

How to Navigate and Interpret Microsoft Office 365 Audit Logs
Office 365 audit logs are records that provide detailed information about activities that occur within a Microsoft Office 365 environment. These activities can be performed by users, administrators, or the system itself. The logs capture a wide range of events and activities, such as file and folder accesses, downloads, edits, deletions, sharing activities, changes in settings, user sign-ins, and many more. This is important for two reasons:
- Security: Audit logs are an essential tool for security analysis and incident response. They allow security teams to track user behavior and investigate suspicious activities. For instance, if there's an unexpected spike in file downloads or deletions, it could indicate a potential security breach. By examining the audit logs, teams can identify the user who performed these actions and the exact time they occurred, which can be instrumental in understanding the scope and nature of the incident.
- Compliance: For organizations subject to regulations that require certain controls over data access and modifications, audit logs provide the necessary documentation. They can demonstrate that the organization has visibility into and control over its data. For example, regulations like GDPR, HIPAA, and SOX require businesses to have a clear understanding of who has access to sensitive data, when they access it, and what they do with it. Office 365 audit logs provide this information, helping organizations meet their compliance obligations.
However, if you don't know what to look for, navigating and interpreting the mess of information in the audit logs can be an endless hassle. Today, let's take a look at the different types of data collected and stored in these audit logs, understand how they are formatted, and learn how to interpret them properly for different use cases.
Understanding the Office 365 Admin Logs
Given the vast amount of information included within each entry, it's important to know how to read and interpret the audit logs for Microsoft 365 . First, let's take a look at the different components that make up each entry:
- Date and Time: The exact date and time when the activity occurred.
- User: The user (or system component) that performed the action. This could be an end user, an administrator, or a service account.
- Activity: The specific action that was performed. This could be anything from viewing a document, editing a file, deleting an item, to administrative actions like changing user permissions or system settings.
- Item: The specific object that was affected by the activity. This could be a file, folder, user account, system setting, etc.
- Details: Additional information about the activity, such as the location from which the activity was performed, the client used (e.g., web browser, mobile app, desktop app), and other relevant data.
Audit logs play a crucial role in tracking user and admin activities. They help you address vulnerabilities in the system and ensure accountability across your organization's chain of command. Here are a few reasons why they're so important:
- Security Monitoring: Audit logs help identify unusual or suspicious activities that could indicate a security threat, such as a potential data breach or misuse of privileges.
- Incident Investigation: In the event of a security incident, audit logs provide detailed information that can help determine what happened, when it happened, who was involved, and what was affected.
- Compliance Monitoring: Many regulatory standards require organizations to maintain detailed logs of user and admin activities. Audit logs can provide the necessary documentation to demonstrate compliance with these regulations.
- Operational Oversight: Audit logs can help administrators understand how users are interacting with the Office 365 environment, which can inform decisions about resource allocation, training needs, policy updates, and more.
Activities Tracked by the Office 365 Logs
Office 365 Audit Logs track a wide variety of activities to provide comprehensive visibility into the actions taken within an organization's Office 365 environment. Here are some of the key types of activities tracked:
- File and Folder Activities: These include actions such as viewing, editing, downloading, moving, copying, or deleting files and folders. This also covers activities related to sharing files and folders, like creating and managing sharing invitations or accessing shared files.
- Email Activities: These involve actions taken in Outlook, such as sending, receiving, or deleting emails. It also includes activities like setting mailbox permissions, mailbox login events, and changes to mailbox settings.
- SharePoint and OneDrive Activities: These include actions like uploading, downloading, viewing, editing, moving, or deleting documents in SharePoint or OneDrive. It also tracks activities like sharing documents, adding or removing apps, and changes to site settings.
- Teams Activities: These involve actions taken in Microsoft Teams, such as creating or deleting teams, adding or removing members, creating or deleting channels, and posting or deleting messages.
- User Administration Activities: These include actions related to managing users in Office 365, such as creating or deleting users, changing user roles or permissions, resetting passwords, and managing user licenses.
- Group and Directory Activities: These involve actions related to managing groups and directories in Office 365, such as creating or deleting groups, adding or removing members from groups, and changes to group settings.
- Role Administration Activities: These include actions related to managing roles in Office 365, such as assigning or removing roles to users, and changes to role settings.
- Synchronization Activities: These involve actions related to synchronizing directories and files in Office 365, such as starting or stopping synchronization, and changes to synchronization settings.
- Exchange Mailbox Activities: These include actions taken in an Exchange mailbox, such as logging into a mailbox, sending or receiving mail, creating or deleting mailbox items, and changes to mailbox properties.
- Security and Compliance Activities: These involve actions related to managing security and compliance features in Office 365, such as managing security policies, conducting audit log searches, and managing data governance policies.
Each of these activities provides valuable insights into how users and administrators are interacting with the Office 365 environment, which can be crucial for security monitoring, incident response, operational oversight, and compliance reporting.
How to Enable or Disable the Microsoft 365 Audit Log?
Microsoft 365 audit logs are always turned on by default for every organization. To turn auditing on or off in your Microsoft 365 organization, you need to be assigned the Audit Logs role in Exchange Online. By default, this role is assigned to the Compliance Management and Organization Management role groups on the Permissions page in the Exchange admin center. Here's how it works:
Enabling the Microsoft 365 Audit Log
- Go to the Microsoft Purview compliance portal .
- Navigate to "Solutions > Audit".
- If auditing isn't turned on for your organization, a banner will be displayed prompting you to start recording user and admin activity.
- Click on the "Start recording user and admin activity" banner. It may take up to 60 minutes for the change to take effect.
You can also enable auditing using Exchange Online PowerShell:
- Connect to Exchange Online PowerShell.
- Run the following PowerShell command to turn on auditing: Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
- A message will be displayed saying that it may take up to 60 minutes for the change to take effect.
Disabling the Microsoft 365 Audit Log
Disabling the audit log can only be done using Exchange Online PowerShell:
- Run the following PowerShell command to turn off auditing: Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $false
After a while, you can verify that auditing is turned off (disabled) in two ways:
- In Exchange Online PowerShell, run the following command: Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabled. The value of False for the UnifiedAuditLogIngestionEnabled property indicates that auditing is turned off.
- Go to the Audit page in the compliance portal. If auditing isn't turned on for your organization, a banner will be displayed prompting you to start recording user and admin activity.
How to Search the Logs When Auditing Office 365
When you're running an audit across your organization's cloud environment, knowing how to search and locate specific information within the audit logs is a crucial skill. Here's a step by step guide on searching the Office 365 audit logs for various activities and events:
Step 1: Run an audit log search
- Go to https://compliance.microsoft.com and sign in.
- In the left pane of the compliance portal, select "Audit".
- On the Search tab, configure the following search criteria:
- Start date and End date: The last seven days are selected by default. Select a date and time range to display the events that occurred within that period. The date and time are presented in Coordinated Universal Time (UTC). The maximum date range that you can specify is 90 days.
- Activities: Select the drop-down list to display the activities that you can search for. User and admin activities are organized into groups of related activities. You can select specific activities or you can select the activity group name to select all activities in the group.
- Users: Select in this box and then select one or more users to display search results for. The audit log entries for the selected activity performed by the users you select in this box are displayed in the list of results.
- File, folder, or site: Type some or all of a file or folder name to search for activity related to the file of folder that contains the specified keyword. You can also specify a URL of a file or folder.
- Select "Search" to run the search using your search criteria.
Step 2: View the search results
The results of an audit log search are displayed under Results on the Audit log search page. A maximum of 50,000 (newest) events are displayed in increments of 150 events. Use the scroll bar or press Shift + End to display the next 150 events.
Step 3: Export the search results to a file
- Run an audit log search, and then revise the search criteria until you have the desired results.
- On the search results page, select "Export > Download all results". All entries from the audit log that meet the search criteria are exported to a CSV file. The raw data from the audit log is saved to a CSV file. Additional information from the audit log entry is included in a column named AuditData in the CSV.
- After the export process is complete, a message is displayed at the top of the window that prompts you to open the CSV file and save it to your local computer.
Please note that you can download a maximum of 50,000 entries to a CSV file from a single audit log search. If 50,000 entries are downloaded to the CSV file, you can probably assume there are more than 50,000 events that met the search criteria. To export more than this limit, try using a date range to reduce the number of audit log entries. You might have to run multiple searches with smaller date ranges to export more than 50,000 entries.
What You Need to Know About Office 365 Audit Log Retention
Audit log retention in Office 365 is an important aspect of the platform's security and compliance features. By default, audit records are retained for 90 days. This means that any action or event that is audited and logged by Office 365 will be kept in the audit log for a period of 90 days from the date of the event.
After this period, the audit record is automatically deleted and is no longer available for audit log searches. This 90-day retention period applies to all user and admin activities across various services in Office 365, including Exchange Online, SharePoint Online, OneDrive for Business, and Azure Active Directory.
However, the retention period for audit logs can be affected by changes to user licensing or retention policies. For instance, users assigned an Office 365 E5 or Microsoft 365 E5 license, or users with a Microsoft 365 E5 Compliance or Microsoft 365 E5 eDiscovery and Audit add-on license, have their audit records for Azure Active Directory, Exchange, and SharePoint activity retained for one year by default. Organizations can also create audit log retention policies to retain audit records for activities in other services for up to one year.
If a user's license is changed, the retention period for their audit data will adjust according to the new license. For example, if a user is moved from an Office 365 E3 license (which has a 90-day retention period) to an Office 365 E5 license (which has a one-year retention period), their audit data will be retained for one year from the date of each event moving forward. However, the retention period for events that occurred before the license change will not be extended.
