For enquiries call:
+1-469-442-0620


60+ Latest Cyber Security Research Topics for 2024
Home Blog Security 60+ Latest Cyber Security Research Topics for 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics /ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security research questions, cyber security topics for the project, best cyber security research topics, research titles about cyber security and web security research topics.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics for 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A) Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B) Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C) Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D) Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E) Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F) Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G) Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H) Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I) Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J) Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
- Privacy Policy
Buy Me a Coffee

Home » 500+ Cyber Security Research Topics
500+ Cyber Security Research Topics

Cybersecurity has become an increasingly important topic in recent years as more and more of our lives are spent online. With the rise of the digital age, there has been a corresponding increase in the number and severity of cyber attacks. As such, research into cybersecurity has become critical in order to protect individuals, businesses, and governments from these threats. In this blog post, we will explore some of the most pressing cybersecurity research topics, from the latest trends in cyber attacks to emerging technologies that can help prevent them. Whether you are a cybersecurity professional, a Master’s or Ph.D. student, or simply interested in the field, this post will provide valuable insights into the challenges and opportunities in this rapidly evolving area of study.
Cyber Security Research Topics
Cyber Security Research Topics are as follows:
- The role of machine learning in detecting cyber threats
- The impact of cloud computing on cyber security
- Cyber warfare and its effects on national security
- The rise of ransomware attacks and their prevention methods
- Evaluating the effectiveness of network intrusion detection systems
- The use of blockchain technology in enhancing cyber security
- Investigating the role of cyber security in protecting critical infrastructure
- The ethics of hacking and its implications for cyber security professionals
- Developing a secure software development lifecycle (SSDLC)
- The role of artificial intelligence in cyber security
- Evaluating the effectiveness of multi-factor authentication
- Investigating the impact of social engineering on cyber security
- The role of cyber insurance in mitigating cyber risks
- Developing secure IoT (Internet of Things) systems
- Investigating the challenges of cyber security in the healthcare industry
- Evaluating the effectiveness of penetration testing
- Investigating the impact of big data on cyber security
- The role of quantum computing in breaking current encryption methods
- Developing a secure BYOD (Bring Your Own Device) policy
- The impact of cyber security breaches on a company’s reputation
- The role of cyber security in protecting financial transactions
- Evaluating the effectiveness of anti-virus software
- The use of biometrics in enhancing cyber security
- Investigating the impact of cyber security on the supply chain
- The role of cyber security in protecting personal privacy
- Developing a secure cloud storage system
- Evaluating the effectiveness of firewall technologies
- Investigating the impact of cyber security on e-commerce
- The role of cyber security in protecting intellectual property
- Developing a secure remote access policy
- Investigating the challenges of securing mobile devices
- The role of cyber security in protecting government agencies
- Evaluating the effectiveness of cyber security training programs
- Investigating the impact of cyber security on the aviation industry
- The role of cyber security in protecting online gaming platforms
- Developing a secure password management system
- Investigating the challenges of securing smart homes
- The impact of cyber security on the automotive industry
- The role of cyber security in protecting social media platforms
- Developing a secure email system
- Evaluating the effectiveness of encryption methods
- Investigating the impact of cyber security on the hospitality industry
- The role of cyber security in protecting online education platforms
- Developing a secure backup and recovery strategy
- Investigating the challenges of securing virtual environments
- The impact of cyber security on the energy sector
- The role of cyber security in protecting online voting systems
- Developing a secure chat platform
- Investigating the impact of cyber security on the entertainment industry
- The role of cyber security in protecting online dating platforms
- Artificial Intelligence and Machine Learning in Cybersecurity
- Quantum Cryptography and Post-Quantum Cryptography
- Internet of Things (IoT) Security
- Developing a framework for cyber resilience in critical infrastructure
- Understanding the fundamentals of encryption algorithms
- Cyber security challenges for small and medium-sized businesses
- Developing secure coding practices for web applications
- Investigating the role of cyber security in protecting online privacy
- Network security protocols and their importance
- Social engineering attacks and how to prevent them
- Investigating the challenges of securing personal devices and home networks
- Developing a basic incident response plan for cyber attacks
- The impact of cyber security on the financial sector
- Understanding the role of cyber security in protecting critical infrastructure
- Mobile device security and common vulnerabilities
- Investigating the challenges of securing cloud-based systems
- Cyber security and the Internet of Things (IoT)
- Biometric authentication and its role in cyber security
- Developing secure communication protocols for online messaging platforms
- The importance of cyber security in e-commerce
- Understanding the threats and vulnerabilities associated with social media platforms
- Investigating the role of cyber security in protecting intellectual property
- The basics of malware analysis and detection
- Developing a basic cyber security awareness training program
- Understanding the threats and vulnerabilities associated with public Wi-Fi networks
- Investigating the challenges of securing online banking systems
- The importance of password management and best practices
- Cyber security and cloud computing
- Understanding the role of cyber security in protecting national security
- Investigating the challenges of securing online gaming platforms
- The basics of cyber threat intelligence
- Developing secure authentication mechanisms for online services
- The impact of cyber security on the healthcare sector
- Understanding the basics of digital forensics
- Investigating the challenges of securing smart home devices
- The role of cyber security in protecting against cyberbullying
- Developing secure file transfer protocols for sensitive information
- Understanding the challenges of securing remote work environments
- Investigating the role of cyber security in protecting against identity theft
- The basics of network intrusion detection and prevention systems
- Developing secure payment processing systems
- Understanding the role of cyber security in protecting against ransomware attacks
- Investigating the challenges of securing public transportation systems
- The basics of network segmentation and its importance in cyber security
- Developing secure user access management systems
- Understanding the challenges of securing supply chain networks
- The role of cyber security in protecting against cyber espionage
- Investigating the challenges of securing online educational platforms
- The importance of data backup and disaster recovery planning
- Developing secure email communication protocols
- Understanding the basics of threat modeling and risk assessment
- Investigating the challenges of securing online voting systems
- The role of cyber security in protecting against cyber terrorism
- Developing secure remote access protocols for corporate networks.
- Investigating the challenges of securing artificial intelligence systems
- The role of machine learning in enhancing cyber threat intelligence
- Evaluating the effectiveness of deception technologies in cyber security
- Investigating the impact of cyber security on the adoption of emerging technologies
- The role of cyber security in protecting smart cities
- Developing a risk-based approach to cyber security governance
- Investigating the impact of cyber security on economic growth and innovation
- The role of cyber security in protecting human rights in the digital age
- Developing a secure digital identity system
- Investigating the impact of cyber security on global political stability
- The role of cyber security in protecting the Internet of Things (IoT)
- Developing a secure supply chain management system
- Investigating the challenges of securing cloud-native applications
- The role of cyber security in protecting against insider threats
- Developing a secure software-defined network (SDN)
- Investigating the impact of cyber security on the adoption of mobile payments
- The role of cyber security in protecting against cyber warfare
- Developing a secure distributed ledger technology (DLT) system
- Investigating the impact of cyber security on the digital divide
- The role of cyber security in protecting against state-sponsored attacks
- Developing a secure Internet infrastructure
- Investigating the challenges of securing industrial control systems (ICS)
- Developing a secure quantum communication system
- Investigating the impact of cyber security on global trade and commerce
- Developing a secure decentralized authentication system
- Investigating the challenges of securing edge computing systems
- Developing a secure hybrid cloud system
- Investigating the impact of cyber security on the adoption of smart cities
- The role of cyber security in protecting against cyber propaganda
- Developing a secure blockchain-based voting system
- Investigating the challenges of securing cyber-physical systems (CPS)
- The role of cyber security in protecting against cyber hate speech
- Developing a secure machine learning system
- Investigating the impact of cyber security on the adoption of autonomous vehicles
- The role of cyber security in protecting against cyber stalking
- Developing a secure data-driven decision-making system
- Investigating the challenges of securing social media platforms
- The role of cyber security in protecting against cyberbullying in schools
- Developing a secure open source software ecosystem
- Investigating the impact of cyber security on the adoption of smart homes
- The role of cyber security in protecting against cyber fraud
- Developing a secure software supply chain
- Investigating the challenges of securing cloud-based healthcare systems
- The role of cyber security in protecting against cyber harassment
- Developing a secure multi-party computation system
- Investigating the impact of cyber security on the adoption of virtual and augmented reality technologies.
- Cybersecurity in Cloud Computing Environments
- Cyber Threat Intelligence and Analysis
- Blockchain Security
- Data Privacy and Protection
- Cybersecurity in Industrial Control Systems
- Mobile Device Security
- The importance of cyber security in the digital age
- The ethics of cyber security and privacy
- The role of government in regulating cyber security
- Cyber security threats and vulnerabilities in the healthcare sector
- Understanding the risks associated with social media and cyber security
- The impact of cyber security on e-commerce
- The effectiveness of cyber security awareness training programs
- The role of biometric authentication in cyber security
- The importance of password management in cyber security
- The basics of network security protocols and their importance
- The challenges of securing online gaming platforms
- The role of cyber security in protecting national security
- The impact of cyber security on the legal sector
- The ethics of cyber warfare
- The challenges of securing the Internet of Things (IoT)
- Understanding the basics of malware analysis and detection
- The challenges of securing public transportation systems
- The impact of cyber security on the insurance industry
- The role of cyber security in protecting against ransomware attacks
- The challenges of securing remote work environments
- Understanding the threats and vulnerabilities associated with social engineering attacks
- The impact of cyber security on the education sector
- Investigating the challenges of securing supply chain networks
- The challenges of securing personal devices and home networks
- The importance of secure coding practices for web applications
- The impact of cyber security on the hospitality industry
- The role of cyber security in protecting against identity theft
- The challenges of securing public Wi-Fi networks
- The importance of cyber security in protecting critical infrastructure
- The challenges of securing cloud-based storage systems
- The effectiveness of antivirus software in cyber security
- Developing secure payment processing systems.
- Cybersecurity in Healthcare
- Social Engineering and Phishing Attacks
- Cybersecurity in Autonomous Vehicles
- Cybersecurity in Smart Cities
- Cybersecurity Risk Assessment and Management
- Malware Analysis and Detection Techniques
- Cybersecurity in the Financial Sector
- Cybersecurity in Government Agencies
- Cybersecurity and Artificial Life
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity in the Education Sector
- Cybersecurity in Virtual Reality and Augmented Reality
- Cybersecurity in the Retail Industry
- Cryptocurrency Security
- Cybersecurity in Supply Chain Management
- Cybersecurity and Human Factors
- Cybersecurity in the Transportation Industry
- Cybersecurity in Gaming Environments
- Cybersecurity in Social Media Platforms
- Cybersecurity and Biometrics
- Cybersecurity and Quantum Computing
- Cybersecurity in 5G Networks
- Cybersecurity in Aviation and Aerospace Industry
- Cybersecurity in Agriculture Industry
- Cybersecurity in Space Exploration
- Cybersecurity in Military Operations
- Cybersecurity and Cloud Storage
- Cybersecurity in Software-Defined Networks
- Cybersecurity and Artificial Intelligence Ethics
- Cybersecurity and Cyber Insurance
- Cybersecurity in the Legal Industry
- Cybersecurity and Data Science
- Cybersecurity in Energy Systems
- Cybersecurity in E-commerce
- Cybersecurity in Identity Management
- Cybersecurity in Small and Medium Enterprises
- Cybersecurity in the Entertainment Industry
- Cybersecurity and the Internet of Medical Things
- Cybersecurity and the Dark Web
- Cybersecurity and Wearable Technology
- Cybersecurity in Public Safety Systems.
- Threat Intelligence for Industrial Control Systems
- Privacy Preservation in Cloud Computing
- Network Security for Critical Infrastructure
- Cryptographic Techniques for Blockchain Security
- Malware Detection and Analysis
- Cyber Threat Hunting Techniques
- Cybersecurity Risk Assessment
- Machine Learning for Cybersecurity
- Cybersecurity in Financial Institutions
- Cybersecurity for Smart Cities
- Cybersecurity in Aviation
- Cybersecurity in the Automotive Industry
- Cybersecurity in the Energy Sector
- Cybersecurity in Telecommunications
- Cybersecurity for Mobile Devices
- Biometric Authentication for Cybersecurity
- Cybersecurity for Artificial Intelligence
- Cybersecurity for Social Media Platforms
- Cybersecurity in the Gaming Industry
- Cybersecurity in the Defense Industry
- Cybersecurity for Autonomous Systems
- Cybersecurity for Quantum Computing
- Cybersecurity for Augmented Reality and Virtual Reality
- Cybersecurity in Cloud-Native Applications
- Cybersecurity for Smart Grids
- Cybersecurity in Distributed Ledger Technology
- Cybersecurity for Next-Generation Wireless Networks
- Cybersecurity for Digital Identity Management
- Cybersecurity for Open Source Software
- Cybersecurity for Smart Homes
- Cybersecurity for Smart Transportation Systems
- Cybersecurity for Cyber Physical Systems
- Cybersecurity for Critical National Infrastructure
- Cybersecurity for Smart Agriculture
- Cybersecurity for Retail Industry
- Cybersecurity for Digital Twins
- Cybersecurity for Quantum Key Distribution
- Cybersecurity for Digital Healthcare
- Cybersecurity for Smart Logistics
- Cybersecurity for Wearable Devices
- Cybersecurity for Edge Computing
- Cybersecurity for Cognitive Computing
- Cybersecurity for Industrial IoT
- Cybersecurity for Intelligent Transportation Systems
- Cybersecurity for Smart Water Management Systems
- The rise of cyber terrorism and its impact on national security
- The impact of artificial intelligence on cyber security
- Analyzing the effectiveness of biometric authentication for securing data
- The impact of social media on cyber security and privacy
- The future of cyber security in the Internet of Things (IoT) era
- The role of machine learning in detecting and preventing cyber attacks
- The effectiveness of encryption in securing sensitive data
- The impact of quantum computing on cyber security
- The rise of cyber bullying and its effects on mental health
- Investigating cyber espionage and its impact on national security
- The effectiveness of cyber insurance in mitigating cyber risks
- The role of blockchain technology in cyber security
- Investigating the effectiveness of cyber security awareness training programs
- The impact of cyber attacks on critical infrastructure
- Analyzing the effectiveness of firewalls in protecting against cyber attacks
- The impact of cyber crime on the economy
- Investigating the effectiveness of multi-factor authentication in securing data
- The future of cyber security in the age of quantum internet
- The impact of big data on cyber security
- The role of cybersecurity in the education system
- Investigating the use of deception techniques in cyber security
- The impact of cyber attacks on the healthcare industry
- The effectiveness of cyber threat intelligence in mitigating cyber risks
- The role of cyber security in protecting financial institutions
- Investigating the use of machine learning in cyber security risk assessment
- The impact of cyber attacks on the transportation industry
- The effectiveness of network segmentation in protecting against cyber attacks
- Investigating the effectiveness of biometric identification in cyber security
- The impact of cyber attacks on the hospitality industry
- The future of cyber security in the era of autonomous vehicles
- The effectiveness of intrusion detection systems in protecting against cyber attacks
- The role of cyber security in protecting small businesses
- Investigating the effectiveness of virtual private networks (VPNs) in securing data
- The impact of cyber attacks on the energy sector
- The effectiveness of cyber security regulations in mitigating cyber risks
- Investigating the use of deception technology in cyber security
- The impact of cyber attacks on the retail industry
- The effectiveness of cyber security in protecting critical infrastructure
- The role of cyber security in protecting intellectual property in the entertainment industry
- Investigating the effectiveness of intrusion prevention systems in protecting against cyber attacks
- The impact of cyber attacks on the aerospace industry
- The future of cyber security in the era of quantum computing
- The effectiveness of cyber security in protecting against ransomware attacks
- The role of cyber security in protecting personal and sensitive data
- Investigating the effectiveness of cloud security solutions in protecting against cyber attacks
- The impact of cyber attacks on the manufacturing industry
- The effective cyber security and the future of e-votingness of cyber security in protecting against social engineering attacks
- Investigating the effectiveness of end-to-end encryption in securing data
- The impact of cyber attacks on the insurance industry
- The future of cyber security in the era of artificial intelligence
- The effectiveness of cyber security in protecting against distributed denial-of-service (DDoS) attacks
- The role of cyber security in protecting against phishing attacks
- Investigating the effectiveness of user behavior analytics
- The impact of emerging technologies on cyber security
- Developing a framework for cyber threat intelligence
- The effectiveness of current cyber security measures
- Cyber security and data privacy in the age of big data
- Cloud security and virtualization technologies
- Cryptography and its role in cyber security
- Cyber security in critical infrastructure protection
- Cyber security in the Internet of Things (IoT)
- Cyber security in e-commerce and online payment systems
- Cyber security and the future of digital currencies
- The impact of social engineering on cyber security
- Cyber security and ethical hacking
- Cyber security challenges in the healthcare industry
- Cyber security and digital forensics
- Cyber security in the financial sector
- Cyber security in the transportation industry
- The impact of artificial intelligence on cyber security risks
- Cyber security and mobile devices
- Cyber security in the energy sector
- Cyber security and supply chain management
- The role of machine learning in cyber security
- Cyber security in the defense sector
- The impact of the Dark Web on cyber security
- Cyber security in social media and online communities
- Cyber security challenges in the gaming industry
- Cyber security and cloud-based applications
- The role of blockchain in cyber security
- Cyber security and the future of autonomous vehicles
- Cyber security in the education sector
- Cyber security in the aviation industry
- The impact of 5G on cyber security
- Cyber security and insider threats
- Cyber security and the legal system
- The impact of cyber security on business operations
- Cyber security and the role of human behavior
- Cyber security in the hospitality industry
- The impact of cyber security on national security
- Cyber security and the use of biometrics
- Cyber security and the role of social media influencers
- The impact of cyber security on small and medium-sized enterprises
- Cyber security and cyber insurance
- The impact of cyber security on the job market
- Cyber security and international relations
- Cyber security and the role of government policies
- The impact of cyber security on privacy laws
- Cyber security in the media and entertainment industry
- The role of cyber security in digital marketing
- Cyber security and the role of cybersecurity professionals
- Cyber security in the retail industry
- The impact of cyber security on the stock market
- Cyber security and intellectual property protection
- Cyber security and online dating
- The impact of cyber security on healthcare innovation
- Cyber security and the future of e-voting
- Cyber security and the role of open source software
- Cyber security and the use of social engineering in cyber attacks
- The impact of cyber security on the aviation industry
- Cyber security and the role of cyber security awareness training
- Cyber security and the role of cybersecurity standards and best practices
- Cyber security in the legal industry
- The impact of cyber security on human rights
- Cyber security and the role of public-private partnerships
- Cyber security and the future of e-learning
- Cyber security and the role of mobile applications
- The impact of cyber security on environmental sustainability
- Cyber security and the role of threat intelligence sharing
- Cyber security and the future of smart homes
- Cyber security and the role of cybersecurity certifications
- The impact of cyber security on international trade
- Cyber security and the role of cyber security auditing
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics

500+ Physics Research Topics

500+ Google Scholar Research Topics
List of 78 Top Cyber Security Topics for Research
Table of contents
- 1 How To Choose The Best Cyber Security Research Topics
- 2 📚10 Cyber Security Topics For Research Paper
- 3 📱Mobile Cyber Security Research Paper Topics
- 4 🕵Top 10 Cyber Security Topics
- 5 👨💻Cyber Security Research Topics 2023
- 6 🔎Best Cyber Security Research Topics
- 7 👨🔬Cyber Security Future Research Topics
- 8 📑Cyber Security Topics For Research Paper
- 9 👩💻Cyber Security Topics on Computer and Software
There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and discuss. Second, cyber security research can be used to improve the security of your own computer systems. By understanding the latest threats and vulnerabilities, you can make your systems more secure and less likely to be compromised. Third, writing about cyber security can help raise awareness about the importance of cyber security. By educating others about the dangers of cyber attacks and the importance of protecting their computers, you can help make the internet a safer place for everyone.
How To Choose The Best Cyber Security Research Topics
When it comes to choosing research paper topics on cyber security, there are a few things to consider. First, it is important to make sure that the topic is relevant and timely. Cyber security is an ever-changing field, so it is important to choose a topic that will be relevant for years to come. Second, it is important to choose a topic that is interesting and engaging. Cybersecurity can be a dry topic, so it is important to choose a topic that will keep readers engaged. Finally, it is important to choose a topic that is researchable. There are a lot of cyber security topics out there, but not all of them are easy to research. Make sure to choose a topic that has plenty of information available.
- Identify your audience.
- Define your research goals.
- Choose a topic that is both interesting and relevant to your audience.
- Do some preliminary research to make sure there is enough information available on your chosen topic.
- Make sure your topic is narrow enough to be covered in a single research paper.
📚10 Cyber Security Topics For Research Paper
- The Importance of Cyber Security
- The Evolution of Cyber Security
- The Future of Cyber Security
- The Impact of Cyber Security on Business
- The Role of Cyber Security in National Security
- The Challenges of Cyber Security
- The Costs of Cyber Security
- The Benefits of Cyber Security
- The Risks of Cyber Security
- The Implications of Cyber Security
📱Mobile Cyber Security Research Paper Topics
- Mobile device security: How to protect your mobile device from cyber attacks.
- The rise of mobile malware: How to protect your device from malicious software.
- Mobile phishing attacks: How to protect your device from being scammed.
- The dangers of public Wi-Fi: How to protect your device from being hacked.
- How to keep your data safe on your mobile device: Tips for keeping your personal information secure.
🕵Top 10 Cyber Security Topics
- Cybersecurity threats and attacks
- Cybersecurity risks and vulnerabilities
- Cybersecurity best practices
- Cybersecurity awareness and training
- Cybersecurity tools and technologies
- Cybersecurity policy and compliance
- Cybersecurity incident response
- Cybersecurity governance
- Cybersecurity risk management
- Cybersecurity strategy
👨💻Cyber Security Research Topics 2023
- The future of cyber security: what trends will shape the field in the coming years?
- The impact of AI and machine learning on cyber security
- The role of quantum computing in cyber security
- The challenges of securing the IoT
- The evolving threat landscape: what new threats are emerging and how can we defend against them?
- The role of data in cyber security: how can we better protect our data?
- The importance of user education in cyber security
- The challenges of securing mobile devices
- The future of cyber warfare: what trends are emerging?
- The role of cryptography in cyber security
🔎Best Cyber Security Research Topics
- The Impact of Cybersecurity on Businesses and Consumers
- The Evolution of Cybersecurity Threats and Attacks
- The Role of Cybersecurity in National Security
- The Economics of Cybersecurity
- The Psychology of Cybersecurity
- The Sociology of Cybersecurity
- The Ethics of Cybersecurity
- The History of Cybersecurity
- Cybersecurity threats and attacks.
- Cybersecurity policies and procedures.
- Cybersecurity awareness and training.
- Cybersecurity technologies and solutions.
- Cybersecurity risk management.
- Cybersecurity incident response.
- Cybersecurity governance.
- Cybersecurity compliance.
- Cybersecurity standards.
- Cybersecurity best practices.
👨🔬Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
📑Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities.
- Cyber security incident response and management.
- Cyber security risk management.
- Cyber security awareness and training.
- Cyber security controls and countermeasures.
- Cyber security governance.
- Cyber security standards.
- Cyber security insurance.
- Cyber security and the law.
- The future of cyber security.
👩💻Cyber Security Topics on Computer and Software
- Cyber security risks associated with computer software
- The importance of keeping computer software up to date
- How to protect your computer from malware and other threats
- The best practices for securing your computer and software
- The different types of cyber security threats and how to avoid them
- The importance of cyber security awareness and education
- The role of cyber security in protecting critical infrastructure
Readers also enjoyed

