- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial

Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
- Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
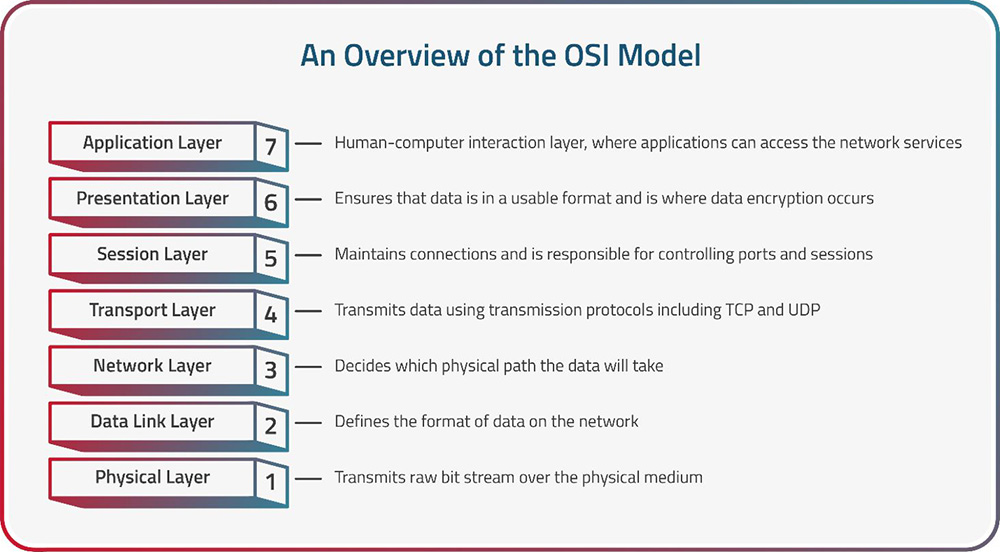
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.
Please Login to comment...
Similar reads.

Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.
OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.

Computer Network
- Operating Systems
- Computer Fundamentals
- Interview Q
Physical Layer
Data link layer, network layer, routing algorithm, transport layer, application layer, application protocols, network security.
Interview Questions
- Send your Feedback to [email protected]
Help Others, Please Share

Learn Latest Tutorials
Transact-SQL
Reinforcement Learning
R Programming
React Native
Python Design Patterns
Python Pillow
Python Turtle
Preparation

Verbal Ability

Company Questions
Trending Technologies
Artificial Intelligence
Cloud Computing
Data Science
Machine Learning
B.Tech / MCA
Data Structures
Operating System
Compiler Design
Computer Organization
Discrete Mathematics
Ethical Hacking
Computer Graphics
Software Engineering
Web Technology
Cyber Security
C Programming
Control System
Data Mining
Data Warehouse

PrepBytes Blog
ONE-STOP RESOURCE FOR EVERYTHING RELATED TO CODING
Sign in to your account
Forgot your password?
Login via OTP
We will send you an one time password on your mobile number
An OTP has been sent to your mobile number please verify it below
Register with PrepBytes
Presentation layer in osi model.
Last Updated on March 7, 2024 by Abhishek Sharma

The OSI (Open Systems Interconnection) model is a conceptual framework used to understand the functions of a telecommunication or computing system. It consists of seven layers, each responsible for specific tasks. The sixth layer, known as the Presentation Layer, plays a crucial role in ensuring that data exchanged between systems is readable and usable. Let’s explore the functions and importance of the Presentation Layer in the OSI model.
What is Presentation Layer in OSI Model?
The Presentation Layer, the sixth layer of the OSI (Open Systems Interconnection) model, is responsible for ensuring that data exchanged between systems is in a format that can be interpreted and used by the receiving system. It performs various functions, including data translation, encryption, compression, and formatting, to facilitate efficient and secure communication between networked devices.
Functions of the Presentation Layer
Below are some of the functions of the Presentation Layer in OSI Model:
- Data Translation: The Presentation Layer translates data from the format used by the application layer into a format that can be transmitted over the network. This includes encoding, compression, and encryption.
- Data Formatting: It ensures that data is formatted according to the specifications of the application layer. This includes converting between different character sets, such as ASCII and Unicode.
- Data Compression: The Presentation Layer compresses data to reduce the amount of bandwidth required for transmission, improving network efficiency.
- Data Encryption: It encrypts data to ensure that it remains secure during transmission, protecting it from unauthorized access.
- Data Syntax: The Presentation Layer defines the syntax for data representation, ensuring that both the sender and receiver understand the structure of the data being exchanged.
Importance of the Presentation Layer
Importance of Presentation Layer are:
- Data Integrity: By ensuring that data is formatted correctly and encrypted, the Presentation Layer helps maintain the integrity of data during transmission.
- Interoperability: The Presentation Layer enables different systems to communicate with each other by ensuring that data is translated into a common format that both systems understand.
- Efficiency: Data compression reduces the amount of data that needs to be transmitted, improving network efficiency and reducing bandwidth requirements.
- Security: Encryption provided by the Presentation Layer ensures that data remains secure and protected from unauthorized access.
Conclusion The Presentation Layer is a crucial component of the OSI model, responsible for ensuring that data exchanged between systems is in a format that can be understood and used. By performing functions such as data translation, formatting, compression, and encryption, the Presentation Layer plays a vital role in maintaining data integrity, facilitating interoperability, and ensuring the security of data during transmission.
FAQs related to Presentation Layer in OSI Model
Here are some of the FAQs related to Presentation Layer in OSI Model:
Q1: What is the role of the Presentation Layer in the OSI model? The Presentation Layer ensures that data exchanged between systems is in a usable format, performing functions such as data translation, encryption, compression, and formatting.
Q2: How does the Presentation Layer ensure data security? The Presentation Layer encrypts data before transmission, making it unreadable to unauthorized parties, thus ensuring data security.
Q3: Why is data compression important in the Presentation Layer? Data compression reduces the size of data packets, leading to faster transmission speeds and optimized bandwidth usage, which is crucial in high-traffic networks.
Q4: How does the Presentation Layer facilitate interoperability between systems? By translating data into a common format that both sender and receiver understand, the Presentation Layer enables different systems to communicate with each other seamlessly.
Q5: Can the Presentation Layer be bypassed in data transmission? While it is possible to bypass the Presentation Layer in some cases, doing so can lead to compatibility issues between systems and is not recommended.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Linked List
- Segment Tree
- Backtracking
- Dynamic Programming
- Greedy Algorithm
- Operating System
- Company Placement
- Interview Tips
- General Interview Questions
- Data Structure
- Other Topics
- Computational Geometry
- Game Theory
Related Post
Quantum cryptography, introduction to sniffers, multiplexing and demultiplexing in transport layer, transport layer responsibilities, tacacs+ and radius.

Unveiling the Interpreter: Fortifying the Presentation Layer’s Role in Cybersecurity
- March 28, 2024
Cherise Esparza
Welcome back to Tea with C. As we navigate deeper into the OSI model, today’s spotlight shines on Layer 6: the Presentation Layer. The Presentation Layer, often likened to an adept interpreter in the digital realm, plays a pivotal role in the seamless transmission and reception of data across the network.
At its essence, the Presentation Layer is tasked with data translation, encryption, and compression. It ensures that the information sent from the application layer is suitably formatted for transmission across the network and can be accurately interpreted by the receiving system. This layer is a universal translator for network communications, bridging different data formats into a universally understood language.
Encryption protocols at this layer are vital for securing data at rest and in transit. They are the bedrock of data integrity and confidentiality, shielding sensitive information from prying eyes and potential cyber threats. This is where the magic of transforming data into a secure format occurs, making it an essential battleground for cybersecurity efforts.
However, the Presentation Layer is not without its vulnerabilities. Some of the most insidious security threats stem from weaknesses in the coding practices used to develop applications interacting at this layer. Buffer overflows, SQL injections, and cross-site scripting are prime examples of exploits that can lead to significant security breaches. These vulnerabilities underscore the critical importance of secure coding practices and robust input validation procedures to fend off attackers.
The roles vital to securing the Presentation Layer span a broad spectrum of cybersecurity expertise. Network security analysts play a key role in scrutinizing the data exchange protocols and ensuring that encryption measures are robust and correctly implemented. Developers adhere to a secure development lifecycle, ensuring that code is thoroughly vetted and sanitized before deployment. Lastly, the overarching vigilance of security analysts dedicated to network monitoring and logging forms the backbone of a comprehensive security strategy at this layer.
Ensuring the security of the Presentation Layer is a multifaceted challenge that requires a concerted effort from all parties involved in the development and deployment of network applications. As we gear up for our following discussion on the final layer of the OSI model , the Application Layer, remember that each layer presents unique challenges and opportunities for enhancing our cybersecurity posture. Join us next week as we conclude our exploration of the OSI model.
Share this post
Recent articles.

