- Mission and history
- Platform features
- Library Advisory Group
- What’s in JSTOR
- For Librarians
- For Publishers

Open and free content on JSTOR and Artstor
Our partnerships with libraries and publishers help us make content discoverable and freely accessible worldwide
Search open content on JSTOR
Explore our growing collection of Open Access journals
Early Journal Content , articles published prior to the last 95 years in the United States, or prior to the last 143 years if initially published internationally, are freely available to all
Even more content is available when you register to read – millions of articles from nearly 2,000 journals
Thousands of Open Access ebooks are available from top scholarly publishers, including Brill, Cornell University Press, University College of London, and University of California Press – at no cost to libraries or users.
This includes Open Access titles in Spanish:
- Collaboration with El Colegio de México
- Partnership with the Latin American Council of Social Sciences
Images and media
JSTOR hosts a growing number of public collections , including Artstor’s Open Access collections , from museums, archives, libraries, and scholars worldwide.
Research reports
A curated set of more than 34,000 research reports from more than 140 policy institutes selected with faculty, librarian, and expert input.
Resources for librarians
Open content title lists:
- Open Access Journals (xlsx)
- Open Access Books (xlsx)
- JSTOR Early Journal Content (txt)
- Research Reports
Open Access ebook resources for librarians
Library-supported collections
Shared Collections : We have a growing corpus of digital special collections published on JSTOR by our institutional partners.
Reveal Digital : A collaboration with libraries to fund, source, digitize and publish open access primary source collections from under-represented voices.
JSTOR Daily
JSTOR Daily is an online publication that contextualizes current events with scholarship. All of our stories contain links to publicly accessible research on JSTOR. We’re proud to publish articles based in fact and grounded by careful research and to provide free access to that research for all of our readers.
Open Source Literature Review Search Tools: A list of search tools help you find open source articles
- A list of search tools help you find open source articles
- Free and open source software useful for open source literature reviews
Open source search tools
Use the search tools below to find open access articles, no cost academic search engines for published papers and preprints - comprehensive.
- Bielefeld University’s Academic Search Engine (BASE) BASE is one of the world's most voluminous search engines especially for academic web resources. BASE provides more than 240 million documents from more than 8,000 content providers. You can access the full texts of about 60% of the indexed documents for free (Open Access). BASE is operated by Bielefeld University Library.
- CORE CORE’s mission is to aggregate all open access research outputs from repositories and journals worldwide and make them available to the public. In this way CORE facilitates free unrestricted access to research for all.
- Directory of Open Access Journals The DOAJ (Directory of Open Access Journals) was launched in 2003 with 300 open access journals. Today, this independent database contains over 15 000 peer-reviewed open access journals covering all areas of science, technology, medicine, social sciences, arts and humanities. Open access journals from all countries and in all languages are welcome to apply for inclusion.
- Google Scholar Comprehensive, indexes academic information from various online web resources especially useful when used with one of the browser plugins such as Unpaywall
- Microsoft Academic Research Use with one of browser extensions Such as Unpaywal. Microsoft Academic understands the meaning of words, it doesn’t just match keywords to content. For example, when you type “Microsoft,” it knows you mean the institution, and shows you publications authored by researchers affiliated with Microsoft. Similarly, Microsoft Academic knows journal titles, conference names, and many research topics. Try these queries to understand the power of semantic search and unleash it yourself!
- OSF PrePrints (Center for Open Science) In academic publishing, a preprint is a version of a scholarly or scientific paper that precedes formal peer review and publication in a peer-reviewed scholarly or scientific journal. The preprint may be available, often as a non-typeset version available free, before and/or after a paper is published in a journal.2,288,043 searchable as of November 25, 2020
- ScienceOpen ScienceOpen is a discovery platform with interactive features for scholars to enhance their research in the open, make an impact, and receive credit for it. We provide context building services for publishers, to bring researchers closer to the content than ever before. Our advanced search and discovery functions, combined with post-publication peer review, recommendation, social sharing, and collection-building features make
- Semantic Scholar (Allen Institute) A Free, AI-powered Tool for Navigating the Scientific Literature Search over 180 million papers across all fields of science
- ResearchGate A social networking website for researchers. Contains more than 100 million publication pages.
- The Multidisciplinary Preprint Platform A platform dedicated to making early versions of research outputs available, including original research articles and reviews
Specialty Open Access Platforms
- Bioline International Bioline International is a not-for-profit scholarly publishing cooperative committed to providing open access to quality research journals published in developing countries. BI's goal of reducing the South to North knowledge gap is crucial to a global understanding of health (tropical medicine, infectious diseases, epidemiology, emerging new diseases), biodiversity, the environment, conservation and international development. By providing a platform for the distribution of peer-reviewed journals (currently from Bangladesh, Brazil, Chile, China, Colombia, Egypt, Ghana, India, Iran, Kenya, Malaysia, Nigeria, Tanzania, Turkey, Uganda and Venezuela), BI helps to reduce the global knowledge divide by making bioscience information generated in these countries available to the international research community world-wide.
- BioOne BioOne was established in 1999[2] in Washington, DC, as a 501(c)(3) not-for-profit organization by five scholarly collaborators: the American Institute of Biological Sciences, the Scholarly Publishing and Academic Resources Coalition (SPARC),[3] The University of Kansas, Greater Western Library Alliance, and Allen Press.
- CERN Document Server Over 650,000 bibliographic records, including 320,000 fulltext documents, of interest to people working in particle physics and related areas. Covers preprints, articles, books, journals, photographs, and much more.
- Cornell’s ArXiv arXiv is a free distribution service and an open-access archive for 1,799,152 scholarly articles in the fields of physics, mathematics, computer science, quantitative biology, quantitative finance, statistics, electrical engineering and systems science, and economics. Materials on this site are not peer-reviewed by arXiv. more... less... Open access to 1.3 million e‐prints in physics, mathematics, computer science, quantitative biology, quantitative finance, statistics, electrical engineering and systems science, and economics.
- Educational Resources Information Center (ERIC) The ERIC Selection Policy establishes the standards and criteria for selecting materials for inclusion in the ERIC collection. It states broad collection goals and defines the standards and criteria required of approved sources and individual materials in the ERIC digital library. The purpose of the selection policy is to provide consistency in the approach for reviewing and selecting sources and individual items, and clearly communicate policy and process to staff, users, publishers, and individual submitter of material.
- Mendeley (Elsevier) Mendeley is a free reference manager and academic social network that can help you organize your research, collaborate with others online, and discover the latest research:
- Organic Eprints Organic Eprints is an international open access archive for papers and projects related to research in organic food and farming. The archive contains full-text papers in electronic form together with bibliographic information, abstracts and other metadata. It also offers information on organisations, projects and facilities in the context of organic farming research.
- Penn State’s CiteSeerX CiteSeerx is an evolving scientific literature digital library and search engine that has focused primarily on the literature in computer and information science. CiteSeerx aims to improve the dissemination of scientific literature and to provide improvements in functionality, usability, availability, cost, comprehensiveness, efficiency, and timeliness in the access of scientific and scholarly knowledge. Rather than creating just another digital library, CiteSeerx attempts to provide resources such as algorithms, data, metadata, services, techniques, and software that can be used to promote other digital libraries. CiteSeerx has developed new methods and algorithms to index PostScript and PDF research articles on the Web.
- PubMed PubMed is a free search engine accessing primarily the MEDLINE database of references and abstracts on life sciences and biomedical topics. The United States National Library of Medicine at the National Institutes of Health maintain the database as part of the Entrez system of information retrieval.
- SSRN, formerly known as Social Science Research Network s a repository for preprints devoted to the rapid dissemination of scholarly research in the social sciences and humanities and more. Elsevier bought SSRN from Social Science Electronic Publishing Inc. in May 2016
- U.S. government’s Science.gov Science.gov searches over 60 databases and over 2,200 scientific websites to provide users with access to more than 200 million pages of authoritative federal science information including research and development results.

- Next: Free and open source software useful for open source literature reviews >>
- Last Updated: Nov 29, 2023 9:44 AM
- URL: https://guides.pnw.edu/opensource
Help | Advanced Search
arXiv is a free distribution service and an open-access archive for nearly 2.4 million scholarly articles in the fields of physics, mathematics, computer science, quantitative biology, quantitative finance, statistics, electrical engineering and systems science, and economics. Materials on this site are not peer-reviewed by arXiv.
arXiv is a free distribution service and an open-access archive for scholarly articles in the fields of physics, mathematics, computer science, quantitative biology, quantitative finance, statistics, electrical engineering and systems science, and economics. Materials on this site are not peer-reviewed by arXiv.
Stay up to date with what is happening at arXiv on our blog.
Latest news
- Astrophysics ( astro-ph new , recent , search ) Astrophysics of Galaxies ; Cosmology and Nongalactic Astrophysics ; Earth and Planetary Astrophysics ; High Energy Astrophysical Phenomena ; Instrumentation and Methods for Astrophysics ; Solar and Stellar Astrophysics
- Condensed Matter ( cond-mat new , recent , search ) Disordered Systems and Neural Networks ; Materials Science ; Mesoscale and Nanoscale Physics ; Other Condensed Matter ; Quantum Gases ; Soft Condensed Matter ; Statistical Mechanics ; Strongly Correlated Electrons ; Superconductivity
- General Relativity and Quantum Cosmology ( gr-qc new , recent , search )
- High Energy Physics - Experiment ( hep-ex new , recent , search )
- High Energy Physics - Lattice ( hep-lat new , recent , search )
- High Energy Physics - Phenomenology ( hep-ph new , recent , search )
- High Energy Physics - Theory ( hep-th new , recent , search )
- Mathematical Physics ( math-ph new , recent , search )
- Nonlinear Sciences ( nlin new , recent , search ) includes: Adaptation and Self-Organizing Systems ; Cellular Automata and Lattice Gases ; Chaotic Dynamics ; Exactly Solvable and Integrable Systems ; Pattern Formation and Solitons
- Nuclear Experiment ( nucl-ex new , recent , search )
- Nuclear Theory ( nucl-th new , recent , search )
- Physics ( physics new , recent , search ) includes: Accelerator Physics ; Applied Physics ; Atmospheric and Oceanic Physics ; Atomic and Molecular Clusters ; Atomic Physics ; Biological Physics ; Chemical Physics ; Classical Physics ; Computational Physics ; Data Analysis, Statistics and Probability ; Fluid Dynamics ; General Physics ; Geophysics ; History and Philosophy of Physics ; Instrumentation and Detectors ; Medical Physics ; Optics ; Physics and Society ; Physics Education ; Plasma Physics ; Popular Physics ; Space Physics
- Quantum Physics ( quant-ph new , recent , search )
Mathematics
- Mathematics ( math new , recent , search ) includes: (see detailed description ): Algebraic Geometry ; Algebraic Topology ; Analysis of PDEs ; Category Theory ; Classical Analysis and ODEs ; Combinatorics ; Commutative Algebra ; Complex Variables ; Differential Geometry ; Dynamical Systems ; Functional Analysis ; General Mathematics ; General Topology ; Geometric Topology ; Group Theory ; History and Overview ; Information Theory ; K-Theory and Homology ; Logic ; Mathematical Physics ; Metric Geometry ; Number Theory ; Numerical Analysis ; Operator Algebras ; Optimization and Control ; Probability ; Quantum Algebra ; Representation Theory ; Rings and Algebras ; Spectral Theory ; Statistics Theory ; Symplectic Geometry
Computer Science
- Computing Research Repository ( CoRR new , recent , search ) includes: (see detailed description ): Artificial Intelligence ; Computation and Language ; Computational Complexity ; Computational Engineering, Finance, and Science ; Computational Geometry ; Computer Science and Game Theory ; Computer Vision and Pattern Recognition ; Computers and Society ; Cryptography and Security ; Data Structures and Algorithms ; Databases ; Digital Libraries ; Discrete Mathematics ; Distributed, Parallel, and Cluster Computing ; Emerging Technologies ; Formal Languages and Automata Theory ; General Literature ; Graphics ; Hardware Architecture ; Human-Computer Interaction ; Information Retrieval ; Information Theory ; Logic in Computer Science ; Machine Learning ; Mathematical Software ; Multiagent Systems ; Multimedia ; Networking and Internet Architecture ; Neural and Evolutionary Computing ; Numerical Analysis ; Operating Systems ; Other Computer Science ; Performance ; Programming Languages ; Robotics ; Social and Information Networks ; Software Engineering ; Sound ; Symbolic Computation ; Systems and Control
Quantitative Biology
- Quantitative Biology ( q-bio new , recent , search ) includes: (see detailed description ): Biomolecules ; Cell Behavior ; Genomics ; Molecular Networks ; Neurons and Cognition ; Other Quantitative Biology ; Populations and Evolution ; Quantitative Methods ; Subcellular Processes ; Tissues and Organs
Quantitative Finance
- Quantitative Finance ( q-fin new , recent , search ) includes: (see detailed description ): Computational Finance ; Economics ; General Finance ; Mathematical Finance ; Portfolio Management ; Pricing of Securities ; Risk Management ; Statistical Finance ; Trading and Market Microstructure
- Statistics ( stat new , recent , search ) includes: (see detailed description ): Applications ; Computation ; Machine Learning ; Methodology ; Other Statistics ; Statistics Theory
Electrical Engineering and Systems Science
- Electrical Engineering and Systems Science ( eess new , recent , search ) includes: (see detailed description ): Audio and Speech Processing ; Image and Video Processing ; Signal Processing ; Systems and Control
- Economics ( econ new , recent , search ) includes: (see detailed description ): Econometrics ; General Economics ; Theoretical Economics
About arXiv
- General information
- How to Submit to arXiv
- Membership & Giving
- Advanced search
- Peer review

Discover relevant research today

Advance your research field in the open

Reach new audiences and maximize your readership
ScienceOpen puts your research in the context of
Publications
For Publishers
ScienceOpen offers content hosting, context building and marketing services for publishers. See our tailored offerings
- For academic publishers to promote journals and interdisciplinary collections
- For open access journals to host journal content in an interactive environment
- For university library publishing to develop new open access paradigms for their scholars
- For scholarly societies to promote content with interactive features
For Institutions
ScienceOpen offers state-of-the-art technology and a range of solutions and services
- For faculties and research groups to promote and share your work
- For research institutes to build up your own branding for OA publications
- For funders to develop new open access publishing paradigms
- For university libraries to create an independent OA publishing environment
For Researchers
Make an impact and build your research profile in the open with ScienceOpen
- Search and discover relevant research in over 93 million Open Access articles and article records
- Share your expertise and get credit by publicly reviewing any article
- Publish your poster or preprint and track usage and impact with article- and author-level metrics
- Create a topical Collection to advance your research field
Create a Journal powered by ScienceOpen
Launching a new open access journal or an open access press? ScienceOpen now provides full end-to-end open access publishing solutions – embedded within our smart interactive discovery environment. A modular approach allows open access publishers to pick and choose among a range of services and design the platform that fits their goals and budget.
Continue reading “Create a Journal powered by ScienceOpen”
What can a Researcher do on ScienceOpen?
ScienceOpen provides researchers with a wide range of tools to support their research – all for free. Here is a short checklist to make sure you are getting the most of the technological infrastructure and content that we have to offer. What can a researcher do on ScienceOpen? Continue reading “What can a Researcher do on ScienceOpen?”
ScienceOpen on the Road
Upcoming events.
- 20 – 22 February – ResearcherToReader Conferece
Past Events
- 09 November – Webinar for the Discoverability of African Research
- 26 – 27 October – Attending the Workshop on Open Citations and Open Scholarly Metadata
- 18 – 22 October – ScienceOpen at Frankfurt Book Fair.
- 27 – 29 September – Attending OA Tage, Berlin .
- 25 – 27 September – ScienceOpen at Open Science Fair
- 19 – 21 September – OASPA 2023 Annual Conference .
- 22 – 24 May – ScienceOpen sponsoring Pint of Science, Berlin.
- 16-17 May – ScienceOpen at 3rd AEUP Conference.
- 20 – 21 April – ScienceOpen attending Scaling Small: Community-Owned Futures for Open Access Books .
- 18 – 20 April – ScienceOpen at the London Book Fair .
What is ScienceOpen?
- Smart search and discovery within an interactive interface
- Researcher promotion and ORCID integration
- Open evaluation with article reviews and Collections
- Business model based on providing services to publishers
Live Twitter stream
Some of our partners:.

- Search Search
- CN (Chinese)
- DE (German)
- ES (Spanish)
- FR (Français)
- JP (Japanese)
- Open Research
- Booksellers
- Peer Reviewers
- Springer Nature Group ↗
- Fundamentals of open research
- Gold or Green routes to open research
- Benefits of open research
- Open research timeline
- Whitepapers
- About overview
- Journal pricing FAQs
- Publishing an OA book
- Journals & books overview
- OA article funding
- Article OA funding and policy guidance
- OA book funding
- Book OA funding and policy guidance
- Funding & support overview
- Open access agreements
- Springer Nature journal policies
- APC waivers and discounts
- Springer Nature book policies
- Publication policies overview
The fundamentals of open access and open research
What is open access and open research.
Open access (OA) refers to the free, immediate, online availability of research outputs such as journal articles or books, combined with the rights to use these outputs fully in the digital environment. OA content is open to all, with no access fees.
Open research goes beyond the boundaries of publications to consider all research outputs – from data to code and even open peer review. Making all outputs of research as open and accessible as possible means research can have a greater impact, and help to solve some of the world’s greatest challenges.
Learn more about gold open access
How can i publish my work open access.
As the author of a research article or book, you have the ability to ensure that your research can be accessed and used by the widest possible audience. Springer Nature supports immediate Gold OA as the most open, least restrictive form of OA: authors can choose to publish their research article in a fully OA journal, a hybrid or transformative journal, or as an OA book or OA chapter.
Alternatively, where articles, books or chapters are published via the subscription route, Springer Nature allows authors to archive the accepted version of their manuscript on their own personal website or their funder’s or institution’s repository, for public release after an embargo period (Green OA). Find out more.
Why should I publish OA?
What is cc by.
The CC BY licence is the most open licence available and considered the industry 'gold standard' for OA; it is also preferred by many funders. It lets others distribute, remix, tweak, and build upon your work, even commercially, as long as they credit you for the original creation. It offers maximum dissemination and use of licenced materials. All Springer Nature journals with OA options offer the CC BY licence, and this is now the default licence for the majority of Springer Nature fully OA journals. It is also the default license for OA books and chapters. Other Creative Commons licenses are available on request.
How do I pay for open access?
As costs are involved in every stage of the publication process, authors are asked to pay an open access fee in order for their article to be published open access under a creative commons license. Springer Nature offers a free open access support service to make it easier for our authors to discover and apply for funding to cover article processing charges (APCs) and/or book processing charges (BPCs). Find out more.
What is open data?
We believe that all research data, including research files and code, should be as open as possible and want to make it easier for researchers to share the data that support their publications, making them accessible and reusable. Find out more about our research data services and policies.
What is a preprint?
A preprint is a version of a scientific manuscript posted on a public server prior to formal peer review. Once posted, the preprint becomes a permanent part of the scientific record, citable with its own unique DOI . Early sharing is recommended as it offers an opportunity to receive feedback on your work, claim priority for a discovery, and help research move faster. In Review is one of the most innovative preprint services available, offering real time updates on your manuscript’s progress through peer review. Discover In Review and its benefits.
What is open peer review?
Open peer review refers to the process of making peer reviewer reports openly available. Many publishers and journals offer some form of open peer review, including BMC who were one of the first publishers to open up peer review in 1999. Find out more .
Blog posts on open access from "The Source"

How to publish open access with fees covered
Could you publish open access with fees covered under a Springer Nature open access agreement?

Celebrating our 2000th open access book
We are proud to celebrate the publication of our 2000th open access book. Take a look at how we achieved this milestone.

open access
Why is Gold OA best for researchers?
Explore the advantages of Gold OA, by reading some of the highlights from our white paper "Going for Gold".

