
Nov 16, 2014
4.01k likes | 9.49k Views
HONEYPOT. MAIN POINTS TO BE DISCUSSED INTRODUCTION OVERVIEW OF HONEYPOT CONCEPTS OF HONEYPOT PLACEMENT OF HONEYPOT HONEYNET DANGERS CONCLUSION BIBLIOGRAPHY. Honeypot Introduction. Countermeasure to detect or prevent attacks Know attack strategies

Share Presentation
- mail server
- virtual honeypot
- low involvement honeypot
- separate operating system environment

Presentation Transcript
MAIN POINTS TO BE DISCUSSED • INTRODUCTION • OVERVIEW OF HONEYPOT • CONCEPTS OF HONEYPOT • PLACEMENT OF HONEYPOT • HONEYNET • DANGERS • CONCLUSION • BIBLIOGRAPHY
Honeypot Introduction • Countermeasure to detect or prevent attacks • Know attack strategies • Gather information which is then used to better identify, understand and protect against threats. • Divert hackers from productive systems 3/26
Definition • A Honeypot is a security resource whose value is in being probed, attacked or compromise. • Two categories of Honeypots • Production Honeypot • Research Honeypots 4/26
Honeypot Concepts • Level of Honeypot • Low-Involvement Honeypot • Mid-Involvement Honeypot • High-Involvement Honeypot • Involvement defines the level of activity a honeypot allows an attacker 5/26
Low-Involvement Honeypot 6/26
Low-Involvement Honeypot • Provides certain fake services • No real operating system • Easily detectable by attackers • Reduce risk • Generate logs and alerts 7/26
Mid-Involvement Honeypot 8/26
Mid-Involvement Honeypot • Provides more to interact • complexity of the honeypot increases • Fake daemons are more sophisticated • No security boundaries and logging mechanisms 9/26
High-Involvement Honeypot 10/26
High-Involvement Honeypot • Has a real underlying Operating System • Attacker has rights on the system • He is in Jail,a Sandbox • Time-consuming to build/maintain • All actions can be recorded and analyzed 11/26
Advantages • Small data sets of high value • New tools and tactics • Minimal resources • Encryption or IPv6 • Simplicity • Disadvantages • Limited view • Risk 12/26
Placement of Honeypot • Honeypot location • Honeynets 13/26
Locations • In front of the firewall(Internet) • DMZ(demilitarized zone) • DMZ is to add an additional layer of security to an organization's local area network (LAN). • Behind the firewall 14/26
Placement of Honeypot 15/26
Honeypot topologies • Simple Honeypot • Honeynet • Virtual Honeynet 16/26
Honeynets 17/26
Honeynet • What is ? • Value of honeynet • How it work ? 18/26
What Is Honeynet ? • Honeynet: A network of honeypots. • Types of Honeynet: • High-interaction honeynet: • A distributed network composing many honeypots. • Low-interaction honeynet: • Emulate a virtual network in one physical machine • Example: honeyd 19/26
Value of Honeynet • Defends Organization and React • Provide an Organization Info. on their own Risk • Test your abilities • Determine System Compromised within Production Network • Risks and Vulnerabilities discovered • Specially for research 20/26
How It Works? • Create a Network • To Be Compromised • Connection from Out side is type of Attack • Requirements • Data Control • Data Capture • Data Collection 21/26
Virtual Honeypot • virtual honeypot uses application software to create a new, separate operating system environment. • The virtual host actually uses or shares that same hardware as the physical OS does. • Instead of using different hardware for each host, many different virtual servers may be contained on one piece of hardware.
Dangers • Unnoticed takeover of the honeypot by an attacker • Lost control over the honeypot installation • Damage done to third parties 22/26
Useful • Honeypot is primarily a research tool, but also has a real commercial applications. The honey pot set in the company's Web or mail server IP address on the adjacent, you can understand that it suffered the attack. • reduce the data to be analyzed. For the usual website or mail server, attack traffic is usually overwhelmed by legitimate traffic. Thus, browsing data to identify the actual behavior of the attacker also much easier.
Conclusion • A Valuable Resource • To be Compromised • Gains Info. About Attackers and their Strategies • Need for Tight Supervision 23/26
Bibliography Reto Baumann, ChristianPlattner “White Paper Honeypots” 2002 “Know Your Enemy: Honeynets“, “http//project.honynet.org” 2003 “Honey pots - Definitions and Value of Honey pots” http//www.tracking-hackers.com 2003 24/26
QUESTIONS? 25/26
THANK YOU 26/26
- More by User

CLEMSON UNIVERSITY. HONEYPOT. By SIDDARTHA ELETI. I ntroduction. Introduced in 1990/1991 by Clifford Stoll’ s in his book “The Cuckoo’s Egg” and by Bill Cheswick’s in his paper “ An Evening With Berferd .”
942 views • 19 slides

Setting Up And Running A Honeypot - Nepenthes
Setting Up And Running A Honeypot - Nepenthes . Brian Allen (ballen at wustl.edu) Network Security Analyst Washington University in St. Louis. Nepenthes. Q: What is a Honeypot ?. A: Generally a computer that appears to be legitimate, but in reality is a trap for malware and hackers
602 views • 23 slides

HONEYPOT whit virtual machine
HONEYPOT whit virtual machine. Elham Hormozi Mazandaran University Science & Technology [email protected]. Overview. Definition Advantages & Disadvantages Types Level of interaction Honeyd project : A Virtual honeypot framework Honeynet project: An Actual honeypot framework.
500 views • 25 slides

