cut hardware costs, enhances scalability, and boosts security.
While cloud RADIUS solutions are pivotal for modernizing network infrastructure and offer various advantages, organizations should consider a provider with robust security measures and a commitment to cybersecurity to ensure their RADIUS implementation is safe.
Are RADIUS servers safe?
When properly configured, RADIUS servers are deemed secure due to their strong user authentication, data encryption, and capacity to interface with multiple devices on a network.
Key security features include:
- Authentication Methods : Utilizing methods such as PAP, CHAP, or EAP.
- Data Encryption : Encrypting user credentials and sensitive data during transmission.
- Centralized AAA : Managing and tracking user activities, preventing unauthorized access.
- Device Validation : Authenticating devices accessing the network.
However, RADIUS security hinges on:
- Correct server configuration.
- Encrypted communication between the server and client.
- Use of modern, secure protocols.
- Ongoing security management and maintenance.
Should you use a RADIUS server?
Whether or not you should use a RADIUS server largely depends on the needs of your business and your network setup. Here are some points that might help you make a decision:
Enhanced security
RADIUS servers offer excellent security features, including encryption and centralized AAA (Authentication, Authorization, Accounting) protocols. A RADIUS server can be an excellent choice if your priority is securing your network.
Centralized control
With a RADIUS server, administrators can manage access to services from a central location, rather than having to configure each networking device individually. This can make managing a large number of devices far easier.
Reporting and auditing
RADIUS servers provide detailed logging of user activities – when they logged in, from where, the resources they accessed, and so on. This can assist with compliance reporting and troubleshooting.
Scalability
If your business requires a network that can handle an increasing number of users or devices, a RADIUS server is designed to manage large amounts of traffic and can be scaled up to accommodate future growth.
Multiple access points
If your setup has multiple access points or networks, a RADIUS server simplifies the authentication process by allowing users to log in with the same credentials across all networks.
Costs and complexity
It’s important to note that setting up and maintaining a RADIUS server can involve extra costs and require skilled IT personnel due to its complex nature.
If you require high network security, centralized control and robust user activity logging, RADIUS functionality would be an essential component for your overall network architecture. But if your needs are simpler, the time and cost of setting up and maintaining a RADIUS server might not be justified.
RADIUS Authentication with Campus Zero Trust
Unlock a seamless integration of secure wireless and wired access, and say goodbye to the complexities of manual configurations and other RADIUS woes with Nile Access Service. It uses 802.1X RADIUS and Single Sign-On (SSO) authentication with device profiling for network access. This helps protect network assets and ensures only authorized users and devices can access the network. Nile Access Service extends zero trust networking principles to wired and wireless access network security in several ways, without the pain of manual workflows.
By integrating several components, Nile automates traditionally manual workflows for network security, reducing business risk and accelerating time to service at scale:
- Automation: A Nile network orchestrates policy intent across the Wi-Fi and wired stack, eliminating potential configuration errors. Automation is also used to provide visibility across the stack for incident response, enabling faster and more efficient responses to security incidents.
- Zero Trust Network Access: Nile implements a zero trust network access model, which isolates every user and device by default and prevents threats from spreading.
- Dynamic Segmentation: Nile orchestrates dynamic rules that move with users and devices, eliminating the need for static Access Control Lists (ACLs).
With Nile, you can rest assured knowing your network performance outcomes like availability and capacity are guaranteed. This includes usage-based billing for scalable, flexible consumption. The service dramatically simplifies network management by offloading key lifecycle management tasks , helping you to focus on what you do best.
Trust nothing, authenticate everything, with NaaS by Nile for a more secure and streamlined network experience.

Stay up-to-date with the latest news and trends from Nile!
Sign Up Today
Sign up for our newsletter to stay up-to-date on all things Nile.

Ready to eliminate your network headaches?
You can experience the nile difference in no time. let’s talk..
- Server News
- Virtualization


What is a RADIUS Server and How Does It Work?

ServerWatch content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
The RADIUS (Remote Authentication Dial-In Service) protocol is a client-server networking protocol that facilitates communication between a central server and individual users who want to gain access to the server.
Essentially, RADIUS allows remote access servers to communicate with the central server to authenticate and authorize remote user access. With RADIUS, companies can store user profiles in a central database that can be shared across all remote servers.
How does RADIUS work?
Radius authentication methods, how is radius used, radius benefits, radius challenges.
RADIUS works based on a client/server model. Users connect to a RADIUS client, which is a network access server (NAS) . The NAS then verifies the user’s information through the RADIUS authentication server. The connection information can include details such as a username, a password, and an IP address.
In complex or geographically spread out networks, a RADIUS proxy client can be used to forward authentication requests to other RADIUS servers.
There are a few types of remote user access authentication servers:
- Virtual private network servers: These accept requests from users and facilitate secure connections to private networks.
- Wireless access points: Wireless access points accept requests from wireless clients and facilitate access to a network
- Managed network access switches: These implement the 802.1x authenticate access protocol
After authentication, the RADIUS server also verifies the level of access a user has. This ensures that only authorized persons have access to a company’s data. In addition to authentication, RADIUS can also report the volume of resources used during a session, which can be useful for billing purposes. Resource utilization is valuable for managed service providers (MSPs) .
After a user provides their login credentials, the RADIUS server uses one of the following authentication methods:
- Password Authentication Protocol (PAP) : This relies on a RADIUS client forwarding a user ID and password to the RADIUS authentication server. If the credentials prove to be correct, the client allows the remote user’s connection.
- Challenge Handshake Authentication Protocol (CHAP) : This protocol relies on the sharing of an encrypted secret between the client and server. It is considered more secure than the PAP.
- MS-CHAP: This is Microsoft’s version of CHAP. It is used with VPNs.
- Extensible Authentication Protocol (EAP) : This is typically used with wireless networks and point-to-point connections.
RADIUS is often used in situations where a remote worker needs to access a company’s network and data centers. It ensures that only authenticated, authorized users are granted access with minimal disruptions to the employee’s productivity.
Additionally, RADIUS is an important part of the zero trust security framework in which all users are assumed to be a threat. RADIUS is fundamental to the authentication and authorization elements that consistently verify a user’s identity and permissions.
Read more: 4 Mistakes to Avoid When Deploying a RADIUS Server
RADIUS provides a central platform for user and system authentication, which makes managing user access a much easier task. The centralized nature of RADIUS also makes it easy for multiple IT administrators to manage the same network.
Plus, the fact that each user has unique credentials in a RADIUS environment eliminates the need for routine password updates. This minimizes the vulnerabilities associated with traditional password security.
Perhaps most importantly, RADIUS prevents attackers from successfully intercepting a valid user’s network connection. Network administrators can verify that every connected user is who they say they are and has the right access privileges to do their job.
RADIUS is typically implemented on-premise, which can make it difficult and time-consuming to set up and maintain. However, there are cloud-based options that can make implementation and maintenance easier.
Additionally, there are many different configuration options that can make it difficult to set up a new RADIUS server and integrate it into an existing environment. These roadblocks can inhibit efficiency and productivity.
The volume of RADIUS solutions on the market can be overwhelming, too. Selecting the right RADIUS server can be a tedious endeavor that involves evaluating the organization’s needs and comparing potential solutions to find the one that will work best.
Our list of the Best Low-Cost RADIUS Servers can provide a valuable starting point in the buying process.
Featured Partners: Remote Monitoring and Management Software
Zoho assist.

Visit website
Strengthen your remote monitoring and management strategy with Zoho Assist's user-friendly interface and proactive solutions. With its robust features, Zoho Assist empowers administrators to monitor devices in real time, control them remotely, install updates, ensure security and compliance, and gain insights through comprehensive reporting.
Learn more about Zoho Assist
SuperOps.com RMM

SuperOps.ai RMM With SuperOps.ai’s RMM (Remote Monitoring and Management) you can manage your client’s network of assets with ease and proactively tackle issues. Monitor assets in real time, dive deep for granular information about an asset and find all the context you need to resolve issues effectively. If you’d like to try the RMM out for yourself, you can sign up for a 21-day free trial to take it for a spin and see the solution in action. No strings attached.
Learn more about SuperOps.com RMM

Site24x7 provides a comprehensive solution for remote monitoring and management of diverse client environments, including endpoints, websites, networks, servers, applications, and cloud. Create customized dashboards, NOC views, and business views highlighting all the critical metrics. With features like white-labeling, multi-tenancy, customizable roles and permissions, and detailed reports and service level agreements, Site24x7 helps you manage your customer accounts with ease.