WHY WAIT? PLACE AN ORDER RIGHT NOW!
Just fill out the form, press the button, and have no worries!
We use cookies to give you the best experience possible. By continuing we’ll assume you board with our cookie policy.
- How It Works
- PhD thesis writing
- Master thesis writing
- Bachelor thesis writing
- Dissertation writing service
- Dissertation abstract writing
- Thesis proposal writing
- Thesis editing service
- Thesis proofreading service
- Thesis formatting service
- Coursework writing service
- Research paper writing service
- Architecture thesis writing
- Computer science thesis writing
- Engineering thesis writing
- History thesis writing
- MBA thesis writing
- Nursing dissertation writing
- Psychology dissertation writing
- Sociology thesis writing
- Statistics dissertation writing
- Buy dissertation online
- Write my dissertation
- Cheap thesis
- Cheap dissertation
- Custom dissertation
- Dissertation help
- Pay for thesis
- Pay for dissertation
- Senior thesis
- Write my thesis
128 High Quality Cybersecurity Research Topics Ideas List

The internet is a global village full of different people. Some people have malicious motives. Once they stumble upon your sensitive data, they will use it to harass you. This also occurs in social media accounts. You may post something and then get some bad or hurtful comments.
That’s a form of cyberbullying that is not acceptable. Therefore, you need to be careful when dealing with people on the internet. Also, try to reduce the data that you expose on your different user profiles. A person may even steal your online identity in a blink of an eye.
Case Situations To Write Cybersecurity Research Paper
Thereby cybersecurity comes in with the motive of defending computers, servers, mobiles, electronic systems, networks, and much more from those malicious attacks. You may need to write a cybersecurity research paper for:
Your final paper, project, thesis, or dissertation. When you are proposing a new strategy to use in your company to prevent cyber-attacks. When you want to bring into light some vulnerabilities being ignored. When you want to do more research and get a better understanding of harassment on the internet.
How To Write Cybersecurity Research Paper
This is the procedure you can use when writing a research paper.
Consult your professor – You will first need to get insights from your professor or teacher on the best way to go about it. You can provide a list of topics you may want to write on for his approval. Brainstorm – Discuss with some like-minded people the best cybersecurity topics to try. You need to be careful to ensure that you choose a topic that you can easily do. Research – Once you settle on a good topic, you can start your research on books, scholarly articles, documentaries, and films to get legit information on your cybersecurity research topic. Jot them down as a draft. Start your paper – Once you are settled with the research, you can use your draft to write a viable research paper. Ensure you follow the right procedure. Proofread the work – Once you are satisfied with your work, consider proofreading it before submitting it.
If you don’t feel like writing research paper yourself, you can get cheap dissertation help from our experts.
Cybersecurity Research Topics
When in high school or college, you need to strive to get good grades. You can use any of these cybersecurity research topics for your paper. Just ensure to do enough research on the concepts.
- The significance of a firewall in the protection of the network.
- Discuss the process of authentication.
- The loss and restoration of data.
- The best data encryption algorithms.
- The best methods to protect your network.
- Evaluate digital piracy and security.
- The significance of social engineering.
- The significance of software updates in devices.
- The major causes of cybersecurity.
- The safety of biometrics.
- The worst cases of IoT hacking.
Cybersecurity Research Paper Topics
Cybersecurity is wide and inexhaustible. Each day, cybercrime are occurring, leading to research on better ways to protect ourselves online. You can use any of these topics for your research paper or project.
- The advantages and disadvantages of unified user profiles.
- The relation between bots and cybersecurity.
- The major cybersecurity vulnerabilities.
- Evaluate digital piracy and its effects on creativity.
- How has automotive hacking grown over the years?
- Evaluate ethical hacking.
- Evolution of phishing over time.
- The best antivirus software currently being used.
- The trends in cybersecurity technology.
- How biometrics is helping in cybersecurity?
- The occurrence of cybersecurity in spoofing.
Cybersecurity Research Topics For Research Papers
Are you in the IT profession? Have you done your project yet? Then you can consider using any of these cybersecurity research topics. They are all ideal and based on current matters.
- The rise of identity theft on the internet.
- Why are more people getting into computer forensics?
- The major threats found using digital forensic techniques.
- The best VPNs in the world that will hide your IP on the internet.
- The disadvantages of exposure of your IP address to the public.
- The major A.I. security systems.
- The centralization of data storage.
- How to identify malicious activity on your devices.
- The safety of a network.
- The applications of network segmentation.
- The major challenges in IT risk management.
PhD Research Topics In Cybersecurity
Are you currently doing your Ph.D.? You can use any of these cybersecurity topics for your paper. They are all based on current matters. There are available resources that you can use to get data.
- The best approach for connected autonomous vehicles.
- The best methods for cognitive cybersecurity.
- The most innovative methods being used to determine the viability of deep learning based on the cybersecurity log analytics system.
- The significance of not sharing sensitive data on social media networks.
- Evaluate cookies on privacy.
- The different types of hackers.
- The disadvantages of Wi-Fi hacking apps on mobile phones.
- The major cyber-attack concepts.
- The best way to develop credible internet security software.
- How to scan malware on your pc.
- Evaluate twitter’s access control policy.
Research Topics In Cybersecurity
You can use any of these research topics in cybersecurity for your papers. You can derive data from some other scholarly articles, documentaries, films, and books. Information about cybersecurity gets updated daily.
- The attack of ransomware.
- The effects of RSA on any network’s security.
- The significance of cloud security.
- How do data leaks occur on mobile apps?
- The effects of a black hole on a network system.
- The significance of applications logging.
- How to detect malicious activities on Google Play apps.
- The best way to check security protocols.
- How does network security deal with cybercrime?
- The network security monitoring process.
- The dangers and flaws of the internet.
Best Research Topics In Cybersecurity
How confident are you about your knowledge of cybersecurity? Then you can consider using any of these topics to test your knowledge capacity. Give it your best to get top grades.
- Initiatives that can be taken to check the growth of cyber hackers.
- The difference between white and black hat hackers.
- How does network intrusion occur and its prevention?
- The authentication processes.
- The most common vulnerabilities.
- The different types of cybercrime.
- The major pandemics caused by cyber viruses.
- The significance of software updates and patches.
- The common laws against cybercrime in the world.
- The best way to suppress the ransomware attack rate.
- The significance of a keylogger.
Hot Topics Cybersecurity Research
These are some of the hottest topics in cybersecurity. You just need to find an ideal topic, do research, jot down the points, and start your research paper.
- The best way to ensure you are safe when downloading files on the internet.
- The best device synchronization and protection methods.
- How can you detect bots on the internet?
- The relation between internet cookies with cybersecurity.
- How are IOS-based apps less prone to ransomware attacks?
- Is it possible for computer hardware to face a cyber-attack?
- The algorithms of data encryption.
- The significance of investing in a strong anti-malware.
- How do encrypting viruses work?
- How do the reverse engineering and vulnerabilities analysis work?
Great Topics For Cybersecurity Research Papers
There are a lot of vulnerabilities on the internet. These great topics for cybersecurity can make you more knowledgeable about the current trends.
- Risk management in computing.
- The most common causes of a data breach in the 21 st
- The best way to protect your device and synchronize the data.
- The significance of computer forensics in the current digital era.
- The major implications of ethical hacking.
- The motivations behind cybercrimes like identity theft.
- The major components of IT and data governance.
- The most secure user authentication methods.
- The threats of digital piracy.
- The significance of device synchronization.
Cybersecurity And Law Research Topics
Did you know that certain laws govern cybersecurity? Then you can use these cybersecurity and law research topics to get a deeper understanding.
- Data and cybersecurity in IoT.
- The correlation between big data analysis with IoT.
- Evaluate Software Defined Network.
- The best tools for excellent email security.
- How to prevent cybercrimes.
- How do phishing scams occur?
- The significance of using strong passwords.
- The worst data breaches of all time.
- How do malicious people use other people’s identities to their benefit?
- How to remove malware from a computer.
Research Topics On Cybersecurity
There are different internet vulnerabilities in the world. Thereby, you can use these research topics on cybersecurity to understand how your security can be compromised on the internet.
- Evaluate botnets in the current world.
- Evaluate a brute force attack.
- The risks of connecting your device to a public wireless network.
- How to secure removable media.
- The occurrence of credit card fraud.
- The most recent cloud security threats.
- The significance of implementing multifactor authentication.
- How is online slandering a cybercrime?
- Email sender spoofing process.
- Stress is caused by periodic cyberbullying.
Cybersecurity Research Topic
Have you ever faced any cyber-attack? How was the experience? These are great topics that can help you become more knowledgeable.
- How to protect yourself from cyberbullying.
- The best security measures to input on Windows, macOS, and Linux.
- How dangerous is cyberstalking?
- Can cyber harassment be termed a crime?
- The major dangers of public Wi-Fi networks.
- Is it possible to identify a phishing attack?
- The best mobile protection methods on your smartphone.
- Malware and how it occurs.
- The best practices to secure your Home Wi-Fi.
- The advantages and disadvantages of antivirus software.
Topic On Cybersecurity
As a student, you need to up your game, to ensure you provide custom work that your teacher or professor will be happy about. Just try any of these topics on cybersecurity.
- The endpoint attacks on devices.
- The dangers posed by tracking cookies.
- The role of backups on your device’s data.
- Evaluate security patches.
- Is it important to read the software terms and conditions?
- Are there any malicious apps on the Google Play Store and Apple Store?
- Evaluate SQL injection attacks.
- The best way to keep your personal information safe.
- The vulnerabilities found in multifactor authentication.
- How to protect your computer.
- How to authenticate on your devices.
Paper Writing Assistance In Cybersecurity Research Paper
Are you busy and wondering how you will do your research paper, project, or thesis? Look no further, you can pay for dissertation and be sure to get perfect result. You just need to order by choosing a topic of your preference and buy it at a cheap price.
You don’t have to worry about not meeting the deadline. With us, you will be sorted. All the best in your research paper.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Comment * Error message
Name * Error message
Email * Error message
Save my name, email, and website in this browser for the next time I comment.
As Putin continues killing civilians, bombing kindergartens, and threatening WWIII, Ukraine fights for the world's peaceful future.
Ukraine Live Updates
- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

High-Impact Research Collection
Explore a collection of freely available high-impact research from 2020 and 2021 published in the Journal of Cybersecurity .
Browse the collection here

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Cookie Notice
This website uses cookies. Contact us for questions or requests.

Information for:
- Current Students
- Faculty & Staff
- Degrees & Programs
- Campus Maps
- Jobs & Careers
- Campus Shuttles
- Student Life
- Giving

- Augusta University
5 Research Topics in Cybersecurity
In 2022, market and consumer data firm Statista reported that cyberattacks would cost individuals and companies $8.4 trillion globally that year. By 2027, it projected, the cost would rise to $23.8 trillion. Cyberattacks occur when individuals gain unauthorized access to digital systems and information for malicious purposes. Their enormous cost to people and organizations makes it critical to protect systems, software and data against those attacks.
The term “cybersecurity” refers to efforts to protect corporate or personal electronic equipment against these costly attacks. Understanding the vulnerabilities that can allow unauthorized and damaging access to digital systems is a key component in cybersecurity research. An advanced degree in information security management can help professionals learn how cybersecurity risks are evolving, what cybersecurity risks to look for in their own organizations and how to address them.
What Is Cybersecurity Research?
Cybersecurity research focuses on reviewing digital tools and processes to reveal potential vulnerabilities. Research on cybersecurity topics ranging from the Internet of Things (IoT) to work-from-home (WFH) information security can help people and companies stave off data breaches in those key areas.
Cybersecurity professionals can rely on computer science research tactics such as testing web browsers and online applications to uncover areas that a hacker could exploit to gain unauthorized data access. They can also turn to empirical research that examines issues related to cybersecurity from various angles, from criminal science to international relations, and that offers approaches to address those concerns.
In fact, conducting research about potential security threats and information technology (IT) trends is a key responsibility of cybersecurity professionals, such as information security analysts.
Why Is Cybersecurity Research Important?
The value of cybersecurity research is growing due to the proliferation of connected devices that allow cybercriminals to access digital information — and as the costs associated with successful cyberattacks increase.
The origin of cyberattacks can be computers and the systems that run them, but it can also be any of hundreds of everyday devices that use technology to collect and share data. From smartphones to medical equipment, the tools that cyberattackers can compromise generate or store a staggering amount of data.
Statista reports that the amount of data created, copied, downloaded and read globally in 2010 was 2 zettabytes. By 2025, Statista predicts, the capacity of the data in use around the world will reach 181 zettabytes.
The growth in the use of data is occurring alongside a host of issues, from COVID-19-related disruptions to geopolitical events, that can make the technology that shares and stores it more vulnerable to attack. Conducting research on cybersecurity topics can assist IT professionals in protecting these large amounts of data during challenging times by helping them:
- Understand the vulnerabilities of digital tools and processes
- Determine the significance of data breach impacts
- Prioritize their efforts to ensure protection of critical information
5 Current Research Topics in Cybersecurity?
Today’s most pressing research topics in cybersecurity go beyond password protection and firewalls. A global pandemic, geopolitical events and technological advances are also behind some key topics that are now driving cybersecurity research. Below are five of those top cybersecurity research topics.
1. Artificial Intelligence
Artificial intelligence (AI), in which machines complete tasks that traditionally had required humans to perform, today is helping computing professionals observe and analyze activity related to large amounts of digital data. The efficiency of using AI for cybersecurity can lead to significant savings as organizations respond to data compromises. The shortened response time led companies to an average of $3 million in savings in those situations, according to a 2022 report from IBM.
One key research topic for cybersecurity professionals is how best to use AI to find potential vulnerabilities and remove them — before cyberattackers use that same technology to find those security risks and exploit them.
However, AI in the wrong hands can also present a cybersecurity risk. AI can also be a tool for misusing data, with cybercriminals relying on this technology to create inauthentic emails and phone messages to trick users into providing personal data. The increasing reliance on AI makes this issue even more important for cybersecurity researchers, with Statista projecting in 2022 that the AI software market would reach $126 billion around the world by 2025.
2. Digital Supply Chains
Digital supply chain systems monitor and evaluate the functions of each party in the chain, to help them produce and distribute products more efficiently. Hackers can exploit the technology used in this process, making cyberattacks an additional threat to supply chains already experiencing disruptions related to the pandemic.
For example, technology research firm Gartner, predicted in 2022 that by 2025, a total of 45 percent of companies would suffer digital attacks on their supply chains. This percentage is three times higher than the percentage from 2021. A 2022 report from cybersecurity company Venafi found that 82 percent of chief information officers feared that their organizations’ supply chains were vulnerable to this type of attack.
Cybersecurity professionals today are investigating potential digital security risks in supply chains, while corporate leaders are seeking out suppliers that focus on researching — and correcting — these vulnerabilities.
3. Internet of Things
The IoT refers to the ability to connect almost any device with the internet and with other connected tools. From kitchen appliances to wearable fitness gadgets, numerous products and tools are part of the IoT. Statista reported in 2022 that more than 11 million devices were digitally connected in 2021. The firm also projected that more than 29 billion devices would be IoT connected by 2030.
The many devices that rely on the IoT measure and process vast amounts of data, and the networks and cloud systems that hold and share that data present a host of security risks. A key area of cybersecurity research has been tracking these vulnerabilities. Manufacturers, consumers and governments have begun using the knowledge gathered by cybersecurity researchers to establish practices and policies that safeguard against the risks these researchers are finding.
4. State-Sponsored Attacks
Cyberattacks from government actors seeking state secrets are nothing new, but a growing trend is for hackers seeking this unauthorized access to target organizations and individuals with no government affiliation. The ultimate goal can be intelligence, technology theft, supply chain disruption or even influencing internal politics through disinformation.
A 2022 Forbes article noted that in 2023, more than 70 nations were set to conduct elections, and the digital activities related to these events, including reports about them, are a frequent target of hostile government actors. Additionally, countries involved in armed conflicts increasingly rely on cyberattacks to gain advantage over enemy governments, even when it involves interfering with the work of private companies and citizens.
These trends have made it critical for cybersecurity researchers to learn more about potential vulnerabilities in government networks, attacks on private companies that can impact critical infrastructure, and the security of elections.
5. Working From Home
Fueled by pandemic restrictions, the number of WFH employees exploded in recent years. The number of remote workers will reach more than 36 million in the U.S. by 2025, according to 2020 projections from freelancing platform Upwork.
The many employees based at off-site locations have made managing data security difficult for companies, whose workers may use unprotected devices to access and transmit business information. That leaves the employees vulnerable to attacks that target sensitive data or threaten malicious activity unless the company meets the hackers’ demands.
Adding to the security risk is the proliferation of work and other activity that requires the use of the internet and internet-based tools like videoconferencing. A 2021 Pew Research Center survey showed that 40 percent of Americans had relied on these types of tools and processes in new ways since the pandemic began in early 2020. Cybersecurity professionals are studying how best to protect employees — and the corporate data they use in their work — from cyberattackers.
Take a Leadership Role in Cybersecurity
Cybersecurity research can shed light on issues with data protection — and the tools and processes that provide it. If you’re ready to help guide your organization’s response to cybersecurity issues, explore Augusta University Online’s Master of Science (MS) in Information Security Management program.
Through online courses focused on Certified Information Systems Security Professional (CISSP) certification elements, students can gain the knowledge to help their employers navigate today’s cybersecurity challenges. Explore how AU Online’s MS in Information Security Management can help you reach your career goals.
Built In, “What Is Artificial Intelligence?” Cybersecurity and Infrastructure Security Agency, Cyber Threats and Advisories Forbes, “The Top Five Cybersecurity Trends in 2023” Gartner, “7 Top Trends in Cybersecurity for 2022” IBM, “Cost of Data Breach 2022: A Million Dollar Race to Detect and Respond” IBM, What Is Cybersecurity? Journal of Cybersecurity, About the Journal Microsoft, What Is a Cyberattack? Network World, “What Is IoT? The Internet of Things Explained” Oracle, “Digital Supply Chain Explained” Pew Research Center, “The Internet and the Pandemic” Statista, Estimated Cost of Cybercrime Worldwide From 2016 to 2027 Statista, Number of Internet of Things (IoT)-Connected Devices Worldwide From 2019 to 2021, With Forecasts From 2022 to 2030 Statista, Revenues From the Artificial Intelligence (AI) Software Market Worldwide From 2018 to 2025 Statista, Volume of Data/Information Created, Captured, Copied, and Consumed Worldwide From 2010 to 2020, With Forecasts From 2021 to 2025 TechRadar Pro, “Why Cybersecurity Research Is Now More Important Than Ever” The Conversation, “5 Ways the COVID-19 Pandemic Has Forever Changed Cybersecurity” Upwork, Upwork Study Finds 22% of American Workforce Will Be Remote by 2025 U.S. Bureau of Labor Statistics, Information Security Analysts Venafi, “Study: 82% of CIOs Say Their Software Supply Chains Are Vulnerable” Vivaldi, “An Insight Into Security Research and Ethical Hacking”
Want to hear more about Augusta University Online’s programs?
Fill out the form below, and an admissions representative will reach out to you via email or phone with more information. After you’ve completed the form, you’ll automatically be redirected to learn more about Augusta University Online and your chosen program.
Programs submenu
Regions submenu, topics submenu, the role of fast payment systems in addressing financial inclusion, modernizing army software acquisition: panel discussion with dasa(sar) margaret boatner and peo iew&s bg ed barker, book event: the mountains are high, energy security and geopolitics conference.
- Abshire-Inamori Leadership Academy
- Aerospace Security Project
- Africa Program
- Americas Program
- Arleigh A. Burke Chair in Strategy
- Asia Maritime Transparency Initiative
- Asia Program
- Australia Chair
- Brzezinski Chair in Global Security and Geostrategy
- Brzezinski Institute on Geostrategy
- Chair in U.S.-India Policy Studies
- China Power Project
- Chinese Business and Economics
- Defending Democratic Institutions
- Defense-Industrial Initiatives Group
- Defense 360
- Defense Budget Analysis
- Diversity and Leadership in International Affairs Project
- Economics Program
- Emeritus Chair in Strategy
- Energy Security and Climate Change Program
- Europe, Russia, and Eurasia Program
- Freeman Chair in China Studies
- Futures Lab
- Geoeconomic Council of Advisers
- Global Food and Water Security Program
- Global Health Policy Center
- Hess Center for New Frontiers
- Human Rights Initiative
- Humanitarian Agenda
- Intelligence, National Security, and Technology Program
International Security Program
- Japan Chair
- Kissinger Chair
- Korea Chair
- Langone Chair in American Leadership
- Middle East Program
- Missile Defense Project
- Project on Critical Minerals Security
- Project on Fragility and Mobility
- Project on Nuclear Issues
- Project on Prosperity and Development
- Project on Trade and Technology
- Renewing American Innovation Project
- Scholl Chair in International Business
- Smart Women, Smart Power
- Southeast Asia Program
- Stephenson Ocean Security Project
Strategic Technologies Program
- Transnational Threats Project
- Wadhwani Center for AI and Advanced Technologies
- All Regions
- Australia, New Zealand & Pacific
- Middle East
- Russia and Eurasia
- American Innovation
- Civic Education
- Climate Change
Cybersecurity
- Defense Budget and Acquisition
- Defense and Security
- Energy and Sustainability
- Food Security
- Gender and International Security
- Geopolitics
- Global Health
- Human Rights
- Humanitarian Assistance
- Intelligence
- International Development
- Maritime Issues and Oceans
- Missile Defense
- Nuclear Issues
- Transnational Threats
- Water Security
Led by the Strategic Technologies Program and the International Security Program , CSIS’s cybersecurity portfolio covers cyber warfare, encryption, military cyber capacity, hacking, financial terrorism, and more.

Photo: iLab/CSIS
Space Threat Assessment 2024
The 2024 Space Threat Assessment covers the growing counterspace capabilities of China, Russia, India, Iran, North Korea, and others. It also features analysis on the normalization of deviance on orbit and a look into coalitions of convenience that are being formed.
Report by Clayton Swope, Kari A. Bingen, Makena Young, Madeleine Chang, Stephanie Songer, and Jeremy Tammelleo — April 17, 2024

Eroding Trust in Government: What Games, Surveys, and Scenarios Reveal about Alternative Cyber Futures
Report by Yasir Atalan, Benjamin Jensen, and Jose M. Macias III — April 8, 2024

TikTok and National Security
Commentary by James Andrew Lewis — March 13, 2024

Government Use of Deepfakes
Report by Daniel Byman, Daniel W. Linna Jr., and V. S. Subrahmanian — March 12, 2024
Latest Podcasts

“Space Threat Assessment 2024”: Audio Brief with Clayton Swope
Podcast Episode by Clayton Swope — April 17, 2024

“Eroding Trust in Government: What Games, Surveys, and Scenarios Reveal about Alternative Cyber Futures”: Audio Brief with Yasir Atalan
Podcast Episode by Yasir Atalan — April 8, 2024

Venture Meets Mission with Arun Gupta
Podcast Episode by James Andrew Lewis — March 27, 2024

“Government Use of Deepfakes: The Questions to Ask”: Audio Brief with Daniel Byman
Podcast Episode by Daniel Byman — March 12, 2024
Past Events

Counterspace Trends: An Evolving Global Landscape

Shaping the Future of Federal Cybersecurity: Insights from FCEBs

5G/6G Technology and the Future of Global Security

A Discussion of the 2023 Counter Ransomware Initiative with DNSA Anne Neuberger

CISA's Evolving .gov Mission: Report Rollout Event

Managing Geopolitical Risk in Mexico's ICT Sector

China's Strategy of Political Warfare: Views from Congress

Next War Online: Using Cyber Games to Understand Emerging Threats
Related programs.

