
Set and Check User Rights Assignment via Powershell
You can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts..
Posted by : blakedrumm on Jan 5, 2022
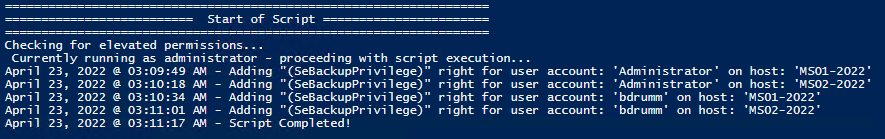
Local Computer
Remote computer, output types.
This post was last updated on August 29th, 2022
I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights.
Set User Rights
How to get it.
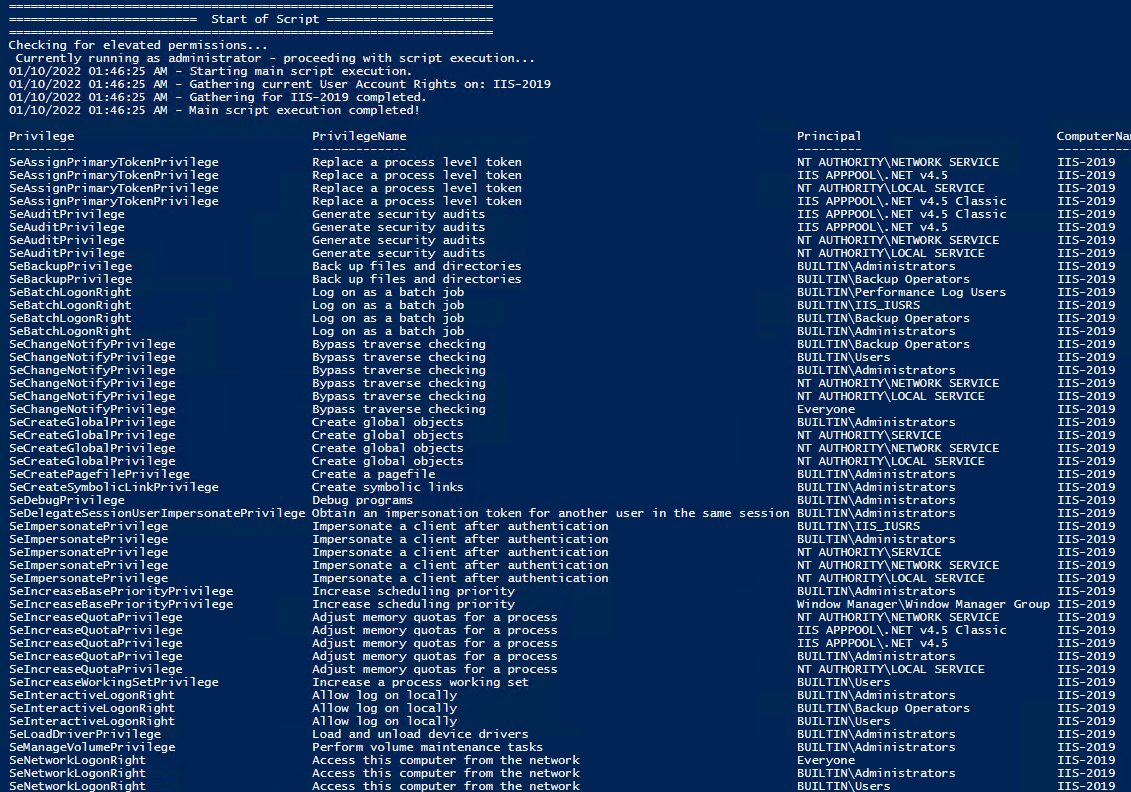
All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Here are a few examples:
Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Check User Rights
In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Get Local User Account Rights and output to text in console:
Get Remote SQL Server User Account Rights:
Get Local Machine and SQL Server User Account Rights:
Output Local User Rights on Local Machine as CSV in ‘C:\Temp’:
Output to Text in ‘C:\Temp’:
PassThru object to allow manipulation / filtering:
I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs.
Email : [email protected]
Website : https://blakedrumm.com
My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
- operationsManager
- troubleshooting
- certificates
WinSecWiki > Security Settings > Local Policies > User Rights
User Rights Assignments
Although in this section they are called user rights, these authority assignments are more commonly called privileges.
Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users. Each computer has its own user rights assignments. In particular this means you should be cognizant of rights assignments on member servers which may easily differ from the rights assignments you find on your domain controllers. To centrally control user rights assignments on computers throughout your domain use group policy.
- Logon rights
- Admin equivalent rights
- Tracking user rights with the security log
- User rights in-depth
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow logon through Terminal Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Debug programs
- Deny access to this computer from the network
- Deny logon as a batch job
- Deny logon as a service
- Deny logon locally
- Deny logon through Terminal Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify firmware environment values
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files and other objects
Child articles:
- Logon Rights
- Admin Equivalent Rights
- Tracking User Rights with the Security Log
- User Rights In-Depth
Back to top

Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
User Rights Assignment Back To Not Defined
Is it possible to put a Local Policy User Rights Assignment back to Not Defined? There is not a checkbox to mark it as Not Defined. Is it possible to set any of the User Rights Assignments back to Not Defined?
I am trying to find an area of a Group Policy that is causing an issue with the installation of a Windows Feature. I have removed the computer from the domain and many parts of the GPO remains on the computer including User Rights Assignment. I am suspicious that this is causing the error I am getting. I would like to go through the User Rights Assignment to see what is causing the issue. If I can se it back to Not Defined per item them I can see what is causing the issue. But I do not see a way to check a box to put it back. I can remove everyone from the list of users/groups but that just makes the list blank and doesn't set it to Not Configured.
- group-policy
- security-policy
- If a local policy is configured as "Not Defined", it means the current value is the default value, which is either the value for enabled or the value for disabled. There a reason you cannot simply just set the value of the policy back to "not defined' using the group policy editor? Encourage you to provide more information, perhaps even explain what problem you are trying to solve, so we can answer your question. – Ramhound Sep 8, 2017 at 20:10
- @Ramhound I added some information. I am trying to find a piece of URS causing errors on the installation of a windows server feature. – JukEboX Sep 8, 2017 at 20:28
- Tell us the exact policy. What it modified in the registry should be easy to determine removing the keys will be how this is done – Ramhound Sep 8, 2017 at 21:32
User Right Assignment don't have a "default" configuration.
This is due to the fact that these settings are modified by when certain Windows roles and features are installed. Other applications can also modify these rights, creating a situation where a one-size-fits-all definition of default would leave many systems half functional.
Further, the User Right Assignments fall into a broader category of GP settings that cannot be conveniently reverted to a default state due to an effect known as Group Policy tattooing.
You must apply your own "default" settings
If you only have a few User Rights to modify , edit the settings through the Local Group Policy editor ( gpedit.msc ) and refer to another workstation that has the desired rights assignments for your configuration.
If you have many User Rights to modify , then consider using the Secedit command-line tool to export the settings from a computer with the desired configuration and then apply them into the target machine. Example commands:
Export the current machine's User Rights Assignments:
Apply the exported User Rights Assignments to the local machine:
More Information
This Microsoft support article explains why it's not possible to restore Windows Security settings to a so-called default state and offers some possible workarounds.
This and this article discuss Group Policy tattooing and its implications for Windows Security Settings.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged windows group-policy security-policy ..
- The Overflow Blog
- You should keep a developer’s journal
- Would you board a plane safety-tested by GenAI?
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- Is there is way to determine if the n-th roots of a polynomial is a polynomial?
- What is the reason for the priest taking the Eucharist without distributing it to the people at mass?
- How do I draw 90 degree angle arrows and background
- Viability of Hydraulic Telegraph System?
- How to reduce margin size for one slide to fit a table in beamer?
- Why is 2 Thessalonians 2:14 translated with a singular "you" when the Greek is plural?
- Should I care about my legacy?
- If gravitation is negligible for small masses, how was Cavendish's experiment successful with balls much smaller than celestial objects?
- Best practices for citing a reference you've found an error in
- Chopin Op. 9 No. 3 m. 27
- What's wrong with my new environment?
- "Vintage" internal cable routing to external
- Sci-fi story set in the future, in which a (small) subplot involves AI being used to send spam
- How much current can a 2N7000 MOSFET guaranteed switch with 3.3V logic
- Can you "spot" the pattern?
- Evidence of lightning-caused mass extinction
- Why would email transmission change the 6-char sequence "0rom "?
- Old CAAD8 with wh-r550 rear wheel
- How does Hard to Kill ability interact with Undead PC?
- Is the Sufficiency Principle an axiom?
- Possible binding agent for Chlorine in blood?
- How to deal as a PhD student with a working colleague who is doing private business during working hours?
- Usage and meaning of “may have” in this context
- When exactly is ~/snap created?
How to apply Group Policy settings to specific users on Windows 11
Do you have to change policy settings but only for some users? Here's how on Windows 11.
On Windows 11 (similar to previous versions), the Local Group Policy Editor is a Microsoft Management Console (MMC) snap-in that provides an interface to allow administrators (and power users) to manage every Group Policy Object (GPO) on the local computer. It enables you to configure and customize system settings and control user accounts, security, and other administrative tasks that are typically not possible to configure through the Settings app (or Control Panel).
The only drawback about this management console is that the settings configured through the method will apply to every user as it doesn't offer an option to configure settings for a specific user or group. However, it's possible to roll out system changes to only some users by creating a User-Specific Local Group Policy (LGPO) snap-in.
This how-to guide will walk you through the steps to use the Local Group Policy Editor to apply settings only to specific users on Windows 11.
How to apply settings to specific user with Group Policy
To configure system settings that will only apply to specific users on Windows 11, use these steps:
- Use the "Windows key + R" keyboard shortcut to open the Run command.
- Type MMC and click the OK button.
- Open the File menu and select the "Add/Remove Snap-in" option.
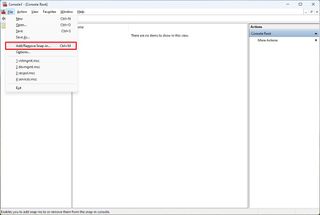
- Under the "Available snap-ins" section, select the "Group Policy Object Editor" snap-in.
- Click the Under the "Available snap-ins" section, and select the "Group Policy Object Editor" snap-in.
- Click the Add button.
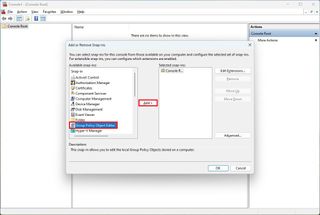
- Click the Browse button.
- Click the User tab.
- Select the user or group to apply the new configurations.
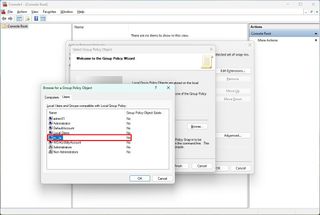
- Quick tip: To change settings for users with a "Standard user" account, select Non-Administrators from the list.
- Click the OK button.
- Click the Finish button.
- Open the File menu and select the Save As option.
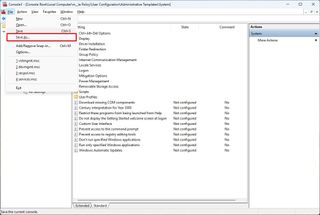
- Confirm a name for the snap-in.
- Select a location to store the custom console with the configurations.
- Click the Save button.
After you complete the steps, you can open the newly created Microsoft Management Console to configure the settings you want to apply to a specific user.
For example, you can use these instructions to configure custom settings or restrict access to certain features, such as Registry , Command Prompt, Settings app, and others, allowing users to make unwanted system changes.
More resources
For more helpful articles, coverage, and answers to common questions about Windows 10 and Windows 11, visit the following resources:
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
- Windows 11 on Windows Central — All you need to know
- Windows 10 on Windows Central — All you need to know
Mauro Huculak is technical writer for WindowsCentral.com. His primary focus is to write comprehensive how-tos to help users get the most out of Windows 10 and its many related technologies. He has an IT background with professional certifications from Microsoft, Cisco, and CompTIA, and he's a recognized member of the Microsoft MVP community.
- 2 Warhammer 40,000: Rogue Trader's first DLC expansion is revealed
- 3 'Uh Oh', VK is pulling the plug on its nostalgic ICQ (I Seek You) instant messaging platform after nearly three decades of keeping people connected
- 4 Microsoft gives a subtle reminder about the upcoming death of Windows 10
- 5 The next DOOM is called 'DOOM: The Dark Ages,' with a medieval feel — and it's coming to Xbox, Windows, and PlayStation
- About the Authors