The Enhanced “Detect” Function in CSF 2.0: A Leap Forward from the 2018 Framework
In the evolving field of cybersecurity, the ability to quickly detect anomalies and cybersecurity events is crucial for maintaining the integrity of organizational assets. The

Fortifying Cybersecurity: Unpacking the Enhancements in CSF 2.0’s ‘Protect’ Function
The need for robust cybersecurity measures has never been more apparent in the rapidly advancing digital landscape. With cyber threats becoming increasingly sophisticated, the National

SecurityGate Unveils New Channel Program
HOUSTON, April 16, 2024 /PRNewswire/– SecurityGate, the provider of the leading SaaS platform for OT cyber improvement, is excited to announce the launch of its new

Deep Dive into the “Identify” Function: Transitioning from the 2018 Framework to CSF 2.0
Understanding an organization’s digital assets and systems in the ever-changing cybersecurity landscape is crucial to ensure effective security. The “Identify” function of the National Institute

Announcing General Availability of ISA/IEC 62443-2-1 Workflow in the SecurityGate Platform
We are thrilled to share that we have added ISA/IEC 62443-2-1 to the SecurityGate Platform. This update will assist users in creating a robust IACS

The Evolution of the Govern Function in the Cybersecurity Framework: A Closer Look at CSF 2.0
In the realm of cybersecurity, staying ahead of threats necessitates not just reactive measures but a proactive and structured approach to safeguarding digital assets. The
5120 Woodway Dr. Suite 9003 Houston, TX 77056
SecurityGate c/o Talent Garden Calabiana Via Arcivescovo Calabiana, 6, 20139 Milano, Italy
- Privacy Policy
- Terms of Service
- Support Terms
Platform Tour
Channel program, case studies, the business of cyber series.

Presentation Layer Of OSI Model For Beginners
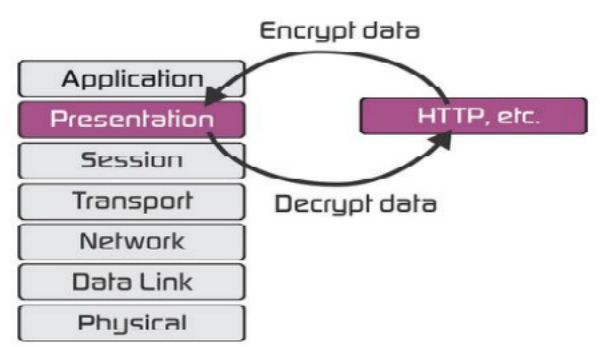
Presentation Layer:
Presentation Layer is the sixth layer in the OSI model and here are some of the functionalities of the presentation layer:
Translation
Before being transmitted, the data remains in the form of characters and numbers. This data has to be changed to bitstreams before transmission. The presentation layer is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats that a network requires and the format a computer needs.
It carries out the process of encryption at the transmitter end and the process of decryption at the receiver end.
Encryption and decryption are ways to protect the confidentiality of the data stored on computer systems or wired over the internet or other computer networks.
Also Read: Network Layer Of OSI Mode: Functionalities and Protocols
In terms of security, modern-day encryption methods play a vital role in the security assurance of IT systems and communications as they can provide not only confidentiality but also, authentication and integrity.
Data compression
Data compression is also known by different names like source coding or bit-rate reduction. As evident from these names, data compression involves encoding information using fewer bits than the original representation. So in this way, the data compression can be either lossy or lossless.
Even though lossless compression reduces bits by identifying and eliminating statistical redundancy, no data information is lost in the lossless compression.
On the other hand, the lossy compression reduces bits by identifying unnecessary information and removing it.
Data compression is useful in computer networks because it helps in the following ways:
- Reducing resource usages such as data storage space or transmission capacity. B
- Reducing the need for an expensive hardware for the data representation. For example, if a video is highly compressed before transmission, an expensive hardware might be required to decompress the video data before playing it.
Thus, data compression is also very helpful in real-time applications over the internet like real-time video or audio streaming.
Data conversion
There are different types of operating systems such as Windows, Linux, Mac OS etc. are being used all around the world. Data conversion is, thus, responsible for the conversion of computer data from one format to another.
Different computers encode data in different ways on the basis of certain standards. On top of that, each computer program handles data in a different manner. Data conversion comes in handy in those situations when the representation of data is needed on different platforms.
The presentation layer can be composed of two sublayers: common application service element (CASE) and specific application service element (SASE).
Also Read: LLC Layer (Logical Link Control): Data Link Layer Of OSI Model
The common application service element sublayer provides services for the application layer and request services from the session layer. It provides support for common application services whereas the specific application service element sublayer provides application specific services (protocols) like remote database access, file transfer, virtual terminal.
If you have any comments or thoughts related to it, feel free to ask and correct us. Also, don’t miss our complete coverage on the Computer networks .
A passionate adventure traveller over Trekkerpedia.com and Author of the book 'The Girl from the Woods'.
Similar Posts

What Is Anime? What Is The Most Popular Anime?
Why is this medium so popular?
![data translation in presentation layer Who Is Travis Kalanick, Former CEO Of Uber? [Super Pumped TV Series]](https://fossbytes.com/wp-content/uploads/2022/05/travis-kalanick-uber-ceo-super-pumped-768x432.jpg)
Who Is Travis Kalanick, Former CEO Of Uber? [Super Pumped TV Series]
The controversial man behind Uber.
~ For Home And / For Root Directories In Linux And Mac: Why Were These Symbols Chosen?
f you’re reading this article, I’m assuming that either you’re a Linux beginner who is busy…

What Is Rooting A Phone, Jailbreaking, And Custom ROM?
Say hello to new possibilities by Rooting/Jailbreaking your Android/iOS devices.

Is Artificial Intelligence Dependency The Future Of AI?
Will our choices be reduced to 0s and 1s?
What Is A Memory Management Stop Code? How Do I Fix Memory Management BSOD?
Looking for a fix for this pesky “Blue Screen Of Death?” Here’s a comprehensive guide to help you out.

- Data Structure
- Coding Problems
- C Interview Programs
- C++ Aptitude
- Java Aptitude
- C# Aptitude
- PHP Aptitude
- Linux Aptitude
- DBMS Aptitude
- Networking Aptitude
- AI Aptitude
- MIS Executive
- Web Technologie MCQs
- CS Subjects MCQs
- Databases MCQs
- Programming MCQs
- Testing Software MCQs
- Digital Mktg Subjects MCQs
- Cloud Computing S/W MCQs
- Engineering Subjects MCQs
- Commerce MCQs
- More MCQs...
- Machine Learning/AI
- Operating System
- Computer Network
- Software Engineering
- Discrete Mathematics
- Digital Electronics
- Data Mining
- Embedded Systems
- Cryptography
- CS Fundamental
- More Tutorials...
- Tech Articles
- Code Examples
- Programmer's Calculator
- XML Sitemap Generator
- Tools & Generators

Home » Computer Network
Presentation Layer: What It Is, Design Issues, Functionalities
Description and Functions of Presentation Layer in the OSI model: In this tutorial, we are going to learn what the Presentation layer is and the Functions of the Presentation Layer in the OSI model in Computer Networking. We will also discuss the Design issues with the Presentation Layer and the working of the Presentation Layer with the help of its diagram. By Monika Jha Last updated : May 05, 2023
What is Presentation Layer?
The Presentation Layer is concerned with the syntax and semantics of the information exchanged between two communicating devices.
- The presentation layer takes care that the data is sent in that way the receiver of the data will understand the information (data) and will be able to use the data.
- Languages that are syntax can be different from the two communicating machines. In this condition, the presentation layer plays the role of translator between them.
- It is possible for two machines to communicate with different data representations, data structures to be exchanged can be defined in an abstract way.
- These abstract data structures will be managed by the presentation layer and this layer allows higher-level data structures (For example banking records), to be defined and exchanged.
This figure shows the relationship of the presentation layer to the session layer and application layer.

Design Issues with Presentation Layer
The following are the design issues with presentation layer:
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed-upon way just like a string, double, date, etc.
- It Performs Standard Encoding scheme on the wire.
Functionalities of the Presentation Layer
Specific functionalities of the presentation layer are as follows:
1. Translation
- The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams because different computers use different encoding schemes.
- The Presentation layer is responsible for compatibility between these encoding methods.
- The Presentation layer at the sender's side changes the information from its sender dependent format.
- The Presentation layer at the receiving machine changes the common format into its receivers dependent format.
Example: Convert ASCII code to EBCDIC code.
2. Encryption
- The system must be able to assure privacy regarding the message or information as it also carries sensitive information.
- Encryption means that the sender transforms the original information or message to another form, this data after encryption is known as the ciphertext and this ciphertext sends the resulting message out over the network.
- Decryption concerned with the transform of the message back to its original form. This decrypted data is known as plain text.