Learn more about Site24x7

BDRSuite's MSP Backup Solution is designed for Cloud and managed Service Providers. Exclusive Pricing to maximize profit margins. No minimum monthly commitments, pay-as-you-go pricing, and bigger discounts for upfront payment. Centralized management through multi-tenancy support and license management portal. Co-branding available. 24/7 technical support. Dedicated account manager. Offer On-Premise, Remote & Hybrid Backup for VMs, Servers, Endpoints, SaaS and cloud.
Learn more about BDRSuite
Get the Free Newsletter!
Subscribe to Daily Tech Insider for top news, trends & analysis
Latest Posts
What is a container understanding containerization, what is e-waste what you need to know, what is a print server | how it works and what it does, 6 best linux virtualization software for 2024, 5 top benefits of virtualization, related stories, top 6 server management software and tools in 2023, what is edge caching definition, how it works, and use cases, what is microsegmentation.

Mastering Network Security: A Step-by-Step Guide to RADIUS Server
Radius stands for remote access dial-in user service. Radius server is a protocol that is primarily used for restricting network access. It authenticates the user who wants to access the device or network. Further, it also authorizes users, what they can do. And at the last, it also responsible for what the user did during his/her login time? It tracks the user when accessing the device or network how much time he spends, and when he logs out.
It was developed in 1991 by Levingston Enterprises. IETF standardized it in 2000 under RFC 2865. It is an open standard. So, we can use it on every vendor’s device. It uses UDP port numbers 1812 and 1813. The radius server combines both the authentication and authorization traffic. It only encrypts the password. Also, the radius server combines the authentication and authorization processes.
Lab topology for Radius server
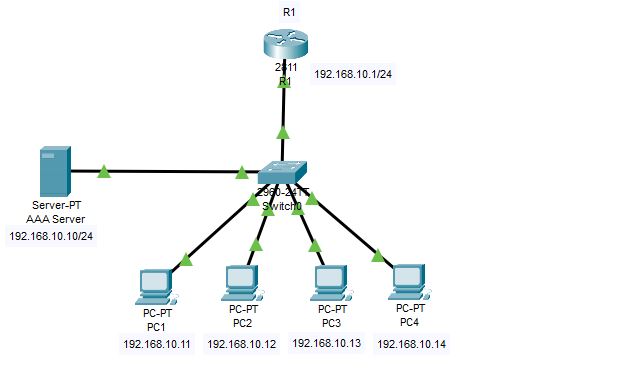
Configure the IP address of a router
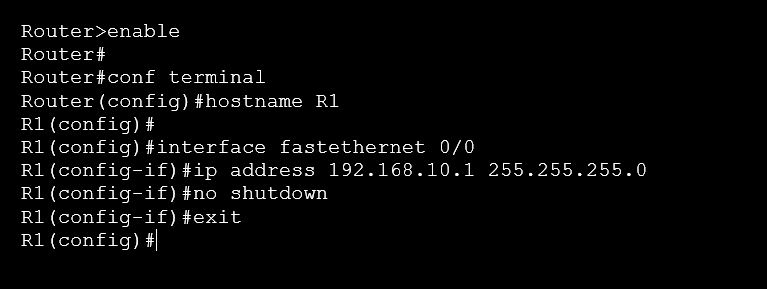
Configure Telnet on the Router
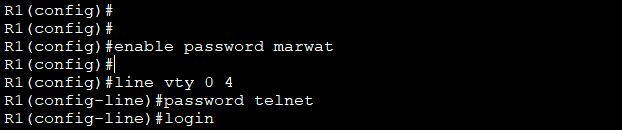
Enable the AAA radius authentication on the router
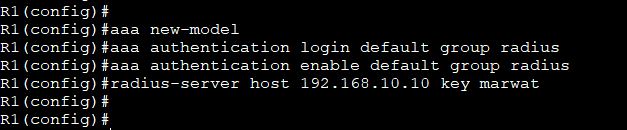
Configure the AAA Radius Server in packet tracer
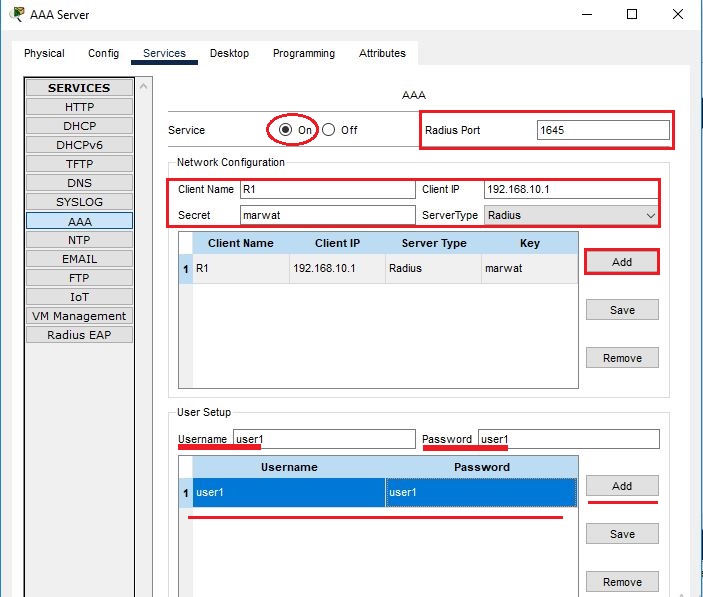
Ping and telnet the router from one of the PCs to check the connectivity
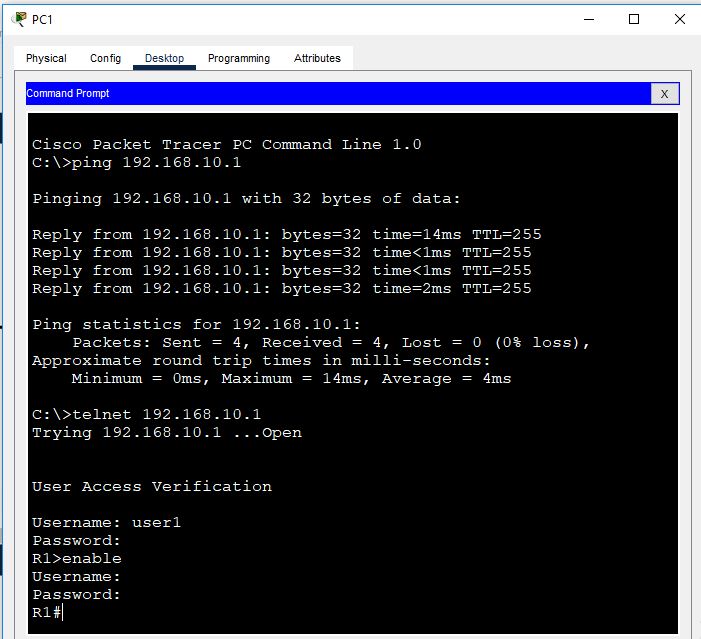
PC1 successfully ping and telnet the router.
Now we are going to disconnect the AAA radius server from the network and will check whether PC1 can telnet the router or not.
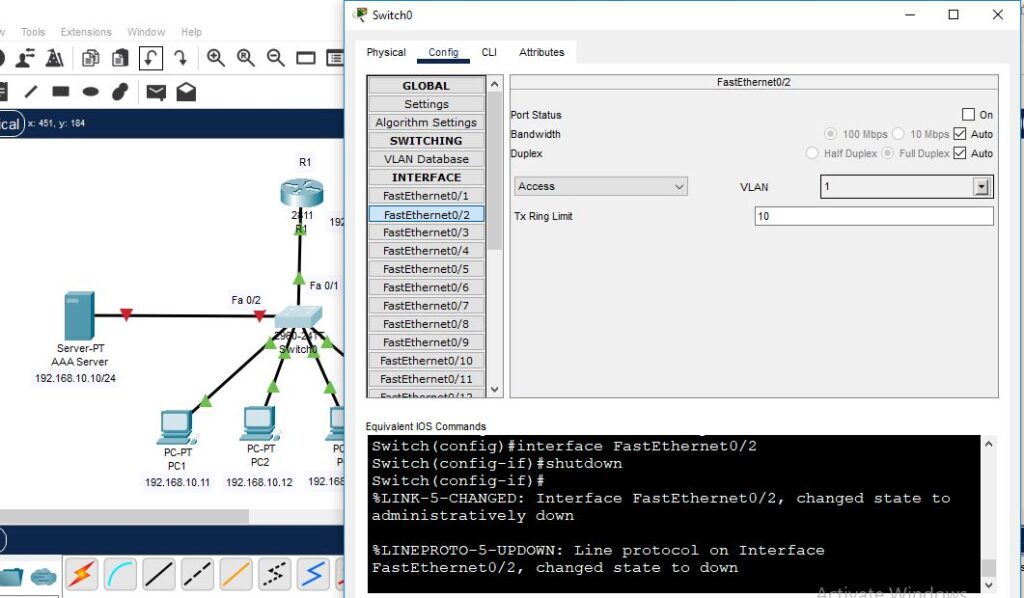
Now, telnet the router from PC1.