Managing “Logon As a Service” Permissions Using Group Policy or PowerShell
“ Log on as a service ” is a security policy in Microsoft Windows operating systems that specifies which user accounts or groups are allowed to start and run Windows services. Services are programs running in the background and performing various tasks without user interaction. They are essential components of the Windows operating system and are used for networking, hardware management, and system monitoring tasks.
When a service starts, it must run under a specific user account, either a built-in system account or a custom user account. The “Log on as a service” policy defines which accounts or groups have the privilege to be assigned as the login credentials for these services. This policy is crucial for maintaining security and preventing unauthorized access to system resources.
Configuring the “Log on as a service” policy involves assigning specific accounts or groups the right to log on as a service. By default, only certain built-in accounts and groups have this privilege. Suppose an application or service requires a specific user account to function correctly. That account needs to be explicitly added to the “Log on as a service” policy to ensure it has the necessary permissions.
“Log on as a service” Rights vs. Privileges User Account
Assigning a specific user account to run Windows services using the “Log on as a service” privilege offers several advantages over using the built-in Local System account or other privileged user accounts:
- Principle of Least Privilege: The principle of least privilege suggests that users, processes, and services should have only the permissions necessary to perform their tasks. Assigning a dedicated user account to run a service allows you to grant precisely the required permissions for that service, reducing the risk of unintended actions or security breaches.
- Isolation of Services: By using individual user accounts for each service, you can isolate the privileges and resources associated with each service. This isolation helps prevent one compromised service from affecting other services or system components.
- Auditability: Using separate user accounts for services makes it easier to track and audit the activities of each service. In the event of security incidents or unauthorized access, it’s simpler to identify the responsible service when services are associated with distinct user accounts.
- Controlled Access: Assigning specific accounts to services allows you to control who has access to run those services. You can restrict the accounts with the “Log on as a service” privilege, reducing the attack surface and improving overall security.
- Password Management: Services associated with dedicated user accounts can manage their passwords separately. This is especially useful in scenarios where password changes are required periodically or when following password management policies.
- Compatibility: Some applications and services are designed to work best under a specific user context rather than the Local System account. Running them as the Local System might lead to compatibility issues or limited functionality.
- Granular Permissions: User accounts assigned to services can have finely tuned permissions. This is particularly important when services interact with specific network resources, databases, or other systems. Assigning the appropriate permissions ensures smooth service operation without granting excessive privileges.
- Debugging and Troubleshooting: When services run under a specific user account, troubleshooting issues becomes easier. You can log in with that account to test and diagnose problems directly, which can be more challenging when using the Local System account.
While there are definite benefits to using dedicated user accounts for services, managing these accounts effectively is essential. Proper management includes maintaining strong passwords, adhering to password policies, and ensuring that the accounts themselves are not susceptible to unauthorized access.
In some cases, certain services may require more extensive privileges, making using the Local System account necessary. But, when possible, using the “Log on as a service” privilege to assign specific user accounts to services is a recommended security practice that enhances control, accountability, and overall system security.
Managing “Log on as a service” Rights Assignments via Group Policy
You can configure the “Log on as a service” rights assignment via the local or domain group policy.
Note . When you deploy the “Log on as a service” policy via Group Policy Object (GPO), the policy settings you define in the GPO will overwrite the existing list of accounts on the target computers. The GPO settings for “Log on as a service” will replace any existing accounts or groups granted the privilege.
- If deploying via GPO, open the Group Policy Management console ( gpmc.msc ) and open the group policy object to modify or create a new one.
- If modifying the local machine’s group policy, open the local group policy editor ( secpol.msc )

Note . The “NT SERVICESERVICES” group is added to the “ Log on as a service ” policy by default on Windows Server 2016, Windows 10, and later.

- THEITBROS\CA IT Ops — domain group
- THEITBROS\jmiller — domain user
- PCX\localadmin01 — local user

Related post . Configure NTP Time Sync Using Group Policy
Managing “Log on as a service” Rights Assignments via PowerShell
Managing the “Log on as a service” rights assignments in the command line is beneficial for systems without a desktop environment, such as Windows Server Core, and when managing computers during remote PowerShell sessions.
There are no native PowerShell cmdlets to manage the “Log on as a service” policy as of this writing. The only native command line tool that can modify the local security policies is the secedit.exe tool.
Download the “Log on as a service” Management Scripts
So, we created three PowerShell script wrappers for secedit.exe that you can download from the following links:
- [ PS-Manage-Log-On-As-A-Service ] — The public GitHub repository.
- [ Get-ServiceLogonRight.ps1 ] — A script to retrieve the local machine’s current “Log on as a service” rights.
- [ Add-ServiceLogonRight.ps1 ] — A script to add a user and group to the “Log on as a service” policy.
- [ Remove-ServiceLogonRight.ps1 ] — A script to remove a user or group from the current “Log on as a service” policy.
Download the above scripts and store them in a folder on your computer. Then open an elevated PowerShell session (run as admin), and change the working directory to where you saved the scripts.

List the Current “Log on as a service” Rights Assignments
To list the current accounts in the “Log on as a service” policy, run the below script.

Add Users and Groups to the “Log on as a service” Policy
To add a user or group to the “Log on as a service” Policy, follow the below example commands.
# Add a local group .\Add-ServiceLogonRight.ps1 -UserOrGroup <local group>
# Add a domain user account .\Add-ServiceLogonRight.ps1 -UserOrGroup <DOMAIN\user>
# Add a domain group .\Add-ServiceLogonRight.ps1 -UserOrGroup <DOMAIN\group>

Confirm that the new users and groups were added to the “Log on as a service” policy.

What happens if you add a non-existing group or user to the “Log on as a service” policy? You’ll get this message.

Remove Users and Groups from the “Log on as a service” Policy
When a group or user is no longer viable for the “Log on as a service” policy, you can remove it using the Remove-ServiceLogonRight.ps1 script.
# Remove a local group .\Remove-ServiceLogonRight.ps1 -UserOrGroup localadmingroup02
# Remove a domain user .\Remove-ServiceLogonRight.ps1 -UserOrGroup ‘THEITBROS\ebrown’
# Remove a domain group .\Remove-ServiceLogonRight.ps1 -UserOrGroup ‘THEITBROS\CA Server Admins’

Run the .\Get-ServiceLogonRight.ps1 script to confirm that the users and groups have been removed.

What happens if you remove a user or group not existing in the “Log on as a service” policy? You’ll get the following message.

While there are scenarios where services necessitate greater privileges and the use of the Local System account, assigning specific user accounts through the “Log on as a service” policy is recommended to enhance control, accountability, and overall system security.
This article has also covered methods for managing “Log on as a service” rights assignments via Group Policy and PowerShell.
For PowerShell users, the article introduced scripts using the secedit.exe tool to manage these rights assignments. These scripts include Get-ServiceLogonRight.ps1 to retrieve current rights, Add-ServiceLogonRight.ps1 to add users or groups, and Remove-ServiceLogonRight.ps1 to remove them.
Lastly, minimizing the number of user accounts to which you grant the “Log on as a service” permissions is advisable. To reduce security risks, you should turn off interactive and remote interactive sessions for service accounts.
Our newsletter is full of great content!
Subscribe TheITBros.com newsletter to get the latest content via email.