3. Compression
- Data Compression means reduces the number of bits to be transmitted by this reduce the bandwidth of the data.
- Data Compression becomes particularly important in the transmission of multimedia such as audio, video, text, etc.
Related Tutorials
- IPV4 Addressing | Classful and Classless Addressing
- Subnetting and Supernetting in Computer Network
- Network Address Translation (NAT) in Computer Network
- Fixed Length and Variable Length Subnet Mask (FLSM & VLSM)
- Line Configuration in Computer Network
- Transmission Modes in Computer Network
- Data Link Layer: What It Is, Sublayers, Design Issues, Functions
- Physical Layer: What It Is, Design Issues, Functions
- Network Layer: What It Is, Design Issues, Responsibilities
- Session Layer: What It Is, Design Issues, Functionalities
- Transport Layer: What It Is, Design Issues, Functions, and Example
- Optical Fiber (Fiber Optics) in Computer Network
- Unguided Transmission Media in Computer Network
- Virtual LAN (VLAN) in Computer Network
- Virtual Storage Area Networking (VSAN)
Comments and Discussions!
Load comments ↻
- Marketing MCQs
- Blockchain MCQs
- Artificial Intelligence MCQs
- Data Analytics & Visualization MCQs
- Python MCQs
- C++ Programs
- Python Programs
- Java Programs
- D.S. Programs
- Golang Programs
- C# Programs
- JavaScript Examples
- jQuery Examples
- CSS Examples
- C++ Tutorial
- Python Tutorial
- ML/AI Tutorial
- MIS Tutorial
- Software Engineering Tutorial
- Scala Tutorial
- Privacy policy
- Certificates
- Content Writers of the Month
Copyright © 2024 www.includehelp.com. All rights reserved.
Presentation Layer
Last Edited
What is the Presentation Layer?
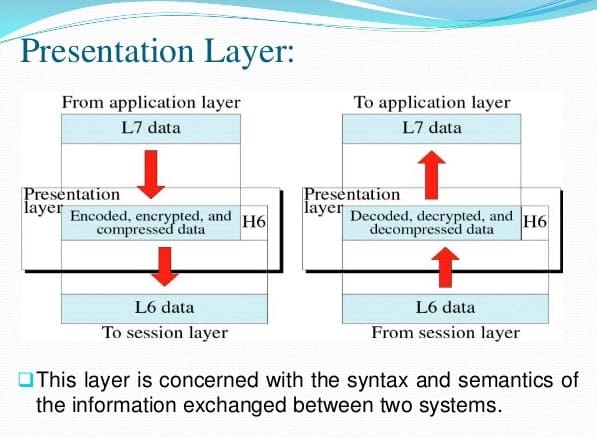
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model . The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. The network redirector also functions at this layer.
Presentation Layer functions
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. Layer 6 is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: Encryption at the transmitter and decryption at the receiver
- Compression: Data compression to reduce the bandwidth of the data to be transmitted. The primary role of data compression is to reduce the number of bits to be transmitted. Multimedia files, such as audio and video, are bigger than text files and compression is more important.
Role of Presentation Layer in the OSI Model
This layer is not always used in network communications because its functions are not always necessary. Translation is only needed if different types of machines need to talk with each other. Encryption is optional in communication. If the information is public there is no need to encrypt and decrypt info. Compression is also optional. If files are small there is no need for compression.
Explaining Layer 6 in video
Most real-world protocol suites, such as TCP/IP , do not use separate presentation layer protocols. This layer is mostly an abstraction in real-world networking.
An example of a program that loosely adheres to layer 6 of OSI is the tool that manages the Hypertext Transfer Protocol (HTTP) — although it’s technically considered an application-layer protocol per the TCP/IP model.
However, HTTP includes presentation layer services within it. HTTP works when the requesting device forwards user requests passed to the web browser onto a web server elsewhere in the network.
It receives a return message from the web server that includes a multipurpose internet mail extensions (MIME) header. The MIME header indicates the type of file – text, video, or audio – that has been received so that an appropriate player utility can be used to present the file to the user.
In short, the presentation layer
Makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there, in a closed network.
- ensures proper formatting and delivery to and from the application layer;
- performs data encryption; and
- manages serialization of data objects.
Understanding the Role of the Presentation Layer in Data Format Translation and Security
1. introduction.
According to a recent study conducted by the Institute of Electrical and Electronics Engineers (IEEE), the presentation layer is responsible for ensuring that the data is in a format that is acceptable to the application layer. This includes data compression and decompression, encryption and decryption, and character set conversion. In today’s data-driven world, the ability to effectively manage and secure data is becoming increasingly important, and understanding the role of the presentation layer in this process is crucial.
This article will explore the techniques and technologies used in the presentation layer to perform data format translation, compression and decompression, and encryption and decryption. This will include a discussion of the benefits and limitations of these techniques, as well as real-life examples and case studies of their implementation. By the end of this article, readers will have a solid understanding of the role and functions of the presentation layer in the OSI model and how it contributes to secure and efficient data transmission.
2. The role of the presentation layer
The presentation layer, also known as the syntax layer, is the sixth layer in the OSI model. It ensures that the data is in a format acceptable to the application layer. This includes data format translation, compression and decompression, encryption and decryption, and character set conversion. It acts as an interface between the application layer and the rest of the layers in the OSI model.
Data Format Translation:
The presentation layer is responsible for translating data between different formats so the application layer can understand it. For example, it may convert a file from one format, such as TIFF, to another format, such as JPEG. This ensures that the data is in a form that is compatible with the application layer and can be processed accordingly.
Compression and Decompression:
Another essential function of the presentation layer is data compression and decompression. The layer compresses the data before sending it to the next layer, the network layer. This reduces the amount of data that needs to be transmitted, reducing the time required for the data to be shared. Once the data reaches the destination, the decompression process takes place, and the data is restored to its original form. There are various compression and decompression techniques like LZ77, LZ78, and Huffman coding that are used to compress and decompress data.
3. Data compression and decompression techniques
Data compression and decompression are essential functions of the presentation layer in the OSI model. Compression refers to reducing the amount of data that needs to be transmitted. At the same time, decompression restores the data to its original form once it reaches the destination. The use of compression techniques can significantly reduce the amount of time required for data to be transmitted, as well as reduce the bandwidth needed for transmission.
The presentation layer’s most commonly used compression techniques include LZ77, LZ78, and Huffman coding.
LZ77 is a lossless data compression algorithm that Abraham Lempel and Jacob Ziv first introduced in 1977. It replaces repeated instances of a data string concerning the original series. LZ77 is a dictionary-based algorithm that uses a sliding window to identify and replace repeated data instances. This technique is effective at compressing data that contains many repeated patterns, but it can be less effective on highly random data.
LZ78 is another lossless data compression algorithm that Lempel and Ziv introduced in 1978. It is similar to LZ77 but uses a different data compression approach. Instead of using a sliding window, LZ78 uses a dictionary of previously encountered data strings. This approach allows LZ78 to achieve higher compression ratios than LZ77 but also requires more memory and processing power.
Huffman coding:
Huffman coding is a lossless data compression algorithm introduced by David Huffman in 1952. Huffman coding is a variable-length coding algorithm that assigns shorter codes to more frequently occurring symbols in the data. This technique is especially effective for compressing data that contains many repeating characters, such as text or DNA sequences.
Each technique has its advantages and disadvantages; LZ77 and LZ78 are simpler than Huffman coding and can be implemented quickly. With a limited amount of memory, on the other hand, Huffman coding is more efficient in terms of compression ratio, but it is more complex and memory-intensive.
In real-life examples, all three algorithms have been used in various applications. For instance, LZ77 has been used to compress data in the telecommunications industry, and LZ78 has been used in data storage devices like hard drives and flash drives. In contrast, Huffman coding compresses text, images, audio and video files.
4. Encryption and decryption in the presentation layer
Encryption and decryption are essential security measures that are used to protect sensitive information as it is transmitted over a network. In the OSI model, encryption and decryption occur at the presentation layer. The presentation layer is responsible for ensuring that the data is in a format acceptable to the application layer, and it also ensures that the information is protected during transmission.
Encryption refers to converting plain text into an unreadable form, known as ciphertext. The ciphertext can only be read and understood by someone with the correct decryption key. Decryption, on the other hand, is the process of converting ciphertext back into plain text using the right decryption key.
The importance of encryption and decryption in the presentation layer is clear, especially with the rise of cyber threats. It ensures that only authorised parties can access and understand the sensitive information being transmitted. Without encryption and decryption, sensitive data would be vulnerable to eavesdropping and tampering.
There are two main types of encryption and decryption methods that are commonly used in the presentation layer: symmetric key encryption and asymmetric key encryption.
Symmetric key encryption:
Symmetric key encryption is a method of encryption where the same key is used for both encryption and decryption. This method is fast and efficient, but it also has some drawbacks. The main disadvantage is that the key must be securely exchanged between the sender and the receiver before any encryption can occur.
Asymmetric key encryption:
Asymmetric key encryption, also known as public key encryption, is a method of encryption where a pair of keys is used. One key is used for encryption, and the other is used for decryption. This method is more secure than symmetric key encryption because the key used for encryption can be made public, while the key used for decryption is kept private.
In real life, symmetric key encryption is used for bulk encryption, for example, in the transportation of email, instant messaging and other types of data where the speed of encryption is more important than key exchange. On the other hand, Asymmetric key encryption is often used for digital signatures, online transactions and handshaking in secure connections.
5. Common Attacks on the Presentation Layer
The Presentation Layer in the OSI model ensures data security during transmission. However, like any other layer in the OSI model, it is also vulnerable to various attacks, vulnerabilities, and threats. These can have severe consequences, such as unauthorised access or manipulation of sensitive information.
One standard attack on the presentation layer is a “format string attack”. This occurs when an attacker can insert random formatting characters into a string, which can then be used to disrupt the normal execution of a program. This can lead to various consequences, including buffer overflows, which can be used to execute arbitrary code or crash the system.
Another attack that targets the presentation layer is “malicious code injection”. This occurs when an attacker can insert malicious code into a seemingly benign file or message. This can be done by exploiting vulnerabilities in data format translation or compression/decompression mechanisms. Once the malicious code is executed, it can cause various types of damage, such as data loss, unauthorised access to sensitive information, or even complete system compromise.
In addition to these specific attacks, the presentation layer is vulnerable to more general threats, such as “man-in-the-middle” or “replay” attacks. These are attacks in which an attacker intercepts and alters communications between two parties to gain unauthorised access to sensitive information. Such attacks can occur on any OSI model layer, but they are particularly dangerous when they target the presentation layer, as the attacker can manipulate or intercept data in transit.
6. How to Secure the Presentation Layer
Securing the Presentation Layer in the OSI model is crucial for protecting sensitive information during transmission. There are various security best practices that organisations can implement to protect against attacks, vulnerabilities, and threats on this layer.
One critical best practice is to keep software and systems up-to-date with the latest security patches and updates. This ensures that known vulnerabilities are fixed, making it harder for attackers to exploit them. It’s also important to regularly monitor systems and networks for signs of suspicious activity, such as unusual traffic patterns or login attempts.
Another best practice is to use secure protocols for data transmission and storage. Examples of secure protocols used at the Presentation Layer are Transport Layer Security (TLS) and Secure Sockets Layer (SSL), which encrypt communications between parties. Additionally, the use of robust encryption and decryption mechanisms, such as symmetric and asymmetric key encryption, can help protect against man-in-the-middle and replay attacks.
Enforcing strict access controls and implementing a solid data classification system can also secure the presentation layer. This includes access controls to limit who can view, modify or delete sensitive data and a data classification system which can help determine how data is handled, processed and protected.
Implementing a robust incident response plan that includes detailed procedures for identifying, containing and reporting security incidents can also be a valuable asset in case of a security breach. It’s also important to regularly train employees on security best practices and to make them aware of the importance of security in the presentation layer.
In addition, performing regular penetration testing, Vulnerability Assessments, and security audits can also help to identify and address security vulnerabilities. This can include testing the effectiveness of encryption and decryption mechanisms, evaluating the robustness of access controls, and identifying potential vulnerabilities in data format translation and compression/decompression mechanisms.
7. Conclusion
In conclusion, the presentation layer in the OSI model is a critical component in the data transmission process. Its functions include data format translation, data compression and decompression, and encryption and decryption. These functions are vital to ensure that the data is in a format compatible with the application layer and to protect the data during transmission.
We have discussed how the presentation layer plays a vital role in the OSI model. The techniques and technologies used in the presentation layer to perform data format translation, compression and decompression, encryption and decryption. The article also includes the advantages and disadvantages of each technique, real-life examples and case studies, if applicable, that illustrate the concepts and makes them more relatable.
The topic of the presentation layer in the OSI model is essential for anyone working in the network security and communications field, as it provides an understanding of how data is protected and formatted during transmission. We hope this article has provided a comprehensive understanding of the role and functions of the presentation layer in the OSI model.
However, it’s important to note that the Presentation Layer, like any other layer in the OSI model, is also vulnerable to various attacks, vulnerabilities, and threats. Therefore, it is crucial to implement security best practices to protect against these threats, such as keeping software and systems up-to-date with the latest security patches and updates, using secure protocols, and robust encryption and decryption mechanisms. Strict access controls, incident response plans, and regular security assessments can also help secure the Presentation Layer.
8. FAQs on the Presentation Layer
- How does the presentation layer ensure data format compatibility?
The presentation layer ensures data format compatibility by providing a set of protocols and standards for data representation and encoding. These protocols, such as ASCII or Unicode, define a standard format for data so that it can be easily understood and processed by different systems. This helps to ensure that data can be exchanged between other systems without loss of meaning or integrity.
- How does the presentation layer protect data during transmission?
The presentation layer protects data during transmission by using various encryption techniques to ensure that the data is secure as it is transmitted over a network. Encryption is the process of converting plaintext data into a coded format (ciphertext) unreadable by unauthorised parties. Standard encryption methods used at the presentation layer include SSL (Secure Sockets Layer) and TLS (Transport Layer Security).
- What are some standard encryption algorithms used in the presentation layer?
Some standard encryption algorithms used in the presentation layer include:
- RSA (Rivest-Shamir-Adleman)
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (Triple Data Encryption Standard)
- What is the difference between symmetric and asymmetric encryption in the presentation layer?
Symmetric key encryption and asymmetric key encryption are both encryption methods that are used to protect data during transmission, but they use different techniques to secure the data.
Symmetric key encryption uses a single shared key for encryption and decryption, meaning that the sender and receiver both have to use the same key to encrypt and decrypt the data.
Asymmetric key encryption, also called public-key encryption, uses a pair of keys, one for encryption (the public key) and one for decryption (the private key). So the sender uses the recipient’s public key to encrypt the data, and the recipient uses their private key to decrypt the data.
- How does the presentation layer handle data format translation for different data types?
The presentation layer handles data format translation for different data types using a set of protocols and standards for data representation and encoding. These protocols, such as ASCII or Unicode, define a standard format for data so that it can be easily understood and processed by different systems. The presentation layer can also use data conversion algorithms to convert data between other formats, such as a Word document to a PDF.
- How does the presentation layer interact with other layers in the OSI model?
The presentation layer, the sixth layer in the OSI model, acts as an intermediary between the application layer (layer 7) and the session layer (layer 5). It is responsible for translating data between different formats and encoding schemes, and it is also responsible for compressing and decompressing data. The presentation layer communicates with the application layer to convert the data it receives into a format the application can understand. It also communicates with the session layer to establish, manage, and terminate sessions between networked devices.
- How do changes in data formats affect the presentation layer?
Changes in data formats can have a significant impact on the presentation layer, as the presentation layer is responsible for converting data between different formats. The presentation layer must be updated when data formats change to support the new design. If this is done, the presentation layer can convert the data, which may be unreadable or lost. Additionally, there are changes in the protocol or standard used in the presentation layer. In that case, it will affect the compatibility with other systems, so the sending and receiving ends have to use the same protocol. Otherwise, they would not be able to understand each other.
- How does the presentation layer handle data compression and decompression in real-time communications?
The presentation layer is responsible for compressing and decompressing data in real-time communications. Compression reduces data size to improve transmission efficiency, while decompression restores the data to its original format. The presentation layer uses various compression algorithms to compress data and the same algorithms to decompress the data when it is received.
In real-time communications, the presentation layer might use lossless compression algorithms to compress the data in order not to lose any information but at the same time still be able to compress the data to a smaller size.
- How can data integrity be maintained in the presentation layer?
Data integrity in the presentation layer can be maintained using encryption, secure hash algorithms, and error-detection codes.
Encryption is the process of converting plaintext data into a coded format (ciphertext) that is unreadable by unauthorised parties. This helps to protect data from unauthorised access and modification during transmission.
Secure hash algorithms are used to create a unique digital signature for each piece of data, which can be used to verify the integrity of the data upon receipt. This helps to detect any changes or modifications that may have occurred during transmission.
Error-detection codes are used to detect errors in the data during transmission and can help to correct these errors.
Additionally, the presentation layer can also use a digital signature or digital certificate to ensure the authenticity of data, which is the process of using a digital signature to ensure that the data is not tampered with during transmission.
- Application Security
The OSI Model: Breaking Down Its Seven Layers