Honeypot An instrument for attracting and detecting attackers
Honeypot An instrument for attracting and detecting attackers. April 2002, R. Baumann [email protected] http://security.rbaumann.net. Agenda. Theory Implementation Administrations Toolkit Attacks Conclusion. Theory Honeypot. Term originally from the military Fake target or ambush
556 views • 22 slides

Honeypot. 서울과학기술대학교 Jeilyn Molina 121336101. Definition. Honeypot is the software or set of computers that are intended to attract attackers, pretending to be weak or vulnerable systems to attack. It is a security tool used to collect information on the attackers and their techniques.
961 views • 24 slides

GENERAL PRESENTATION . HONEYPOT. OUTLINE. INTRODUCATION DETAIL OF HONEY POT WHAT A HONEY POT IS BRIEF HISTORY OF HONEYPOT TYPE OF HONEYPOT PRODUCATION HONEYPOT RESEARCH HONEYPOT ADVANTAGES DISADVANTAGES. INTRODUCATION.
694 views • 11 slides

Honeypot Data Analysis Final presentation
Honeypot Data Analysis Final presentation. By: Michael Kuritzky and Guy Cepelevich Supervisor: Amichai Shulman. What is a Honeypot ?.
281 views • 17 slides

Honeypot, Botnet, Security Measurement, Email Spam
Honeypot, Botnet, Security Measurement, Email Spam. Cliff C. Zou CDA6938 02/01/07. What Is a Honeypot?. “A honeypot is a faked vulnerable system used for the purpose of being attacked, probed, exploited and compromised.”. Example of a Simple Honeypot.
395 views • 19 slides

A Virtual Honeypot Framework
A Virtual Honeypot Framework. Niels Provos Google, Inc. The 13th USENIX Security Symposium, August 9–13, 2004 San Diego, CA Presented by: Sean Mondesire. Honeyd’s Contributions. Provides an alternative technique for detecting attacks Extremely low-cost option for honeypots
499 views • 21 slides

Honeyd Virtual Honeypot Frame Work
Honeyd Virtual Honeypot Frame Work. CS591 Research Project. Niels Provos. Supervised by: Dr. Chow. Presented by: Fadi Mohsen. Presented by: Fadi Mohsen. Intrusion Detection System.
421 views • 18 slides

Honeycomb and the current state of Honeypot Technology
Honeycomb and the current state of Honeypot Technology. Christian Kreibich. Coming up. Introduction to Honeypots Current state of the art: Honeynets Honeycomb - automated NIDS signature creation Three days in the life of an unprotected cable modem connection. So what’s a Honeypot?.
644 views • 31 slides

The Honeypot Project
The Honeypot Project. By Itzik Jislin Yiftach Benjamini Supervisor: Ben Bershtein. Introduction. What is a Honeypot?. "A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource." - Lance Spitzner. Honeypot Overview.
832 views • 43 slides

Introduction to Honeypot, Denial-of-Service, and Rootkit
Introduction to Honeypot, Denial-of-Service, and Rootkit. Cliff C. Zou CAP6135 Spring, 2011. Acknowledgement. Some contents on honeypot are from http://staff.washington.edu/dittrich/talks/aro-honeynets.ppt Some figures on DDoS are from
544 views • 37 slides

Workshop – Intro to Honeypot Palembang, 20 Juni 2014
Workshop – Intro to Honeypot Palembang, 20 Juni 2014. Charles Lim [email protected] Mario Marcello [email protected]. Agenda. Introduction to Honeypot Why Honeypot Honeypot – Dionaea Installation Configuration Detecting OS Submitting Samples Visualizing the Attack. Honeypot.
689 views • 51 slides

Honeynet/Honeypot Project
Honeynet/Honeypot Project. Leslie Cherian Todd Deshane Patty Jablonski Creighton Long. May 2, 2006. Overview. Honeynet/Honeypot Background Setting Up Our Own Honeypot VM VMware Snort Tripwire Filemon, Regmon Ethereal Demo – Port Scan, Install Spyware. Honeypots.
483 views • 27 slides

.nz honeypot project
Keith Davidson. .nz honeypot project. Drive-by-Downloads. Attacks launched by servers that target vulnerable clients Web based client-side attacks (web server attacking web browser) Visiting a page is sufficient for exploit to be delivered
265 views • 12 slides