Cyril Kardashevsky
I enjoy technology and developing websites. Since 2012 I'm running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.
Understanding ProxyAddresses Attribute in Active Directory
How to use get-acl and set-acl cmdlets when managing ntfs permissions for a file or folder with powershell.
Thank you. Literally NO ONE in Enterprise IT understands this about most of the stuff in the USer Rights Assignment of Group Policy. I’ve fixed so many outages due to admins settings this via GPO across many servers and overwriting what’s already set in there by x, y, z application that was installed who put accounts in there. Admins just blindly follow along application documentation or posts like this. I’m so tired of it.
– Angry Sr. Systems Admin LOL
Been like this for 20 years now.
Microsoft really needs to add switches for append, remove and replace for setting group policy objects, or just remove these from GPO management altogether as it’s half baked.
Please follow this up with how to set Logon As a Service for a user or group policy on Windows Server 2016 Core – there is no GUI, no control panel, no gpedit.msc, no gpmc.msc, no services.msc, etc etc.
For example, to setup Jenkins requires a user account with Logon As a Service enabled. Thank you
Leave a Comment Cancel Reply
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Windows User Rights Assignment Utility
jcasale/UserRights
Folders and files, repository files navigation.
The UserRights.exe utility is an application for managing the User Rights Assignment security policy settings.
UserRights.exe is similar to ntrights.exe from the Windows 2003 Resource Kit utility, with additional functionality making it more flexible for use in automation.
Use Case - Automating User Rights Assignment on Windows Servers
Managing user rights assignment with group policies is not trivial. The interface only allows either exclusively specifying all the principals that will be granted the right, or leaving the user right unmanaged. That is the only reasonable approach, the grants will vary depending on the roles or applications that are installed. There may be virtual accounts (e.g., IIS application pool accounts with security identifiers matching S-1-5-82-*) or NT service accounts (e.g., MSSQL accounts with security identifiers matching S-1-5-80-*) that are granted privileges.
This requires the creation and maintenance of unique and highly specific group policies for each platform and software combination. For example, a typical approach for managing the SeServiceLogonRight right might resemble:
- Create a new group policy object.
- Ensure the mode is set to Update .
- Ensure Delete all member users is enabled.
- Ensure Delete all member groups is enabled.
- Enable item level targeting, add an LDAP Query and configure it to pass only when the LDAP query does not return a value indicating the related directory group was not found (e.g., DOMAIN\allow-log-on-service-%ComputerName% ).
- Configure a single member by adding the related directory group using the variable based convention (e.g., DOMAIN\allow-log-on-service-%ComputerName% ).
- Enable item level targeting, add an LDAP Query and configure it to pass only when the LDAP query does return a value indicating the related directory group was found (e.g., DOMAIN\allow-log-on-service-%ComputerName% ).
- Add any required local users.
- Add any required local groups.
- Add any required virtual accounts.
- Add any required NT service accounts.
- Add the new local group created above, allow-log-on-service .
- Link the policy and configure the security and filtering as required.
When the policy executes, the %ComputerName% variable will be expanded and the applicable preference will create the local group, and the grants for the user right privilege will be overwritten. If the related directory security group is later provisioned, it will be added to the local group and the user rights will apply. While there is nothing wrong with this approach, it certainly is the most secure, but it has fairly high overhead.
An alternative approach without the local groups that uses UserRights.exe to grant the required directory group and revoke any inappropriate grants using a pattern is possible.
This example illustrates an approach for managing the SeServiceLogonRight right and can be applied to any of the user rights.
Copy the UserRights.exe utility to a network share that is accessible by all computer accounts.
Create an Active Directory security group for the server that should have the SeServiceLogonRight right managed. The group name must contain the sAMAccountName in addition to any conventions that are required. For example, to manage the SeServiceLogonRight privilege for a server named MyServer , create a security group named allow-log-on-service-MyServer and grant membership to all the required service accounts.
Create a group policy object, open it in the editor, and create a new scheduled immediate task:

Select the general tab and configure the task:

- Set the task to run in the NT AUTHORITY\System context.
- Set the task to run whether the user is logged in or not.
- Set the task to run with the highest privileges.
- Set the task to be hidden in the scheduled task console while it is executing.
Select the action tab and configure the task to execute the UserRights.exe utility.

Set the program to the full path to the utility. For example: \\example.com\NETLOGON\UserRights.exe .
Set the arguments to execute the utility in privilege mode, grant the SeServiceLogonRight privilege to a security group corresponding to the servers sAMAccountName value, and remove any other regular user accounts or groups. For example:
privilege SeServiceLogonRight --grant EXAMPLE\allow-log-on-service-%ComputerName% --revoke-pattern "^S-1-5-21"
Select the common tab and enable item level targeting.

Select the targeting button, and configure item level targeting to ensure the preference is only executed when the corresponding Active Directory security exists in the directory.

