An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Healthcare (Basel)


Healthcare Data Breaches: Insights and Implications
Adil hussain seh.
1 Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow 226025, India; moc.liamg@niassuhlidaa (A.H.S.); moc.liamg@rakraslama (A.K.S.); ni.oc.oohay@umjsc_akla (A.A.); moc.oohay@seearnahk (R.A.K.)
Mohammad Zarour
2 College of Computer & Information Sciences, Prince Sultan University, Riyadh 12435, Saudi Arabia; as.ude.usp@ruorazm (M.Z.); as.ude.usp@izenelam (M.A.)
Mamdouh Alenezi
Amal krishna sarkar.
3 System Manager, Sanjay Gandhi Post Graduate Institute of Medical Sciences, Lucknow 226014, India
Alka Agrawal
Rajeev kumar, raees ahmad khan.
The Internet of Medical Things, Smart Devices, Information Systems, and Cloud Services have led to a digital transformation of the healthcare industry. Digital healthcare services have paved the way for easier and more accessible treatment, thus making our lives far more comfortable. However, the present day healthcare industry has also become the main victim of external as well as internal attacks. Data breaches are not just a concern and complication for security experts; they also affect clients, stakeholders, organizations, and businesses. Though the data breaches are of different types, their impact is almost always the same. This study provides insights into the various categories of data breaches faced by different organizations. The main objective is to do an in-depth analysis of healthcare data breaches and draw inferences from them, thereby using the findings to improve healthcare data confidentiality. The study found that hacking/IT incidents are the most prevalent forms of attack behind healthcare data breaches, followed by unauthorized internal disclosures. The frequency of healthcare data breaches, magnitude of exposed records, and financial losses due to breached records are increasing rapidly. Data from the healthcare industry is regarded as being highly valuable. This has become a major lure for the misappropriation and pilferage of healthcare data. Addressing this anomaly, the present study employs the simple moving average method and the simple exponential soothing method of time series analysis to examine the trend of healthcare data breaches and their cost. Of the two methods, the simple moving average method provided more reliable forecasting results.
1. Introduction
Advances in information and communication technology have helped the healthcare industry to replace paper-based systems with electronic health record (EHRs) systems to provide better and more cost-effective services to its customers. EHRs enhance patient care, develop patient cooperation, enhance disease diagnosis, improve practice efficiency, and make patient health information accessible all the time [ 1 ]. Additionally, smartphones and other web-based smart devices have changed the way we communicate. These devices empower users to easily and conveniently access the online services provided by different organizations. Healthcare is one among them. The last few years have seen healthcare data become more digitized, distributed, and mobile [ 2 ]. The Internet of Medical Things (IOMT) has also played a vital role in this context. Sensitive data are collected by healthcare organizations from their customers and stored on network servers to make them accessible all the time, and to facilitate patient care, but unfortunately, every blessing has a curse, which also applies here. The use of smartphones and other smart devices has also become a key source of privacy breaches [ 3 ]. Due to software vulnerabilities, security failures, and human error, these databases are sometimes accessed by unauthorized users. This leads to the exposure of sensitive data in the form of data breaches. Sometimes, insider attackers cause damage to protected health information, which results in the loss, theft, or disclosure of sensitive healthcare data. The price of a complete record file of a single patient can be hundreds of dollars on the dark web [ 4 ]. In comparison to other data industries, the healthcare industry is among the worst affected [ 5 ].
As reported by many practitioners, from 2005 to 2019, the total number of individuals affected by healthcare data breaches was 249.09 million. Out of these, 157.40 million individuals were affected in the last five years alone [ 6 ]. In the year 2018, the number of data breaches reported was 2216 from 65 countries. Out of these, the healthcare industry faced 536 breaches. This implies that the healthcare industry has faced the highest number of breaches among all industries [ 7 ]. There were 2013 data breaches reported from 86 countries in the year 2019 [ 8 ]. The total number of healthcare records that were exposed, stolen, or illegally disclosed in the year 2019 was 41.2 million in 505 healthcare data breaches [ 8 ]. According to an IBM report, the average cost of a data breach in 2019 was $3.92 million, while a healthcare industry breach typically costs $6.45 million [ 9 ]. This cost was the highest in the USA compared to other countries. Usually, a data breach would fetch $8.19 million. However, the average cost of a healthcare data breach (average breach size 25,575 records) in the USA is $15 million [ 10 ]. The average cost of a data breach increased by 12% from 2014 to 2019, and the average cost of a breached record increased 3.4% in the same time period. Moreover, the cost of a breached record in the healthcare sector registered an increase of 19.4%, the highest in this time period [ 10 , 11 , 12 , 13 ].
The aforementioned facts and figures show that the data assets of individuals and organizations are at risk. Even more alarmingly, the healthcare industry in particular is being targeted by attackers, and is therefore the most vulnerable. Thus, data privacy and confidentiality has become a serious concern for both individuals and organizations. Healthcare data are more sensitive than other types of data because any data tampering can lead to faulty treatment, with fatal and irreversible losses to patients. Hence, healthcare data need enhanced security, and should be breach-proof. In this study, our main concern was to investigate the healthcare data breaches reported or published by different eminent and authentic sources. We aimed to examine the causes of these breaches and use the results to improve healthcare data confidentiality. The analyzed factors that lead to healthcare data breaches will be addressed in our future research work to improve healthcare data confidentiality.
The rest of this study is divided into the following sections. The Section 2 defines the adopted methodology. The Section 3 provides information about the data sources. The Section 4 frames the analysis of data breaches, providing insights into the data breaches which are pertinent to healthcare. The Section 5 depicts the forecasting of healthcare data breaches. The Section 6 provides a discussion and the summarized results of this work, and the Section 7 chronicles the conclusion of the work.
2. Adopted Methodology
The sole aim of this study was to examine and investigate healthcare data breaches. This investigation was intended to provide insights into the causes and consequences of these occurrences on individuals and organizations. To this end, the authors analyzed different eminent and authentic data sources that included the Privacy Rights Clearinghouse (PRC), Health Insurance Portability and Accountability Act (HIPAA) journals, the Office for Civil Rights (OCR) Department of Health and Human Services (HSS.Gov.) USA, Ponemon Institute reports on data breach costs, and Verizon Data Breach Investigations Reports (Verizon-DBIR). In the next section, we briefly discuss these sources. The format of the data analysis method that was adopted in this study can be enumerated in the following steps:
- First, data are compiled from the sources mentioned above and presented in tabular form.
- Second, then sum, percentage, and average methods are applied to this data, and different types of patterns are extracted.
- Third, these patterns will help us to understand the sources and consequences of healthcare data breaches, the rise and downfall of data breaches, the behavior of different types of attacks, and other important things that are discussed in analysis section of this study.
- Fourth, a time series analysis is applied for healthcare data breach forecasting.
3. Data Sources
The data for the present research endeavor was obtained from the following sources:
PRC Database: PRC is a US based, non-profit organization established by Beth Givens in 1992. Its main purpose is to protect consumer information, to provide consumer advocacy services and guidelines to control personal information, and to improve consumer awareness about the technological effects of personal privacy. It provides a complete database of data breaches. The database has a record of 9016 data breach instances reported by different organizations. According to the PRC database, more than 10 billion user records have been compromised since 2005.
HIPAA Journal: The HIPAA journal is an effective outcome of the HIPAA Act 1996. It is a US-based journal that provides comprehensive information about healthcare data breaches, guidelines for HIPAA compliance, and practical guidelines for data breach avoidance. It has been providing comprehensive information about healthcare data breaches since September 2009.
OCR Reports: The Office for Civil Rights Department of Health and Human Services of the USA also provides yearly/bi-yearly or tri-yearly data breach reports, named, “Report to Congress on Breaches of Unsecured Protected Health Information”. These reports provide comprehensive information about healthcare data breaches from 2009 to 2017 [ 14 , 15 ].
Ponemon Institute Reports: The Ponemon Institute is an eminent research institute that mainly focuses on the protection of data, privacy, and security of information issues and policies. It was established in 2002 in Michigan by Dr. L. Ponemon. The institute’s reports are a repository of authentic records on data breach costs, sponsored by IBM.
Verizon-DBIR: Data breach investigation reports by Verizon Enterprises comprise yearly investigations reports on data breaches. The first such report was published in 2008. The reports record instances of data invasion in private as well as public organizations across the world.
All these are globally accepted sources of eminent and authentic data on data breaches.
For this research endeavor, we have premised our analysis on the sources that are mentioned above to examine healthcare data breaches and their causes and consequences. These sources have enabled us to garner an in-depth understanding of patterns in data breaches, and have facilitated our research on mapping the implications.
4. Analysis of Data Breaches
Generally, a data breach is an illegal disclosure or use of information without authorization. The United States Department of Health and Human Services defines a data breach as “the illegal use or disclosure of confidential health information that compromises the privacy or security of it under the privacy rule that poses a sufficient risk of financial, reputational, or other type of harm to the affected person” [ 11 ]. The HIPAA definition of a data breach is “the procurement, access, use or expose of confidential health information illegitimately, which compromises the privacy or security of that confidential health information” [ 14 ].
Data breaches can harm individuals and organizations in several ways. Besides the huge financial setback that organizations have to deal with in cases of data pilferage, such instances also dent the image of the organizations, marring their reputation and brand value. Data breaches are usually classified into two major categories: internal and external. Internal data breaches comprise incidents that are occur with the help of an internal agent. These may be privilege abuse, inauthentic access/disclosure, improper disposal of unnecessary but sensitive data, loss or theft, or the unintentional sharing of confidential data to an unauthorized party. External data breaches are incidents caused by any external entity or source. These include any hacking/IT incident such as a malware attack, ransomware attack, phishing, spyware, or fraud in the form of stolen cards, etc.
The Privacy Rights Clearinghouse (PRC), a nonprofit organization based in the USA, reported that there were 9016 data breach instances in different sectors from January 2005 to October 2019. The total number of records exposed in these breaches was more than 10 billion (10,376,741,867) [ 6 ]. The different types of attacks used to breach the information were Intentional Insider Attacks (INSD), Frauds Using Cards (CARD), Physical Damage such as the theft or loss of paper documents (PHYS), Damage of Portable Device such as lost or theft (PORT), Hacking or Malicious Attacks (HACK), Stationary Computer Loss (STAT), Unknown Approaches (UNKN), and Unintentional Disclosure (DISC). The organizations that were affected by these data breaches may be classified into the following categories:
Some data breach incidents corresponding to each sector have been reported in the PRC database. Since in these intrusions, no records were breached, the authors have not included those numbers in their reference on the representation of data breaches by sector. After an exhaustive analysis of the PRC database, the compiled information was tabulated in Table 1 .
Representation of Data Breaches by Sector.
EDU: Educational Organizations; BSF: Businesses-Financial; BSO: Businesses-Other; BSR: Business-Retail Includes Online Retail; MED: Healthcare Service Providers; GOV: Government and Defense Institutes; NGO: Non-Governmental Organizations.
Table 1 presents information on data breach incidents by sector in two scenarios. The first scenario is a collation of the breach episodes that have occurred in the last 15 years. The second scenario, which is the core focus of our study, records the breach episodes that occurred in the healthcare industry in the last 5 years. A comparative analysis of the two scenarios clearly reveals that the healthcare industry is most susceptible to data pilfering.
A thorough analysis of the entire 15-year timeframe shows that the healthcare (MED) sector in both the time frames from (2005 to 2019) and (2015 to 2019) has faced the highest number of data breaches. Out of the 6355 breach incidents reported during 2005–2019, 3912 were recorded in the healthcare industry alone. This accounts for 61.55% of the total. The MED sector is followed by the EDU and GOV sectors, which account for 10.55% and 8.82%, respectively. Out of the 3912 incidents that the healthcare industry faced, 1587 were carried out in the last five years (2015 to 2019), comprising 40.56% of the total healthcare data breaches. This is cause for great alarm, and calls for immediate remedial action.
In the second case, from 2015 to 2019, there were a total of 2027 data breach incidents faced among the specified sectors. Out of these 2079 incidents, 1587 were recorded in the healthcare (MED) sector, which is 76.59% of the total. The MED sector is followed by the BSF sector, with a share of 9.36%. However, the other sectors show a small decrease in incidents. The data clearly shows that the healthcare industry has become the main victim of data breaches. Moreover, the rate of healthcare data breaches has increased even more rapidly in the last five years.
Figure 1 presents a graphical representation of Table 1 . The figure shows that the slope of the graph in each sector has witnessed a decrease in the second case (2015–2019), except in the MED sector, followed by the BSF sector. The graph indicates that the healthcare industry is the preferred target of attackers because of the high commercial value of EHRs.