Similarly, changes to retention policies can also affect the expiration date of audit data. If an organization decides to extend the retention period for certain types of audit data, the new retention period will apply to all future events of that type. However, it will not retroactively extend the retention period for events that occurred before the policy change.
How to Simplify Office 365 Audit Log Management With Simeon Cloud
Simeon Cloud is a premium end-to-end configuration management solution for enterprise organizations and managed service providers running Microsoft 365. It uses configuration-as-code technology to automate the setup and maintenance of Microsoft 365 services like Office 365, Intune, and Azure AD.
When it comes to managing Office 365 Audit Logs , Simeon Cloud offers several key features that simplify the process of navigating and interpreting them:
- Verification of Audit Log Status: With Simeon, you can easily verify the status of the audit log feature for every tenant you currently manage. You can make sure that the Unified Audit Log is working for a particular tenant, and if not, you can switch it on directly through Simeon.
- Enhanced Audit Log Reports: Simeon enhances and improves the cumbersome audit log provided by Microsoft by breaking it down into daily reports that update you on changes made to the default configurations of all your tenants. It offers a single-pane-of-glass view for implementing, reviewing, and managing changes to your multi-tenant ecosystem in Microsoft 365.
- Searchable Inventory of Changes: From the Sync tab in the Simeon dashboard, you can access a searchable inventory of all the changes made to your tenant configurations. Here, you can review deviations from your baseline configuration and choose to approve, reject, or roll back configuration changes to your organization’s tenants.
- Simplified Rollback of Changes: Simeon Cloud improves upon the existing documentation provided by Microsoft by making it more digestible and search-friendly, while also letting you roll back changes with a single click from within the same UI. That way, you can always rest assured knowing that your organization has proper access to detailed documentation on all your tenants in case of a security breach as well as the ability to revert those tenants back to a known good state should a disaster occur.
Simeon Cloud provides a powerful and user-friendly solution for managing Office 365 Audit Logs. It not only ensures that audit logging is enabled for all your tenants but also provides enhanced reporting, searchable inventory of changes, and simplified rollback capabilities. Want to learn more? Sign up for a free demo with our sales team, today!
Try Simeon Cloud for free
Getting started is easy! No credit card required.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Microsoft 365 Reports in the admin center
- 25 contributors
Check out Microsoft 365 small business help on YouTube.
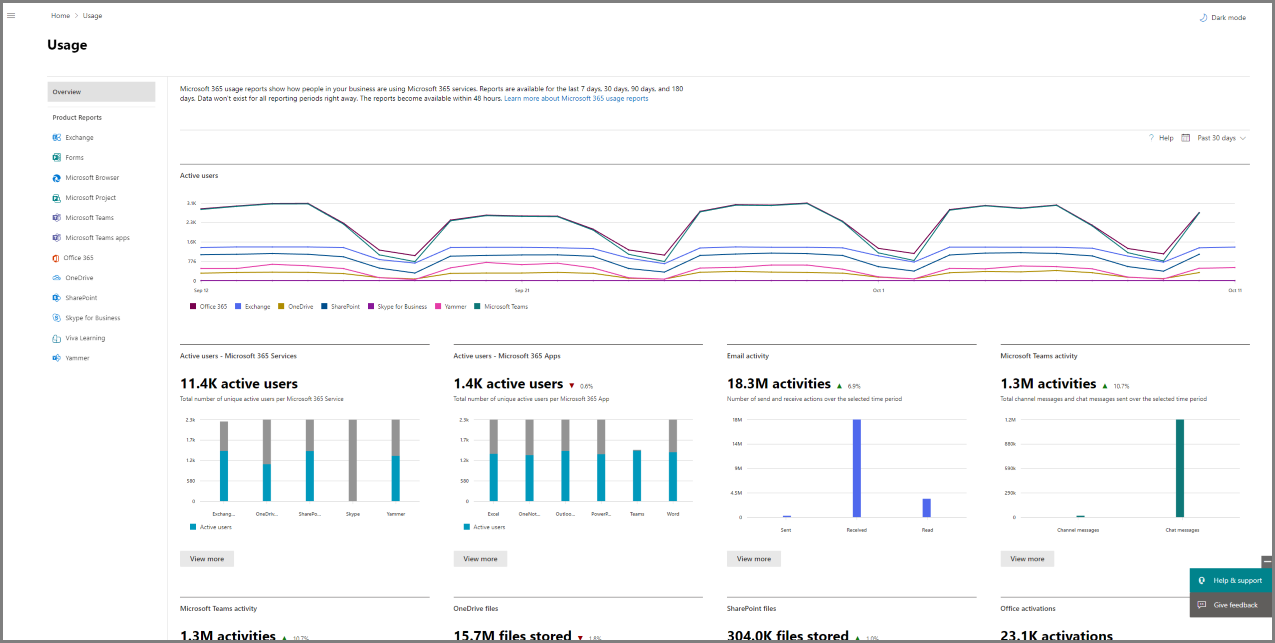
You can easily see how people in your business are using Microsoft 365 services. For example, you can identify who is using a service a lot and reaching quotas, or who may not need a Microsoft 365 license at all. Perpetual license model won't be included in the reports.
Reports are available for the last 7 days, 30 days, 90 days, and 180 days. Data won't exist for all reporting periods right away. The reports typically become available within 48 hours, but might sometimes take several days to become available.
Watch: Act on a usage report in Microsoft 365
Check out this video and others on our YouTube channel .
How to get to the Reports dashboard
- In the admin center, go to the Reports > Usage page.
- In the admin center , go to the Reports > Usage page.
Select the View more button from the at-a-glance activity card for a service (such as email or OneDrive) to see the report detail page. On that page, different reports for the service are provided in tabs.
Who can see reports
People who have the following permissions:
Global admins: We recommend that only a few people in your company have this role. It reduces the risk to your business.
Exchange admins
SharePoint admins
Skype for Business admins
Global reader (with no user details)
Usage Summary Reports reader (with no user details): By design, this role has read access to user, groups, and other settings by default in the Microsoft 365 admin center, as the role is based on Microsoft Entra.
Reports reader
Teams Administrator
Teams Communications Administrator
User Experience Success Manager (with no user details)
To learn more, see About admin roles and Assign admin roles .
Which activity reports are available in the admin center
Depending on your subscription, here are the available reports in all environments.
N/A 1 : The report is planned to be released in the future. The Microsoft 365 Roadmap will be updated before the release.
N/A 2 : The service is not available in the environment, so there's no plan to release the report.
How to view licensing information
To see how many licenses you have assigned and unassigned, in the admin center, go to the Billing > Licenses page.
To see who is licensed, unlicensed, or guest, in the admin center, go to the Users > Active users page.
How to view usage information for a specific user
Use the service reports to research how much a specific user is using the service. For example, to find out how much mailbox storage a specific user has consumed, open the Mailbox usage report, and sort the users by name. If you have thousands of users, export the report to Excel so you filter through the list quickly.
You can't generate a report where you enter a user's account and then get a list of which services they're using and how much.
There are circumstances where new users show up as unknown . This is usually due to occasional delays in creating user profiles.
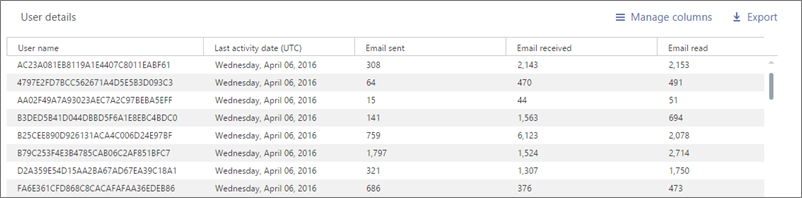
Show user details in the reports
By default, user details will be hidden for all reports.
Your user list will look like this:
If you want to unhide user-level information when you're generating your reports, a global administrator can quickly make that change in the admin center.
Reports provide information about your organization's usage data. By default, reports display information with identifiable names for users, groups, and sites. Starting September 1, 2021, we're hiding user information by default for all reports as part of our ongoing commitment to help companies support their local privacy laws.
Global administrators can revert this change for their tenant and show identifiable user information if their organization's privacy practices allow it. It can be achieved in the Microsoft 365 admin center by following these steps:
In the admin center, go to the Settings > Org Settings > Services page.
Select Reports .
Uncheck the statement Display concealed user, group, and site names in all reports , and then save your changes.
Beginning on June 23, 2022, an API will gradually become available to all environments for global admins to change this setting without needing to visit the Microsoft 365 admin center. The API details are below:
The URL is https://graph.microsoft.com/beta/admin/reportSettings
Two methods have been approved for this API:
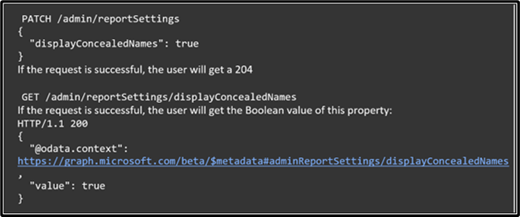
The report will only contain a Privacy Setting property. For more information on Graph API, see Use the Microsoft Graph API . Global admins can use the Software Development Kit (SDK) or directly call the API using any program language with network ability. We recommend using Graph Explorer .