Core Functions of the OSI Model
The seven layers of the osi model, the importance of the osi model, osi model vs. tcp/ip model, radware solutions for network and application security.
The OSI (Open Systems Interconnection) Model is a conceptual framework that standardizes and defines the functions of a telecommunication or networking system. It's a crucial tool in the world of networking and plays a fundamental role in understanding how data communication works across various network protocols and technologies.
The model was developed by the International Organization for Standardization (ISO) to promote interoperability and facilitate communication between different devices and systems, regardless of their manufacturers. The OSI Model is structured into seven distinct layers, each with a specific set of functions and responsibilities, as explained in the next section.
The OSI Model operates by allowing each of its seven layers to perform specific functions while relying on the services provided by the layer immediately below it. When data is transmitted from one device to another, it passes through all seven layers at the sender and then traverses all seven layers at the receiver. Here's how it works:
Data Encapsulation: Data from the application layer is encapsulated in a format specific to that layer. As it moves down the OSI Model, each layer adds its own header and possibly trailer information to the data.
Data Transmission: The data, now structured into frames or packets, is transmitted from the sender's physical layer over the physical medium to the receiver's physical layer.
Interoperability: The OSI Model promotes interoperability by providing a common framework that different vendors and technologies can adhere to. As long as devices and software follow the specifications of the OSI Model, they can communicate effectively, regardless of their origins.
Data De-encapsulation: At the receiver's end, the data goes through a process of de-encapsulation. Each layer removes its header and trailer, leaving the original data from the application layer.
Essentially, the OSI Model divides network communication into seven layers, each with specific responsibilities—as explained below—to ensure efficient data transmission and interoperability. Data passes through these layers, undergoing encapsulation and de-encapsulation, as it travels from sender to receiver, allowing for a structured and standardized approach to networking.
The OSI Model serves as a foundational framework in the field of networking, defining the fundamental functions and responsibilities necessary for successful data communication. Comprised of seven distinct layers, this model guides the way data is transmitted, received, and processed across networks. Each layer is designed with specific tasks, and collectively they work together to ensure reliable, efficient, and interoperable communication between devices and systems. In the following section, we will delve into each layer of the OSI Model, providing detailed insights into their functions, protocols, and contributions to the seamless operation of network communication.
Layer 1: Physical Layer
The Physical Layer serves as the foundation of the OSI Model, focusing on the actual transmission of data in its raw bit form over a physical medium. Its essential functions encompass:
Encoding and Signaling: Encoding bits into electrical or optical signals suitable for the chosen physical medium. For example, it decides how ‘0’ and ‘1’ bits are represented through variations in voltage levels (for copper cables) or light pulses (for optical fibers).
Bit Rate: Determining the bit rate, which is the speed at which bits are transmitted. It defines how fast data can move over the network, commonly measured in bits per second (bps).
Transmission Media: Managing the characteristics and properties of the physical medium used for data transmission. This medium can vary widely, including copper wires, fiber-optic cables, radio waves, or even satellite links.
Physical Connectors: Defining the types of physical connectors and interfaces needed for devices to connect to the network. This includes specifications for cables, plugs, and sockets.
Error Detection and Correction: Implementing basic error-detection mechanisms to ensure data integrity during transmission. While more advanced error correction is often handled by higher layers, the Physical Layer can include simple parity checks or checksums.
Transmission Modes: Determining how data is sent between devices—whether it's simplex (one-way), half-duplex (two-way but not simultaneously), or full-duplex (two-way simultaneously).
Transmission Distance: Setting limits on the distance data can travel over the physical medium before it needs to be boosted or regenerated. This is crucial for understanding the reach of a network.
Example Use Cases: The Physical Layer plays a pivotal role in various networking scenarios, including high-speed data centers, telecommunications networks, wireless communication systems, and home Wi-Fi networks. It ensures that data is transmitted reliably and efficiently over diverse physical media, optimizing network performance and integrity.
Layer 2: Data Link Layer
The Data Link Layer sits just above the Physical Layer and plays a pivotal role in network communication. Its primary responsibilities include framing data for transmission and managing MAC addresses for efficient and reliable data exchange.
Framing: One of the key functions of the Data Link Layer is to divide the stream of bits received from the Physical Layer into manageable frames. A frame is a structured unit of data, often with a header and trailer, that encapsulates the actual data along with control information. Framing helps in delineating the boundaries of data packets, allowing devices to recognize the start and end of each transmission. This process ensures that data is correctly segmented for transmission over the network.
MAC Addressing: Another vital aspect of the Data Link Layer is the management of MAC addresses. MAC addresses are unique identifiers assigned to network interface cards (NICs) or network adapters. These addresses are used to identify devices on a local network segment. When a device wants to send data to another device within the same network, it uses the recipient's MAC address to direct the frame to the correct destination. The Data Link Layer is responsible for adding the MAC address information to the frame's header.
Network Devices: The Data Link Layer is crucial for the operation of network devices like switches. Switches operate at this layer and use MAC addresses to determine how to forward frames. When a frame arrives at a switch, it examines the MAC address in the frame's header to make forwarding decisions. This capability enables switches to efficiently direct data only to the specific port where the destination device is connected, minimizing network congestion and enhancing overall network performance.
LLC (Logical Link Control): The Data Link Layer is further divided into two sub-layers: the Logical Link Control (LLC) sub-layer and the MAC sub-layer. The LLC sub-layer is responsible for managing flow control, error checking, and addressing within the Data Link Layer. It ensures that data is reliably transmitted between devices, handles error detection and correction, and manages communication between devices using various data-link protocols.
Example Use Cases: Use cases for the Data Link Layer include Ethernet communication within local networks, wireless Wi-Fi connections, point-to-point serial communication, and protocols that ensure data integrity and efficient use of the network medium. It ensures reliable and orderly data exchange, particularly within the local network segment, enhancing network performance and ensuring data integrity.
Layer 3: Network Layer
The Network Layer is the third layer in the OSI Model and serves as a critical component of network communication. Its primary role is to manage the routing of data packets from the source to the destination across multiple networks while maintaining logical addressing and path determination.
Routing Data Packets: One of the fundamental tasks of the Network Layer is to route data packets from the sender to the receiver. It accomplishes this by determining the most efficient path for data to travel through a complex network topology. Routing algorithms and protocols, such as RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol), are implemented at this layer to make routing decisions.
Logical Addressing: The Network Layer introduces logical addressing, where each device on a network is assigned a unique address known as an IP (Internet Protocol) address. IP addresses, both IPv4 and IPv6, are used for identifying devices and their network location. The Network Layer is responsible for managing these addresses, which are used for source and destination identification in data packets.
Packet Forwarding: As data packets traverse the network, the Network Layer handles packet forwarding. This involves inspecting the destination IP address in each packet's header and determining the next hop (next network device) on the route to the destination. The Network Layer also manages the encapsulation and decapsulation of data packets for transmission and reception.
Inter-Network Communication: The Network Layer is crucial for enabling communication between different networks. It acts as the boundary where data moves between local area networks (LANs) and wide area networks (WANs). Routers, which operate at this layer, play a central role in connecting disparate networks and ensuring data can traverse these boundaries.
Error Handling: While the primary responsibility for error handling lies with higher layers, the Network Layer may perform basic error detection and reporting. If a packet is found to be corrupt or undeliverable, the Network Layer may discard it or request retransmission.
Subnetting: The Network Layer allows for the division of large IP address spaces into smaller subnetworks or subnets. Subnetting aids in efficient IP address allocation, routing optimization, and network management.
Example Use Cases: The OSI Network Layer finds diverse applications in networking, notably in routing data packets across the global Internet, handling IP addressing and subnetting within local networks, securing communications through Virtual Private Networks (VPNs), managing Quality of Service (QoS) to prioritize critical traffic types, automating IP address assignment via DHCP, enabling efficient one-to-many communications via multicast routing, and interconnecting private networks over public or dedicated links. It serves as the linchpin for directing data to its destination efficiently, whether within local networks or across vast interconnected infrastructures, ensuring the reliability and security of data transmission.
Layer 4: Transport Layer
The Transport Layer, positioned as the fourth layer in the OSI Model, is primarily responsible for ensuring end-to-end communication and the reliable delivery of data between devices on different hosts across a network. It accomplishes this through various mechanisms, including segmentation, flow control, error detection, and multiplexing.
End-to-End Communication: The Transport Layer ensures that data reaches its intended destination reliably and in the correct sequence. To achieve this, it assigns a source port and a destination port to each data segment, creating what is known as a “socket.” Sockets—represented as a combination of IP address, source port, and destination port—allow multiple applications to simultaneously communicate on the same device while ensuring that data from different applications is correctly routed to its respective destination.