Representation of Data Breach Incidents.
4.1. Healthcare Data Breach Analysis
Generally, healthcare data breaches can be defined as “illegitimate access or disclosure of the protected health information that compromises the privacy and security of it”. To analyze healthcare data breaches, the authors investigated the MED domain of the PRC database thoroughly [ 6 ]. Table 2 provides information about healthcare data breaches reported by PRC. In this table, the data has been presented in two different scenarios. In the first scenario, data is presented as whole from 2005 to 2019. In the second scenario, we presented the data in three clusters, i.e., from 2005 to 2009, 2010 to 2014, and 2015 to 2019. The objective of data clustering is to detect changes in the trends of healthcare data breaches with the passage of time.
Types of Attacks on MED Sector and Number of Individuals Affected.
HACK: Hacking or Malicious Attacks; INSD: Intentional Insider Attacks; PHYS: Physical Damage such as the theft or loss of paper documents; PORT: Damage of Portable Device such as lost or theft; STAT: Stationary Computer Loss; UNKN: Unknown Approaches.
Analysis of Table 2 shows that 249.09 million people were the victims of healthcare data breach episodes. From 2005 to 2009, 13.49 million Health Records were exposed, i.e., 5.41% of the total number of cases. In the period from 2010 to 2014, 78.18 million records were exposed; this makes up 31.38% of the total. From 2015 to 2019, 157.40 million records were exposed, that is, 63.19% of the total. In addition, out of 249.09 million records, 161.05 were exposed through hacking attacks that comprised 64.65% of the total exposed health records from 2005 to 2019. An interesting pattern that can be detected here is that:
- In first cluster of five years (2005 to 2009), only 0.6 million records were exposed through hacking.
- In the second cluster of five years (2010–2014), 14.70 million records were exposed through hacking.
- In the third cluster of five years (2015–2019), 145.75 million records were exposed.
Thus, it is evident that the healthcare industry has been inundated by hackers in the last five years, compromising 90.49% of health records during this time period.
This analysis places the healthcare industry in a very vulnerable position. Yet another facet to note is the types of attacks employed for data breaches. Other than HACK attacks, the healthcare sector has also been targeted by PHYS and PORT attacks. Reports state that 14.39% of PHYS attacks and 9.51% of PORT attacks were engineered from 2005 to 2019. But in last five years (2015 to 2019), a significant decline has been recorded in the numbers of HACK and PHYS attacks. Only 1.75% of reported attacks from 2015–2019 were HACK, and as few as 0.25% were PHYS. The highest number of data breaches from 2005 to 2019 was in the form of DISK type attacks. There were as many as 1019 DISK attacks out of a total of 3912 data breach incidents, comprising 26.04% of the total. However, these attacks only succeeded in exposing 13.77 million records.
Figure 2 and Figure 3 depict the proportion of records exposed with each type of attack, given in percentages, from 2005 to 2019 and 2015 to 2019, respectively. Both figures show that hacking is the main cause behind the exposure of highly sensitive health records. The figure also shows an abrupt increase in hacking incidents in the same time zone.

Proportion of Records Exposed From 2005–2019 with Different Types of Attack.

Proportion of Records Exposed from 2015–2019 with Different Types of Attack.
Furthermore, Figure 2 and Figure 3 show that the INSD (Intentional Insider Attacks) and UNKN (Unknown Approach)-type attacks have the least effect on the healthcare industry. INSD and UNKN were responsible for only 0.5% and 1.36%, respectively, of the total number of exposed records from 2005 to 2019. The type of attacks that have shown a rapid decrease in the last five years (2015–2019) are PHYS, from 14.39% to 2.78%, PORT, from 9.52% to 0.4%, and STAT, (Stationary Computer Loss) from 4.04% to 0.0006%.
CARD (Fraud involving Debit and Credit Cards) is a type of attack mentioned in the OCR database specifications, but we could not confirm any such data breaches. Hence, we have not included CARD in our analysis. Cyber-attacks are carried out to disrupt computer server systems, and in our study, we have bracketed them under the umbrella of Hacking/IT incidents.
4.2. HIPAA and OCR Data Breach Report Analysis
The authors of this study have also compiled the data of healthcare breaches published by the HIPAA journal from 2010 to 2019. The data were outsourced and analyzed from different monthly, yearly, and other reports published by HIPAA. It is not possible to provide references of every HIPAA journal report that we referred to in compiling the data; therefore, we have only cited the main references of the journal reports. These references authenticate our data. The data are presented in Table 3 [ 8 , 16 , 17 ]. We found quantitative variations in some reports while compiling the same data, e.g., the number of data breaches reported in 2014 was 307 in one HIPAA report and 314 in another. In such contradictory cases, we opted to take the data from the latest report.
HIPAA Reported Healthcare Data Breaches.
In Table 4 , we present the compiled data of different reports generated by the Office for Civil Rights with the title name “Report to Congress on Breaches of Unsecured Protected Health Information” from 2010 to 2017. The OCR data breach reports for the years 2018 and 2019 have not been published by the OCR yet [ 15 ].
Reported Healthcare Data Breaches.
To check the accuracy and consistency of the data, we compared it only with the compiled data of HIPAA and OCR reports from 2009 to 2017 because of the unavailability of OCR data for 2018–2019. A comparative study of the HIPAA and OCR data breach reports shows a small variation in number of breaches recorded each year and the number of exposed records from these breaches. The total number of breaches reported by HIPAA from 2010 to 2017 was 2163, and the total number of records exposed from these breaches was 180.65 million, while the total number of breaches reported by the OCR for the same period was 2244, and the total number of records exposed from these breaches was 180.6 million. The HIPPA and OCR data note that the highest number of data breaches was reported in 2017, whereas the highest number of records was exposed in 2015.
The data analysis in Table 3 and Table 4 shows that the healthcare sector saw a mercurial rise in data breach cases in 2015, when more than 40% of the health records were exposed. After 2015, the maximum number of health records was exposed in the 2019. The number of cases accounted for 16.14% of the total of 255.18 million exposed health records from 2010 to 2019. The compiled data also shows that the number of healthcare data breach cases was considerably less in the 2017, when only 5.1 or 5.7 million records were breached. An overall analysis indicates that the data breach trend started to show an abrupt increase from the year 2014.
4.2.1. Data Disclosure Types
A comprehensive analysis was carried out on HIPAA data breach reports. It was found that the main disclosure types of protected healthcare information were hacking incidents, unauthorized access (internal), theft or loss, and improper disposal of unnecessary data. The procedure that we discussed in Section 4.2 for references [ 8 , 17 , 18 ] is also followed in this context. The different disclosure types mentioned above are briefly explained below:
Hacking Incidents: Hacking incidents comprise all cyber-attacks that are used to gain unauthorized access to confidential data. Ransomware and malware are the main approaches that are used to expose protected health information [ 8 , 17 ].
Unauthorized Access (internal): These includes all types of attacks that lead to the exposure of confidential health data with the help of any internal source of an organization. This may be abuse of privileges, unauthenticated access/disclosure, etc.
Theft or loss: This comprises all incidents that lead to the disclosure of protected health information in the form theft or loss, such as the theft of hard disks, laptops, or any other portable device that contains protected healthcare data. This can also be because of catastrophic damage or the loss of these devices.
Improper disposal of unnecessary data: Unnecessary but sensitive and confidential data should be properly disposed of so that it cannot later be retrieved. Improper disposal of this data can lead to the disclosure of protected health information. Improper disposal attack type includes all breached incidents that are caused by the improper disposal of unnecessary but sensitive and confidential health data.
Table 5 presents detailed information about the number of healthcare data breach incidents carried out with these disclosure types.
Type of Healthcare Data Breaches.
In this table, we present the number of breach incidents executed by a particular disclosure type from 2010 to 2019. As per the table, the following facts can be underscored:
- From 2010 to 2019, a total of 2860 breached incidents were carried out through the aforementioned disclosure types.
- 29.72% of breach instances were due to separately hacking/ IT incidents.
- 29.47% of breach instances were due to internal unauthorized disclosures.
- 37.65% of instances were due to theft/loss cases.
- 3.14% of instances occurred due to the improper disposal of unnecessary but sensitive data.
- The overall results show that theft/loss cases are the highest in number, followed by Hacking/IT incidents and unauthorized internal disclosure, while there are very few cases of improper disposal in the ten-year period.
- When we analyzed the pattern over the last four years, we found an abrupt increase in hacking/IT incidents. Out of the 850 hacking/IT incidents reported in ten years (2010–2019) period, 692 incidents were reported in the last four years alone (2016–2019); that accounts for 81.85% of the total, among which 32.23% were reported in 2019 alone.
Thus, this analysis clearly depicts that hacking and other IT-related attacks have become a serious concern for the healthcare data industry. Unauthorized access/ internal disclosure have also shown an increase in the last few years, but not as fast as hacking incidents. Out of the total of 843 unauthorized internal disclosure incidents, 542 were reported in the last four years. This figure comprises 64.29% of the total, and out of this, 16.84% incidents were reported in 2019. A comparison of this proportion (16.84%) with last year (2019) shows that hacking incidents increased by 32.23%. This is double the number of unauthorized internal disclosure incidents. Here, we also found how hacking incidents became more frequent and became a severe concern for the healthcare sector.
On the other hand, theft/loss and improper disposal have shown a clear decrease in the last four years. Out of a total of 1077 theft/loss incidents, only 257 were reported in the last four years, that is, 23.86% of the total. Furthermore, out of a total of 90 improper disposal cases, only 34 were reported in last four years, that is, 37.77% of the total. These calculations show that theft/loss and improper disposal have a far less adverse effect on the healthcare industry. Figure 4 provides a graphical presentation of different disclosure types.

Graphical Presentation of Different Data Disclosure Types.
The above graph shows that theft/loss and improper disposal incidents have decreased in frequency, but that hacking/IT incidents and unauthorized access incidents have increased. Notably, hacking/IT incidents have shown an abrupt increase over the last few years. In the next subsection, we will discuss the locations of breached information and from where the sensitive health information has been breached/disclosed.
4.2.2. Breached Locations
Protected health information is stored either on paper or on electromechanical storage devices. This section details the locations from where the protected health information is breached through different approaches. Yearly information about the location of data breach incidents is shown in Table 6 . The data presented in this table were compiled from OCR and HIPAA reports. In this context, we also followed the same procedure as discussed in Section 4.2 . We have provided only the important references [ 8 , 13 , 17 , 18 , 19 , 20 , 21 ], because for 2018 and 2019, we referred to 24 different reports, and including all of them in this study would not be feasible.
PHI Breached Location.
PHI: Protected Health Information; EMR: Electronic Medical Records; PED: Portable Electronic Devices.
In Table 6 , eight locations, i.e., Electronic Medical Records (EMR), Laptop, Desktop computers, Other Portable electronic devices, Paper documents, Network Server, Email, and Other, are the locations from where the protected health information (PHI) was breached. According to the analysis, out of the 8 locations, Paper/Film is the most susceptible to breaches. It saw 575 breached incidents out of a total of 3253 incidents, accounting for 17.67% of the total number of episodes during 2010 to 2019. The leading position of Paper/Films is because of the improper disposal of unnecessary but sensitive healthcare data. Paper/Films is followed by Email, which represented 17.52%, and Network servers, which accounted for16.69% of the total.
Electronic Medical Records (EMR) saw the least fewest instances of intrusion, with only 195; this is only 5.99% of the total of 3253 incidents carried out in the same time period. EMR is followed by the Other Portable Electronic Devices (PED) which made up 6.64% of the total. Desktop computers accounted for 9.40% of the total. As per the data, the attacks on Email and Network Server locations showed a marked increase from 2016–2019. Out of a total of 570 Email location based data breach incidents, 457 were reported in the last four years (2016 to 2019), of which 35.03% were reported in the year 2019 only. Moreover, out of a total of 543 Network server location-based data breach incidents, 348 were reported in the last four years (2016 to 2019). Yet again, 22.03% of these cases were reported in 2019 alone. This is because of the digitization of healthcare organizations and the excessive use of smart devices by customers. Studies also show that outdated security software, Database servers without passwords, and email accounts with weak or no passwords are the most common reasons behind these breaches. Our analysis also revealed that Paper/Films, Desktop computers, and Laptops have shown a small decrease in the number of breaches over the last four years.
Our study observed that at present, attacks on sensitive healthcare data are being perpetrated by cyber criminals who use different techniques such as malware, ransomware, or phishing attacks [ 8 , 17 ] to prey on EHRs. Email and Network servers have become attack-prone locations for hackers. Figure 5 shows a comparative representation of these locations on the basis of the number of breached incidents every year carried out on each location. Graphical representation will help the reader to understand the results that we have produced through this analysis, and will also help to map the variation of healthcare data breach incidents carried out on specified locations over a ten-year period.