- Select New Item , then choose LDAP Query .
- Select Item Options , then choose IS .
- Set the filter to (&(objectCategory=group)(name=allow-log-on-service-%ComputerName%))
- Set the binding to LDAP:
- Set the attribute to the same type used in the filter name
The example above uses the groups name attribute type, which may be a better option than sAMAccountName in some environments.
Repeat all the above steps with the following changes to accommodate the case when the directory group does not exist:
Configure the action to execute the UserRights.exe utility with the following arguments:
privilege SeServiceLogonRight --revoke-pattern "^S-1-5-21"
Configure item level targeting to enable the preference when the LDAP query does not return a value.
Granting the privilege to a new user or service account only requires granting membership in the associated directory security group. Servers without a corresponding directory security will only have the user right privilege pruned according to the pattern.
If the privilege is later directly granted to a local or domain user account or group, group policy will revoke the grant. The pattern can be extended to prevent well-known security identifiers for built-in non-privileged contexts as well (use the dry-run flag to verify your regular expression).
Instrumentation
Diagnostic messages are emitted to the console and the Windows application event log.
Events originate from the UserRights source and have the following possible ids:
Manage a Principal
- Grant a privilege and revoke a different privilege from a principal:
- Grant multiple privileges, and revoke any other privileges assigned to a principal:
- Revoke a privilege from a principal:
- Revoke all privileges from a principal:
Manage a Privilege
- Assign a principal, and revoke all other principals matching a pattern (everything except builtin and virtual accounts) from a privilege in dryrun mode to only instrument the changes:
- Revoke all principals matching a pattern (everything except builtin and virtual accounts) from a privilege:
- Assign a principal and revoke a different principal from a privilege:
- Revoke a principal assigned to a privilege:
- Revoke all principals assigned to a privilege:
Enumerate Privileges and Principals
- List all principals and privileges in CSV format to STDOUT :
- List all principals and privileges in JSON format to STDOUT :
- List all principals and privileges in CSV format to a file:
Additional Info
Releases are provided in two formats that both target .Net 8.0:
- An archive containing a runtime-dependent executable and all the required libraries.
- An archive containing a single, self-contained executable to make deployment simple.
Useful Links
- User Rights Assignment
- Well-Known SID Structures
- Regular Expression Language - Quick Reference
Releases 14
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to define the built-in administrators group in a group-policy object?
How do I define the built-in administrators group in a group policy? For example
Do I need to set the string " BUILTIN\Administrators " or just " Administrators "?
What about " LOCAL SERVICE " and " NETWORK SERVICE "?
Do I need to set " NT AUTHORITY\LOCAL SERVICE " or just " LOCAL SERVICE "?
Microsoft documentation is very misleading and incomplete in that respect. Thanks in advance!
- group-policy
Do I need to set the string "BUILTIN\Administrators" or just "Administrators"? What about "LOCAL SERVICE" and "NETWORK SERVICE"? Do I need to set "NT AUTHORITY\LOCAL SERVICE" or just "LOCAL SERVICE"?
You don't need the explicit BUILTIN or NT AUTHORITY at the beginning, as your domain should successfully infer it - there's only one group named Administrators , only one account named LOCAL SERVICE and only one account named NETWORK SERVICE .
For future reference, when in doubt, keep two things in mind:
You can use the Browse -> Check Names GUI options to have the proper object filled in for you.
- If you're building a script based on this, you can then look up the properties, including the SID, of the object that's been filled in.
- As with anything else, when in doubt, specify explicitly or prefer a more qualified/distinguished named over a less qualified/distinguished one.
- Thanks for answering. Some background: I am currently building GPOs based on the CIS security benchmarks. A lot of this checks are failing as the regular expressions are expecting "BUILTIN\Administrators" and "NT AUTHORITY\LOCAL SERVICE" – Matthias Güntert Jul 30, 2014 at 7:48
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged group-policy ..
- The Overflow Blog
- You should keep a developer’s journal
- Would you board a plane safety-tested by GenAI?
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- How to manually set system wide proxy used by gnome-control-center in Ubuntu 22
- Why is "dict[int, int]" incompatible with "dict[int, int | str]"?
- Where is "Corridoio 1 \ Passageway 1" at the Vatican museums?
- Pacman can't run. Can't find libicuuc.so.75
- What flag had a black cross blue field 1589?
- What is a Christian response to the claim that atheists make that "the Bible condones slavery" in Colossians 3:22-25?
- Evidence of lightning-caused mass extinction
- Torus Flow Free
- The flaw in the [rationalism = utopian = socialism] and [empiricism = realism = liberalism] Burkean argument
- Communications "cauldron" in Iain Banks novel
- Can "go into" ever be used to mean "used in" or "made of"?
- Rotating a Pot of Boiling Water on a Stove
- Are "factory methods" anti-pattern now?
- What are those little pieces for on the C27J?
- Regarding a Coin Toss Experiment by Neil DeGrasse Tyson, and its validity
- When did `apt` output change to include "Done" after "Building dependency tree"?
- Unable to :set printoptions for :hardcopy command
- Given the maximum likelihood function- estimate the value of the parameter
- Usage and meaning of “may have” in this context
- Declare a math operator with only lower limit
- Can a crater form inside another crater
- Are transponders sometimes referred to as ‘parrots’?
- Which signals (wifi, mobile phone, gps) can reliably be blocked by aluminum foil
- Old CAAD8 with wh-r550 rear wheel
TechRepublic

TIOBE Index for May 2024: Top 10 Most Popular Programming Languages
Fortran is in the spotlight again in part due to the increased interest in artificial intelligence.

Adobe Adds Firefly and Content Credentials to Bug Bounty Program
Security researchers can earn up to $10,000 for critical vulnerabilities in the generative AI products.

NVIDIA GTC 2024: CEO Jensen Huang’s Predictions About Prompt Engineering
"The job of the computer is to not require C++ to be useful," said Huang at NVIDIA GTC 2024.

White House Recommends Memory-Safe Programming Languages and Security-by-Design
A new report promotes preventing cyberattacks by using memory-safe languages and the development of software safety standards.

How to Hire a Python Developer
Spend less time researching and more time recruiting the ideal Python developer. Find out how in this article.
Latest Articles

Price Drop: Code Faster and More Accurately, Even in Collaboration, for Just $40
Microsoft Visual Studio Professional 2022 for Windows allows you to code with teams across platforms and languages, and offers advanced tools to ensure accuracy. Now at $39.97 through May 31st.

Snowflake Arctic, a New AI LLM for Enterprise Tasks, is Coming to APAC
Data cloud company Snowflake’s Arctic is promising to provide APAC businesses with a true open source large language model they can use to train their own custom enterprise LLMs and inference more economically.

Anthropic’s Generative AI Research Reveals More About How LLMs Affect Security and Bias
Anthropic opened a window into the ‘black box’ where ‘features’ steer a large language model’s output.

Learn How to Code From Novice-Friendly Courses for Just $40 Through 5/31
Learning to code can be so easy with the classes in this bundle; most were designed for novices, and others will take you further when you’re ready.

Microsoft Build 2024: Copilot AI Will Gain ‘Personal Assistant’ and Custom Agent Capabilities
Other announcements included a Snapdragon Dev Kit for Windows, GitHub Copilot Extensions and the general availability of Azure AI Studio.

Learn the Python Programming Language Online for Just $24
Get certified for the most popular language used by software development companies with these ten online training courses. Use code TRA20 at checkout to unlock an extra 20% off its already discounted price.

The Apple Developer Program: What Professionals Need to Know
If you want to develop software for macOS, iOS, tvOS, watchOS or visionOS, read this overview of Apple's Developer Program.

U.K.’s AI Safety Institute Launches Open-Source Testing Platform
Inspect is the first AI safety testing platform created by a state-backed body to be made freely available to the global AI community.