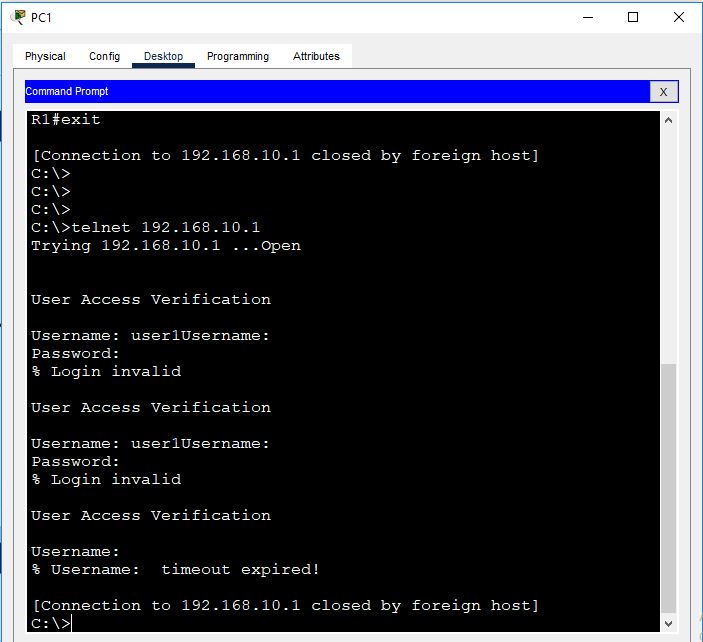
PC1 is not able to telnet into the router, because the router doesn’t authenticate its username and password from the AAA server. Router R1 is not also able to get its console session as below in the screenshot:
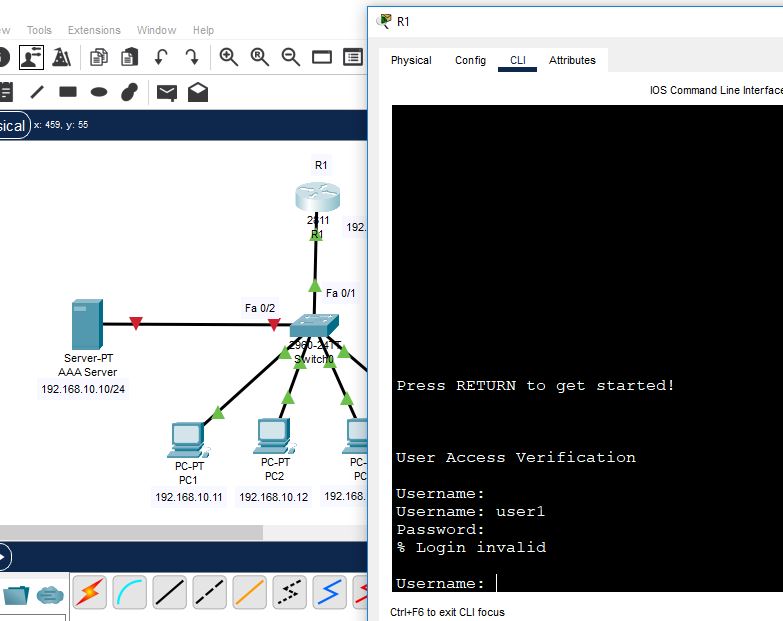
Again, enable the AAA radius server.
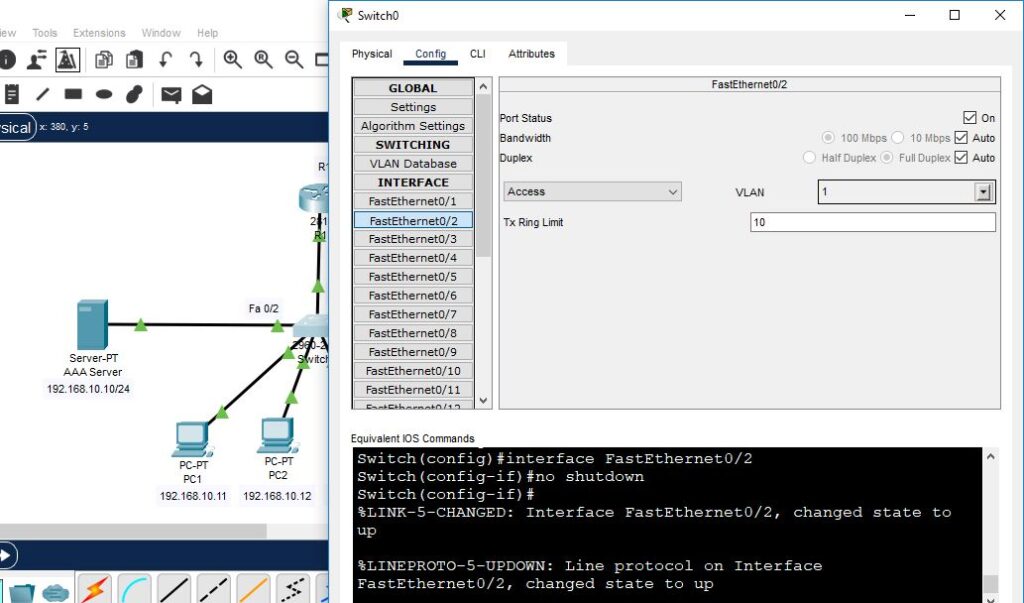
Check again, whether R1 is accessible or not from PC1, because it is now connected with the AAA radius server.
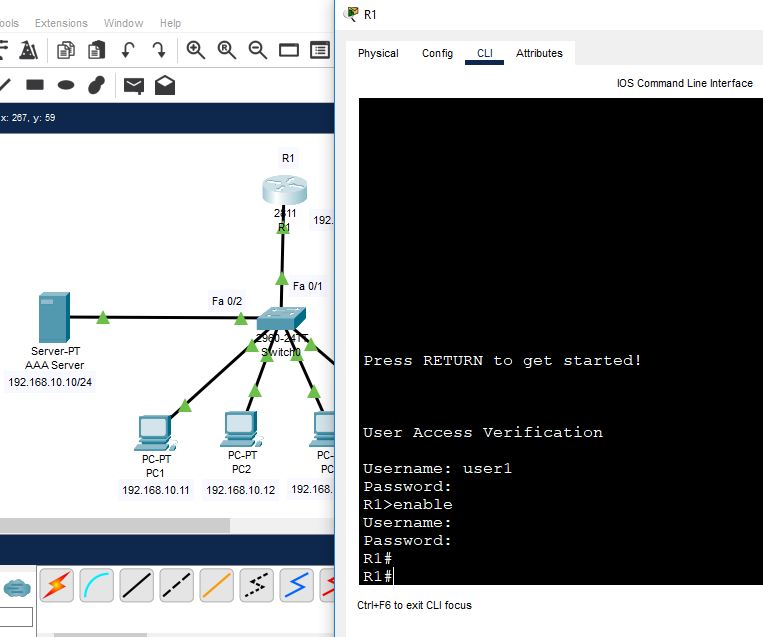
We are going to configure such a AAA radius authentication that when the AAA server is not accessible, then we can access to the router. So, remove the existing AAA authentication and rewrite it again with local authentication. Anyhow, when the AAA server shuts down, or when it is not accessible, then the router will be accessible.
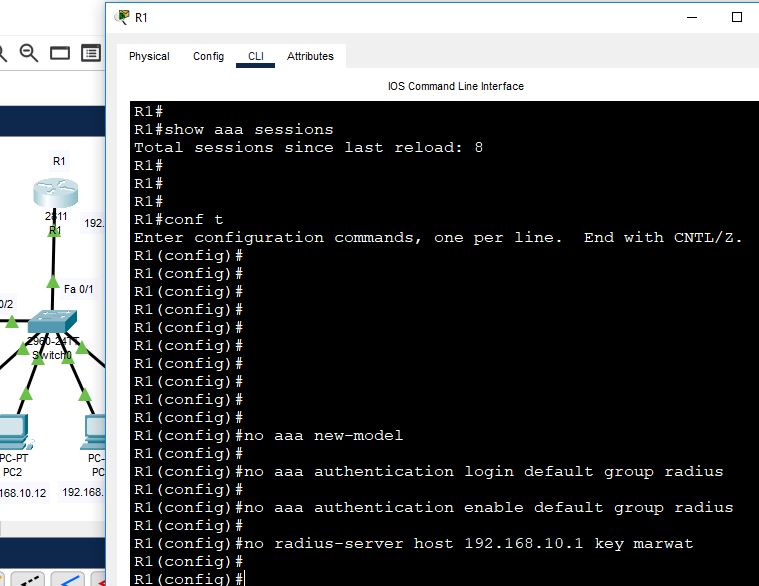
Create one more user user2
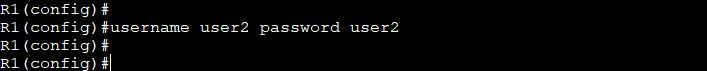
Again, telnet Router R1 from PC1 through user1. User2 will not access the router, because we didn’t create user2 in the AAA server, but created it in the local router database.