Comparative Graphical Representation.
4.3. Financial Effect of Data Breaches
Data breach cost calculation is a complex task. Different institutions have set parameters and applied different techniques to estimate the average cost of data breaches. The Ponemon Institute calculates both direct and indirect expenses incurred by an organization to determine the average cost of a data breach. This section discusses the financial effects of data breaches, and mainly focuses on healthcare data breaches. For this purpose, the data breach cost reports generated by the Ponemon Institute sponsored by IBM were analyzed to determine the financial effects of data breaches on individuals, organizations, and countries. Table 7 provides information about data breach costs from 2010 to 2019. The data presented in this table were compiled from different Ponemon-IBM sponsored data breach cost reports [ 12 , 13 , 22 , 23 , 24 , 25 , 26 , 27 ].
Cost of Data Breaches.
Data breach cost analysis shows that healthcare breached record costs have increased rapidly compared to the average cost of a breached record. The average record cost was $214 in 2010, but in 2011, it had decreased by 10%. In 2012, it decreased by 42.64% from the previous year. After that, it gradually increased or decreased year by year; in 2019, it increased by 1.55% from the previous year. From 2010 to 2019, the healthcare breached record cost increased by 45.91% from $294 to $429. The cost of each breached record in the healthcare sector was $294 in 2010; this figure decreased until 2012, after which it increased by 1.11% from 2014 to 2015, 7.04% from 2016 to 2017, and 5.14% from 2018 to 2019. The 2018 Verizon DBIR report showed that 76% of data breaches carried out in 2018 were financially motivated [ 7 ]. In line with that report, it was shown that 83% of healthcare data breaches had financial motives [ 21 ]. Figure 6 provides a graphical cost comparison of average breached record costs and healthcare breached record costs by year. In the next subsection of this study, we will perform a time series analysis to find the trend of healthcare data breaches and their costs.

Graphical Comparison of Average Record Cost and Healthcare Record Cost.
5. Forecasting of Healthcare Data Breaches
The time series analysis is a statistical approach that is used for forecasting or trend analysis; it works on data sets ordered in time, or deals with time series data. Time series data defines the set of values that a variable takes at different times. In this study, the Simple Moving Average (SMA) and Simple Exponential Smoothing (SES) methods of time series were applied to the data to determine the trend of healthcare data breaches and their cost on the healthcare industry. Two methods of time series were applied to the same data in this study to determine the variations, if any, and to make the forecasting results more consistent.
The Simple Moving Average (SMA) method has been adopted extensively to keep update forecasts. This method is based on the calculated averages of subsets of a data set. The moving average can be calculated by making subgroups of observations. It can include two, three, four, or five observation groups. After calculating the moving average, it was used to forecast the next period [ 25 ].
where At is moving average at time t, which is the forecast value at time t + 1; Ot is Observation at time t; and ‘n’ is number of observations in an interval or sub-group [ 28 ].
Here we take the interval of two observations as a subgroup, and the moving averages are calculated. Table 8 summarizes the forecast information about healthcare data breaches via the SMA method. Here, the actual values represent known observations, while the forecast values are the predicted values calculated using the SMA method. With the help of the data analysis tool in Microsoft excel, we generated the forecast results and compared them with manually calculated results with the help of Equation (1) for accuracy. In the interests of brevity, we have only showed the final forecast results in tabular and graphical form. Figure 7 provide a graphical presentation of the forecast data breaches, while Figure 8 cites the forecast costs for breached healthcare records.

Forecasting Graph of Healthcare Data Breaches from 2010–2020 through SMA method.

Forecasting graph of Healthcare Record Cost since 2010–2020 through SMA method.
Healthcare Data Breach Forecasting through SMA method.
SMA: Simple Moving Average.
In Figure 7 , the green curve represents actual data breaches, while blue represents forecast data breaches calculated on the basis of the moving average. Both curves are close to each other and show an increasing trend. However, the actual curve always lies above the forecast line, which predicts that the magnitude of data breaches will increase in the coming years. Hence, all necessary and preventive measures have to be taken by researchers, security experts, and healthcare organizations to minimize this.
Figure 8 presents the results of cost forecasting of exposed health records, determined using the SMA method. The actual and forecast curves are close to each other from the beginning to the end. However, the actual curve consistently grows from the upper side. The forecast curve shows that the cost of healthcare breached records increases consistently. From this trend, we can predict that in future, the cost of healthcare breached records will increase, albeit gradually.
Simple Exponential Smoothing (SES) is a forecasting method used for univariate data. It is one of the most popular forecasting methods that uses the weighted moving average of past data as the basis for a forecast. Unlike the Simple Moving Average method, the idea of this method is to provide the highest weights to recent data points (observations) and the lowest weights to older data points (observations) [ 29 ]. It is better known for short-term forecasting, and its accuracy strongly depends on the optimal value of the smoothing constant, α. The value of α is between 0 and 1. When α is close to 1, fast learning is indicated (in this case, forecasting is influenced by only the most recent values), whereas when α is close to 0, slow learning (in that case, forecasting is influenced by old observations) occurs. The general formula for SES is:
where F t+1 is the forecast value at time t + 1, α is the smoothing constant, y t is a known value at time t, and Ft is the forecast value of the variable Y at the time t [ 29 ]. Here, we take the value of α = 0.4 so as to accomplish a balanced influence of observations on the forecasting results. Table 9 provides the forecast results of healthcare data breaches and their cost, determined using the SES method. The forecast values were calculated on the basis of actual (known observations) values using Equation (2). Later, we compared the results with those generated by the data analysis tool in MS-Excel to verify the accuracy. The final results of the forecasting are presented in Table 9 .
Healthcare Data Breach Forecasting Using the SES method.
SES: Simple Exponential Smoothing.
Figure 9 summarizes healthcare data breach forecasting using the SES method. The actual curve of the graph always moves above the forecast curve except at data point 6, where the forecast data point value is higher than the actual (known) value. For the year 2020, only a forecast value was available, which we predicted on the basis of previous historical data.

Forecasting Graph of Healthcare Data Breaches from 2010–2020 using the SES method.
Figure 10 presents the results of cost forecasting of exposed health records, as determined using the SES method. The data points on the actual curve represent the original values of observations, whereas those on the forecast curve represent prediction (forecasting) values.

Forecasting graph of Healthcare Record Costs from 2010–2020 Using the SES method.
6. Discussion
The transformation of the healthcare industry from one that uses paper-based systems to one that is based upon electronic health record systems has been made possible because of smart phones, information systems, IOMT, cloud services, internet connectivity, and other web based smart devices. Advances in information and communication technology have made healthcare data more digitized, distributive, and mobile. Despite the numerous advantages of EHRs, the digital health data of patients is at huge risk today. As chronicled in our study, data breach trends have also undergone a massive transformation. The comprehensive analysis undertaken in this study reveals that the healthcare industry is the focus of many cyber invaders. Moreover, we analyzed different data breach reports generated by different organizations and institutes to gain insights, and apply them, in our future research work. The final results which from this study are:
- More than 10 billion records were exposed from different sectors from 2005 to 2019. These sectors were MED, BSF, BSO, EDU, NGO, BSR, and GOV.
- There have been 3912 confirmed data breach cases in the healthcare sector alone. Nearly 43.38% of health data was compromised from 2005 to 2019, the highest among all sectors.
- The greatest number of breach attacks on EHRs was initiated by Hacking (HACK). Statistics show that more than 64% of health data was breached from 2005–2019. Moreover, in the last five years (2015–2019) alone, hacking incidents exposed more than 92% of records. This shows an alarming change in hacking attacks on healthcare organizations. Other types of attacks that affected the healthcare industry were PHYS and PORT, being the causes of 14.39% and 9.51% of the total exposed records from 2005 to 2019, respectively.
- HIPAA and OCR reports also showed that hacking/IT incidents are the main cause behind healthcare data breaches. As per the HIPAA reports, 255.18 million people were affected from 3051 healthcare data breach incidents from 2010 to 2019.
- The main types of attacks used to breach protected health data are Hacking/IT incidents, unauthorized access/ internal disclosure, Theft/loss, or Improper disposal. However, in the last three or four years, theft/loss and improper disposal have shown a decreasing trend. In contrast, hacking/IT incidents and unauthorized internal disclosures have shown a marked increases, especially hacking incidents, which have increased very rapidly in frequency in last few years.
- Hacking/IT incidents have increased by 73.4% in 2019 from 2018. However, unauthorized internal disclosure, theft/loss, and improper disposal decreased by 0.7%, 7.8%, and 22.22%, respectively, from 2018 to 2019.
- The main locations from where confidential healthcare data were breached over the last four years were email and network servers. Paper/Films have also been major targets since 2010, although there has been a decrease in attacks on Paper/Films in the last four years.
- In the healthcare industry at present, the average cost of data breach is $6.45 million, up from $3.92 million in 2019 [ 9 ]. The average cost of a breached record is $150. But in the healthcare industry, the cost of each breached record was $429 in 2019 [ 13 ]. The average cost of each record increased by 1.35% in 2019 relative to 2018, and the cost of each breached record in the healthcare sector increased by 5.14% in 2019.
- The SMA and SES methods of time series analysis were used for healthcare data breach and cost forecasting. The generated results indicated that SMA provides more accurate forecast results than SES. SMA produced results which showed more symmetry with the actual results than the SES results.
7. Conclusions
From our analysis of healthcare data breaches, the authors concluded that E-health data is highly susceptible, as it is targeted most frequently by attackers. A long-term analysis of data breaches showed that healthcare records were exposed by both internal and external attacks, such as hacking, theft/loss, unauthentic internal disclosure, and the improper disposal of unnecessary but sensitive data. However, our short-term analysis showed that hacking/IT incidents are most commonly used by attackers. Furthermore, the short-term analysis also showed that Email and Network servers are the main locations from where confidential health data is beached. Our cost analysis showed that healthcare data breaches are far more expensive than the average cost of data breaches, especially in developed countries. The time series analysis results showed that both data breaches and their costs will increase in future. Hence, preventive measures need to be prioritized by the researchers, security experts, and healthcare organizations.
There are several other aspects that need to be focused upon in research that seeks to provide insights into healthcare data breaches. The authors of the present study only used the most pertinent ones. However, the authors intend to pursue the following specific domains in the future:
- Identify and address the main victims of cyber-attacks on the healthcare sector.
- Undertake a study that investigates whether healthcare organizations are lacking usable-security measures because of the absence of accountability and improper training of employees and clients.
- Classify hacking/IT incidents that led to healthcare data breaches.
- Identify preventive measures that should be taken to avoid healthcare data breaches.
Acknowledgments
Authors are grateful to the College of Computer and Information Sciences, Prince Sultan University for providing the funds to undertake this research study.
Author Contributions
A.H.S., A.K.S., M.Z. and M.A. contributed to the motivation, the interpretation of the method effects and the results. R.K. proposed minor suggestions. A.H.S., A.A. and R.A.K. provided the concept, prepared the draft versions, performed the evaluation and extracted the conclusions. A.A. and R.A.K. supervised the study. All authors have read and agreed to the published version of the manuscript.
College of Computer and Information Sciences, Prince Sultan University, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
14 biggest healthcare data breaches [updated 2024].