James Andrew Lewis

Suzanne Spaulding

Emily Harding

Clayton Swope
All cybersecurity content, type open filter submenu.
- Article (152)
- Event (140)
- Expert/Staff (32)
- Podcast Episode (81)
- Report (66)
Article Type open filter submenu
Report type open filter submenu, region open filter submenu.
- Afghanistan (5)
- Americas (39)
- Australia, New Zealand & Pacific (5)
- Caribbean Security (1)
- Central Asia (1)
- Eastern Europe (12)
- Europe (40)
- European Union (18)
- Middle East (10)
- North Africa (1)
- North America (57)
- Russia (34)
- Russia and Eurasia (29)
- South America (7)
- Southeast Asia (11)
- Sub-Saharan Africa (4)
- The South Caucasus (1)
Please join scholars from CSIS’s Aerospace Security Project and the Secure World Foundation as they discuss the latest counterspace weapons trends.
Event — April 17, 2024

A short, spoken-word summary from CSIS’s Clayton Swope on his report with Kari A. Bingen, Makena Young, Madeline Chang, Stephanie Songer, and Jeremy Tammelleo, Space Threat Assessment 2024.

In the future, malign actors will seek to undermine trust in government through disrupting basic needs and services such as food aid and medical assistance, in place of costly offensive cyber campaigns.

A short, spoken-word summary from CSIS’s Yasir Atalan on his report with Benjamin Jensen and Jose M. Macias III, Eroding Trust in Government: What Games, Surveys, and Scenarios Reveal about Alternative Cyber Futures.
In the last episode of the podcast, host Jim Lewis talks to Arun Gupta, a venture capitalist, lecturer, entrepreneur and author of ‘ Venture Meets Mission’ . They discuss the landscape of venture capital and government collaboration, tech innovation and overcoming a risk-averse culture.

The House of Representatives' recent decision on TikTok highlights concerns about its potential national security risks. This commentary highlights why the United States needs to reassess its technological connection to its largest competitor, China.

Will the lure of deepfakes prove irresistible to democratic governments? What questions should governments ask—and who in government should be asking them—when a deepfake is being considered?

A short, spoken-word summary from CSIS’s Daniel Byman on his report with Daniel W. Linna Jr. and V.S. Subrahmanian, Government Use of Deepfakes: The Questions to Ask.
The New Executive Order on Personal Data
This commentary analyzes Biden's executive order on safeguarding sensitive personal data, potentially compensating for Congress's lapse in privacy legislation, though practical challenges may arise given the era of increased espionage risks from Russia and China.
Commentary by James Andrew Lewis — March 6, 2024

Cybersecurity

Most Cited Paper
We are pleased to announce the top 5 cited papers of Cybersecurity.
This list is based on the cites received from 2018 to 2023. You can find the top five articles here .
Cybersecurity Award 2024
Call for Nomination - Cybersecurity Award
The Cybersecurity Award is held annually and presented to authors whose work represents outstanding and groundbreaking research in all essential aspects of cybersecurity from the previous year.
- Most accessed
Iterative and mixed-spaces image gradient inversion attack in federated learning
Authors: Linwei Fang, Liming Wang and Hongjia Li
Winternitz stack protocols for embedded systems and IoT
Authors: Alex Shafarenko
Joint contrastive learning and belief rule base for named entity recognition in cybersecurity
Authors: Chenxi Hu, Tao Wu, Chunsheng Liu and Chao Chang
DTA: distribution transform-based attack for query-limited scenario
Authors: Renyang Liu, Wei Zhou, Xin Jin, Song Gao, Yuanyu Wang and Ruxin Wang
A survey on lattice-based digital signature
Authors: Fengxia Liu, Zhiyong Zheng, Zixian Gong, Kun Tian, Yi Zhang, Zhe Hu, Jia Li and Qun Xu
Most recent articles RSS
View all articles
Survey of intrusion detection systems: techniques, datasets and challenges
Authors: Ansam Khraisat, Iqbal Gondal, Peter Vamplew and Joarder Kamruzzaman
Review and insight on the behavioral aspects of cybersecurity
Authors: Rachid Ait Maalem Lahcen, Bruce Caulkins, Ram Mohapatra and Manish Kumar
Fuzzing: a survey
Authors: Jun Li, Bodong Zhao and Chao Zhang
A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges
Authors: Ansam Khraisat and Ammar Alazab
Detecting telecommunication fraud by understanding the contents of a call
Authors: Qianqian Zhao, Kai Chen, Tongxin Li, Yi Yang and XiaoFeng Wang
Most accessed articles RSS
Thematic Series
2020 Data-Driven Security Edited by: Yang Liu, Xinming Ou, Xinyu Xing, Guozhu Meng
2019 Data Security and Privacy Edited by: Dan Lin, Jingqiang Lin and Bo Luo
Information Abuse Prevention Edited by: Gang Li and Jianlong Tan
2018 System Security Edited by: Peng Liu
AI and Security Edited by: Xiaofeng Wang

Aims and scope
This journal is aimed to systematically cover all essential aspects of cybersecurity, with a focus on reporting on cyberspace security issues, the latest research results, and real-world deployment of security technologies.
The journal publishes research articles and reviews in the areas including, but not limited to:
• Cryptography and its applications • Network and critical infrastructure security • Hardware security • Software and system security • Cybersecurity data analytics • Data-driven security and measurement studies • Adversarial reasoning • Malware analysis • Privacy-enhancing technologies and anonymity • IoT Security • AI Security
Why submit to us
• 1 st open access journal on Cybersecurity • APC fully covered by IIE, CAS • Served by a dedicated international editorial board to give thorough swift editorial response
Editor-in-Chief: MENG Dan

Full Professor in Institute of Information Engineering (IIE), Chinese Academy of Sciences (CAS). His work focuses on network and system security, parallel distributed processing. He has lead important research projects including Dawning supercomputers, National Science and Technology Major Project, National High Technology Research and Development Program of China, and strategic priority research program of CAS. He has published over one hundred peer-reviewed papers. He is the director of IIE, after serving as the deputy director of IIE, the deputy director of the High Technology Research and Development Bureau of CAS.
Executive Editor-in-Chief: LIU Peng

LIU Peng received his BS and MS degrees from the University of Science and Technology of China, and his PhD from George Mason University in 1999. Dr. Liu is a Professor of Information Sciences and Technology, founding Director of the Center for Cyber-Security, Information Privacy, and Trust, and founding Director of the Cyber Security Lab at Penn State University. His research interests are in all areas of computer and network security. He has published a monograph and over 260 refereed technical papers. His research has been sponsored by NSF, ARO, AFOSR, DARPA, DHS, DOE, AFRL, NSA, TTC, CISCO, and HP. He has served as a program (co-)chair or general (co-)chair for over 10 international conferences (e.g., Asia CCS 2010) and workshops (e.g., MTD 2016). He chaired the Steering Committee of SECURECOMM during 2008-14. He has served on over 100 program committees and reviewed papers for numerous journals. He is an associate editor for IEEE TDSC. He is a recipient of the DOE Early Career Principle Investigator Award. He has co-led the effort to make Penn State a NSA-certified National Center of Excellence in Information Assurance Education and Research. He has advised or co-advised over 30 PhD dissertations to completion.
- Editorial Board
- Sign up for article alerts and news from this journal
Affiliated with

The Institute of Information Engineering (IIE) is a national research institute in Beijing that specializes in comprehensive research on theories and applications related to information technology.
IIE strives to be a leading global academic institution by creating first-class research platforms and attracting top researchers. It also seeks to become an important national strategic power in the field of information technology.
IIE’s mission is to promote China’s innovation and industrial competitiveness by advancing information science, standards, and technology in ways that enhance economic security and public safety as well as improve our quality of life.
Read more..
The journal is indexed by
- EI Compendex
- Emerging Sources Citation Index
- EBSCO Discovery Service
- Institute of Scientific and Technical Information of China
- Google Scholar
- Norwegian Register for Scientific Journals and Series
- OCLC WorldCat Discovery Service
- ProQuest-ExLibris Primo
- ProQuest-ExLibris Summon
- TD Net Discovery Service
- UGC-CARE List (India)
Annual Journal Metrics
2022 Citation Impact 3.1 - 2-year Impact Factor 4.8 - 5-year Impact Factor 2.071 - SNIP (Source Normalized Impact per Paper) 1.266 - SJR (SCImago Journal Rank)
2023 Speed 8 days submission to first editorial decision for all manuscripts (Median) 95 days submission to accept (Median)
2023 Usage 408,523 downloads 15 Altmetric mentions
- ISSN: 2523-3246 (electronic)
A List of 181 Hot Cyber Security Topics for Research [2024]
Your computer stores your memories, contacts, and study-related materials. It’s probably one of your most valuable items. But how often do you think about its safety?
Our specialists will write a custom essay specially for you!
Cyber security is something that can help you with this. Simply put, it prevents digital attacks so that no one can access your data. Do you want to write a research paper related to the modern challenges of cyberspace? This article has all you need. In here, you’ll find:
- An overview of cyber security’s research areas.
- A selection of compelling cyber security research topics.
And don’t hesitate to contact our custom writing team in case you need any assistance!
- 🔝 Top 10 Topics
- ✅ Research Areas
- ⭐ Top 10 Cybersecurity Topics
- 🔒 Technology Security Topics
- 🖥️ Cybercrime Topics
- ⚖️ Cyber Law & Ethics Topics
🔍 References
🔝 top 10 cyber security topics.
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- The importance of end-user education
- Cloud security posture management
- Do biometrics ensure security of IPhones?
- Can strong passwords protect information?
- Is security in critical infrastructure important?
✅ Cyber Security Topics & Research Areas
Cyber security is a vast, constantly evolving field. Its research takes place in many areas. Among them are:

- Safe quantum and space communications . Progress in quantum technologies and space travel calls for extra layers of protection.
- Data privacy. If someone’s personal information falls into the wrong hands, the consequences can be dire. That’s why research in this area focuses on encryption techniques.
- (Inter)national cyberethics, criminology, and law. This branch analyzes how international legal frameworks work online.
- AI and IoT security . We spend more and more of our daily lives online. Additionally, our reliance on AI increases. This scientific field strives to ensure a safe continuation of this path.
As you can see, cyber security extends in various exciting directions that you can explore. Naturally, every paper needs a cover page. We know that it’s one of the more annoying parts, so it’s not a bad thing to use a title page generator for your research paper . Now, let’s move on to our cyber topics list.
⭐ Top 10 Cybersecurity Topics 2024
- Is removable media a threat?
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How to prevent phishing attacks
- Physical security measures in banks
- Security breaches of remote working
- How does two-factor authentication work?
- How to prevent social engineering attacks
- Cybersecurity standards for automotive
- Privacy settings of social media accounts
🔒 Computer Security Topics to Research
Safe computer and network usage is crucial. It concerns not only business but also individuals. Security programs and systems ensure this protection. Explore them with one of our topics:
Just in 1 hour! We will write you a plagiarism-free paper in hardly more than 1 hour
- How do companies avoid sending out confidential information ? Sending an email to the wrong person has happened to the best of us. But what happens if the message’s contents were classified? For your paper, you can find out what technologies can prevent such slip-ups.
- What are the best ways to detect malicious activity ? Any organization’s website gets plenty of daily traffic. People log in, browse, and interact with each other. Among all of them, it might be easy for an intruder to slip in.
- Internet censorship: classified information leaks . China takes internet censorship to the next level. Its comprehensive protection policies gave the system the nickname Great Firewall of China . Discuss this technology in your essay.
- Encrypted viruses as the plague of the century . Antivirus programs are installed on almost every computer. They prevent malicious code from tampering with your data. In your paper, you can conduct a comparison of several such programs.
- What are the pros and cons of various cryptographic methods? Data privacy is becoming more and more critical. That’s why leading messaging services frequently advertise with their encryption technologies .
- What makes blockchain secure ? This technique allows anonymity and decentralization when working with cryptocurrencies . How does it work? What risks are associated with it?
- What are the advantages of SIEM ? Security Incident and Event Management helps organizations detect and handle security threats. Your essay can focus on its relevance for businesses.
- What are the signs of phishing attempts?
- Discuss unified cyber security standards in healthcare .
- Compare and contrast various forms of data extraction techniques.
- What do computers need protocols for?
- Debate the significance of frequent system updates for data security .
- What methods does HTTPS use that make it more secure than HTTP?
- The role of prime numbers in cryptography .
- What are public key certificates , and why are they useful?
- What does a VPN do?
- Are wireless internet connections less secure than LAN ones? If so, why?
- How do authentication processes work?
- What can you do with IP addresses?
- Explain the technology of unlocking your phone via facial recognition vs. your fingerprint.
- How do you prevent intrusion attempts in networks ?
- What makes Telnet vulnerable?
- What are the phases of a Trojan horse attack?
- Compare the encryption technologies of various social networks.
- Asymmetric vs. symmetric algorithms.
- How can a person reach maximum security in the computer networking world ?
- Discuss autoencoders and reveal how they work.
💾 Information Security Topics to Research
Information security’s goal is to protect the transmission and storage of data. On top of that, network security topics are at the forefront of infosec research. If you’re looking for inspiration on the subject, check out these ideas.
- What are the mechanics of password protection ? Passwords are a simple tool to ensure confidentiality. What do users and developers need to keep in mind when handling passwords?
- What are the safest ways to ensure data integrity ? Everybody wants their data to be intact. Accidental or malicious modifications of data can have dire consequences for organizations and individuals. Explore ways to avoid it.
- How can one establish non-repudiation? Non-repudiation proves the validity of your data. It’s essential in legal cases and cyber security .
- How did the advent of these new technologies impact information security ? Mobile networks have changed the way we access information. On a smartphone , everything is permanently available at your fingertips. What adverse consequences did these technologies bring?
- How do big corporations ensure that their database environment stays conflict-free? We expect our computers to always run fast and without errors. For institutions such as hospitals, a smooth workflow is vital. Discuss how it can be achieved.
- Describe solid access control methods for organizations. In a company, employees need access to different things. This means that not everyone should have an admin account. How should we control access to information ?
- Medical device cyber security. For maximum safety, it’s best to employ several measures. Protection on the hard- and software side is just a part of it. What are some other means of security?
- Write an argumentative essay on why a career in information security doesn’t require a degree.
- Pros and cons of various infosec certificates.
- Cybersecurity in cruise ship industry
- The influence of remote work on a businesses’ infosec network .
- What should everyone be aware of when it comes to safeguarding private information?
- Select a company and calculate how much budget they should allocate on cyber security.
- What are the dangers of public Wi-Fi networks ?
- How secure are cloud services ?
- Apple vs. Microsoft : whose systems offer better security?
- Why is it important to remove a USB flash drive safely?
- Is it possible to create an unguessable password?
- Intranet security : best practices.
- Does the use of biometrics increase security?
- Face recognition vs. a simple code: what are the safest locking options for smartphones ?
- How do you recover data from a broken hard drive?
- Discuss the functions and risks of cookies and cache files.
- Online privacy regulations in the US and China.
- Physical components of infosec .
- Debate security concerns regarding electronic health records .
- What are unified user profiles, and what makes them potentially risky?
🖥️ Cybercrime Topics for a Research Paper
Knowledge is one of today’s most valuable assets. Because of this, cybercrimes usually target the extraction of information. This practice can have devastating effects. Do you want to learn more about the virtual world’s dark side? This section is for you.
- Give an overview of the various types of cybercrimes today . Cybercriminals are becoming more and more inventive. It’s not easy to keep up with the new threats appearing every day. What threats are currently the most prominent?
- How does cryptojacking work, and why is it problematic? Cryptocurrency’s value explosion has made people greedy. Countries such as Iceland have become a haven for datamining. Explore these issues in your essay.
- Analyze the success rate of email frauds . You’ve probably seen irrelevant ads in your spam folder before. They often sound so silly it’s hard to believe they work. Yet, unfortunately, many people become victims of such scams.
- How did the WannaCry malware work? WannaCry was ransomware that caused global trouble in 2017. It led to financial losses in the billions. What made it so dangerous and hard to stop?
- Give famous examples of cybercrimes that targeted people instead of money . Not all cybercrimes want to generate profit. Sometimes, the reasons are political or personal. Explore several instances of such crimes in your essay. How did they pan out?

- Analyze the implications of the Cyberpunk 2077 leak. The game’s bugs and issues made many people angry. Shortly after its flop, hackers released developer CD Projekt Red’s source codes. What far-reaching consequences could this have?
- Why do hackers commit identity theft? Social media has made it easy to steal identities . Many like to display their lives online. In your paper, research what happens to the victims of identity thefts.
- Should governments punish cybercrimes like real-life crimes?
- How does ransomware work?
- Describe the phases of a DDoS attack.
- What cybercrime cases led to changes in the legislature ?
- Track the evolution of online scams.
- Online grooming: how to protect children from predators.
- Are cybercrimes “gateway crimes” that lead to real-life misbehavior?
- What are man-in-the-middle attacks?
- Big data and the rise of internet crimes.
- Are cybercrimes more dangerous to society than they are to corporations?
- Is the internet increasing the likelihood of adolescents engaging in illegal activities?
- Do the downsides of cyberlife outweigh its positives?
- Is constantly checking your crush’s Facebook page cyberstalking?
- How do you recognize your online date is a scam?
- Describe what happens during a Brute Force attack.
- What’s the difference between pharming and phishing?
- The Lehman Bank cybercrimes
- Should the punishments for cybercriminals be harsher than they are now?
- Compare various types of fraud methods .
- How do you mitigate a denial-of-service attack?
🕵️ Topics for a Research Paper on Hacking
Blinking screens and flashing lines of code: the movie industry makes hacking look fascinating. But what actually happens when someone breaks into another person’s computer’s system? Write a paper about it and find out! The following prompts allow you to dive deeper into the subject.
- Is it vital to keep shutting down online movie streaming sites? Many websites offer free movie streaming. If one of their domains gets closed down, they just open another one. Are they a threat to the industry that must be stopped? Or should cyber law enforcement rather focus on more serious crimes?
- Explore the ethical side of whistleblowing. WikiLeaks is a platform for whistleblowers. Its founder, Julian Assange, has been under arrest for a long time. Should whistleblowing be a crime? Why or why not?
- How did Kevin Mitnick’s actions contribute to the American cyber legislature? Mitnick was one of the US’s first most notorious hackers. He claimed to have broken into NORAD’s system. What were the consequences?
- Examine how GhostNet operates. GhostNet is a large organization attacking governments. Its discovery in 2009 led to a major scandal.
- Describe how an SQL injection attack unfolds. Injection attacks target SQL databases and libraries. This way, hackers gain unauthorized access to data.
- What political consequences did the attack on The Interview imply? In 2014, hackers threatened to attack theaters that showed The Interview . As a result, Sony only showed the movie online and in limited releases.
- Write about cross-site request forgery attacks. Every website tells you that logging out is a crucial step. But what can happen if you don’t do it?
- What is “Anonymous,” and what do they do?
- Is it permissible to hack a system to raise awareness of its vulnerabilities?
- Investigate the origins of the hacking culture .
- How did industrial espionage evolve into hacking?
- Is piracy destroying the music and movie industries ?
- Explain the term “cyberwarfare.”
- Contrast different types of hacking .
- Connections between political protests and hacking.
- Is it possible to create an encryption that can’t be hacked?
- The role of hackers in modern warfare .
- Can hacking be ethical?
- Who or what are white hat hackers ?
- Discuss what various types of hackers do.
- Is jailbreaking a crime?
- How does hacking a phone differ from hacking a computer?
- Is hacking your personal home devices problematic?
- What is clickjacking?
- Why would hackers target newspapers ?
- Examine the consequences society would have to bear if a hacker targeted the state.
- Compare and analyze different hacking collectives.
⚖️ Topics on Cyber Law & Ethics to Look Into
Virtual life needs rules just like the real one does. The online world brings a different set of values and issues to the table. And, naturally, cyberlife has a legal framework. That’s where researching cyber law and ethics comes into play.
- Is it ethical that governments can always access their citizens’ data? In some countries, online platforms for personal information are standard. From medical exams to debts , everything is available with a click. The system is inarguably convenient. But what about its downsides?
- Is it still morally permissible to use Spotify ? Spotify has made listening to music more accessible than ever. However, artists only receive a tiny fraction of the company’s profits. Discuss the implications of this fact.
- Should internet forums require users to display their real names? Online harassment is a widespread problem. Nicknames hide the identities of ordinary users as well as perpetrators. Can the mandatory use of real names change the situation?
- Analyze online gaming behavior from a psychological standpoint. If one wants to play online games, one needs to have a thick skin. The community can be harsh. You can dedicate your paper to exploring these behaviors. Or you might want to ponder what game publishers can do to reduce hate speech.
- What type of restrictions should sellers implement to prevent domain speculation? Some people buy domains hoping that they will sell them later for more money. This practice makes registering a new website trickier.
- Does the internet need regulations to make adult content less visible? Every computer without parental control can access pornographic websites. Most of them don’t require registration . Their contents can be disturbing, and their ads can appear anywhere. What can be done about it?
- What are cyber laws still missing in America? The US has established many laws to regulate internet usage. Select the most significant ones and explain their relevance.
- Why should cyber ethics be different from real-world norms?
- Are there instances in which illegal downloading is justified?
- The rule of law in real life vs. in cyberspace.
- Does the internet need a government?
- What is cyber terrorism, and what makes it dangerous?
- Who is responsible for online misbehavior?
- How binding are netiquettes?
- What did the implementation of the GDPR change?
- Compare and contrast Indian vs. Venezuelan internet regulations.
- What does the CLOUD entail?
- How should law enforcement adapt to online technologies?
- AI applications : ethical limits and possibilities.
- Discuss trending topics in cyber law of the past ten years.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- Is data privacy more important than convenience and centralization?
- Debate whether bitcoins could become the currency of the future.
- How can online consumers protect themselves from fraud ?
- Is buying from websites like eBay and Craigslist more ethical than buying from other online marketplaces?
- Present RSF’s Minecraft library and discuss its moral implications.
🖱️ Cyberbullying Topics for Essays and Papers
On the web, everyone can remain anonymous. With this added comfort, bullying rises to another level. It’s a serious issue that’s getting more and more problematic. Cyber security measures can alleviate the burden. Do you want to address the problem? Have a look at our cyberbullying topics below.
Receive a plagiarism-free paper tailored to your instructions. Cut 20% off your first order!
- Cyberbullying prevention in online learning environments . Online classes increase the possibility of cyberbullying. What can teachers do to watch out for their students?
- What makes online emotional abuse particularly difficult to bear? Bullying doesn’t necessarily have to be physical to hurt. Statistics show increased suicide rates among students who were harassed online. Explore the reasons behind this phenomenon.
- How can victims of identity theft reclaim their lives? Identity theft leads not only to mental distress. Thieves also have access to credit card information and other essential assets.
- What are the best methods to stay safe online? When surfing the internet, one always has to be on one’s toes. Avoiding harassment and bullying is a particularly challenging task.
- How can parents monitor their children’s behavior on the web? Children are particularly vulnerable online. They might enter dangerous online relationships with strangers if they feel lonely. They are also more susceptible to scams. What can parents do to protect them?
- Cyberbullying among university students. Online abuse in such websites is very common. Everyone can be a potential target, regardless of age or gender. Discuss whether the structure of social networks helps to spread cyberbullying.
- What societal factors contribute to online bullying? Not everyone who uses the internet becomes an abuser. It’s possible to establish several psychological characteristics of cyberbullies. Explore them in your paper.
- Define how cyberbullying differs from in-person harassment .
- Establish a link between feminism and the fight against cyberstalking .
- The emotional consequences of physical vs. verbal abuse.
- The effects of cyberbullying and academics.
- Short vs. long-term mental health effects of internet bullying .
- What are the most widespread means of cyberbullying ?
- Should people who want to play video games online get over the fact that the community is toxic?
- Is defending the freedom of speech more important than preventing the spread of hate speech?
- Reasons and consequences of Amanda Todd’s suicide.
- The dangers of pro-ana/-mia communities for adolescents.
- What are effective strategies to cope with online harassment ?
- Would cyber communism decrease bullying?
- How enhanced cyber security measures can help reduce abuse.
- The importance of parental control mechanisms on children’s computers.
- Traditional vs. cyberbullying in children.
- Do image-heavy websites such as Tumblr and Instagram affect one’s mental state similarly to active abuse?
- What kind of people does cyber abuse affect the most, and why?
- Analyze how the stalker uses the internet in Netflix’s series You .
- Catfishing: effects and solutions.
Thanks for reading through our article. If you found it helpful, consider sharing it with your friends. We wish you good luck with your project!
Further reading:
- 220 Best Science and Technology Essay Topics to Write About
- 204 Research Topics on Technology & Computer Science
- A List of 580 Interesting Research Topics [2024 Edition]
- A List of 179 Problem Solution Essay Topics & Questions
- 193 Interesting Proposal Essay Topics and Ideas
- 226 Research Topics on Criminal Justice & Criminology
- What Is Cybersecurity?: Cisco
- Cyber Security: Research Areas: The University of Queensland, Australia
- Cybersecurity: National Institute of Standards and Technology
- What Is Information Security?: CSO Online
- Articles on Cyber Ethics: The Conversation
- What Is Cybercrime?: Kaspersky
- Types of Cybercrime and How to Protect Yourself Against Them: Security Traits
- Hacking: Computing: Encyclopedia Britannica
- Hacking News: Science Daily
- Cyberbullying and Cybersecurity: How Are They Connected?: AT&T
- Cyberbullying: What Is It and How to Stop It: UNICEF
- Current Awareness: Cyberlaw Decoded: Florida State University
- Share to Facebook
- Share to Twitter
- Share to LinkedIn
- Share to email

Have you ever wondered why everyone has a unique set of character traits? What is the connection between brain function and people’s behavior? How do we memorize things or make decisions? These are quite intriguing and puzzling questions, right? A science that will answer them is psychology. It’s a multi-faceted...
![research topics for cybersecurity Student Exchange Program (Flex) Essay Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/student-exchange-program-284x153.jpg)
Participating in a student exchange program is a perfect opportunity to visit different countries during your college years. You can discover more about other cultures and learn a new language or two. If you have a chance to take part in such a foreign exchange, don’t miss it. Keep in...