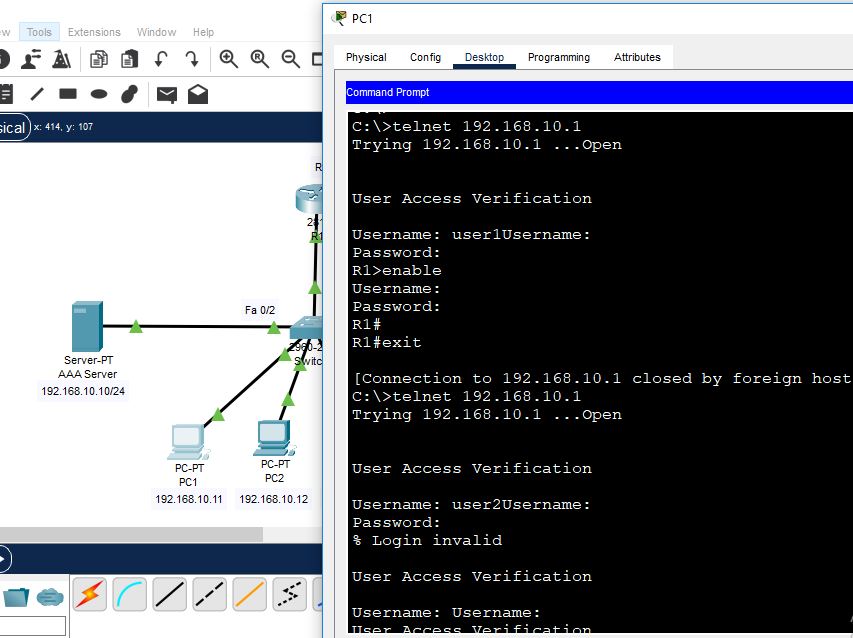
Shutdown AAA server interface. So, we will try to telnet the router from both user1 and user2. We will check who can log into it and why.
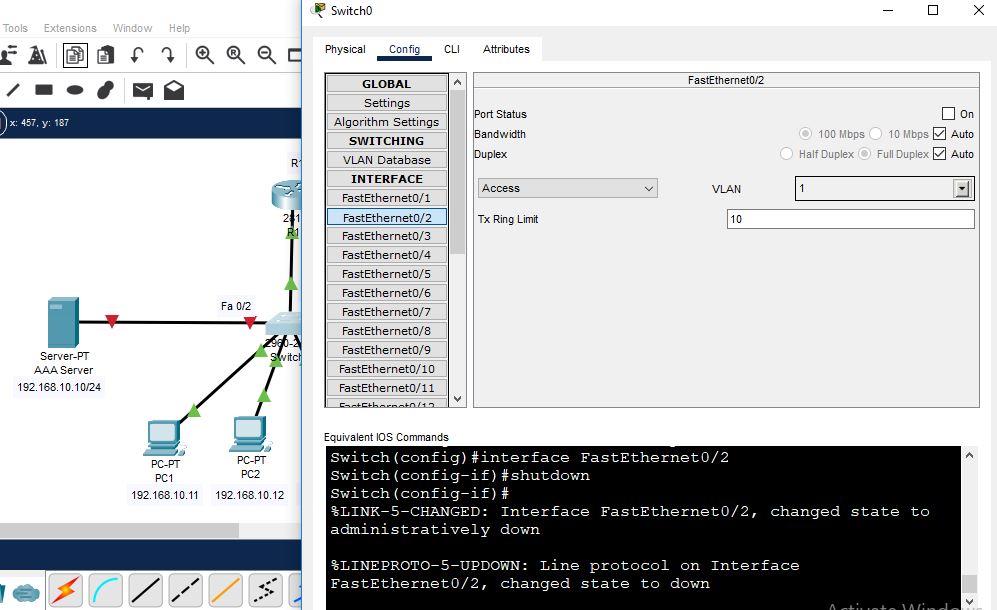
Try to access the router through user2 telnet. R2 will access the router now because user2 is in the local database of a router. The router first looks up it in the AAA server, but the AAA server is down. So, it then looks up in its local database.
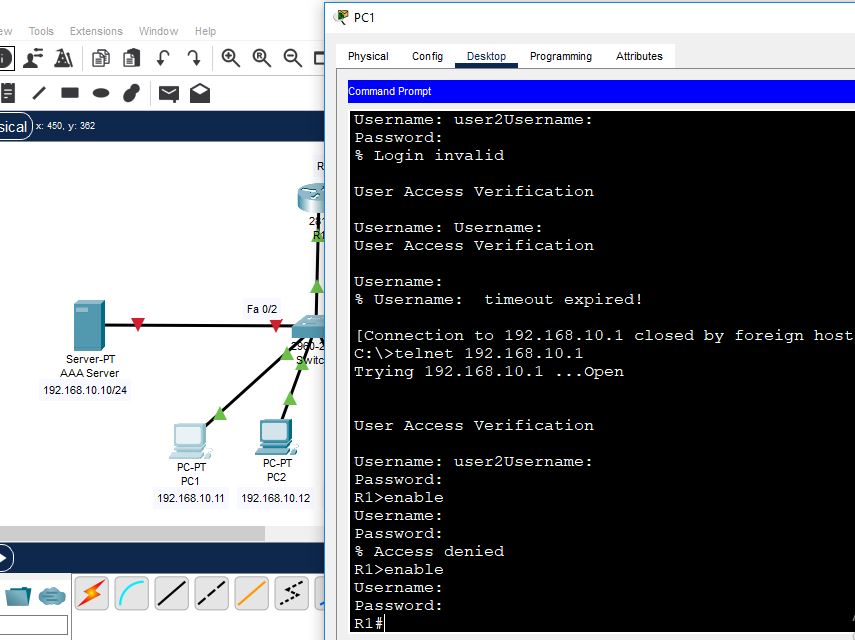
Again, enable the interface of a AAA radius server
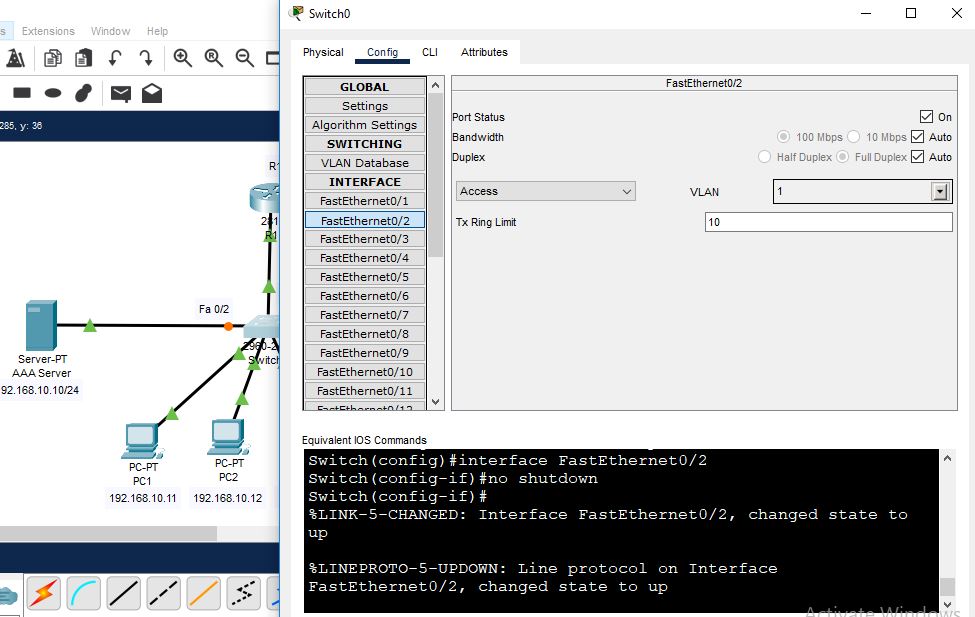
This time, both the AAA server remote authentication and local authentication are enabled on the router. So which user, whether user1 or user2, will logged into the router? Let’s check below in the screenshot:
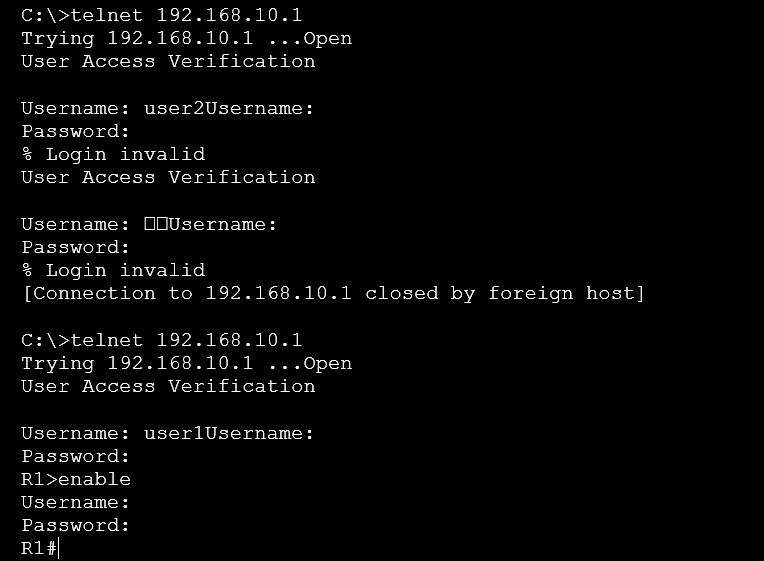
As AAA is up, so router will find user2 in the AAA server. When the router doesn’t find it in the AAA server, then it will not allow user2 to log in to the router.