Edward Kost
The healthcare industry suffers some of the highest volumes of cyberattacks and there are whispers of a lot more to come . Combine this trend with breach damage costs surpassing all other industries and you get the thunderous warning of a devastating cyberattack storm approaching the sector.
To help healthcare entities strengthen their cyber resilience , we’ve compiled a list of some of the biggest data breaches in the healthcare industry, ordered by degree of impact.
If you're concerned about your current level of data breach resilience, this cybersecurity guide for the healthcare industry will help.
The 14 Biggest Data Breaches in Healthcare Ranked by Impact
Each listed event is supported with a summary of the data that was comprised, how the breach occurred, and key learnings to protect you from suffering a similar fate.
1. Tricare Data Breach

Date: September 2011
Impact: 5 million patients
How did the breach occur?
Tricare, a healthcare program servicing active-duty troops, their dependents, and military retirees, suffered a significant data breach following the theft of backup tapes of electronic health records. The backups were stolen from the car of an individual responsible for transporting the tapes between facilities.
It’s unclear whether the criminals possessed the necessary acumen to decrypt the information stored on the tapes, or if they understood what they were stealing. As a necessary precaution, the incident was treated as a data breach.
What data was compromised?
The following data may have been compromised in the Tricare data breach:
- Social security numbers
- Phone numbers
- Personal health data
- Clinical notes
- Prescription information
Learn from this data breach
Though the data on these backup tapes was encrypted, the encryption method did not align with a particular federal standard. To dampen the impact of data breaches reported to HIPAA, a data encryption policy that aligns with federal standards should be implemented.
Learn how to choose the best healthcare attack surface management product >
2. Community Health Systems Data Breach

Date: April-June 2014
Impact: 4.5 million patients
Cybercriminals believed to be located in China, exploited a software vulnerability by deploying high-sophisticated malware leading to the theft of sensitive patient data. The incident impacted anyone that received treatment from a facility associated with the community health system network in the last 5 years.
The following information was compromised in the Community Health System data breach:
- Birth dates
- Social Security numbers
- Teach employees to recognize the warning signs of malware injection attempts and other cyber threats common to healthcare .
- Remediate vulnerabilities commonly abused during malware attacks.
- Regularly refer to the CVE database to remain informed about zero-day exploits impacting popular software solutions.
3. UCLA Health Data Breach

Date: July 2015
UCLA suffered a data breach that is believed to have started in October 2014, but this activity did not appear to have malicious potential. But in May of 2015, a cyberattack involving the compromise of sensitive patient information was confirmed.
The following data was compromised in the UCLA data breach:
- Dates of birth
- Health plan identification numbers
- Some medical data
Learn from this breach
UCLA health was issued with a $7.5 million fine for its failure to report the breach in a timely manner, a violation of the breach notification protocol specified under HIPAA.
To prevent such breach reporting delays, it’s important to commit to a thorough investigation whenever suspicious network activity is detected .
4. Advocate Health Care Data Breach

Date: August 2013
Impact: 4.03 million patients
Advocate Health Care fell victim to a series of data breaches following the theft of four personal computers storing unencrypted medical information pertaining to 4.03 million patients.
The following data was compromised in the Advocate Health Care data breach:
- Credit card numbers with expiration dates
- Demographic information
- Clinical information
- Health insurance information
The failure to implement the most basic cybersecurity practice of data encryption was a blatant violation of the data protection standards outlined in HIPAA . To send a strong message to other health entities about the implications of such malpractice, Advocate Health Care Network was changed with a $5.55 million fine payable to the Health and Human Services Department.
To prevent such an outcome, physical security controls as specified in ISO 27001 should be implemented to protect internal devices from theft, in addition to encryption practices across all facilities interacting with sensitive data .
Learn how to choose a healthcare cyber risk remediation product >
5. Medical Informatics Engineering Data Breach

Impact: 3.9 million patients
How did the data breach occur?
Medical Informatics Engineering (MIE), a developer of electronic medical record software, suffered a data breach impacting at least 11 of its healthcare provider clients.
Cybercriminals accessed one of MIE's servers by using a compromised username and password and maintained undetected access for 19 days. 239 of MIE's clients were impacted by the breach.
The following data may have been compromised in the Medical Informatics Engineering data breach:
- Telephone numbers
- Mailing addresses
- Hashed passwords
- Security questions and answers
- Spousal information
- Email addresses
- Lab results
- Health insurance policy information
- Disability codes
- Doctor names
- Medical conditions
- Names of children
- Birth statistics
The Office for Civil Rights discovered that the breach occurred because MIE violated HIPPA security rule 45 CFR § 164.308 which specifies the requirement for thorough risk analysis to discover potential exposures to personal health identification. Because of this violation, MIE was given a $100,000 fine.
To prevent non-compliance with cybersecurity regulations, and the resulting costly fines, a security solution capable of mapping specific compliance efforts against recognized security frameworks should be implemented .
Cybercriminals were able to effortlessly gain access to MIE’s private network by using compromised credentials. To prevent such an event, a dark web monitoring solution should be implemented to monitor for sensitive data leaks that could include network access credentials.
6. Newkirk Products Data Breach

Date: July 2016
Impact: 3.8 million patients
Newkirk Products, once of the largest providers of healthcare identification card issuers in the United States, suffered a data breach when cyber criminals gained access to one of its servers.
Many healthcare entities were impacted by the event, but perhaps the most significant victim that led to such a high impact was insurer Blue Cross Shield, the largest healthcare insurance provider by enrolment. Several Blue Cross Shield branches were associated with the compromised data.
The following data was compromised in the Newkirk products data breach:
- Primary care provider information
- Medicaid ID numbers
- Patient names
- Names of dependants
- Invoice information
- Rigorously test server software for security vulnerabilities and misconfigurations .
- Secure all privileged access management protocols.
- Continuously scan servers for potential exploits .
7. Banner Health Data Breach

Date: Aug 2016
Impact: 3.62 million patients
Cybercriminals gained access to one of Banner’s private servers, an intrusion that was discovered upon the discovery of unusual log activity by Banner Health staff.
The compromised server was used to process card payment information from food outlets across different Banner Health locations.
The following data was compromised in the Banner Health data breach:
- Social security information
- Appointment dates
- Physician information
- Ensure third-party vendors comply with mandatory financial regulations to prevent the accessibility of customer payment information through a third-party data breach.
- Ensure continued improvements of security postures across all third-party vendors through regular risk assessments and security rating monitoring .
8. Trinity Health Data Breach

Date: May 2020
Impact: 3.3 million patients
In May 2020, Blackbaud, Trinity Health’s third-party vendor responsible for storing a backup of its donor database, fell victim to a ransomware attack attempt. Trinity Health, with the support of forensic experts and law enforcement, was able to successfully block the ransomware attack attempt, but not before the hackers exfiltrated a subset of data that included information linked to Trinity Health.
In violation of the F.B.I’s firm stance against cybercriminal compliance , Blackbaud paid the cybercriminal’s demand in exchange for the stolen database alongside a guarantee that any copies of the data would be permanently destroyed.
Because such a guarantee cannot be confirmed, Trinity Health treated the event as a highly probable data breach, ranking this event as the largest data breach in the healthcare industry in 2020.
In 2021, Trinity Health fell victim to another data breach impacting 586,869 patients. This incident was part of a large-scale data breach resulting from a cyberattack against third-party file transfer platform, Accellion.
According to Trinity Health, the following patient information was potentially compromised:
- Healthcare providers
- Dates and types of health care services
- Medical record numbers
- Immunization types
- Medications
- Claims information
- Certain financial information (excluding credit card information)
- Implement a third-party vendor attack surface monitoring solution to discover and address vulnerabilities that could potentially facilitate ransomware attacks.
- Never comply with cybercriminal demands. Cooperation is never guaranteed and you’ll still have to treat the event as a potential breach with the addition of negative publicity and major financial losses .
- Blackbaud’s successful interception of the ransomware attack attempt is a testament to its highly optimized incident response plan and awareness of the ransomware attack sequence .
9. Shields Healthcare Group Data Breach

Date: March 2022
Impact: 2 million people
An unknown cyberattacker gained access to the network server belonging to Shields Healthcare Group from March 7, 2022, to March 21, 2022. The hacker’s presence activated a security alert on March 18; however, after investigating the alert, data compromise was not confirmed at the time.
According to Shield’s security incident notice , data compromise hasn’t yet not been confirmed. However, given the particular private network segments that were accessed by the cybercriminal, the following types of data are at risk of compromise:
- Home Addresses
- Provider Information
- Diagnosis Information
- Billing Information
- Insurance numbers
- Medial record numbers
- Patient IDs
- Other medical treatment information
Shield’s failure to identify a malicious actor in their network during the initial security alert allowed malicious activity to continue for another three days. A zero-trust approach to cyber threat investigation may have resulted in a more vigorous investigation that would have identified the presence of a data exfiltration backdoor.
Learn how to detect data exfiltration before it’s too late.
10. Broward Health Data Breach

Date: January 2022
Impact: 1.3 million patients
Broward Health suffered a data breach through a compromised third-party medical provider with access to its patient database.
It’s speculated that the compromised device belonging to Brown Health’s third-party was not implementing Multi-Factor Authentication .
The following patient information was compromised in the Broward Health data beach:
- Driver’s license numbers
- Insurance information
- Medical information
- Implement Multi-Factor Authentication (MFA) across all endpoints
- Secure all Privileged Access Management
- Keep track of all endpoints that connect, and attempt to connect, to your private network
11. Morley Companies Data Breach

Date: February 2022
Impact: 521,046 individuals
Morley Companies , a third-party provider of business services to Fortune 500 companies including medical industries, suffered a ransomware attack resulting in the exposure of over 521,000 individual records.
The following data was compromised in the Morley Companies data breach:
- Client identification numbers
- Medical diagnostic and treatment information
Though the attack began on August 1, 2021, Morley waited until February 2022 to notify potential victims. This significant delay placed Morley at a heightened risk of violating the HIPAA Breach Notification rule - a mistake that could have resulted in a fine of at least $50,000.
Learn more about the HIPAA privacy rule and how to maintain compliance.
Another key learning from this incident is the similar effects between ransomware attacks and data breaches . Ransomware attacks also result in sensitive data exposure when ransom demands are not paid in a timely manner. Because of the similar outcomes between the two events, data breach security controls could also support a defense against ransomware attacks.
12. L’Assurance Maladie Data Breach

Date: March 2022
Impact: 510,000 people
French insurance body, L’Assurance Maladie , suffered a data breach after 19 accounts, primarily belonging to pharmacists, were compromised.
Hackers likely retrieved the passwords for these accounts from a dark web forum hosting credentials stolen in previous data breaches.
The stolen data included the following:
- Dates of birth
- Level of reimbursement
- Implement Multi-Factor Authentication to block cyber criminals trying to log in with stolen credentials
- Implement a data leak detection solution to discover and shut down sensitive data exposures posted on the dark web.
13. ARcare Data Breach

Impact: 345,000 people
Between January 18, 2022, and February 24, cybercriminals maintained unauthorized access inside ARcare’s computer systems, reviewing and stealing sensitive individual information.
On April 4, it was discovered that some of the stolen data was exposed on the internet. This pattern of behaviour - exposing stolen records shortly after a breach - mirrors that of ransomware attackers, suggesting that the incident may have been a ransomware attack.
The following data was compromised in the breach:
- Drivers license numbers
- State identification numbers
- Dates of Birth
- Financial account information
- Medical treatment information
- Medical diagnosis information
- Condition information
This incident forced ARcare to review its data security practices and consider superior risk mitigation strategies. These aren’t efforts that should follow a data breach. Instead, they should be firmly established well before a cyber incident occurs. Don’t wait for a data breach to initiate a review of your security protocols; review your incident response plans and implement a third-party risk mitigation strategy ASAP.
14. OneTouchPoint (OTP)

Date: July 2022
Impact: 2.6 million people
OneTouchPoint is a third-party mailing and printing vendor that provided services mainly to healthcare organizations. OTP first noticed some of its files had been locked and decrypted in July 2022. After investigation, OTP concluded that their systems had been illegally accessed in the months prior. Shortly after, over 30 healthcare providers (including Blue Shield of California, Kaiser Permanente, Anthem, and Blue Cross) that had been clients of OTP began to report data breaches of its medical and patient records.
The following sensitive information was exposed in the breach:
- Patient medical records (immunizations, allergies, vitals, medication, medical history)
- Patient demographics
- Employee employment dates
- Employee ID numbers
- Service descriptions and dates
- Health assessment test results
- Diagnosis codes
Although OTP did not release the exact nature of the breach, the company is currently undergoing a class-action lawsuit by the medical firms claiming that OTP failed to safeguard sensitive medical information that could expose its patients to fraud and theft. Additionally, OTP failed to notify affected organizations and patients on time, despite finding out about the breach months before initial reporting.
To avoid incidents like these, businesses need to do an annual review of their security policies to ensure all safeguards are up to date and equipped to defend against evolving cyber threats. Furthermore, healthcare organizations working with third-party contractors need to ensure their business associates are HIPAA-compliant if they are handling sensitive patient information.
Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, join 27,000+ cybersecurity newsletter subscribers, whitepaper: the state of cybersecurity in healthcare.
Related posts
How to prevent data breaches in 2024 (highly effective strategy), the 72 biggest data breaches of all time [updated 2024].

9 Ways to Prevent Third-Party Data Breaches in 2024
What are cloud leaks, what is a supply chain attack examples & prevention strategies, zero trust as a defence against supply chain attacks.
- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity

- HIPAA Resources
- Website Accessibility
Resource Library
Preventing hipaa data breaches: case studies and best practices.
The healthcare industry experiences more data breaches (confirmed data disclosure) than any other industry in the United States, accounting for more than 24% of all breaches. 1 In 2017, healthcare data breaches compromised more than 5 million healthcare records 2 and cost providers an average of $380 per record — more than any other industry and 69% greater than the overall average.