It will take a few minutes for these changes to take effect on the reports in the reports dashboard. This setting also applies to the Microsoft 365 usage reports in Microsoft Graph and Power BI and the usage reports in Microsoft Teams Admin center . Showing identifiable user information is a logged event in the Microsoft Purview compliance portal audit log.
What happens to usage data when a user account is deleted?
Whenever you delete a user's account, Microsoft will delete that user's usage data within 30 days. Deleted users will still be included in the Activity chart totals for the periods they were active in, but will not appear in the User Details table.
However, when you select a particular day, up to 28 days from the current date, the report show the user's usage for that day in the User Details table.
Related content
Microsoft 365 usage analytics (article) Customize the reports in Microsoft 365 usage analytics (article) Working with Microsoft 365 usage reports in Microsoft Graph beta (article) Working with Microsoft 365 usage reports in Microsoft Graph v1.0 (article)
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Subscribe for Practical 365 updates
Please turn off your ad blocker and refresh the page to subscribe.
You may withdraw your consent at any time. Please visit our Privacy Statement for additional information
Azure Active Directory
Why microsoft 365 license assignment dates can be misleading.

Table of Contents
Just When Did a User Account Receive a License?
My article about using the Microsoft Graph PowerShell SDK to generate a licensing report for a tenant is quite popular. The intention of the script is to illustrate the principles of retrieving license information for Azure AD user accounts with the SDK cmdlets. It’s not to deliver a fully-finished licensing report solution. If you’re looking for a more polished report, you can either consider an ISV license management product or upgrade the script to meet your needs.
A recent comment asked about retrieving license assignment data to know when accounts receive licenses. It’s an interesting question and I’m sure it’s information that administrators might find useful in some circumstances.
Azure AD Account Properties Used by Licensing
Azure AD user accounts have two properties of interest for licensing. The first is assignedLicenses , which details the assigned licenses for the account. This example shows that the account has one license identified by an SKU and that three of the service plans are disabled (see this article for details about license management with the Microsoft Graph PowerShell SDK).
The second property is assignedPlans and contains the service plans from all assigned licenses. A service plan is a not-for-sale license component like Exchange_S_Enterprise , the Exchange Online component that’s bundled into Office 365 E3 and Office 365 E5. The assignedPlans property notes if a service plan is enabled or deleted (removed) and the assignment date. Here’s an edited version of what you might see for an account with an Office 365 E5 license:
Multiple service plans are listed for the same service. That’s because some services (like Exchange Online) are responsible for the delivery of multiple services. For example, Exchange Online delivers both email services and the information barriers service to accounts with Office 365 E5 licenses.
TEC Talk: Five Things Microsoft 365 Security Administrators Should Do in 2023
Don’t miss Tony Redmond’s free TEC Talk on March 23rd at 11:00 am EST.
Figuring Out License Assignment Dates
The assignment information for a service plan includes a timestamp. Is it therefore valid to find a service plan associated with a license and assume that its assignment date reflects when an administrator assigned the license to an account?
Regretfully, no. The problem is that the license assignment information reported by the Graph APIs doesn’t distinguish between human-initiated and system-initiated actions. Microsoft tweaks licenses all the time to add or remove service plans (for example, to introduce the Viva Engage Core service plan for products like Office 365 E3 ). These actions occur in the background and tenant administrators aren’t aware of when they happen. The APIs treat a license update performed by Microsoft as the same as when an administrator assigns a license or disables a service plan for a user account. In a nutshell, this means that the reported assignment date is valid but tells you nothing about the last time an administrator managed licenses for an account.
Figure 1 illustrates the problem. This information comes from selecting a known service plan (information protection) from the Office 365 E3 SKU and using it to report the assignment date for the license. I see accounts like Paul Robichaux whom I know received their license well before August 12, 2019.
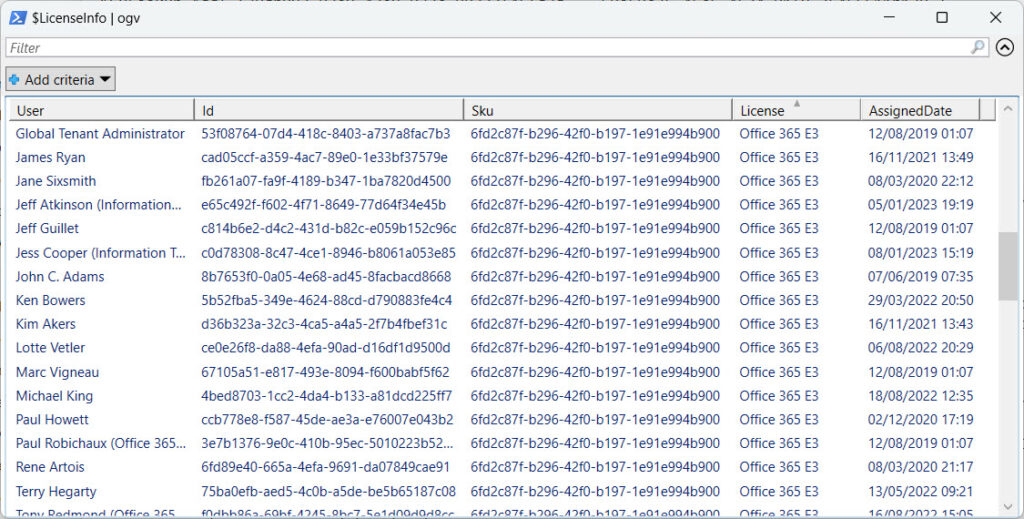
Nevertheless, the license assignment data is accurate in one sense in that someone or something assigned the license to the account on that date. The possibility that the action might have been a reassignment of a previously held license is another matter.
Tracking License Assignment Dates
To analyze license assignment dates for accounts, I wrote a script that:
- Defines a hash table of license/SKU identifier (the key) and a service plan identifier that I know exists in the SKU. For example, the Teams Premium license (989a1621-93bc-4be0-835c-fe30171d6463) includes the Teams Webinars Pro service plan (78b58230-ec7e-4309-913c-93a45cc4735b).
- Runs the Get-MgUser cmdlet to find all licensed users.
- For each user, find the set of currently enabled licenses and service plans. Then loop through the licenses to check the assigned date for a service plan that belongs to that license (that’s where the hash table comes in).
- Report the date for each user (Figure 1 shows an extract).
- The script also outputs an assignment date for each license (European dates shown).
Here’s the code. The information about product/SKU and service plan identifiers is available online .
Using the License Assignment State API
PowerShell being PowerShell, there’s usually an alternative method to explore to do something. In this instance, we can use the Graph License Assignment State API to retrieve the timestamp stored in the Graph for the last time the license assignment changed. This is a relatively new API, and its timestamps only go back to mid-2022. However, it might be an option to explore.
The Azure AD Product names and service plan identifiers for licensing page includes the option to download a CSV file containing license and service plan identifiers. Microsoft updates the CSV file regularly and it’s a useful tool to have.
In my case, I wanted to resolve product identifiers into human-understandable names, so I downloaded the file and loaded it into an array. I then selected the properties I needed, sorted them to create unique values, and loaded the data into a hash table for fast lookup. If your tenant uses some newly-introduced licenses, you might need to “patch” the data by inserting them into the table. I do this below for the Teams Premium test and Viva Suite licenses.
To find the license assignment state for a user account, we can do this:
The code generates output like:

Using the Audit Log to Track License Assignments
The audit log is the other source of information about license assignments. I’ve covered this topic previously and concluded that although the data revealed by audit events needs some work to uncover, it does tell you when administrators assigned or removed licenses from user accounts. The problem is that the audit log is only available for Office 365 E3 licenses (and above) and audit events are only available for 90 days (Office 365 E3) or 365 days (Office 365 E5). Many organizations get around this problem by offloading audit data to a SIEM like Splunk or Microsoft Sentinel .
Various Methods Exist, All Flawed
Getting back to the original question, various methods exist to track license assignments:
- Use a service plan-assigned date.
- Use the license assignment state date.
- Use the audit data.
All methods have their downsides. It would be nice if Microsoft noted a timestamp for the last administrator-initiated change for each license assigned to user accounts, but they don’t and leave the task of assignment interpretation to administrators. Just another thing to add to the list…
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!
About the Author

Tony Redmond
Where do we get the billingenddate for the subcriptions of our tenants in O365 Products without using the MsolSubscription in powershell
Billing date for subscriptions is coming (or so I hear from Microsoft)
I really wanted something like this to be native from Microsoft but found the same — automated changes by Microsoft reset the date making it an unreliable data source. I wrote a script that gathers user licensing information similar to your methods above, compares to log file from the previous run, and keeps a running date for when that subscription was initially assigned. I store everything on a SPO site and have that data going back to 2019 when I first started. It’s been VERY helpful when making additional decisions about reclamation, especially comparing to things like the Project usage report. Newly assigned license that hasn’t been used in 90 days after assignment? Older license that hasn’t been used in 180 days? Those get made available for others to use. Without knowing when the assignment occurred, those decisions can’t be made. Having the initial assignment data within a week’s worth of time has been good enough for us.
Original script was using AzureAD module, but I migrated to Microsoft Graph PowerShell SDK last year. There is probably some solution out there that would have taken care of all this for us, but this was also a great way to learn how to interact with the Microsoft Graph PowerShell SDK and serves us well, even if there is occasional maintenance needed.
Yep. This is a real pain…
Besides the audit log for User License Updated (individual changes), we would also need to check AD group membership changes and AD group assigned licenses, correct?
Yep. I cover reporting of group-based licensing in https://practical365.com/group-based-licensing-report/
Leave a Reply Cancel reply
Latest articles.