How researchers are using open data in 2022
How are researchers using open data in 2022? Read this year’s State of Open Data Report, providing insights into the attitudes, motivations and challenges of researchers towards open data.
Ready to publish?

A pioneer of open access publishing, BMC is committed to innovation and offers an evolving portfolio of some 300 journals.

Open research is at the heart of Nature Research. Our portfolio includes Nature Communications , Scientific Reports and many more.

Springer offers a variety of open access options for journal articles and books across a number of disciplines.

Palgrave Macmillan is committed to developing sustainable models of open access for the HSS disciplines.

Apress is dedicated to meeting the information needs of developers, IT professionals, and tech communities worldwide.
Discover more tools and resources along with our author services

Author services

Early Career Resource Center

Journal Suggester

Using Your ORCID ID

The Transfer Desk
Tutorials and educational resources.

How to Write a Manuscript

How to submit a journal article manuscript

Nature Masterclasses
Stay up to date.
Here to foster information exchange with the library community
Connect with us on LinkedIn and stay up to date with news and development.
- Tools & Services
- Account Development
- Sales and account contacts
- Professional
- Press office
- Locations & Contact
We are a world leading research, educational and professional publisher. Visit our main website for more information.
- © 2023 Springer Nature
- General terms and conditions
- Your US State Privacy Rights
- Your Privacy Choices / Manage Cookies
- Accessibility
- Legal notice
- Help us to improve this site, send feedback.

The Trusted Solution for Open Access Publishing
Fully Open Access Topical Journals
IEEE offers over 30 technically focused gold fully open access journals spanning a wide range of fields.
Hybrid Open Access Journals
IEEE offers 180+ hybrid journals that support open access, including many of the top-cited titles in the field. These titles have Transformative Status under Plan S.
IEEE Access
The multidisciplinary, gold fully open access journal of the IEEE, publishing high quality research across all of IEEE’s fields of interest.

About IEEE Open
Many authors in today’s publishing environment want to make access to research freely available to all reader communities. To help authors gain maximum exposure for their groundbreaking research, IEEE provides a variety of open access options to meet the needs of authors and institutions.
Call for Papers
Browse our fully open access topical journals and submit a paper.
News & Events
IEEE Announces 6 New Fully Open Access Journals and 3 Hybrid Journals Coming in 2024
IEEE Commits its Entire Hybrid Journal Portfolio to Transformative Journal Status Aligned with Plan S
IEEE and CRUI Sign Three-Year Transformative Agreement to Accelerate Open Access Publishing in Italy
New IEEE Open Access Journals Receive First Impact Factors

IEEE Access, a Multidisciplinary, Open Access Journal
IEEE Access is a multidisciplinary, online-only, gold fully open access journal, continuously presenting the results of original research or development across all IEEE fields of interest. Supported by article processing charges (APCs), its hallmarks are rapid peer review, a submission-to-publication time of 4 to 6 weeks, and articles that are freely available to all readers.

Now On-Demand
How to publish open access with ieee.
This newly published on-demand webinar will provide authors with best practices in preparing a manuscript, navigating the journal submission process, and important tips to help an author get published. It will also review the opportunities authors and academic institutions have to enhance the visibility and impact of their research by publishing in the many open access options available from IEEE.
Register Now

IEEE Publications Dominate Latest Citation Rankings
Each year, the Journal Citation Reports® (JCR) from Web of Science Group examines the influence and impact of scholarly research journals. JCR reveals the relationship between citing and cited journals, offering a systematic, objective means to evaluate the world’s leading journals. The 2022 JCR study, released in June 2023, reveals that IEEE journals continue to maintain rankings at the top of their fields.
Open Access
Open Access is the free, immediate, online availability of research articles coupled with the rights to use these articles fully in the digital environment. Open Access ensures that anyone can access and use these results—to turn ideas into industries and breakthroughs into better lives.
Open Education
- Impact Stories
- Share on Facebook
- Share on Twitter
- Share via Email
Research provides the foundation of modern society. Research leads to breakthroughs, and communicating the results of research is what allows us to turn breakthroughs into better lives—to provide new treatments for disease, to implement solutions for challenges like global warming, and to build entire industries around what were once just ideas.
However, our current system for communicating research is crippled by a centuries old model that hasn’t been updated to take advantage of 21st century technology:
- Governments provide most of the funding for research—hundreds of billions of dollars annually—and public institutions employ a large portion of all researchers.
- Researchers publish their findings without the expectation of compensation. Unlike other authors, they hand their work over to publishers without payment, in the interest of advancing human knowledge.
- Through the process of peer review, researchers review each other’s work for free.
- Once published, those that contributed to the research (from taxpayers to the institutions that supported the research itself) have to pay again to access the findings. Though research is produced as a public good, it isn’t available to the public who paid for it.
Our current system for communicating research uses a print-based model in the digital age. Even though research is largely produced with public dollars by researchers who share it freely, the results are hidden behind technical, legal, and financial barriers. These artificial barriers are maintained by legacy publishers and restrict access to a small fraction of users, locking out most of the world’s population and preventing the use of new research techniques.
This fundamental mismatch between what is possible with digital technology—an open system for communicating research results in which anyone, anywhere can contribute—and our outdated publishing system has led to the call for Open Access.
Open Access is the free, immediate, online availability of research articles combined with the rights to use these articles fully in the digital environment. Open Access is the needed modern update for the communication of research that fully utilizes the Internet for what it was originally built to do—accelerate research.
Funders invest in research to advance human knowledge and ultimately improve lives. Open Access increases the return on that investment by ensuring the results of the research they fund can be read and built on by anyone.
Breakthroughs often come from unexpected places ; the Theory of Relativity was developed by a patent clerk. Open Access expands the number of potential contributors to research from just those at institutions wealthy enough to afford journal subscriptions to anyone with an internet connection.
Researchers benefit from having the widest possible audience. Researchers provide their articles to publishers for free, because their compensation comes in the form of recognition for their findings. Open Access means more readers, more potential collaborators, more citations for their work, and ultimately more recognition.
The research enterprise itself benefits when the latest techniques can be easily used. For years, we have had powerful text and data mining tools that can analyze the entire research literature, uncovering trends and connections that no human reader could. While publishers’ technical and legal barriers currently prevent their widespread use, Open Access empowers anyone to use these tools, which hold the potential of revolutionizing how research is conducted.
Even the best ideas remain just that until they are shared, until they can be utilized by others. The more people that can access and build upon the latest research, the more valuable that research becomes and the more likely we are to benefit as a society. More eyes make for smaller problems.
- Learn about SPARC’s policy priorities
- Download SPARC's OA policy one-pager
Open Access Impact Stories
The impact of embracing community over commercialization.
To catalyze discussion around the 2023 International Open Access Week theme of “Community over...
Zenodo’s Open Repository Streamlines Sharing Science
A decade ago, the scientific community recognized that to move from open access to open science,...
African Open Access Textbook and Journal Publishing Gains...
The high cost of college textbooks and scholarly journals puts many students and institutions at a...
Popular Resources
2021 update to the sparc landscape analysis & roadmap for action, sparc resources related to covid-19, data analysis for negotiation, latest news, all tdm & ai rights reserved fair use & evolving publisher copyright statements, theme for open access week 2024 continues call to put “community over commercialization”, open access as a means to equity: progress, challenges, and the continued role for the boai, upcoming events, oct 21: open access week 2024, learn more about our work.
Navigation group
Home banner.

Where scientists empower society
Creating solutions for healthy lives on a healthy planet.
most-cited publisher
largest publisher
2.5 billion
article views and downloads
Main Content
- Editors and reviewers
- Collaborators

Find a journal
We have a home for your research. Our community led journals cover more than 1,500 academic disciplines and are some of the largest and most cited in their fields.

Submit your research
Start your submission and get more impact for your research by publishing with us.

Author guidelines
Ready to publish? Check our author guidelines for everything you need to know about submitting, from choosing a journal and section to preparing your manuscript.

Peer review
Our efficient collaborative peer review means you’ll get a decision on your manuscript in an average of 61 days.

Article publishing charges (APCs) apply to articles that are accepted for publication by our external and independent editorial boards

Press office
Visit our press office for key media contact information, as well as Frontiers’ media kit, including our embargo policy, logos, key facts, leadership bios, and imagery.

Institutional partnerships
Join more than 555 institutions around the world already benefiting from an institutional membership with Frontiers, including CERN, Max Planck Society, and the University of Oxford.

Publishing partnerships
Partner with Frontiers and make your society’s transition to open access a reality with our custom-built platform and publishing expertise.

Policy Labs
Connecting experts from business, science, and policy to strengthen the dialogue between scientific research and informed policymaking.

How we publish
All Frontiers journals are community-run and fully open access, so every research article we publish is immediately and permanently free to read.

Editor guidelines
Reviewing a manuscript? See our guidelines for everything you need to know about our peer review process.

Become an editor
Apply to join an editorial board and collaborate with an international team of carefully selected independent researchers.

My assignments
It’s easy to find and track your editorial assignments with our platform, 'My Frontiers' – saving you time to spend on your own research.

Scientists call for urgent action to prevent immune-mediated illnesses caused by climate change and biodiversity loss
Climate change, pollution, and collapsing biodiversity are damaging our immune systems, but improving the environment offers effective and fast-acting protection.

Safeguarding peer review to ensure quality at scale
Making scientific research open has never been more important. But for research to be trusted, it must be of the highest quality. Facing an industry-wide rise in fraudulent science, Frontiers has increased its focus on safeguarding quality.

Chronic stress and inflammation linked to societal and environmental impacts in new study
Scientists hypothesize that as-yet unrecognized inflammatory stress is spreading among people at unprecedented rates, affecting our cognitive ability to address climate change, war, and other critical issues.

Tiny crustaceans discovered preying on live jellyfish during harsh Arctic night
Scientists used DNA metabarcoding to show for the first time that jellyfish are an important food for amphipods during the Arctic polar night in waters off Svalbard, at a time of year when other food resources are scarce.

Why studying astronauts’ microbiomes is crucial to ensure deep space mission success
In a new Frontiers’ guest editorial, Prof Dr Lembit Sihver, director of CRREAT at the Nuclear Physics Institute of the Czech Academy of Sciences and his co-authors explore the impact the microbiome has on human health in space.

Cake and cookies may increase Alzheimer’s risk: Here are five Frontiers articles you won’t want to miss
At Frontiers, we bring some of the world’s best research to a global audience. But with tens of thousands of articles published each year, it’s impossible to cover all of them. Here are just five amazing papers you may have missed.

2024's top 10 tech-driven Research Topics
Frontiers has compiled a list of 10 Research Topics that embrace the potential of technology to advance scientific breakthroughs and change the world for the better.
Get the latest research updates, subscribe to our newsletter
You are using an outdated browser. Please upgrade your browser to improve your experience and security.
All Research Articles
Impact of cyp3a4 rs2242480 polymorphisms on imatinib hplc determined trough concentration and response in chronic myeloid leukaemia in pakistani patients [version 1; peer review: awaiting peer review].
Dr. Asma Khan, Dr. Zunera Hakim, Dr. Akbar Waheed, Dr. Naila Abrar
Revised Sargassum sp. extract improve hematological profile of tilapia fish ( Oreochromis niloticus ) [version 4; peer review: 1 approved, 1 approved with reservations]
Mohamad Gazali, Irwan Effendi, Amir Husni, Nurjanah Nurjanah, Sri Wahyuni, Ronal Kurniawan
Revised Comparative evaluation and co-relation in variation of curve of Spee and curve of Wilson in Class II div. 1, Class II div. 2, and Class III as against Class I malocclusion in central India population- an in vitro study [version 2; peer review: 1 approved with reservations]
Ruchika Pandey, Ranjit Kamble
Postural control imbalance in individuals with a minor lower extremity amputation: a scoping review protocol. [version 1; peer review: awaiting peer review]
Maxime Acien, Ahmed Dami, Virginie Blanchette, Gabriel Moisan
Revised “The person was like the glue in the cracked pot which was no longer there”: co-production of the web-based Families and Friends in Bereavement intervention [version 2; peer review: 2 approved with reservations]
Previously titled: “The person was like the glue in the cracked pot which was no longer there”: Family-focused support for bereavement via co-production of a web-based intervention
Natasha Campling, Susi Lund, Alison Allam, Gail Precious, Michelle Myall
Revised Pharmacists’ readiness and willingness to vaccinate the public in United Arab Emirates community pharmacies: A cross-sectional study [version 2; peer review: 2 approved with reservations]
Dixon Thomas, Amal Abdalla, Saeed Hussein, Jean Joury, Amin Elshamy, Sherief Khalifa, Ziad Saleh
Artificial Intelligence Model Chatgpt-4: Entrepreneur Candidate and Entrepreneurship Example [version 1; peer review: awaiting peer review]
Muhammet SAYGIN, Mustafa BEKMEZCİ, Evren DİNÇER
Neck pain and distance learning: A pain in the neck for university students during COVID-19 [version 1; peer review: awaiting peer review]
Awab Musaad Mohamed, Mohamad Abdulkafi Abbara, Sara Alaaeldin Bashier, Danya Aasim Elkhidir, Amal Hussein, Anu Vinod Ranade
Case Report: Post-operative mitral valve replacement complicating with a large cardiac mass and role of TEE in decision making [version 1; peer review: awaiting peer review]
Narasimha Pai D, Chaithra Nayak, Padmanabh Kamath, Syed Waleem Pasha, Deepa Noronha
Greenland 2022 GHOST project: Sampling Greenland geothermal springs - expedition report [version 1; peer review: awaiting peer review]
Donato Giovannelli, Matteo Selci, Margaret Cramm, James A. Bradley, J. Maarten de Moor, Peter H. Barry, Shaunna M. Morrison, Monica Correggia, Luciano di Iorio, Angelina Cordone, Stefano Caliro, Saemundur A. Halldórsson
In silico analysis of the action of saturated, monounsaturated, and polyunsaturated fatty acids against Echinococcus granulosus fatty-acid-binding protein 1 [version 1; peer review: awaiting peer review]
Margot Paco-Chipana, Karel Mena-Ulecia, Yoan Hidalgo Rosa, Maria Isabel Herrera Valdivida, Luis Daniel Goyzueta-Mamani, Berly Cardenas-Pillco, Miguel Angel Chavez-Fumagalli, Haruna Luz Barazorda-Ccahuana
Revised Micro(nano)plastics: invisible compounds with a visible impact [version 2; peer review: 2 approved with reservations, 1 not approved]
Prabhakar Sharma, Prateek Sharma
Transforming the tourism experience: Virtual Reality for customer loyalty in the tourism industry [version 1; peer review: awaiting peer review]
Carlos Cayahuallpa-Paquirachi, Alex Pacheco, Yrene Uribe-Hernandez
Proposal of a domain model for 3D representation of buildings in Ecuador. [version 1; peer review: awaiting peer review]
Luis Alejandro Velastegui Cáceres, Julia Desirée Velastegui Cáceres, Pedro A Carretero Poblete, Manuel Fabian Moyón Gusqui, María Alejandra Cevallos Díaz
A prospective randomized comparative study to evaluate efficacy of intrathecal dexamethasone and dexmedetomidine added as adjuvant to bupivacaine in pregnant patients posted for elective LSCS [version 1; peer review: awaiting peer review]
Samarpan Patel, Aruna Chandak, Dnyanshree Wanjari
Revised Acrylamide in starchy foods subjected to deep-frying, 20 years after its discovery (2002-2022): a patent review [version 2; peer review: 3 approved]
William Yesid Díaz-Ávila, Sylvia María Villarreal-Archila, Francisco Javier Castellanos-Galeano
Revised `I-know-it-when-I-see-it' - Motivating Examples in the Psychology of Conspiracy Theory Theory [version 2; peer review: 1 approved, 2 approved with reservations, 1 not approved]
M R. X. Dentith
Morphology of gracilis muscle and the topographic anatomy of its neurovascular pedicles: A cross sectional study [version 1; peer review: awaiting peer review]
Chettiar Ganesh Kumar, Rajanigandha Vadgaonkar, M.D. Prameela, Vandana Blossom, B.V. Murlimanju, Mamatha Tonse, Mangala M. Pai

A cross-sectional study on the role of computed tomography in the evaluation of oral cavity malignancies in tertiary care hospital in central India: A study protocol [version 1; peer review: awaiting peer review]
Paschyanti Kasat, Shivali Kashikar
Determinants of immediate postpartum long acting reversible contraceptive utilization among women who gave birth in public health facilities in northwest Ethiopia: unmatched case-control study design [version 1; peer review: awaiting peer review]
Getachew Asmare Adella, Getiye Kibret Abtew, Mihiret Tesfaw Gellaw, Gizachew Ambaw Kassie, Molalegn Mesele Gesese, Endeshaw Chekol Abebe, Misganaw Asmamaw Mengstie, Mohammed Abdu Seid, Sefineh Fenta Feleke, Tadesse Asmamaw Dejenie, Berihun Bantie, Yenealem Solomon, Melkamu Aderajew Zemene, Anteneh Mengist Dessie, Denekew Tenaw Anley, Wubet Alebachew Bayih, Natnael Amare Tesfa, Natnael Atnafu Gebeyehu

Explore millions of high-quality primary sources and images from around the world, including artworks, maps, photographs, and more.
Explore migration issues through a variety of media types
- Part of The Streets are Talking: Public Forms of Creative Expression from Around the World
- Part of The Journal of Economic Perspectives, Vol. 34, No. 1 (Winter 2020)
- Part of Cato Institute (Aug. 3, 2021)
- Part of University of California Press
- Part of Open: Smithsonian National Museum of African American History & Culture
- Part of Indiana Journal of Global Legal Studies, Vol. 19, No. 1 (Winter 2012)
- Part of R Street Institute (Nov. 1, 2020)
- Part of Leuven University Press
- Part of UN Secretary-General Papers: Ban Ki-moon (2007-2016)
- Part of Perspectives on Terrorism, Vol. 12, No. 4 (August 2018)
- Part of Leveraging Lives: Serbia and Illegal Tunisian Migration to Europe, Carnegie Endowment for International Peace (Mar. 1, 2023)
- Part of UCL Press
Harness the power of visual materials—explore more than 3 million images now on JSTOR.
Enhance your scholarly research with underground newspapers, magazines, and journals.
Explore collections in the arts, sciences, and literature from the world’s leading museums, archives, and scholars.
When you choose to publish with PLOS, your research makes an impact. Make your work accessible to all, without restrictions, and accelerate scientific discovery with options like preprints and published peer review that make your work more Open.
- PLOS Biology
- PLOS Climate
- PLOS Complex Systems
- PLOS Computational Biology
- PLOS Digital Health
- PLOS Genetics
- PLOS Global Public Health
- PLOS Medicine
- PLOS Mental Health
- PLOS Neglected Tropical Diseases
- PLOS Pathogens
- PLOS Sustainability and Transformation
- PLOS Collections
Open Data is a strategy for incorporating research data into the permanent scientific record by releasing it under an Open Access license. Whether data is deposited in a purpose-built repository or published as Supporting Information alongside a research article, Open Data practices ensure that data remains accessible and discoverable. For verification, replication, reuse, and enhanced understanding of research.
Benefits of Open Data
Readers rely on raw scientific data to enhance their understanding of published research, for purposes of verification, replication and reanalysis, and to inform future investigations.
Ensure reproducibility Proactively sharing data ensures that your work remains reproducible over the long term.
Inspire trust Sharing data demonstrates rigor and signals to the community that the work has integrity.
Receive credit Making data public opens opportunities to get academic credit for collecting and curating data during the research process.
Make a contribution Access to data accelerates progress. According to the 2019 State of Open Data report, more than 70% of researchers use open datasets to inform their future research.
Preserve the scientific record Posting datasets in a repository or uploading them as Supporting Information prevents data loss.
Why do researchers choose to make their data public?
Watch the short video that explores the top benefits of data sharing, what types of research data you should share, and how you can get it ready to help ensure more impact for your research.
PLOS Open Data policy
Publishing in a PLOS journal carries with it a commitment to make the data underlying the conclusions in your research article publicly available upon publication.
Our data policy underscores the rigor of the research we publish, and gives readers a fuller understanding of each study.
Read more about Open Data
Data sharing has long been a hallmark of high-quality reproducible research. Now, Open Data is becoming...
For PLOS, increasing data-sharing rates—and especially increasing the amount of data shared in a repository—is a high priority.
Ensure that you’re publication-ready and ensure future reproducibility through good data management How you store your data matters. Even after…
Data repositories
All methods of data sharing data facilitate reproduction, improve trust in science, ensure appropriate credit, and prevent data loss. When you choose to deposit your data in a repository, those benefits are magnified and extended.
Data posted in a repository is…
…more discoverable.
Detailed metadata and bidirectional linking to and from related articles help to make data in public repositories easily findable.
…more reusable
Machine-readable data formatting allows research in a repository to be incorporated into future systematic reviews or meta analyses more easily.
…easier to cite
Repositories assign data its own unique DOI, distinct from that of related research articles, so datasets can accumulate citations in their own right, illustrating the importance and lasting relevance of the data itself.
…more likely to earn citations
A 2020 study of more than 500,000 published research articles found articles that link to data in a public repository were likely to have a 25% higher citation rate on average than articles where data is available on request or as Supporting Information.
Open Data is more discoverable and accessible than ever
Deposit your data in a repository and earn an accessible data icon.