Hey, I'm Imran Ullah Khan, an IT enthusiast from Lakki Marwat, Pakistan. I hold a BSCS degree and wear a tech-belt with certifications like CCNA, CCNP, MCSE, RHCSA, RHCE, FIREWALL, and VMWARE.
With 8 years of tech exploration, I'm currently an I.T instructor and the force behind CCNA Practical Labs. My blog is your gateway to practical CCNA insights. Let's simplify networking! WhatsApp at 0092313-9492026. Let's connect and tech-chat!
Similar Posts

How to Configure Different Cisco Router Passwords Step-by-Step
A password is a primary protection mechanism to secure a device. Cisco uses different types of passwords to restrict access to its devices, such as routers, switches, firewalls, etc. We have explained configuring different Cisco router passwords to restrict a user from accessing the router privilege exec mode. In the router privilege exec mode, a…

Routing Information Protocol (RIP): Latest Essentials and Grateful Guide
Introduction Routing Information Protocol or RIP is one of the oldest routing protocols. Bellman-Ford developed it in 1980. It passed through certain revisions which are version 1, version 2 for IPv4, and RIPng for IPv6. Moreover, it is a distance routing protocol that uses hop count as a metric. It is used in small as…
How to Automate Network Access With Python Netmiko Library part-1
We use the Python Netmiko Library to automate network access securely. Netmiko is a Python library that is used to build a secure remote connection with network devices using an SSH connection. Nemiko is not the default library in Python. you will have to install it manually in it. It is necessary to enable SSH…
How to Create Multiple VLANs with Python Script
Vlan stands for virtual local area network. Creating a VLAN is an important part of the configuration of a switch. n this article, we will write a script and run this script to create Multiple VLANs with Python script on a switch. We will perform this lab in EVE-NG software. Creating Management Cloud in the…
Step-by-Step Guide: How to Restore a Cisco Router Password
Maintaining network devices is an important job role of a network administrator. He is performing day-to-day network device configuration. Among other devices, there are also routers in his/her responsibilities. Sometimes, he lost the router Password. He is trying to find a solution to log into the router but he fails. The last option is to…
How to connect two PCs in a Cisco Packet tracer?
Packet Tracer A packet tracer is easy to install and easy to make a computer network by dragging and dropping network devices and end devices. I am going to start with a very basic lab in packet tracer. The first lab starts with how to connect two PCs in a packet tracer. For this reason,…
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
How a RADIUS server works
A RADIUS server utilizes a central database to authenticate remote users. RADIUS functions as a client-server protocol, authenticating each user with a unique encryption key when access is granted. How a RADIUS server works depends upon the exact nature of the RADIUS ecosystem. Below is an overview of how RADIUS servers work.
First, the user initiates authentication to the network access server (NAS).
The network access server then requests either a username and password or a challenge (CHAP).
The user replies.
Upon receiving the user’s reply, the RADIUS client sends the username and the uniquely encrypted password to the RADIUS server.
The RADIUS server accepts or rejects the user.
RADIUS servers are well known for their AAA capabilities — Authentication, Authorization, and Accounting. The main advantage of the centralized AAA capabilities of a RADIUS server are heightened security and better efficiency. RADIUS servers provide each business with the ability to preserve the privacy and security of both the system and each individual user.

Published 2017-11-15 12:00:00 +0000 Categories: articles
Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users that connect and use a network service. RADIUS is the transport for AAA services. The services can include the user profiles including storing user credentials, user access policies, and user activity statistics which can reside on the same server. Gateway devices that control network access, such as remote access servers, VPN servers, and network switches, can use the RADIUS protocol to communicate with a RADIUS server for:
Authentication — verifying user credentials regarding granted access to their networks.
Authorization — verifying user access policy on how much and what kind of resources are allowed for an authenticated user.
Accounting — keeping statistic information about the user activities for accounting purpose.
RADIUS client and server requirements
Clients can be dual-stack, IPv4-only or IPv6 only.
Client authentication can be through 802.1X, MAC authentication, or web-based authentication. (clients using web-based authentication must be IPv4-capable.)
Server must support IPv4 and have an IPv4 address.
The following information provides an overview about RADIUS services supported on a switch, including CoS (802.1p priority), ingress and egress rate-limiting, and ACL client services on a RADIUS server. For information on configuring client authentication capability on the switch, see RADIUS Authentication, Authorization, and Accounting .
RADIUS services supported on the switch
RADIUS server support
Optional hpe pcm and idm network management applications.
All RADIUS-based services described here can be used without PCM+ or PMC IDM (Identity-Driven Management) support, if desired. For information on these services in the PCM+ application using the IDM plug-in, see the documentation for these applications on the HPE Support web site.
RADIUS server configuration for CoS (802.1p priority) and rate-limiting
The following information provides general guidelines for configuring RADIUS servers, so that the features listed in CoS and rate-limiting services can be dynamically applied on ports that support authenticated clients.
CoS and rate-limiting services
Standard Attribute used in the RADIUS server: 59 (This is the preferred attribute for new or updated configurations.)
Vendor-Specific Attribute used in the RADIUS server.
(This attribute is maintained for legacy configurations.)
HP vendor-specific ID:11
Setting: User-Priority-Table=xxxxxxxx where: x=desired 802.1p priority
Note: This is an eight-digit field. Enter the same x-value for all eight digits.
Requires a port-access authentication method (802.1X, Web Auth, or MAC Auth) configured on the client's port on the switch.
For more on 802.1p priority levels, see "Quality of Service (QoS)" in the advanced traffic management guide for your switch.
Ingress (inbound) rate-limiting per-user
Assigns a RADIUS-configured bandwidth limit to the inbound packets received from a specific client authenticated on a port.
Setting: HP-Bandwidth-Max-Egress=<bandwidth-in-Kbps>
Note: RADIUS-assigned rate-limit bandwidths must be specified in Kbps. (Bandwidth percentage settings are not supported.) Using a VSA on a RADIUS server to specify a per-user rate-limit requires the actual Kbps to which you want to limit ingress (inbound) traffic volume. For example, to limit inbound traffic on a gigabit port to half of the port's bandwidth capacity requires a VSA setting of 500,000 Kbps.
The actual bandwidth available for ingress traffic from an authenticated client can be affected by the total bandwidth available on the client port. See Per-port bandwidth override .
Egress (outbound) rate-limiting per-port
Assigns a RADIUS-configured bandwidth limit to the outbound traffic sent to a switch port.
VSA: 48 (string=HP)
Setting: HP-RATE-LIMIT=<bandwidth-in-Kbps>
Note: RADIUS-assigned rate-limit bandwidths must be specified in Kbps. (Bandwidth percentage settings are not supported.) Using a VSA on a RADIUS server to specify a per-port rate-limit requires the actual Kbps to which you want to limit outbound traffic volume. For example, to limit outbound traffic on a gigabit port to half of the port's bandwidth capacity requires a VSA setting of 500,000 Kbps.
In instances where multiple, authenticated clients are using this feature on the same switch port, only one (per-port) rate limit is applied. In this case, the actual rate used is the rate assigned by the RADIUS server to the most recently authenticated client. This rate remains in effect as long as any authenticated client remains connected on the port.