- Loss or theft of computers, storage devices or smartphones containing patient information from cars, offices, briefcases, employees’ homes, hotel rooms, etc.
- Incorrectly addressed email containing patient information
- Electronic patient records accessed inappropriately by unauthorized employees
- Hacked servers
HIPAA Terms
According to the HIPAA statute:
Patient Health Information (PHI) is individually identifiable health information created or received by a healthcare provider regarding the physical or mental health of any individual that is transmitted by electronic media, maintained in electronic media, or transmitted or maintained in any other form or medium.
Electronic protected health information (ePHI) is PHI that is created, stored, transmitted, or received electronically. The focus of the linked case studies is ePHI, although a HIPAA data breach can occur with paper records. Unless When patient data or patient healthcare information is referenced in the case studies and best practices linked here, it refers to ePHI.
Covered entity is a health plan, healthcare clearinghouse or healthcare provider who transmits any health information in electronic form for qualifying transactions. The U.S. Centers for Medicare & Medicaid Services (CMS) website offers guidance on how to determine whether a healthcare provider is a covered entity .
Even the most innocent mistake, however, if it leads to a data breach, can result in a costly and disruptive incident investigation, patient notification expenses, and significant fines and corrective action requirements.
An analysis of NORCAL Group data breach closed claims shows that inadvertent, unauthorized release of medical records or patient information is the most frequent reason for a data breach claim. Theft or loss of portable electronic devices like laptops, flash drives and smartphones is the second most frequent reason. NORCAL has also seen a marked increase in the past two years in incidents involving hacking, malware, and viruses, which (together) is now tied with theft/loss of portable devices as the second most common reason for a data breach claim.
The case studies linked here are based on NORCAL Mutual HIPAA data breach closed claims. The case studies introduce strategies to help reduce the risk of a HIPAA data breach and to appropriately respond to a breach when it happens. While the discussions here and in the linked case studies and best practices are not meant to be a comprehensive overview of compliance with the HIPAA Privacy Rule and Security Rule, compliance with the rules should prevent many security breaches.
What is a HIPAA Data Breach?
In general, a HIPAA data breach is an impermissible use or disclosure that compromises the security or privacy of PHI. An impermissible use or disclosure of PHI is presumed to be a breach unless the covered entity can show there is a low probability the PHI has been compromised based on a risk assessment of at least the following four factors: 4
- The nature and extent of the PHI involved in the use or disclosure, including the types of identifiers and the likelihood that PHI could be re-identified (e.g., aggregated PHI vs. complete, intact patient records)
- The unauthorized person who used the PHI or to whom the disclosure was made (e.g., whether the inadvertent disclosure was made to another covered entity regulated under HIPAA vs. a hacker)
- The likelihood that any PHI was actually acquired or viewed (e.g., an audit trail shows there has been no access to the databases at risk vs. a stolen laptop with PHI stored on the hard drive where access cannot be determined)
- The extent to which the risk to the PHI has been mitigated (e.g., encryption keys are promptly changed and network access monitoring shows no access vs. lost device with no opportunity to determine whether access has occurred)
When performing this assessment, a covered entity must address each element separately and then analyze the combined four elements to determine the overall probability that PHI has been compromised. If this assessment indicates there is low likelihood of compromised PHI, then the use or disclosure may not be classified as a HIPAA breach, and notification may not be required. If, on the other hand, the covered entity is unable to overcome the presumption of a breach and show that there is a low likelihood that the PHI was compromised, then breach notification may be required. 4
HIPAA Breach Analysis Flowchart
This flowchart outlines how a privacy or security incident is analyzed to determine whether a HIPAA breach has occurred, including the four factors outlined above. It forms the basis of the analyses in the case studies linked on this page and is also included on those pages.
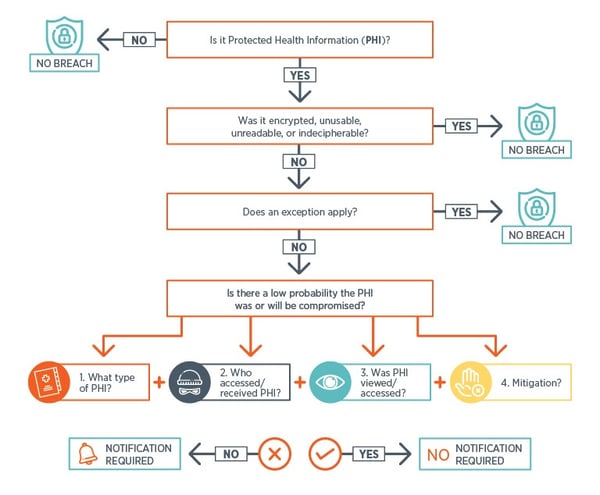
In addition to federal HIPAA regulations, covered entities may also have to comply with state data breach laws. State laws vary on what triggers a breach notification obligation and the nature of breach notification obligations. The linked case studies focus on federal data breach notification laws. The Health Information & the Law website has an interactive map that provides links to state health data security and breach notification laws .
HIPAA Data Breach Safe Harbor and Exceptions
Whether a privacy or security incident is a HIPAA breach depends on the nature of the PHI and the circumstances of the use or disclosure. Included in the HIPAA regulations is a critical safe harbor: If an impermissible use or disclosure involves PHI that has been rendered unusable, unreadable, or indecipherable (i.e., encrypted or remotely cleared, purged or destroyed), it does not rise to the level of a breach and, therefore, does not require notification. 4
If the incident involves unsecured PHI, but the disclosure falls into one of three narrow breach exceptions, notification is similarly not required:
“The first exception applies to the unintentional acquisition, access, or use of protected health information by a workforce member or person acting under the authority of a covered entity or business associate, if such acquisition, access, or use was made in good faith and within the scope of authority. The second exception applies to the inadvertent disclosure of protected health information by a person authorized to access protected health information at a covered entity or business associate to another person authorized to access protected health information at the covered entity or business associate, or organized healthcare arrangement in which the covered entity participates. In both cases, the information cannot be further used or disclosed in a manner not permitted by the Privacy Rule. The final exception applies if the covered entity or business associate has a good faith belief that the unauthorized person to whom the impermissible disclosure was made, would not have been able to retain the information.” (excerpt from the HHS HIPAA “HIPAA Breach Notification Rule,” line breaks added for clarity) 5
HIPAA Breach Notification
The HIPAA Breach Notification Rule requires HIPAA-covered entities and their business associates to provide notification following a breach of unsecured protected health information. 5 Covered entities must notify affected individuals, HHS and at times the media about the HIPAA breach. To whom and when notification must occur primarily depends on the number of individuals affected by the breach. If there is a breach of unsecured PHI that affects 500 or more individuals, the covered entity must notify the individuals and HHS without reasonable delay, and no later than 60 days after the covered entity discovers the breach. Once notified, HHS posts the breach on the HHS Office for Civil Rights (OCR) Breach Portal Website . The OCR is responsible for investigating breach incidents to determine if they were the result of HIPAA violations. OCR investigations may be initiated based on complaints, breach reports, information from other government agencies or reports in the media.
If the breach affects 500 or more individuals in the same jurisdiction or state, the covered entity must also notify the media. If a breach affects fewer than 500 individuals, the covered entity must notify affected individuals without reasonable delay, and no later than 60 days after discovery of the breach, and HHS no later than 60 days after the end of the calendar year in which the breach occurred. 4,5
Safeguard PHI with Encryption to Prevent a HIPAA Data Breach
Failure to adequately safeguard PHI can result in costly and time-consuming forensic investigations to determine whether and to what extent data may have been accessed. PHI encryption is a way to avoid these difficulties. If PHI is appropriately encrypted, there is a low probability that anyone other than the intended party who has the private key will be able to decrypt and ultimately decipher the contents. Using strong encryption may be the most efficient and effective means to avoid a HIPAA data breach, as the rule makes clear that impermissible use or disclosure of PHI encrypted pursuant to HIPAA guidelines is not considered a breach. 6,7
HIPAA defines encryption as “the use of an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without the use of confidential process or key.” 8 Data at rest (i.e., data stored in work stations, laptops, tablets, phones, flash drives, or external hard drives) and data in motion (i.e., data in a non-persistent state that is in transit across the Internet, wireless networks and connections, etc.) are addressed separately in HIPAA encryption guidance. 7 According to the Breach Notification Rule, the proper standards for encrypting data at rest are consistent with NIST Special Publication 800-111, Guide to Storage Encryption Technologies for End User Devices . 7 The appropriate standards for encrypting data in motion are consistent with any of the following NIST publications: 9
- 800-52, Guidelines for the Selection and Use of Transport Layer Security (TLS) Implementations .
- 800-77, Guide to IPsec VPNs: Recommendations of the National Institute of Standards and Technology .
- 800-113, Guide to SSL VPNs .
- 140-2, Security Requirements for Cryptographic Modules [includes Change Notices as of 12/3/2002] .
General Risk Management Strategies for Avoiding a HIPAA Data Breach
Consider the following general strategies for avoiding and mitigating a data breach: 4,10
Educate Staff and Clinicians
- Know what state and federal health data security laws require.
- Educate clinicians, staff and administrators on responding to a data security incident.
- The HHS HealthIT website has two different computer games created for training healthcare clinicians and staff on HIPAA device security .
Assess Data Security Risk
Perform thorough HIPAA risk assessments on a regular basis:
- Analyze all sources, systems, movement and storage of PHI.
- Document the results of the risk assessment.
- Implement additional safeguards to address any security risks identified.
Mitigate Data Security Risk
Imagine all of the ways data can be inappropriately accessed and put up road blocks:
- Encrypt all PHI.
- Install software to remotely wipe PHI and disable passwords in case of device loss or theft.
- Require authentication to access mobile devices, including complex passwords or biometric measures.
- Encrypt email and text messages.
- Install software to stop viruses and malware.
Monitor for Security Breaches
Implement a data activity monitoring system to alert IT to potential security threats. The HHS OCR HIPAA Audit Protocol provides guidance for determining monitoring protocols.
Respond to Security Incidents
Have a documented data security incident response plan in place:
- Identify who is on the incident response team and what actions they will take to address the incident.
- Report security incidents to the covered entity’s information technology/security department.
- Notify affected patients and the appropriate regulatory agencies in the manner advised by your attorney.
Every data security incident is unique (despite seemingly similar fact patterns) and federal and state data security breach regulations are constantly evolving and changing. It is important to stay current with breach notification requirements. Because breach notification is time sensitive, immediate action is frequently required. Although HIPAA generally allows 60 days for notifying patients and regulatory agencies about a breach, state law may require shorter notification periods, and determining the breadth of a security incident may involve hiring outside IT professionals, which can be time consuming.
More Information About Preventing HIPAA Data Breaches
- Best Practices: Mobile Device Policies for Preventing HIPAA Data Breaches
- Best Practices: Best Practices for Preventing HIPAA Data Breaches by Criminal Hackers
- Case Study Comparison: HIPAA Data Breaches and PHI on Stolen Laptops
- Closed Claim Case Study: Misdelivered Email Results in a HIPAA Data Breach
- Closed Claim Case Study: Employee Voyeurism Leads to a HIPAA Data Breach
- Closed Claim Case Study: Unsecured PHI on a Lost Flash Drive Results in a HIPAA Data Breach
Additional Resources for Policyholders
Guidance and additional information on the HIPAA Security Rule and on medical records security, access and release are available to all NORCAL policyholders by contacting a NORCAL Risk Management Specialist at 855.882.3412.

1. Verizon Enterprise. “ 2018 Data Breach Investigations Report .” (accessed 5/9/2018)
2. Identity Theft Resource Center. “ 2017 Annual Data Breach Year-End Review .” (accessed 5/9/2018)
3. Intel. “ Grand Theft Data — Data Exfiltration Study: Actors, Tactics, and Detection .” 2015. (accessed 5/9/2018)
4. Office of the National Coordinator for Health Information Technology (ONC). Guide to Privacy and Security of Electronic Health Information . “Chapter 7: Breach Notification, HIPAA Enforcement, and Other Laws and Requirements.” (accessed 5/9/2018)
5. HHS. “ Breach Notification Rule .” (accessed 5/9/2018)
6. Federal Register Volume 78, Number 17 (Friday, January 25, 2013), Page 5644. (accessed 5/9/2018)
7. Office of the National Coordinator for Health Information Technology (ONC). Guide to Privacy and Security of Electronic Health Information . “Chapter 4: Understanding Electronic Health Records, the HIPAA Security Rule, and Cybersecurity.” (accessed 5/9/2018)
8. Cornell Law School, Legal Information Institute. U.S. Code of Federal Regulations . “ 45 CFR 164.304 - Definitions .” (accessed 5/9/2018)
9. California Medical Association (CMA) Legal Counsel. “ Security Breach of Health Information [Document #4006] .” January 2015. (accessed 5/9/2018)
10. Psychiatric Times. “ How to Protect Patient Information — And What to Do if It Gets Lost or Stolen .” 3 May 2011. (accessed 5/9/2018)
Additional Linked Sources
Ponemon. “ 2017 Cost of Data Breach Study — United States .” (accessed 5/9/2018)
U.S. Department of Health and Human Services Office for Civil Rights (OCR). “ Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information .” (accessed 5/9/2018)
Health Info & the Law Project. “ States .” (accessed 5/9/2018)
U.S. Centers for Medicare & Medicaid Services (CMS). “ Are You a Covered Entity? ” (accessed 5/9/2018)
Filed under: Digital Health , Privacy & HIPAA , Cybersecurity , Article , Practice Manager , Information Security
Topics
specialties , recently added.
Interested in NORCAL Group?
Contact Your Agent/Broker or call 844.4NORCAL today

© 2001 - 2023 ProAssurance All rights reserved
- 844-466-7225
- Privacy Policy
- Terms of Use

Ethical Implications of AI in Healthcare Data: A Case Study Using Healthcare Data Breaches from the US Department of Health and Human Services Breach Portal between 2009-2021
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Share full article
Advertisement
Supported by
Cyberattack Paralyzes the Largest U.S. Health Care Payment System
The hacking shut down the nation’s biggest health care payment system, causing financial chaos that affected a broad spectrum ranging from large hospitals to single-doctor practices.