Xebek A next generation honeypot monitoring system
Xebek A next generation honeypot monitoring system. EuSecWest/Core06 – London Feb 20-21, 2006. Nguyen Anh Quynh Takefuji-lab Keio university, Japan. Who am I ?. Nguyen Anh Quynh, from Vietnam Currently a PhD candidate of Keio university, Japan
724 views • 61 slides
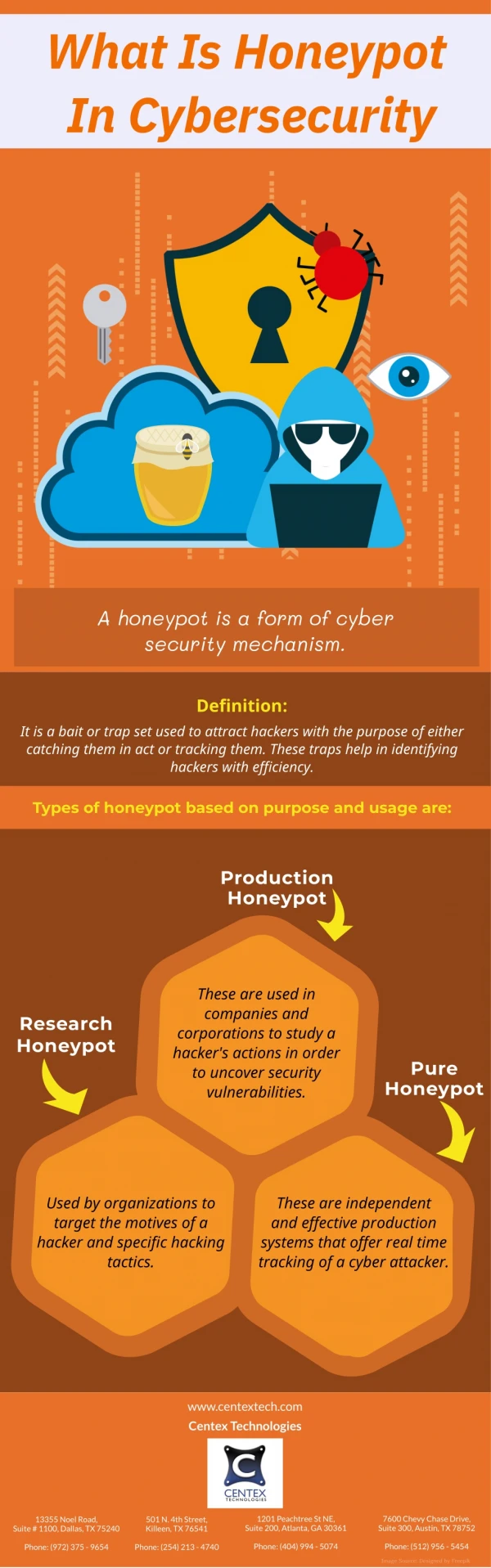
What Is Honeypot In Cybersecurity
140 views • 1 slides

Introduction to Honeypot, Botnet, and Security Measurement
Introduction to Honeypot, Botnet, and Security Measurement. Cliff C. Zou 02/07/06. What Is a Honeypot?. Abstract definition: “A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource.” (Lance Spitzner) Concrete definition:
211 views • 17 slides

433 views • 27 slides
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

A Review on Honeypot Deployment

2020, London Journal Press
A honeypot is a source which is proposed to be attacked and cooperated to gain more information about the attacker and its used tools. It can also be installed to draw and divert an attacker from their existent targets. The honeypots are planned and placed in a cloud network to gather the strange presence as well as known occurrences happened in cloud computing. Honeypots are a computer software tool designed to help, learn the purpose and methods of the hacker community. Honeypot describes in-depth the concepts of their involvement in the field of security. The present review paper proposes and designs the importance of honeypot deployment technique in the protection of data based on the in-frastructures of honeypot, its advantages and disadvantages. The authors also try to offer possible solutions for issues that are generated while using honeypot.