Google I/O 2024: Google Search’s AI Overviews Are Generally Available This Week
Plus, Google reveals plans to unleash Gemini across Workspace to make interpreting long email threads or creating spreadsheets easier.

TIOBE Index News (May 2024): Why is Fortran Popular Again?
The AI boom is starting to show up on the TIOBE Index by bringing back a formative programming language.

Udemy Report: Which IT Skills Are Most in Demand in Q1 2024?
Informatica PowerCenter, Microsoft Playwright and Oracle Database SQL top Udemy’s list of most popular tech courses.

The 10 Best AI Courses in 2024
Today’s options for best AI courses offer a wide variety of hands-on experience with generative AI, machine learning and AI algorithms.

Learn Windows PowerShell for just $17
Streamline your workflow, automate tasks and more with The 2024 Windows PowerShell Certification Bundle.

Llama 3 Cheat Sheet: A Complete Guide for 2024
Learn how to access Meta’s new AI model Llama 3, which sets itself apart by being open to use under a license agreement.
Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Policy CSP - UserRights
- 26 contributors

This CSP contains some settings that are under development and only applicable for Windows Insider Preview builds . These settings are subject to change and may have dependencies on other features or services in preview.
User rights are assigned for user accounts or groups. The name of the policy defines the user right in question, and the values are always users or groups. Values can be represented as Security Identifiers (SID) or strings. For more information, see Well-known SID structures .
Even though strings are supported for well-known accounts and groups, it's better to use SIDs, because strings are localized for different languages. Some user rights allow things like AccessFromNetwork, while others disallow things, like DenyAccessFromNetwork.
General example
Here's an example for setting the user right BackupFilesAndDirectories for Administrators and Authenticated Users groups.
Here are examples of data fields. The encoded 0xF000 is the standard delimiter/separator.
Grant a user right to Administrators group via SID:
Grant a user right to multiple groups (Administrators, Authenticated Users) via SID:
Grant a user right to multiple groups (Administrators, Authenticated Users) via a mix of SID and Strings:
Grant a user right to multiple groups (Authenticated Users, Administrators) via strings:
Empty input indicates that there are no users configured to have that user right:
If you use Intune custom profiles to assign UserRights policies, you must use the CDATA tag ( <![CDATA[...]]> ) to wrap the data fields. You can specify one or more user groups within the CDATA tag by using 0xF000 as the delimiter/separator.
 is the entity encoding of 0xF000 .
For example, the following syntax grants user rights to Authenticated Users and Replicator user groups:
For example, the following syntax grants user rights to two specific Microsoft Entra users from Contoso, user1 and user2:
For example, the following syntax grants user rights to a specific user or group, by using the SID of the account or group:
AccessCredentialManagerAsTrustedCaller
This user right is used by Credential Manager during Backup/Restore. No accounts should've this privilege, as it's only assigned to Winlogon. Users' saved credentials might be compromised if this privilege is given to other entities.
Description framework properties :
Group policy mapping :
AccessFromNetwork
This user right determines which users and groups are allowed to connect to the computer over the network. Remote Desktop Services aren't affected by this user right.
Remote Desktop Services was called Terminal Services in previous versions of Windows Server.
ActAsPartOfTheOperatingSystem
This user right allows a process to impersonate any user without authentication. The process can therefore gain access to the same local resources as that user. Processes that require this privilege should use the LocalSystem account, which already includes this privilege, rather than using a separate user account with this privilege specially assigned.
Assigning this user right can be a security risk. Only assign this user right to trusted users.
AdjustMemoryQuotasForProcess
Adjust memory quotas for a process - This privilege determines who can change the maximum memory that can be consumed by a process. This privilege is useful for system tuning on a group or user basis.
AllowLocalLogOn
This user right determines which users can log on to the computer.
Modifying this setting may affect compatibility with clients, services, and applications. For compatibility information about this setting, see Allow log on locally ( https://go.microsoft.com/fwlink/?LinkId=24268 ) at the Microsoft website.
AllowLogOnThroughRemoteDesktop
Allow log on through Remote Desktop Services - This policy setting determines which users or groups can access the sign-in screen of a remote device through a Remote Desktop Services connection.
BackupFilesAndDirectories
This user right determines which users can bypass file, directory, registry, and other persistent objects permissions when backing up files and directories. Specifically, this user right is similar to granting the following permissions to the user or group in question on all files and folders on the system:Traverse Folder/Execute File, Read.
Assigning this user right can be a security risk. Since users with this user right can read any registry settings and files, only assign this user right to trusted users.
BypassTraverseChecking
This user right determines which users can traverse directory trees even though the user may not have permissions on the traversed directory. This privilege doesn't allow the user to list the contents of a directory, only to traverse directories.
ChangeSystemTime
This user right determines which users and groups can change the time and date on the internal clock of the computer. Users that are assigned this user right can affect the appearance of event logs. If the system time is changed, events that are logged will reflect this new time, not the actual time that the events occurred.
When you configure user rights, it replaces existing users or groups that were previously assigned to those user rights. The system requires that the Local Service account (SID S-1-5-19 ) always has the ChangeSystemTime right. Always specify Local Service , in addition to any other accounts that you need to configure in this policy.
If you don't include the Local Service account, the request fails with the following error:
ChangeTimeZone
This user right determines which users and groups can change the time zone used by the computer for displaying the local time, which is the computer's system time plus the time zone offset. System time itself is absolute and isn't affected by a change in the time zone.
CreateGlobalObjects
This security setting determines whether users can create global objects that are available to all sessions. Users can still create objects that are specific to their own session if they don't have this user right. Users who can create global objects could affect processes that run under other users' sessions, which could lead to application failure or data corruption.
Assigning this user right can be a security risk. Assign this user right only to trusted users.
CreatePageFile
This user right determines which users and groups can call an internal application programming interface (API) to create and change the size of a page file. This user right is used internally by the operating system and usually doesn't need to be assigned to any users.
CreatePermanentSharedObjects
This user right determines which accounts can be used by processes to create a directory object using the object manager. This user right is used internally by the operating system and is useful to kernel-mode components that extend the object namespace. Because components that are running in kernel mode already have this user right assigned to them, it isn't necessary to specifically assign it.
CreateSymbolicLinks
This user right determines if the user can create a symbolic link from the computer he is logged-on to.
This privilege should only be given to trusted users. Symbolic links can expose security vulnerabilities in applications that aren't designed to handle them.
This setting can be used in conjunction a symlink filesystem setting that can be manipulated with the command line utility to control the kinds of symlinks that are allowed on the machine. Type 'fsutil behavior set symlinkevaluation /?' at the command line to get more information about fsutil and symbolic links.
CreateToken
This user right determines which accounts can be used by processes to create a token that can then be used to get access to any local resources when the process uses an internal application programming interface (API) to create an access token. This user right is used internally by the operating system. Unless it's necessary, don't assign this user right to a user, group, or process other than Local System.
Assigning this user right can be a security risk. Don't assign this user right to any user, group, or process that you don't want to take over the system.
DebugPrograms
This user right determines which users can attach a debugger to any process or to the kernel. Developers who are debugging their own applications don't need to be assigned this user right. Developers who are debugging new system components will need this user right to be able to do so. This user right provides complete access to sensitive and critical operating system components.
DenyAccessFromNetwork
This user right determines which users are prevented from accessing a computer over the network. This policy setting supersedes the Access this computer from the network policy setting if a user account is subject to both policies.
DenyLocalLogOn
This security setting determines which service accounts are prevented from registering a process as a service.
This security setting doesn't apply to the System, Local Service, or Network Service accounts.
DenyLogOnAsBatchJob
This security setting determines which accounts are prevented from being able to log on as a batch job. This policy setting supersedes the Log on as a batch job policy setting if a user account is subject to both policies.