You already know depositing research data in a repository yields benefits like improved reproducibility, discoverability, and more attention and citations for your research.
PLOS helps to magnify these benefits even further with our Accessible Data icon. When you link to select, popular data repositories, your article earns an eye-catching graphic with a link to the associated dataset, so it’s more visible to readers.
Participating data repositories include:
- Open Science Framework (OSF)
- Gene Expression Omnibus
- NCBI Bioproject
- NCBI Sequence Read Archive
- Demographic and Health Surveys
We aim to add more repositories to the list in future. Read more
The PLOS Open Science Toolbox
The future is open
The PLOS Open Science Toolbox is your source for sci-comm tips and best-practice. Learn practical strategies and hands-on tips to improve reproducibility, increase trust, and maximize the impact of your research through Open Science.
Sign up to have new issues delivered to your inbox every week.
Learn more about the benefits of Open Science. Open Science
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- PeerJ Comput Sci

Journal of Open Source Software (JOSS): design and first-year review
Arfon m. smith.
1 Data Science Mission Office, Space Telescope Science Institute, Baltimore, MD, United States of America
Kyle E. Niemeyer
2 School of Mechanical, Industrial, and Manufacturing Engineering, Oregon State University, Corvallis, OR, United States of America
Daniel S. Katz
3 National Center for Supercomputing Applications & Department of Computer Science & Department of Electrical and Computer Engineering & School of Information Sciences, University of Illinois at Urbana-Champaign, Urbana, IL, United States of America
Lorena A. Barba
4 Department of Mechanical & Aerospace Engineering, The George Washington University, Washington, D.C., United States of America
George Githinji
5 KEMRI—Wellcome Trust Research Programme, Kilifi, Kenya
Melissa Gymrek
6 Departments of Medicine & Computer Science and Engineering, University of California, San Diego, La Jolla, CA, United States of America
Kathryn D. Huff
7 Department of Nuclear, Plasma, and Radiological Engineering, University of Illinois at Urbana-Champaign, Urbana, IL, United States of America
Christopher R. Madan
8 School of Psychology, University of Nottingham, Nottingham, United Kingdom
Abigail Cabunoc Mayes
9 Mozilla Foundation, Toronto, Ontario, Canada
Kevin M. Moerman
10 MIT Media Lab, Massachusetts Institute of Technology, Cambridge, MA, United States of America
11 Trinity Centre for Bioengineering, Trinity College, The University of Dublin, Dublin, Ireland
Pjotr Prins
12 University of Tennessee Health Science Center, Memphis, TN, United States of America
13 University Medical Centre Utrecht, Utrecht, The Netherlands
Karthik Ram
14 Berkeley Institute for Data Science, University of California, Berkeley, CA, United States of America
Ariel Rokem
15 eScience Institute, University of Washington, Seattle, WA, United States of America
Tracy K. Teal
16 Data Carpentry, Davis, CA, United States of America
Roman Valls Guimera
17 University of Melbourne Centre for Cancer Research, University of Melbourne, Melbourne, Australia
Jacob T. Vanderplas
Associated data.
- Niemeyer KE. 2017a. JOSS first-year publication data and figures. Figshare. [ CrossRef ]
- Niemeyer KE. 2017b. JOSS publication flowchart. Figshare. [ CrossRef ]
The following information was supplied regarding data availability:
Niemeyer, Kyle (2017): JOSS first-year publication data and figures. figshare. https://doi.org/10.6084/m9.figshare.5147722 .
Source code of JOSS, on GitHub: https://github.com/openjournals/joss .
This article describes the motivation, design, and progress of the Journal of Open Source Software (JOSS). JOSS is a free and open-access journal that publishes articles describing research software. It has the dual goals of improving the quality of the software submitted and providing a mechanism for research software developers to receive credit. While designed to work within the current merit system of science, JOSS addresses the dearth of rewards for key contributions to science made in the form of software. JOSS publishes articles that encapsulate scholarship contained in the software itself, and its rigorous peer review targets the software components: functionality, documentation, tests, continuous integration, and the license. A JOSS article contains an abstract describing the purpose and functionality of the software, references, and a link to the software archive. The article is the entry point of a JOSS submission, which encompasses the full set of software artifacts. Submission and review proceed in the open, on GitHub. Editors, reviewers, and authors work collaboratively and openly. Unlike other journals, JOSS does not reject articles requiring major revision; while not yet accepted, articles remain visible and under review until the authors make adequate changes (or withdraw, if unable to meet requirements). Once an article is accepted, JOSS gives it a digital object identifier (DOI), deposits its metadata in Crossref, and the article can begin collecting citations on indexers like Google Scholar and other services. Authors retain copyright of their JOSS article, releasing it under a Creative Commons Attribution 4.0 International License. In its first year, starting in May 2016, JOSS published 111 articles, with more than 40 additional articles under review. JOSS is a sponsored project of the nonprofit organization NumFOCUS and is an affiliate of the Open Source Initiative (OSI).
Introduction
Modern scientific research produces many outputs beyond traditional articles and books. Among these, research software is critically important for a broad spectrum of fields. Current practices for publishing and citation do not, however, acknowledge software as a first-class research output. This deficiency means that researchers who develop software face critical career barriers. The Journal of Open Source Software ( JOSS ) was founded in May 2016 to offer a solution within the existing publishing mechanisms of science. It is a developer-friendly, free and open-access, peer-reviewed journal for research software packages. By its first anniversary, JOSS had published more than a hundred articles. This article discusses the motivation for creating a new software journal, delineates the editorial and review process, and summarizes the journal’s first year of operation via submission statistics. We expect this article to be of interest to three core audiences: (1) researchers who develop software and could submit their work to JOSS , (2) those in the community with an interest in advancing scholarly communications who may appreciate the technical details of the JOSS journal framework, and (3) those interested in possibilities for citing software in their own research publications.
The sixteen authors of this article are the members of the JOSS Editorial Board at the end of its first year (May 2017). Arfon Smith is the founding editor-in-chief, and the founding editors are Lorena A. Barba, Kathryn Huff, Daniel Katz, Christopher Madan, Abigail Cabunoc Mayes, Kevin Moerman, Kyle Niemeyer, Karthik Ram, Tracy Teal, and Jake Vanderplas. Five new editors joined in the first year to handle areas not well covered by the original editors, and to help manage the large and growing number of submissions. They are George Githinji, Melissa Gymrek, Pjotr Prins, Ariel Rokem, and Roman Valls Guimera. (Since then, we added three more editors: Jason Clark, Lindsey Heagy, and Thomas Leeper.)
The JOSS editors are firm supporters of open-source software for research, with extensive knowledge of the practices and ethics of open source. This knowledge is reflected in the JOSS submission system, peer-review process, and infrastructure. The journal offers a familiar environment for developers and authors to interact with reviewers and editors, leading to a citable published work: a software article. The article describes the software at a high level, and the software itself includes both source code and associated artifacts such as tests, documentation, and examples. With a Crossref digital object identifier (DOI), the article is able to collect citations, empowering the developers/authors to gain career credit for their work. JOSS thus fills a pressing need for computational researchers to advance professionally, while promoting higher quality software for science. JOSS also supports the broader open-science movement by encouraging researchers to share their software openly and follow best practices in its development.
Background and Motivation
A 2014 study of UK Russell Group Universities ( Hettrick et al., 2014 ) reports that ∼90% of academics surveyed said they use software in their research, while more than 70% said their research would be impractical without it. About half of these UK academics said they develop their own software while in the course of doing research. Similarly, a 2017 survey of members of the US National Postdoctoral Association found that 95% used research software, and 63% said their research would be impractical without it ( Nangia & Katz, 2017 ).
Despite being a critical part of modern research, software lacks support across the scholarly ecosystem for its publication, acknowledgement, and citation ( Niemeyer, Smith & Katz, 2016 ). Academic publishing has not changed substantially since its inception. Science, engineering, and many other academic fields still view research articles as the key indicator of research productivity, with research grants being another important indicator. Yet, the research article is inadequate to fully describe modern, data-intensive, computational research. JOSS focuses on research software and its place in the scholarly publishing ecosystem.
Why publish software?
Most academic fields still rely on a one-dimensional credit model where academic articles and their associated citations are the dominant factor in the success of a researcher’s career. Software creators, to increase the likelihood of receiving career credit for their work, often choose to publish “software articles” that act as placeholder publications pointing to their software. At the same time, recent years have seen a push for sharing open research software ( Barnes, 2010 ; Vandewalle, 2012 ; Morin et al., 2012 ; Ince, Hatton & Graham-Cumming, 2012 ; Nature Methods Editorial Board, 2014 ; Prins et al., 2015 ).
Beyond career-credit arguments for software creators, publishing research software enriches the scholarly record. Buckheit and Donoho paraphrased Jon Claerbout, a pioneer of reproducible research, as saying: “An article about a computational result is advertising, not scholarship. The actual scholarship is the full software environment, code and data, that produced the result” ( Buckheit & Donoho, 1995 ). The argument that articles about computational science are not satisfactory descriptions of the work, needing to be supplemented by code and data, is more than twenty years old! Yet, despite the significance of software in modern research, documenting its use and including it in the scholarly ecosystem presents numerous challenges.
Challenges of publishing software
The conventional publishing mechanism of science is the research article, and a researcher’s career progression hinges on collecting citations for published works. Unfortunately, software citation ( Smith et al., 2016 ) is in its infancy (as is data citation ( FORCE11, 2014 ; Starr et al., 2015 )). Publishing the software itself and receiving citation credit for it may be a better long-term solution, but this is still impractical. Even when software (and data) are published so that they can be cited, we do not have a standard culture of peer review for them. This leads many developers today to publish software articles.
The developer’s next dilemma is where to publish, given the research content, novelty, length and other features of a software article. Since 2012, Neil Chue Hong has maintained a growing list of journals that accept software articles ( Chue Hong, 2016 ). He includes both generalist journals, accepting software articles from a variety of fields, and domain-specific journals, accepting both research and software articles in a given field. For many journals, particularly the domain-specific ones, a software article must include novel results to justify publication.
From the developer’s point of view, writing a software article can involve a great deal of extra work. Good software includes documentation for both users and developers that is sufficient to make it understandable. A software article may contain much of the same content, merely in a different format, and developers may not find value in rewriting their documentation in a manner less useful to their users and collaborators. These issues may lead developers to shun the idea of software articles and prefer to publish the software itself. Yet, software citation is not common and the mostly one-dimensional credit model of academia (based on article citations) means that publishing software often does not “count” for career progression ( Niemeyer, Smith & Katz, 2016 ; Smith et al., 2016 ).
The Journal of Open Source Software
To tackle the challenges mentioned above, the Journal of Open Source Software ( JOSS ) launched in May 2016 ( Smith, 2016c ) with the goal of drastically reducing the overhead of publishing software articles. JOSS offers developers a venue to publish their complete research software wrapped in relatively short high-level articles, thus enabling citation credit for their work. In this section we describe the goals and principles, infrastructure, and business model of JOSS , and compare it with other software journals.
Goals and principles
JOSS articles are deliberately short and only include an abstract describing the high-level functionality of the software, a list of the authors of the software (with their affiliations), a list of key references, and a link to the software archive and software repository. Articles are not allowed to include other content often found in software articles, such as descriptions of the API (application programming interface) and novel research results obtained using the software. The software API should already be described in the software documentation, and domain research results do not belong in JOSS —these should be published in a domain journal. Unlike most journals, which ease discoverability of new research and findings, JOSS serves primarily as a mechanism for software developers/authors to improve and publish their research software. Thus, software discovery is a secondary feature.
The JOSS design and implementation are based on the following principles:
- • Other than their short length, JOSS articles are conventional articles in every other sense: the journal has an ISSN, articles receive Crossref DOIs with high-quality submission metadata, and articles are appropriately archived.
- • Because software articles are “advertising” and simply pointers to the actual scholarship (the software), short abstract-length submissions are sufficient for these “advertisements.”
- • Software is a core product of research and therefore the software itself should be archived appropriately when submitted to and reviewed in JOSS .
- • Code review, documentation, and contributing guidelines are important for open-source software and should be part of any review. In JOSS , they are the focus of peer review. (While a range of other journals publish software, with various peer-review processes, the focus of the review is usually the submitted article and reviewers might not even look at the code.) The JOSS review process itself, described in Section ‘Peer review in JOSS ’, was based on the on-boarding checklist for projects joining the rOpenSci collaboration ( Boettiger et al., 2015 ).
Acceptable JOSS submissions also need to meet the following criteria:
- • The software must be open source by the Open Source Initiative (OSI) definition ( https://opensource.org ).
- • The software must have a research application.
- • The submitter should be a major contributor to the software they are submitting.
- • The software should be a significant new contribution to the available open-source software that either enables some new research challenge(s) to be addressed or makes addressing research challenges significantly better (e.g., faster, easier, simpler).
- • The software should be feature-complete, i.e., it cannot be a partial solution.
How JOSS works
JOSS is designed as a small collection of open-source tools that leverage existing infrastructure such as GitHub, Zenodo, and Figshare. A goal when building the journal was to minimize the development of new tools where possible.
The JOSS web application and submission tool
The JOSS web application and submission tool is hosted at http://joss.theoj.org . It is a simple Ruby on Rails web application ( Smith, 2016b ) that lists accepted articles, provides the article submission form (see Fig. 1 ), and hosts journal documentation such as author submission guidelines. This application also automatically creates the review issue on GitHub once a submission has been pre-reviewed by an editor and accepted to start peer review in JOSS .

Open peer review on GitHub
JOSS conducts reviews on the joss-reviews GitHub repository ( Smith, 2016a ). Review of a submission begins with the opening of a new GitHub issue, where the editor-in-chief assigns an editor, the editor assigns a reviewer, and interactions between authors, reviewer(s), and editor proceed in the open. Figure 2 shows an example of a recent review for the (accepted) hdbscan package ( McInnes, Healy & Astels, 2017 ). The actual review includes the code, software functionality/performance claims, test suite (if present), documentation, and any other material associated with the software.

Whedon and the Whedon-API
Many of the tasks associated with JOSS reviews and editorial management are automated. A core RubyGem library named Whedon ( Smith, 2016d ) handles common tasks associated with managing the submitted manuscript, such as compiling the article (from its Markdown source) and creating Crossref metadata. An automated bot, Whedon-API ( Smith, 2016e ), handles other parts of the review process (such as assigning editors and reviewers based on editor input) and leverages the Whedon RubyGem library. For example, to assign the editor for a submission, one may type the following command in a comment box within the GitHub issue: @whedon assign @danielskatz as editor . Similarly, to assign a reviewer, one enters: @whedon assign @zhaozhang as reviewer (where the reviewer and editor GitHub handles identify them). The next section describes the review process in more detail.
Business model and content licensing
JOSS is designed to run at minimal cost with volunteer labor from editors and reviewers. The following fixed costs are currently incurred:
- • Crossref membership: $275. This is a yearly fixed cost for the JOSS parent entity— Open Journals —so that article DOIs can be registered with Crossref.
- • Crossref article DOIs: $1. This is a fixed cost per article.
- • JOSS web application hosting (currently with Heroku): $19 per month
Assuming a publication rate of 100 articles per year results in a core operating cost of ∼$6 per article. With 200 articles per year—which seems possible for the second year—the cost drops to ∼$3.50 per article:
Submitting authors retain copyright of JOSS articles and accepted articles are published under a Creative Commons Attribution 4.0 International License ( Creative Commons Corporation, 2016 ). Any code snippets included in JOSS articles are subject to the MIT license ( Open Source Initiative, 2016 ) regardless of the license of the submitted software package under review, which itself must be licensed under an OSI-approved license (see https://opensource.org/licenses/alphabetical for a complete list).
Comparison with other software journals
A good number of journals now accept, review, and publish software articles ( Chue Hong, 2016 ), which we group into two categories. The first category of journals include those similar to JOSS , which do not focus on a specific domain and only consider submissions of software/software articles: the Journal of Open Research Software ( JORS , http://openresearchsoftware.metajnl.com ), SoftwareX ( https://www.journals.elsevier.com/softwarex/ ), and now JOSS . Both JORS ( Chue Hong, 2017 ) and SoftwareX ( Elsevier, 2017 ) now review both the article text and the software. In JOSS , the review process focuses mainly on the software and associated material (e.g., documentation) and less on the article text, which is intended to be a brief description of the software. The role and form of peer review also varies across journals. In SoftwareX and JORS , the goal of the review is both to decide if the article is acceptable for publication and to improve it iteratively through a non-public, editor-mediated interaction between the authors and the anonymous reviewers. In contrast, JOSS has the goal of accepting most articles after improving them as needed, with the reviewers and authors communicating directly and publicly through GitHub issues.
The second category includes domain-specific journals that either accept software articles as a special submission type or exclusively consider software articles targeted at the domain. For example, Collected Algorithms (CALGO, http://www.acm.org/calgo/ ) is a long-running venue for reviewing and sharing mathematical algorithms associated with articles published in Transactions on Mathematical Software and other ACM journals. However, CALGO authors must transfer copyright to ACM and software is not available under an open-source license—this contrasts with JOSS , where authors retain copyright and software must be shared under an open-source license. Computer Physics Communications ( https://www.journals.elsevier.com/computer-physics-communications ) and Geoscientific Model Development ( https://www.geoscientific-model-development.net/ ) publish full-length articles describing application software in computational physics and geoscience, respectively, where review primarily focuses on the article. Chue Hong maintains a list of journals in both categories ( Chue Hong, 2016 ).
Peer review in JOSS
In this section, we illustrate the JOSS submission and review process using a representative example, document the review criteria provided to authors and reviewers, and explain a fast-track option for already-reviewed rOpenSci contributions.
The JOSS process
Figure 3 shows a typical JOSS submission and review process, described here in more detail using the hdbscan package ( McInnes, Healy & Astels, 2017 ) as an example:

- 1. Leland McInnes submitted the hdbscan software and article to JOSS on 26 February 2017 using the web application and submission tool. The article is a Markdown file named paper.md , visibly located in the software repository (here, and in many cases, placed together with auxiliary files in a paper directory).
The editor then asked the automated bot Whedon to create the main submission review issue via the command @whedon start review magic-word=bananas . (“ magic-word=bananas ” is a safeguard against accidentally creating a review issue prematurely.)
Note that JOSS reviews are subject to a code of conduct ( Smith & Niemeyer, 2016 ), adopted from the Contributor Covenant Code of Conduct ( Ehmke, 2016 ). Both authors and reviewers must confirm that they have read and will adhere to this Code of Conduct, during submission and with their review, respectively.
- 4. After the review was complete, the editor asked the submitting author to make a permanent archive of the software (including any changes made during review) with a service such as Zenodo or Figshare, and to post a link to the archive in the review thread. This link, in the form of a DOI, was associated with the submission via the command @whedon set 10.5281/zenodo.401403 as archive .
- 5. The editor-in-chief used the Whedon RubyGem library on his local machine to produce the compiled PDF, update the JOSS website, deposit Crossref metadata, and issue a DOI for the submission ( https://doi.org/10.21105/joss.00205 ).
- 6. Finally, the editor-in-chief updated the review issue with the JOSS article DOI and closed the review. The submission was then accepted into the journal.
Authors can also first submit a pre-submission inquiry via an issue in the main JOSS repository ( Smith, 2016b ) if they have questions regarding the suitability of their software for publication, or for any other questions.
JOSS review criteria
As previously mentioned, the JOSS review is primarily concerned with the material in the software repository, focusing on the software and documentation. We do not ask authors to use their software in a research study or include research results in their article beyond as examples; submissions focused on results rather than software should be submitted to research journals. The specific items in the reviewer checklist are:
- – As the reviewer I confirm that I have read the JOSS conflict of interest policy and that there are no conflicts of interest for me to review this work.
- – I confirm that I read and will adhere to the JOSS code of conduct .
- – Repository : Is the source code for this software available at the repository URL?
- – License : Does the repository contain a plain-text LICENSE file with the contents of an OSI-approved software license?
- – Version : Does the release version given match the GitHub release?
- – Authorship : Has the submitting author made major contributions to the software?
- – Installation : Does installation proceed as outlined in the documentation?
- – Functionality : Have the functional claims of the software been confirmed?
- – Performance : Have any performance claims of the software been confirmed?
- – A statement of need : Do the authors clearly state what problems the software is designed to solve and who the target audience is?
- – Installation instructions : Is there a clearly-stated list of dependencies? Ideally these should be handled with an automated package management solution.
- – Example usage : Do the authors include examples of how to use the software (ideally to solve real-world analysis problems)?
- – Functionality documentation : Is the core functionality of the software documented to a satisfactory level (e.g., API method documentation)?
- – Automated tests : Are there automated tests or manual steps described so that the function of the software can be verified?
- – Community guidelines : Are there clear guidelines for third parties wishing to (1) contribute to the software, (2) report issues or problems with the software, and (3) seek support?
- – Authors : Does the paper.md file include a list of authors with their affiliations?
- – References : Do all archival references that should have a DOI list one (e.g., papers, datasets, software)?
Fast track for reviewed rOpenSci contributions
For submissions of software that has already been reviewed under rOpenSci’s rigorous onboarding guidelines ( Ram, Ross & Chamberlain, 2016 ; Ram et al., 2017 ), JOSS does not perform further review. The editor-in-chief is alerted with a note “This submission has been accepted to rOpenSci. The review thread can be found at [LINK TO ONBOARDING ISSUE] ,” allowing such submissions to be fast-tracked to acceptance.
A Review of the First Year
By the end of May 2017, JOSS published 111 articles since its inception in May 2016, and had an additional 41 articles under consideration. Figure 4 shows the monthly and cumulative publication rates; on average, we published 8.5 articles per month, with some (nonstatistical) growth over time.

(A) Numbers of articles published per month, and (B) Cumulative sum of numbers of articles published per month. Data, plotting script, and figure files available ( Niemeyer, 2017a ).
Figure 5 shows the numbers of days taken for processing and review of the 111 published articles (i.e., time between submission and publication), including finding a topic editor and reviewer(s). Since the journal’s inception in May 2016, articles spent on average 45.5 days between submission and publication (median 32 days, interquartile range 52.3 days) The shortest review took a single day, for Application Skeleton ( Zhang et al., 2016 ), while the longest review took 190 days, for walkr ( Yao & Kane, 2017 ). In the former case, the rapid turnaround can be attributed to the relatively minor revisions needed (in addition to quick editor, reviewer, and author actions and responses). In contrast, the latter case took much longer due to delays in selecting an editor and finding an appropriate reviewer, and a multimonth delay between selecting a reviewer and receiving reviews. In other cases with long review periods, some delays in responding to requests for updates may be attributed to reviewers (or editors) missing GitHub notifications from the review issue comments. We have already taken steps to improve the ability of authors, reviewers, and editors to keep track of their submissions, including a prompt to new reviewers to unsubscribe from the main joss-reviews repository ( Smith, 2016a ) (to reduce unnecessary notifications) and a weekly digest email for JOSS editors to keep track of their submissions. In the future we may collect the email addresses of reviewers so we can extend this functionality to them.

Figure 6 shows the frequency of programming languages appearing in JOSS articles. Python appears the most with over half of published software articles (54), while R is used in nearly one-third of articles (29). We believe the popularity of Python and R in JOSS submissions is the result of (1) the adoption of these languages (and open-source practices) in scientific computing communities and (2) our relationship with the rOpenSci project.

Total sums to greater than 111, because some packages are multi-language. Data, plotting script, and figure file are available ( Niemeyer, 2017a ).
Each article considered by JOSS undergoes review by one or more reviewers. The set of 111 published articles have been reviewed by 93 unique reviewers. The majority of articles received a review by one reviewer (average of 1.11 ± 0.34), with a maximum of three reviewers. Based on available data in the review issues, on average, editors reached out to 1.85 ± 1.40 potential reviewers (at most 8 in one case) via mentions in the GitHub review issue. This does not include external communication, e.g., via email or Twitter. Overall, JOSS editors contacted 1.65 potential reviewers for each actual review (based on means).
Interestingly, the current reviewer list contains only 52 entries, as of this writing ( reviewers.csv, 2017 ). 2 Considering the unique reviewer count of 93, we clearly have reached beyond those that volunteered to review a priori. Benefits of using GitHub’s issue infrastructure and our open reviews include: (1) the ability to tag multiple people, via their GitHub handles, to invite them as potential reviewers; (2) the discoverability of the work so that people may volunteer to review without being formally contacted; (3) the ability to get additional, unprompted feedback and comments; and (4) the ability to find reviewers by openly advertising, e.g., on social media. Furthermore, GitHub is a well-known, commonly used platform where many (if not most) potential authors and reviewers already have accounts.
Figure 7 shows the numbers of articles managed by each of the JOSS editors. Editor-in-chief Arfon Smith stewarded the majority of articles published in the first year. This was somewhat unavoidable in the first three months after launch, as Smith served as the de facto sole editor for all submissions, with other members of the editorial board assisting. This strategy was not sustainable and, over time, we adopted the pre-review/review procedure to hand off articles to editors. Also, authors can now select during submission the appropriate editor based on article topic.

Data, plotting script, and figure file are available ( Niemeyer, 2017a ).
Lastly, we analyzed the affiliations of the 286 authors associated with articles published in the first year. Figure 8 shows the number of authors per country; we represented authors with multiple affiliations in different countries using their first affiliation. Authors with no affiliation, or where we could not identify the country, are shown as “unknown.” From the articles published in the first year, approximately 48% of authors live in the United States and approximately 40% live in Europe (including Switzerland). The remaining 12% come from the rest of the world, most notably Australia (6.6%) and Canada (2.1%). Moving forward, we hope to receive submissions from authors in more countries that even better represent who develops research software around the world; one strategy to achieve this involves continuing to expand our editorial board.

In its first year, JOSS also developed formal relationships with two US-based nonprofit organizations. In March 2017, JOSS became a community affiliate of the Open Source Initiative ( https://opensource.org ), the steward of the open-source definition, which promotes open-source software and educates about appropriate software licenses. And, in April 2017, JOSS became a fiscally sponsored project of NumFOCUS ( https://www.numfocus.org ), a 501(c)(3) charity that supports and promotes “world-class, innovative, open source scientific computing.” Being associated with these two prominent community organizations increases the trust of the community in our efforts. Furthermore, as a NumFOCUS project, JOSS will be able to raise funding to sustain its activities and grow.
The Second Year for JOSS
Our focus for the second year will be on continuing to provide a high-quality experience for submitting authors and reviewers, and making the best use of the editorial board. In our first year, we progressed from a model where the editor-in-chief handled most central functions to one with more distributed roles for the editors, particularly that of ensuring that reviews are useful and timely. Editors can now select and self-assign to submissions they want to manage, while the editor-in-chief only assigns the remaining submissions. As JOSS grows, the process of distributing functions across the editorial board will continue to evolve—and more editors may be needed.
In the second year, we plan to complete a number of high-priority improvements to the JOSS toolchain. Specifically, we plan on automating the final steps for accepting an article. For example, generating Crossref metadata and compiling the article are both currently handled by the editor-in-chief on his local machine using the Whedon RubyGem library. In the future, we would like authors and reviewers to be able to ask the Whedon-API bot to compile the paper for them, and other editors should be able to ask the bot to complete the submission of Crossref metadata on their behalf. Other improvements are constantly under discussion on the JOSS GitHub repository ( https://github.com/openjournals/joss/issues ). In fact, anyone is able to report bugs and suggest enhancements to the experience. And, since the JOSS tools are open source, we welcome contributions in the form of bug-fixes or enhancements via the usual pull-request protocols.
Beyond roles and responsibilities for the editors, and improvements to the JOSS tools and infrastructure, we will take on the more tricky questions about publishing software, such as how to handle new software versions. Unlike traditional research articles that remain static once published, software usually changes over time, at least for maintenance and to avoid software rot/collapse (where software stops working because of changes in the environment, such as dependencies on libraries or operating system). Furthermore, because all potential uses of the software are not known at the start of a project, the need or opportunity arises to add features, improve performance, improve accuracy, etc. After making one or more changes, software developers frequently update the software with a new version number. Over time, the culmination of these changes may result in a major update to the software, and with many new contributors a new version might correspond to a new set of authors if the software is published. However, this process may not translate clearly to JOSS . The editorial board will accept a new JOSS article published with each major version or even a minor version if the changes seem significant enough to the editor and reviewer(s), but we do not yet know if this will satisfy the needs of both developers and users (corresponding to JOSS authors and readers, respectively).
The discussion about new software versions also generally applies to software forks, where software is copied and, after some divergent development, a new software package emerges. Similar to how we handle new software versions, the JOSS editorial board will consider publication of an article describing a forked version of software if it includes substantial changes from a previously published version. Authorship questions may be more challenging when dealing with forks compared with new versions, since forks can retain varying amounts of code from the original projects. However, while a version control history generally makes it easy to suggest people who should be authors, deciding on authorship can be difficult and subjective, and is therefore ultimately project-dependent. We prefer to leave authorship decisions to the projects, with discussion taking place as needed with reviewers and editors.
Conclusions
Software today encapsulates—and generates—important research knowledge, yet it has not entered the science publication ecosystem in a practical way. This situation is costly for science, through the lack of career progression for valuable personnel: research software developers. We founded JOSS in response to the acute need for an answer to this predicament. JOSS is a venue for authors who wish to receive constructive peer feedback, publish, and collect citations for their research software. By encouraging researchers to develop their software following best practices, and then share and publish it openly, JOSS supports the broader open-science movement. The number of submissions confirms the keen demand for this publishing mechanism: more than 100 accepted articles in the first year and more than 40 others under review. By the end of 2017, JOSS has published nearly 200 articles. Community members have also responded positively when asked to review submissions in an open and non-traditional format, contributing useful reviews of the submitted software.
However, we are still overcoming initial hurdles to achieve our goals. JOSS is currently not fully indexed by Google Scholar, despite the fact that JOSS articles include adequate metadata and that we made an explicit request for inclusion in March 2017 (see GitHub issue #130). Also, we may need to invest more effort into raising awareness of good practices for citing JOSS articles. That said, we have some preliminary citation statistics: according to Google Scholar, corner.py ( Foreman-Mackey, 2016 ) and Armadillo ( Sanderson & Curtin, 2016 ) have been cited the most at 116 and 79 times, respectively. Crossref’s Cited-by service—which relies on publishers depositing reference information—reports 45 and 28 citations for the same articles ( JOSS Cited-by report, 2017 ). While most other articles have received no citations to-date, a few have been cited between one and five times. We have had at least two “repeat” submissions, i.e., submissions of a new version with major changes from a prior version. Clementi et al. (2017) published PyGBe-LSPR , a new version that added substantially new features over the original PyGBe of Cooper et al. (2016) . Similarly, the software published by Sanderson & Curtin (2017) extended on (and cited) their earlier article ( Sanderson & Curtin, 2016 ).
The journal cemented its position in the first year of operation, building trust within the community of open-source research-software developers and growing in name recognition. It also earned weighty affiliations with OSI and NumFOCUS, the latter bringing the opportunity to raise funding for sustained operations. Although publishing costs are low at $3–6 per article, JOSS does need funding, with the editor-in-chief having borne the expenses personally to pull off the journal launch. Incorporating a small article charge (waived upon request) may be a route to allow authors to contribute to JOSS in the future, but we have not yet decided on this change. Under the NumFOCUS nonprofit umbrella, JOSS is now eligible to seek grants for sustaining its future, engaging in new efforts like outreach, and improving its infrastructure and tooling.
Outreach to other communities still unaware of JOSS is certainly part of our growth strategy. Awareness of the journal so far has mostly spread through word-of-mouth and social networking ( Tauber, 2016 ; Brown, 2017 ), plus a couple of news articles ( Perkel, 2017 ; Moore, 2016 ). As of August 2017, JOSS is also listed in the Directory of Open Access Journals (DOAJ) ( https://doaj.org/toc/2475-9066 ). We plan to present JOSS at relevant domain conferences, like we did at the 2017 SIAM Conference on Computational Science & Engineering ( Smith et al., 2017 ) and the 16th Annual Scientific Computing with Python Conference (SciPy 2017). We are also interested in partnering with other domain journals that focus on (traditional) research articles. In such partnerships, traditional peer review of the research would be paired with peer review of the software, with JOSS taking responsibility for the latter.
Finally, the infrastructure and tooling of JOSS have unexpected added values: while developed to support and streamline the JOSS publication process, these open-source tools generalize to a lightweight journal-management system. The JOSS web application and submission tool, the Whedon RubyGem library, and the Whedon-API bot could be easily forked to create overlay journals for other content types (data sets, posters, figures, etc.). The original artifacts could be archived on other services such as Figshare, Zenodo, Dryad, arXiv, or engrXiv/AgriXiv/LawArXiv/PsyArXiv/SocArXiv/bioRxiv. This presents manifold opportunities to expand the ways we assign career credit to the digital artifacts of research. JOSS was born to answer the needs of research software developers to thrive in the current merit traditions of science, but we may have come upon a generalizable formula for digital science.
Funding Statement
This work was supported in part by the Alfred P. Sloan Foundation. Work by K E Niemeyer was supported in part by the National Science Foundation (No. ACI-1535065). Work by P Prins was supported by the National Institute of Health (R01 GM123489, 2017-2022). Work by K. Ram was supported in part by The Leona M and Harry B. Helmsley Charitable Trust (No. 2016PG-BRI004). Work by A Rokem was supported by the Gordon & Betty Moore Foundation and the Alfred P. Sloan Foundation, and by grants from the Bill & Melinda Gates Foundation, the National Science Foundation (No. 1550224), and the National Institute of Mental Health (No. 1R25MH112480). There was no additional external funding received for this study. The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
Additional Information and Declarations
Daniel S. Katz is an Academic Editor for PeerJ CS. Abigail Cabunoc Mayes is an employee of Mozilla Foundation. Tracy K. Teal is an employee of Data Carpentry.
Arfon M. Smith conceived and designed the experiments, wrote the paper, prepared figures and/or tables, performed the computation work, reviewed drafts of the paper, edited submissions.
Kyle E. Niemeyer conceived and designed the experiments, analyzed the data, wrote the paper, prepared figures and/or tables, performed the computation work, reviewed drafts of the paper, edited submissions.
Daniel S. Katz and Lorena A. Barba , conceived and designed the experiments, wrote the paper, reviewed drafts of the paper, edited submissions.
George Githinji , Melissa Gymrek , Pjotr Prins , Ariel Rokem and Roman Valls Guimera reviewed drafts of the paper, edited submissions.
Kathryn D. Huff , Christopher R. Madan , Abigail Cabunoc Mayes , Kevin M. Moerman , Karthik Ram , Tracy K. Teal and Jacob T. Vanderplas conceived and designed the experiments, reviewed drafts of the paper, edited submissions.
- Fellowships
Covering thought leadership in journalism

Open-Source Journalism in a Wired World
Spurred by russia’s invasion of ukraine, open-source investigations are being integrated into standard newsroom practice.

By Maxim Edwards
December 7, 2022.
Apple’s Find My tool can show you where that Russian soldier who stole a local’s headphones ended up.
A heat signature tracker can show you where fires rage in the warzones of Ukraine’s east and south.
Satellite imagery starkly comparing Ukraine’s cityscapes before and after Russian airstrikes is now a regular fixture in the news.
More than nine months into the Russian invasion of Ukraine, the online methods for tracking this war are many and proliferating, including the most obvious source of all — social media networks. A 2019 law designed to keep its military from posting on social media has not deterred Russian servicemen from sharing images and updates from the frontline, not least on Telegram and the Russian social network VKontakte, potentially allowing anyone with an Internet connection to pinpoint the place, time, and sometimes individuals seen in footage of military movements.
Open-source investigations (OSI), popularly and misleadingly known as open-source intelligence, is not synonymous with social media, however. OSI is any information that can be publicly accessed by others, including but not limited to online sources. That includes everything from local newspapers to satellite imagery and images shared on TripAdvisor. What it doesn’t include are two mainstays of traditional investigative journalism — non-public document leaks or closed-source reporting, otherwise known as shoe-leather reporting and interviews.
Over the past few years, newsrooms have started integrating open-source methods into their coverage and building their own OSI teams. That’s in part to verify social media posts, and in part to report on places where it is simply too dangerous for journalists to venture — areas on or behind the frontlines — where open-source imagery allows a glimpse into military movements and potential war crimes. Since Russia’s invasion of Ukraine, open-source investigations have surged in prominence and the genre as a whole has attracted scrutiny, not least from state actors themselves.
Rising awareness of what open sources can yield has motivated journalists to do more than simply verify what they find online. Several newsrooms now have dedicated open-source teams, like The Washington Post’s visual forensics team and the BBC’s Africa Eye, which recently used social media images to reconstruct the scene of a horrific clash at the fence surrounding the Spanish enclave of Melilla’s border with Morocco, in which 24 migrants were killed. There’s also The New York Times’ visual investigations unit, which in April used satellite imagery to debunk Moscow’s claims that bodies had been placed on the streets of Bucha after Russian troops had withdrawn from the Ukrainian town.
Open-source newsgathering is becoming integrated into journalistic practice as a standard reporting technique, particularly in investigative newsrooms. The divide between open-source investigations in the form of online research and closed-source investigations may turn out to be a generational one. For young journalists who have been socialized online, the Internet has always been a source of public interest information.
A Brief History of OSI
Before these changes, the techniques and processes needed to analyze such images existed but were seldom pursued publicly and in the public interest. Corporations could use them to scour the earth’s surface for signs of hydrocarbons or minerals; governments could take stock of their opponents’ airstrips or military emplacements. They still do. But now, so can everybody else.