The actual bandwidth available for egress traffic from an authenti-cated client can be affected by the total bandwidth available on the client port. See Per-port bandwidth override .
To configure support for the services listed in CoS and rate-limiting services on a specific RADIUS server application, see the documentation provided with the RADIUS application.
Applied rates for RADIUS-assigned rate limits
Rate limits are applied incrementally on the switches, as determined by the RADIUS-applied rate. For any given bandwidth assignment, the switch applies the nearest rate increment that does not exceed the assigned value. The increments are in graduated steps, as described in RADIUS-assigned rate-limit increments .
RADIUS-assigned rate-limit increments
For example, some of the following RADIUS-assigned rates fall between their respective incremental values, resulting in applied rates lower than the RADIUS-assigned rates. However, others match their respective incremental values, resulting in no difference between the RADIUS-assigned rate limits and the applied rate limits.
Assigned and applied rate limits example
Per-port bandwidth override
Hewlett Packard Enterprise recommends that rate-limiting be configured either solely through RADIUS assignments or solely through static CLI configuration on the switch unless the potential for the override described below is specifically desired.
Ingress (inbound) traffic
Beginning with software release K.14.01, RADIUS-assigned ingress rate-limits are applied to individual clients instead of to the client's port. But if you use the CLI to configure a per-port ingress rate-limit on the same port where an authenticated client receives a RADIUS-assigned ingress rate-limit, the client's assigned ingress limit can be reduced by the CLI-configured port ingress limit. This occurs if the port reaches its CLI-configured rate-limit maximum before the client reaches its RADIUS-assigned rate-limit maximum, thus denying the client its intended maximum.
Egress (outbound) traffic
The most recent RADIUS-assigned egress rate-limit specifies the maximum egress rate-limit for a port, even if the CLI has also been used to configure an egress rate limit on the port.
For example, suppose the CLI is used to configure a gigabit port to have an ingress rate limit of 500,000 Kbps (50% of available bandwidth), and is receiving 450,000 Kbps of traffic from existing clients. If a RADIUS server then authenticates a new client with an ingress rate-limit of 100,000 Kbps, the maximum ingress rate limit actually available for the new client is 50,000 Kbps as long as the bandwidth usage by the other clients already on the port remains at 450,000 Kbps.
For more on static rate-limiting, see "Rate-Limiting" in the "Port Traffic Controls" in the management and configuration guide for your switch.
Configuring and using dynamic (RADIUS-assigned) access control lists
A RADIUS-assigned ACL is configured on a RADIUS server and dynamically assigned by the server to filter IP traffic from a specific client after the client is authenticated by the server.
The information in this section describes how to apply RADIUS-assigned ACLs on the switch, and assumes a general understanding of ACL structure and operation. If you need information on ACL filtering criteria, design, and operation, see the following:
IPv4 Access Control Lists (ACLs)
“IPv6 Access Control Lists (ACLs)" in the latest IPv6 configuration guide for your switch.
Overview of RADIUS-assigned, dynamic ACLs
RADIUS-assigned ACLs enhance network and switch management access security and traffic control by permitting or denying authenticated client access to specific network resources and to the switch management interface. This includes preventing clients from using TCP or UDP applications, ICMP packet types, and IGMP (IPv4 only) if you do not want their access privileges to include these capabilities.
Traffic applications
Beginning with software release K.14.01, the switch supports RADIUS-assigned ACLs for the following traffic applications:
Inbound IPv4 traffic only
Inbound IPv4 and IPv6 traffic
This feature is designed for use on the network edge to accept RADIUS-assigned ACLs for Layer-3 filtering of IP traffic entering the switch from authenticated clients. A given RADIUS-assigned ACL is identified by a unique user name/password pair or client MAC address, and applies only to IP traffic entering the switch from clients that authenticate with the required, unique credentials. The switch allows multiple RADIUS-assigned ACLs on a given port, up to the maximum number of authenticated clients allowed on the port. Also, a RADIUS-assigned ACL for a given client's traffic can be assigned regardless of whether other ACLs assigned to the same port are statically configured on the switch.
A RADIUS-assigned ACL filters IP traffic entering the switch from the client whose authentication caused the ACL assignment. Filter criteria is based on:
Destination address
IPv4 or IPv6 traffic type, such as TCP and UDP traffic
Implementing the feature requires:
RADIUS authentication using the 802.1X, web-based authentication, or MAC authentication available on the switch to provide client authentication services
Configuring one or more ACLs on a RADIUS server instead of the switch, and assigning each ACL to the user name/password pair or MAC address of the clients you want the ACLs to support
Using RADIUS to dynamically apply ACLs to clients on edge ports enables the switch to filter IP traffic coming from outside the network, thus removing unwanted IP traffic as soon as possible and helping to improve system performance. Also, applying RADIUS-assigned ACLs to the network edge is likely to be less complex than configuring static port and VLAN-based ACLs in the network core to filter unwanted IP traffic that could have been filtered at the edge.
Simultaneous ACL activity supported per-port [ 1 ]
ACLs enhance network security by blocking selected IP traffic, and can serve as one aspect of network security. However, because ACLs do not protect from malicious manipulation of data carried in IP packet transmissions, they should not be relied upon for a complete edge security solution.
Depending on the ACL configuration in the RADIUS server, the ACLs described in this section filter either IPv4 traffic only or both IPv4 and IPv6 traffic. These ACLs do not filter non-IP traffic such as AppleTalk and IPX.
Contrasting RADIUS-assigned and static ACLs
Contrasting dynamic (RADIUS-assigned) and static ACLs highlights several key differences between the static ACLs configurable on switch VLANs and ports, and the dynamic ACLs that can be assigned by a RADIUS server to filter IP traffic from individual clients.
Contrasting dynamic (RADIUS-assigned) and static ACLs
IPv4 traffic:
inbound RACL
outbound RACL
static port ACL
IPv6 traffic:
An RACL applied to inbound traffic on a VLAN filters routed IPv4 traffic entering the switch through a port on that VLAN, as well as any inbound traffic having a DA on the switch itself. An RACL can be applied to outbound IPv4 traffic on a VLAN to filters routed IPv4 traffic leaving the switch through a port on that VLAN (and includes routed IPv4 traffic generated by the switch itself).
A VACL can be applied on a VLAN to filter either IPv4 or IPv6 traffic entering the switch through a port on that VLAN.
A static port ACL can be applied on a port to filters either IPv4 or IPv6 traffic entering the switch through that port.
Beginning with software release K.14.01, the show statistics command includes options for displaying the packet match count, see Monitoring static ACL performance .
Also, ACEs allow a log option that generates a log message whenever there is a packet match with a "deny" ACE.
How a RADIUS server applies a RADIUS-assigned ACL to a client on a switch port
A RADIUS-assigned ACL configured on a RADIUS server is identified and invoked by the unique credentials (user name/password pair or a client MAC address) of the specific client the ACL is intended to service. Where the user name/password pair is the selection criteria, the corresponding ACL can also be used for a group of clients that all require the same ACL policy and use the same user name/password pair. Where the client MAC address is the selection criteria, only the client having that MAC address can use the corresponding ACL. When a RADIUS server authenticates a client, it also assigns the ACL configured with that client's credentials to the client's port. The ACL then filters the client's inbound IP traffic and denies (drops) any such traffic that is not explicitly permitted by the ACL.
If the filter rule used for a RADIUS-based ACL is one of the options that specifies only IPv4 traffic, then the ACL implicitly denies any inbound IPv6 traffic from the authenticated client.
If the filter rule used for a RADIUS-based ACL is the option for specifying both IPv4 and IPv6 traffic, then the ACL filter both IP traffic types according to the ACEs included in the RADIUS-assigned ACL.
When the client session ends, the switch removes the RADIUS-assigned ACL from the client port.
Multiple clients sharing the same RADIUS-assigned ACL
When multiple clients supported by the same RADIUS server use the same credentials, they are all serviced by different instances of the same ACL. (The actual IP traffic inbound from any client on the switch carries a source MAC address unique to that client. The RADIUS-assigned ACL uses this MAC address to identify the traffic to be filtered.)
Effect of multiple ACL application types on an interface
The switch allows simultaneous use of all supported ACL application types on an interface. Thus, a static ACL assigned to an interface filters authenticated client traffic, regardless of whether a RADIUS-assigned ACL is also filtering the client's traffic. For more information, see Multiple ACLs on an interface .
General ACL features, planning, and configuration
These steps suggest a process for using RADIUS-assigned ACLs to establish access policies for client IP traffic.