PowerShell, Teams, and Exchange News with Special Guest MVP Michel De Rooij: The Practical 365 Podcast S4 E17
On the show this week, we're joined by fellow Microsoft MVP and long-term PowerShell, Exchange and Microsoft 365 expert, Michel De Rooij to discuss PowerShell, GitHub Copilot, Teams, and more!
- Exchange Online
Streamlining Device Management: Integrating Devices with Intune
Integrating devices with Intune requires a multifaceted approach to accommodate various organizational needs. In this blog, we review a few strategies for effectively integrating devices with Intune in your organization.

Translating SharePoint Online Documents
SharePoint Translation is a SharePoint Premium service that can translate the content of Office documents and PDF files to the languages supported by the Microsoft Translator service. Be careful about the costs, which can be heavy if you process large documents.

- Active Directory Reporting
- Office 365 Reporting
- Azure AD Monitoring
- How to Monitor Office 365 Activity Logs for Improved Security

- May 15, 2023
How to Monitor Office 365 Activity Logs for Improved Security. Looking to enhance the security of your Office 365 ? It’s crucial to monitor the activity logs of Office 365, and Microsoft’s unified Office 365 audit logging portal provides a single platform to do that.
In this article, we explore an overview of the Office 365 unified audit logging.
Then, we learn the licensing and permission requirements to use the Microsoft 365 unified audit log. Moreover, this section includes steps to check if you meet these requirements and what to do if you don’t.
Next, we examine how to check if unified audit logging is enabled for your organization. Then, we discuss the steps to enable it through the Microsoft compliance portal or Windows PowerShell .
Once audit logging is enabled, we cover how to search, view, and export Office 365 audit logs to CSV . Finally, we show how to monitor and analyse the 365 activity logs to improve your organization’s security.
Also Read How to Configure Azure AD Activity Logs for Effective Monitoring
Overview of the Office 365 Unified Audit Logging
Microsoft 365 (M365) is a set of cloud based services. Some services included in M365 are Azure Active Directory , Exchange Online , and SharePoint Online.
The services included in your M365 subscription depends on your subscription.
Now, with so many Office 365 services, admins face the considerable challenge to monitor the activity logs of the various services for improved security of the organization. The good news is that the Microsoft Purview compliance portal offers Microsoft 365 admins a single location to enable unified audit.
Now, you must wonder which of the Microsoft 365 services supports unified auditing . To view all services you monitor, see the list in the Microsoft 365 services that support auditing page.
Also Read How to Connect to Office 365 using Powershell
Microsoft 365 Audit Log Licensing and Permissions
Microsoft offers two versions of the Microsoft Purview Audit, which allows you to enable, search for and monitor Microsoft 365 unified audit logs.
So, you get the Microsoft Purview Audit (Standard) or (Premium) , depending on your organization’s Microsoft 365 subscription and licensing .
Additionally, admins that need to run audit log reports must be granted the required permissions.
To configure the licensing and user permission requirements, complete these steps.
Step 1: Confirm that Your Organization Meets Subscription / User Licensing Requirements
To access Microsoft 365 unified audit log, your organization must have a minimum of Microsoft Business Basic/Standard subscriptions. It is the same as the Azure AD Premium P1 license.
On the contrary, to access the Audit (Premium) feature, you require at least the Microsoft 365 Enterprise E5 subscription.
Follow the steps below to check your assigned subscription.
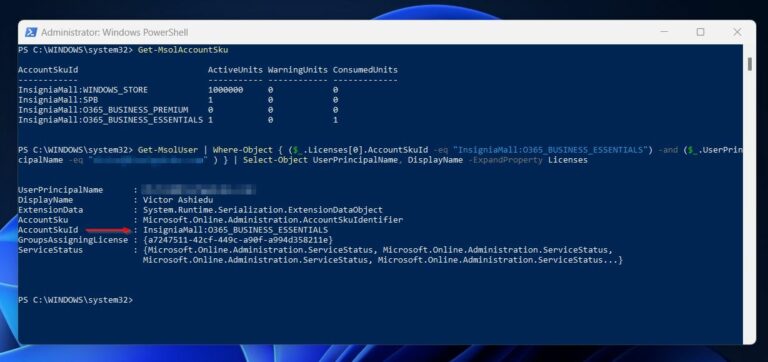
1. Follow the steps in our article – How to Connect to Office 365 using Powershell- to install the MSOnline PowerShell Module. Then, connect to Office 365. 2. Run the Get- MsolAccountSku command to list the Microsoft 365 license available in your tenant.
2. Next, run the command below to return the license your admin has assigned to you.
Replace the License_AccountSkuId with the AccountSkuId (the license name) from the last command. Also, replace [email protected] with your Office 365 UPN.
Check the value of the last command displayed in the AccountSkuId property. Then, compare that with the Microsoft 365 Licensing requirements .
Finally, if the license your admin assigned you is listed, check the Microsoft 365 permission requirements using the steps in the following subsection.
Also Read Get-AzureADAuditSignInLogs – Find Sign In Logs Last 30 Days PowerShell
Step 2: Confirm that Your Account Meets the Permission Requirements
To view and run Office 365 unified audit log searches, admins or users must be assigned the View Only Audit Logs or Audit Logs role in Exchange Online . The Compliance Management and Organization Management role groups have the required permissions by default.
Furthermore, members of the Office 365 Global Administrators group are added to Organization Management role group in Exchange Online by default.
Follow the steps below to check, if an account has the required permission to enable and search the audit logs. If you’re a Global Admin for your Office 365 tenant, ignore the steps below and proceed to the next section.
1. Open the Exchange Online admin center via admin.exchange.microsoft.com . Next, expand Roles and click “Admin Roles.” 2. On the search box of the “Admin roles” page, enter “management” to return only roles that include that term. Then, click the Compliance Management role.
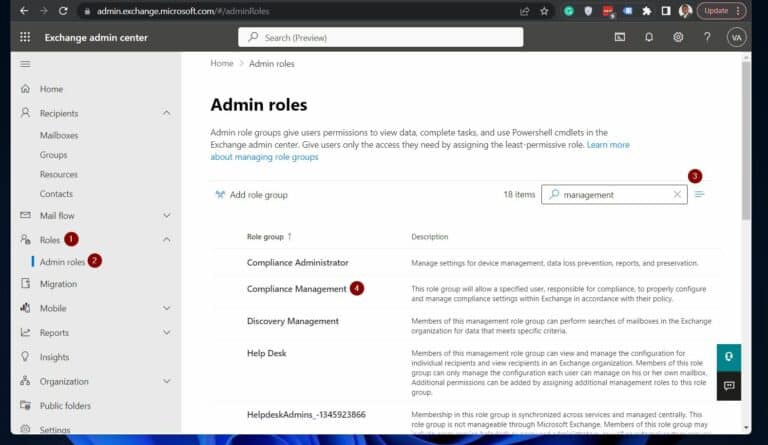
3. On the Compliance Management role flyout, click the “Assigned” tab. All users listed in this tab have permission to view search audit logs.
To add a user to this role, click the “+ Add” button – see the second screenshot.
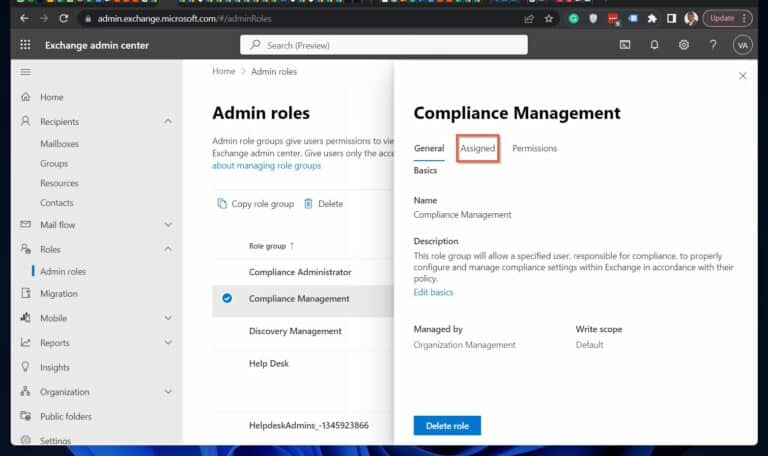
4. Repeat step 3 for the Organization Management role.
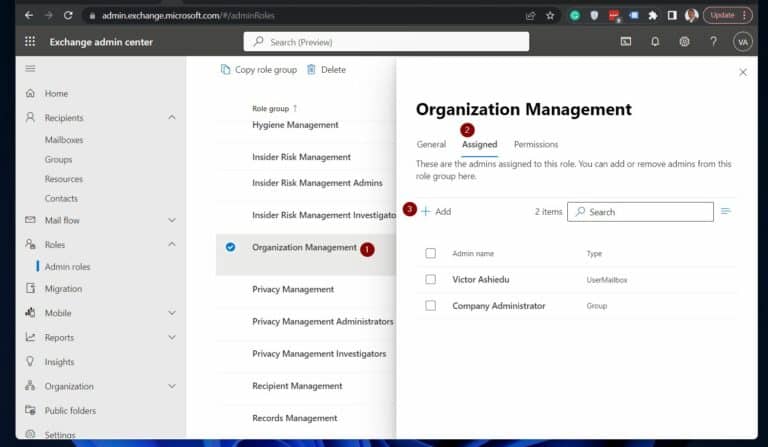
Also Read Top 15 Office 365 PowerShell Commands (Users, Groups, Licensing)
Check the Current Status of Audit Logging for Your Organization
Before using the Microsoft compliance portal to monitor Office 365 activity logs for improved security of your organization’s services, you must enable audit monitoring . Enabled by default in organizations with Microsoft 365 and Office 365 enterprise subscriptions .