Related Papers
International Journal of Engineering Research and Technology (IJERT)
IJERT Journal
https://www.ijert.org/research-on-various-next-generation-honeypot-systems https://www.ijert.org/research/research-on-various-next-generation-honeypot-systems-IJERTV1IS10490.pdf The increasing use of next generation cloud computing in Internet for providing the different services leads us to the security problems. There are many security problems like DoS (Denial of service) attack, hacking intrusions viruses and worms and many more. Since all the resources are connected with each other and monitored centrally by controller in a cloud environment make an easiest way for hackers. If any of a resource is hacked, it may also expose other resources in the cloud. They cannot be eliminated but they can be reduced by using a tracing system Honeypot. Honeypot is used to collect information about hackers. It tries to gain knowledge about attacker's patterns, purposes and motivation for attack. In this paper we will discuss the basic idea of honeypot, different Honeypot systems, and finally the comparison of today's honeypots available.
International Journal for Research in Applied Science & Engineering Technology (IJRASET)
IJRASET Publication
The rapid increase in the number of users, there is a rise in issues related to hardware failure, web hosting, space and memory allocation of data, which is directly or indirectly leading to the loss of data. With the objective of providing services that are reliable, fast and low in cost, we turn to cloud-computing practices. With a tremendous development in this technology, there is ever increasing chance of its security being compromised by malicious users. A way to divert malicious traffic away from systems is by using Honeypot. It is a colossal strategy that has shown signs of improvement in security of systems. Keeping in mind the various legal issues one may face while deploying Honeypot on third-party cloud vendor servers, the concept of Honeypot is implemented in a file-sharing application which is deployed on cloud server. This paper discusses the detection attacks in a cloud-based environment as well as the use of Honeypot for its security, thereby proposing a new technique to do the same.
Renu Meghani
International Journal of Data and Network Science
Wael alzoubi
For the development of technologies and networks that have been evolving and expanding day by day. In this generation, these facilities allow users to interact more efficiently. Safety is therefore very important to consider preserving the network and database and the need to detect a potential attack before an attack occurs. Network security has become the main issue, particularly in the industries, and there are many techniques to be used to protect network systems. One of them is called Honeypot, a software that is used to detect unauthorized misuse of information systems and to evaluate the actions and behavior of the attacker. Honeypot is, in other words, a trap for any attackers to log in to the network. If the behavior of these attackers is detected, the information will be used to improve network security. Using Honeypot does not cause attackers to notice they are being detected. This research is primarily focused on Honeypot, which is a ground-breaking new technology that h...
Ijaems Journal
—This paper discusses about the honeypot, which serves as advanced security tool minimizing the risks from attack on IT and networks. The methods deployed to show the working of honeypots are discussed in this paper along with advantage and disadvantages of honeypot.
IJNRD Journal
PRASHANT KHANPARA
This article presents Honeypot, a novel network security mechanism. The basics of honeypots, their use in modern computer networks, including their employment in educational settings are all covered in this study. The different types of honeypots are described, like the Production honeypot, Research honeypot. The benefits and drawbacks of honeypots are further examined. Future research in the field of honeypots, including possible improvements to the framework, is considered.
yokesh yoki
In this paper we review the recent advances in honeypot. Some notable proposals and there analysis have been discussed. The aspects of using honeypot in education and in hybrid environment with IDS have been explained. In this paper we also defines the use of signature technique in honeypot for traffic analysis. In the end we summarizes all these aspects.
olaniyi Ayeni
In this paper, a new framework is proposed for the design and implementation of decoy honeypot. In this research work, emphasis is laid on ways to improve network security by deploying honeypot technology. The design and configuration of a honeypot was implemented using a virtual machine(VM) ware workstation to detect attack or malicious traffic on a network. VM ware enables the creation, configuration, distribution, support and manages virtual machine similar to the one used on real computer system. Intrusion detection system (IDS), Entropy based detection scheme and Virtual machine (VM) ware work station were used to capture and analyse traffic over the network. The result shows that the deployment of an honeypot successfully fools an attacker to believe he is attacking a real system. Also, it shows that Honeypot can be deployed on a network to help in enhancing system security.
subanitha sevvel
The primary focus of this paper is to demonstrate about the exciting new technology " HONEYPOTS ". In this era of technology, the hectic usage of internet plays a major role in all activities ranging from education to money transactions. In order to undergo all these tasks in a healthy manner we must ensure security in the network we use. Honeypots are the developing technology to secure our networks. Honeypots are typically virtual machines, designed to emulate real machines, feigning or creating the appearance of running full services and applications, with open ports that might be found on a typical system or server on a network. Honeypots allows the system administrators to " trace back " the source of hackers. The main goal of this paper is to give an elaborate explanation of honeypots, and how they can be deployed to enhance organizational and enterprise security across critical systems and networks. Honeypots can do everything from detecting new attacks to tracking automated credit card fraud and identity theft. In the past several years we have seen the technology rapidly develop, with new concepts such as honeypot farms, commercial and open source solutions, and documented findings released. Honeypots have different forms which may range from a Windows program that emulates common services, such as the Windows honeypot KFSensor3, to entire networks of real computers to be attacked, such as Honeynet. Some commercial honeypots available are Back Officer Friendly (BOF) by NFR, Tripwire by tripwire, Spector, Mantrap etc. Thus, this new technology of network securing technology increases network security and helps in detecting the hackers.
Proceedings of the International Conference on Security and Cryptography
Patrice Clemente
RELATED PAPERS
Biophysical Journal
Katsuhisa Tawada
América sin Nombre
Maria Gabriella Dionisi
Research, Society and Development
Ninalva De Andrade Santos
Mechanisms of Ageing and Development
Sarah Catchlove
Asad Masood
Temas em Psicologia
Nara Rejane Cruz Oliveira
ChemMedChem
Jason Smith
Destriana Saraswati
Revista de Sociologia e Política
Gabriela Pontoni
Diego Gonzalo García Soria
Clinical Science
Scientia Plena
Rosenilde Paniago
Molecular and Cellular Endocrinology
Maria Pennuto
Geofísica Internacional
Luis Alberto Escobar de la cruz
Indian Journal of Dermatology, Venereology, and Leprology
laxmikanta mishra
Geografia Ensino & Pesquisa
Antonio Tavares
Frontiers in Aging
A Kashif Anwar
Eizan Azira
Darko Grbesa
Presidential Studies Quarterly
Robert Himmelberg
Circuits and Systems
Dr. RS Tomar
Astina Joice
Oloo Daniel
European Archives of Psychiatry and Clinical Neuroscience
Wolfgang Sommer
Polish journal of pathology : official journal of the Polish Society of Pathologists
Dorota Jesionek-Kupnicka
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Honeypots for Cybercrime Research
- First Online: 30 July 2021
Cite this chapter