Felipe Dana/AP Photo
Open-source research used to take place at both ends of the resource spectrum. At one end, state actors and corporate due-diligence departments vetting new employees or compiling risk assessments for investors; at the other, social media hobbyists with lots of time and patience scouring images and videos to fact-check claims made by parties in various armed conflicts. Theirs was a smaller community confined to mailing groups, forums, and independent blogs rather than the largely Twitter-dominated open-source volunteer community we know today.
Around a decade or so ago, early news aggregator sites started to fill the space in-between. Storyful, founded in 2010, offered a service akin to an open-source newswire, verifying and contextualizing social media posts to a standard that traditional news media could then incorporate in their reporting — later offering its own open-source investigative services. Collectives like Forensic Architecture, also founded in 2010, and Bellingcat, where I work, founded in 2014, turned these techniques towards egregious human rights violations in a manner more like the research department of a watchdog NGO than a traditional newsroom.
Bellingcat’s first big scoop, for example, concerned the shooting down of Malaysian Airlines flight MH17 in July 2014. Founder Eliot Higgins and other volunteers examined social media footage to corroborate claims that a BUK missile launcher operated by pro-Russian militiamen had fired from occupied Ukrainian territory on the day of the attack. This doggedness also took aim at Russian state actors’ attempts to obfuscate and derail this line of enquiry, most notably in apparently doctored satellite imagery presented at a press conference in July 2014 by the Russian Ministry of Defense.
Journalists have used open sources in coverage before. In 2013, The New York Times’ C.J. Chivers and Eric Schmitt followed up on Higgins’ documentation of small arms being used in the Syrian Civil War to produce a longer article on how Yugoslav-manufactured weapons made during the Cold War were making their way to that conflict. The first clues to the existence of the Xinjiang internment camps were discovered by the German academic Adrian Zenz, in the form of construction tenders publicly available on local government websites that corroborated rumors of a new mass incarceration system. In several cases, the size and location of these facilities could then be verified with satellite imagery and were consistent with survivor testimony.
In the tense weeks before Russia’s Feb. 24 invasion, open-source imagery — showing the incremental buildup of a significant Russian military force along the borders of Ukraine — was the basis among the commentariat for a battle of interpretations as to Russia’s ultimate objectives.
When Russian tanks crossed into Ukraine, open-source analysts saw a surge in followers, although the generational shift in the field could be felt in the increased importance of a wider range of social networks, most prominently TikTok, as a source for footage of Russian military equipment on the move. Most reporters online following the war now know the intricate maps compiled by Nathan Ruser, based on open-source evidence of military movements on the frontline as well as geo- and chronolocated footage posted on social media networks, particularly Telegram. They know the pseudonymous Oryx Spioenkop, who famously counts Russian tank losses (and their conversion to Ukrainian tank gains), and the ship spotter Yorük Işık, who tracks maritime movement through the Turkish straits. These names now feature prominently in news and investigative reports.
How OSI Works

Dominique Faget/AFP via Getty Images
These kinds of responses were familiar to anybody who had witnessed the reaction of Russian state media channels following the shooting down of flight MH17 eight years earlier. The purpose was presumably not to convince anybody of the merits of these false arguments but, like similar “fake news” strategies used by politicians and governments, to muddy the waters, to advance an epistemological nihilism. Open-source evidence showed the truth.
While journalists in Ukraine for The Guardian and CNN were able to visit Kremenchuk and interview eyewitnesses, Bellingcat quickly verified and analyzed all open-source imagery we could find relating to the event. A CCTV video from a nearby factory posted to social media showed the moment of the explosion as locals strolling in a park fled for cover. There were no secondary explosions from neighboring buildings, as would be expected if an ammunition warehouse had been struck. No significant impact site could be seen anywhere near the mall, undermining claims that a fire spread from the factory area.
Russian media had claimed that a lack of activity and reviews on Google and a lack of images from inside the mall proved that the building was closed at the time of the strikes. But the social media pages of various businesses based at the Amstor mall had posted announcements welcoming their customers back on June 25. These later offered messages of condolences to their employees who had been killed or wounded in the attack.
The same pro-Kremlin media outlets opined that the lack of vehicles in the mall’s car park in the footage of the aftermath also proved that the mall had been closed. But satellite imagery Bellingcat reviewed dating back to 2016 showed many occasions during opening hours when the parking lot had been sparsely occupied. Moreover, online mapping services and guides to Kremenchuk put the Amstor mall well within walking distance of bus and trolley stops. One Ukrainian even posted a receipt for a purchase made at the mall shortly before the attack, showing the date, time and address of the mall — a key piece of evidence that widely circulated on Twitter.
None of us working on the Kremenchuk missile strike set foot in Ukraine that day. But we reached the same conclusions as journalists in-country, such as The Guardian’s Lorenzo Tondo, who cited our findings in his report from Amstor. What makes an organization like Bellingcat unique is no longer that we produce open-source investigations, but that we use exclusively open-source information in our investigative process.
“The successful integration of open source into journalism requires humility about the limitations of the genre, an acknowledgement of what information cannot be obtained from open sources, and how traditional reporting methods must be used to obtain that information”
Kremenchuk was one of several cases where Bellingcat employed open-source research to debunk specific, contradictory Russian claims designed to deflect scrutiny. But the excitement for open source can lead to extravagant expectations for the genre. A ‘footage fetish’ — a phrase coined by Jeremy Morris, professor of global studies at Aarhus University in Denmark — is taking hold on social media. It’s more important than ever to remember that a single image rarely tells the whole story. A case in point is Ukrainians’ adherence to their government’s request not to post images and videos of the Ukrainian military on the move — leaving an important gap in what open-source research alone can contribute to comparisons between the Russian and Ukrainian forces. The successful integration of open source into journalism requires humility about the limitations of the genre, an acknowledgement of what information cannot be obtained from open sources, and how traditional reporting methods must be used to obtain that information.
Open-source sleuthing will not — and should not — fully replace traditional reporting. In fact, some of the finest investigative journalism on Russia’s invasion has come from the union of the two genres. In May, a spraypainted Instagram handle in a house in Bucha gave one Reuters journalist a further clue as to the Russian unit present during the massacres in the occupied Ukrainian town. Later that month, The Wall Street Journal combined local news reports, on-the-ground interviews, and dash cam videos filmed by locals to show how Russian forces had fired on civilians traversing the “road of death” west of Kyiv.
Residents of the town of Motyzhyn told the Wall Street Journal that they had been deliberately fired upon on this perilous four-mile road. Journalists later analyzed mortar fragments — they were a type that has a range of between two to five miles — found at the locations identified by the civilians. A local in the town who had shared a firing location with Ukrainian territorial defense units shared the information with reporters. This location was not only within the range of the aforementioned mortar type but had seen heavy Russian military activity in the timeframe civilians mentioned coming under attack.
This forested area yielded mass graves and the detritus of Russian military soldiers’ encampments, including badges from the 37th Guards’ Motor Rifle Brigade. A creative confirmation of Russian military activity was provided by the family of Oleg Moskalenko, a local who was detained by Russian soldiers at an impromptu checkpoint along the road that was threatened by Russian fire from the north. During his absence, his relatives traced his iPhone to the grassy area north of the road using the Find My function.
The Ethics of OSI
Yet these new methods bring with them new editorial and ethical questions about applying journalistic best practice.

Daniel Berehulak/New York Times via Redux
Open-source research offers journalism the promise of a participatory model that could, in theory, help enhance trust in the media, which has been in steady decline for more than a decade. At the heart of open-source research is the hope that audiences can, if they access the same materials, follow the same steps and reach the same conclusions as the journalists did. This is the essence of the “show your work” principle — sharing source documents, publishing full transcripts of interviews — that many news outlets now make a routine part of their reporting.
Journalists’ pleas for public input to complete their stories are not new. In 2010, amid growing enthusiasm for the rise of citizen journalism, The Guardian’s Paul Lewis took to Twitter to appeal to airline passengers and later for their ticket stubs. He was seeking anybody who had witnessed the death of asylum seeker Jimmy Mubenga, who lost consciousness while being restrained on a British Airways plane bound for Angola.
In 2016, David Fahrenthold, then with The Washington Post, pieced together Donald Trump’s charitable giving through a mix of old newspaper clippings and New York State tax filings to compare Trump’s public statements about his foundation’s philanthropy with hard data. When Fahrenthold began contacting hundreds of charities to see if they’d gotten donations from Trump, he took pictures of his notes and shared them on Twitter to see if he was missing anything. The result was a comprehensive look at how Trump used his charitable donations to purchase art and other items for himself.
A recent Reuters Institute study found that many of today’s news consumers implicitly trust visual media more than text, a finding that should be very promising for open-source journalism. But open-source intelligence does not always speak for itself. It often needs contextualization and interpretation. Images of rows of burnt-out tanks alone may mean little to readers, and even less when the open-source researchers do not state clearly how they verified the image.
Even when open-source research is not paired with shoe-leather reporting, it still needs thorough vetting. One example is the extensive use of expert comment by BBC’s World Service Disinformation Team in debunking Russian state media claims that Ukraine was selling weapons provided by NATO on the black market. A standard reverse image search revealed that photographs that ostensibly showed weapons for sale were in fact several years old and had previously appeared on a gun enthusiast’s website in 2014. But reporters also noticed that these purportedly Ukrainian channels had misspelled Kyiv in Ukrainian, a clue that prompted them to go undercover and contact the site administrators posing as a buyer. Their interlocutor also made significant errors in Ukrainian. According to a linguist interviewed by the journalists, these mistakes suggested the messages had in fact been written by a Russian speaker with the aid of translation software. Without this expert comment, such an editorial observation may have seemed highly subjective and speculative, undermining trust in both open- and closed-source components of the reporting.
In today’s open-source journalism, transparency of method and transparency of sources are even more tightly braided together. After Bellingcat’s December 2020 investigation into the poisoning of Russian opposition politician Alexey Navalny, which implicated members of Russia’s Federal Security Services (FSB), we decided to make public a spreadsheet containing the travel data of members of the poison squad. Several members of the public soon noticed correlations with the mysterious deaths or severe illnesses of a number of other opposition activists in Russia — from a local activist in Dagestan to the celebrated Russian poet Dmitry Bykov. Thus, an entire series of investigations was born. Our readers had not just contributed to the story but determined what that story would be.
The Limits of OSI
When it comes to footage, this participatory model can be complicated by platforms’ attempts to become more responsible content moderators. Posts from warzones that are relevant to journalists are removed because they often breach policies on depictions of violence. So, when this kind of material is deleted, the unconvinced reader may still have only the journalist’s word that relevant posts ever existed, potentially undermining transparency.
But best practice can also dictate that journalists sometimes refrain from being fully transparent about source material. In several European jurisdictions, media generally refrain from publishing the faces of private individuals suspected of but not officially charged with a crime.
Bellingcat obscures much of the extremist, incendiary social media posts we encounter in our reporting on far-right online subcultures, in line with best practice laid out in the Data Society’s 2018 Oxygen of Amplification report. This decision stems from a desire not only to avoid inadvertently amplifying hate speech, but to instead emphasize its context, discourse, and spread in order to redirect the focus away from that preferred by extremists. As we know from reporting on the far-right in North America, fascist groups are particularly adept at gaming the system, parrying and provoking the news media into rewarding them with notoriety and free publicity. The same questions could be asked of the need to gratuitously reproduce the hate speech made by Russian television pundits and nationalist bloggers towards Ukrainians.

David Fahrenthold/Washington Post
This dilemma is even more acute when faced with distressing footage that may depict war crimes. In February, Bellingcat reported on a series of apparently staged videos recorded by pro-Russian media channels in the run-up to the war. In one gruesome example from the Donetsk-Horlivka highway, a cadaver showing signs of a medical autopsy had been placed in a burnt-out vehicle; Russian journalists asserted that the body belonged to a local civilian killed by a Ukrainian improvised explosive device (IED). My colleagues noted a neat cut through the skull cap of one of the corpses in the vehicle, which a forensic pathologist told us was consistent with an autopsy procedure. This indicated that the body was likely placed in the vehicle before it was set alight. We chose not to embed links to the full, extremely graphic content and to obscure sections of imagery we had to publish in order to show the top of the skull in question.
In August, we reported on one of the most disturbing videos of the conflict, posted on Russian social media from the frontline near Pryvillia, depicted a group of Russian paramilitary fighters mutilating and then executing a captured Ukrainian soldier in an act of horrific sexual violence. We chose not to link to the video and obscured disturbing elements of screenshots presented for analytical purposes — in this case, features which allowed us to connect two videos believed to be taken at the same spot as well as those that allowed us to eventually geolocate both to the crime scene. These features were not only visual: In describing the video, we omitted several extremely disturbing details about the act of sexual violence depicted, which were not essential to the purpose of the analysis.
There are a growing number of resources dedicated to the ethics of open-source research in media. A recent report from the Stanley Center, a policy organization dedicated to peace and security, includes a comprehensive workbook designed to introduce researchers to conundrums loosely based on real examples, for example. Some of these, such as a researcher considering whether to use a “sock puppet” account to view a closed social media profile, broadly echo traditional journalistic debates about the ethical limits of what can be done to secure access to crucial sources. Others, such as a manager considering the ethical responsibilities of requesting her employees to review hours of graphic material online, are perhaps more novel. In the context of Ukraine, the latter can have broader implications for readers, too. Frank conversations about the need to share extremely graphic evidence of war crimes need to be held, especially when Russian state actors and conspiracy theorists repeatedly deny such evidence.
The consequences of poorly conducted OSINT analysis can be severe. In the case of the disturbing video from Pryvillia, there were very few visual clues to conclusively identify the culprit in the mutilation scene itself, though the face of a man wearing the same clothes as the culprit could be seen in other videos taken in the same area with the same Russian paramilitary unit. Crucially, this man was one of the few of East Asian appearance in footage of these soldiers, likely a member of an ethnic minority from Siberia, Russia’s Far East, or areas of the North Caucasus. On this basis, some open-source researchers used facial recognition websites that incorrectly identified a man from Russia’s Republic of Kalmykia in the North Caucasus as the suspected culprit. The likely culprit, Bellingcat and partners ascertained, actually came from southern Siberia.
In Ukraine, this facial recognition process often involves Russian search engines, such as FindClone, which then attribute a name and social media page link to the identified face. Researchers should be careful never to rely wholly on facial recognition for identification given the possible ethnic and racial bias, as studies have found on U.S. examples with Black faces. Nevertheless, the incorrect identification circulated widely, a testament to the high stakes of online misinformation. The actual suspect was later sanctioned by the U.S. authorities.
Then there are the risks Ukrainians themselves face. Ordinary Ukrainians are increasingly waging their own war with digital tools and drones. But footage is geolocatable, and they risk becoming targets for prosecution or worse, particularly in occupied territories. These risks place a palpable ethical burden on newsrooms, which are the first to amplify such footage. For example, in Bellingcat’s interactive map of incidents of harm to civilians in Ukraine, my colleagues have partially obscured the geolocations of footage when it is believed that the authors could be endangered if their identity was revealed.
An awareness that the fruits of their research can translate into real action against people perpetrating possible war crimes may draw even more enthusiasts towards these open-source methods
Footage of these horrors — not only potential war crimes but the cumulative drip of suffering in the form of destroyed schools, crying refugees, and homes ablaze — can present a psychological risk to volunteer researchers and members of the public who may not benefit from the same institutional support afforded journalists. Yet these same researchers are increasingly an invaluable resource to mainstream journalists. Concerns about secondary traumatic stress — repeated and prolonged exposure to the trauma of others — has prompted my colleagues to either remove particularly disturbing elements of such content when working on it with volunteers or not expose them to it at all.
The horrors unfolding in Ukraine could set an important precedent for the admissibility of online information in international criminal tribunals. An awareness that the fruits of their research can translate into real action against people perpetrating possible war crimes may draw even more enthusiasts towards these open-source methods. This thirst for justice and accountability is the same pull factor that drew enthusiasts towards traditional investigative journalism.
In this sense, open-source practitioners’ openness to collaboration also interrupts traditional journalistic exclusivity, promoting a skillset and methodology that can be and is being employed by the general public. However, in an ideal collaboration with news media, its impact is enhanced not only by the reach of the latter but by the application of ethically grounded journalistic practice. In this partnership, as University of Gothenburg researchers Nina Müller and Jenny Wiik wrote in Journalism Practice in 2021, journalists are “no longer gatekeepers” but “gate-openers,” coordinating different actors with different skills and competencies.
But the process of producing OSINT in newsrooms to journalistic standards takes time, training, and money — things often in short supply. What appears to be a simple geolocation can take hours if not days of paid staff time to verify. Some of the most memorable open-source stories are the fruits of long-established habits of trawling online data about highly specific if not arcane subjects of interest. This can be a luxury to reporters under time and financial pressure. Moreover, the fruits of crowdsourced research from the volunteer community should also be verified in-house. All this takes considerable time, and that time means staffing costs. Open source is no silver bullet.
Established open-source researchers can learn a lot from journalistic best practice, but journalism also has a great deal to learn from the open-source research community. OSINT practitioners are not as proprietorial about their findings as journalists, and they exhibit the collaborative impulse journalists hope will help save their field. Just as the collaboration among journalists also needs to gain equilibrium, so should the relationship between large legacy newsrooms and open-source volunteers who have substantially contributed to their coverage of Ukraine.

Dimitar Dilkoff/AFP via Getty Images
Open-source research is also fragile by nature. The wider the publicity for sensitive open-source investigations, the more circumspect social media users become about sharing information that could be in the public interest. The field’s methodological transparency is at once its greatest asset and its greatest hindrance. As open-source research gains prominence, more and more actors will be inspired, and not all of them will use these techniques for the public good.
In autocratic and democratic societies alike, data has become a very valuable commodity for political control or commercial advantage. But governments have been slow to recognize that the surveillance can go both ways. States that collect data about their citizens also collect this data about their own functionaries. The internet is sieve, and in some countries it leaks more than others. Russia’s black data markets, which played the key role in investigating the men who followed and poisoned Alexey Navalny, have thrived in part due to the pervasive corruption in Russia.
But the same dynamic can be found in countries of diverse political systems: As Haaretz has reported, Israel’s data brokers have also come to the fore to sell personal information. Perhaps the greatest ally of an open-source researcher is banal human error by those hunters who believe that they cannot be hunted — the same human error which allowed my colleagues to discover that U.S. servicemen in Europe upload sensitive details about nuclear weapons to publicly available flashcard applications. The hope has to be that OSI will continue to offer a way to hold the powerful to account.
“Back when I started training media in 2013 and presenting open-source techniques, it was as though I was doing magic tricks,” says Eliot Higgins, Bellingcat’s founder. “But now, if you’re not doing it, you’re not doing your job.”
🇺🇦 make metadata, not war
A comprehensive bibliographic database of the world’s scholarly literature
The world’s largest collection of open access research papers, machine access to our vast unique full text corpus, core features, indexing the world’s repositories.
We serve the global network of repositories and journals
Comprehensive data coverage
We provide both metadata and full text access to our comprehensive collection through our APIs and Datasets
Powerful services
We create powerful services for researchers, universities, and industry
Cutting-edge solutions
We research and develop innovative data-driven and AI solutions
Committed to the POSI
Cost-free PIDs for your repository
OAI identifiers are unique identifiers minted cost-free by repositories. Ensure that your repository is correctly configured, enabling the CORE OAI Resolver to redirect your identifiers to your repository landing pages.
OAI IDs provide a cost-free option for assigning Persistent Identifiers (PIDs) to your repository records. Learn more.
Who we serve?
Enabling others to create new tools and innovate using a global comprehensive collection of research papers.

“ Our partnership with CORE will provide Turnitin with vast amounts of metadata and full texts that we can ... ” Show more
Gareth Malcolm, Content Partner Manager at Turnitin
Academic institutions.
Making research more discoverable, improving metadata quality, helping to meet and monitor open access compliance.

“ CORE’s role in providing a unified search of repository content is a great tool for the researcher and ex... ” Show more
Nicola Dowson, Library Services Manager at Open University
Researchers & general public.
Tools to find, discover and explore the wealth of open access research. Free for everyone, forever.

“ With millions of research papers available across thousands of different systems, CORE provides an invalu... ” Show more
Jon Tennant, Rogue Paleontologist and Founder of the Open Science MOOC
Helping funders to analyse, audit and monitor open research and accelerate towards open science.