DenyLogOnAsService
Deny log on as a service -This security setting determines which service accounts are prevented from registering a process as a service. This policy setting supersedes the Log on as a service policy setting if an account is subject to both policies.
This security setting doesn't apply to the System, Local Service, or Network Service accounts. Default: None.
DenyRemoteDesktopServicesLogOn
This user right determines which users and groups are prohibited from logging on as a Remote Desktop Services client.
EnableDelegation
This user right determines which users can set the Trusted for Delegation setting on a user or computer object. The user or object that's granted this privilege must have write access to the account control flags on the user or computer object. A server process running on a computer (or under a user context) that's trusted for delegation can access resources on another computer using delegated credentials of a client, as long as the client account doesn't have the Account can't be delegated account control flag set.
Misuse of this user right, or of the Trusted for Delegation setting, could make the network vulnerable to sophisticated attacks using Trojan horse programs that impersonate incoming clients and use their credentials to gain access to network resources.
GenerateSecurityAudits
This user right determines which accounts can be used by a process to add entries to the security log. The security log is used to trace unauthorized system access. Misuse of this user right can result in the generation of many auditing events, potentially hiding evidence of an attack or causing a denial of service. Shut down system immediately if unable to log security audits security policy setting is enabled.
ImpersonateClient
Assigning this user right to a user allows programs running on behalf of that user to impersonate a client. Requiring this user right for this kind of impersonation prevents an unauthorized user from convincing a client to connect (for example, by remote procedure call (RPC) or named pipes) to a service that they've created and then impersonating that client, which can elevate the unauthorized user's permissions to administrative or system levels.
By default, services that are started by the Service Control Manager have the built-in Service group added to their access tokens. Component Object Model (COM) servers that are started by the COM infrastructure and that are configured to run under a specific account also have the Service group added to their access tokens. As a result, these services get this user right when they're started. In addition, a user can also impersonate an access token if any of the following conditions exist. 1) The access token that's being impersonated is for this user. 2) The user, in this logon session, created the access token by logging on to the network with explicit credentials. 3) The requested level is less than Impersonate, such as Anonymous or Identify. Because of these factors, users don't usually need this user right.
If you enable this setting, programs that previously had the Impersonate privilege may lose it, and they may not run.
IncreaseProcessWorkingSet
Increase a process working set. This privilege determines which user accounts can increase or decrease the size of a process's working set. The working set of a process is the set of memory pages currently visible to the process in physical RAM memory. These pages are resident and available for an application to use without triggering a page fault. The minimum and maximum working set sizes affect the virtual memory paging behavior of a process.
Increasing the working set size for a process decreases the amount of physical memory available to the rest of the system.
IncreaseSchedulingPriority
This user right determines which accounts can use a process with Write Property access to another process to increase the execution priority assigned to the other process. A user with this privilege can change the scheduling priority of a process through the Task Manager user interface.
If you remove Window Manager\Window Manager Group from the Increase scheduling priority user right, certain applications and computers won't function correctly. In particular, the INK workspace doesn't function correctly on unified memory architecture (UMA) laptop and desktop computers that run Windows 10, version 1903 or later and that use the Intel GFX driver.
On affected computers, the display blinks when users draw on INK workspaces such as those that are used by Microsoft Edge, Microsoft PowerPoint, or Microsoft OneNote. The blinking occurs because the inking-related processes repeatedly try to use the Real-Time priority, but are denied permission.
LoadUnloadDeviceDrivers
This user right determines which users can dynamically load and unload device drivers or other code in to kernel mode. This user right doesn't apply to Plug and Play device drivers. It's recommended that you don't assign this privilege to other users.
This user right determines which accounts can use a process to keep data in physical memory, which prevents the system from paging the data to virtual memory on disk. Exercising this privilege could significantly affect system performance by decreasing the amount of available random access memory (RAM).
LogOnAsBatchJob
This security setting allows a user to be logged-on by means of a batch-queue facility and is provided only for compatibility with older versions of Windows. For example, when a user submits a job by means of the task scheduler, the task scheduler logs that user on as a batch user rather than as an interactive user.
LogOnAsService
This security setting allows a security principal to log on as a service. Services can be configured to run under the Local System, Local Service, or Network Service accounts, which have a built in right to log on as a service. Any service that runs under a separate user account must be assigned the right.
ManageAuditingAndSecurityLog
This user right determines which users can specify object access auditing options for individual resources, such as files, Active Directory objects, and registry keys. This security setting doesn't allow a user to enable file and object access auditing in general. You can view audited events in the security log of the Event Viewer. A user with this privilege can also view and clear the security log.
ManageVolume
This user right determines which users and groups can run maintenance tasks on a volume, such as remote defragmentation. Use caution when assigning this user right. Users with this user right can explore disks and extend files in to memory that contains other data. When the extended files are opened, the user might be able to read and modify the acquired data.
ModifyFirmwareEnvironment
This user right determines who can modify firmware environment values. Firmware environment variables are settings stored in the nonvolatile RAM of non-x86-based computers. The effect of the setting depends on the processor. On x86-based computers, the only firmware environment value that can be modified by assigning this user right is the Last Known Good Configuration setting, which should only be modified by the system. On Itanium-based computers, boot information is stored in nonvolatile RAM. Users must be assigned this user right to run bootcfg.exe and to change the Default Operating System setting on Startup and Recovery in System Properties. On all computers, this user right is required to install or upgrade Windows.
This security setting doesn't affect who can modify the system environment variables and user environment variables that are displayed on the Advanced tab of System Properties.
ModifyObjectLabel
This user right determines which user accounts can modify the integrity label of objects, such as files, registry keys, or processes owned by other users. Processes running under a user account can modify the label of an object owned by that user to a lower level without this privilege.
ProfileSingleProcess
This user right determines which users can use performance monitoring tools to monitor the performance of system processes.
ProfileSystemPerformance
This security setting determines which users can use performance monitoring tools to monitor the performance of system processes.
RemoteShutdown
This user right determines which users are allowed to shut down a computer from a remote location on the network. Misuse of this user right can result in a denial of service.
ReplaceProcessLevelToken
This security setting determines which user accounts can call the CreateProcessAsUser() application programming interface (API) so that one service can start another. An example of a process that uses this user right is Task Scheduler. For information about Task Scheduler, see Task Scheduler overview.
RestoreFilesAndDirectories
This user right determines which users can bypass file, directory, registry, and other persistent objects permissions when restoring backed up files and directories, and determines which users can set any valid security principal as the owner of an object. Specifically, this user right is similar to granting the following permissions to the user or group in question on all files and folders on the system:Traverse Folder/Execute File, Write.
Assigning this user right can be a security risk. Since users with this user right can overwrite registry settings, hide data, and gain ownership of system objects, only assign this user right to trusted users.
ShutDownTheSystem
This security setting determines which users who are logged-on locally to the computer can shut down the operating system using the Shut Down command. Misuse of this user right can result in a denial of service.
TakeOwnership
This user right determines which users can take ownership of any securable object in the system, including Active Directory objects, files and folders, printers, registry keys, processes, and threads.
Assigning this user right can be a security risk. Since owners of objects have full control of them, only assign this user right to trusted users.
Related articles
Policy configuration service provider
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