- Robert C. Perkins 3 &
- C. Jordan Howell 3 , 4
1413 Accesses
5 Citations
Honeypots are a type of cybersecurity tool designed with the general purpose of being attacked and compromised by cyberthreats. They became widely popularized throughout the 1990s by computer scientists due to their multi-functional capabilities. As a result, a wide variety of honeypots have been introduced to handle different cybersecurity tasks. Only recently have social scientists begun using them in cybercrime research to test criminological theories and shed light on deviant human behavior in cyberspace. However, arguments have been made for, and against, the utilization of honeypots in this line of research. In this chapter, what constitutes honeypot research in the context of both computer and social science is described. Finally, the chapter concludes itself with advice and suggestions for scholars interested in using honeypots in their own research endeavors.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Akers, R. L. (2011). Social learning and social structure: A general theory of crime and deviance . Transaction Publishers.
Google Scholar
Alata, É., Alberdi, I., Nicomette, V., Owezarski, P., & Kaâniche, M. (2008). Internet attacks monitoring with dynamic connection redirection mechanisms. Journal in Computer Virology, 4 (2), 127–136.
Article Google Scholar
Alata, E., Nicomette, V., Kaâniche, M., Dacier, M., & Herrb, M. (2006). Lessons learned from the deployment of a high-interaction honeypot. In 2006 Sixth European Dependable Computing Conference (pp. 39–46). IEEE.
Alberdi, I., Philippe, É., Vincent, O., & Kaâniche, N. M. (2007). Shark: Spy honeypot with advanced redirection kit. In Proceedings of the IEEE Workshop on Monitoring, Attack detEction and Mitigation (pp. 47–52).
Anagnostakis, K. G., Sidiroglou, S., Akritidis, P., Xinidis, K., Markatos, E., & Keromytis, A. D. (2005). Detecting targeted attacks using shadow honeypots .
Baecher, P., Holz, T., Kötter, M., & Wicherski, G (2016). The Malware Collection Tool (mwcollect) . Available at: http://www.mwcollect.org/ .
Bailey, M., Cooke, E., Watson, D., Jahanian, F., & Provos, N. (2004). A hybrid honeypot architecture for scalable network monitoring . Univ. Michigan, Ann Arbor, MI, USA, Tech. Rep. CSE-TR-499–04.
Bossler, A. M. (2017). Need for debate on the implications of honeypot data for restrictive deterrence policies in cyberspace. Criminology and Public Policy, 16, 679.
Bringer, M. L., Chelmecki, C. A., & Fujinoki, H. (2012). A survey: Recent advances and future trends in honeypot research. International Journal of Computer Network and Information Security, 4 (10), 63.
Buller, D. B., & Burgoon, J. K. (1996). Interpersonal deception theory. Communication Theory, 6 (3), 203–242.
Cheswick, B. (1992). An evening with Berferd in which a cracker is lured, endured, and studied. In Proceedings of Winter USENIX Conference (pp. 20–24). San Francisco.
Clarke, R. V. (1980). Situational crime prevention: Theory and practice. British Journal of Criminology, 20, 136.
Cohen, F. (1998). The RISKS Digest (Vol. 19, Issue 62). Available at: http://catless.ncl.ac.uk/Risks/19.62 .
Cohen, L. E., & Felson, M. (1979). Social change and crime rate trends: A routine activity approach. American sociological review , 588–608.
Cui, W., Paxson, V., & Weaver, N. (2006). GQ: Realizing a system to catch worms in a quarter million places . Technical Report TR-06–004, ICSI.
Deutsche Telekom. (2021). Available at: https://www.telekom.com/en .
Do Carmo, R., Nassar, M., & Festor, O. (2011). Artemisa: An open-source honeypot back-end to support security in VoIP domains. In 12th IFIP/IEEE International Symposium on Integrated Network Management (IM 2011) and Workshops (pp. 361–368). IEEE.
Even, L. R. (2000). Honey pot systems explained . Available at: https://www.sans.org/security-resources/idfaq/honeypot3.php .
Fan, W., Du, Z., Fernández, D., & Villagrá, V. A. (2017). Enabling an anatomic view to investigate honeypot systems: A survey. IEEE Systems Journal, 12 (4), 3906–3919.
Gibbs, J. P. (1975). Crime, punishment, and deterrence . Elsevier.
Grégio, A., Santos, R., & Montes, A. (2007). Evaluation of data mining techniques for suspicious network activity classification using honeypots data. In Data Mining, Intrusion Detection, Information Assurance, and Data Networks Security 2007 (Vol. 6570, p. 657006). International Society for Optics and Photonics.
Heartfield, R., Loukas, G., Budimir, S., Bezemskij, A., Fontaine, J. R., Filippoupolitis, A., & Roesch, E. (2018). A taxonomy of cyber-physical threats and impact in the smart home. Computers and Security, 78, 398–428.
Hecker, C., Nance, K. L., & Hay, B. (2006). Dynamic honeypot construction. In Proceedings of the 10th Colloquium for Information Systems Security Education (Vol. 102). MD, USA.
Holt, T. J. (2017). On the value of honeypots to produce policy recommendations. Criminology and Public Policy, 16, 737.
Holz, T., & Raynal, F. (2005). Detecting honeypots and other suspicious environments. In Proceedings from the Sixth Annual IEEE SMC Information Assurance Workshop (pp. 29–36). IEEE.
Honeynet Project. (2020). Available at: https://www.honeynet.org .
Howell, C. J., & Burruss, G. W. (2020). Datasets for analysis of cybercrime. In The Palgrave handbook of international cybercrime and cyberdeviance (pp. 207–219).
Howell, C. J., Maimon, D., Cochran, J. K., Jones, H. M., & Powers, R. A. (2017). System trespasser behavior after exposure to warning messages at a Chinese computer network: An examination. International Journal of Cyber Criminology, 11 (1), 63–77.
Hsu, C. L., & Lin, J. C. C. (2016). An empirical examination of consumer adoption of Internet of Things services: Network externalities and concern for information privacy perspectives. Computers in Human Behavior, 62, 516–527.