“ Aggregation plays an increasingly essential role in maximising the long-term benefits of open access, hel... ” Show more
Ben Johnson, Research Policy Adviser at Research England
Our services, access to raw data.
Create new and innovative solutions.
Content discovery
Find relevant research and make your research more visible.
Managing content
Manage how your research content is exposed to the world.
Companies using CORE

Gareth Malcolm
Content Partner Manager at Turnitin
Our partnership with CORE will provide Turnitin with vast amounts of metadata and full texts that we can utilise in our plagiarism detection software.
Academic institution using CORE
Kathleen Shearer
Executive Director of the Confederation of Open Access Repositories (COAR)
CORE has significantly assisted the academic institutions participating in our global network with their key mission, which is their scientific content exposure. In addition, CORE has helped our content administrators to showcase the real benefits of repositories via its added value services.
Partner projects

Ben Johnson
Research Policy Adviser
Aggregation plays an increasingly essential role in maximising the long-term benefits of open access, helping to turn the promise of a 'research commons' into a reality. The aggregation services that CORE provides therefore make a very valuable contribution to the evolving open access environment in the UK.

Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Published: 26 October 2023
Building open-source AI
- Yash Raj Shrestha 1 ,
- Georg von Krogh 2 , 3 &
- Stefan Feuerriegel ORCID: orcid.org/0000-0001-7856-8729 4 , 5
Nature Computational Science volume 3 , pages 908–911 ( 2023 ) Cite this article
2763 Accesses
5 Altmetric
Metrics details
- Computer science
- Scientific community
Artificial intelligence (AI) drives innovation across society, economies and science. We argue for the importance of building AI technology according to open-source principles to foster accessibility, collaboration, responsibility and interoperability.
You have full access to this article via your institution.
The computer science community has a long tradition of embracing open-source principles. However, companies increasingly restrict access to AI innovations. An example is OpenAI, which was founded to make scientific research openly available but which eventually restricted access to research findings. Although such a strategy reflects a company’s legitimate incentive to obtain financial returns, such protection increases concentration of power, restricting access to AI technology. Further down the road, concentrated power could lead to growing inequality in AI research, education and public use. Here we discuss why proprietary AI technology should be complemented by open-source AI across the essential components for building AI technology: datasets, source codes and models.
Why exclusive proprietary AI technology is a problem
AI is a key technology that drives innovation across society, economies and science. For example, large language models (LLMs) such as GPT-4 have recently become the backbone of text processing in many fields such as education, entertainment, media and management. Therefore, downstream innovations including novel business models, products and services may be at risk when widespread access to AI becomes restricted. Not surprisingly, the concentration of power over technology is known to hamper future innovation, fair competition, scientific progress, and hence human welfare and development at large 1 .
Proprietary AI technology could also jeopardize inclusiveness and responsibility. When new AI technologies like LLMs are developed exclusively by a few companies, those companies may also arbitrarily decide which countries and languages to support in their systems and may thus exclude some users, such as those from small markets (for instance, the Global South and rare languages). A certain level of openness of AI technology is further necessary for researchers to determine the safety, security and fairness inherent in AI systems operations. Proprietary AI systems are difficult for members of the public to appraise, and thus to identify and fix errors within them.
The benefits of open-source principles in software development
The cardinal idea of open-source software (OSS) is that an organization relies not only on its internal knowledge sources and resources to innovate, but also draws on multiple external technical sources, such as software packages, bug reports, customer feedback, published patents or communities 2 . Depending on the chosen license, OSS may not preclude commercialization: companies can combine OSS with additional products and services to generate revenue (for instance, RedHat offers Linux for free but charges for premium support, Amazon contributes to Apache but charges for hosting services in the cloud, and so forth). Nowadays, the open-source model safeguards effective and efficient software development. Yet it has taken several decades for this model to mature and for companies to realize and utilize its full potential 3 . Also, an important lesson from OSS is that governments played an important part in boosting OSS adoption 4 , suggesting that many ways to promote open-source AI will benefit from governments taking an active role.
OSS offers several benefits relative to proprietary software in terms of accessibility, collaboration, responsibility and interoperability 5 . First, proprietary software is mostly available under licensing fees. In contrast, OSS is free and comes with no or limited restrictions on use, inspection and modification. Second, OSS tends to be developed and maintained by a community. Diversity in an OSS community stimulates improved software quality, faster innovation and increased creativity of OSS development relative to proprietary alternatives 6 . Third, errors in OSS are detected and corrected with everyday use, and much faster than in closed-source software 7 , thus making OSS applicable to critical and highly reliable technical systems. Fourth, OSS typically relies upon open standards and modularity, which decouples dependencies among software components and leads to greater reusability and interoperability 6 .
In addition to cost savings, companies also benefit from OSS in multiple ways. Companies may establish low-cost OSS software as their backbone and then build business models around complementary goods and services 8 . In addition, companies can gain trust and reputation by contributing to OSS, which attracts top talent and fosters the dissemination of their own technologies and products. By participating in OSS activities, companies can also steer the direction of innovation and control the further development of the technology on which they depend (for instance, by introducing a standard that helps the company to compete more effectively). By contributing to OSS, companies also gain valuable feedback on their technologies and are able to identify potential issues with the products early on. Finally, the presence of OSS drives innovation and competitiveness of commercial solutions.
Promoting open-source AI technology
The development of open-source AI and that of OSS share several similarities. However, there are also some important differences that require a tailored approach to building open-source AI. Whereas conventional software is programmed with explicit rules to perform a task, AI is programmed to learn to perform a task. As a result, AI technology has three essential components: datasets for training, source codes for formalizing the training task, and models that eventually store the trained weights. In addition, training AI models requires substantial hardware resources and comes with high operating costs. Furthermore, the use of AI may expose society to large risks (for example, the malicious use of AI to create misinformation), which mandates a responsible societal approach to open-source AI technology. Below we discuss a tailored approach to open-source AI complementary to proprietary AI by fostering (1) accessibility, (2) collaboration, (3) responsibility and (4) interoperability (see Fig. 1 ).
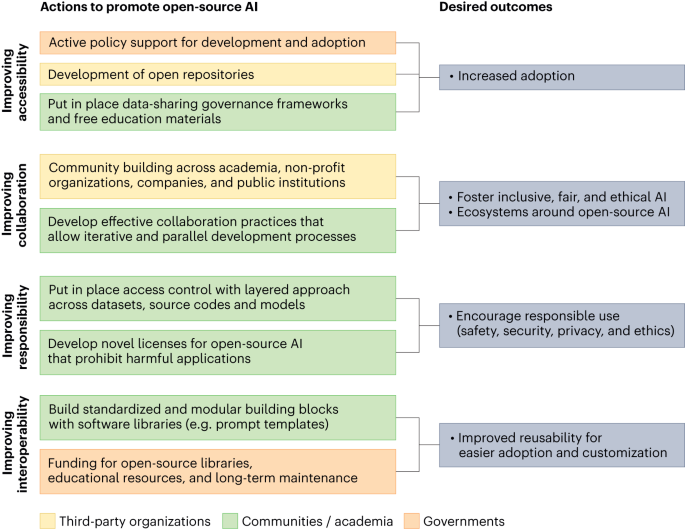
The suggested actions should foster accessibility, collaboration, responsibility and interoperability.
Improving accessibility
To foster accessibility, policy-makers should proactively encourage the development and adoption of open-source AI. Since AI innovation is considerably more capital-intensive than regular software development, given the data and infrastructure needs of building contemporary AI models, additional resources (such as funding and access to large-scale infrastructure and data) are needed to kickstart and scale open-source AI technology. Importantly, existing computational resources are often not of sufficient magnitude to build state-of-the-art AI technology comparable to that of for-profit companies. For example, the development of a LLM is estimated to cost between 300 and 400 million euros. Another limiting factor is that, even if the resources are made available, they are often bound to academia and are thus inaccessible to other stakeholders such as non-profit organizations seeking opportunities where AI could be leveraged for social benefits. A promising counterexample is the US roadmap offering broader access to computational resources, including public–private partnerships. Scientists are currently often unable to replicate the AI technology obtained from companies owing to the lack of resources, so such roadmaps could help to facilitate reproducibility (for instance, via the ML Reproducibility Challenge ).
To broaden access to data and models, policy-makers could support the development of open repositories for hosting both under a trustworthy and responsible governance model. Importantly, open datasets from public institutions are often large and originate from diverse sources, which is beneficial in practice. Furthermore, public institutions can actively incentivize data-sharing partnerships, which, in combination with federated learning, may promote AI across institutional boundaries while ensuring data privacy. For example, the German government recently launched a consortium called Mobility Data Space where different stakeholders in the mobility sector (such as public transport companies, private car-sharing providers and car manufacturers) are able to access shared data, even those of competitors.
However, data sharing comes with challenges. First, opening up datasets increases the likelihood of privacy breaches and raises ethical issues around confidentiality, data misrepresentation and informed consent. Second, to organize open data and to maintain fairness in terms of distribution rights and acknowledgments for its contributors is challenging. Fortunately, there has been recent progress with respect to the development of governance frameworks to tackle these challenges, such as the FOT-Net Data Sharing Framework , designed for connected automated driving under the General Data Protection Regulation in the European Union. Such frameworks could be useful starting points in improving accessibility while tackling the ethical, legal and organizational challenges.
Finally, much educational material on state-of-the-art AI is managed by for-profit companies (such as Coursera and Udemy) and is often hidden behind paywalls. Hence, to promote the adoption of open-source AI, more effort is needed to improve access to high-quality educational materials. As a result of the above, the barriers to entry for contribution and access to AI applications will drop considerably.
Improving collaboration
AI technologies may be jointly developed and maintained by diverse and inclusive communities of developers, users and stakeholders. This collaborative approach may greatly reduce the cost of development and contribute to solving scaling problems. This will result in broad participation by stakeholders who can make the future of AI more inclusive and fairer.
To promote collaboration in open-source AI technology, clear steps should be taken towards building communities across academia, non-profit organizations, companies and public institutions. Given that the development of AI models is less easily decomposable into smaller tasks and that task division is more difficult than in standard software development, further effort is needed to develop suitable collaboration practices that allow for more iterative and parallel development processes. Here, the lessons learned from the project BigScience 9 , where over a thousand volunteer scientists have assembled to develop an LLM called BLOOM 10 , should be valuable. Furthermore, policy-makers should fund large-scale initiatives to produce open-source LLMs as complements to proprietary LLMs.
Creating synergies and networks between universities, research centers, government and industry may establish new ecosystems around open-source AI and become a driver for future innovation. Building such ecosystems is especially relevant for start-up firms, and small- and medium-sized enterprises 11 because they often lack the dedicated infrastructure and capacity to boost AI technology.
Improving responsibility
It is important to establish clear barriers against the misuse of AI technology. To this end, access control, similar to existing norms for open data, is needed to enforce the responsible use of open-source AI in practice. Consider, for example, MIMIC-III , a large, freely available health-related dataset. Given the sensitive nature of medical data, MIMIC-III is open to researchers only after they undergo compulsory ethics training. Similarly, access control for open-source AI should consist of a layered approach that varies appropriately across datasets, source codes and models to ensure responsible use, taking into account safety, security and privacy.
In addition, novel licenses are required—inspired by those for OSS but carefully tailored to open-source AI 12 . Such licenses must ensure broad user access while enforcing guidelines that prohibit malicious practices (such as abusing LLMs by automatically generating propaganda campaigns) under legally enforceable premises. Furthermore, such licenses for open-source AI should include sub-clauses that define permissive and restrictive use and also how the technology can or cannot be repurposed. Prominent examples are the RAIL licenses , which prevent irresponsible and harmful applications of AI technologies by granting permission only for certain use cases. Over time, customized variants of licenses for open-source AI could be developed, so that high-risk applications of AI technology are more restricted.
Similar to OSS, the development and use of AI technology under open-source principles will be especially effective in addressing bias in AI systems and steering innovations in a fair, ethical and trustworthy direction. First, owing to the diversity of inputs from stakeholders from around the world, there will be a greater emphasis on removing bias. Addressing bias will be as important when curating datasets as when training models. Second, a common concern is that open-source AI may not have the same level of quality control and testing as proprietary solutions, leading to potential bugs accidentally introduced by its developers. To this end, collaboration is important because it naturally leads to extensive testing.
Further, the development of AI in open communities may introduce decentralized organizations (that is, without authority hierarchies based on employment contracts). Many open communities have developed effective organizational structures based on merit, effort and expertise that are effective at resolving both coordination and cooperation issues, including how to manage conflicts. For instance, the Debian community developed a constitution that determines the decision-making rights of contributors and a set of rules that the community can refer to in case of conflicts or accountability issues. Lessons from communities such as Debian could be incorporated into a functional organizational structure and effective governance for open-source AI communities. Likewise, given that designated bodies for maintaining adherence to legal frameworks are typically missing and questions around accountability are often unclear, there can be legal challenges that originate from regulatory compliance. Nevertheless, open-source AI technology brings important principles to the table that go beyond existing regulatory frameworks for responsible and trustworthy use of AI.
It is also worth noting that there are privacy and security threats associated with the use of open-source AI. For example, malicious actors could perform backdoor attacks in which they manipulate a small portion of the training data to make an AI model learn additional, hidden functionalities 13 . In general, vulnerabilities in open-source AI are often public knowledge, which can make attacks but also their identification easier. Furthermore, there are also risks for society when open-source AI is used for nefarious purposes. Examples are the use of open-source AI technologies for the development of weapons and AI-generated propaganda campaigns 14 . Nevertheless, the benefits are likely to outweigh the downsides of open-source AI, especially if a responsible open-source approach with clear barriers against misuse is pursued, as laid out above.
Improving interoperability
Over time, AI technology will need to build upon more standardized and modular building blocks within software libraries (such as prompt templates and standardized prompt optimizers in the case of LLMs) that allow for easier adoption and customization in downstream applications. Interoperability of pre-trained models across platforms should also drastically reduce the need to retrain large models. The result will be a greater reusability of AI technologies, thus reducing the need to ‘reinvent the wheel’ and promoting faster iterations during development. Interoperability is not only important for rapidly building AI applications but also so that high-quality source codes and models designed in a responsible and robust manner can be reused.
In terms of standardization, various regulatory bodies such as the International Organization for Standardization have several standards under draft that aim at the harmonization of AI technology. The current initiatives cover various aspects including life cycle management, data quality, risk management and auditing. Such standardization roadmaps are helpful for developing trustworthy AI systems in high-risk applications (for example, through standardized conformity checks). Crucially, standardization must be brought to life through software libraries for developing AI technology. In this regard, public funding to support the development of open-source libraries could be necessary, as well as corresponding educational resources and long-term maintenance.
As a result of growing harmonization, dependence on a specific AI technology will diminish, so that end-users can avoid ‘lock-in’ effects and benefit from reduced switching costs (for instance, when changing from the LLM of company A to that of company B). For developers, interoperability can eventually help to counteract growing inequality in the development of, access to and use of AI technology, while also promoting effective competition. In this regard, a concern from a corporate perspective may be that, if AI research is forced to be open, then companies may not see value in investing as much in research and development as they would otherwise do. For example, the motivation of companies to develop new AI technologies may be reduced in the presence of open-source alternatives, which may hamper innovation more broadly and could eventually also lead to gatekeeping behavior in established companies. However, we argue that the presence of open-source AI complementary to proprietary alternatives may increase healthy competition, which can also make commercial products better.
A call for open-source AI technology
We have argued that companies and society can benefit enormously from fostering open-source AI technology to complement proprietary alternatives. The broad adoption of open-source principles across datasets, models and source codes will foster accessibility, collaboration, responsibility and interoperability in AI technology and will help to reverse the growing inequality in AI research and thereby lower barriers to future innovation.
Aghion, P., Harris, C., Howitt, P. & Vickers, J. Rev. Econ. Stud. 68 , 467–492 (2001).
Article Google Scholar
Chesbrough, H. W. Open Innovation: the New Imperative for Creating and Profiting from Technology (Harvard Business Press, 2003).
Fitzgerald, B. MIS Q. 30 , 587–598 (2006).
Lerner, J. & Schankerman, M. The Comingled Code: Open Source and Economic Development (MIT Press, 2013).
Haefliger, S., Von Krogh, G. & Spaeth, S. Manage. Sci. 54 , 180–193 (2008).
Von Krogh, G. & Von Hippel, E. Manage. Sci. 52 , 975–983 (2006).
Paulson, J. W., Succi, G. & Eberlein, A. IEEE Trans. Softw. Eng. 30 , 246–256 (2004).
Golden, B. Succeeding with Open-Source (Addison-Wesley Professional, 2005).
Akiki, C. et al. BigScience: a case study in the social construction of a multilingual large language model. In NeurIPS Worksh. on Broadening Research Collaborations in ML (NeurIPS, 2022).
BigScience Workshop (Scao, T. L. et al.) BLOOM: A 176B-parameter open-access multilingual language model. Preprint at https://arxiv.org/abs/2211.05100 (2022).
Jacobides, M. G., Brusoni, S. & Candelon, F. Strat. Sci. 6 , 412–435 (2021).
Contractor, D. et al. Behavioral use licensing for responsible AI. In ACM Conf. on Fairness, Accountability, and Transparency (FAccT) (ACM, 2022).
Saha, A., Subramanya, A. & Pirsiavash, H. Hidden trigger backdoor attacks. In AAAI Conf. on Artificial Intelligence (AAAI, 2020).
Feuerriegel, S. et al. Nat. Human Behav . (in the press).
Download references
Author information
Authors and affiliations.
Faculty of Business and Economics (HEC), University of Lausanne, Lausanne, Switzerland
Yash Raj Shrestha
Department of Management, Technology and Economics, ETH Zurich, Zurich, Switzerland
Georg von Krogh
ETH AI Center, ETH Zurich, Zurich, Switzerland
Institute of AI in Management, LMU Munich, Munich, Germany
Stefan Feuerriegel
Munich Center for Machine Learning, Munich, Germany
You can also search for this author in PubMed Google Scholar
Contributions
All authors wrote, edited and approved the manuscript.
Corresponding author
Correspondence to Stefan Feuerriegel .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Peer review
Peer review information.
Nature Computational Science thanks Giada Pistilli and the other, anonymous reviewer(s) for their contribution to the peer review of this work.
Rights and permissions
Reprints and permissions
About this article
Cite this article.
Shrestha, Y.R., von Krogh, G. & Feuerriegel, S. Building open-source AI. Nat Comput Sci 3 , 908–911 (2023). https://doi.org/10.1038/s43588-023-00540-0
Download citation
Published : 26 October 2023
Issue Date : November 2023
DOI : https://doi.org/10.1038/s43588-023-00540-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
Center for Security and Emerging Technology
Into the jungle: best practices for open-source researchers.
Ryan Fedasiuk
The goal of this guide is to acquaint researchers and analysts with tools, resources, and best practices to ensure security when collecting or accessing open-source information.
Open sources on the internet present numerous potential hazards both to users and the information they access. Navigating these hazards requires habitual vigilance.
There are three main considerations when collecting open-source information online. In order of priority, they are:
- Protecting your devices, network, and files from malware.
- Archiving your sources for posterity.
- Masking your activities from intrusive onlookers.
The Cardinal Rules of Open-Source Investigations
- Always assume the source has been compromised and could present a privacy risk.
- Always stay connected to a VPN.
- Never download files locally.
- Whenever possible, access only the cached or archived versions of web pages.
- Whenever appropriate, archive sources immediately.
- Whenever in doubt, scan before you click.
Resources, Tools, and Best Practices
A virtual private network (VPN) can secure your network by masking your internet protocol (IP) address and encrypting information that is transmitted from your device. Most VPN services will let you select a server through which to route internet traffic. This has the added benefit of camouflaging your IP address. For a faster connection, choose a server located near you. For a slower connection likely to raise fewer eyebrows, choose a connection based near the entity that you are researching. For China, that might be Hong Kong, Taiwan, or Singapore—or, use a service that allows you to tunnel directly beneath the Great Firewall. For Russia, the Baltic states are good options. For North Korea, consider VPN servers based in Seoul.
There are many options and considerations when choosing a VPN: price, number of servers, connection speed, whether the service keeps logs of your browsing activity, and saturation—whether the government whose files you are browsing has blocked many of the service’s possible connection nodes.
2. Cached Web Pages
A safer way to access any web page is to access Google’s cached version of that page, rather than visiting the website directly. A cached page is a past version of the website in question, which Google’s search engine accessed and saved internally while creating search results and previews. Not every web page is cached, but you will find that most web pages have this option.
To access the cached version of a web page, either type cache:[URL] directly into your browser’s navigation bar, or click on the three dots next to a Google search result to see more information about the page:
The bottom-right corner of the ensuing pop-up will include a button that says “Cached.” Click on it to access the cached page.
The cached version of a web page will have a banner at the top that looks like this:
Accessing the cached version of a web page is not foolproof. It is still possible for a website owner to track which IP address is viewing a cached webpage, through certain embedded images and other elements. Accessing the text-only version of a cached page, or the HTML source code, can mitigate some of these risks, and will allow you to more quickly find information on web pages that are slow to load.
Cached web pages are especially useful for previewing documents that you would otherwise have to download directly onto your computer— something that you should avoid if at all possible . For example, take this .xls spreadsheet file hosted by the Cyberspace Affairs Commission of China:
Just clicking on this Google search result would normally result in the file being automatically downloaded to your computer—a disaster. Grappling with auto-download links is a never-ending challenge when collecting open-source information from foreign websites.
A safer (and faster) way of getting at the information is to access the cached version of the web page that is hosting the file. Rather than downloading something and opening it in Excel, Google’s cache transforms it into a web page that you can view in your browser:
This strategy works for all common file types: .doc, .pdf, .xls, and .xlsx, among others, but will sometimes cause errors in file formatting (especially PDFs).
3. Archive Services
Archiving sources is incredibly important. Within days or even hours of publishing research, sources of information frequently disappear, and original website links are frequently broken. But there are several reasons why you might want to archive a website, beyond ensuring future access to the material:
- Archive services can serve a similar function to a cached web page, allowing you to view a safer version of the page. (It is also possible to archive a Google-cached web page, rather than the original source, for layered protection.)
- Some archive services, like the Wayback Machine (discussed below), will tell you if someone else has already archived the page, which can be useful to know.
- Some archive services will generate unique links and display the exact time stamps for when they were generated. This can be helpful in plagiarism disputes and/or tracking project timelines.
In particular, two free archiving services are embraced by the open-source community. These include:
- The Internet Archive (Wayback Machine): https://web.archive.org/save/
- Archive Today: https://archive.vn/
It is often worth archiving particularly valuable documents across more than one archive service.
Please note that most archive services will “ping” the website with a U.S.-based IP address . This can ruin your attempts to remain stealthy, for example, with a China- or Russia-based VPN. Please also note it may be possible for website owners to retroactively break archive links you have already established. For these reasons, web-based digital archive services may not always be the best option.
To maintain maximum privacy, security, and long-term access, it is often worthwhile to save local copies of web pages as PDFs to your computer, then upload them to cloud storage or an external hard drive. This is not the same thing as downloading a PDF from the website itself— which you should avoid if at all possible . Rather, when you are viewing a web page, follow these steps:
- First, attempt to “print” the web page by opening the print interface (press CTRL+P on a PC; CMD+P on a Mac).
- Then, instead of actually printing it out, change the destination to “Save as PDF.”
- Finally, consider duplicating the saved file to external flash drives or uploading it to a secure web cloud like Google Drive.
4. URL and File Scanners
Sometimes, there will be a potentially valuable source of information that resists archiving and has no cached web page. It’s a gamble to directly access these kinds of links. But you can exercise due diligence: Whenever in doubt, scan before you click .
VirusTotal is a free service that scans files and URLs for malware by checking them against dozens of antivirus software services, including well-known consumer brands like AVG, BitDefender, and Kaspersky.
VirusTotal collects information about the files and URLs uploaded to its database. It is a testing platform for antivirus services. It has access to 79+ antivirus services because it provides diagnostic information to improve antivirus products from the scans that users generate. It does not require users to have an account.
5. Browser Sandbox
If you are sitting down for an extended session of information-hunting, it is best to do all of your searching inside a virtual sandbox (or virtual machine, VM). There are several applications that can create a firewall around programs and applications you choose to run, such as web browsers like Google Chrome and Firefox.
A web browser session run inside the sandbox will close when the sandbox is closed. Any files downloaded from the browser will remain inside the sandbox, and can be wiped when the sandbox is closed, without being saved to your actual computer. You can still give permission to transfer individual files out of the sandbox.
There are different sandbox options available for PC or Mac users, but many are free, open-source, and relatively lightweight applications. A popular virtual sandbox application for PC users is Sandboxie . For Mac users, consider Oracle’s VirtualBox .
6. Antivirus Software
If you are conducting open-source research, it behooves you to have a subscription to high-quality antivirus software. However, if you do not already have antivirus on your computer, there are some free options worth downloading and running regularly:
- Malwarebytes offers free, relatively lightweight, on-demand malware scans. It can be run in conjunction with other antivirus software products.
- Bitdefender is often cited as a high-quality, free antivirus software.
- And free trials are offered by paid subscription sources including Norton, McAfee, AVG and Kaspersky.
If at any point you break one of the six cardinal rules outlined in this guide, or accidentally click on an auto-download link, it’s worth running a quick Malwarebytes scan. But remember—the best practice when conducting open-source investigations is to assume compromise. If a state wants to track your browsing and research activity, it will surely be able to do so.
Governments and media publications everywhere are starting to embrace the value of open-source investigations. Even in relatively closed societies, there is an unmined ocean of data capable of informing business and policy decisions. Recent studies have highlighted the utility of budget documents , purchasing orders , geospatial imagery , social media posts , government records , and elite biographies in understanding states’ geopolitical ambitions and military capabilities. Armed with these tips and tricks, where will you venture next?
This website uses cookies.
Privacy overview.
This Week in AI: When ‘open source’ isn’t so open