How can you define America? If you’ve ever asked yourself this question, studying US history will help you find the answer. This article will help you dive deeper into this versatile subject. Here, you will find: Early and modern US history topics to write about. We’ve also got topics for...
![research topics for cybersecurity 380 Powerful Women’s Rights & Feminism Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Womens-Rights-284x153.jpg)
Are you looking for perfect feminist topics? Then you’ve come to the right place. With our help, you can be sure to craft a great essay. Here, you can find feminist topics for discussion, feminism research topics and other ideas and questions for students. Some people think all feminists hate...

If you have an assignment in politics, look no further—this article will help you ace your paper. Here, you will find a list of unique political topics to write about compiled by our custom writing team. But that’s not all of it! Keep reading if you want to: See how to tackle political essay topics in your paper; Choose a topic that will be interesting for you to research; Refresh your knowledge of essential political concepts. Now, without further ado, let’s get started! Below, you’ll find political topics and questions for your task. 🔝 Top 10...

It’s not a secret that our health largely depends on nutrition. A balanced and wholesome diet improves our immune system. It lowers the risk of getting sick and makes us more productive. But if we don’t eat right, our overall well-being and performance worsen. You see, nutrition topics are more...

A presentation is a speech in which you explain a topic to an audience. It usually includes visuals done in a program such as PowerPoint. Teachers in schools and in colleges love to assign presentations for various reasons: It requires students to put their knowledge into practice.It teaches them how...

In modern societies, people do everything to live peacefully. Still, tensions often arise. We call them social issues when they start negatively impacting a specific group of people. Poverty, discrimination, and addiction are examples of such problems. We need to confront them to ensure equal treatment for everyone.

There are many ways to define popular culture. Here’s one of them: pop culture includes mainstream preferences in society within a specific time frame. It covers fashion, music, language, and even food. Pop culture is always evolving, engaging in new trends, and leaving the old ones behind.
![research topics for cybersecurity 500 Sociology Questions and Topics [Examples & Tips]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Sociology-Questions-284x153.jpg)
Sociology is a study that focuses on people’s interactions. It looks at structures and changes in social life. Any situation involving people can become a topic of sociology. This article is designed to help high school and college students with sociology assignments. Whether you’re writing an essay, creating a presentation,...

Controversial issues are the ones that evoke a variety of opinions. They often cause heated debates. And, as you can guess, controversial research topics are not easy to handle. Luckily, we’ve got you covered. This article will: help you pick a controversial question for your essay;provide you a list of...

Plates break when you drop them. Glasses help you see better. Have you ever wondered why? Physics has the answer. It studies the observable as well as invisible aspects of nature. An essential part of this is examining the structure and interactions of matter.
- Write my thesis
- Thesis writers
- Buy thesis papers
- Bachelor thesis
- Master's thesis
- Thesis editing services
- Thesis proofreading services
- Buy a thesis online
- Write my dissertation
- Dissertation proposal help
- Pay for dissertation
- Custom dissertation
- Dissertation help online
- Buy dissertation online
- Cheap dissertation
- Dissertation editing services
- Write my research paper
- Buy research paper online
- Pay for research paper
- Research paper help
- Order research paper
- Custom research paper
- Cheap research paper
- Research papers for sale
- Thesis subjects
- How It Works
50 Great Cybersecurity Research Paper Topics

Students are required to write papers and essays on cyber security topics when pursuing programs in cyber security disciplines. These topics are technical and they require learners to inherently understand this subject. What’s more, students should have impeccable research and writing skills.
Additionally, students should choose cyber security topics to write their papers and essays carefully. As a science field, cyber security is developing rapidly and constantly. As such, learners can always find interesting topics to write papers and essays about.
Pick Cyber Security Topics From Our List
Software and computer administration cyber security topics.
- Cyber Security Research Paper Topics on Data Protection
- Cyber Security Awareness Topics
Network Security Topic Ideas
- Current and Interesting Topics in Cyber Security
Nevertheless, selecting cybersecurity topics for research shouldn’t be a rushed process. That’s because the chosen topics will influence the experience of students while writing and the grades they will score. Therefore, learners should focus on choosing topics that they will be comfortable researching and writing about.
If you’re having a hard time choosing the topics to research and write about, here are categories of some of the best cybersecurity paper topics that you can consider. We also advise you to check out capstone project topics .
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category.
- Evaluation of the operation of antimalware in preventing cyber attacks
- How does virus encryption work
- Is countering malware difficult because of the fast evolution of technology?
- Why should companies train their staff on cyber security?
- Why should people worry about identity theft?
- How important are software updates when it comes to cyber security?
- What causes cyber crimes?
- What are the major threats to the cyber security of social media users?
- What are the most effective methods of preventing phishing?
- What is the major threat to cyber security today and why?
These topics address issues that affect anybody or any organization that uses a computer or any device to access the internet and exchange information. As such, most people, including teachers and professors, will be impressed by papers and essays written about them.
CyberSecurity Research Paper Topics on Data Protection
Individuals and companies send and receive a lot of data every day. As such, this category has some of the best cybersecurity topics for presentation. That’s because they address issues that affect many people and organizations. Here are some of the best information security topics to consider when writing papers and essays or preparing a presentation.
- The best security measures for protecting your data
- How third-party applications can be used to access and acquire data without permission
- How to prevent the loss of data from a computer
- Can biometrics be used to prevent unauthorized data access?
- Can you protect yourself from cyber crimes by keeping personal data private?
- What should you do in case of a data breach?
- How can you secure your data with a 2-steps authentication process?
- How can public Wi-Fi or the internet be used to steal personal data?
- What information can be accessed by unauthorized persons if they hack an account?
- Can software updates help in protecting personal data?
Every computer or internet user wants to be sure that their data is safe and protected. Papers and essays that are written on these topics address issues of data protection. As such, many people will find them worth reading.
CyberSecurity Awareness Research Paper Topics
The best cyber security topics for research papers do more than just address a single issue. They also inform the readers. Here are some of the best cyber security topics for research papers that also focus on creating awareness.
- What is reverse engineering?
- How efficient are RFID security systems?
- How does the dark web propagate organized cyber crimes?
- How can steganalysis be applied?
- Analyze the best authorization infrastructures today
- How important is computer forensics in the current digital era?
- What strategies have been proven effective in preventing cyber-attacks?
- Which forensic tools are the best when it comes to detecting cyber threats?
- Can changing the password regularly help in predicting a cyber attack?
- How can you tell that you’re at risk of online identity theft?
Many people are not aware of many things that affect their cyber security. These topics are relevant because they enhance the awareness of the internet and computer users.
Most organizations today have networked systems that enhance their operations. Unfortunately, criminals have learned to target those networked systems with their criminal activities. As such, students can address some of these issues with their cyber security thesis topics. Here are interesting topics that learners can research and write about in this category.
- Evaluation of the cyber security legal framework in the U.S
- Analysis of the most difficult aspect of the administration of cyber security
- How can the possibilities of multiple threats be managed effectively?
- How does data backup help when it comes to cyber security?
- How effective is two-factor authentication?
- How should a company respond to hacking in its system?
- Which are the best cyber security protection approaches for a multinational company?
- What are the pros and cons of unified user profiles?
- What are the most important components of effective data governance?
- What motivates individuals to commit cybercrimes?
These computer security topics can be used to write papers and essays for college or even commissioned by organizations and used for presentation purposes.
Current and Interesting Topics in CyberSecurity
Some computer security research topics seek to address issues that affect society at the moment. Here are examples of such topics.
- How phishing is evolving and getting more sophisticated
- Explain the evolution of Ransomware strategies
- Explain how the cryptocurrency movement affects cybersecurity
- Cyber-Physical Attacks: How do they work?
- What are state-sponsored attacks and how do they affect cyber security at a global level?
- Discuss cyber security risks when it comes to third-party vendor relationships
- How digital advertisements are being used to collect user characteristics
- How can a person sync all their devices while ensuring their protection
- Why it’s advisable to avoid downloading files from sites that are not trusted
- Why consumers should read the terms and conditions of software before they decide to install it
Such technology security topics are trendy because they address issues that affect most people in modern society. Nevertheless, students should conduct extensive research to draft solid papers and essays on these topics.
This cyber security topic list is not exhaustive. You can contact our thesis writers if you need more ideas or help. Students have many topics to consider depending on their academic programs, interests, and instructions provided by educators or professors. Nevertheless, students should focus on choosing topics that will enable them to come up with informative and comprehensive papers. Thus, every student should choose an information security topic for which they can find relevant and supporting data.
Leave a Reply Cancel reply
Cyber risk and cybersecurity: a systematic review of data availability
- Open access
- Published: 17 February 2022
- Volume 47 , pages 698–736, ( 2022 )
Cite this article
You have full access to this open access article
- Frank Cremer 1 ,
- Barry Sheehan ORCID: orcid.org/0000-0003-4592-7558 1 ,
- Michael Fortmann 2 ,
- Arash N. Kia 1 ,
- Martin Mullins 1 ,
- Finbarr Murphy 1 &
- Stefan Materne 2
63k Accesses
60 Citations
42 Altmetric
Explore all metrics
Cybercrime is estimated to have cost the global economy just under USD 1 trillion in 2020, indicating an increase of more than 50% since 2018. With the average cyber insurance claim rising from USD 145,000 in 2019 to USD 359,000 in 2020, there is a growing necessity for better cyber information sources, standardised databases, mandatory reporting and public awareness. This research analyses the extant academic and industry literature on cybersecurity and cyber risk management with a particular focus on data availability. From a preliminary search resulting in 5219 cyber peer-reviewed studies, the application of the systematic methodology resulted in 79 unique datasets. We posit that the lack of available data on cyber risk poses a serious problem for stakeholders seeking to tackle this issue. In particular, we identify a lacuna in open databases that undermine collective endeavours to better manage this set of risks. The resulting data evaluation and categorisation will support cybersecurity researchers and the insurance industry in their efforts to comprehend, metricise and manage cyber risks.
Similar content being viewed by others
The role of artificial intelligence in healthcare: a structured literature review
Silvana Secinaro, Davide Calandra, … Paolo Biancone

The Ethical Implications of Using Artificial Intelligence in Auditing
Ivy Munoko, Helen L. Brown-Liburd & Miklos Vasarhelyi