However, Microsoft may not enable auditing in some Microsoft 365 subscriptions by default. So, confirming if auditing is enabled in your O365 tenant before proceeding is a good idea.
Follow the steps below to check the current auditing status.
1. Use the steps in our Connect to Exchange Online using PowerShell article- to connect to your Exchange Online tenant. 2. Once you’ve connected to Exchange Online,
The screenshot below shows all the commands you need to install the Exchange Online PowerShell module. Then, connect and run the Get- AdminAuditLogConfig to determine, if auditing is enabled for your organization.
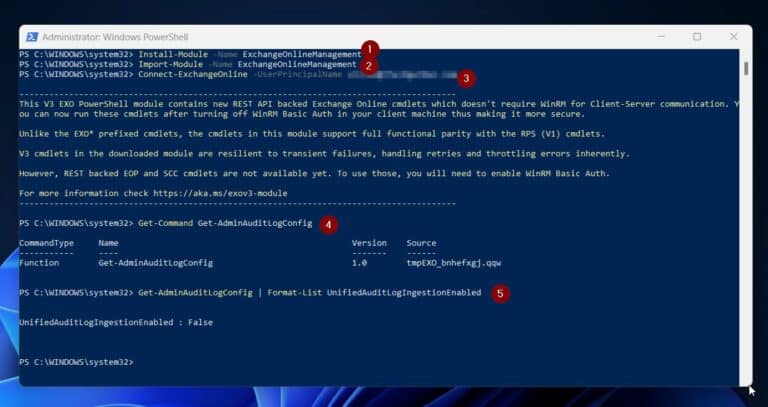
If the Get-AdminAuditLogConfig command returns the UnifiedAuditLogIngestionEnabled property as True, it indicates that unified auditing is turned on for your organization. If it returns a value of False , it means that auditing is not turned on.
So, from the result of my Get-AdminAuditLogConfig command, auditing is NOT turned, since the value is False. If this is your situation, proceed to the following section to enable auditing.
Try our Active Directory & Office 365 Reporting & Auditing Tools
Try us out for Free . 100’s of report templates available. Easily customise your own reports on AD, Azure AD & Office 355.
Also Read How to Check if MFA is Enabled in Office 365 for Users
Enable Office 365 Unified Audit Logs
Microsoft offers 2 methods to enable Office 365 audit logs to monitor user activity logs for improved organization security . Specifically, do this via the Compliance Portal or PowerShell .
Enable Auditing Using the Compliance Portal
1. Open- compliance.microsoft.com . 2. Navigate to the Solutions section and click Audit . Alternatively, open the Audit section directly by clicking compliance.microsoft.com/auditlogsearch .
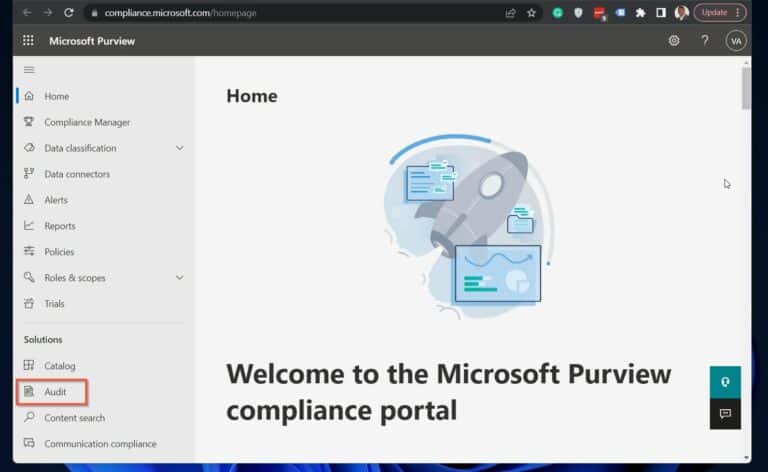
3. Finally, enable Microsoft 365 unified audit log, click “Start recording user and admin activity.”
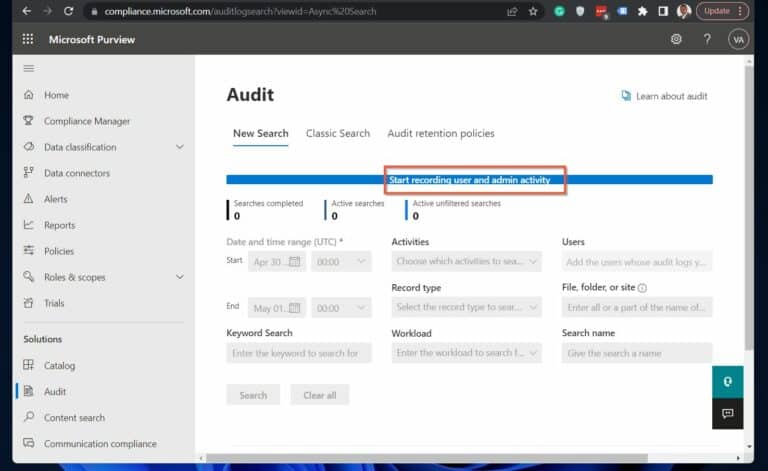
Please note that it may take up to 60 minutes for the change to take effect.
Also Read Deploy Office 365 Contact Reports
Enable Auditing Using Windows PowerShell
If you still have the PowerShell console, where you connected to the Exchange Online PowerShell module, run the command below to enable unified M365 auditing. You must run the first command before the second.
You may receive an error message, if you run the Set-AdminAuditLogConfig command without running the Enable-OrganizationCustomization command first.
Note that the Enable-OrganizationCustomization command takes a while to complete. Also, after enabling unified audit logging, may take up 60 mins to take effect.
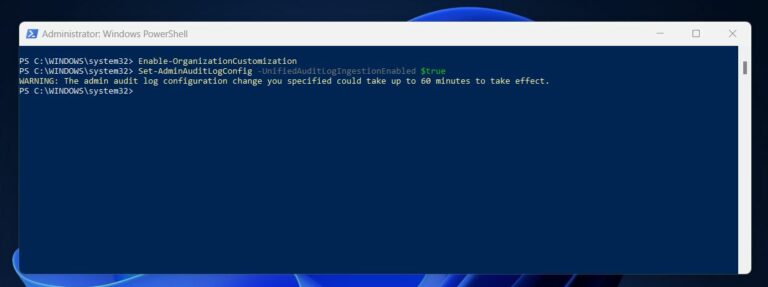
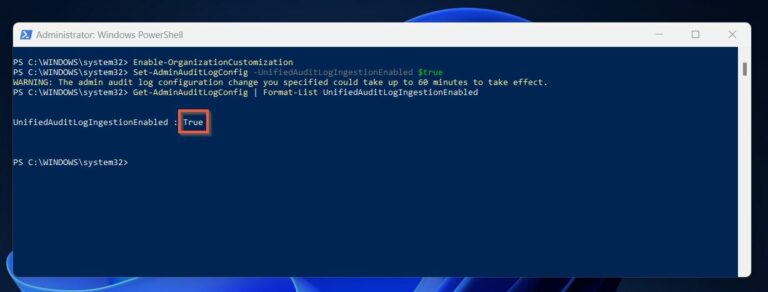
Then, re-run the Get-AdminAuditLogConfig command to confirm the audit login status.
If you successfully enabled auditing via the Compliance Portal or Windows PowerShell , the last command should return the UnifiedAuditLogIngestionEnabled as True. See the screenshot below.
Finally, you may turn off the unified audit login for your Microsoft 365 organization by running the command below.
Also Read Office 365 vs Exchange Online — What’s the Difference?
Search and Monitor Office 365 Audit Activity Logs for Improved Security
Let’s explore how to search it for relevant user and admin activities.
In this section, we show you how to run an audit log search and export the result to CSV . Additionally, we explain how you analyse the exported Office 365 Activity Logs for improved Security.
Also Read Check out Office 365 User Reports
Step 1 (Option 1 of 2):
Run an office 365 audit log search in the compliance portal.