Jacobs, B. A. (1993). Undercover deception clues: A case of restrictive deterrence. Criminology, 31 (2), 281–299.
Jiang, X., & Xu, D. (2004). Collapsar: A VM-based architecture for network attack detention center. In USENIX Security Symposium (pp. 15–28).
Kaaniche, M., Deswarte, Y., Alata, E., Dacier, M., & Nicomette, V. (2007). Empirical analysis and statistical modeling of attack processes based on honeypots . arXiv preprint. arXiv:0704.0861 .
Kennedy, J., Holt, T., & Cheng, B. (2019). Automotive cybersecurity: Assessing a new platform for cybercrime and malicious hacking. Journal of Crime and Justice, 42 (5), 632–645.
Khattab, S. M., Sangpachatanaruk, C., Mossé, D., Melhem, R., & Znati, T. (2004). Roaming honeypots for mitigating service-level denial-of-service attacks. In 24th International Conference on Distributed Computing Systems, 2004. Proceedings (pp. 328–337). IEE.
Leita, C., & Dacier, M. (2008). SGNET: a worldwide deployable framework to support the analysis of malware threat models. In 2008 Seventh European Dependable Computing Conference (pp. 99–109). IEEE.
Leita, C., Pham, V. H., Thonnard, O., Ramirez-Silva, E., Pouget, F., Kirda, E., & Dacier, M. (2008). The leurre.com project: Collecting Internet threats information using a worldwide distributed honeynet. In 2008 WOMBAT Workshop on Information Security Threats Data Collection and Sharing (pp. 40–57). IEEE.
Lengyel, T. K., Neumann, J., Maresca, S., & Kiayias, A. (2013). Towards hybrid honeynets via virtual machine introspection and cloning. In International Conference on Network and System Security (pp. 164–177). Springer, Berlin, Heidelberg.
Li, S., & Schmitz, R. (2009). A novel anti-phishing framework based on honeypots (pp. 1–13). IEEE.
Maimon, D., Alper, M., Sobesto, B., & Cukier, M. (2014). Restrictive deterrent effects of a warning banner in an attacked computer system. Criminology, 52 (1), 33–59.
Maimon, D., Becker, M., Patil, S., & Katz, J. (2017). Self-protective behaviors over public WiFi networks. In The {LASER} Workshop: Learning from Authoritative Security Experiment Results ({LASER} (pp. 69–76).
Maimon, D., Howell, C. J., Jacques, S., & Perkins, R. C. (2020a). Situational awareness and public Wi-Fi users’ self-protective behaviors. Security Journal (online first).
Maimon, D., Howell, C. J., Moloney, M., & Park, Y. S. (2020b). An examination of email fraudsters’ modus operandi. Crime and Delinquency (online first).
Maimon, D., & Louderback, E. R. (2019). Cyber-dependent crimes: an interdisciplinary review. Annual Review of Criminology, 2 , 191–216.
Maimon, D., Santos, M., & Park, Y. (2019a). Online deception and situations conducive to the progression of non-payment fraud. Journal of Crime and Justice, 42 (5), 516–535.
Maimon, D., Testa, A., Sobesto, B., Cukier, M., & Ren, W. (2019b). Predictably deterrable? The case of system trespassers. In International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage (pp. 317–330). Springer.
Chapter Google Scholar
Maimon, D., Wilson, T., Ren, W., & Berenblum, T. (2015). On the relevance of spatial and temporal dimensions in assessing computer susceptibility to system trespassing incidents. British Journal of Criminology, 55 (3), 615–634.
Markatos, E., & Anagnostakis, K. (2008). Noah: A european network of affined honeypots for cyber-attack tracking and alerting. The Parliament Magazine , p. 262.
McGrew, R. (2006). Experiences with honeypot systems: Development, deployment, and analysis. In Proceedings of the 39th Annual Hawaii International Conference on System Sciences (HICSS’06) (Vol. 9, pp. 220a–220a). IEEE.
Nawrocki, M., Wählisch, M., Schmidt, T. C., Keil, C., & Schönfelder, J. (2016). A survey on honeypot software and data analysis. arXiv preprint arXiv:1608.06249 .
Newman, G. R., & Socia, K. (2007). Sting operations . US Department of Justice, Office of Community Oriented Policing Services.
Oluwatosin, H. S. (2014). Client-server model. IOSR Journal of Computer Engineering (IOSR-JCE) , 16 (1), 67.
Oosterhof, M. (2015). Cowrie—Active kippo fork .
Pa, Y. M. P., Suzuki, S., Yoshioka, K., Matsumoto, T., Kasama, T., & Rossow, C. (2015). IoTPOT: Analysing the rise of IoT compromises. In 9th {USENIX} Workshop on Offensive Technologies ({WOOT} 15) .
Patton, M., Gross, E., Chinn, R., Forbis, S., Walker, L., & Chen, H. (2014). Uninvited connections: A study of vulnerable devices on the Internet of Things (IoT). In 2014 IEEE Joint Intelligence and Security Informatics Conference (pp. 232–235). IEEE.
Podhradsky, A., Casey, C., & Ceretti, P. (2012). The Bluetooth honeypot project: Measuring and managing bluetooth risks in the workplace. International Journal of Interdisciplinary Telecommunications and Networking (IJITN), 4 (3), 1–22.
Poeplau, S., & Gassen, J. (2012). A honeypot for arbitrary malware on USB storage devices. In 2012 7th International Conference on Risks and Security of Internet and Systems (CRiSIS) (pp. 1–8). IEEE.
Portokalidis, G., Slowinska, A., & Bos, H. (2006). Argos: An emulator for fingerprinting zero-day attacks for advertised honeypots with automatic signature generation. ACM SIGOPS Operating Systems Review, 40 (4), 15–27.
Pouget, F., & Dacier, M. (2004). Honeypot-based forensics. In AusCERT Asia Pacific Information Technology Security Conference.
Provos, N. (2004). A virtual honeypot framework. In USENIX Security Symposium (Vol. 173, No. 2004, pp. 1–14).
Provos, N., & Holz, T. (2007). Virtual honeypots: From botnet tracking to intrusion detection . Pearson Education.
Raynal, F., Berthier, Y., Biondi, P., & Kaminsky, D. (2004). Honeypot forensics part 1: Analyzing the network. IEEE Security and Privacy, 2 (4), 72–78.
Rege, A. (2013). Factors Impacting Attacker Decision-Making in Power Grid Cyber Attacks. In International Conference on Critical Infrastructure Protection (pp. 125–138). Springer, Berlin, Heidelberg.
Rist, L. (2009). Glastopf project. The Honeynet Project .