Determine the polices you want to enforce for authenticated client traffic inbound on the switch.
Plan ACLs to execute traffic policies:
Apply ACLs on a per-client basis where individual clients need different traffic policies or where each client must have a different user name/password pair or will authenticate using MAC authentication.
Apply ACLs on a client group basis where all clients in a given group can use the same traffic policy and the same user name/password pair.
Configure the ACLs on a RADIUS server accessible to the intended clients.
Configure the switch to use the desired RADIUS server and to support the desired client authentication scheme. Options include 802.1X, web-based authentication, or MAC authentication. (Note that the switch supports the option of simultaneously using 802.1X with either web-based or MAC authentication.)
Test client access on the network to ensure that your RADIUS-assigned ACL application is properly enforcing your policies.
For further information common to all IPv4 or IPv6 ACL applications, see the IPv4 configuration guide or IPv6 configuration guide for your switch.
The packet-filtering process
Packet-filtering in an applied ACL is sequential, from the first ACE in the ACL to the implicit deny any any following the last explicit ACE. This operation is the same regardless of whether the ACL is applied dynamically from a RADIUS server or statically in the switch configuration.
Operating rules for RADIUS-assigned ACLs
Relating a client to a RADIUS-assigned ACL
A RADIUS-assigned ACL for a particular client must be configured in the RADIUS server under the authentication credentials the server should expect for that client. If the client must authenticate using 802.1X and web-based authentication, the user name/password pair forms the credential set. If authentication is through MAC Authentication, then the client MAC address forms the credential set. See Configuring an ACL in a RADIUS server .
Multiple clients using the same user name/password pair
Multiple clients using the same user name/password pair uses duplicate instances of the same ACL.
Limits for ACEs in RADIUS-assigned ACLs
The switch supports up to 80 characters in a single ACE. Exceeding this limit causes the related client authentication to fail.
Effect of other, statically configured ACLs
Suppose that port B1 belongs to VLAN "Y" and has a RADIUS-assigned ACL to filter inbound traffic from an authenticated client. Port B1 is also configured with IPv4 and IPv6 static port ACLs, and VLAN "Y" is statically configured with IPv4 and IPv6 VACLs.
IP traffic entering the switch on port B1 from the client and having a match with a deny ACE configured in any of the ACLs mentioned above is dropped.
If an inbound RACL was also configured on VLAN "Y", then a deny match in the RACL would apply to any inbound, routed IPv4 traffic from the client (and to any inbound, switched traffic having a destination on the switch itself).
If an outbound RACL was also configured on VLAN "Y", then any outbound, routed IPv4 traffic leaving the switch through the port B1 would be filtered by the outbound RACL.
Configuring an ACL in a RADIUS server
The following information provides general guidelines for configuring a RADIUS server to specify RADIUS-assigned ACLs. It also provides an example configuration for a FreeRADIUS server application. To configure services on a specific RADIUS server application, see the documentation provided with that application.
A RADIUS-assigned ACL configuration in a RADIUS server includes the following elements:
Nas-Filter-Rule attributes — standard and vendor-specific
ACL configuration, entered in the server, and associated with specific user name/password or MAC address criteria, and comprised of ACEs entered in the server
A RADIUS-assigned ACL includes:
One or more explicit permit and deny ACEs
An implicit deny in ip from any to any ACE automatically applied after the last operator-created ACE
Nas-Filter-Rule-Options
Nas-Filter-Rule Attribute Options
Set IP Mode
Used with the Nas-filter-Rule attribute described above to provide IPv6 traffic-filtering capability in an ACE.
HP-Nas-Rules-IPv6: 63 (Vendor-Specific Attribute)
When using the standard attribute (92) described above in a RADIUS-assigned ACL to support both IPv4 and IPv6 traffic inbound from an authenticated client, one instance of this VSA must be included in the ACL. Note that this attribute supports either of the following IP modes for Nas-filter-Rule ACEs:
both IPv6 and IPv4 traffic
only IPv4 traffic
HP vendor-specific ID: 11
VSA: 63 (string=HP-Nas-Rules-IPv6)
IPv6 and IPv4 ACLs: integer = 1(Using this option causes the ACL to filter both IPv4 and IPv6 traffic.)
IPv4-only ACLs: integer=2 (Using this option causes the ACL to drop any IPv6 traffic received from the authenticated client.)
Setting: HP-Nas-Rules-IPv6 =<1
2> Nas-filter-Rule "<permit or deny ACE> "
However, if you do not want both the IPv4 and IPv6 traffic of the selected type to go to their respective "any" destinations, then two ACEs with explicit destination addresses are needed. In this case, do one of the following:
Use 0.0.0.0/0 in one ACE to specify the "any" destination for IPv4 traffic, and use a specific IPv6 address for the destination in the other ACE.
Use ::/0 in one ACE to specify the "any" destination for IPv6 traffic, and use a specific IPv4 address for the destination in the other ACE.
For example, if you want to allow the IPv4 Telnet traffic from a client to go to any destination, but you want the IPv6 Telnet traffic from the same client to go only to a specific address or group of addresses, you must distinguish the separate destinations. This is done by using explicit addresses for the "any" destinations. For example:
The above example sends IPv4 Telnet traffic to its "any" destination, but allows IPv6 Telnet traffic only to fe80::b1 23.To reverse this example, you would configure ACEs such as the following:
In cases where you do not want the selected traffic type for either IPv4 or IPv6 to go to the "any" destination, you must use two ACEs to specify the destination addresses. For example:
To use the IPv6 VSA while allowing only IPv4 traffic to be filtered, you would use a configuration such as the following:
IPv4-only ACLs applied to client traffic inbound to the switch
Assigns a RADIUS-configured IPv4 ACL to filter inbound IPv4 packets received from a specific client authenticated on a switch port.
HP-Nas-Filter-rule (Vendor-Specific Attribute): 61
This attribute is maintained for legacy purposes (for configurations predating software release K.14.01) to support ACEs in RADIUS-assigned ACLs capable of filtering only IPv4 traffic. However, for new or updated configurations (and any configurations supporting IPv6 traffic filtering) Hewlett Packard Enterprise recommends using the Standard Attribute (92) described earlier in this table instead of the HP-Nas-filter-Rule attribute described here.
VSA: 61 (string=HP-Nas-Filter-Rule
Setting: HP-Nas-filter-Rule ="<permit or deny ACE> "
ACE syntax in RADIUS servers
The following information describes ACE syntax configuration options in a RADIUS server.
Configuration notes
Explicitly permit ipv4 and ipv6 traffic from an authenticated client.
This option for ending a RADIUS-assigned ACL permits all of the client's inbound IPv4 and IPv6 traffic not previously permitted or denied.
See Nas-Filter-Rule Attribute Options for information on the above attributes.
Explicitly permit only the IPv4 traffic from an authenticated client
Any of the following three options for ending a RADIUS-assigned ACL explicitly permit all of the client's inbound IPv4 traffic not previously permitted or denied. These options also deny any of the client's IPv6 traffic not previously permitted or denied.
- Nas-filter-Rule += permit in ip from any to any
(Using this attribute to permit IPv4 traffic from the client while denying any IPv6 traffic from the client assumes that HP-Nas-Rules-IPv6=1 does not exist elsewhere in the ACL. See Nas-Filter-Rule Attribute Options for more on HP-Nas-Rules-IPv6. )
- HP-Nas-Filter-Rule += permit in ip from any to any
- Nas-filter-Rule += permit in ip from any to any HP-Nas-Rules-IPv6=2
Explicitly denying inbound traffic from an authenticated client
Any of the following three options for ending a RADIUS-assigned ACL explicitly deny all of the client's inbound IPv4 and IPv6 traffic not previously permitted or denied.
- Nas-filter-Rule += deny in ip from any to any
- HP-Nas-Filter-Rule += deny in ip from any to any
- Nas-filter-Rule += deny in ip from any to any HP-Nas-Rules-IPv6=2
Implicitly denying any IP traffic
For any packet being filtered by a RADIUS-assigned ACL, there is always a match. That is, any packet that does not have a match with an explicit permit or deny ACE in the list matches with the implicit deny any any ACE automatically included at the end of the ACL. That is, a RADIUS-assigned ACL includes an implicit deny in ip from any to any ACE at the end of the ACL to deny any IPv4 and IPv6 traffic not previously permitted or denied.
Monitoring shared resources
Currently active, RADIUS-based authentication sessions (including IDM client sessions) using RADIUS-assigned ACLs share internal switch resources with several other features. The switch provides ample resources for all features. However, if the internal resources do become fully subscribed, new RADIUS-based sessions using RADIUS-assigned ACLs cannot be authenticated until the necessary resources are released from other applications.