Segmentation: One of the key roles of the Transport Layer is to divide large messages into smaller segments, making them easier to transmit across the network. These segments are typically referred to as “packets” or “datagrams.” Segmenting data is especially important when the message is too large to fit into a single network packet.
Flow Control: Flow control mechanisms are implemented at the Transport Layer to manage the rate of data transmission between sender and receiver. This is crucial to prevent network congestion and ensure that the receiving device can process data at its own pace. Flow control can be achieved through techniques like windowing, where the sender adjusts its transmission rate based on acknowledgments from the receiver.
Error Detection and Correction: The Transport Layer employs error detection and correction techniques to ensure the integrity of data during transmission. Protocols like TCP (Transmission Control Protocol), a commonly used Transport Layer protocol, include checksums to detect errors in data segments. If errors are detected, TCP requests retransmission of the affected segments to guarantee data accuracy.
Multiplexing and Demultiplexing: Multiplexing is the process of combining multiple data streams into a single stream for transmission over the network. At the receiving end, demultiplexing separates the combined stream back into individual data streams using the destination port information in the Transport Layer header. This enables multiple applications to use the same network connection simultaneously.
Connection-Oriented vs. Connectionless: The Transport Layer supports both connection-oriented and connectionless communication. TCP is a connection-oriented protocol that establishes a reliable, bidirectional communication link before data transfer. UDP (User Datagram Protocol), on the other hand, is a connectionless protocol that sends data without prior connection setup, making it faster but less reliable compared to TCP.
Example Use Cases: Key Transport Layer use cases include the reliable and error-checked transmission of data across networks via protocols like TCP for applications such as web browsing and email. Additionally, the Transport Layer offers connectionless communication through UDP, making it ideal for real-time applications like voice and video conferencing. It manages data segmentation, reassembly, and flow control, ensuring that large files can be transmitted efficiently and without data loss. The Transport Layer also handles port-based addressing, allowing multiple services to run simultaneously on a single device, supporting various applications and facilitating secure data transfer over encrypted connections.
Layer 5: Session Layer
The Session Layer, positioned as the fifth layer in the OSI Model, is responsible for establishing, maintaining, and terminating communication sessions between devices. It plays a crucial role in ensuring that data exchange between applications is synchronized, organized, and reliable.
Session Maintenance: During an ongoing communication session, the Session Layer oversees its continuity. It manages synchronization between devices, ensuring that data is exchanged in an orderly and predictable manner. This layer also handles error recovery and retransmission of lost or corrupted data if needed, maintaining the integrity of the session.
Session Establishment: The Session Layer is responsible for initiating communication sessions between devices. This involves setting up parameters for communication, such as session identifiers, authentication, and synchronization points. Session establishment ensures that both sender and receiver are ready to exchange data.
Session Termination: Once a communication session has concluded or is no longer needed, the Session Layer facilitates its graceful termination. This involves releasing any resources allocated for the session, such as buffers or connections, and ensuring that both parties agree to end the session in a coordinated manner.
Dialog Control: The Session Layer is responsible for managing the dialog between devices, which involves determining which device can transmit and when. It helps prevent conflicts and ensures that data is exchanged in an organized and coherent manner.
Synchronization Points: In some applications, the Session Layer establishes synchronization points within the data stream, allowing devices to resume communication from specific points in case of interruptions. This is particularly useful in scenarios where large files are being transferred, and resuming from the last synchronized point reduces data loss.
Checkpointing: The Session Layer may implement checkpointing, where it periodically saves the current state of the communication session. This enables recovery from unexpected failures by allowing the session to resume from the last checkpointed state.
Example Use Cases: The Session Layer is particularly relevant in scenarios such as file transfer protocols (e.g., FTP), remote desktop connections (e.g., RDP), and online gaming, where maintaining a synchronized and reliable session is critical for a seamless user experience.
Layer 6: Presentation Layer
The Presentation Layer, positioned as the sixth layer in the OSI Model, is responsible for managing data translation, encryption, compression, and ensuring that data exchanged between applications is in a format that can be understood by both sender and receiver.
Data Translation: One of the primary functions of the Presentation Layer is to handle data translation and format conversion. This includes tasks like character encoding, where it ensures that characters from different character sets (e.g., ASCII, Unicode) are correctly represented and understood by both communicating devices. It also deals with issues like byte order, making sure that multi-byte data is arranged consistently for devices with different architectures.
Encryption and Decryption: The Presentation Layer plays a vital role in data security by providing encryption and decryption services. It can encrypt data before transmission, ensuring that sensitive information remains confidential during its journey across the network. Upon receipt, it decrypts the data, allowing the recipient to access the original content.
Data Formatting: The Presentation Layer also handles data formatting and representation, ensuring that data is structured in a way that can be easily interpreted by the receiving application. For example, it may convert data into a standard format for presentation on a web browser or a word processing application.
Compression: In scenarios where bandwidth efficiency is crucial, the Presentation Layer can compress data before transmission and decompress it at the receiving end. Data compression reduces the amount of data transmitted over the network, improving transfer speeds and reducing network congestion.
Translation Between Data Formats: When data is exchanged between applications running on different systems, the Presentation Layer can translate the data between different formats or representations to ensure compatibility. This is particularly important in heterogeneous environments with a variety of software and hardware platforms.
Example Use Cases: The Presentation Layer is particularly relevant in applications like web browsers, where it translates and renders web content (HTML, images) for display. It's also essential in secure communication, where it handles encryption and decryption of data for confidentiality.
Layer 7: Application Layer
The Application Layer, positioned as the seventh and highest layer in the OSI Model, is the interface between network services and end-user applications. It is the layer closest to the end-users and encompasses a wide range of functions that facilitate communication and interaction between applications and network services.
Application Protocols: This layer defines numerous application protocols that govern specific types of communication between applications and services. These protocols dictate how data is formatted, transmitted, and interpreted. Common application layer protocols include HTTP (for web browsing), SMTP and POP3/ IMAP (for email), and FTP (for file transfer).
User Interface: The Application Layer provides the user interface that allows individuals or software applications to interact with network services. This includes applications like web browsers, email clients, instant messaging programs, and more. The user interface ensures that users can input commands, request data, and view responses.
Data Exchange: The Application Layer is responsible for the exchange of data between applications running on different devices over a network. It ensures that data sent from one application can be correctly received and understood by another application, regardless of their operating systems or hardware platforms.
Data Presentation: Building on the work of the Presentation Layer, the Application Layer may also handle data presentation and rendering. This includes tasks such as displaying web content, rendering multimedia, or formatting documents for printing.
Security and Authentication: Security mechanisms, including user authentication and data encryption, are often implemented at the Application Layer to safeguard data and ensure that only authorized users can access certain services or resources.
Example Use Cases: The Application Layer encompasses a wide array of applications and services, ranging from web browsers, email clients, and remote desktop software to online gaming platforms, file sharing tools, and more. Essentially, any software that relies on network communication falls within the domain of the Application Layer.
The OSI Model's relevance in networking lies in its ability to serve as a universal reference framework. Here's why it's crucial:
Layered Approach: The model breaks down network communication into discrete layers, making it easier to design, develop, troubleshoot, and maintain network protocols and systems.
Standardization: It offers a standardized way to discuss and understand network communication. This standardization simplifies communication between different vendors and technologies.
Interoperability: By defining clear boundaries and responsibilities for each layer, the OSI Model promotes interoperability. Devices and software developed independently can communicate effectively if they adhere to the model's specifications.
Troubleshooting: When network issues arise, the model helps in pinpointing the layer at which the problem exists. This aids network administrators and engineers in diagnosing and resolving issues efficiently.
The OSI Model and the TCP/IP Model are two fundamental frameworks used to conceptualize and understand network architecture and communication. While both models serve as guides for designing and troubleshooting networks, they differ significantly in their approach.
The OSI Model, with its seven-layer structure, offers a comprehensive and highly structured view of networking concepts, promoting interoperability and clear separation of concerns. In contrast, the TCP/IP Model, with its four-layer structure, mirrors the practical implementation of the Internet, simplifying the model for real-world network communication. This simplification, however, can come at the cost of some of the comprehensive structure found in the OSI Model, making each model suitable for different networking contexts.
Pros and Cons of the OSI Model compared with the TCP/IP Model:
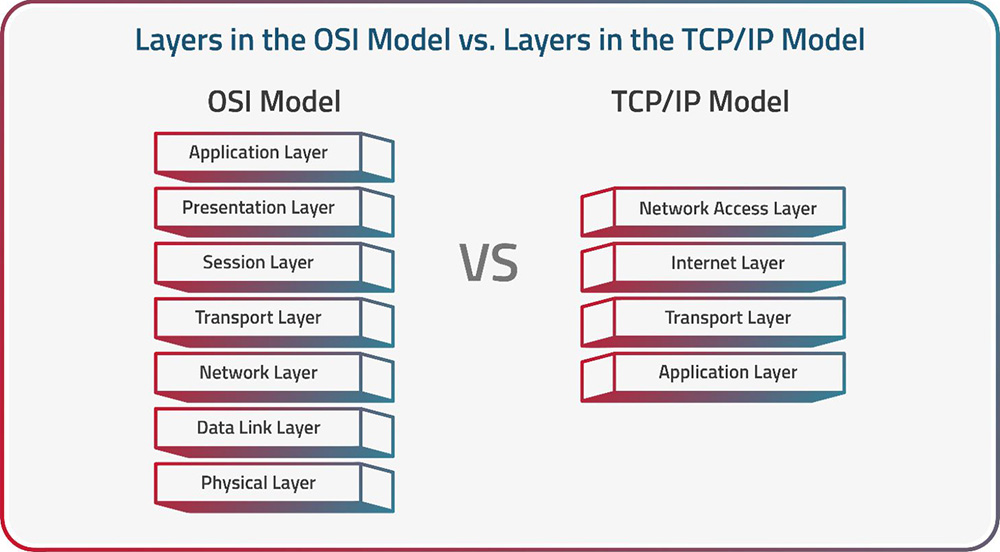
Radware's solutions seamlessly integrate with various OSI model layers to provide enhanced network and application security to protect against threats and vulnerabilities. Below are a few examples—in the context of the OSI Model—of how Radware solutions help enhance network and application security:
Transport Layer Protection:
Scenario: An e-commerce platform experiences slow performance due to a high volume of bot-generated traffic on its payment gateway.