Artificial Intelligence and Fraud Detection
Avoid common mistakes on your manuscript.
Introduction
Globalisation, digitalisation and smart technologies have escalated the propensity and severity of cybercrime. Whilst it is an emerging field of research and industry, the importance of robust cybersecurity defence systems has been highlighted at the corporate, national and supranational levels. The impacts of inadequate cybersecurity are estimated to have cost the global economy USD 945 billion in 2020 (Maleks Smith et al. 2020 ). Cyber vulnerabilities pose significant corporate risks, including business interruption, breach of privacy and financial losses (Sheehan et al. 2019 ). Despite the increasing relevance for the international economy, the availability of data on cyber risks remains limited. The reasons for this are many. Firstly, it is an emerging and evolving risk; therefore, historical data sources are limited (Biener et al. 2015 ). It could also be due to the fact that, in general, institutions that have been hacked do not publish the incidents (Eling and Schnell 2016 ). The lack of data poses challenges for many areas, such as research, risk management and cybersecurity (Falco et al. 2019 ). The importance of this topic is demonstrated by the announcement of the European Council in April 2021 that a centre of excellence for cybersecurity will be established to pool investments in research, technology and industrial development. The goal of this centre is to increase the security of the internet and other critical network and information systems (European Council 2021 ).
This research takes a risk management perspective, focusing on cyber risk and considering the role of cybersecurity and cyber insurance in risk mitigation and risk transfer. The study reviews the existing literature and open data sources related to cybersecurity and cyber risk. This is the first systematic review of data availability in the general context of cyber risk and cybersecurity. By identifying and critically analysing the available datasets, this paper supports the research community by aggregating, summarising and categorising all available open datasets. In addition, further information on datasets is attached to provide deeper insights and support stakeholders engaged in cyber risk control and cybersecurity. Finally, this research paper highlights the need for open access to cyber-specific data, without price or permission barriers.
The identified open data can support cyber insurers in their efforts on sustainable product development. To date, traditional risk assessment methods have been untenable for insurance companies due to the absence of historical claims data (Sheehan et al. 2021 ). These high levels of uncertainty mean that cyber insurers are more inclined to overprice cyber risk cover (Kshetri 2018 ). Combining external data with insurance portfolio data therefore seems to be essential to improve the evaluation of the risk and thus lead to risk-adjusted pricing (Bessy-Roland et al. 2021 ). This argument is also supported by the fact that some re/insurers reported that they are working to improve their cyber pricing models (e.g. by creating or purchasing databases from external providers) (EIOPA 2018 ). Figure 1 provides an overview of pricing tools and factors considered in the estimation of cyber insurance based on the findings of EIOPA ( 2018 ) and the research of Romanosky et al. ( 2019 ). The term cyber risk refers to all cyber risks and their potential impact.
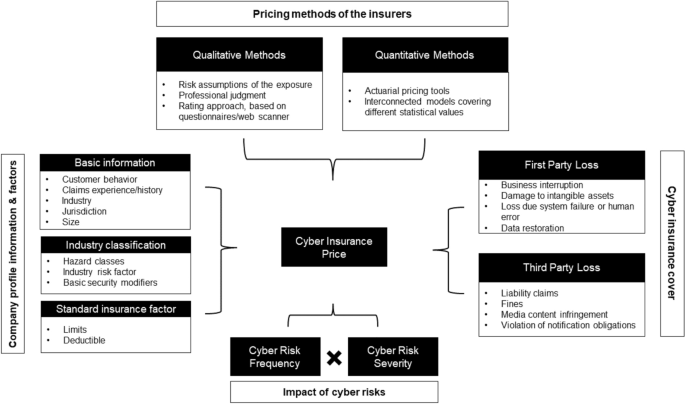
An overview of the current cyber insurance informational and methodological landscape, adapted from EIOPA ( 2018 ) and Romanosky et al. ( 2019 )
Besides the advantage of risk-adjusted pricing, the availability of open datasets helps companies benchmark their internal cyber posture and cybersecurity measures. The research can also help to improve risk awareness and corporate behaviour. Many companies still underestimate their cyber risk (Leong and Chen 2020 ). For policymakers, this research offers starting points for a comprehensive recording of cyber risks. Although in many countries, companies are obliged to report data breaches to the respective supervisory authority, this information is usually not accessible to the research community. Furthermore, the economic impact of these breaches is usually unclear.
As well as the cyber risk management community, this research also supports cybersecurity stakeholders. Researchers are provided with an up-to-date, peer-reviewed literature of available datasets showing where these datasets have been used. For example, this includes datasets that have been used to evaluate the effectiveness of countermeasures in simulated cyberattacks or to test intrusion detection systems. This reduces a time-consuming search for suitable datasets and ensures a comprehensive review of those available. Through the dataset descriptions, researchers and industry stakeholders can compare and select the most suitable datasets for their purposes. In addition, it is possible to combine the datasets from one source in the context of cybersecurity or cyber risk. This supports efficient and timely progress in cyber risk research and is beneficial given the dynamic nature of cyber risks.
Cyber risks are defined as “operational risks to information and technology assets that have consequences affecting the confidentiality, availability, and/or integrity of information or information systems” (Cebula et al. 2014 ). Prominent cyber risk events include data breaches and cyberattacks (Agrafiotis et al. 2018 ). The increasing exposure and potential impact of cyber risk have been highlighted in recent industry reports (e.g. Allianz 2021 ; World Economic Forum 2020 ). Cyberattacks on critical infrastructures are ranked 5th in the World Economic Forum's Global Risk Report. Ransomware, malware and distributed denial-of-service (DDoS) are examples of the evolving modes of a cyberattack. One example is the ransomware attack on the Colonial Pipeline, which shut down the 5500 mile pipeline system that delivers 2.5 million barrels of fuel per day and critical liquid fuel infrastructure from oil refineries to states along the U.S. East Coast (Brower and McCormick 2021 ). These and other cyber incidents have led the U.S. to strengthen its cybersecurity and introduce, among other things, a public body to analyse major cyber incidents and make recommendations to prevent a recurrence (Murphey 2021a ). Another example of the scope of cyberattacks is the ransomware NotPetya in 2017. The damage amounted to USD 10 billion, as the ransomware exploited a vulnerability in the windows system, allowing it to spread independently worldwide in the network (GAO 2021 ). In the same year, the ransomware WannaCry was launched by cybercriminals. The cyberattack on Windows software took user data hostage in exchange for Bitcoin cryptocurrency (Smart 2018 ). The victims included the National Health Service in Great Britain. As a result, ambulances were redirected to other hospitals because of information technology (IT) systems failing, leaving people in need of urgent assistance waiting. It has been estimated that 19,000 cancelled treatment appointments resulted from losses of GBP 92 million (Field 2018 ). Throughout the COVID-19 pandemic, ransomware attacks increased significantly, as working from home arrangements increased vulnerability (Murphey 2021b ).
Besides cyberattacks, data breaches can also cause high costs. Under the General Data Protection Regulation (GDPR), companies are obliged to protect personal data and safeguard the data protection rights of all individuals in the EU area. The GDPR allows data protection authorities in each country to impose sanctions and fines on organisations they find in breach. “For data breaches, the maximum fine can be €20 million or 4% of global turnover, whichever is higher” (GDPR.EU 2021 ). Data breaches often involve a large amount of sensitive data that has been accessed, unauthorised, by external parties, and are therefore considered important for information security due to their far-reaching impact (Goode et al. 2017 ). A data breach is defined as a “security incident in which sensitive, protected, or confidential data are copied, transmitted, viewed, stolen, or used by an unauthorized individual” (Freeha et al. 2021 ). Depending on the amount of data, the extent of the damage caused by a data breach can be significant, with the average cost being USD 392 million Footnote 1 (IBM Security 2020 ).
This research paper reviews the existing literature and open data sources related to cybersecurity and cyber risk, focusing on the datasets used to improve academic understanding and advance the current state-of-the-art in cybersecurity. Furthermore, important information about the available datasets is presented (e.g. use cases), and a plea is made for open data and the standardisation of cyber risk data for academic comparability and replication. The remainder of the paper is structured as follows. The next section describes the related work regarding cybersecurity and cyber risks. The third section outlines the review method used in this work and the process. The fourth section details the results of the identified literature. Further discussion is presented in the penultimate section and the final section concludes.
Related work
Due to the significance of cyber risks, several literature reviews have been conducted in this field. Eling ( 2020 ) reviewed the existing academic literature on the topic of cyber risk and cyber insurance from an economic perspective. A total of 217 papers with the term ‘cyber risk’ were identified and classified in different categories. As a result, open research questions are identified, showing that research on cyber risks is still in its infancy because of their dynamic and emerging nature. Furthermore, the author highlights that particular focus should be placed on the exchange of information between public and private actors. An improved information flow could help to measure the risk more accurately and thus make cyber risks more insurable and help risk managers to determine the right level of cyber risk for their company. In the context of cyber insurance data, Romanosky et al. ( 2019 ) analysed the underwriting process for cyber insurance and revealed how cyber insurers understand and assess cyber risks. For this research, they examined 235 American cyber insurance policies that were publicly available and looked at three components (coverage, application questionnaires and pricing). The authors state in their findings that many of the insurers used very simple, flat-rate pricing (based on a single calculation of expected loss), while others used more parameters such as the asset value of the company (or company revenue) or standard insurance metrics (e.g. deductible, limits), and the industry in the calculation. This is in keeping with Eling ( 2020 ), who states that an increased amount of data could help to make cyber risk more accurately measured and thus more insurable. Similar research on cyber insurance and data was conducted by Nurse et al. ( 2020 ). The authors examined cyber insurance practitioners' perceptions and the challenges they face in collecting and using data. In addition, gaps were identified during the research where further data is needed. The authors concluded that cyber insurance is still in its infancy, and there are still several unanswered questions (for example, cyber valuation, risk calculation and recovery). They also pointed out that a better understanding of data collection and use in cyber insurance would be invaluable for future research and practice. Bessy-Roland et al. ( 2021 ) come to a similar conclusion. They proposed a multivariate Hawkes framework to model and predict the frequency of cyberattacks. They used a public dataset with characteristics of data breaches affecting the U.S. industry. In the conclusion, the authors make the argument that an insurer has a better knowledge of cyber losses, but that it is based on a small dataset and therefore combination with external data sources seems essential to improve the assessment of cyber risks.
Several systematic reviews have been published in the area of cybersecurity (Kruse et al. 2017 ; Lee et al. 2020 ; Loukas et al. 2013 ; Ulven and Wangen 2021 ). In these papers, the authors concentrated on a specific area or sector in the context of cybersecurity. This paper adds to this extant literature by focusing on data availability and its importance to risk management and insurance stakeholders. With a priority on healthcare and cybersecurity, Kruse et al. ( 2017 ) conducted a systematic literature review. The authors identified 472 articles with the keywords ‘cybersecurity and healthcare’ or ‘ransomware’ in the databases Cumulative Index of Nursing and Allied Health Literature, PubMed and Proquest. Articles were eligible for this review if they satisfied three criteria: (1) they were published between 2006 and 2016, (2) the full-text version of the article was available, and (3) the publication is a peer-reviewed or scholarly journal. The authors found that technological development and federal policies (in the U.S.) are the main factors exposing the health sector to cyber risks. Loukas et al. ( 2013 ) conducted a review with a focus on cyber risks and cybersecurity in emergency management. The authors provided an overview of cyber risks in communication, sensor, information management and vehicle technologies used in emergency management and showed areas for which there is still no solution in the literature. Similarly, Ulven and Wangen ( 2021 ) reviewed the literature on cybersecurity risks in higher education institutions. For the literature review, the authors used the keywords ‘cyber’, ‘information threats’ or ‘vulnerability’ in connection with the terms ‘higher education, ‘university’ or ‘academia’. A similar literature review with a focus on Internet of Things (IoT) cybersecurity was conducted by Lee et al. ( 2020 ). The review revealed that qualitative approaches focus on high-level frameworks, and quantitative approaches to cybersecurity risk management focus on risk assessment and quantification of cyberattacks and impacts. In addition, the findings presented a four-step IoT cyber risk management framework that identifies, quantifies and prioritises cyber risks.
Datasets are an essential part of cybersecurity research, underlined by the following works. Ilhan Firat et al. ( 2021 ) examined various cybersecurity datasets in detail. The study was motivated by the fact that with the proliferation of the internet and smart technologies, the mode of cyberattacks is also evolving. However, in order to prevent such attacks, they must first be detected; the dissemination and further development of cybersecurity datasets is therefore critical. In their work, the authors observed studies of datasets used in intrusion detection systems. Khraisat et al. ( 2019 ) also identified a need for new datasets in the context of cybersecurity. The researchers presented a taxonomy of current intrusion detection systems, a comprehensive review of notable recent work, and an overview of the datasets commonly used for assessment purposes. In their conclusion, the authors noted that new datasets are needed because most machine-learning techniques are trained and evaluated on the knowledge of old datasets. These datasets do not contain new and comprehensive information and are partly derived from datasets from 1999. The authors noted that the core of this issue is the availability of new public datasets as well as their quality. The availability of data, how it is used, created and shared was also investigated by Zheng et al. ( 2018 ). The researchers analysed 965 cybersecurity research papers published between 2012 and 2016. They created a taxonomy of the types of data that are created and shared and then analysed the data collected via datasets. The researchers concluded that while datasets are recognised as valuable for cybersecurity research, the proportion of publicly available datasets is limited.
The main contributions of this review and what differentiates it from previous studies can be summarised as follows. First, as far as we can tell, it is the first work to summarise all available datasets on cyber risk and cybersecurity in the context of a systematic review and present them to the scientific community and cyber insurance and cybersecurity stakeholders. Second, we investigated, analysed, and made available the datasets to support efficient and timely progress in cyber risk research. And third, we enable comparability of datasets so that the appropriate dataset can be selected depending on the research area.
Methodology
Process and eligibility criteria.
The structure of this systematic review is inspired by the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) framework (Page et al. 2021 ), and the search was conducted from 3 to 10 May 2021. Due to the continuous development of cyber risks and their countermeasures, only articles published in the last 10 years were considered. In addition, only articles published in peer-reviewed journals written in English were included. As a final criterion, only articles that make use of one or more cybersecurity or cyber risk datasets met the inclusion criteria. Specifically, these studies presented new or existing datasets, used them for methods, or used them to verify new results, as well as analysed them in an economic context and pointed out their effects. The criterion was fulfilled if it was clearly stated in the abstract that one or more datasets were used. A detailed explanation of this selection criterion can be found in the ‘Study selection’ section.
Information sources
In order to cover a complete spectrum of literature, various databases were queried to collect relevant literature on the topic of cybersecurity and cyber risks. Due to the spread of related articles across multiple databases, the literature search was limited to the following four databases for simplicity: IEEE Xplore, Scopus, SpringerLink and Web of Science. This is similar to other literature reviews addressing cyber risks or cybersecurity, including Sardi et al. ( 2021 ), Franke and Brynielsson ( 2014 ), Lagerström (2019), Eling and Schnell ( 2016 ) and Eling ( 2020 ). In this paper, all databases used in the aforementioned works were considered. However, only two studies also used all the databases listed. The IEEE Xplore database contains electrical engineering, computer science, and electronics work from over 200 journals and three million conference papers (IEEE 2021 ). Scopus includes 23,400 peer-reviewed journals from more than 5000 international publishers in the areas of science, engineering, medicine, social sciences and humanities (Scopus 2021 ). SpringerLink contains 3742 journals and indexes over 10 million scientific documents (SpringerLink 2021 ). Finally, Web of Science indexes over 9200 journals in different scientific disciplines (Science 2021 ).
A search string was created and applied to all databases. To make the search efficient and reproducible, the following search string with Boolean operator was used in all databases: cybersecurity OR cyber risk AND dataset OR database. To ensure uniformity of the search across all databases, some adjustments had to be made for the respective search engines. In Scopus, for example, the Advanced Search was used, and the field code ‘Title-ABS-KEY’ was integrated into the search string. For IEEE Xplore, the search was carried out with the Search String in the Command Search and ‘All Metadata’. In the Web of Science database, the Advanced Search was used. The special feature of this search was that it had to be carried out in individual steps. The first search was carried out with the terms cybersecurity OR cyber risk with the field tag Topic (T.S. =) and the second search with dataset OR database. Subsequently, these searches were combined, which then delivered the searched articles for review. For SpringerLink, the search string was used in the Advanced Search under the category ‘Find the resources with all of the words’. After conducting this search string, 5219 studies could be found. According to the eligibility criteria (period, language and only scientific journals), 1581 studies were identified in the databases:
Scopus: 135
Springer Link: 548
Web of Science: 534
An overview of the process is given in Fig. 2 . Combined with the results from the four databases, 854 articles without duplicates were identified.
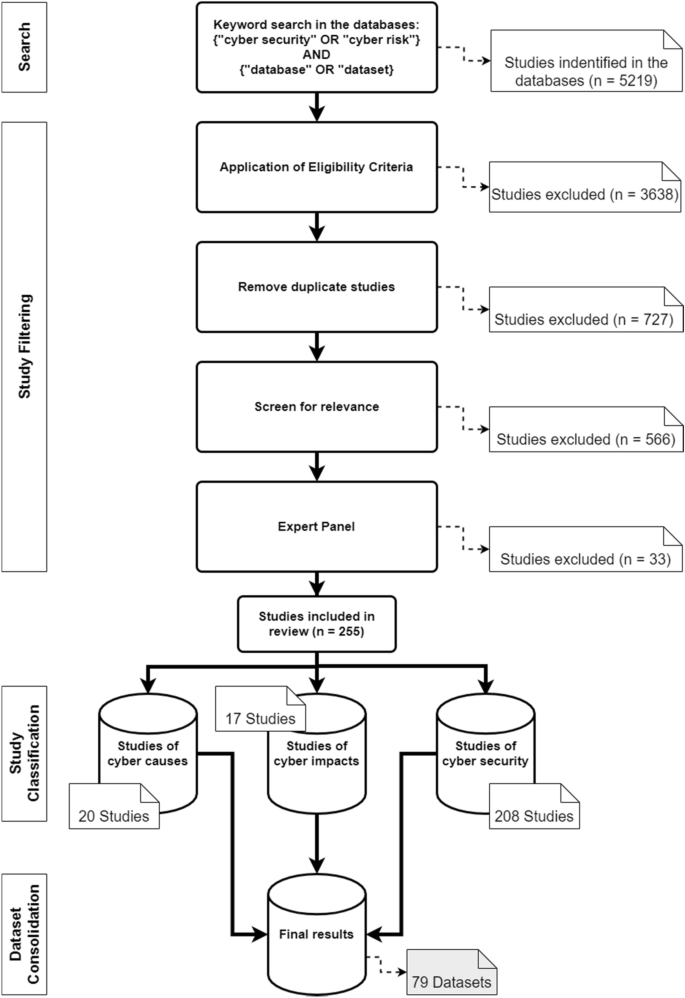
Literature search process and categorisation of the studies
Study selection
In the final step of the selection process, the articles were screened for relevance. Due to a large number of results, the abstracts were analysed in the first step of the process. The aim was to determine whether the article was relevant for the systematic review. An article fulfilled the criterion if it was recognisable in the abstract that it had made a contribution to datasets or databases with regard to cyber risks or cybersecurity. Specifically, the criterion was considered to be met if the abstract used datasets that address the causes or impacts of cyber risks, and measures in the area of cybersecurity. In this process, the number of articles was reduced to 288. The articles were then read in their entirety, and an expert panel of six people decided whether they should be used. This led to a final number of 255 articles. The years in which the articles were published and the exact number can be seen in Fig. 3 .
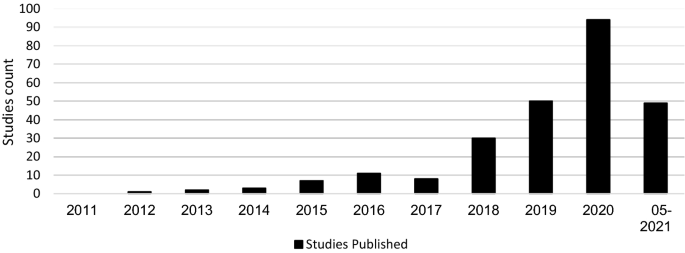
Distribution of studies
Data collection process and synthesis of the results
For the data collection process, various data were extracted from the studies, including the names of the respective creators, the name of the dataset or database and the corresponding reference. It was also determined where the data came from. In the context of accessibility, it was determined whether access is free, controlled, available for purchase or not available. It was also determined when the datasets were created and the time period referenced. The application type and domain characteristics of the datasets were identified.
This section analyses the results of the systematic literature review. The previously identified studies are divided into three categories: datasets on the causes of cyber risks, datasets on the effects of cyber risks and datasets on cybersecurity. The classification is based on the intended use of the studies. This system of classification makes it easier for stakeholders to find the appropriate datasets. The categories are evaluated individually. Although complete information is available for a large proportion of datasets, this is not true for all of them. Accordingly, the abbreviation N/A has been inserted in the respective characters to indicate that this information could not be determined by the time of submission. The term ‘use cases in the literature’ in the following and supplementary tables refers to the application areas in which the corresponding datasets were used in the literature. The areas listed there refer to the topic area on which the researchers conducted their research. Since some datasets were used interdisciplinarily, the listed use cases in the literature are correspondingly longer. Before discussing each category in the next sections, Fig. 4 provides an overview of the number of datasets found and their year of creation. Figure 5 then shows the relationship between studies and datasets in the period under consideration. Figure 6 shows the distribution of studies, their use of datasets and their creation date. The number of datasets used is higher than the number of studies because the studies often used several datasets (Table 1 ).
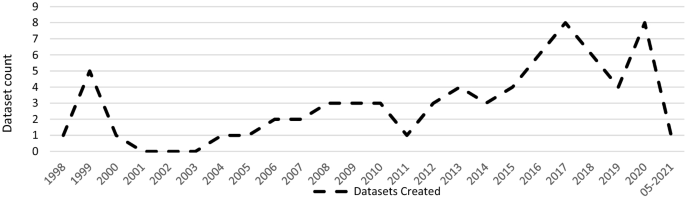
Distribution of dataset results
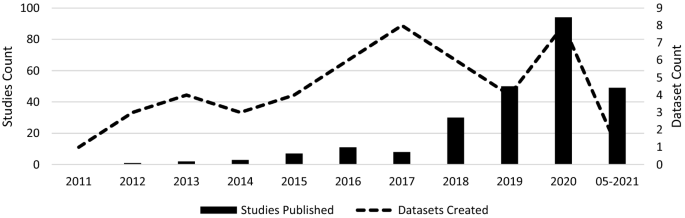
Correlation between the studies and the datasets
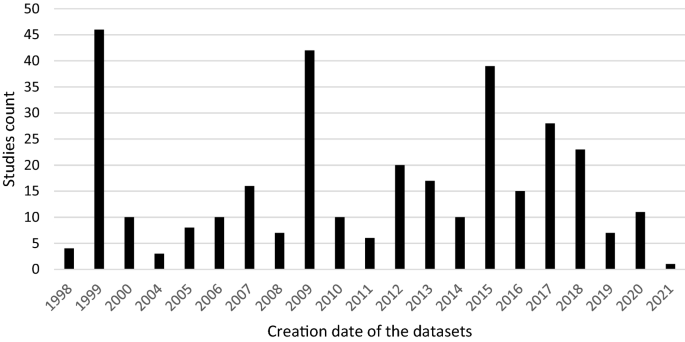
Distribution of studies and their use of datasets
Most of the datasets are generated in the U.S. (up to 58.2%). Canada and Australia rank next, with 11.3% and 5% of all the reviewed datasets, respectively.
Additionally, to create value for the datasets for the cyber insurance industry, an assessment of the applicability of each dataset has been provided for cyber insurers. This ‘Use Case Assessment’ includes the use of the data in the context of different analyses, calculation of cyber insurance premiums, and use of the information for the design of cyber insurance contracts or for additional customer services. To reasonably account for the transition of direct hyperlinks in the future, references were directed to the main websites for longevity (nearest resource point). In addition, the links to the main pages contain further information on the datasets and different versions related to the operating systems. The references were chosen in such a way that practitioners get the best overview of the respective datasets.
Case datasets
This section presents selected articles that use the datasets to analyse the causes of cyber risks. The datasets help identify emerging trends and allow pattern discovery in cyber risks. This information gives cybersecurity experts and cyber insurers the data to make better predictions and take appropriate action. For example, if certain vulnerabilities are not adequately protected, cyber insurers will demand a risk surcharge leading to an improvement in the risk-adjusted premium. Due to the capricious nature of cyber risks, existing data must be supplemented with new data sources (for example, new events, new methods or security vulnerabilities) to determine prevailing cyber exposure. The datasets of cyber risk causes could be combined with existing portfolio data from cyber insurers and integrated into existing pricing tools and factors to improve the valuation of cyber risks.
A portion of these datasets consists of several taxonomies and classifications of cyber risks. Aassal et al. ( 2020 ) propose a new taxonomy of phishing characteristics based on the interpretation and purpose of each characteristic. In comparison, Hindy et al. ( 2020 ) presented a taxonomy of network threats and the impact of current datasets on intrusion detection systems. A similar taxonomy was suggested by Kiwia et al. ( 2018 ). The authors presented a cyber kill chain-based taxonomy of banking Trojans features. The taxonomy built on a real-world dataset of 127 banking Trojans collected from December 2014 to January 2016 by a major U.K.-based financial organisation.
In the context of classification, Aamir et al. ( 2021 ) showed the benefits of machine learning for classifying port scans and DDoS attacks in a mixture of normal and attack traffic. Guo et al. ( 2020 ) presented a new method to improve malware classification based on entropy sequence features. The evaluation of this new method was conducted on different malware datasets.