By Reed Abelson and Julie Creswell
An urgent care chain in Ohio may be forced to stop paying rent and other bills to cover salaries. In Florida, a cancer center is racing to find money for chemotherapy drugs to avoid delaying critical treatments for its patients. And in Pennsylvania, a primary care doctor is slashing expenses and pooling all of her cash — including her personal bank stash — in the hopes of staying afloat for the next two months.
Listen to this article with reporter commentary
These are just a few examples of the severe cash squeeze facing medical care providers — from large hospital networks to the smallest of clinics — in the aftermath of a cyberattack two weeks ago that paralyzed the largest U.S. billing and payment system in the country. The attack forced the shutdown of parts of the electronic system operated by Change Healthcare, a sizable unit of UnitedHealth Group, leaving hundreds, if not thousands, of providers without the ability to obtain insurance approval for services ranging from a drug prescription to a mastectomy — or to be paid for those services.
In recent days, the chaotic nature of this sprawling breakdown in daily, often invisible transactions led top lawmakers, powerful hospital industry executives and patient groups to pressure the U.S. government for relief. On Tuesday, the Health and Human Services Department announced that it would take steps to try to alleviate the financial pressures on some of those affected: Hospitals and doctors who receive Medicare reimbursements would mainly benefit from the new measures.
U.S. health officials said they would allow providers to apply to Medicare for accelerated payments, similar to the advanced funding made available during the pandemic, to tide them over. They also urged health insurers to waive or relax the much-criticized rules imposing prior authorization that have become impediments to receiving care. And they recommended that insurers offering private Medicare plans also supply advanced funding.
H.H.S. said it was trying to coordinate efforts to avoid disruptions, but it remained unclear whether these initial government efforts would bridge the gaps left by the still-offline mega-operations of Change Healthcare, which acts as a digital clearinghouse linking doctors, hospitals and pharmacies to insurers. It handles as many as one of every three patient records in the country.
The hospital industry was critical of the response, describing the measures as inadequate.
Beyond the news of the damage caused by another health care cyberattack, the shutdown of parts of Change Healthcare cast renewed attention on the consolidation of medical companies, doctors’ groups and other entities under UnitedHealth Group. The acquisition of Change by United in a $13 billion deal in 2022 was initially challenged by federal prosecutors but went through after the government lost its case.
So far, United has not provided any timetable for reconnecting this critical network. “Patient care is our top priority, and we have multiple workarounds to ensure people have access to the medications and the care they need,” United said in an update on its website .
But on March 1, a bitcoin address connected to the alleged hackers, a group known as AlphV or BlackCat, received a $22 million transaction that some security firms say was probably a ransom payment made by United to the group, according to a news article in Wired . United declined to comment, as did the security firm that initially spotted the payment.
Still, the prolonged effects of the attack have once again exposed the vast interconnected webs of electronic health information and the vulnerability of patient data. Change handles some 15 billion transactions a year.
The shutdown of some of Change’s operations has severed its digital role connecting providers with insurers in submitting bills and receiving payments. That has delayed tens of millions of dollars in insurance payments to providers. Pharmacies were initially unable to fill many patients’ medications because they could not verify their insurance, and providers have amassed large sums of unpaid claims in the two weeks since the cyberattack occurred.
“It absolutely highlights the fragility of our health care system,” said Ryan S. Higgins, a lawyer for McDermott Will & Emery who advises health care organizations on cybersecurity. The same entity that was said to be responsible for the cyberattack on Colonial Pipeline, a pipeline from Texas to New York that carried 45 percent of the East Coast’s fuel supplies, in 2021 is thought to be behind the Change assault. “They have historically targeted critical infrastructure,” he said.
In the initial days after the attack on Feb. 21, pharmacies were the first to struggle with filling prescriptions when they could not verify a person’s insurance coverage. In some cases, patients could not get medicine or vaccinations unless they paid in cash. But they have apparently resolved these snags by turning to other companies or developing workarounds.
“Almost two weeks in now, the operational crisis is done and is pretty much over,” said Patrick Berryman, a senior vice president for the National Community Pharmacists Association.
But with the shutdown growing longer, doctors, hospitals and other providers are wrestling with paying expenses because the steady revenue streams from private insurers, Medicare and Medicaid are simply not flowing in.
Arlington Urgent Care, a chain of five urgent care centers around Columbus, Ohio, has about $650,000 in unpaid insurance reimbursements. Worried about cash, the chain’s owners are weighing how to pay bills — including rent and other expenses. They’ve taken lines of credit from banks and used their personal savings to set aside enough money to pay employees for about two months, said Molly Fulton, the chief operating officer.
“This is worse than when Covid hit because even though we didn’t get paid for a while then either, at least we knew there was going to be a fix,” Ms. Fulton said. “Here, there is just no end in sight. I have no idea when Change is going to come back up.”
The hospital industry has labeled the infiltration of Change “the most significant cyberattack on the U.S. health care system in American history,” and urged the federal government and United to provide emergency funding. The American Hospital Association, a trade group, has been sharply critical of United’s efforts so far and the latest initiative that offered a loan program.
“It falls far short of plugging the gaping holes in funding,” Richard J. Pollack, the trade group’s president, said on Monday in a letter to Dirk McMahon, the president of United.
“We need real solutions — not programs that sound good when they are announced but are fundamentally inadequate when you read the fine print,” Mr. Pollack said.
The loan program has not been well received out in the country.
Diana Holmes, a therapist in Attleboro, Mass., received an offer from Optum to lend her $20 a week when she says she has been unable to submit roughly $4,000 in claims for her work since Feb. 21. “It’s not like we have reserves,” she said.
She says there has been virtually no communication from Change or the main insurer for her patients, Blue Cross of Massachusetts. “It’s just been maddening,” she said. She has been forced to find a new payment clearinghouse with an upfront fee and a year’s contract. “You’ve had to pivot quickly with no information,” she said.
Blue Cross said it was working with providers to find different workarounds.
Florida Cancer Specialists and Research Institute in Gainesville resorted to new contracts with two competing clearinghouses because it spends $300 million a month on chemotherapy and other drugs for patients whose treatments cannot be delayed.
“We don’t have that sort of money sitting around in a bank,” said Dr. Lucio Gordan, the institute’s president. “We’re not sure how we’re going to retrieve or collect the double expenses we’re going to have by having multiple clearinghouses.”
Dr. Christine Meyer, who owns and operates a primary care practice with 20 clinicians in Exton, Pa., west of Philadelphia, has piled “hundreds and hundreds” of pages of Medicare claims in a FedEx box and sent them to the agency. Dr. Meyer said she was weighing how to conserve cash by cutting expenses, such as possibly reducing the supply of vaccines the clinic has on hand. She said if she pulled together all of her cash and her line of credit, her practice could survive for about two and a half months.
Through Optum’s temporary funding assistance program, Dr. Meyer said she received a loan of $4,000, compared with the roughly half-million dollars she typically submits through Change. “That is less than 1 percent of my monthly claims and, adding insult to injury, the notice came with this big red font that said, you have to pay all of this back when this is resolved,” Dr. Meyer said. “It is all a joke.”
The hospital industry has been pushing Medicare officials and lawmakers to address the situation by freeing up cash to hospitals. Senator Chuck Schumer, Democrat of New York and the chamber’s majority leader, wrote a letter on Friday, urging federal health officials to make accelerated payments available. “The longer this disruption persists, the more difficult it will be for hospitals to continue to provide comprehensive health care services to patients,” he said.
In a statement, Senator Schumer said he was pleased by the H.H.S. announcement because it “will get cash flowing to providers as our health care system continues to reel from this cyberattack.” He added, “The work cannot stop until all affected providers have sufficient financial stability to weather this storm and continue serving their patients.”
Audio produced by Jack D’Isidoro .
Reed Abelson covers the business of health care, focusing on how financial incentives are affecting the delivery of care, from the costs to consumers to the profits to providers. More about Reed Abelson
Julie Creswell is a business reporter covering the food industry for The TImes, writing about all aspects of food, including farming, food inflation, supply-chain disruptions and climate change. More about Julie Creswell
Case Study on a Session Hijacking Attack: The 2021 CVS Health Data Breach
- Conference paper
- First Online: 15 August 2022
- Cite this conference paper

- Aversa Prentosito 10 ,
- McKenna Skoczen 10 ,
- Lauren Kahrs 10 &
- Suman Bhunia 10
Part of the book series: Lecture Notes in Computer Science ((LNCS,volume 13475))
Included in the following conference series:
- International Conference on Mobile Web and Intelligent Information Systems
The CVS medical data breach in March of 2021 was a source of anxiety, fear, and anger in many users, leading to lower customer loyalty. Our study found that their websites used misconfigured databases, allowing an adversary to steal healthcare data through session hijacking attacks. Customers’ search metadata containing email addresses, prescriptions, and other medical search queries, were stored in cloud-hosted log files. Although no concrete evidence of data misuse was uncovered, the research found that over a billion confidential search queries were potentially exposed to adversaries. This paper analyzes the data breach methodology and impact in detail and provides possible defense strategies against such attacks. It violates the security and protection regulations mandating proper confidentiality of users’ private medical and healthcare information. This paper also outlines possible defense measures against healthcare data session hijacking attacks, including having policies in place, such as an incident response plan, preserving evidence of the breach, and isolating the data breach.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
McKeon, J.: CVS health faces data breach, 1B search records exposed, June 2021. https://healthitsecurity.com/news/cvs-health-faces-data-breach1b-search-records-exposed
McGee, M.K., Ross, R.: Researcher: 1 billion CVS health website records exposed, June 2021. https://www.govinfosecurity.com/researcher-1-billion-cvs-health-website-records-exposed-a-16890
Alder, S.: 1 billion-record database of searches of CVS website exposed online, June 2021. https://www.hipaajournal.com/1-billion-record-database-of-searches-of-cvs-website-exposed-online/
CVS: CVS health notice of privacy practices. https://www.cvs.com/content/patient-privacy
Chatterjee, S., Gao, X., Sarkar, S., Uzmanoglu, C.: Reacting to the scope of a data breach: the differential role of fear and anger. J. Bus. Res. 101 , 183–193 (2019)
Article Google Scholar
CyberTalk: CVS accidentally leaks more than 1 billion records. https://www.cybertalk.org/2021/06/16/cvs-accidentally-leaks-more-than-1-billion-records
Fowler, J.: Report: CVS health exposed search records online. https://www.websiteplanet.com/blog/cvs-health-leak-report/
Leggate, J.: What is CVS health? https://www.foxbusiness.com/markets/what-is-cvs-health
CVS: About CVS health. https://www.foxbusiness.com/markets/what-is-cvs-health
Caremark. https://www.caremark.com/
Conner, B.: Mid-year update: 2021 SonicWall cyber threat report (2021)
Google Scholar
1 billion CVS health records breached, June 2021. https://rocketit.com/cvs-health-data-breach/
Brewster, T.: CVS accidentally leaks 1 billion website records-including Covid-19 vaccine searches. https://www.forbes.com/sites/thomasbrewster/2021/06/16/cvs-accidentally-leaks-1-billion-website-records-including-covid-19-vaccine-searches/?sh=1986e4d92c4f
Paganini, P.: Over a billion records belonging to CVS Health exposed online, June 2021
More than 1 billion CVS data records accidentally exposed, researcher says, June 2021. https://abc30.com/cvs-data-breach-medical-records-health-cyber-attack/10798172/
Turea, M.: CVS health suffers database breach leaving 1b records exposed online, July 2021. https://healthcareweekly.com/cvs-health-database-breach
Hussain Seh, A., et al.: Healthcare data breaches: insights and implications. Healthcare 8 (2), 133 (2020)
The potential damages and consequences of medical identity theft and healthcare data breaches, April 2010. https://www.experian.com/assets/data-breach/white-papers/consequences-medical-id-theft-healthcare.pdf
Sinanaj, G., Zafar, H.: Who wins in a data breach?-A comparative study on the intangible costs of data breach incidents. In: PACIS, p. 60 (2016)
Tweneboah-Koduah, S., Atsu, F., Prasad, R.: Reaction of stock volatility to data breach: an event study. J. Cyber Secur. Mob. 9 (3), 355–384 (2020)
Azubuike, S.: Cybersecurity attacks: regulatory and practical approach towards preventing data breach and cyber-attacks in USA (2021)
Stone, J.: How to manage a healthcare data breach. https://www.securitymetrics.com/blog/how-manage-healthcare-data-breach
Landi, H.: CVS health database leak left 1B user records exposed online, June 2021. https://www.fiercehealthcare.com/tech/cvs-health-database-leak-leaves-1-billion-user-records-exposed-online
Download references
Author information
Authors and affiliations.
Miami University, Oxford, OH, 45056, USA
Aversa Prentosito, McKenna Skoczen, Lauren Kahrs & Suman Bhunia
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Aversa Prentosito .
Editor information
Editors and affiliations.
University of Bradford, Bradford, UK
Oxford Brookes University, Oxford, UK
Muhammad Younas
Lodz University of Technology, Lodz, Poland
Aneta Poniszewska-Marańda
Rights and permissions
Reprints and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper.
Prentosito, A., Skoczen, M., Kahrs, L., Bhunia, S. (2022). Case Study on a Session Hijacking Attack: The 2021 CVS Health Data Breach. In: Awan, I., Younas, M., Poniszewska-Marańda, A. (eds) Mobile Web and Intelligent Information Systems. MobiWIS 2022. Lecture Notes in Computer Science, vol 13475. Springer, Cham. https://doi.org/10.1007/978-3-031-14391-5_7
Download citation
DOI : https://doi.org/10.1007/978-3-031-14391-5_7
Published : 15 August 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-14390-8
Online ISBN : 978-3-031-14391-5
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