Radware Solution: Radware Bot Manager, operating at Layer 4, employs device fingerprinting to distinguish between legitimate users and malicious bots. By identifying and blocking bot-generated requests at the transport layer, it safeguards the payment gateway from fraudulent activities.
Network Layer Protection:
Scenario: A company's network faces repeated DDoS attacks targeting the routing infrastructure, causing network disruptions.
Radware Solution: Radware's DDoS protection solutions, operating at Layer 3, use advanced traffic analysis techniques to detect and mitigate DDoS attacks in real time. By identifying and diverting malicious traffic away from critical network resources, these solutions ensure uninterrupted network availability.
Application Layer Protection:
Scenario: A healthcare provider's web application handles sensitive patient data, making it a target for cyberattacks.
Radware Solution: Radware's Application Security solutions, operating at Layer 7, provide comprehensive protection against application-layer attacks such as SQL injection and cross-site scripting (XSS). By examining application traffic patterns and using device fingerprinting, these solutions identify and block malicious activities, ensuring the security and privacy of patient data.
Secure Remote Access - Across OSI Layers:
Scenario: A financial institution needs to provide secure remote access for employees working from various locations.
Radware Solution: Radware's remote access solutions, operating across OSI layers, use device fingerprinting to ensure that only authorized and secure devices can access the institution's network. By examining device attributes and behavior, these solutions enhance security during remote access, regardless of the OSI layer.
Client Reputation - Across OSI Layers:
Scenario: An online gaming platform faces challenges with user accounts engaging in suspicious or cheating behavior.
Radware Solution: Radware's Client Reputation solution, spanning OSI layers, assesses the reputation of incoming clients based on their behavior and device characteristics. This multi-layer approach, including device fingerprinting, helps in identifying and taking action against users with a history of cheating or fraudulent activities.
6 Common Cloud Vulnerabilities That Can Lead To A Data Breach
This guide outlines 6 common cloud computing vulnerabilities that can lead to a data breach and how automation can stop it.
Radware 360° Application Protection Guide
For many organizations, the greatest concern they have about migrating their application environment to the cloud is what it may mean to their attack surface.
The State Of Web Application And API Protection
This report uses survey data to examine organizations’ application and API security awareness, visibility, best practices and security strategies and looks at how different roles within a company view app security.
Best Practices For Frictionless Application Protection
This white paper outlines the challenges organizations face when security becomes a roadblock to innovation and agility, and provides 6 best practices to follow to ensure cybersecurity remains frictionless
Contact Radware Sales
Our experts will answer your questions, assess your needs, and help you understand which products are best for your business.
Already a Customer?
We’re ready to help, whether you need support, additional services, or answers to your questions about our products and solutions.
Connect with experts and join the conversation about Radware technologies.
What are you looking for?
- Cloud Application Protection Services
- Application Protection for Any Cloud
- Bot Management
- API Protection
- Client-Side Protection
- On-Prem Application Delivery & Security
Free Assessment Tools
- API Vulnerability Scanner
- Bad Bot Analyzer
- Bad Bot Vulnerability Scanner
- Application Vulnerability Analyzer
Products & Services
- Cloud WAF Service
- Bot Manager
- Web DDoS Protection
- Alteon Integrated WAF
- Kubernetes WAF
By Industry
- Financial Services
- Open Banking
- End-to-End DDoS Protection
- Multi Layered DDoS Protection
- Encrypted Attack Protection
- Advanced Cloud Network Analytics
- Cloud Firewall-as-a-Service
- DNS DDoS Protection
- Cloud DDoS Protection Service
- Cloud Web DDoS Protection
- Threat Intelligence
- ERT Services
- Cyber Controller
- End to End Public Cloud Protection
- Cloud Security Posture Management (CSPM)
- Cloud Infrastructure Entitlement Management (CIEM)
- Cloud Threat Detection & Response (CTDR)
- Public Cloud Application Protection
- Cross-Cloud Visibility & Reporting
- Cloud Native Protector
- Application Delivery Across Hybrid Environments
- Application Delivery & Automation for DevOps
- Secured Application Delivery
- SSL Inspection, Offloading and Acceleration
- Alteon Automation For Self-service and Private Clouds
- SSL Inspection
- LinkProof NG
- DDoS Protection
- Application Protection for Service Providers
- 5G Protection Solution
- Application Delivery for Service Providers
- Managed Security Services
- DefenseFlow
- Cloud DDoS Peak Protection Service
- MSSP Portal
- White Papers
- Data Sheets
- Solution Briefs
- Infographics
- Integration Guides
- Webinars & Virtual Events
- In Person Events
- Application Delivery
- Application Protection
Software Downloads
- Alteon VA for Network Administrators
- Alteon VA for Developers
Security Research Center
- Threat Alerts
- Threat Analysis Center
- Live Threat Map
- Security Research & Reports
Local Websites
- English (US)
Please Whitelist This Site? I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :) If you like The TCP/IP Guide, please consider the download version . It's priced very economically and you can read all of it in a convenient format without ads. If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK. Thanks for your understanding! Sincerely, Charles Kozierok Author and Publisher, The TCP/IP Guide
The presentation layer is the sixth layer of the OSI Reference Model protocol stack, and second from the top. It is different from the other layers in two key respects. First, it has a much more limited and specific function than the other layers; it's actually somewhat easy to describe, hurray! Second, it is used much less often than the other layers; in many types of connections it is not required.
The name of this layer suggests its main function as well: it deals with the presentation of data. More specifically, the presentation layer is charged with taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. It also takes care of any special processing that must be done to data from the time an application tries to send it until the time it is sent over the network.
Here are some of the specific types of data handling issues that the presentation layer handles:
The reason that the presentation layer is not always used in network communications is that the jobs mentioned above are simply not always needed. Compression and encryption are usually considered “optional”, and translation features are also only needed in certain circumstances. Another reason why the presentation layer is sometimes not mentioned is that its functions may be performed as part of the application layer.
The fact that the translation job done by the presentation layer isn't always needed means that it is common for it to be “skipped” by actual protocol stack implementations. This means that protocols at layer seven may talk directly with those at layer five. Once again, this is part of the reason why all of the functions of layers five through seven may be included together in the same software package, as described in the overview of layers and layer groupings .
COMPUTER NETWORK BASICS
- Introduction To Computer Networks
- Uses of Computer Networks
- Line Configuration
- Types of Network Topology
- Transmission Modes
- Transmission Mediums
- Bounded/Guided Transmission Media
- UnBounded/UnGuided Transmission Media
- Types of Communication Networks
- Connection Oriented and Connectionless Services
- Network Layer
- Quality of Service(QoS)
- IGMP Protocol
- Reference Models
Physical Layer
- Digital Transmission
- Multiplexing
- Circuit-Switched
- Message-Switched Networks
- Packet Switching
Data link layer
- Error Correction
- Data Link Control
- Flow and Error
- Simplest Protocol
- Stop-and-Wait Protocol
- Go-Back-N Automatic Repeat
- Sliding Window Protocol
- HDLC Protocol
- Point-to-Point Protocol
- Multiple Access in DL
- Channelization Protocols
- Gigabit Ethernet
- Random Access Protocol
- Controlled Access Protocols
- Carrier Sense Multiple Access
Transport layer
- Transport Layer
- Telnet vs SSH
- UDP Protocol
- TCP - Protocol
ISO/OSI REFERENCE MODEL
- Introduction to Reference Models
- OSI Model: Physical Layer
- OSI Model: Datalink Layer
- OSI Model: Network Layer
- OSI Model: Transport Layer
- OSI Model: Session Layer
- OSI Model: Presentation Layer
- OSI Model: Application Layer
TCP/IP REFERENCE MODELCOMPUTER NETWORKS
- The TCP/IP Reference Model
- Difference between OSI and TCP/IP Model
- Key Terms - Computer Network
Session layer
- Session Layer
Computer Networks
- Components of Computer Networks
- Features of Computer Network
- Protocols and Standards
- Connection Oriented and Connectionless
- OSI Vs TCP/IP
Presentation layer
- Presentation Layer
Application layer
- HTTP Protocol
- FTP Protocol
- SMTP Protocol
- POP Protocol
- SNMP Protocol
- Electronic Mail
- MIME Protocol
- World Wide Web
- DNS Protocol
Presentation Layer - OSI Model
The primary goal of this layer is to take care of the syntax and semantics of the information exchanged between two communicating systems. Presentation layer takes care that the data is sent in such a way that the receiver will understand the information(data) and will be able to use the data. Languages(syntax) can be different of the two communicating systems. Under this condition presentation layer plays a role translator.
In order to make it possible for computers with different data representations to communicate, the data structures to be exchanged can be defined in an abstract way. The presentation layer manages these abstract data structures and allows higher-level data structures(eg: banking records), to be defined and exchanged.
Functions of Presentation Layer
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. The presentation layer is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: It carries out encryption at the transmitter and decryption at the receiver.
- Compression: It carries out data compression to reduce the bandwidth of the data to be transmitted. The primary role of Data compression is to reduce the number of bits to be 0transmitted. It is important in transmitting multimedia such as audio, video, text etc.
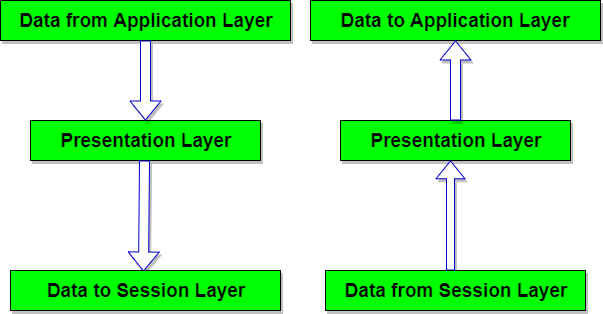
Design Issues with Presentation Layer
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed upon way. Eg: String, double, date, etc.
- Perform Standard Encoding on wire.
- ← Prev
- Next →
CN MCQ Tests
gate interview tests.
Presentation Layer: Protocols, Examples, Services | Functions of Presentation Layer
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts. Now, we will explain about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. At the end of this article, you will completely educate about What is Presentation Layer in OSI Model without any hassle.
- What is Presentation Layer?
Definition : Presentation layer is 6th layer in the OSI model , and its main objective is to present all messages to upper layer as a standardized format. It is also known as the “ Translation layer “. This layer takes care of syntax and semantics of messages exchanged in between two communication systems. Presentation layer has responsible that receiver can understand all data, and it will be to implement all data languages can be dissimilar of two communication system.