To reconstruct attack scenarios and draw conclusions based on the evidence in the alert stream, Barzegar and Shajari ( 2018 ) use the DARPA2000 and MACCDC 2012 dataset for their research. Giudici and Raffinetti ( 2020 ) proposed a rank-based statistical model aimed at predicting the severity levels of cyber risk. The model used cyber risk data from the University of Milan. In contrast to the previous datasets, Skrjanc et al. ( 2018 ) used the older dataset KDD99 to monitor large-scale cyberattacks using a cauchy clustering method.
Amin et al. ( 2021 ) used a cyberattack dataset from the Canadian Institute for Cybersecurity to identify spatial clusters of countries with high rates of cyberattacks. In the context of cybercrime, Junger et al. ( 2020 ) examined crime scripts, key characteristics of the target company and the relationship between criminal effort and financial benefit. For their study, the authors analysed 300 cases of fraudulent activities against Dutch companies. With a similar focus on cybercrime, Mireles et al. ( 2019 ) proposed a metric framework to measure the effectiveness of the dynamic evolution of cyberattacks and defensive measures. To validate its usefulness, they used the DEFCON dataset.
Due to the rapidly changing nature of cyber risks, it is often impossible to obtain all information on them. Kim and Kim ( 2019 ) proposed an automated dataset generation system called CTIMiner that collects threat data from publicly available security reports and malware repositories. They released a dataset to the public containing about 640,000 records from 612 security reports published between January 2008 and 2019. A similar approach is proposed by Kim et al. ( 2020 ), using a named entity recognition system to extract core information from cyber threat reports automatically. They created a 498,000-tag dataset during their research (Ulven and Wangen 2021 ).
Within the framework of vulnerabilities and cybersecurity issues, Ulven and Wangen ( 2021 ) proposed an overview of mission-critical assets and everyday threat events, suggested a generic threat model, and summarised common cybersecurity vulnerabilities. With a focus on hospitality, Chen and Fiscus ( 2018 ) proposed several issues related to cybersecurity in this sector. They analysed 76 security incidents from the Privacy Rights Clearinghouse database. Supplementary Table 1 lists all findings that belong to the cyber causes dataset.
Impact datasets
This section outlines selected findings of the cyber impact dataset. For cyber insurers, these datasets can form an important basis for information, as they can be used to calculate cyber insurance premiums, evaluate specific cyber risks, formulate inclusions and exclusions in cyber wordings, and re-evaluate as well as supplement the data collected so far on cyber risks. For example, information on financial losses can help to better assess the loss potential of cyber risks. Furthermore, the datasets can provide insight into the frequency of occurrence of these cyber risks. The new datasets can be used to close any data gaps that were previously based on very approximate estimates or to find new results.
Eight studies addressed the costs of data breaches. For instance, Eling and Jung ( 2018 ) reviewed 3327 data breach events from 2005 to 2016 and identified an asymmetric dependence of monthly losses by breach type and industry. The authors used datasets from the Privacy Rights Clearinghouse for analysis. The Privacy Rights Clearinghouse datasets and the Breach level index database were also used by De Giovanni et al. ( 2020 ) to describe relationships between data breaches and bitcoin-related variables using the cointegration methodology. The data were obtained from the Department of Health and Human Services of healthcare facilities reporting data breaches and a national database of technical and organisational infrastructure information. Also in the context of data breaches, Algarni et al. ( 2021 ) developed a comprehensive, formal model that estimates the two components of security risks: breach cost and the likelihood of a data breach within 12 months. For their survey, the authors used two industrial reports from the Ponemon institute and VERIZON. To illustrate the scope of data breaches, Neto et al. ( 2021 ) identified 430 major data breach incidents among more than 10,000 incidents. The database created is available and covers the period 2018 to 2019.
With a direct focus on insurance, Biener et al. ( 2015 ) analysed 994 cyber loss cases from an operational risk database and investigated the insurability of cyber risks based on predefined criteria. For their study, they used data from the company SAS OpRisk Global Data. Similarly, Eling and Wirfs ( 2019 ) looked at a wide range of cyber risk events and actual cost data using the same database. They identified cyber losses and analysed them using methods from statistics and actuarial science. Using a similar reference, Farkas et al. ( 2021 ) proposed a method for analysing cyber claims based on regression trees to identify criteria for classifying and evaluating claims. Similar to Chen and Fiscus ( 2018 ), the dataset used was the Privacy Rights Clearinghouse database. Within the framework of reinsurance, Moro ( 2020 ) analysed cyber index-based information technology activity to see if index-parametric reinsurance coverage could suggest its cedant using data from a Symantec dataset.
Paté-Cornell et al. ( 2018 ) presented a general probabilistic risk analysis framework for cybersecurity in an organisation to be specified. The results are distributions of losses to cyberattacks, with and without considered countermeasures in support of risk management decisions based both on past data and anticipated incidents. The data used were from The Common Vulnerability and Exposures database and via confidential access to a database of cyberattacks on a large, U.S.-based organisation. A different conceptual framework for cyber risk classification and assessment was proposed by Sheehan et al. ( 2021 ). This framework showed the importance of proactive and reactive barriers in reducing companies’ exposure to cyber risk and quantifying the risk. Another approach to cyber risk assessment and mitigation was proposed by Mukhopadhyay et al. ( 2019 ). They estimated the probability of an attack using generalised linear models, predicted the security technology required to reduce the probability of cyberattacks, and used gamma and exponential distributions to best approximate the average loss data for each malicious attack. They also calculated the expected loss due to cyberattacks, calculated the net premium that would need to be charged by a cyber insurer, and suggested cyber insurance as a strategy to minimise losses. They used the CSI-FBI survey (1997–2010) to conduct their research.
In order to highlight the lack of data on cyber risks, Eling ( 2020 ) conducted a literature review in the areas of cyber risk and cyber insurance. Available information on the frequency, severity, and dependency structure of cyber risks was filtered out. In addition, open questions for future cyber risk research were set up. Another example of data collection on the impact of cyberattacks is provided by Sornette et al. ( 2013 ), who use a database of newspaper articles, press reports and other media to provide a predictive method to identify triggering events and potential accident scenarios and estimate their severity and frequency. A similar approach to data collection was used by Arcuri et al. ( 2020 ) to gather an original sample of global cyberattacks from newspaper reports sourced from the LexisNexis database. This collection is also used and applied to the fields of dynamic communication and cyber risk perception by Fang et al. ( 2021 ). To create a dataset of cyber incidents and disputes, Valeriano and Maness ( 2014 ) collected information on cyber interactions between rival states.
To assess trends and the scale of economic cybercrime, Levi ( 2017 ) examined datasets from different countries and their impact on crime policy. Pooser et al. ( 2018 ) investigated the trend in cyber risk identification from 2006 to 2015 and company characteristics related to cyber risk perception. The authors used a dataset of various reports from cyber insurers for their study. Walker-Roberts et al. ( 2020 ) investigated the spectrum of risk of a cybersecurity incident taking place in the cyber-physical-enabled world using the VERIS Community Database. The datasets of impacts identified are presented below. Due to overlap, some may also appear in the causes dataset (Supplementary Table 2).
Cybersecurity datasets
General intrusion detection.
General intrusion detection systems account for the largest share of countermeasure datasets. For companies or researchers focused on cybersecurity, the datasets can be used to test their own countermeasures or obtain information about potential vulnerabilities. For example, Al-Omari et al. ( 2021 ) proposed an intelligent intrusion detection model for predicting and detecting attacks in cyberspace, which was applied to dataset UNSW-NB 15. A similar approach was taken by Choras and Kozik ( 2015 ), who used machine learning to detect cyberattacks on web applications. To evaluate their method, they used the HTTP dataset CSIC 2010. For the identification of unknown attacks on web servers, Kamarudin et al. ( 2017 ) proposed an anomaly-based intrusion detection system using an ensemble classification approach. Ganeshan and Rodrigues ( 2020 ) showed an intrusion detection system approach, which clusters the database into several groups and detects the presence of intrusion in the clusters. In comparison, AlKadi et al. ( 2019 ) used a localisation-based model to discover abnormal patterns in network traffic. Hybrid models have been recommended by Bhattacharya et al. ( 2020 ) and Agrawal et al. ( 2019 ); the former is a machine-learning model based on principal component analysis for the classification of intrusion detection system datasets, while the latter is a hybrid ensemble intrusion detection system for anomaly detection using different datasets to detect patterns in network traffic that deviate from normal behaviour.
Agarwal et al. ( 2021 ) used three different machine learning algorithms in their research to find the most suitable for efficiently identifying patterns of suspicious network activity. The UNSW-NB15 dataset was used for this purpose. Kasongo and Sun ( 2020 ), Feed-Forward Deep Neural Network (FFDNN), Keshk et al. ( 2021 ), the privacy-preserving anomaly detection framework, and others also use the UNSW-NB 15 dataset as part of intrusion detection systems. The same dataset and others were used by Binbusayyis and Vaiyapuri ( 2019 ) to identify and compare key features for cyber intrusion detection. Atefinia and Ahmadi ( 2021 ) proposed a deep neural network model to reduce the false positive rate of an anomaly-based intrusion detection system. Fossaceca et al. ( 2015 ) focused in their research on the development of a framework that combined the outputs of multiple learners in order to improve the efficacy of network intrusion, and Gauthama Raman et al. ( 2020 ) presented a search algorithm based on Support Vector machine to improve the performance of the detection and false alarm rate to improve intrusion detection techniques. Ahmad and Alsemmeari ( 2020 ) targeted extreme learning machine techniques due to their good capabilities in classification problems and handling huge data. They used the NSL-KDD dataset as a benchmark.
With reference to prediction, Bakdash et al. ( 2018 ) used datasets from the U.S. Department of Defence to predict cyberattacks by malware. This dataset consists of weekly counts of cyber events over approximately seven years. Another prediction method was presented by Fan et al. ( 2018 ), which showed an improved integrated cybersecurity prediction method based on spatial-time analysis. Also, with reference to prediction, Ashtiani and Azgomi ( 2014 ) proposed a framework for the distributed simulation of cyberattacks based on high-level architecture. Kirubavathi and Anitha ( 2016 ) recommended an approach to detect botnets, irrespective of their structures, based on network traffic flow behaviour analysis and machine-learning techniques. Dwivedi et al. ( 2021 ) introduced a multi-parallel adaptive technique to utilise an adaption mechanism in the group of swarms for network intrusion detection. AlEroud and Karabatis ( 2018 ) presented an approach that used contextual information to automatically identify and query possible semantic links between different types of suspicious activities extracted from network flows.
Intrusion detection systems with a focus on IoT
In addition to general intrusion detection systems, a proportion of studies focused on IoT. Habib et al. ( 2020 ) presented an approach for converting traditional intrusion detection systems into smart intrusion detection systems for IoT networks. To enhance the process of diagnostic detection of possible vulnerabilities with an IoT system, Georgescu et al. ( 2019 ) introduced a method that uses a named entity recognition-based solution. With regard to IoT in the smart home sector, Heartfield et al. ( 2021 ) presented a detection system that is able to autonomously adjust the decision function of its underlying anomaly classification models to a smart home’s changing condition. Another intrusion detection system was suggested by Keserwani et al. ( 2021 ), which combined Grey Wolf Optimization and Particle Swam Optimization to identify various attacks for IoT networks. They used the KDD Cup 99, NSL-KDD and CICIDS-2017 to evaluate their model. Abu Al-Haija and Zein-Sabatto ( 2020 ) provide a comprehensive development of a new intelligent and autonomous deep-learning-based detection and classification system for cyberattacks in IoT communication networks that leverage the power of convolutional neural networks, abbreviated as IoT-IDCS-CNN (IoT-based Intrusion Detection and Classification System using Convolutional Neural Network). To evaluate the development, the authors used the NSL-KDD dataset. Biswas and Roy ( 2021 ) recommended a model that identifies malicious botnet traffic using novel deep-learning approaches like artificial neural networks gutted recurrent units and long- or short-term memory models. They tested their model with the Bot-IoT dataset.
With a more forensic background, Koroniotis et al. ( 2020 ) submitted a network forensic framework, which described the digital investigation phases for identifying and tracing attack behaviours in IoT networks. The suggested work was evaluated with the Bot-IoT and UINSW-NB15 datasets. With a focus on big data and IoT, Chhabra et al. ( 2020 ) presented a cyber forensic framework for big data analytics in an IoT environment using machine learning. Furthermore, the authors mentioned different publicly available datasets for machine-learning models.
A stronger focus on a mobile phones was exhibited by Alazab et al. ( 2020 ), which presented a classification model that combined permission requests and application programme interface calls. The model was tested with a malware dataset containing 27,891 Android apps. A similar approach was taken by Li et al. ( 2019a , b ), who proposed a reliable classifier for Android malware detection based on factorisation machine architecture and extraction of Android app features from manifest files and source code.
Literature reviews
In addition to the different methods and models for intrusion detection systems, various literature reviews on the methods and datasets were also found. Liu and Lang ( 2019 ) proposed a taxonomy of intrusion detection systems that uses data objects as the main dimension to classify and summarise machine learning and deep learning-based intrusion detection literature. They also presented four different benchmark datasets for machine-learning detection systems. Ahmed et al. ( 2016 ) presented an in-depth analysis of four major categories of anomaly detection techniques, which include classification, statistical, information theory and clustering. Hajj et al. ( 2021 ) gave a comprehensive overview of anomaly-based intrusion detection systems. Their article gives an overview of the requirements, methods, measurements and datasets that are used in an intrusion detection system.
Within the framework of machine learning, Chattopadhyay et al. ( 2018 ) conducted a comprehensive review and meta-analysis on the application of machine-learning techniques in intrusion detection systems. They also compared different machine learning techniques in different datasets and summarised the performance. Vidros et al. ( 2017 ) presented an overview of characteristics and methods in automatic detection of online recruitment fraud. They also published an available dataset of 17,880 annotated job ads, retrieved from the use of a real-life system. An empirical study of different unsupervised learning algorithms used in the detection of unknown attacks was presented by Meira et al. ( 2020 ).
New datasets
Kilincer et al. ( 2021 ) reviewed different intrusion detection system datasets in detail. They had a closer look at the UNS-NB15, ISCX-2012, NSL-KDD and CIDDS-001 datasets. Stojanovic et al. ( 2020 ) also provided a review on datasets and their creation for use in advanced persistent threat detection in the literature. Another review of datasets was provided by Sarker et al. ( 2020 ), who focused on cybersecurity data science as part of their research and provided an overview from a machine-learning perspective. Avila et al. ( 2021 ) conducted a systematic literature review on the use of security logs for data leak detection. They recommended a new classification of information leak, which uses the GDPR principles, identified the most widely publicly available dataset for threat detection, described the attack types in the datasets and the algorithms used for data leak detection. Tuncer et al. ( 2020 ) presented a bytecode-based detection method consisting of feature extraction using local neighbourhood binary patterns. They chose a byte-based malware dataset to investigate the performance of the proposed local neighbourhood binary pattern-based detection method. With a different focus, Mauro et al. ( 2020 ) gave an experimental overview of neural-based techniques relevant to intrusion detection. They assessed the value of neural networks using the Bot-IoT and UNSW-DB15 datasets.
Another category of results in the context of countermeasure datasets is those that were presented as new. Moreno et al. ( 2018 ) developed a database of 300 security-related accidents from European and American sources. The database contained cybersecurity-related events in the chemical and process industry. Damasevicius et al. ( 2020 ) proposed a new dataset (LITNET-2020) for network intrusion detection. The dataset is a new annotated network benchmark dataset obtained from the real-world academic network. It presents real-world examples of normal and under-attack network traffic. With a focus on IoT intrusion detection systems, Alsaedi et al. ( 2020 ) proposed a new benchmark IoT/IIot datasets for assessing intrusion detection system-enabled IoT systems. Also in the context of IoT, Vaccari et al. ( 2020 ) proposed a dataset focusing on message queue telemetry transport protocols, which can be used to train machine-learning models. To evaluate the performance of machine-learning classifiers, Mahfouz et al. ( 2020 ) created a dataset called Game Theory and Cybersecurity (GTCS). A dataset containing 22,000 malware and benign samples was constructed by Martin et al. ( 2019 ). The dataset can be used as a benchmark to test the algorithm for Android malware classification and clustering techniques. In addition, Laso et al. ( 2017 ) presented a dataset created to investigate how data and information quality estimates enable the detection of anomalies and malicious acts in cyber-physical systems. The dataset contained various cyberattacks and is publicly available.
In addition to the results described above, several other studies were found that fit into the category of countermeasures. Johnson et al. ( 2016 ) examined the time between vulnerability disclosures. Using another vulnerabilities database, Common Vulnerabilities and Exposures (CVE), Subroto and Apriyana ( 2019 ) presented an algorithm model that uses big data analysis of social media and statistical machine learning to predict cyber risks. A similar databank but with a different focus, Common Vulnerability Scoring System, was used by Chatterjee and Thekdi ( 2020 ) to present an iterative data-driven learning approach to vulnerability assessment and management for complex systems. Using the CICIDS2017 dataset to evaluate the performance, Malik et al. ( 2020 ) proposed a control plane-based orchestration for varied, sophisticated threats and attacks. The same dataset was used in another study by Lee et al. ( 2019 ), who developed an artificial security information event management system based on a combination of event profiling for data processing and different artificial network methods. To exploit the interdependence between multiple series, Fang et al. ( 2021 ) proposed a statistical framework. In order to validate the framework, the authors applied it to a dataset of enterprise-level security breaches from the Privacy Rights Clearinghouse and Identity Theft Center database. Another framework with a defensive aspect was recommended by Li et al. ( 2021 ) to increase the robustness of deep neural networks against adversarial malware evasion attacks. Sarabi et al. ( 2016 ) investigated whether and to what extent business details can help assess an organisation's risk of data breaches and the distribution of risk across different types of incidents to create policies for protection, detection and recovery from different forms of security incidents. They used data from the VERIS Community Database.
Datasets that have been classified into the cybersecurity category are detailed in Supplementary Table 3. Due to overlap, records from the previous tables may also be included.
This paper presented a systematic literature review of studies on cyber risk and cybersecurity that used datasets. Within this framework, 255 studies were fully reviewed and then classified into three different categories. Then, 79 datasets were consolidated from these studies. These datasets were subsequently analysed, and important information was selected through a process of filtering out. This information was recorded in a table and enhanced with further information as part of the literature analysis. This made it possible to create a comprehensive overview of the datasets. For example, each dataset contains a description of where the data came from and how the data has been used to date. This allows different datasets to be compared and the appropriate dataset for the use case to be selected. This research certainly has limitations, so our selection of datasets cannot necessarily be taken as a representation of all available datasets related to cyber risks and cybersecurity. For example, literature searches were conducted in four academic databases and only found datasets that were used in the literature. Many research projects also used old datasets that may no longer consider current developments. In addition, the data are often focused on only one observation and are limited in scope. For example, the datasets can only be applied to specific contexts and are also subject to further limitations (e.g. region, industry, operating system). In the context of the applicability of the datasets, it is unfortunately not possible to make a clear statement on the extent to which they can be integrated into academic or practical areas of application or how great this effort is. Finally, it remains to be pointed out that this is an overview of currently available datasets, which are subject to constant change.
Due to the lack of datasets on cyber risks in the academic literature, additional datasets on cyber risks were integrated as part of a further search. The search was conducted on the Google Dataset search portal. The search term used was ‘cyber risk datasets’. Over 100 results were found. However, due to the low significance and verifiability, only 20 selected datasets were included. These can be found in Table 2 in the “ Appendix ”.
The results of the literature review and datasets also showed that there continues to be a lack of available, open cyber datasets. This lack of data is reflected in cyber insurance, for example, as it is difficult to find a risk-based premium without a sufficient database (Nurse et al. 2020 ). The global cyber insurance market was estimated at USD 5.5 billion in 2020 (Dyson 2020 ). When compared to the USD 1 trillion global losses from cybercrime (Maleks Smith et al. 2020 ), it is clear that there exists a significant cyber risk awareness challenge for both the insurance industry and international commerce. Without comprehensive and qualitative data on cyber losses, it can be difficult to estimate potential losses from cyberattacks and price cyber insurance accordingly (GAO 2021 ). For instance, the average cyber insurance loss increased from USD 145,000 in 2019 to USD 359,000 in 2020 (FitchRatings 2021 ). Cyber insurance is an important risk management tool to mitigate the financial impact of cybercrime. This is particularly evident in the impact of different industries. In the Energy & Commodities financial markets, a ransomware attack on the Colonial Pipeline led to a substantial impact on the U.S. economy. As a result of the attack, about 45% of the U.S. East Coast was temporarily unable to obtain supplies of diesel, petrol and jet fuel. This caused the average price in the U.S. to rise 7 cents to USD 3.04 per gallon, the highest in seven years (Garber 2021 ). In addition, Colonial Pipeline confirmed that it paid a USD 4.4 million ransom to a hacker gang after the attack. Another ransomware attack occurred in the healthcare and government sector. The victim of this attack was the Irish Health Service Executive (HSE). A ransom payment of USD 20 million was demanded from the Irish government to restore services after the hack (Tidy 2021 ). In the car manufacturing sector, Miller and Valasek ( 2015 ) initiated a cyberattack that resulted in the recall of 1.4 million vehicles and cost manufacturers EUR 761 million. The risk that arises in the context of these events is the potential for the accumulation of cyber losses, which is why cyber insurers are not expanding their capacity. An example of this accumulation of cyber risks is the NotPetya malware attack, which originated in Russia, struck in Ukraine, and rapidly spread around the world, causing at least USD 10 billion in damage (GAO 2021 ). These events highlight the importance of proper cyber risk management.