For information on determining the current resource availability and usage, see “Monitoring Resources" in the management and configuration guide for your switch.
For a summary of ACL resource limits, see the topics covering scalability in the latest management and configuration guide for your switch.
Event log messages
See theEvent Log message reference guide for information about Event Log messages.
Causes of client deauthentication immediately after authenticating
ACE formatted incorrectly in the RADIUS server
from , any , or to keyword missing.
An IPv4 or IPv6 protocol number in the ACE exceeds 255.
An optional UDP or TCP port number is invalid, or a UDP/TCP port number is specified when the protocol is neither UDP or TCP.
A RADIUS-assigned ACL limit has been exceeded.
An ACE in the ACL for a given authenticated client exceeds 80 characters.
The TCP/UDP port-range quantity of 14 per slot or port group has been exceeded.
The rule limit of 3048 per slot or port group has been exceeded.
An IPv6 ACE has been received on a port and either the HP-Nas-Rules-IPv6 attribute is missing or HP-Nas-Rules-IPv6=2 is configured. See Nas-Filter-Rule Attribute Options for more on this attribute.
Copyright © 2016 Hewlett Packard Enterprise Development LP
Configuring the switch to access a RADIUS server
Configuring a RADIUS server to support web-based authentication and MAC Authentication require the following minimal commands:
(See RADIUS Authentication, Authorization, and Accounting for information on other RADIUS command options.)
radius-server no radius-server
[host < ip-addresss >]
Adds a server to the RADIUS configuration or, when no is used, deletes a server from the configuration. You can configure up to three RADIUS server addresses. The switch uses the first server it successfully accesses. (See RADIUS Authentication, Authorization, and Accounting ).
[key < global-key-string >]
Specifies the global encryption key the switch uses with servers for which the switch does not have a server specific key assignment (below). This key is optional if all RADIUS server addresses configured in the switch include a server-specific encryption key. The tilde (~) character is allowed in the string, for example, radius server key aruba~switch. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character.
(Default: Null.)
radius-server host < ip-address > key < server-specific key-string > no radius-server host < ip-address > key
Specifies an encryption key for use during authentication (or accounting) sessions with the specified server. This key must match the encryption key used on the RADIUS server. Use this command only if the specified server requires a different encryption key than configured for the global encryption key, above. The tilde (~) character is allowed in the string. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character.
The no form of the command removes the key configured for a specific server.
For example, to configure the switch to access a RADIUS server at IP address 192.168.32.11 using a server specific shared secret key of ‘1A7rd’:
Configure the switch to access a RADIUS server


IMAGES
VIDEO
COMMENTS
Which assignment technique requires a RADIUS server? a. Static VLAN assignment b. Dynamic VLAN assignment c. Dynamic IP address assignment d. Static IP address assignment. b. Dynamic VLAN assignment ... If a server has a subnet mask of 255.255.255.224, how many bits in its IP address identify the host? a. 27 bits b. 8 bits c. 5 bits d. 30 bits ...
Which assignment technique requires a RADIUS server? Dynamic VLAN assignment. Dynamic IP address assignment. Static IP address assignment. Static VLAN assignment. 8 of 18. Term. ... Which IP addressing technique subnets a subnet to create subnets of various sizes? Choose matching definition. Private vlan (pvlan) Variable Length Subnet Masking ...
RADIUS authentication is a method employed to confirm a user's identity when they endeavor to establish a connection with a network. Here's how it works: 1. User connection attempt. A user attempts to connect to a network or network resource, such as a VPN or Wi-Fi access point.
This procedure explains how to configure the users in the RADIUS server and the RADIUS (IETF) attributes used to assign VLAN IDs to these users. Complete these steps: From the ACS GUI, click User Setup. In the User Setup window, enter a username in the User field and click Add/Edit.
The RADIUS (Remote Authentication Dial-In Service) protocol is a client-server networking protocol that facilitates communication between a central server and individual users who want to gain access to the server. Essentially, RADIUS allows remote access servers to communicate with the central server to authenticate and authorize remote user ...
To set up the RADIUS preauthentication profile, use the call type string as the username, and use the password defined in the ctype command as the password. The table below lists the call type strings that can be used in the preauthentication profile. Table 1 Call Type Strings Used in Preauthentication. Call Type String.
Lab topology for Radius server. Configure the IP address of a router. Configure Telnet on the Router. Enable the AAA radius authentication on the router. Configure the AAA Radius Server in packet tracer. Ping and telnet the router from one of the PCs to check the connectivity. PC1 successfully ping and telnet the router.
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users connecting to a network. RADIUS operates on a client-server model, with the RADIUS server managing user credentials, access rules, and accounting information, while the ...
The IEEE-802.1X authentication provides a security standard for network access control with RADIUS servers and holds a network port disconnected until authentication is completed. With 802.1X authentication, the supplicant provides credentials, such as user name, password, or digital certificate to the authenticator, and the authenticator forwards the credentials to the authentication server ...
Which assignment technique requires a RADIUS server? a. Static VLAN assignment b. Dynamic VLAN assignment c. Dynamic IP address assignment d. Static IP address assignment. Here's the best way to solve it. Powered by Chegg AI. View the full answer.
TEL +1 (613) 454-5037. FAX +1 (613) 800-0322. [email protected]. A RADIUS server utilizes a central database to authenticate remote users. RADIUS functions as a client-server protocol, authenticating each user with a unique encryption key when access is granted. How a RADIUS server works depends upon the exact nature of the RADIUS ecosystem.
Figure 11-19.Specifying the Accounting Server in the Radius Configuration Screen. To enforce RADIUS accounting, the WLAN must use 802.1X authentica-tion, Web-Auth, or MAC authentication for the Authentication mode. Configure settings for the primary accounting server in the Primary. column of the Accounting section.
Requires client authentication by a RADIUS server configured to dynamically assign an ACL to a client on a switch port, based on client credentials. No client authentication requirement. ACEs allow a counter (cnt) option that causes a counter to increment when there is a packet match.
Study with Quizlet and memorize flashcards containing terms like How many bits of a class A IP address are used for host information?, What is the formula for determining the number of possible hosts on a network?, Which of the following is not a good reason to segment a network? and more.
Because Flexible authentication uses dynamic VLANs, it is recommended to configure the VLAN information in the RADIUS server. Refer to Configuring the RADIUS server to support dynamic VLAN assignment for flexible authentication for a list of the attributes that must be set on the RADIUS server. If one of the attributes in the Access-Accept ...
The assignment technique requires a RADIUS server are:. Dynamic VLAN Assignment .; Static VLAN assignment.; Which assignment technique requires a radius server? The VLAN assignments is known to be created on the use of RADIUS to monitor access to the network.. Note that with the use of RADIUS integration, a WiFi access point (WAP) does not really need only an SSID and passphrase, but a user's ...
Study with Quizlet and memorize flashcards containing terms like Which of the following techniques does not break up a large broadcast domain into smaller broadcast domains?, Benefits of Subnetting, What is the minimum number of bits that should be borrowed to create 14 subnets? and more. ... Which assignment technique requires a RADIUS server ...
Configure the Users and the RADIUS (IETF) Attributes Used for Dynamic VLAN Assignment on the RADIUS Server • Configure the AAA Client for the WLC on the RADIUS Server This procedure explains how to add the WLC as a AAA client on the RADIUS server so that the WLC can pass the user credentials to the RADIUS server. Complete these steps: 1.
User role assignment is configured on the RADIUS server using VSAs (vendor-specific attributes). RADIUS servers can return multiple attribute value pairs (AVPs) in response to an authentication request. The attributes are processed in this order of precedence to determine the user role assigned: If the Aruba-Admin-Role VSA is present, map the ...
d. To narrow down the location of problems on a. network. c. To increase the number of networking devices on a network. What is the greatest number of bits you could borrow from the host portion of a class B subnet mask and still have at least 130 hosts per subnet? a. 0 bits b. 8 bits c. 9 bits d. 10 bits. b. 8 bits.
(See RADIUS Authentication, Authorization, and Accounting for information on other RADIUS command options.) Syntax: radius-server no radius-server [host < ip-addresss >] Adds a server to the RADIUS configuration or, when no is used, deletes a server from the configuration. You can configure up to three RADIUS server addresses. The switch uses ...
Created by. santosjaguar2000. Module8 Homework and QuizHow many bits of a class A IP address are used for host information? 1 / 2. Module8 Homework and QuizHow many bits of a class A IP address are used for host information? Learn with flashcards, games, and more — for free.
Study with Quizlet and memorize flashcards containing terms like How many bits of a Class A IP address are used for host information?, What is the formula for determining the number of possible hosts on a network?, Which of the following is not a good reason to segment a network? and more.