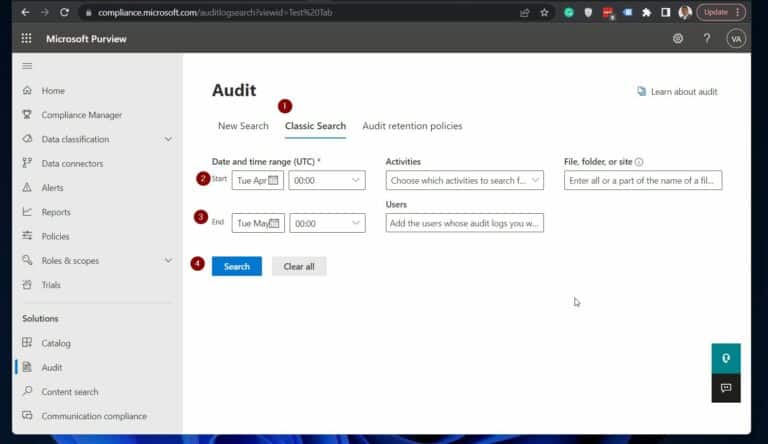
1. Open Microsoft Compliance Audit page compliance.microsoft.com/auditlogsearch . Then, set the search criteria following the numbering in the screenshot below:
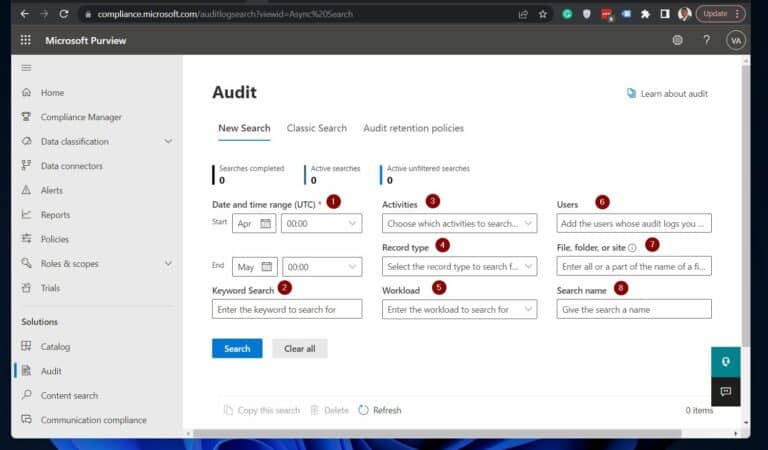
(1) Date and time range (UTC) : The audit search tool selects the last 7 days by default.
However, select your data range up to 90 days from the start date. Note that selecting more than 90 days returns an error message.
(2) Keyword Search : if you need the Office 365 unified audit tool to find logs about a word or phrase, enter it in this field.
(3) Activities : a drop-down with a long list of checkboxes.
(4) Record Type : search for specific record types like Azure Active Directory.
(5) Workload : To filter the search criteria by workload, click the drop down and check the Office 365 service from which you wish to view audit logs.
(6) Users : to filter the audit logs for specific users, use the search criterion to enter their names. If you leave the user field blank, the Compliance Portal search tool returns audit logs for all users across your Microsoft 365 services.
(7) Files, folders, or sites : search for activity related to a file or folder containing a specific keyword by typing some or all of its name. Also allows to specify a file’s or folder’s URL.
(8) Search name : give the search a name, then click Search. Finally, to view the status of the reports, click Refresh .
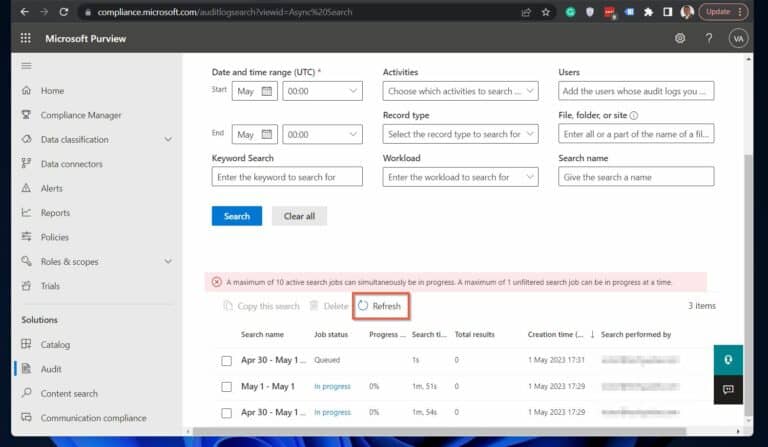
Also Read Get Members of Active Directory Group and Export to CSV using PowerShell
Step 1 (Option 2 of 2):
Run an office 365 audit log search using powershell.
Use PowerShell to perform Office 365 audit log searches. You do not need to use PowerShell if you have already used the Compliance Portal
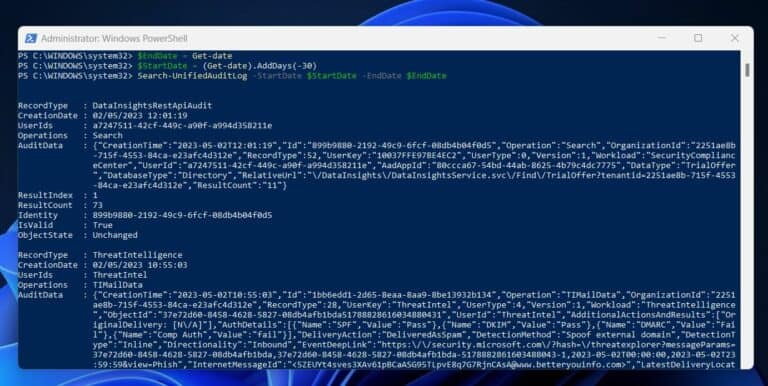
1. Connect to Exchange Online using PowerShell-by running the following commands in order:
2. Once connected to Exchange Online, run the Search-UnifiedAuditLog to search the Microsoft 365 unified audit log.
The StartDate and EndDate parameters are the only required parameters for this cmdlet. However, the cmdlet has other parameters.
The commands below search for all audit logs in the past 30 days.
The command returns audit log data for the date range you specify with the StartDat e and EndDate parameters. Note that the Start date must be earlier than the end date.
Also Read Check Azure AD Audit Logs for User Sign-Ins (Success Failures)
Step 2: View and Export the Office 365 Audit Activity Logs
Export the report to CSV from the Compliance Portal or via PowerShell.
Click on a report to export it from the Compliance Portal. Then, click the Export button.
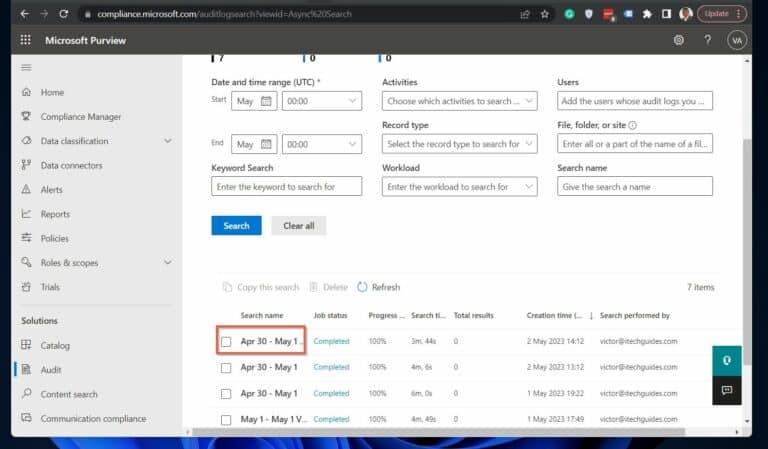
The New Search audit report yielded no results when we wrote this article in May 2023. I suspect that there was a bug with it.
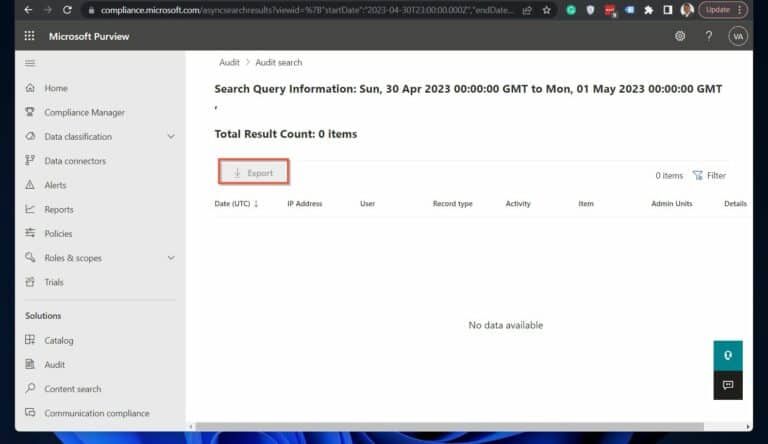
So, we used the Classic Search instead. Finally, to download the audit logs, click “Export,” then select “Download all results”
Alternatively, if you prefer to export the result of your Microsoft 365 unified audit log using PowerShell, use the script below.
The script includes some of the commands in the “ Step 1 (Option 2 of 2): Run an Office 365 Audit Log Search Using PowerShell “.
The script displays results on the PowerShell console and exports it to a CSV file.
Also Read How to Secure Azure AD Against Cyber Threats
Step 3: Analyze the 365 Activity Logs and Use them for Improved Security
Some organizations monitor Office 365 activity logs for improved security, while others do so for compliance purposes. After exporting M365 audit logs, the next step is to analyse them.
We included a sample report we exported using the above PowerShell script.
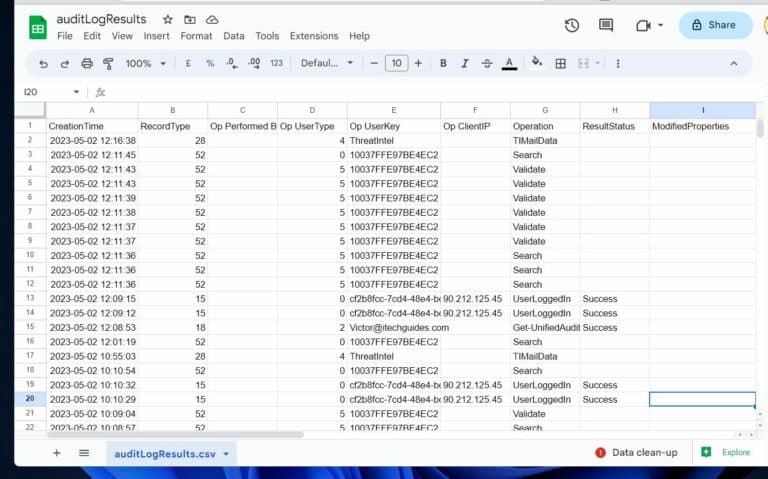
When using the report to improve security, look for patterns and potential actions that may lead to security breaches . Conversely, if you require the audit logs for compliance purposes, search for instances of compliance breaches.