Rist, L., Vestergaard, J., Haslinger, D., Pasquale, A., & Smith, J. (2013). Conpot ics/SCADA honeypot . Honeynet Project ( conpot.org ).
Roesch, M. (1999). Snort: Lightweight intrusion detection for networks. In Lisa (Vol. 99, No. 1, pp. 229–238).
Ryan, J. (2010). A history of the Internet and the digital future . Reaktion Books.
Schindler, S., Schnor, B., & Scheffler, T. (2015). Hyhoneydv6: A hybrid honeypot architecture for IPV6 networks. International Journal of Intelligent Computing Research, 6 .
Schneier, B. (2015). Secrets and lies: Digital security in a networked world . Wiley.
Book Google Scholar
Seifert, C., Welch, I., & Komisarczuk, P. (2007). Honeyc-the low-interaction client honeypot. In Proceedings of the 2007 NZCSRCS (Vol. 6). Waikato University, Hamilton, New Zealand.
Spitzner, L. (2001). The value of honeypots, part one: Definitions and values of honeypots. Security Focus .
Spitzner, L. (2002). Honeypots: Tracking hackers Addison Wesley Professional .
Spitzner, L. (2003). Specter: A commercial honeypot solution for windows. Acesso em , 26 (8).
Spitzner, L. (2005). Know your enemy: Honeynets. Honeynet Project .
Spitzner, L., & Roesch, M. (2001). The value of honeypots, part one: Definitions and values of honeypots .
Stanislav, M., & Beardsley, T. (2015). Hacking IoT: A case study on baby monitor exposures and vulnerabilities. Rapid7 Report .
Steinmetz, K. F. (2017). Ruminations on warning banners, deterrence, and system intrusion research. Criminology & Pub. Pol’y, 16 , 725.
Stoll, C. (1990). The cuckoo’s egg: Tracking a spy through the maze of computer espionage .
Testa, A., Maimon, D., Sobesto, B., & Cukier, M. (2017). Illegal roaming and file manipulation on target computers: Assessing the effect of sanction threats on system trespassers’ online behaviors. Criminology and Public Policy, 16 (3), 689–726.
Trivedi, A. J., Judge, P., & Krasser, S. (2007). Analyzing network and content characteristics of spim using honeypots. In SRUTI .
Udhani, S., Withers, A., & Bashir, M. (2019). Human vs bots: Detecting human attacks in a honeypot environment. In 2019 7th International Symposium on Digital Forensics and Security (ISDFS) (pp. 1–6). IEEE.
Vetterl, A. (2020). Honeypots in the age of universal attacks and the Internet of Things . Doctoral dissertation, University of Cambridge.
Vlajic, N., & Zhou, D. (2018). IoT as a land of opportunity for DDoS hackers. Computer, 51 (7), 26–34.
Wilson, T., Maimon, D., Sobesto, B., & Cukier, M. (2015). The effect of a surveillance banner in an attacked computer system: Additional evidence for the relevance of restrictive deterrence in cyberspace. Journal of Research in Crime and Delinquency, 52 (6), 829–855.
Yaqoob, I., Ahmed, E., ur Rehman, M. H., Ahmed, A. I. A., Al-garadi, M. A., Imran, M., & Guizani, M. (2017). The rise of ransomware and emerging security challenges in the Internet of Things. Computer Networks, 129, 444–458.
Yegneswaran, V., Barford, P., & Paxson, V. (2005). Using honeynets for internet situational awareness. In Proceedings of the Fourth Workshop on Hot Topics in Networks (HotNets IV) (pp. 17–22).
Download references
Author information
Authors and affiliations.
Department of Criminal Justice and Criminology, Georgia State University, Atlanta, Georgia, United States of America
Robert C. Perkins & C. Jordan Howell
Department of Criminal Justice, The University of Texas at El Paso, El Paso, Texas, USA
C. Jordan Howell
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Robert C. Perkins .
Editor information
Editors and affiliations.
Department of Sociology, Social Policy and Criminology, University of Southampton, Southampton, UK
Anita Lavorgna
School of Criminal Justice, Michigan State University, East Lansing, MI, USA
Thomas J. Holt
Rights and permissions
Reprints and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Perkins, R.C., Howell, C.J. (2021). Honeypots for Cybercrime Research. In: Lavorgna, A., Holt, T.J. (eds) Researching Cybercrimes. Palgrave Macmillan, Cham. https://doi.org/10.1007/978-3-030-74837-1_12
Download citation
DOI : https://doi.org/10.1007/978-3-030-74837-1_12
Published : 30 July 2021
Publisher Name : Palgrave Macmillan, Cham
Print ISBN : 978-3-030-74836-4
Online ISBN : 978-3-030-74837-1
eBook Packages : Law and Criminology Law and Criminology (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Help | Advanced Search
Computer Science > Cryptography and Security
Title: a survey of honeypots and honeynets for internet of things, industrial internet of things, and cyber-physical systems.
Abstract: The Internet of Things (IoT), the Industrial Internet of Things (IIoT), and Cyber-Physical Systems (CPS) have become essential for our daily lives in contexts such as our homes, buildings, cities, health, transportation, manufacturing, infrastructure, and agriculture. However, they have become popular targets of attacks, due to their inherent limitations which create vulnerabilities. Honeypots and honeynets can prove essential to understand and defend against attacks on IoT, IIoT, and CPS environments by attracting attackers and deceiving them into thinking that they have gained access to the real systems. Honeypots and honeynets can complement other security solutions (i.e., firewalls, Intrusion Detection Systems - IDS) to form a strong defense against malicious entities. This paper provides a comprehensive survey of the research that has been carried out on honeypots and honeynets for IoT, IIoT, and CPS. It provides a taxonomy and extensive analysis of the existing honeypots and honeynets, states key design factors for the state-of-the-art honeypot/honeynet research and outlines open issues for future honeypots and honeynets for IoT, IIoT, and CPS environments.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
DBLP - CS Bibliography
Bibtex formatted citation.
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .

IMAGES
VIDEO
COMMENTS
This paper presents Honeyd, a framework for virtual honeypots, that simulates virtual computer systems at the network level. The simulated computer systems appear to run on unallocated network ...
Introduction. Honeypot is a part or complete system that is designed to be easily compromised by. attackers, so we keep them away from our real environment since they think they already. in, also we can track them and study their tactics, methods, behaviors and tools as if they. inside our production environment.
Paper presentation on HONEYPOTS FOR INFORMATION SECURITY IN NETWORKS Presented by S.SUBANITHA Department of Computer Science and Engineering Second year Kamaraj College of Engineering and Technology Email Id:[email protected] ABSTRACT The primary focus of this paper is to demonstrate about the exciting new technology "HONEYPOTS". In this ...
1) Honeypot pla ys a significant role in preventing the a ttacks. and malicious activities. 2) It improves the attack detection time, response time [4]. 3) It extracts the intrusion behaviour ...
Paper characteristics: Th is table shows the Honeypot survey/review pap ers included in t his work and their physical fe a- tures. The number o f citations/yea r, helps to show the relevance of p ...
Presentation Transcript. Honeypot Introduction • Countermeasure to detect or prevent attacks • Know attack strategies • Gather information which is then used to better identify, understand and protect against threats. • Divert hackers from productive systems 3/26.
This ppt contains all the basics of honeypots like their types, implementation technologies, position in the network etc. In the end, it contains a screenshot of a live honeypot processing. Read more. Technology. 1 of 19. Download now. Download to read offline. Honeypot Basics - Download as a PDF or view online for free.
analysed which honeypots are more suited for a university setting, and second the results of an actual honeypot deployment is presented and discussed. The rest of the paper is organised as follows: In Section 2 we provide a background on di↵erent kinds of honeypots and analyse which honeypots are most suited for a university setting.
The present review paper proposes and designs the importance of honeypot deployment technique in the protection of data based on the in-frastructures of honeypot, its advantages and disadvantages. The authors also try to offer possible solutions for issues that are generated while using honeypot. See Full PDF.
Honeypots are a type of cybersecurity tool designed with the general purpose of being attacked and compromised by cyberthreats. They became widely popularized throughout the 1990s by computer scientists due to their multi-functional capabilities. As a result, a wide variety of honeypots have been introduced to handle different cybersecurity tasks.
IIoT, and CPS honeypots and honeynets, Presentation of open research problems that still need to be addressed in honeypot and honeynet research for IoT, IIoT, and CPS. Organization: The paper is organized as follows: Section II gives the related work. Section III provides background infor-mation onhoneypots, honeynets,and related terms. Section IV
A Practical Guide to Honeypots Eric Peter, epeter(at)wustl(dot)edu and Todd Schiller, tschiller(at)acm(dot)org (A project report written under the guidance of Prof. Raj Jain) Download Abstract This paper is composed of two parts: a survey of honeypot technology and a case study describing a low-interaction honeypot implemented in Java.
Threat Briefings & Webinar. Briefing document and presentation that provides actionable information on health sector cybersecurity threats and mitigations. Analysts present current cybersecurity topics, engage in discussions with participants on current threats, and highlight best practices and mitigation tactics.
Seminar on Honeypot Technology - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. Honeypots are a security resource whose values lies in being intruded or attacked. They are an internet-based server that acts as a decoy,luring potential hackers so that specialist may monitor and study how system break-ins occur.
Honeypot is an exciting new technology with enormous potential for the security community. According to Lance Spitzner, founder of honeypot project: "A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource." Used for monitoring, detecting and analyzing attacks 4
Paper presentation on HONEYPOTS FOR INFORMATION SECURITY IN NETWORKS Presented by S.SUBANITHA Department of Computer Science and Engineering Second year Kamaraj College of Engineering and Technology Email Id:[email protected] ABSTRACT The primary focus of this paper is to demonstrate about the exciting new technology "HONEYPOTS".In this era of technology, the hectic usage of internet plays ...
Honeypot technology and traditional security system combined can build an active network security protection system.[4] II. HONEYPOT CLASSIFICATION A. Based on level of interaction Honeypots can be classified based on the level of interaction between intruder and system. These are Low-interaction, high-interaction and medium-interaction honeypot.
FRANCE. Research Report RR-03-081. White Paper: "Honeypot, Honeynet, Honeytoken: T erminological issues 1". September 14, 2003. Fabien Pouget, Marc Dacier Hervé Debar. Institut Eurécom ...
Daniel Zielinski, Hisham A. Kholidy. State University of New York (SUNY) Polytechnic Institute, College of Engineering, Network and Computer Security Department, Utica, NY USA. [email protected], [email protected]. Abstract— This paper explores deploying a cyber honeypot system to learn how cyber defenders can use a honeypot ...
This paper makes the following contributions: (1) We provide a summary of the limitations and shortcomings of existing ICS Honeypots and discuss how they address (or not) emerging malware threats, as well as new ICS technology, e.g., new PLC models and ICS network protocols. (2) We present HoneyPLC, a high-interaction honeypot for PLCs,
There are few steps in order to flash the Raspbian OS on the SD card: Insert the micro SD card into computer or laptop Open the Raspberry Pi Imager and select OS i.e. Raspbian OS as shown in ...
This paper provides a comprehensive survey of the research that has been carried out on honeypots and honeynets for IoT, IIoT, and CPS. It provides a taxonomy and extensive analysis of the existing honeypots and honeynets, states key design factors for the state-of-the-art honeypot/honeynet research and outlines open issues for future honeypots ...
Abstract and Figures. Honeypots have been utilized broadly for more than two decades. Notwithstanding, their improvement is infrequently went with a comprehension of how assailants can distinguish ...