Presentation layer is capable to handle abstract data structures, and further it helps to defined and exchange of higher-level data structures.
Presentation Layer Tutorial Headlines:
In this section, we will show you all headlines about this entire article; you can check them as your choice; below shown all:
- Functions of Presentation Layer
Protocols of Presentation Layer
- Example of Presentation Layer Protocols
Presentation Layer Services
Design issues with presentation layer, faqs (frequently asked questions), what is meant by presentation layer in osi model, what protocols are used in the presentation layer, can you explain some presentation layer examples, what are the main functions of the presentation layer, what are services of presentation layer in osi, let’s get started, functions of presentation layer.
Presentation layer performs various functions in the OSI model ; below explain each one –
- Presentation layer helps to translate from American standard code for information interchange (ASCII) to the extended binary code decimal interchange code (EBCDIC).
- It deals with user interface as well as supporting for several services such as email and file transfer.
- It provides encoding mechanism for translating all messages from user dependent format with common format and vice – versa.
- It’s main goal for data encryption and decryption of entire data before they are getting transmission over all common platforms.
- It provides data compression mechanism for source point to decrease the all bits which are transmitted. Due to this data compression system, user are able to transmit enlarge multimedia file at fastest file transfer rate.
- Due to use of Data Encryption and Decryption algorithm, presentation layer provides more network protection and confidentiality while transmission data over the entire network.
- This layer offers best flexibility for data translation for making connections with various kinds of servers , computers, and mainframes over the similar network.
- Presentation layer has responsible to fix all translations in between all network systems .
Presentation layer is used various protocols; below list is available –
- Multipurpose Internet Mail Extensions
- File Transfer Protocol
- Network News Transfer Protocol
- Apple Filing Protocol (AFP)
- Independent Computing Architecture (ICA), the Citrix system core protocol
- Lightweight Presentation Protocol (LPP)
- NetWare Core Protocol (NCP)
- Network Data Representation (NDR)
- Telnet (a remote terminal access protocol)
- Tox Protocol
- eXternal Data Representation (XDR)
- 25 Packet Assembler/Disassembler Protocol (PAD)
Example of Presentation Layer Protocols:
Here, we will discuss all examples of presentation layer protocols; below explain each one –
Multipurpose Internet Mail Extensions (MIME) : MIME protocol was introduced by Bell Communications in 1991, and it is an internet standard that provides scalable capable of email for attaching of images, sounds and text in a message.
File Transfer Protocol (FTP) : FTP is a internet protocol, and its main goal is to transmit all files in between one host to other hosts over the internet on TCP/IP connections.
Network News Transfer Protocol (NNTP) : This protocol is used to make connection with Usenet server and transmit all newsgroup articles in between system over internet.
Apple Filing Protocol (AFP ) : AFP protocol is designed by Apple company for sharing all files over the entire network .
Lightweight Presentation Protocol (LPP) : This protocol is used to offer ISO presentation services on top of TCP/IP based protocol stacks.
NetWare Core Protocol (NCP) : NCP is a Novell client server model protocol that is designed especially for Local Area Network (LAN). It is capable to perform several functions like as file/print-sharing, clock synchronization, remote processing and messaging.
Network Data Representation (NDR) : NDR is an data encoding standard, and it is implement in the Distributed Computing Environment (DCE).
Telnet (Telecommunication Network) : Telnet protocol was introduced in 1969, and it offers the command line interface for making communication along with remote device or server .
Tox : The Tox protocol is sometimes regarded as part of both the presentation and application layer , and it is used for sending peer-to-peer instant-messaging as well as video calling.
eXternal Data Representation (XDR) : This protocol provides the description and encoding of entire data, and it’s main goal is to transfer data in between dissimilar computer architecture.
25 Packet Assembler/Disassembler Protocol (PAD) : Main objective of this protocol is to obtain all data from group of terminal and allots the data into X. 25 packets.
Presentation layer provides several services like as –
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
- It helps to handle and maintain Syntax and Semantics of the message transmitted.
- Encoding data can be done as standard agreed like as String, double, date, and more.
- Standard Encoding can be done on wire.
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model that is the lowest layer, where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts.
Presentation layer is used various protocols like as:
Yes! In this article, already we have been explained many examples of presentation layer; you can check them.
Presentation layer has a responsibility for formatting, translation, and delivery of the information for getting to process otherwise display .
Now, i hope that you have completely learnt about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. If this post is useful for you, then please share it along with your friends, family members or relatives over social media platforms like as Facebook, Instagram, Linked In, Twitter, and more.
Also Read: Data Link Layer: Protocols, Examples | Functions of Data Link Layer
If you have any experience, tips, tricks, or query regarding this issue? You can drop a comment!
Related Posts