This research provides cyber insurance stakeholders with an overview of cyber datasets. Cyber insurers can use the open datasets to improve their understanding and assessment of cyber risks. For example, the impact datasets can be used to better measure financial impacts and their frequencies. These data could be combined with existing portfolio data from cyber insurers and integrated with existing pricing tools and factors to better assess cyber risk valuation. Although most cyber insurers have sparse historical cyber policy and claims data, they remain too small at present for accurate prediction (Bessy-Roland et al. 2021 ). A combination of portfolio data and external datasets would support risk-adjusted pricing for cyber insurance, which would also benefit policyholders. In addition, cyber insurance stakeholders can use the datasets to identify patterns and make better predictions, which would benefit sustainable cyber insurance coverage. In terms of cyber risk cause datasets, cyber insurers can use the data to review their insurance products. For example, the data could provide information on which cyber risks have not been sufficiently considered in product design or where improvements are needed. A combination of cyber cause and cybersecurity datasets can help establish uniform definitions to provide greater transparency and clarity. Consistent terminology could lead to a more sustainable cyber market, where cyber insurers make informed decisions about the level of coverage and policyholders understand their coverage (The Geneva Association 2020).
In addition to the cyber insurance community, this research also supports cybersecurity stakeholders. The reviewed literature can be used to provide a contemporary, contextual and categorised summary of available datasets. This supports efficient and timely progress in cyber risk research and is beneficial given the dynamic nature of cyber risks. With the help of the described cybersecurity datasets and the identified information, a comparison of different datasets is possible. The datasets can be used to evaluate the effectiveness of countermeasures in simulated cyberattacks or to test intrusion detection systems.
In this paper, we conducted a systematic review of studies on cyber risk and cybersecurity databases. We found that most of the datasets are in the field of intrusion detection and machine learning and are used for technical cybersecurity aspects. The available datasets on cyber risks were relatively less represented. Due to the dynamic nature and lack of historical data, assessing and understanding cyber risk is a major challenge for cyber insurance stakeholders. To address this challenge, a greater density of cyber data is needed to support cyber insurers in risk management and researchers with cyber risk-related topics. With reference to ‘Open Science’ FAIR data (Jacobsen et al. 2020 ), mandatory reporting of cyber incidents could help improve cyber understanding, awareness and loss prevention among companies and insurers. Through greater availability of data, cyber risks can be better understood, enabling researchers to conduct more in-depth research into these risks. Companies could incorporate this new knowledge into their corporate culture to reduce cyber risks. For insurance companies, this would have the advantage that all insurers would have the same understanding of cyber risks, which would support sustainable risk-based pricing. In addition, common definitions of cyber risks could be derived from new data.
The cybersecurity databases summarised and categorised in this research could provide a different perspective on cyber risks that would enable the formulation of common definitions in cyber policies. The datasets can help companies addressing cybersecurity and cyber risk as part of risk management assess their internal cyber posture and cybersecurity measures. The paper can also help improve risk awareness and corporate behaviour, and provides the research community with a comprehensive overview of peer-reviewed datasets and other available datasets in the area of cyber risk and cybersecurity. This approach is intended to support the free availability of data for research. The complete tabulated review of the literature is included in the Supplementary Material.
This work provides directions for several paths of future work. First, there are currently few publicly available datasets for cyber risk and cybersecurity. The older datasets that are still widely used no longer reflect today's technical environment. Moreover, they can often only be used in one context, and the scope of the samples is very limited. It would be of great value if more datasets were publicly available that reflect current environmental conditions. This could help intrusion detection systems to consider current events and thus lead to a higher success rate. It could also compensate for the disadvantages of older datasets by collecting larger quantities of samples and making this contextualisation more widespread. Another area of research may be the integratability and adaptability of cybersecurity and cyber risk datasets. For example, it is often unclear to what extent datasets can be integrated or adapted to existing data. For cyber risks and cybersecurity, it would be helpful to know what requirements need to be met or what is needed to use the datasets appropriately. In addition, it would certainly be helpful to know whether datasets can be modified to be used for cyber risks or cybersecurity. Finally, the ability for stakeholders to identify machine-readable cybersecurity datasets would be useful because it would allow for even clearer delineations or comparisons between datasets. Due to the lack of publicly available datasets, concrete benchmarks often cannot be applied.
Average cost of a breach of more than 50 million records.
Aamir, M., S.S.H. Rizvi, M.A. Hashmani, M. Zubair, and J. Ahmad. 2021. Machine learning classification of port scanning and DDoS attacks: A comparative analysis. Mehran University Research Journal of Engineering and Technology 40 (1): 215–229. https://doi.org/10.22581/muet1982.2101.19 .
Article Google Scholar
Aamir, M., and S.M.A. Zaidi. 2019. DDoS attack detection with feature engineering and machine learning: The framework and performance evaluation. International Journal of Information Security 18 (6): 761–785. https://doi.org/10.1007/s10207-019-00434-1 .
Aassal, A. El, S. Baki, A. Das, and R.M. Verma. 2020. 2020. An in-depth benchmarking and evaluation of phishing detection research for security needs. IEEE Access 8: 22170–22192. https://doi.org/10.1109/ACCESS.2020.2969780 .
Abu Al-Haija, Q., and S. Zein-Sabatto. 2020. An efficient deep-learning-based detection and classification system for cyber-attacks in IoT communication networks. Electronics 9 (12): 26. https://doi.org/10.3390/electronics9122152 .
Adhikari, U., T.H. Morris, and S.Y. Pan. 2018. Applying Hoeffding adaptive trees for real-time cyber-power event and intrusion classification. IEEE Transactions on Smart Grid 9 (5): 4049–4060. https://doi.org/10.1109/tsg.2017.2647778 .
Agarwal, A., P. Sharma, M. Alshehri, A.A. Mohamed, and O. Alfarraj. 2021. Classification model for accuracy and intrusion detection using machine learning approach. PeerJ Computer Science . https://doi.org/10.7717/peerj-cs.437 .
Agrafiotis, I., J.R.C.. Nurse, M. Goldsmith, S. Creese, and D. Upton. 2018. A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate. Journal of Cybersecurity 4: tyy006.
Agrawal, A., S. Mohammed, and J. Fiaidhi. 2019. Ensemble technique for intruder detection in network traffic. International Journal of Security and Its Applications 13 (3): 1–8. https://doi.org/10.33832/ijsia.2019.13.3.01 .
Ahmad, I., and R.A. Alsemmeari. 2020. Towards improving the intrusion detection through ELM (extreme learning machine). CMC Computers Materials & Continua 65 (2): 1097–1111. https://doi.org/10.32604/cmc.2020.011732 .
Ahmed, M., A.N. Mahmood, and J.K. Hu. 2016. A survey of network anomaly detection techniques. Journal of Network and Computer Applications 60: 19–31. https://doi.org/10.1016/j.jnca.2015.11.016 .
Al-Jarrah, O.Y., O. Alhussein, P.D. Yoo, S. Muhaidat, K. Taha, and K. Kim. 2016. Data randomization and cluster-based partitioning for Botnet intrusion detection. IEEE Transactions on Cybernetics 46 (8): 1796–1806. https://doi.org/10.1109/TCYB.2015.2490802 .
Al-Mhiqani, M.N., R. Ahmad, Z.Z. Abidin, W. Yassin, A. Hassan, K.H. Abdulkareem, N.S. Ali, and Z. Yunos. 2020. A review of insider threat detection: Classification, machine learning techniques, datasets, open challenges, and recommendations. Applied Sciences—Basel 10 (15): 41. https://doi.org/10.3390/app10155208 .
Al-Omari, M., M. Rawashdeh, F. Qutaishat, M. Alshira’H, and N. Ababneh. 2021. An intelligent tree-based intrusion detection model for cyber security. Journal of Network and Systems Management 29 (2): 18. https://doi.org/10.1007/s10922-021-09591-y .
Alabdallah, A., and M. Awad. 2018. Using weighted Support Vector Machine to address the imbalanced classes problem of Intrusion Detection System. KSII Transactions on Internet and Information Systems 12 (10): 5143–5158. https://doi.org/10.3837/tiis.2018.10.027 .
Alazab, M., M. Alazab, A. Shalaginov, A. Mesleh, and A. Awajan. 2020. Intelligent mobile malware detection using permission requests and API calls. Future Generation Computer Systems—the International Journal of eScience 107: 509–521. https://doi.org/10.1016/j.future.2020.02.002 .
Albahar, M.A., R.A. Al-Falluji, and M. Binsawad. 2020. An empirical comparison on malicious activity detection using different neural network-based models. IEEE Access 8: 61549–61564. https://doi.org/10.1109/ACCESS.2020.2984157 .
AlEroud, A.F., and G. Karabatis. 2018. Queryable semantics to detect cyber-attacks: A flow-based detection approach. IEEE Transactions on Systems, Man, and Cybernetics: Systems 48 (2): 207–223. https://doi.org/10.1109/TSMC.2016.2600405 .
Algarni, A.M., V. Thayananthan, and Y.K. Malaiya. 2021. Quantitative assessment of cybersecurity risks for mitigating data breaches in business systems. Applied Sciences (switzerland) . https://doi.org/10.3390/app11083678 .
Alhowaide, A., I. Alsmadi, and J. Tang. 2021. Towards the design of real-time autonomous IoT NIDS. Cluster Computing—the Journal of Networks Software Tools and Applications . https://doi.org/10.1007/s10586-021-03231-5 .
Ali, S., and Y. Li. 2019. Learning multilevel auto-encoders for DDoS attack detection in smart grid network. IEEE Access 7: 108647–108659. https://doi.org/10.1109/ACCESS.2019.2933304 .
AlKadi, O., N. Moustafa, B. Turnbull, and K.K.R. Choo. 2019. Mixture localization-based outliers models for securing data migration in cloud centers. IEEE Access 7: 114607–114618. https://doi.org/10.1109/ACCESS.2019.2935142 .
Allianz. 2021. Allianz Risk Barometer. https://www.agcs.allianz.com/content/dam/onemarketing/agcs/agcs/reports/Allianz-Risk-Barometer-2021.pdf . Accessed 15 May 2021.
Almiani, M., A. AbuGhazleh, A. Al-Rahayfeh, S. Atiewi, and Razaque, A. 2020. Deep recurrent neural network for IoT intrusion detection system. Simulation Modelling Practice and Theory 101: 102031. https://doi.org/10.1016/j.simpat.2019.102031
Alsaedi, A., N. Moustafa, Z. Tari, A. Mahmood, and A. Anwar. 2020. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 8: 165130–165150. https://doi.org/10.1109/access.2020.3022862 .
Alsamiri, J., and K. Alsubhi. 2019. Internet of Things cyber attacks detection using machine learning. International Journal of Advanced Computer Science and Applications 10 (12): 627–634.
Alsharafat, W. 2013. Applying artificial neural network and eXtended classifier system for network intrusion detection. International Arab Journal of Information Technology 10 (3): 230–238.
Google Scholar
Amin, R.W., H.E. Sevil, S. Kocak, G. Francia III., and P. Hoover. 2021. The spatial analysis of the malicious uniform resource locators (URLs): 2016 dataset case study. Information (switzerland) 12 (1): 1–18. https://doi.org/10.3390/info12010002 .
Arcuri, M.C., L.Z. Gai, F. Ielasi, and E. Ventisette. 2020. Cyber attacks on hospitality sector: Stock market reaction. Journal of Hospitality and Tourism Technology 11 (2): 277–290. https://doi.org/10.1108/jhtt-05-2019-0080 .
Arp, D., M. Spreitzenbarth, M. Hubner, H. Gascon, K. Rieck, and C.E.R.T. Siemens. 2014. Drebin: Effective and explainable detection of android malware in your pocket. In Ndss 14: 23–26.
Ashtiani, M., and M.A. Azgomi. 2014. A distributed simulation framework for modeling cyber attacks and the evaluation of security measures. Simulation 90 (9): 1071–1102. https://doi.org/10.1177/0037549714540221 .
Atefinia, R., and M. Ahmadi. 2021. Network intrusion detection using multi-architectural modular deep neural network. Journal of Supercomputing 77 (4): 3571–3593. https://doi.org/10.1007/s11227-020-03410-y .
Avila, R., R. Khoury, R. Khoury, and F. Petrillo. 2021. Use of security logs for data leak detection: A systematic literature review. Security and Communication Networks 2021: 29. https://doi.org/10.1155/2021/6615899 .
Azeez, N.A., T.J. Ayemobola, S. Misra, R. Maskeliunas, and R. Damasevicius. 2019. Network Intrusion Detection with a Hashing Based Apriori Algorithm Using Hadoop MapReduce. Computers 8 (4): 15. https://doi.org/10.3390/computers8040086 .
Bakdash, J.Z., S. Hutchinson, E.G. Zaroukian, L.R. Marusich, S. Thirumuruganathan, C. Sample, B. Hoffman, and G. Das. 2018. Malware in the future forecasting of analyst detection of cyber events. Journal of Cybersecurity . https://doi.org/10.1093/cybsec/tyy007 .
Barletta, V.S., D. Caivano, A. Nannavecchia, and M. Scalera. 2020. Intrusion detection for in-vehicle communication networks: An unsupervised Kohonen SOM approach. Future Internet . https://doi.org/10.3390/FI12070119 .
Barzegar, M., and M. Shajari. 2018. Attack scenario reconstruction using intrusion semantics. Expert Systems with Applications 108: 119–133. https://doi.org/10.1016/j.eswa.2018.04.030 .
Bessy-Roland, Y., A. Boumezoued, and C. Hillairet. 2021. Multivariate Hawkes process for cyber insurance. Annals of Actuarial Science 15 (1): 14–39.
Bhardwaj, A., V. Mangat, and R. Vig. 2020. Hyperband tuned deep neural network with well posed stacked sparse AutoEncoder for detection of DDoS attacks in cloud. IEEE Access 8: 181916–181929. https://doi.org/10.1109/ACCESS.2020.3028690 .
Bhati, B.S., C.S. Rai, B. Balamurugan, and F. Al-Turjman. 2020. An intrusion detection scheme based on the ensemble of discriminant classifiers. Computers & Electrical Engineering 86: 9. https://doi.org/10.1016/j.compeleceng.2020.106742 .
Bhattacharya, S., S.S.R. Krishnan, P.K.R. Maddikunta, R. Kaluri, S. Singh, T.R. Gadekallu, M. Alazab, and U. Tariq. 2020. A novel PCA-firefly based XGBoost classification model for intrusion detection in networks using GPU. Electronics 9 (2): 16. https://doi.org/10.3390/electronics9020219 .
Bibi, I., A. Akhunzada, J. Malik, J. Iqbal, A. Musaddiq, and S. Kim. 2020. A dynamic DL-driven architecture to combat sophisticated android malware. IEEE Access 8: 129600–129612. https://doi.org/10.1109/ACCESS.2020.3009819 .
Biener, C., M. Eling, and J.H. Wirfs. 2015. Insurability of cyber risk: An empirical analysis. The Geneva Papers on Risk and Insurance—Issues and Practice 40 (1): 131–158. https://doi.org/10.1057/gpp.2014.19 .
Binbusayyis, A., and T. Vaiyapuri. 2019. Identifying and benchmarking key features for cyber intrusion detection: An ensemble approach. IEEE Access 7: 106495–106513. https://doi.org/10.1109/ACCESS.2019.2929487 .
Biswas, R., and S. Roy. 2021. Botnet traffic identification using neural networks. Multimedia Tools and Applications . https://doi.org/10.1007/s11042-021-10765-8 .
Bouyeddou, B., F. Harrou, B. Kadri, and Y. Sun. 2021. Detecting network cyber-attacks using an integrated statistical approach. Cluster Computing—the Journal of Networks Software Tools and Applications 24 (2): 1435–1453. https://doi.org/10.1007/s10586-020-03203-1 .
Bozkir, A.S., and M. Aydos. 2020. LogoSENSE: A companion HOG based logo detection scheme for phishing web page and E-mail brand recognition. Computers & Security 95: 18. https://doi.org/10.1016/j.cose.2020.101855 .
Brower, D., and M. McCormick. 2021. Colonial pipeline resumes operations following ransomware attack. Financial Times .
Cai, H., F. Zhang, and A. Levi. 2019. An unsupervised method for detecting shilling attacks in recommender systems by mining item relationship and identifying target items. The Computer Journal 62 (4): 579–597. https://doi.org/10.1093/comjnl/bxy124 .
Cebula, J.J., M.E. Popeck, and L.R. Young. 2014. A Taxonomy of Operational Cyber Security Risks Version 2 .
Chadza, T., K.G. Kyriakopoulos, and S. Lambotharan. 2020. Learning to learn sequential network attacks using hidden Markov models. IEEE Access 8: 134480–134497. https://doi.org/10.1109/ACCESS.2020.3011293 .
Chatterjee, S., and S. Thekdi. 2020. An iterative learning and inference approach to managing dynamic cyber vulnerabilities of complex systems. Reliability Engineering and System Safety . https://doi.org/10.1016/j.ress.2019.106664 .
Chattopadhyay, M., R. Sen, and S. Gupta. 2018. A comprehensive review and meta-analysis on applications of machine learning techniques in intrusion detection. Australasian Journal of Information Systems 22: 27.
Chen, H.S., and J. Fiscus. 2018. The inhospitable vulnerability: A need for cybersecurity risk assessment in the hospitality industry. Journal of Hospitality and Tourism Technology 9 (2): 223–234. https://doi.org/10.1108/JHTT-07-2017-0044 .
Chhabra, G.S., V.P. Singh, and M. Singh. 2020. Cyber forensics framework for big data analytics in IoT environment using machine learning. Multimedia Tools and Applications 79 (23–24): 15881–15900. https://doi.org/10.1007/s11042-018-6338-1 .
Chiba, Z., N. Abghour, K. Moussaid, A. Elomri, and M. Rida. 2019. Intelligent approach to build a Deep Neural Network based IDS for cloud environment using combination of machine learning algorithms. Computers and Security 86: 291–317. https://doi.org/10.1016/j.cose.2019.06.013 .
Choras, M., and R. Kozik. 2015. Machine learning techniques applied to detect cyber attacks on web applications. Logic Journal of the IGPL 23 (1): 45–56. https://doi.org/10.1093/jigpal/jzu038 .
Chowdhury, S., M. Khanzadeh, R. Akula, F. Zhang, S. Zhang, H. Medal, M. Marufuzzaman, and L. Bian. 2017. Botnet detection using graph-based feature clustering. Journal of Big Data 4 (1): 14. https://doi.org/10.1186/s40537-017-0074-7 .
Cost Of A Cyber Incident: Systematic Review And Cross-Validation, Cybersecurity & Infrastructure Agency , 1, https://www.cisa.gov/sites/default/files/publications/CISA-OCE_Cost_of_Cyber_Incidents_Study-FINAL_508.pdf (2020).
D’Hooge, L., T. Wauters, B. Volckaert, and F. De Turck. 2019. Classification hardness for supervised learners on 20 years of intrusion detection data. IEEE Access 7: 167455–167469. https://doi.org/10.1109/access.2019.2953451 .
Damasevicius, R., A. Venckauskas, S. Grigaliunas, J. Toldinas, N. Morkevicius, T. Aleliunas, and P. Smuikys. 2020. LITNET-2020: An annotated real-world network flow dataset for network intrusion detection. Electronics 9 (5): 23. https://doi.org/10.3390/electronics9050800 .
De Giovanni, A.L.D., and M. Pirra. 2020. On the determinants of data breaches: A cointegration analysis. Decisions in Economics and Finance . https://doi.org/10.1007/s10203-020-00301-y .
Deng, L., D. Li, X. Yao, and H. Wang. 2019. Retracted Article: Mobile network intrusion detection for IoT system based on transfer learning algorithm. Cluster Computing 22 (4): 9889–9904. https://doi.org/10.1007/s10586-018-1847-2 .
Donkal, G., and G.K. Verma. 2018. A multimodal fusion based framework to reinforce IDS for securing Big Data environment using Spark. Journal of Information Security and Applications 43: 1–11. https://doi.org/10.1016/j.jisa.2018.10.001 .
Dunn, C., N. Moustafa, and B. Turnbull. 2020. Robustness evaluations of sustainable machine learning models against data Poisoning attacks in the Internet of Things. Sustainability 12 (16): 17. https://doi.org/10.3390/su12166434 .
Dwivedi, S., M. Vardhan, and S. Tripathi. 2021. Multi-parallel adaptive grasshopper optimization technique for detecting anonymous attacks in wireless networks. Wireless Personal Communications . https://doi.org/10.1007/s11277-021-08368-5 .
Dyson, B. 2020. COVID-19 crisis could be ‘watershed’ for cyber insurance, says Swiss Re exec. https://www.spglobal.com/marketintelligence/en/news-insights/latest-news-headlines/covid-19-crisis-could-be-watershed-for-cyber-insurance-says-swiss-re-exec-59197154 . Accessed 7 May 2020.
EIOPA. 2018. Understanding cyber insurance—a structured dialogue with insurance companies. https://www.eiopa.europa.eu/sites/default/files/publications/reports/eiopa_understanding_cyber_insurance.pdf . Accessed 28 May 2018
Elijah, A.V., A. Abdullah, N.Z. JhanJhi, M. Supramaniam, and O.B. Abdullateef. 2019. Ensemble and deep-learning methods for two-class and multi-attack anomaly intrusion detection: An empirical study. International Journal of Advanced Computer Science and Applications 10 (9): 520–528.
Eling, M., and K. Jung. 2018. Copula approaches for modeling cross-sectional dependence of data breach losses. Insurance Mathematics & Economics 82: 167–180. https://doi.org/10.1016/j.insmatheco.2018.07.003 .
Eling, M., and W. Schnell. 2016. What do we know about cyber risk and cyber risk insurance? Journal of Risk Finance 17 (5): 474–491. https://doi.org/10.1108/jrf-09-2016-0122 .
Eling, M., and J. Wirfs. 2019. What are the actual costs of cyber risk events? European Journal of Operational Research 272 (3): 1109–1119. https://doi.org/10.1016/j.ejor.2018.07.021 .
Eling, M. 2020. Cyber risk research in business and actuarial science. European Actuarial Journal 10 (2): 303–333.
Elmasry, W., A. Akbulut, and A.H. Zaim. 2019. Empirical study on multiclass classification-based network intrusion detection. Computational Intelligence 35 (4): 919–954. https://doi.org/10.1111/coin.12220 .
Elsaid, S.A., and N.S. Albatati. 2020. An optimized collaborative intrusion detection system for wireless sensor networks. Soft Computing 24 (16): 12553–12567. https://doi.org/10.1007/s00500-020-04695-0 .
Estepa, R., J.E. Díaz-Verdejo, A. Estepa, and G. Madinabeitia. 2020. How much training data is enough? A case study for HTTP anomaly-based intrusion detection. IEEE Access 8: 44410–44425. https://doi.org/10.1109/ACCESS.2020.2977591 .
European Council. 2021. Cybersecurity: how the EU tackles cyber threats. https://www.consilium.europa.eu/en/policies/cybersecurity/ . Accessed 10 May 2021
Falco, G. et al. 2019. Cyber risk research impeded by disciplinary barriers. Science (American Association for the Advancement of Science) 366 (6469): 1066–1069.
Fan, Z.J., Z.P. Tan, C.X. Tan, and X. Li. 2018. An improved integrated prediction method of cyber security situation based on spatial-time analysis. Journal of Internet Technology 19 (6): 1789–1800. https://doi.org/10.3966/160792642018111906015 .
Fang, Z.J., M.C. Xu, S.H. Xu, and T.Z. Hu. 2021. A framework for predicting data breach risk: Leveraging dependence to cope with sparsity. IEEE Transactions on Information Forensics and Security 16: 2186–2201. https://doi.org/10.1109/tifs.2021.3051804 .
Farkas, S., O. Lopez, and M. Thomas. 2021. Cyber claim analysis using Generalized Pareto regression trees with applications to insurance. Insurance: Mathematics and Economics 98: 92–105. https://doi.org/10.1016/j.insmatheco.2021.02.009 .
Farsi, H., A. Fanian, and Z. Taghiyarrenani. 2019. A novel online state-based anomaly detection system for process control networks. International Journal of Critical Infrastructure Protection 27: 11. https://doi.org/10.1016/j.ijcip.2019.100323 .
Ferrag, M.A., L. Maglaras, S. Moschoyiannis, and H. Janicke. 2020. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. Journal of Information Security and Applications 50: 19. https://doi.org/10.1016/j.jisa.2019.102419 .
Field, M. 2018. WannaCry cyber attack cost the NHS £92m as 19,000 appointments cancelled. https://www.telegraph.co.uk/technology/2018/10/11/wannacry-cyber-attack-cost-nhs-92m-19000-appointments-cancelled/ . Accessed 9 May 2018.
FitchRatings. 2021. U.S. Cyber Insurance Market Update (Spike in Claims Leads to Decline in 2020 Underwriting Performance). https://www.fitchratings.com/research/insurance/us-cyber-insurance-market-update-spike-in-claims-leads-to-decline-in-2020-underwriting-performance-26-05-2021 .
Fossaceca, J.M., T.A. Mazzuchi, and S. Sarkani. 2015. MARK-ELM: Application of a novel Multiple Kernel Learning framework for improving the robustness of network intrusion detection. Expert Systems with Applications 42 (8): 4062–4080. https://doi.org/10.1016/j.eswa.2014.12.040 .
Franke, U., and J. Brynielsson. 2014. Cyber situational awareness–a systematic review of the literature. Computers & security 46: 18–31.
Freeha, K., K.J. Hwan, M. Lars, and M. Robin. 2021. Data breach management: An integrated risk model. Information & Management 58 (1): 103392. https://doi.org/10.1016/j.im.2020.103392 .
Ganeshan, R., and P. Rodrigues. 2020. Crow-AFL: Crow based adaptive fractional lion optimization approach for the intrusion detection. Wireless Personal Communications 111 (4): 2065–2089. https://doi.org/10.1007/s11277-019-06972-0 .
GAO. 2021. CYBER INSURANCE—Insurers and policyholders face challenges in an evolving market. https://www.gao.gov/assets/gao-21-477.pdf . Accessed 16 May 2021.
Garber, J. 2021. Colonial Pipeline fiasco foreshadows impact of Biden energy policy. https://www.foxbusiness.com/markets/colonial-pipeline-fiasco-foreshadows-impact-of-biden-energy-policy . Accessed 4 May 2021.
Gauthama Raman, M.R., N. Somu, S. Jagarapu, T. Manghnani, T. Selvam, K. Krithivasan, and V.S. Shankar Sriram. 2020. An efficient intrusion detection technique based on support vector machine and improved binary gravitational search algorithm. Artificial Intelligence Review 53 (5): 3255–3286. https://doi.org/10.1007/s10462-019-09762-z .
Gavel, S., A.S. Raghuvanshi, and S. Tiwari. 2021. Distributed intrusion detection scheme using dual-axis dimensionality reduction for Internet of things (IoT). Journal of Supercomputing . https://doi.org/10.1007/s11227-021-03697-5 .
GDPR.EU. 2021. FAQ. https://gdpr.eu/faq/ . Accessed 10 May 2021.
Georgescu, T.M., B. Iancu, and M. Zurini. 2019. Named-entity-recognition-based automated system for diagnosing cybersecurity situations in IoT networks. Sensors (switzerland) . https://doi.org/10.3390/s19153380 .
Giudici, P., and E. Raffinetti. 2020. Cyber risk ordering with rank-based statistical models. AStA Advances in Statistical Analysis . https://doi.org/10.1007/s10182-020-00387-0 .
Goh, J., S. Adepu, K.N. Junejo, and A. Mathur. 2016. A dataset to support research in the design of secure water treatment systems. In CRITIS.
Gong, X.Y., J.L. Lu, Y.F. Zhou, H. Qiu, and R. He. 2021. Model uncertainty based annotation error fixing for web attack detection. Journal of Signal Processing Systems for Signal Image and Video Technology 93 (2–3): 187–199. https://doi.org/10.1007/s11265-019-01494-1 .