Also Read Using Conditional Access Policies to Enhance Office 365 Security
How to Monitor Office 365 Activity Logs for Improved Security Conclusion
In conclusion, by monitoring Office 365 activity logs , you enhance security of your organization. Throughout this guide, we covered the following:
- An overview of the Office 365 Unified Audit Logging, including the Microsoft 365 services it supports.
- Microsoft 365 Audit Log licensing and permissions, which are necessary for monitoring Office 365 activity logs.
- The steps to check the current status of audit logging for your organization.
- The steps to enable Office 365 Unified Audit Logs via Compliance Portal and PowerShell .
- How to search and monitor the Office 365 audit activity logs, allowing you to use them to improve your organization’s security.
By following these steps, you stay on top of potential security breaches and protect your organization’s sensitive information.
Try InfraSOS for FREE
Invite your team and explore InfraSOS features for free
- Free 15-Days Trial
- SaaS Reporting & Auditing Solution
- Full Access to All Features
Related posts:
- How to Configure Azure AD Activity Logs for Effective Monitoring
- View Active Directory (AD) Event Logs and What They Track
- Check Azure AD Audit Logs for User Sign-Ins (Success Failures)
- Office 365 Compliance: Meet Security & Compliance Requirements
- Office 365 Identity & Access: Manage Users & Permissions
- Victor Ashiedu
- No Comments

Leave a comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
All about Microsoft 365
Automatic assignment of licenses via Auto-claim policies in Office 365
Microsoft has a long history of trying to drive increase for its cloud services usage at the expense of admin control. One of the most blatant examples was the attempt to roll out self-service purchase capabilities for the Power platform. After some customer uproar, a decision was made to delay the feature until admin controls are introduced, with a “request a license” feature introduced later on.
Now, another similar feature has been introduced as part of MC244882 , namely Auto-Claim Policies. Since nothing has changed in the effort put in naming those features, you’ll need to go over the description and additional information in order to make sense of what it is all about. In a nutshell, the feature offers an admin-configurable way to automatically assign licenses to users:
An auto-claim policy lets users automatically claim a license for a product the first time that they sign into an app. As an admin, you typically assign licenses to users either manually, or by using group-based licensing. By using auto-claim policies, you manage the products for which users can automatically claim licenses. You can also control which products those licenses come from.
In a rare example of showing that they can learn from past mistakes, Microsoft is releasing the feature in a default OFF state, meaning an admin will have to enable it first. To do so, you can login as a global admin and navigate to the M365 Admin Center > Settings > Org settings > Services > scroll down to User owned apps and services > toggle the value of Let users auto-claim licenses the first time they sign in . Alternatively, you can also enable the feature from it’s configuration page under M365 Admin Center > Billing > Licenses > Auto-claim policy . You cannot however toggle it off from said page.
Toggling the feature does nothing on its own, you will also need to configure one or more policies for the actual “claiming” or assignment of licenses. As Microsoft Teams is currently the only product that supports this feature, and policies are configured per product, currently you can only create a single policy. The creation process itself is fairly straightforward and driven by the familiar “wizard” interface.
Start by accessing the aforementioned configuration page by following the left nav menu or by directly opening this link , then press the Add a policy button. After giving the policy an appropriate Name , you will need to select which app or product the policy will apply to under the Policy details section. Again, currently the only choice is Microsoft Teams, so accordingly once you select the Microsoft Teams entry from the When a user signs in to this app dropbox, the list of SKUs containing a Teams service entry will be populated in the This policy will assign a license from this product dropbox.
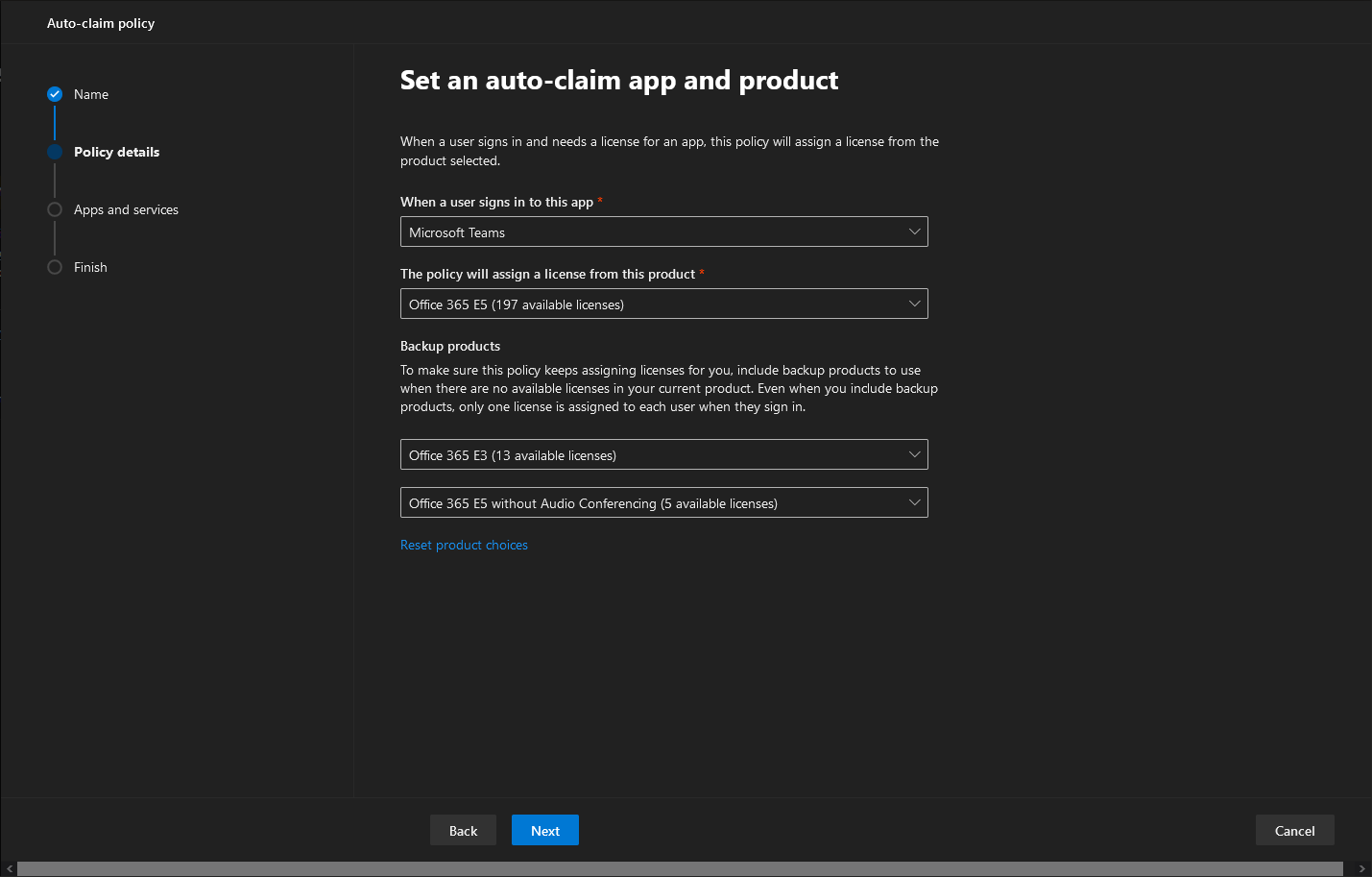
Once you are done with configuring the Policy details, hit the Next button to advance to the Apps and services page, where you can granularly control the set of individual services corresponding to a given SKU. Interestingly, in my case each of the selected (“primary” and “backup”) SKUs had the Exchange Online Plan 2 service unchecked, so make sure to double- and triple-check things. That’s probably my fault, as the user I’ve chosen already had a mailbox, so it was more of a corner case scenario. Some caution is advertised though, after all, you do need an Exchange mailbox for best Teams experience .
Once you are done with the individual services configuration, press the Next button again to progress to the Finish section of the wizard. Apart from getting a summary of the policy settings, on this page you can change the order of the SKUs from which the license will be assigned, but selecting the entry and clicking the Move up/Move down button as appropriate. If everything is set as desired, press the Finish button to complete the auto-claim policy creation process.
Do note that nowhere in the process we were asked to provide a list of users (or groups) to which the newly configured auto-claim policy will apply. In other words, auto-claim policies are tenant-wide and apply to all existing and newly created users within the tenancy (not Guests though!). While the feature itself might remind you of the good old Group-based licensing capabilities in Azure AD, the lack of granularity in this aspect is one of the main differences between the two. Of course, the use of the Group-based licensing feature is tied in to E3/Azure AD Premium, whereas auto-claim policies are available for free. Another one is that Group-based licenses are generally processed immediately (well, almost), whereas a license assigned by an auto-claim policy will only be “consumed” after the user logs in to a given app/service for the first time. Which I suppose is the reasoning for the unfortunate feature name…
Once the policy has been created, you will be able to see some information about it or change some of it settings by clicking the policy entry in the list. An option to Turn this policy on or off will be presented in the right-hand pane. In addition, selecting the policy entry will also surface some additional action items, such as the Delete button, a Refresh button and the Report button. Clicking the latter will take you to a new page where you can get some details about the usage of this feature. Details include the Name of the user (I would prefer something more appropriate such as the UserPrincipalName), the datetime at which the license was assigned, the license name and the policy that “acted”. A Download report button is available should you want to export this information to a CSV file, which sadly does not contain any additional details.