- 862 271 2727
- [email protected]
Home > Resources > Blog
Change Healthcare Breach as a Case Study

The breach incident involving Change Healthcare serves as a critical case study highlighting the importance of cybersecurity and data protection in the healthcare industry. Here’s an overview of the Change Healthcare breach as a case study, presented by Prima Systems, a leading healthcare BPO company committed to the highest standards of data protection and cybersecurity.
Incident Overview : In February, 2024, “Change Healthcare” , a subsidiary of United healthcare experienced a data breach incident that compromised the security of sensitive patient information and also caused providers to not being able to processed claims for their services.
Scope of the Breac h: The breach involved unauthorized access to Change Healthcare patient’s data, and it effected thousands of doctors, hospitals, and other healthcare providers affiliated to that entity.
Impact : The breach had significant implications for both Change Healthcare and the affected individuals, including potential financial losses amounting to millions(ransoms), reputational damage, and risks to patient privacy and confidentiality.
Factors Contributing to the Breach
Vulnerabilities in Security Controls : The breach orchestrated by APLHV or BlackCat may have resulted from vulnerabilities in Change Healthcare’s cybersecurity defenses, such as inadequate access controls, outdated software, or misconfigured systems.
Insider Threats : Insider threats, including employee negligence, malicious insiders, or unintentional data exposure, could have played a role in the breach.
Sophisticated Cyberattacks : The breach may have been the result of sophisticated cyberattacks, such as phishing scams, malware infections, or ransomware attacks, targeting Change Healthcare’s systems and networks.
Third-Party Risk : The involvement of third-party vendors or partners in Change Healthcare’s operations may have introduced additional security risks and vulnerabilities, leading to the breach.

Response and Remediation Efforts
Incident Response Plan : Change Healthcare activated its incident response plan to address the breach promptly and mitigate its impact on affected individuals and stakeholders. According to Change health care official statement, it also paid a significant ransom to APHV/BlackCat to take down the data from dark web.
Notification and Communication : Change Healthcare communicated transparently with affected individuals, and the public about the breach, providing timely updates and guidance on protective measures.
Forensic Investigation : Change Healthcare conducted a thorough forensic investigation to determine the root cause of the breach, identify the extent of the compromise, and implement corrective actions to prevent future incidents.
Enhanced Security Measures : Change Healthcare implemented enhanced security measures, such as strengthening access controls, implementing multi-factor authentication, encrypting sensitive data, and enhancing employee training and awareness programs.
Regulatory Compliance : Change Healthcare ensured compliance with applicable data protection regulations, such as HIPAA (Health Insurance Portability and Accountability Act), GDPR (General Data Protection Regulation), and other relevant privacy laws, to mitigate legal and regulatory risks associated with the breach.
At Prima Systems, we strictly follow ISO 27001 and HIPAA protocols to ensure robust data protection and cybersecurity measures that align with or exceed industry standards. Our commitment to these regulations demonstrates our dedication to safeguarding patient data and preserving trust in healthcare organizations.
Lessons Learned and Best Practices
Prioritize Cybersecurity : Healthcare organizations must prioritize cybersecurity and invest in robust security measures to protect sensitive patient data from unauthorized access, disclosure, or misuse.
Risk Management : Proactively identify and mitigate cybersecurity risks, including vulnerabilities in systems and networks, insider threats, and third-party risks.
Incident Response Preparedness : Develop and regularly test incident response plans to ensure a swift and coordinated response to cybersecurity incidents, minimizing the impact on operations and stakeholders.
Transparency and Accountability : Maintain transparency and accountability in cybersecurity incidents by promptly notifying affected individuals, regulatory authorities , and the public about the breach and its impact.
The Change Healthcare breach underscores the critical importance of cybersecurity in safeguarding patient data and preserving trust in healthcare organizations. By learning from this case study and implementing best practices in cybersecurity and data protection, healthcare organizations can mitigate the risk of breaches and uphold their commitment to patient privacy and confidentiality.
Share it on


MediSecure data breach: why is health data so lucrative for hackers?
Senior Lecturer in Law, The University of Melbourne
Disclosure statement
Megan Prictor previously received funding from the Commonwealth Department of Health. She is a member of the International Association of Privacy Professionals, European Association of Health Law (associate member), and the Australasian Association of Bioethics and Health Law.
University of Melbourne provides funding as a founding partner of The Conversation AU.
View all partners
The latest large-scale ransomware attack on a health technology provider, electronic prescription company MediSecure, was revealed last week.
MediSecure announced it had suffered a “cyber security incident” affecting people’s personal and health information. Details of the attack are scant. We’ve been told it stemmed from a “third-party vendor”, which means a company that provides services to another company.
In a general sense, ransomware attacks occur when a hacker gets access to a system, infects and locks up files , and then demands a ransom – usually in cryptocurrency – for their release.
Government agencies including the National Cyber Security Coordinator and Australian Federal Police are investigating the incident.
Cybercrime is big business, generating huge profits . This latest incident shines a light on the vulnerability of health data specifically.
What are e-prescriptions?
E-prescribing works by sending prescriptions to a digital exchange, essentially a secure database of prescription information. From there, patients control which pharmacy can access it , by showing pharmacy staff a token such as a QR code or barcode.
Electronic prescriptions contain personal information such as people’s name, address, date of birth and Medicare number. They include details about prescribed medicines, as well as the prescriber’s name, address and other information.
The Digital Health Agency (an agency of the Australian government) reports that over the past four years, more than 189 million e-prescriptions have been issued by more than 80,000 clinicians.
Until late 2023, MediSecure was one of two national e-prescribing services, delivering prescriptions from health-care providers to pharmacies.
Last year, MediSecure was overlooked in a government tender process to appoint a single national e-prescribing provider. At that time, MediSecure held more than 28 million scripts .
MediSecure has noted the incident relates to data held by its systems up until November 2023 .
While it’s unclear who has been affected by this breach, the potential pool of patients and prescribers involved is large.
A worrying trend
This incident, which comes less than two years after the widely publicised Medibank hack , is alarming but unfortunately not surprising.
Health care is digitising rapidly, with innovations such as patient-accessible electronic health records, remote monitoring and wearable devices. These developments can make health care more efficient and effective. They improve people’s access to care, and mean that information – such as prescriptions – is readily available where and when it’s needed.
Partly because of the scale of digital health data, breaches are very common. The Office of the Australian Information Commissioner routinely reports that health services suffer the most breaches of any sector, mainly through malicious or criminal attacks.
Why is health data so lucrative?
Health data is very attractive to hackers because of its volume, and ease of access via system vulnerabilities . Historical under-investment in IT security in the sector, understaffing and overstretched staff (leading to human error), and high connectivity, all contribute to this risk.
Health data is also easy to ransom because of the value patients, clinicians and health organisations place on keeping it private. No one wants a repeat of the Medibank ransomware attack , where Australians’ most sensitive health information – such as drug treatment or pregnancy termination details – was published online.

Beyond finding out how the MediSecure attack happened, patients want to know how to protect themselves from harm. At present it seems too early to say . The initial advice from the government is that no action is required.
Unfortunately, the usual measures we use to protect against hacks of financial and identity data don’t work for health data. We cannot change our prescription or other medical history like we might change our passwords, get a new driver’s licence, or scrutinise our bank statements for fraud.
If someone’s medication history is released it may indicate things about their health status, such as mental illness, gender transitioning, fertility treatment or care for drug and alcohol addiction. Not much can be done to stop the personal distress and stigmatisation that may follow. People may be blackmailed through this information, or suffer harms such as discrimination.
Data breach notification is a legal requirement on organisations to inform individuals about breaches affecting their data. It was touted as a solution to the problem of hacking when laws were introduced in Australia in 2018, but it doesn’t help affected people very much in this situation. Being informed your prescription for an anxiety medication or a treatment for obesity is now public knowledge might simply cause greater distress.
Where does responsibility lie?
Hacking is a major threat to organisations holding health data, and the onus must largely be on them to protect against it. They must all have rigorous cyber-security protections, the capacity to respond rapidly when attacks take place, and resilience measures such as backups to restore systems quickly.
Patients are now taking steps against companies who don’t protect their data. In the case of Medibank, affected customers have launched several class actions with the national privacy regulator and under Australian corporations and consumer law .
The introduction of a right to sue for serious invasions of privacy under an amended Privacy Act is an important, impending, change. It would mean people whose prescriptions and other sensitive health information were hacked could pursue breached companies for damages.
Companies facing heightened cyber threats, increased regulatory scrutiny and legal claims by those whose data has been breached find themselves in a tight spot. But so do patients, who watch unfolding news of the MediSecure attack, waiting to find out what information about their health may soon be on public display.
- Health data
- Data breaches
- Health in the news

Head, School of Psychology

Senior Lecturer (ED) Ballarat

Senior Research Fellow - Women's Health Services

Lecturer / Senior Lecturer - Marketing

Assistant Editor - 1 year cadetship
Healthcare company WebTPA discloses breach affecting 2.5 million people

A Texas-based company that provides health insurance and benefit plans disclosed a data breach affecting almost 2.5 million people, some of whom had their Social Security number stolen.
WebTPA said in a data breach notice published earlier this month that the company detected “evidence of suspicious activity” on December 28, 2023, which prompted the company to launch an investigation “to mitigate the threat and further secure our network.”
The investigation, the company said, “concluded that the unauthorized actor may have obtained personal information between April 18 and April 23, 2023,” approximately eight months before the company detected the breach.
“The information that was impacted may have included name, contact information, date of birth, date of death, Social Security number, and insurance information. Not every data element was present for every individual,” the company wrote in the notice posted on its website.
WebTPA reported the breach to the U.S. Department of Health and Human Services earlier this month on May 8, according to the federal department’s website . In this report, WebTPA disclosed that the breach affected 2,429,175 individuals and that the breach occurred on a “network server.”
TechCrunch asked the company to clarify exactly how many people had their Social Security numbers stolen, among other questions. WebTPA did not respond to multiple requests for comment.
WebTPA also said that it is not aware of “any misuse of benefit plan member information,” and that financial account information, credit card numbers as well as “treatment or diagnostic information” were not impacted in the breach.
Do you know more about this WebTPA breach? Or similar data breaches? From a non-work device, you can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, or via Telegram, Keybase and Wire @lorenzofb, or email. You also can contact TechCrunch via SecureDrop .
More TechCrunch
Get the industry’s biggest tech news, techcrunch daily news.
Every weekday and Sunday, you can get the best of TechCrunch’s coverage.
Startups Weekly
Startups are the core of TechCrunch, so get our best coverage delivered weekly.
TechCrunch Fintech
The latest Fintech news and analysis, delivered every Tuesday.
TechCrunch Mobility
TechCrunch Mobility is your destination for transportation news and insight.
China’s $47B semiconductor fund puts chip sovereignty front and center
China has closed a third state-backed investment fund to bolster its semiconductor industry and reduce reliance on other nations, both for using and for manufacturing wafers — prioritizing what is…

Apple’s Design Awards nominees highlight indies and startups, largely ignore AI (except for Arc)
Apple’s annual list of what it considers the best and most innovative software available on its platform is turning its attention to the little guy.