Keeping up with an industry as fast-moving as AI is a tall order. So until an AI can do it for you, here’s a handy roundup of recent stories in the world of machine learning, along with notable research and experiments we didn’t cover on their own.
This week, Meta released the latest in its Llama series of generative AI models : Llama 3 8B and Llama 3 70B. Capable of analyzing and writing text, the models are “open sourced,” Meta said — intended to be a “foundational piece” of systems that developers design with their unique goals in mind.
“We believe these are the best open source models of their class, period,” Meta wrote in a blog post . “We are embracing the open source ethos of releasing early and often.”
There’s only one problem: the Llama 3 models aren’t really “open source,” at least not in the strictest definition .
Open source implies that developers can use the models how they choose, unfettered. But in the case of Llama 3 — as with Llama 2 — Meta has imposed certain licensing restrictions. For example, Llama models can’t be used to train other models. And app developers with over 700 million monthly users must request a special license from Meta.
Debates over the definition of open source aren’t new. But as companies in the AI space play fast and loose with the term, it’s injecting fuel into long-running philosophical arguments.
Last August, a study co-authored by researchers at Carnegie Mellon, the AI Now Institute and the Signal Foundation found that many AI models branded as “open source” come with big catches — not just Llama. The data required to train the models is kept secret. The compute power needed to run them is beyond the reach of many developers. And the labor to fine-tune them is prohibitively expensive.
So if these models aren’t truly open source, what are they, exactly? That’s a good question; defining open source with respect to AI isn’t an easy task.
One pertinent unresolved question is whether copyright, the foundational IP mechanism open source licensing is based on, can be applied to the various components and pieces of an AI project, in particular a model’s inner scaffolding (e.g. embeddings ). Then, there’s the mismatch between the perception of open source and how AI actually functions to overcome: open source was devised in part to ensure that developers could study and modify code without restrictions. With AI, though, which ingredients you need to do the studying and modifying is open to interpretation.
Wading through all the uncertainty, the Carnegie Mellon study does make clear the harm inherent in tech giants like Meta co-opting the phrase “open source.”
Often, “open source” AI projects like Llama end up kicking off news cycles — free marketing — and providing technical and strategic benefits to the projects’ maintainers. The open source community rarely sees these same benefits, and, when they do, they’re marginal compared to the maintainers’.
Instead of democratizing AI, “open source” AI projects — especially those from big tech companies — tend to entrench and expand centralized power, say the study’s co-authors. That’s good to keep in mind the next time a major “open source” model release comes around.
Here are some other AI stories of note from the past few days:
- Meta updates its chatbot: Coinciding with the Llama 3 debut, Meta upgraded its AI chatbot across Facebook, Messenger, Instagram and WhatsApp — Meta AI — with a Llama 3-powered backend. It also launched new features, including faster image generation and access to web search results.
- AI-generated porn: Ivan writes about how the Oversight Board, Meta’s semi-independent policy council, is turning its attention to how the company’s social platforms are handling explicit, AI-generated images.
- Snap watermarks: Social media service Snap plans to add watermarks to AI-generated images on its platform. A translucent version of the Snap logo with a sparkle emoji, the new watermark will be added to any AI-generated image exported from the app or saved to the camera roll.
- The new Atlas: Hyundai-owned robotics company Boston Dynamics has unveiled its next-generation humanoid Atlas robot, which, in contrast to its hydraulics-powered predecessor, is all-electric — and much friendlier in appearance.
- Humanoids on humanoids: Not to be outdone by Boston Dynamics, the founder of Mobileye, Amnon Shashua, has launched a new startup, Menteebot, focused on building bibedal robotics systems. A demo video shows Menteebot’s prototype walking over to a table and picking up fruit.
- Reddit, translated: In an interview with Amanda, Reddit CPO Pali Bhat revealed that an AI-powered language translation feature to bring the social network to a more global audience is in the works, along with an assistive moderation tool trained on Reddit moderators’ past decisions and actions.
- AI-generated LinkedIn content: LinkedIn has quietly started testing a new way to boost its revenues: a LinkedIn Premium Company Page subscription, which — for fees that appear to be as steep as $99/month — include AI to write content and a suite of tools to grow follower counts.
- A Bellwether: Google parent Alphabet’s moonshot factory, X, this week unveiled Project Bellwether, its latest bid to apply tech to some of the world’s biggest problems. Here, that means using AI tools to identify natural disasters like wildfires and flooding as quickly as possible.
- Protecting kids with AI: Ofcom, the regulator charged with enforcing the U.K.’s Online Safety Act, plans to launch an exploration into how AI and other automated tools can be used to proactively detect and remove illegal content online, specifically to shield children from harmful content.
- OpenAI lands in Japan: OpenAI is expanding to Japan, with the opening of a new Tokyo office and plans for a GPT-4 model optimized specifically for the Japanese language.
More machine learnings

Image Credits: DrAfter123 / Getty Images
Can a chatbot change your mind? Swiss researchers found that not only can they, but if they are pre-armed with some personal information about you, they can actually be more persuasive in a debate than a human with that same info.
“This is Cambridge Analytica on steroids,” said project lead Robert West from EPFL. The researchers suspect the model — GPT-4 in this case — drew from its vast stores of arguments and facts online to present a more compelling and confident case. But the outcome kind of speaks for itself. Don’t underestimate the power of LLMs in matters of persuasion, West warned: “In the context of the upcoming US elections, people are concerned because that’s where this kind of technology is always first battle tested. One thing we know for sure is that people will be using the power of large language models to try to swing the election.”
Why are these models so good at language anyway? That’s one area there is a long history of research into, going back to ELIZA. If you’re curious about one of the people who’s been there for a lot of it (and performed no small amount of it himself), check out this profile on Stanford’s Christopher Manning . He was just awarded the John von Neuman Medal; congrats!
In a provocatively titled interview, another long-term AI researcher (who has graced the TechCrunch stage as well), Stuart Russell, and postdoc Michael Cohen speculate on “How to keep AI from killing us all.” Probably a good thing to figure out sooner rather than later! It’s not a superficial discussion, though — these are smart people talking about how we can actually understand the motivations (if that’s the right word) of AI models and how regulations ought to be built around them.
Stuart Russell on how to make AI ‘human-compatible’
The interview is actually regarding a paper in Science published earlier this month, in which they propose that advanced AIs capable of acting strategically to achieve their goals, which they call “long-term planning agents,” may be impossible to test. Essentially, if a model learns to “understand” the testing it must pass in order to succeed, it may very well learn ways to creatively negate or circumvent that testing. We’ve seen it at a small scale, why not a large one?
Russell proposes restricting the hardware needed to make such agents… but of course, Los Alamos and Sandia National Labs just got their deliveries. LANL just had the ribbon-cutting ceremony for Venado , a new supercomputer intended for AI research, composed of 2,560 Grace Hopper Nvidia chips.

Researchers look into the new neuromorphic computer.
And Sandia just received “an extraordinary brain-based computing system called Hala Point,” with 1.15 billion artificial neurons, built by Intel and believed to be the largest such system in the world. Neuromorphic computing, as it’s called, isn’t intended to replace systems like Venado, but to pursue new methods of computation that are more brain-like than the rather statistics-focused approach we see in modern models.
“With this billion-neuron system, we will have an opportunity to innovate at scale both new AI algorithms that may be more efficient and smarter than existing algorithms, and new brain-like approaches to existing computer algorithms such as optimization and modeling,” said Sandia researcher Brad Aimone. Sounds dandy… just dandy!
Open source groups say more software projects may have been targeted for sabotage
- Medium Text

Get weekly news and analysis on the U.S. elections and how it matters to the world with the newsletter On the Campaign Trail. Sign up here.
Reporting by Raphael Satter; Editing by Josie Kao and Leslie Adler
Our Standards: The Thomson Reuters Trust Principles. New Tab , opens new tab

Thomson Reuters
Reporter covering cybersecurity, surveillance, and disinformation for Reuters. Work has included investigations into state-sponsored espionage, deepfake-driven propaganda, and mercenary hacking.

Technology Chevron

Short sellers pocket record weekly profit from Big Tech selloff
Traders who bet against the "Magnificent 7" group of big U.S. tech stocks booked their biggest-ever weekly profit of more than $10 billion last week, with the biggest gains coming from their short position in shares of Nvidia and Tesla, Ortex data showed.
Data-management software firm Informatica is not currently engaged in any discussions to be acquired, the company said on Monday, after media reports of takeover interest from Salesforce .

Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
What the data says about Americans’ views of climate change