COMMENTS
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
Logon rights control who is authorized to log on to a device and how they can log on. User rights permissions control access to computer and domain resources, and they can override permissions that have been set on specific objects. User rights are managed in Group Policy under the User Rights Assignment item.
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
In the console tree, click Computer Configuration, select Windows Settings, and then select Security Settings. Do one of the following: Select Account Policies to edit the Password Policy or Account Lockout Policy. Select Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. In the details pane, double-click the ...
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
User Rights Assignment. Specify the users or groups that have sign-in rights or privileges on a device ... within AD DS that enables directory-based configuration management of user and computer settings on devices running Windows Server. By using Group Policy, you can define configurations for groups of users and computers, including policy ...
To centrally control user rights assignments on computers throughout your domain use group policy. Logon rights; Admin equivalent rights; Tracking user rights with the security log; User rights in-depth; Access this computer from the network; Act as part of the operating system; Add workstations to domain; Adjust memory quotas for a process ...
C) Open the ntrights.zip file, copy or move the ntrights.exe file into your C:\Windows\System32 folder, and click/tap on Continue to approve. 2 Open an elevated command prompt. 3 Type the command you want below into the elevated command prompt, and press Enter. (Add user or group to allow) ntrights +r SeRemoteInteractiveLogonRight -u " User or ...
In my previous post,Windows Server security features and best practices, I introduced the built-in features that can be used to increase your organization's security. Today, I will focus on one of the main security mechanisms in Windows: security policy settings, specifically local policies/user rights assignment, in Windows Server 2016.
If you're asking for User Rights Assignment on a single computer, look for Local Security Policy. If you're asking for User Rights Assignment as a group policy, well, it shows up just fine in my console. Are you using RSAT (Remote Server Administration Tools)? I'm using the RSAT available for Windows 10.
You cannot edit this User Rights Assignment policy because this setting is being managed by a domain-based Group Policy. In this case, the domain Group Policy setting has precedence and you are prevented from modifying the policy via Local Group Policy. To modify this policy, either: Modify the policy in the applicable domain Group Policy Object.
You must apply your own "default" settings. If you only have a few User Rights to modify, edit the settings through the Local Group Policy editor ( gpedit.msc) and refer to another workstation that has the desired rights assignments for your configuration. If you have many User Rights to modify, then consider using the Secedit command-line tool ...
How to apply settings to specific user with Group Policy. Use the "Windows key + R" keyboard shortcut to open the Run command. Type MMC and click the OK button. Open the File menu and select the ...
I want to edit security settings of user rights assignment of local security policy using powershell or cmd. Eg: policy = "change the system time". default_security_settings = "local service,Administrators". i want to remove everything except Administrators. i have tried ntrights command, but seems like not working Any command will be appreciated.
Navigate to Security Settings → Local Policies → User Rights Assignments and double-click the " Log on as a service " policy. Click Add User or Group. Note. The "NT SERVICESERVICES" group is added to the " Log on as a service " policy by default on Windows Server 2016, Windows 10, and later. Specify the groups or users (domain ...
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
Enable the group policy User Right Assignment for the SeServiceLogonRight right: Add any required local users. Add any required local groups. Add any required virtual accounts. Add any required NT service accounts. Add the new local group created above, allow-log-on-service. Link the policy and configure the security and filtering as required.
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. Group Policy. Settings are applied in the following order through a Group Policy Object (GPO), which will overwrite settings on the local computer at the next Group Policy update: Local policy settings; Site policy settings
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Change the system time policy in the right pane. (see screenshot below) 3 Click/tap on the Add ...
5. How do I define the built-in administrators group in a group policy? For example. Computer Configuration => Policies => Windows Settings => Security Options => Local Policies => User Rights Assignment => Adjust memory quotas for a process. Do I need to set the string " BUILTIN\Administrators " or just " Administrators "?
Open the Group Policy Management Console. Right-click the domain or the required subfolder to create a new GPO, or select an existing one. On the GPO, right-click and select Edit to open the Group ...
Manual steps: Open Group Policy Management. Navigate to the following path in the Group Policy Object. Select Policy. Right click & Edit: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Add/remove the necessary users. Windows. Active Directory.
Microsoft Windows is a product line of proprietary graphical operating systems developed and marketed by Microsoft.It is grouped into families and sub-families that cater to particular sectors of the computing industry - Windows (unqualified) for a consumer or corporate workstation, Windows Server for a server and Windows IoT for an embedded system. ...
Developer TR Academy Learn the Python Programming Language Online for Just $24 . Get certified for the most popular language used by software development companies with these ten online training ...
User rights are assigned for user accounts or groups. The name of the policy defines the user right in question, and the values are always users or groups. Values can be represented as Security Identifiers (SID) or strings. For more information, see Well-known SID structures.