COMMENTS
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over ...
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
The presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. On the sending system it is responsible for conversion to standard, transmittable formats. [7] On the receiving system it is responsible for the translation, formatting, and delivery of ...
It is a 6th layer in the OSI model that translates one data format into another data format. The presentation layer may also be called the translation layer or syntax layer. You have learned about the functions of the presentation layer, such as translation, encryption & decryption, and compression & decompression.
The Presentation Layer is a crucial component of the OSI model, responsible for ensuring that data exchanged between systems is in a format that can be understood and used. By performing functions such as data translation, formatting, compression, and encryption, the Presentation Layer plays a vital role in maintaining data integrity ...
The presentation layer in OSI model is also known as the translation layer. The OSI presentation layer receives data which it then translates and formats so that data representation in the ...
Known as a translator, the presentation layer converts data into an accurate, well-defined, standard format after it receives it from the application layer. The converted format varies, however, based on the type of data received. ... Translation. Layer 6 translates data based on the host's needs. Different hosts represent data in diverse ...
In the presentation layer, data translation is the primary activity performed. The sender's application passes data down to the presentation layer, where it is put into a common format. When the data is received on the other end, the presentation layer changes the data from the common format back into a format that is useable by the application.
The Presentation Layer, often likened to an adept interpreter in the digital realm, plays a pivotal role in the seamless transmission and reception of data across the network. At its essence, the Presentation Layer is tasked with data translation, encryption, and compression.
Presentation Layer is the sixth layer in the OSI model and here are some of the functionalities of the presentation layer: Translation. Before being transmitted, the data remains in the form of ...
Specific functionalities of the presentation layer are as follows: 1. Translation. The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams because different computers use different ...
This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. ... Presentation Layer functions. Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. Layer 6 is responsible for interoperability ...
The Presentation Layer, situated at Layer 6 of the OSI model, acts as an intermediary between the Application Layer (Layer 7) and the Session Layer (Layer 5). ... Data Translation: It translates ...
The presentation layer, also known as the syntax layer, is the sixth layer in the OSI model. It ensures that the data is in a format acceptable to the application layer. This includes data format translation, compression and decompression, encryption and decryption, and character set conversion. It acts as an interface between the application ...
The presentation layer establishes data formatting and data translation into a format specified by the application layer during the encapsulation of outgoing messages while being passed down the protocol stack, and possibly reversed during the deencapsulation of incoming messages when being passed up the protocol stack. For this very reason ...
Layer 6: Presentation Layer. The Presentation Layer, positioned as the sixth layer in the OSI Model, is responsible for managing data translation, encryption, compression, and ensuring that data exchanged between applications is in a format that can be understood by both sender and receiver.
The presentation layer is the sixth layer of the OSI Reference Model protocol stack, and second from the top. It is different from the other layers in two key respects. First, it has a much more limited and specific function than the other layers; it's actually somewhat easy to describe, hurray! Second, it is used much less often than the other ...
Data translation is another key function at the Presentation Layer, ensuring that data from the Application Layer is in a format that can be understood by the lower layers, and vice versa.
0. The presentation layer delivers information to the application layer for display. The presentation layer, in some cases, handles data translation to allow use on a particular system. The user interface shows you the data once the presentation layer has done any translations it needs to.
The presentation layer manages these abstract data structures and allows higher-level data structures(eg: banking records), to be defined and exchanged. Functions of Presentation Layer. Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. The presentation layer is responsible ...
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts. ... This layer offers best flexibility for data translation for making connections with ...
In technical speech, the presentation layer is the sixth of seven layers of OSI code that translates data stored in another layer into something a human can interpret. It's the presentation layer that knows to put the right information into the appropriate fields of a customer record, for example: Name, Date of Birth, Address, etc.