A recent report from the United Nations’ Intergovernmental Panel on Climate Change has underscored the need for international action to avoid increasingly severe climate impacts in the years to come. Steps outlined in the report, and by climate experts, include major reductions in greenhouse gas emissions from sectors such as energy production and transportation.
But how do Americans feel about climate change, and what steps do they think the United States should take to address it? Here are eight charts that illustrate Americans’ views on the issue, based on recent Pew Research Center surveys.
Pew Research Center published this collection of survey findings as part of its ongoing work to understand attitudes about climate change and energy issues. The most recent survey was conducted May 30-June 4, 2023, among 10,329 U.S. adults. Earlier findings have been previously published, and methodological information, including the sample sizes and field dates, can be found by following the links in the text.
Everyone who took part in the June 2023 survey is a member of the Center’s American Trends Panel (ATP), an online survey panel that is recruited through national, random sampling of residential addresses. This way, nearly all U.S. adults have a chance of selection. The survey is weighted to be representative of the U.S. adult population by gender, race, ethnicity, partisan affiliation, education and other categories. Read more about the ATP’s methodology .
Here are the questions used for this analysis , along with responses, and its methodology .
A majority of Americans support prioritizing the development of renewable energy sources. Two-thirds of U.S. adults say the country should prioritize developing renewable energy sources, such as wind and solar, over expanding the production of oil, coal and natural gas, according to a survey conducted in June 2023.
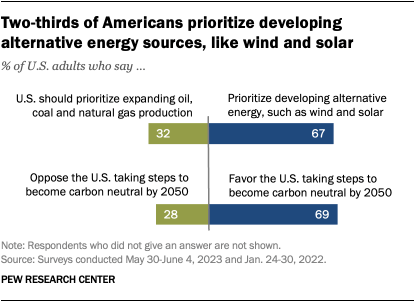
In a previous Center survey conducted in 2022, nearly the same share of Americans (69%) favored the U.S. taking steps to become carbon neutral by 2050 , a goal outlined by President Joe Biden at the outset of his administration. Carbon neutrality means releasing no more carbon dioxide into the atmosphere than is removed.
Nine-in-ten Democrats and Democratic-leaning independents say the U.S. should prioritize developing alternative energy sources to address America’s energy supply. Among Republicans and Republican leaners, 42% support developing alternative energy sources, while 58% say the country should prioritize expanding exploration and production of oil, coal and natural gas.
There are important differences by age within the GOP. Two-thirds of Republicans under age 30 (67%) prioritize the development of alternative energy sources. By contrast, 75% of Republicans ages 65 and older prioritize expanding the production of oil, coal and natural gas.
Americans are reluctant to phase out fossil fuels altogether, but younger adults are more open to it. Overall, about three-in-ten adults (31%) say the U.S. should completely phase out oil, coal and natural gas. More than twice as many (68%) say the country should use a mix of energy sources, including fossil fuels and renewables.
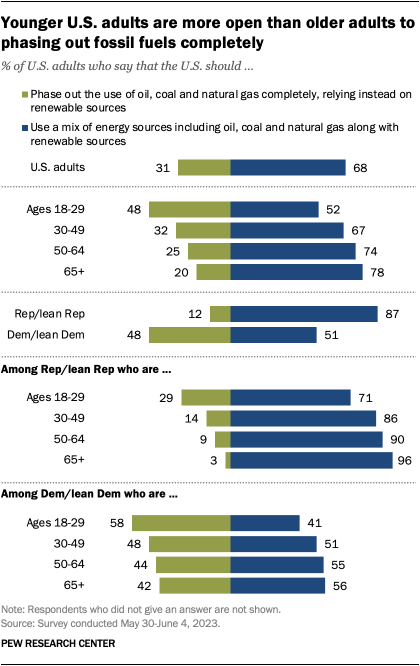
While the public is generally reluctant to phase out fossil fuels altogether, younger adults are more supportive of this idea. Among Americans ages 18 to 29, 48% say the U.S. should exclusively use renewables, compared with 52% who say the U.S. should use a mix of energy sources, including fossil fuels.
There are age differences within both political parties on this question. Among Democrats and Democratic leaners, 58% of those ages 18 to 29 favor phasing out fossil fuels entirely, compared with 42% of Democrats 65 and older. Republicans of all age groups back continuing to use a mix of energy sources, including oil, coal and natural gas. However, about three-in-ten (29%) Republicans ages 18 to 29 say the U.S. should phase out fossil fuels altogether, compared with fewer than one-in-ten Republicans 50 and older.
There are multiple potential routes to carbon neutrality in the U.S. All involve major reductions to carbon emissions in sectors such as energy and transportation by increasing the use of things like wind and solar power and electric vehicles. There are also ways to potentially remove carbon from the atmosphere and store it, such as capturing it directly from the air or using trees and algae to facilitate carbon sequestration.
The public supports the federal government incentivizing wind and solar energy production. In many sectors, including energy and transportation, federal incentives and regulations significantly influence investment and development.
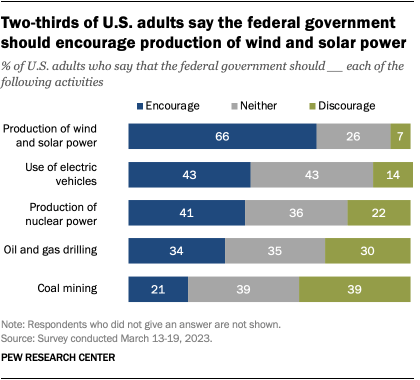
Two-thirds of Americans think the federal government should encourage domestic production of wind and solar power. Just 7% say the government should discourage this, while 26% think it should neither encourage nor discourage it.
Views are more mixed on how the federal government should approach other activities that would reduce carbon emissions. On balance, more Americans think the government should encourage than discourage the use of electric vehicles and nuclear power production, though sizable shares say it should not exert an influence either way.
When it comes to oil and gas drilling, Americans’ views are also closely divided: 34% think the government should encourage drilling, while 30% say it should discourage this and 35% say it should do neither. Coal mining is the one activity included in the survey where public sentiment is negative on balance: More say the federal government should discourage than encourage coal mining (39% vs. 21%), while 39% say it should do neither.
Americans see room for multiple actors – including corporations and the federal government – to do more to address the impacts of climate change. Two-thirds of adults say large businesses and corporations are doing too little to reduce the effects of climate change. Far fewer say they are doing about the right amount (21%) or too much (10%).
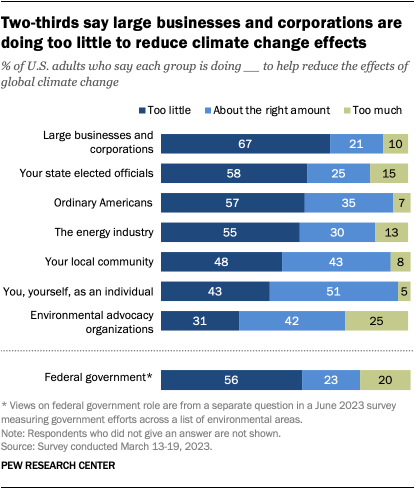
Majorities also say their state elected officials (58%) and the energy industry (55%) are doing too little to address climate change, according to a March 2023 survey.
In a separate Center survey conducted in June 2023, a similar share of Americans (56%) said the federal government should do more to reduce the effects of global climate change.
When it comes to their own efforts, about half of Americans (51%) think they are doing about the right amount as an individual to help reduce the effects of climate change, according to the March 2023 survey. However, about four-in-ten (43%) say they are doing too little.
Democrats and Republicans have grown further apart over the last decade in their assessments of the threat posed by climate change. Overall, a majority of U.S. adults (54%) describe climate change as a major threat to the country’s well-being. This share is down slightly from 2020 but remains higher than in the early 2010s.
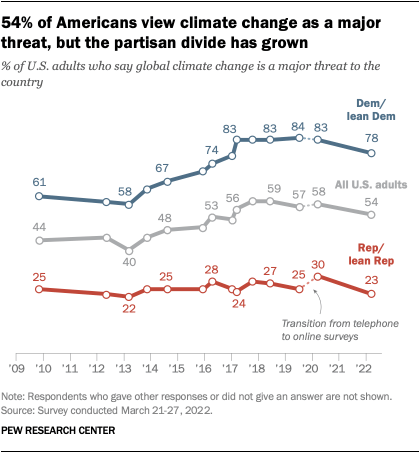
Nearly eight-in-ten Democrats (78%) describe climate change as a major threat to the country’s well-being, up from about six-in-ten (58%) a decade ago. By contrast, about one-in-four Republicans (23%) consider climate change a major threat, a share that’s almost identical to 10 years ago.
Concern over climate change has also risen internationally, as shown by separate Pew Research Center polling across 19 countries in 2022. People in many advanced economies express higher levels of concern than Americans . For instance, 81% of French adults and 73% of Germans describe climate change as a major threat.
Climate change is a lower priority for Americans than other national issues. While a majority of adults view climate change as a major threat, it is a lower priority than issues such as strengthening the economy and reducing health care costs.
Overall, 37% of Americans say addressing climate change should be a top priority for the president and Congress in 2023, and another 34% say it’s an important but lower priority. This ranks climate change 17th out of 21 national issues included in a Center survey from January.
As with views of the threat that climate change poses, there’s a striking contrast between how Republicans and Democrats prioritize the issue. For Democrats, it falls in the top half of priority issues, and 59% call it a top priority. By comparison, among Republicans, it ranks second to last, and just 13% describe it as a top priority.
Our analyses have found that partisan gaps on climate change are often widest on questions – such as this one – that measure the salience or importance of the issue. The gaps are more modest when it comes to some specific climate policies. For example, majorities of Republicans and Democrats alike say they would favor a proposal to provide a tax credit to businesses for developing technologies for carbon capture and storage.
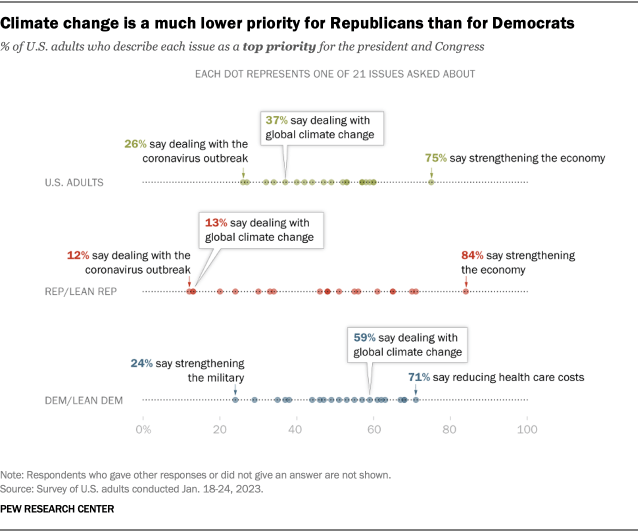
Perceptions of local climate impacts vary by Americans’ political affiliation and whether they believe that climate change is a serious problem. A majority of Americans (61%) say that global climate change is affecting their local community either a great deal or some. About four-in-ten (39%) see little or no impact in their own community.
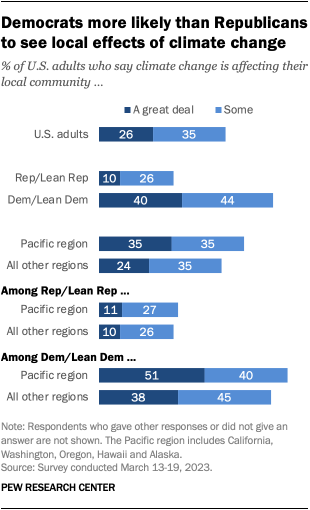
The perception that the effects of climate change are happening close to home is one factor that could drive public concern and calls for action on the issue. But perceptions are tied more strongly to people’s beliefs about climate change – and their partisan affiliation – than to local conditions.
For example, Americans living in the Pacific region – California, Washington, Oregon, Hawaii and Alaska – are more likely than those in other areas of the country to say that climate change is having a great deal of impact locally. But only Democrats in the Pacific region are more likely to say they are seeing effects of climate change where they live. Republicans in this region are no more likely than Republicans in other areas to say that climate change is affecting their local community.
Our previous surveys show that nearly all Democrats believe climate change is at least a somewhat serious problem, and a large majority believe that humans play a role in it. Republicans are much less likely to hold these beliefs, but views within the GOP do vary significantly by age and ideology. Younger Republicans and those who describe their views as moderate or liberal are much more likely than older and more conservative Republicans to describe climate change as at least a somewhat serious problem and to say human activity plays a role.
Democrats are also more likely than Republicans to report experiencing extreme weather events in their area over the past year – such as intense storms and floods, long periods of hot weather or droughts – and to see these events as connected with climate change.
About three-quarters of Americans support U.S. participation in international efforts to reduce the effects of climate change. Americans offer broad support for international engagement on climate change: 74% say they support U.S. participation in international efforts to reduce the effects of climate change.
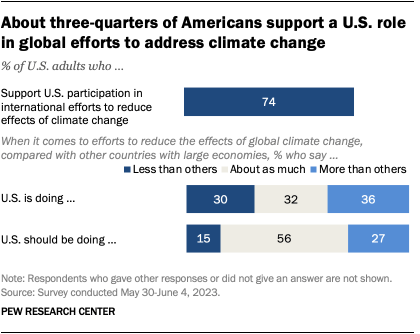
Still, there’s little consensus on how current U.S. efforts stack up against those of other large economies. About one-in-three Americans (36%) think the U.S. is doing more than other large economies to reduce the effects of global climate change, while 30% say the U.S. is doing less than other large economies and 32% think it is doing about as much as others. The U.S. is the second-largest carbon dioxide emitter , contributing about 13.5% of the global total.
When asked what they think the right balance of responsibility is, a majority of Americans (56%) say the U.S. should do about as much as other large economies to reduce the effects of climate change, while 27% think it should do more than others.
A previous Center survey found that while Americans favor international cooperation on climate change in general terms, their support has its limits. In January 2022 , 59% of Americans said that the U.S. does not have a responsibility to provide financial assistance to developing countries to help them build renewable energy sources.
In recent years, the UN conference on climate change has grappled with how wealthier nations should assist developing countries in dealing with climate change. The most recent convening in fall 2022, known as COP27, established a “loss and damage” fund for vulnerable countries impacted by climate change.
Note: This is an update of a post originally published April 22, 2022. Here are the questions used for this analysis , along with responses, and its methodology .
- Climate, Energy & Environment
- Environment & Climate
- Partisanship & Issues
- Political Issues

How Republicans view climate change and energy issues
How americans view future harms from climate change in their community and around the u.s., americans continue to have doubts about climate scientists’ understanding of climate change, growing share of americans favor more nuclear power, why some americans do not see urgency on climate change, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Terms & Conditions
Privacy Policy
Cookie Settings
Reprints, Permissions & Use Policy
Advertisement
Iran’s Attacks Bring Long Shadow War With Israel Into the Open
The volley of drones and missiles was the first time that Tehran directly attacked Israel from its own territory, one expert said.
- Share full article

By Cassandra Vinograd
- Published April 14, 2024 Updated April 18, 2024
Follow live updates on Israeli military strikes in Iran.
For decades, Israel and Iran have fought a shadow war across the Middle East , trading attacks by land, sea, air and in cyberspace. The barrage of drones and missiles Iran launched at Israel on Saturday — though nearly all were shot down or intercepted — represented a watershed in the conflict.
It was the first time that Iran directly attacked Israel from its own territory, according to Ahron Bregman, a political scientist and expert in Middle East security issues at King’s College in London, who called it a “historic event.”
Iran has largely used foreign proxies such as Lebanon’s Hezbollah militia to strike Israeli interests, while targeted assassinations of Iranian military leaders and nuclear scientists have been a key part of Israel’s strategy. Here is a recent history of the conflict:
August 2019: An Israeli airstrike killed two Iranian-trained militants in Syria, a drone set off a blast near a Hezbollah office in Lebanon and an airstrike in Qaim, Iraq, killed a commander of an Iran-backed Iraqi militia. Israel accused Iran at the time of trying to establish an overland arms-supply line through Iraq and northern Syria to Lebanon, and analysts said the strikes were aimed at stopping Iran and signaling to its proxies that Israel would not tolerate a fleet of smart missiles on its borders.
January 2020: Israel greeted with satisfaction the assassination of Maj. Gen. Qassim Suleimani , the commander of the foreign-facing arm of Iran’s Islamic Revolutionary Guards Corps, in an American drone strike in Baghdad.
Iran hit back by attacking two bases in Iraq that housed American troops with a barrage of missiles, wounding about 100 U.S. military personnel .
2021-22: In July 2021, an oil tanker managed by an Israeli-owned shipping company was attacked off the coast of Oman, killing two crew members, according to the company and three Israeli officials. Two of the officials said that the attack appeared to have been carried out by Iranian drones.
Iran did not explicitly claim or deny responsibility, but a state-owned television channel described the episode as a response to an Israeli strike in Syria.
In November 2021, Israel killed Iran’s top nuclear scientist, Mohsen Fakhrizadeh , and followed up with the assassination of a Revolutionary Guards commander, Col. Sayad Khodayee , in May 2022.
December 2023: After Israel’s bombardment of Gaza began in response to the Oct. 7 Hamas-led assault, Iranian-backed militias stepped up their own attacks . And late last year, Iran accused Israel of killing a high-level military figure, Brig. Gen. Sayyed Razi Mousavi , in a missile strike in Syria.
A senior adviser to the Revolutionary Guards, General Mousavi was described as having been a close associate of General Suleimani and was said to have helped oversee the shipment of arms to Hezbollah. Israel, adopting its customary stance, declined to comment directly on whether it was behind General Mousavi’s death.
January 2024: An explosion in a suburb of Beirut, Lebanon, killed Saleh al-Arouri , a Hamas leader, along with two commanders from that group’s armed wing, the first assassination of a top Hamas official outside the West Bank and Gaza in recent years. Officials from Hamas, Lebanon and the United States ascribed the blast to Israel , which did not publicly confirm involvement.
Hezbollah, which receives major support from Iran, stepped up its assaults on Israel after Mr. al-Arouri’s death. Israel’s military hit back at Hezbollah in Lebanon, killing several of the group’s commanders .
March and April: An Israeli drone strike hit a car in southern Lebanon, killing at least one person. Israel’s military said it had killed the deputy commander of Hezbollah’s rocket and missile unit. Hezbollah acknowledged the death of a man, Ali Abdulhassan Naim, but did not provide further details.
The same day, airstrikes killed soldiers near Aleppo, northern Syria, in what appeared to be one of the heaviest Israeli attacks in the country in years. The strikes killed 36 Syrian soldiers, seven Hezbollah fighters and a Syrian from a pro-Iran militia, according to the Syrian Observatory for Human Rights, a British-based group that tracks Syria’s civil war.
Israel’s military did not claim responsibility. But the country’s defense minister, Yoav Gallant, wrote on social media, “We will pursue Hezbollah every place it operates and we will expand the pressure and the pace of the attacks.”
Three days later, strikes on an Iranian Embassy building in Damascus killed three top Iranian commanders and four officers, an attack Iran blamed on Israel.
Matthew Mpoke Bigg contributed reporting.

IMAGES
VIDEO
COMMENTS
About the directory. DOAJ is a unique and extensive index of diverse open access journals from around the world, driven by a growing community, and is committed to ensuring quality content is freely available online for everyone. DOAJ is committed to keeping its services free of charge, including being indexed, and its data freely available.
Journals. Explore our growing collection of Open Access journals. Early Journal Content, articles published prior to the last 95 years in the United States, or prior to the last 143 years if initially published internationally, are freely available to all. Even more content is available when you register to read - millions of articles from nearly 2,000 journals
Open Source Literature Review Search Tools: A list of search tools help you find open source articles. No cost academic search engines for published papers and preprints. ... CORE's mission is to aggregate all open access research outputs from repositories and journals worldwide and make them available to the public. In this way CORE ...
arXiv is a free distribution service and an open-access archive for nearly 2.4 million scholarly articles in the fields of physics, mathematics, computer science, quantitative biology, quantitative finance, statistics, electrical engineering and systems science, and economics. Materials on this site are not peer-reviewed by arXiv.
Make an impact and build your research profile in the open with ScienceOpen. Search and discover relevant research in over 93 million Open Access articles and article records; Share your expertise and get credit by publicly reviewing any article; Publish your poster or preprint and track usage and impact with article- and author-level metrics; Create a topical Collection to advance your ...
Reddit also hosts open source research communities, including r/Bellingcat, a community-run subreddit. r/OSINT boasts over 26,000 members, making it an active hub of questions and answers on all things related to the field.. The r/TraceAnObject subreddit is dedicated to bringing together people who want to help EUROPOL with its #TraceAnObject campaign and the FBI's Endangered Child Alert ...
Opening Science. PLOS is a nonprofit, Open Access publisher empowering researchers to accelerate progress in science and medicine by leading a transformation in research communication. Every country. Every career stage. Every area of science. Hundreds of thousands of researchers choose PLOS to share and discuss their work.
Open access (OA) refers to the free, immediate, online availability of research outputs such as journal articles or books, combined with the rights to use these outputs fully in the digital environment. OA content is open to all, with no access fees. Open research goes beyond the boundaries of publications to consider all research outputs ...
It is a challenging task for any research field to screen the literature and determine what needs to be included in a systematic review in a transparent way. A new open source machine learning ...
IEEE Access, a Multidisciplinary, Open Access Journal. IEEE Access is a multidisciplinary, online-only, gold fully open access journal, continuously presenting the results of original research or development across all IEEE fields of interest. Supported by article processing charges (APCs), its hallmarks are rapid peer review, a submission-to ...
Open Source and nonprofit. Unpaywall is run by OurResearch, a nonprofit dedicated to making scholarship more accessible to everyone. Open is our passion. ... Research. Products & integrations Unsub Chrome/Firefox extension Database snapshot Data Feed REST API Simple Query Tool Library link resolver integration Search articles.
Open Access is the free, immediate, online availability of research articles coupled with the rights to use these articles fully in the digital environment. Open Access ensures that anyone can access and use these results—to turn ideas into industries and breakthroughs into better lives. Research provides the foundation of modern society.
Open access publisher of peer-reviewed scientific articles across the entire spectrum of academia. Research network for academics to stay up-to-date with the latest scientific publications, events, blogs and news.
British Heart Foundation. Wellcome. Medical Research Council. UK Prevention Research Partnership. Wellcome Open Research | Published 18 Apr 2024. 1-20 of 13,645 ARTICLES. Browse all open access articles and accelerate the impact of your research.
Harness the power of visual materials—explore more than 3 million images now on JSTOR. Enhance your scholarly research with underground newspapers, magazines, and journals. Explore collections in the arts, sciences, and literature from the world's leading museums, archives, and scholars. JSTOR is a digital library of academic journals ...
Such open-source activity has been "exploding", says computer scientist Stella Biderman, head of research at EleutherAI, an AI research institute in New York City.
A 2020 study of more than 500,000 published research articles found articles that link to data in a public repository were likely to have a 25% higher citation rate on average than articles where data is ... The PLOS Open Science Toolbox is your source for sci-comm tips and best-practice. Learn practical strategies and hands-on tips to improve ...
The Journal of Open Source Software ( JOSS) was founded in May 2016 to offer a solution within the existing publishing mechanisms of science. It is a developer-friendly, free and open-access, peer-reviewed journal for research software packages. By its first anniversary, JOSS had published more than a hundred articles.
Open-source research used to take place at both ends of the resource spectrum. At one end, state actors and corporate due-diligence departments vetting new employees or compiling risk assessments for investors; at the other, social media hobbyists with lots of time and patience scouring images and videos to fact-check claims made by parties in various armed conflicts.
Aggregation plays an increasingly essential role in maximising the long-term benefits of open access, helping to turn the promise of a 'research commons' into a reality. The aggregation services that CORE provides therefore make a very valuable contribution to the evolving open access environment in the UK. Show all.
Creating synergies and networks between universities, research centers, government and industry may establish new ecosystems around open-source AI and become a driver for future innovation.
The Open Research Library (ORL) is planned to include all Open Access book content worldwide on one platform for user-friendly discovery, offering a seamless experience navigating more than 20,000 Open Access books.
Open sources on the internet present numerous potential hazards both to users and the information they access. Navigating these hazards requires habitual vigilance. There are three main considerations when collecting open-source information online. In order of priority, they are: Protecting your devices, network, and files from malware.
"However, we believe there is room and need for multiple perspectives. … No single approach nor single entity could address the most pressing challenges facing research." Elsevier, which runs Scopus, says it has long backed open initiatives and welcomes "any projects that support research as we share the same goal."
Open source implies that developers can use the models how they choose, unfettered. But in the case of Llama 3 — as with Llama 2 — Meta has imposed certain licensing restrictions.
The recent attempt by an unknown actor to sabotage a widely used software program may have been one of several attempts to subvert key pieces of digital infrastructure across the internet, two ...
Americans are reluctant to phase out fossil fuels altogether, but younger adults are more open to it. Overall, about three-in-ten adults (31%) say the U.S. should completely phase out oil, coal and natural gas. More than twice as many (68%) say the country should use a mix of energy sources, including fossil fuels and renewables.
Iran's Attacks Bring Long Shadow War With Israel Into the Open. The volley of drones and missiles was the first time that Tehran directly attacked Israel from its own territory, one expert said.