Spyware maker pcTattletale shutters after data breach
The spyware maker’s founder, Bryan Fleming, said pcTattletale is “out of business and completely done,” following a data breach.

AI models have favorite numbers, because they think they’re people
AI models are always surprising us, not just in what they can do, but what they can’t, and why. An interesting new behavior is both superficial and revealing about these…

Rock band’s hidden hacking-themed website gets hacked
On Friday, Pal Kovacs was listening to the long-awaited new album from rock and metal giants Bring Me The Horizon when he noticed a strange sound at the end of…

Anthropic hires former OpenAI safety lead to head up new team
Jan Leike, a leading AI researcher who earlier this month resigned from OpenAI before publicly criticizing the company’s approach to AI safety, has joined OpenAI rival Anthropic to lead a…
The demise of BaaS fintech Synapse could derail the funding prospects for other startups in the space
Welcome to TechCrunch Fintech! This week, we’re looking at the long-term implications of Synapse’s bankruptcy on the fintech sector, Majority’s impressive ARR milestone, and more! To get a roundup of…

YouTube’s free games catalog ‘Playables’ rolls out to all users
YouTube’s free Playables don’t directly challenge the app store model or break Apple’s rules. However, they do compete with the App Store’s free games.

Featured Article
A comprehensive list of 2024 tech layoffs
The tech layoff wave is still going strong in 2024. Following significant workforce reductions in 2022 and 2023, this year has already seen 60,000 job cuts across 254 companies, according to independent layoffs tracker Layoffs.fyi. Companies like Tesla, Amazon, Google, TikTok, Snap and Microsoft have conducted sizable layoffs in the first months of 2024. Smaller-sized…

OpenAI’s new safety committee is made up of all insiders
OpenAI has formed a new committee to oversee “critical” safety and security decisions related to the company’s projects and operations. But, in a move that’s sure to raise the ire…

Early bird gets the savings — 4 days left for Disrupt sale
Time is running out for tech enthusiasts and entrepreneurs to secure their early-bird tickets for TechCrunch Disrupt 2024! With only four days left until the May 31 deadline, now is…

Skej’s AI meeting scheduling assistant works like adding an EA to your email
AI may not be up to the task of replacing Google Search just yet, but it can be useful in more specific contexts — including handling the drudgery that comes…

Faircado raises $3M to nudge people to buy pre-owned goods
Faircado has built a browser extension that suggests pre-owned alternatives for ecommerce listings.

Tumblr launches its semi-private Communities in open beta
Tumblr, the blogging site acquired twice, is launching its “Communities” feature in open beta, the Tumblr Labs division has announced. The feature offers a dedicated space for users to connect…

Félix Pago raises $15.5 million to help Latino workers send money home via WhatsApp
Remittances from workers in the U.S. to their families and friends in Latin America amounted to $155 billion in 2023. With such a huge opportunity, banks, money transfer companies, retailers,…

Google adds AI-powered features to Chromebook
Google said today it’s adding new AI-powered features such as a writing assistant and a wallpaper creator and providing easy access to Gemini chatbot to its Chromebook Plus line of…

The Chainsmokers light up Disrupt 2024
The dynamic duo behind the Grammy Award–winning music group the Chainsmokers, Alex Pall and Drew Taggart, are set to bring their entrepreneurial expertise to TechCrunch Disrupt 2024. Known for their…

LumApps, the French ‘intranet super app,’ sells majority stake to Bridgepoint in a $650M deal
The deal will give LumApps a big nest egg to make acquisitions and scale its business.

More neobanks are becoming mobile networks — and Nubank wants a piece of the action
Nubank is taking its first tentative steps into the mobile network realm, as the NYSE-traded Brazilian neobank rolls out an eSIM (embedded SIM) service for travelers. The service will give customers access to 10GB of free roaming internet in more than 40 countries without having to switch out their own existing physical SIM card or…

MARS doubles down on India’s Infra.Market with new $50M investment
Infra.Market, an Indian startup that helps construction and real estate firms procure materials, has raised $50M from MARS Unicorn Fund.

Cloover wants to speed solar adoption by helping installers finance new sales
Small operations can lose customers by not offering financing, something the Berlin-based startup wants to change.

Adani looks to battle Reliance, Walmart in India’s e-commerce, payments race, report says
India’s Adani Group is in discussions to venture into digital payments and e-commerce, according to a report.

Ledger starts shipping its high-end hardware crypto wallet
Ledger, a French startup mostly known for its secure crypto hardware wallets, has started shipping new wallets nearly 18 months after announcing the latest Ledger Stax devices. The updated wallet…

EU’s ChatGPT taskforce offers first look at detangling the AI chatbot’s privacy compliance
A data protection taskforce that’s spent over a year considering how the European Union’s data protection rulebook applies to OpenAI’s viral chatbot, ChatGPT, reported preliminary conclusions Friday. The top-line takeaway…

LatAm startups: Apply to Startup Battlefield 200
Here’s a shoutout to LatAm early-stage startup founders! We want YOU to apply for the Startup Battlefield 200 at TechCrunch Disrupt 2024. But you’d better hurry — time is running…

5 days left to get your early-bird Disrupt passes
The countdown to early-bird savings for TechCrunch Disrupt, taking place October 28–30 in San Francisco, continues. You have just five days left to save up to $800 on the price…

Spanish startups reached €100 billion in aggregate value last year
Venture investment into Spanish startups also held up quite well, with €2.2 billion raised across some 850 funding rounds.

Onyx Motorbikes was in trouble — and then its 37-year-old owner died
James Khatiblou, the owner and CEO of Onyx Motorbikes, was watching his e-bike startup fall apart. Onyx was being evicted from its warehouse in El Segundo, near Los Angeles. The company’s unpaid bills were stacking up. Its chief operating officer had abruptly resigned. A shipment of around 100 CTY2 dirt bikes from Chinese supplier Suzhou…

Iyo thinks its GenAI earbuds can succeed where Humane and Rabbit stumbled
Iyo represents a third form factor in the push to deliver standalone generative AI devices: Bluetooth earbuds.

Women in AI: Arati Prabhakar thinks it’s crucial to get AI ‘right’
Arati Prabhakar, profiled as part of TechCrunch’s Women in AI series, is director of the White House Office of Science and Technology Policy.


IMAGES
COMMENTS
The total number of healthcare records that were exposed, stolen, or illegally disclosed in the year 2019 was 41.2 million in 505 healthcare data breaches [ 8 ]. According to an IBM report, the average cost of a data breach in 2019 was $3.92 million, while a healthcare industry breach typically costs $6.45 million [ 9 ].
The CVS medical data breach in March of 2021 was a source of anxiety, fear, and anger in many users, leading to lower customer loyalty. Our study found that their websites used misconfigured databases, allowing an adversary to steal healthcare data through session hijacking attacks. Customers' search metadata containing email addresses ...
The 14 Biggest Data Breaches in Healthcare Ranked by Impact. Each listed event is supported with a summary of the data that was comprised, how the breach occurred, and key learnings to protect you from suffering a similar fate. 1. Tricare Data Breach. Date: September 2011.
These challenges encompass data breaches, unauthorised access, ransomware attacks and the potential misuse of patient data. ... Analysis of security incidents in healthcare: Lessons learned from case studies. Journal of Medical Systems, 43(5), 1-9. Google Scholar. Lyles C. R., Sarkar U., Schillinger D., Ralston J. D., Allen J. Y., Nguyen R ...
More than 10 billion records were exposed from different sectors from 2005 to 2019. These sectors were MED, BSF, BSO, EDU, NGO, BSR, and GOV. There have been 3912 confirmed data breach cases in the healthcare sector alone. Nearly 43.38% of health data was compromised from 2005 to 2019, the highest among all sectors.
Resource Library. Preventing HIPAA Data Breaches: Case Studies and Best Practices. The healthcare industry experiences more data breaches (confirmed data disclosure) than any other industry in the United States, accounting for more than 24% of all breaches. 1 In 2017, healthcare data breaches compromised more than 5 million healthcare records 2 ...
Data breaches continue to plague most industries but especially the healthcare sector. While previous studies have aimed at assessing the financial implications arising from data breaches, none of them focused on the healthcare sector. This study of market reactions following data breaches fills that gap. Federal disclosure requirements of data breaches within the healthcare sector allow for ...
Healthcare Data Breaches by Year. Between 2009 and 2023, 5,887 healthcare data breaches of 500 or more records were reported to OCR. Those breaches have resulted in the exposure or impermissible disclosure of 519,935,970 healthcare records. That equates to more than 1.5x the population of the United States. In 2018, healthcare data breaches of ...
The total number of healthcare records that were exposed, stolen, or illegally disclosed in the year 2019 was 41.2 million in 505 healthcare data breaches [8]. According to an IBM report, the average cost of a data breach in 2019 was $3.92 million, while a healthcare industry breach typically costs $6.45 million [9].
Health care data breaches occur due to unauthorized access to patients' health records that violate the privacy and security of confidential health information. Therefore, this study aimed to use Microsoft Power BI tools to conduct in-depth data analytics and visualization on healthcare data breaches to determine the causes of the breach and ...
The hacking shut down the nation's biggest health care payment system, causing financial chaos that affected a broad spectrum ranging from large hospitals to single-doctor practices.
Cerebral: 3,179,835 Individuals Impacted. Online mental healthcare platform Cerebral notified more than 3.1 million users of a data breach that stemmed from its use of tracking pixels. As ...
The Department of Health and Human Services' Office for Civil Rights (OCR) breach portal shows a 12% month-over-month reduction in the number of 66 healthcare data breaches of 500 or more records were reported to the HHS' Office for Civil Rights in June. Across those breaches, more than 5 million healthcare records were exposed or impermissibly disclosed.
The diagram shows a significant increase annually in the healthcare data breach cases. Fig. 2. Individuals affected by healthcare data breaches [4] Fig. 2 Alt Text: A diagram shows the number of individuals that are affected by healthcare data breaches from 2009 to 2020. The diagram shows that the major healthcare data breaches occured in 2015 ...
A recent data breach study estimates that these security breaches cost the healthcare industry more than $5.5 billion each year; this number is expected to continue to grow as new EMR and ePHI technology continues to be developed and adopted by the healthcare industry.
The CVS medical data breach in March of 2021 was a source of anxiety, fear, and anger in many users, leading to lower customer loy-alty. Our study found that their websites used misconfigured databases, allowing an adversary to steal healthcare data through session hijacking attacks. Customers' search metadata containing email addresses, pre ...
The authors of this study have also compiled the data of healthcare breaches published by the HIP AA journal from 2010 to 2019. The data were outsourced and analyzed from di ff erent monthly ,
The breach incident involving Change Healthcare serves as a critical case study highlighting the importance of cybersecurity and data protection in the healthcare industry. Here's an overview of the Change Healthcare breach as a case study, presented by Prima Systems, a leading healthcare BPO company committed to the highest standards of data ...
Healthcare data breaches fell 43% month-over-month, with 54 data breaches of 500 or more records reported to the HHS' Office for Civil Rights. That's the Healthcare data breaches fell by 43% in April to a 2024 low of 54 breaches; however, there was a 416% increase in breached records. More than 15 million individuals had their PHI exposed or impermissibly disclosed.
A joint investigation into the massive 2019 LifeLabs' healthcare data breach impacting 15 million patients found the vendor lacked adequate security programs and policies to protect patient data.
Data breach notification is a legal requirement on organisations to inform individuals about breaches affecting their data. It was touted as a solution to the problem of hacking when laws were ...
A pair of recent ransomware attacks crippled computer systems at two major American health care firms, disrupting patient care and exposing fundamental weaknesses in the US health care system's ...
The healthcare industry suffers more data breaches than any other business segment—a total of 51 percent of all breaches. This video presents an overview of ...
May 20, 2024 - More than 2.4 million individuals were affected by a healthcare data breach that occurred at WebTPA Employer Services, a third-party administrator that processes health plan claims.
A Texas-based company that provides health insurance and benefit plans disclosed a data breach affecting almost 2.5 million people, some of whom had their Social Security number stolen.
Providers are urging the HHS to publicly confirm that Change Healthcare parent company UnitedHealth Group could handle data breach reporting and notification requirements after a major cyberattack ...
A study published in the academic journal JAMA Network found that over half of the 1,138 data breaches reported to the U.S. Department of Health and Human Services between 2009 and 2017 could be ...