Finally, a few words about the end user experience. Once an auto-claim policy has been created, any user within the tenant will automatically get a license assigned to them once they login to Microsoft Teams. The process itself is transparent to the end user, which is both good an bad. Not having the user to worry about licensing requirements is of course helpful, however given the number of services available within Office 365/Microsoft 365 nowadays, it’s more than likely that organizations will want to provide some sort of training or onboarding experience. In the case of auto-claim policies, the end user is “in control” of when the actual license assignment happens, and they might get a bit overwhelmed by the number of apps/services they get access to after their attempt to login to Teams.
In any case, the feature seems like a step in the right direction, at least when we compare it to previous Microsoft attempts in this space. Being released as disabled by default and doing nothing until an admin with the appropriate permissions configures it is commendable and almost unexpected. Sure, the Global admin requirements seem to be a bit steep, but going forward they might be relaxed to something more appropriate. And of course, it will need to expand to cover additional apps and services to become a viable alternative to the group-based licensing feature. Some minor improvements in naming might also be a good idea, as might be controls to limit the scope of the feature to specific users/groups of users or plugging in an approval workflow. Additional information can be found in the official documentation.
4 thoughts on “ Automatic assignment of licenses via Auto-claim policies in Office 365 ”
Do you have a script or automatic way of Removing the license of the 365 user which is disabled & sync from On-premise AD i.e. once the sync user is disabled, all the licenses that is assigned to this disabled user in 365 should be automatically removed either via script or Automation using Azure Automation or Power Automate, etc.
Please suggest.
There are plenty such examples on the blog, i.e. https://www.michev.info/blog/post/3490/remove-all-office-365-licenses-for-a-group-of-users-from-csv-file-via-graph
- Pingback: Some more disconnects with managing users and groups in the Microsoft 365 Admin Center | Blog
- Pingback: [m365weekly] #27 - M365 Weekly Newsletter
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .

Contribute to the Microsoft 365 and Office forum! Click here to learn more 💡
April 9, 2024
Contribute to the Microsoft 365 and Office forum!
Click here to learn more 💡
- Search the community and support articles
- Microsoft 365 and Office
- Subscription, account, billing
- Search Community member
Ask a new question
Licenses got removed from a few users in my tenant but when I am searching for Audit Logs in security and compliance there are no logs present
Report abuse.
- Microsoft Agent |
Hello AnkushDeb,
What if you search directly via “Change User License” option? Please be kindly noted that do not use the impacted user account in “Users” action, for this field after refers to the user who performed the action:
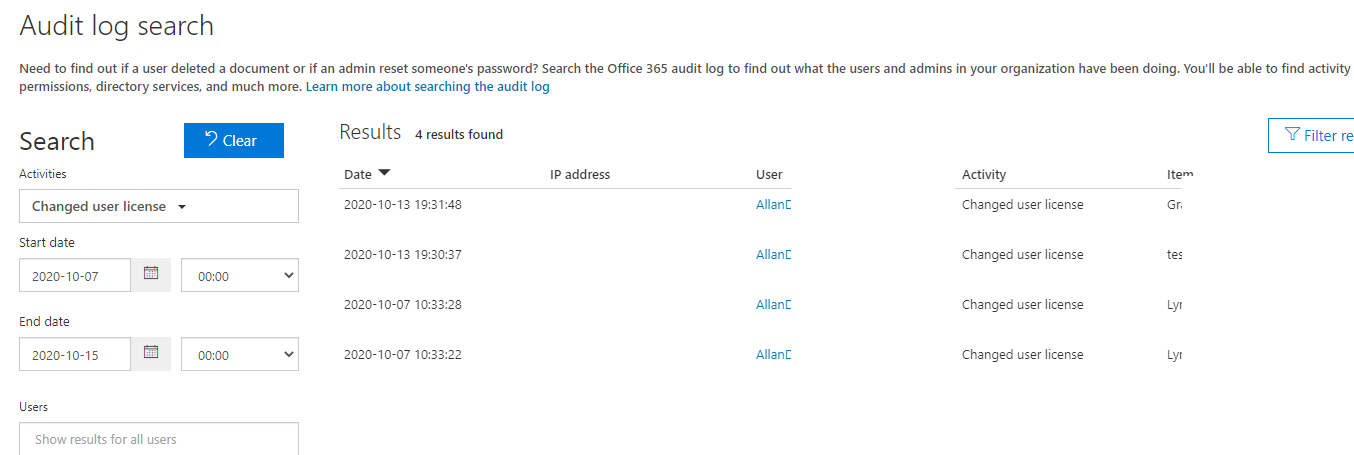
If above method can’t help, I recommend you use Exchange Online PowerShell to check it, like:
Search-UnifiedAuditLog -StartDate " 10/1/2020 8:00 AM " -EndDate " 10/1/2020 6:00 PM " -RecordType AzureActiveDirectory | Export-Csv -Append -Path c:\AuditLogs\PowerShellAuditlog.csv
If you still can’t find any related entry, there may be 2 scenarios, one is that there’s problem in Microsoft 365 Audit log, in this scenario, I think it’s better to use an account to assign and unassign license for test and check if issue persists, you can also confirm this by Azure Audit logs . Another scenario is that there’s no one removed users’ license, this scenario may be more complicated and need to further consult, for it should be caused by other factors deeper inside.
Best Regards,
Was this reply helpful? Yes No
Sorry this didn't help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
Thanks for your feedback.
Replies (3)
Question info.
- Norsk Bokmål
- Ελληνικά
- Русский
- עברית
- العربية
- ไทย
- 한국어
- 中文(简体)
- 中文(繁體)
- 日本語

IMAGES
VIDEO
COMMENTS
Here is Search the audit log in the Office 365 Security & Compliance Cente r for your reference. Besides, if the issue occurs again, I would like to collect following information: 1.Are these users Online users or local AD users? 2.What licenses do they have before these license lost? Regards, Eli
For users assigned an Office 365 E5 or Microsoft 365 E5 license (or users with a Microsoft 365 E5 Compliance or Microsoft 365 E5 eDiscovery and Audit add-on license), audit records for Microsoft Entra ID, Exchange, and SharePoint activity are retained for one year by default. ... If you want to programmatically download data from the audit log ...
This is a quick video to show how you can check user license changes record in Audit log. Microsoft 365 Compliance URL -https://compliance.microsoft.com/audi...
To search for text in the logs run the following command : Search-UnifiedAuditLog -StartDate 10/1/2021 -EndDate 10/04/2021 -FreeText "baseball". The log below returns result with text of "baseball" highlighted below. Limits: The ResultSize parameter specifies the maximum number of results to return.
Step 3: Export the search results to a file. . Run an audit log search, and then revise the search criteria until you have the desired results. On the search results page, select "Export > Download all results". All entries from the audit log that meet the search criteria are exported to a CSV file.
To upgrade the report to handle group-based licensing, the script that analyzes license data checks the licenseAssignmentStates array returned by the Get-MgUser cmdlet. When a group-based assignment exists, the array holds information about the assigning group and the product identifier. An entry in the array is present for each product license ...
We're looking for the ability to sort out WHO has assigned specific licenses within O365. We have someone who is direct assigning licenses rather than using our configured Azure AD groups, and would like to figure out how that individual is. ... I tried to assign a license to an account in my testbed - I can see the license being assigned under ...
How to get to the Reports dashboard. In the admin center, go to the Reports > Usage page. In the admin center, go to the Reports > Usage page. Select the View more button from the at-a-glance activity card for a service (such as email or OneDrive) to see the report detail page. On that page, different reports for the service are provided in tabs.
The audit events generated for license assignments to user accounts available in the Azure AD audit log and Office 365 audit log are inconsistent and incomplete. Subscribe for Practical 365 updates ... if you assign a new SKU with some of the service plans disabled, changing an existing license assignment or removing a license from an account ...
The problem is that the audit log is only available for Office 365 E3 licenses (and above) and audit events are only available for 90 days (Office 365 E3) or 365 days (Office 365 E5). Many organizations get around this problem by offloading audit data to a SIEM like Splunk or Microsoft Sentinel. Various Methods Exist, All Flawed
Step 2: View and Export the Office 365 Audit Activity Logs. Export the report to CSV from the Compliance Portal or via PowerShell. Click on a report to export it from the Compliance Portal. Then, click the Export button. The New Search audit report yielded no results when we wrote this article in May 2023.
In a nutshell, the feature offers an admin-configurable way to automatically assign licenses to users: An auto-claim policy lets users automatically claim a license for a product the first time that they sign into an app. As an admin, you typically assign licenses to users either manually, or by using group-based licensing.
6 Spice ups. user827215 (CMD88) January 28, 2022, 7:47am 2. You should be able to use the audit log feature in Azure Active Directory to track licensing changes. That said, you really, really need to set up separate logins for you and the helpdesk contact. Ideally with using PIM to give just-in-time access too.
If you still can't find any related entry, there may be 2 scenarios, one is that there's problem in Microsoft 365 Audit log, in this scenario, I think it's better to use an account to assign and unassign license for test and check if issue persists, you can also confirm this by Azure Audit logs . Another scenario is that there's no one ...