Goode, S., H. Hoehle, V. Venkatesh, and S.A. Brown. 2017. USER compensation as a data breach recovery action: An investigation of the sony playstation network breach. MIS Quarterly 41 (3): 703–727.
Guo, H., S. Huang, C. Huang, Z. Pan, M. Zhang, and F. Shi. 2020. File entropy signal analysis combined with wavelet decomposition for malware classification. IEEE Access 8: 158961–158971. https://doi.org/10.1109/ACCESS.2020.3020330 .
Habib, M., I. Aljarah, and H. Faris. 2020. A Modified multi-objective particle swarm optimizer-based Lévy flight: An approach toward intrusion detection in Internet of Things. Arabian Journal for Science and Engineering 45 (8): 6081–6108. https://doi.org/10.1007/s13369-020-04476-9 .
Hajj, S., R. El Sibai, J.B. Abdo, J. Demerjian, A. Makhoul, and C. Guyeux. 2021. Anomaly-based intrusion detection systems: The requirements, methods, measurements, and datasets. Transactions on Emerging Telecommunications Technologies 32 (4): 36. https://doi.org/10.1002/ett.4240 .
Heartfield, R., G. Loukas, A. Bezemskij, and E. Panaousis. 2021. Self-configurable cyber-physical intrusion detection for smart homes using reinforcement learning. IEEE Transactions on Information Forensics and Security 16: 1720–1735. https://doi.org/10.1109/tifs.2020.3042049 .
Hemo, B., T. Gafni, K. Cohen, and Q. Zhao. 2020. Searching for anomalies over composite hypotheses. IEEE Transactions on Signal Processing 68: 1181–1196. https://doi.org/10.1109/TSP.2020.2971438
Hindy, H., D. Brosset, E. Bayne, A.K. Seeam, C. Tachtatzis, R. Atkinson, and X. Bellekens. 2020. A taxonomy of network threats and the effect of current datasets on intrusion detection systems. IEEE Access 8: 104650–104675. https://doi.org/10.1109/ACCESS.2020.3000179 .
Hong, W., D. Huang, C. Chen, and J. Lee. 2020. Towards accurate and efficient classification of power system contingencies and cyber-attacks using recurrent neural networks. IEEE Access 8: 123297–123309. https://doi.org/10.1109/ACCESS.2020.3007609 .
Husák, M., M. Zádník, V. Bartos, and P. Sokol. 2020. Dataset of intrusion detection alerts from a sharing platform. Data in Brief 33: 106530.
IBM Security. 2020. Cost of a Data breach Report. https://www.capita.com/sites/g/files/nginej291/files/2020-08/Ponemon-Global-Cost-of-Data-Breach-Study-2020.pdf . Accessed 19 May 2021.
IEEE. 2021. IEEE Quick Facts. https://www.ieee.org/about/at-a-glance.html . Accessed 11 May 2021.
Kilincer, I.F., F. Ertam, and S. Abdulkadir. 2021. Machine learning methods for cyber security intrusion detection: Datasets and comparative study. Computer Networks 188: 107840. https://doi.org/10.1016/j.comnet.2021.107840 .
Jaber, A.N., and S. Ul Rehman. 2020. FCM-SVM based intrusion detection system for cloud computing environment. Cluster Computing—the Journal of Networks Software Tools and Applications 23 (4): 3221–3231. https://doi.org/10.1007/s10586-020-03082-6 .
Jacobs, J., S. Romanosky, B. Edwards, M. Roytman, and I. Adjerid. 2019. Exploit prediction scoring system (epss). arXiv:1908.04856
Jacobsen, A. et al. 2020. FAIR principles: Interpretations and implementation considerations. Data Intelligence 2 (1–2): 10–29. https://doi.org/10.1162/dint_r_00024 .
Jahromi, A.N., S. Hashemi, A. Dehghantanha, R.M. Parizi, and K.K.R. Choo. 2020. An enhanced stacked LSTM method with no random initialization for malware threat hunting in safety and time-critical systems. IEEE Transactions on Emerging Topics in Computational Intelligence 4 (5): 630–640. https://doi.org/10.1109/TETCI.2019.2910243 .
Jang, S., S. Li, and Y. Sung. 2020. FastText-based local feature visualization algorithm for merged image-based malware classification framework for cyber security and cyber defense. Mathematics 8 (3): 13. https://doi.org/10.3390/math8030460 .
Javeed, D., T.H. Gao, and M.T. Khan. 2021. SDN-enabled hybrid DL-driven framework for the detection of emerging cyber threats in IoT. Electronics 10 (8): 16. https://doi.org/10.3390/electronics10080918 .
Johnson, P., D. Gorton, R. Lagerstrom, and M. Ekstedt. 2016. Time between vulnerability disclosures: A measure of software product vulnerability. Computers & Security 62: 278–295. https://doi.org/10.1016/j.cose.2016.08.004 .
Johnson, P., R. Lagerström, M. Ekstedt, and U. Franke. 2018. Can the common vulnerability scoring system be trusted? A Bayesian analysis. IEEE Transactions on Dependable and Secure Computing 15 (6): 1002–1015. https://doi.org/10.1109/TDSC.2016.2644614 .
Junger, M., V. Wang, and M. Schlömer. 2020. Fraud against businesses both online and offline: Crime scripts, business characteristics, efforts, and benefits. Crime Science 9 (1): 13. https://doi.org/10.1186/s40163-020-00119-4 .
Kalutarage, H.K., H.N. Nguyen, and S.A. Shaikh. 2017. Towards a threat assessment framework for apps collusion. Telecommunication Systems 66 (3): 417–430. https://doi.org/10.1007/s11235-017-0296-1 .
Kamarudin, M.H., C. Maple, T. Watson, and N.S. Safa. 2017. A LogitBoost-based algorithm for detecting known and unknown web attacks. IEEE Access 5: 26190–26200. https://doi.org/10.1109/ACCESS.2017.2766844 .
Kasongo, S.M., and Y.X. Sun. 2020. A deep learning method with wrapper based feature extraction for wireless intrusion detection system. Computers & Security 92: 15. https://doi.org/10.1016/j.cose.2020.101752 .
Keserwani, P.K., M.C. Govil, E.S. Pilli, and P. Govil. 2021. A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. Journal of Reliable Intelligent Environments 7 (1): 3–21. https://doi.org/10.1007/s40860-020-00126-x .
Keshk, M., E. Sitnikova, N. Moustafa, J. Hu, and I. Khalil. 2021. An integrated framework for privacy-preserving based anomaly detection for cyber-physical systems. IEEE Transactions on Sustainable Computing 6 (1): 66–79. https://doi.org/10.1109/TSUSC.2019.2906657 .
Khan, I.A., D.C. Pi, A.K. Bhatia, N. Khan, W. Haider, and A. Wahab. 2020. Generating realistic IoT-based IDS dataset centred on fuzzy qualitative modelling for cyber-physical systems. Electronics Letters 56 (9): 441–443. https://doi.org/10.1049/el.2019.4158 .
Khraisat, A., I. Gondal, P. Vamplew, J. Kamruzzaman, and A. Alazab. 2020. Hybrid intrusion detection system based on the stacking ensemble of C5 decision tree classifier and one class support vector machine. Electronics 9 (1): 18. https://doi.org/10.3390/electronics9010173 .
Khraisat, A., I. Gondal, P. Vamplew, and J. Kamruzzaman. 2019. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2 (1): 20. https://doi.org/10.1186/s42400-019-0038-7 .
Kilincer, I.F., F. Ertam, and A. Sengur. 2021. Machine learning methods for cyber security intrusion detection: Datasets and comparative study. Computer Networks 188: 16. https://doi.org/10.1016/j.comnet.2021.107840 .
Kim, D., and H.K. Kim. 2019. Automated dataset generation system for collaborative research of cyber threat analysis. Security and Communication Networks 2019: 10. https://doi.org/10.1155/2019/6268476 .
Kim, G., C. Lee, J. Jo, and H. Lim. 2020. Automatic extraction of named entities of cyber threats using a deep Bi-LSTM-CRF network. International Journal of Machine Learning and Cybernetics 11 (10): 2341–2355. https://doi.org/10.1007/s13042-020-01122-6 .
Kirubavathi, G., and R. Anitha. 2016. Botnet detection via mining of traffic flow characteristics. Computers & Electrical Engineering 50: 91–101. https://doi.org/10.1016/j.compeleceng.2016.01.012 .
Kiwia, D., A. Dehghantanha, K.K.R. Choo, and J. Slaughter. 2018. A cyber kill chain based taxonomy of banking Trojans for evolutionary computational intelligence. Journal of Computational Science 27: 394–409. https://doi.org/10.1016/j.jocs.2017.10.020 .
Koroniotis, N., N. Moustafa, and E. Sitnikova. 2020. A new network forensic framework based on deep learning for Internet of Things networks: A particle deep framework. Future Generation Computer Systems 110: 91–106. https://doi.org/10.1016/j.future.2020.03.042 .
Kruse, C.S., B. Frederick, T. Jacobson, and D. Kyle Monticone. 2017. Cybersecurity in healthcare: A systematic review of modern threats and trends. Technology and Health Care 25 (1): 1–10.
Kshetri, N. 2018. The economics of cyber-insurance. IT Professional 20 (6): 9–14. https://doi.org/10.1109/MITP.2018.2874210 .
Kumar, R., P. Kumar, R. Tripathi, G.P. Gupta, T.R. Gadekallu, and G. Srivastava. 2021. SP2F: A secured privacy-preserving framework for smart agricultural Unmanned Aerial Vehicles. Computer Networks . https://doi.org/10.1016/j.comnet.2021.107819 .
Kumar, R., and R. Tripathi. 2021. DBTP2SF: A deep blockchain-based trustworthy privacy-preserving secured framework in industrial internet of things systems. Transactions on Emerging Telecommunications Technologies 32 (4): 27. https://doi.org/10.1002/ett.4222 .
Laso, P.M., D. Brosset, and J. Puentes. 2017. Dataset of anomalies and malicious acts in a cyber-physical subsystem. Data in Brief 14: 186–191. https://doi.org/10.1016/j.dib.2017.07.038 .
Lee, J., J. Kim, I. Kim, and K. Han. 2019. Cyber threat detection based on artificial neural networks using event profiles. IEEE Access 7: 165607–165626. https://doi.org/10.1109/ACCESS.2019.2953095 .
Lee, S.J., P.D. Yoo, A.T. Asyhari, Y. Jhi, L. Chermak, C.Y. Yeun, and K. Taha. 2020. IMPACT: Impersonation attack detection via edge computing using deep Autoencoder and feature abstraction. IEEE Access 8: 65520–65529. https://doi.org/10.1109/ACCESS.2020.2985089 .
Leong, Y.-Y., and Y.-C. Chen. 2020. Cyber risk cost and management in IoT devices-linked health insurance. The Geneva Papers on Risk and Insurance—Issues and Practice 45 (4): 737–759. https://doi.org/10.1057/s41288-020-00169-4 .
Levi, M. 2017. Assessing the trends, scale and nature of economic cybercrimes: overview and Issues: In Cybercrimes, cybercriminals and their policing, in crime, law and social change. Crime, Law and Social Change 67 (1): 3–20. https://doi.org/10.1007/s10611-016-9645-3 .
Li, C., K. Mills, D. Niu, R. Zhu, H. Zhang, and H. Kinawi. 2019a. Android malware detection based on factorization machine. IEEE Access 7: 184008–184019. https://doi.org/10.1109/ACCESS.2019.2958927 .
Li, D.Q., and Q.M. Li. 2020. Adversarial deep ensemble: evasion attacks and defenses for malware detection. IEEE Transactions on Information Forensics and Security 15: 3886–3900. https://doi.org/10.1109/tifs.2020.3003571 .
Li, D.Q., Q.M. Li, Y.F. Ye, and S.H. Xu. 2021. A framework for enhancing deep neural networks against adversarial malware. IEEE Transactions on Network Science and Engineering 8 (1): 736–750. https://doi.org/10.1109/tnse.2021.3051354 .
Li, R.H., C. Zhang, C. Feng, X. Zhang, and C.J. Tang. 2019b. Locating vulnerability in binaries using deep neural networks. IEEE Access 7: 134660–134676. https://doi.org/10.1109/access.2019.2942043 .
Li, X., M. Xu, P. Vijayakumar, N. Kumar, and X. Liu. 2020. Detection of low-frequency and multi-stage attacks in industrial Internet of Things. IEEE Transactions on Vehicular Technology 69 (8): 8820–8831. https://doi.org/10.1109/TVT.2020.2995133 .
Liu, H.Y., and B. Lang. 2019. Machine learning and deep learning methods for intrusion detection systems: A survey. Applied Sciences—Basel 9 (20): 28. https://doi.org/10.3390/app9204396 .
Lopez-Martin, M., B. Carro, and A. Sanchez-Esguevillas. 2020. Application of deep reinforcement learning to intrusion detection for supervised problems. Expert Systems with Applications . https://doi.org/10.1016/j.eswa.2019.112963 .
Loukas, G., D. Gan, and Tuan Vuong. 2013. A review of cyber threats and defence approaches in emergency management. Future Internet 5: 205–236.
Luo, C.C., S. Su, Y.B. Sun, Q.J. Tan, M. Han, and Z.H. Tian. 2020. A convolution-based system for malicious URLs detection. CMC—Computers Materials Continua 62 (1): 399–411.
Mahbooba, B., M. Timilsina, R. Sahal, and M. Serrano. 2021. Explainable artificial intelligence (XAI) to enhance trust management in intrusion detection systems using decision tree model. Complexity 2021: 11. https://doi.org/10.1155/2021/6634811 .
Mahdavifar, S., and A.A. Ghorbani. 2020. DeNNeS: Deep embedded neural network expert system for detecting cyber attacks. Neural Computing & Applications 32 (18): 14753–14780. https://doi.org/10.1007/s00521-020-04830-w .
Mahfouz, A., A. Abuhussein, D. Venugopal, and S. Shiva. 2020. Ensemble classifiers for network intrusion detection using a novel network attack dataset. Future Internet 12 (11): 1–19. https://doi.org/10.3390/fi12110180 .
Maleks Smith, Z., E. Lostri, and J.A. Lewis. 2020. The hidden costs of cybercrime. https://www.mcafee.com/enterprise/en-us/assets/reports/rp-hidden-costs-of-cybercrime.pdf . Accessed 16 May 2021.
Malik, J., A. Akhunzada, I. Bibi, M. Imran, A. Musaddiq, and S.W. Kim. 2020. Hybrid deep learning: An efficient reconnaissance and surveillance detection mechanism in SDN. IEEE Access 8: 134695–134706. https://doi.org/10.1109/ACCESS.2020.3009849 .
Manimurugan, S. 2020. IoT-Fog-Cloud model for anomaly detection using improved Naive Bayes and principal component analysis. Journal of Ambient Intelligence and Humanized Computing . https://doi.org/10.1007/s12652-020-02723-3 .
Martin, A., R. Lara-Cabrera, and D. Camacho. 2019. Android malware detection through hybrid features fusion and ensemble classifiers: The AndroPyTool framework and the OmniDroid dataset. Information Fusion 52: 128–142. https://doi.org/10.1016/j.inffus.2018.12.006 .
Mauro, M.D., G. Galatro, and A. Liotta. 2020. Experimental review of neural-based approaches for network intrusion management. IEEE Transactions on Network and Service Management 17 (4): 2480–2495. https://doi.org/10.1109/TNSM.2020.3024225 .
McLeod, A., and D. Dolezel. 2018. Cyber-analytics: Modeling factors associated with healthcare data breaches. Decision Support Systems 108: 57–68. https://doi.org/10.1016/j.dss.2018.02.007 .
Meira, J., R. Andrade, I. Praca, J. Carneiro, V. Bolon-Canedo, A. Alonso-Betanzos, and G. Marreiros. 2020. Performance evaluation of unsupervised techniques in cyber-attack anomaly detection. Journal of Ambient Intelligence and Humanized Computing 11 (11): 4477–4489. https://doi.org/10.1007/s12652-019-01417-9 .
Miao, Y., J. Ma, X. Liu, J. Weng, H. Li, and H. Li. 2019. Lightweight fine-grained search over encrypted data in Fog computing. IEEE Transactions on Services Computing 12 (5): 772–785. https://doi.org/10.1109/TSC.2018.2823309 .
Miller, C., and C. Valasek. 2015. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015 (S 91).
Mireles, J.D., E. Ficke, J.H. Cho, P. Hurley, and S.H. Xu. 2019. Metrics towards measuring cyber agility. IEEE Transactions on Information Forensics and Security 14 (12): 3217–3232. https://doi.org/10.1109/tifs.2019.2912551 .
Mishra, N., and S. Pandya. 2021. Internet of Things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access . https://doi.org/10.1109/ACCESS.2021.3073408 .
Monshizadeh, M., V. Khatri, B.G. Atli, R. Kantola, and Z. Yan. 2019. Performance evaluation of a combined anomaly detection platform. IEEE Access 7: 100964–100978. https://doi.org/10.1109/ACCESS.2019.2930832 .
Moreno, V.C., G. Reniers, E. Salzano, and V. Cozzani. 2018. Analysis of physical and cyber security-related events in the chemical and process industry. Process Safety and Environmental Protection 116: 621–631. https://doi.org/10.1016/j.psep.2018.03.026 .
Moro, E.D. 2020. Towards an economic cyber loss index for parametric cover based on IT security indicator: A preliminary analysis. Risks . https://doi.org/10.3390/risks8020045 .
Moustafa, N., E. Adi, B. Turnbull, and J. Hu. 2018. A new threat intelligence scheme for safeguarding industry 4.0 systems. IEEE Access 6: 32910–32924. https://doi.org/10.1109/ACCESS.2018.2844794 .
Moustakidis, S., and P. Karlsson. 2020. A novel feature extraction methodology using Siamese convolutional neural networks for intrusion detection. Cybersecurity . https://doi.org/10.1186/s42400-020-00056-4 .
Mukhopadhyay, A., S. Chatterjee, K.K. Bagchi, P.J. Kirs, and G.K. Shukla. 2019. Cyber Risk Assessment and Mitigation (CRAM) framework using Logit and Probit models for cyber insurance. Information Systems Frontiers 21 (5): 997–1018. https://doi.org/10.1007/s10796-017-9808-5 .
Murphey, H. 2021a. Biden signs executive order to strengthen US cyber security. https://www.ft.com/content/4d808359-b504-4014-85f6-68e7a2851bf1?accessToken=zwAAAXl0_ifgkc9NgINZtQRAFNOF9mjnooUb8Q.MEYCIQDw46SFWsMn1iyuz3kvgAmn6mxc0rIVfw10Lg1ovJSfJwIhAK2X2URzfSqHwIS7ddRCvSt2nGC2DcdoiDTG49-4TeEt&sharetype=gift?token=fbcd6323-1ecf-4fc3-b136-b5b0dd6a8756 . Accessed 7 May 2021.
Murphey, H. 2021b. Millions of connected devices have security flaws, study shows. https://www.ft.com/content/0bf92003-926d-4dee-87d7-b01f7c3e9621?accessToken=zwAAAXnA7f2Ikc8L-SADkm1N7tOH17AffD6WIQ.MEQCIDjBuROvhmYV0Mx3iB0cEV7m5oND1uaCICxJu0mzxM0PAiBam98q9zfHiTB6hKGr1gGl0Azt85yazdpX9K5sI8se3Q&sharetype=gift?token=2538218d-77d9-4dd3-9649-3cb556a34e51 . Accessed 6 May 2021.
Murugesan, V., M. Shalinie, and M.H. Yang. 2018. Design and analysis of hybrid single packet IP traceback scheme. IET Networks 7 (3): 141–151. https://doi.org/10.1049/iet-net.2017.0115 .
Mwitondi, K.S., and S.A. Zargari. 2018. An iterative multiple sampling method for intrusion detection. Information Security Journal 27 (4): 230–239. https://doi.org/10.1080/19393555.2018.1539790 .
Neto, N.N., S. Madnick, A.M.G. De Paula, and N.M. Borges. 2021. Developing a global data breach database and the challenges encountered. ACM Journal of Data and Information Quality 13 (1): 33. https://doi.org/10.1145/3439873 .
Nurse, J.R.C., L. Axon, A. Erola, I. Agrafiotis, M. Goldsmith, and S. Creese. 2020. The data that drives cyber insurance: A study into the underwriting and claims processes. In 2020 International conference on cyber situational awareness, data analytics and assessment (CyberSA), 15–19 June 2020.
Oliveira, N., I. Praca, E. Maia, and O. Sousa. 2021. Intelligent cyber attack detection and classification for network-based intrusion detection systems. Applied Sciences—Basel 11 (4): 21. https://doi.org/10.3390/app11041674 .
Page, M.J. et al. 2021. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. Systematic Reviews 10 (1): 89. https://doi.org/10.1186/s13643-021-01626-4 .
Pajouh, H.H., R. Javidan, R. Khayami, A. Dehghantanha, and K.R. Choo. 2019. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Transactions on Emerging Topics in Computing 7 (2): 314–323. https://doi.org/10.1109/TETC.2016.2633228 .
Parra, G.D., P. Rad, K.K.R. Choo, and N. Beebe. 2020. Detecting Internet of Things attacks using distributed deep learning. Journal of Network and Computer Applications 163: 13. https://doi.org/10.1016/j.jnca.2020.102662 .
Paté-Cornell, M.E., M. Kuypers, M. Smith, and P. Keller. 2018. Cyber risk management for critical infrastructure: A risk analysis model and three case studies. Risk Analysis 38 (2): 226–241. https://doi.org/10.1111/risa.12844 .
Pooser, D.M., M.J. Browne, and O. Arkhangelska. 2018. Growth in the perception of cyber risk: evidence from U.S. P&C Insurers. The Geneva Papers on Risk and Insurance—Issues and Practice 43 (2): 208–223. https://doi.org/10.1057/s41288-017-0077-9 .
Pu, G., L. Wang, J. Shen, and F. Dong. 2021. A hybrid unsupervised clustering-based anomaly detection method. Tsinghua Science and Technology 26 (2): 146–153. https://doi.org/10.26599/TST.2019.9010051 .
Qiu, J., W. Luo, L. Pan, Y. Tai, J. Zhang, and Y. Xiang. 2019. Predicting the impact of android malicious samples via machine learning. IEEE Access 7: 66304–66316. https://doi.org/10.1109/ACCESS.2019.2914311 .
Qu, X., L. Yang, K. Guo, M. Sun, L. Ma, T. Feng, S. Ren, K. Li, and X. Ma. 2020. Direct batch growth hierarchical self-organizing mapping based on statistics for efficient network intrusion detection. IEEE Access 8: 42251–42260. https://doi.org/10.1109/ACCESS.2020.2976810 .
Rahman, Md.S., S. Halder, Md. Ashraf Uddin, and U.K. Acharjee. 2021. An efficient hybrid system for anomaly detection in social networks. Cybersecurity 4 (1): 10. https://doi.org/10.1186/s42400-021-00074-w .
Ramaiah, M., V. Chandrasekaran, V. Ravi, and N. Kumar. 2021. An intrusion detection system using optimized deep neural network architecture. Transactions on Emerging Telecommunications Technologies 32 (4): 17. https://doi.org/10.1002/ett.4221 .
Raman, M.R.G., K. Kannan, S.K. Pal, and V.S.S. Sriram. 2016. Rough set-hypergraph-based feature selection approach for intrusion detection systems. Defence Science Journal 66 (6): 612–617. https://doi.org/10.14429/dsj.66.10802 .
Rathore, S., J.H. Park. 2018. Semi-supervised learning based distributed attack detection framework for IoT. Applied Soft Computing 72: 79–89. https://doi.org/10.1016/j.asoc.2018.05.049 .
Romanosky, S., L. Ablon, A. Kuehn, and T. Jones. 2019. Content analysis of cyber insurance policies: How do carriers price cyber risk? Journal of Cybersecurity (oxford) 5 (1): tyz002.
Sarabi, A., P. Naghizadeh, Y. Liu, and M. Liu. 2016. Risky business: Fine-grained data breach prediction using business profiles. Journal of Cybersecurity 2 (1): 15–28. https://doi.org/10.1093/cybsec/tyw004 .
Sardi, Alberto, Alessandro Rizzi, Enrico Sorano, and Anna Guerrieri. 2021. Cyber risk in health facilities: A systematic literature review. Sustainability 12 (17): 7002.
Sarker, Iqbal H., A.S.M. Kayes, Shahriar Badsha, Hamed Alqahtani, Paul Watters, and Alex Ng. 2020. Cybersecurity data science: An overview from machine learning perspective. Journal of Big Data 7 (1): 41. https://doi.org/10.1186/s40537-020-00318-5 .
Scopus. 2021. Factsheet. https://www.elsevier.com/__data/assets/pdf_file/0017/114533/Scopus_GlobalResearch_Factsheet2019_FINAL_WEB.pdf . Accessed 11 May 2021.
Sentuna, A., A. Alsadoon, P.W.C. Prasad, M. Saadeh, and O.H. Alsadoon. 2021. A novel Enhanced Naïve Bayes Posterior Probability (ENBPP) using machine learning: Cyber threat analysis. Neural Processing Letters 53 (1): 177–209. https://doi.org/10.1007/s11063-020-10381-x .
Shaukat, K., S.H. Luo, V. Varadharajan, I.A. Hameed, S. Chen, D.X. Liu, and J.M. Li. 2020. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 13 (10): 27. https://doi.org/10.3390/en13102509 .
Sheehan, B., F. Murphy, M. Mullins, and C. Ryan. 2019. Connected and autonomous vehicles: A cyber-risk classification framework. Transportation Research Part a: Policy and Practice 124: 523–536. https://doi.org/10.1016/j.tra.2018.06.033 .
Sheehan, B., F. Murphy, A.N. Kia, and R. Kiely. 2021. A quantitative bow-tie cyber risk classification and assessment framework. Journal of Risk Research 24 (12): 1619–1638.
Shlomo, A., M. Kalech, and R. Moskovitch. 2021. Temporal pattern-based malicious activity detection in SCADA systems. Computers & Security 102: 17. https://doi.org/10.1016/j.cose.2020.102153 .
Singh, K.J., and T. De. 2020. Efficient classification of DDoS attacks using an ensemble feature selection algorithm. Journal of Intelligent Systems 29 (1): 71–83. https://doi.org/10.1515/jisys-2017-0472 .
Skrjanc, I., S. Ozawa, T. Ban, and D. Dovzan. 2018. Large-scale cyber attacks monitoring using Evolving Cauchy Possibilistic Clustering. Applied Soft Computing 62: 592–601. https://doi.org/10.1016/j.asoc.2017.11.008 .
Smart, W. 2018. Lessons learned review of the WannaCry Ransomware Cyber Attack. https://www.england.nhs.uk/wp-content/uploads/2018/02/lessons-learned-review-wannacry-ransomware-cyber-attack-cio-review.pdf . Accessed 7 May 2021.
Sornette, D., T. Maillart, and W. Kröger. 2013. Exploring the limits of safety analysis in complex technological systems. International Journal of Disaster Risk Reduction 6: 59–66. https://doi.org/10.1016/j.ijdrr.2013.04.002 .
Sovacool, B.K. 2008. The costs of failure: A preliminary assessment of major energy accidents, 1907–2007. Energy Policy 36 (5): 1802–1820. https://doi.org/10.1016/j.enpol.2008.01.040 .
SpringerLink. 2021. Journal Search. https://rd.springer.com/search?facet-content-type=%22Journal%22 . Accessed 11 May 2021.
Stojanovic, B., K. Hofer-Schmitz, and U. Kleb. 2020. APT datasets and attack modeling for automated detection methods: A review. Computers & Security 92: 19. https://doi.org/10.1016/j.cose.2020.101734 .
Subroto, A., and A. Apriyana. 2019. Cyber risk prediction through social media big data analytics and statistical machine learning. Journal of Big Data . https://doi.org/10.1186/s40537-019-0216-1 .
Tan, Z., A. Jamdagni, X. He, P. Nanda, R.P. Liu, and J. Hu. 2015. Detection of denial-of-service attacks based on computer vision techniques. IEEE Transactions on Computers 64 (9): 2519–2533. https://doi.org/10.1109/TC.2014.2375218 .
Tidy, J. 2021. Irish cyber-attack: Hackers bail out Irish health service for free. https://www.bbc.com/news/world-europe-57197688 . Accessed 6 May 2021.
Tuncer, T., F. Ertam, and S. Dogan. 2020. Automated malware recognition method based on local neighborhood binary pattern. Multimedia Tools and Applications 79 (37–38): 27815–27832. https://doi.org/10.1007/s11042-020-09376-6 .
Uhm, Y., and W. Pak. 2021. Service-aware two-level partitioning for machine learning-based network intrusion detection with high performance and high scalability. IEEE Access 9: 6608–6622. https://doi.org/10.1109/ACCESS.2020.3048900 .
Ulven, J.B., and G. Wangen. 2021. A systematic review of cybersecurity risks in higher education. Future Internet 13 (2): 1–40. https://doi.org/10.3390/fi13020039 .
Vaccari, I., G. Chiola, M. Aiello, M. Mongelli, and E. Cambiaso. 2020. MQTTset, a new dataset for machine learning techniques on MQTT. Sensors 20 (22): 17. https://doi.org/10.3390/s20226578 .
Valeriano, B., and R.C. Maness. 2014. The dynamics of cyber conflict between rival antagonists, 2001–11. Journal of Peace Research 51 (3): 347–360. https://doi.org/10.1177/0022343313518940 .
Varghese, J.E., and B. Muniyal. 2021. An Efficient IDS framework for DDoS attacks in SDN environment. IEEE Access 9: 69680–69699. https://doi.org/10.1109/ACCESS.2021.3078065 .
Varsha, M. V., P. Vinod, K.A. Dhanya. 2017 Identification of malicious android app using manifest and opcode features. Journal of Computer Virology and Hacking Techniques 13 (2): 125–138. https://doi.org/10.1007/s11416-016-0277-z
Velliangiri, S., and H.M. Pandey. 2020. Fuzzy-Taylor-elephant herd optimization inspired Deep Belief Network for DDoS attack detection and comparison with state-of-the-arts algorithms. Future Generation Computer Systems—the International Journal of Escience 110: 80–90. https://doi.org/10.1016/j.future.2020.03.049 .
Verma, A., and V. Ranga. 2020. Machine learning based intrusion detection systems for IoT applications. Wireless Personal Communications 111 (4): 2287–2310. https://doi.org/10.1007/s11277-019-06986-8 .
Vidros, S., C. Kolias, G. Kambourakis, and L. Akoglu. 2017. Automatic detection of online recruitment frauds: Characteristics, methods, and a public dataset. Future Internet 9 (1): 19. https://doi.org/10.3390/fi9010006 .
Vinayakumar, R., M. Alazab, K.P. Soman, P. Poornachandran, A. Al-Nemrat, and S. Venkatraman. 2019. Deep learning approach for intelligent intrusion detection system. IEEE Access 7: 41525–41550. https://doi.org/10.1109/access.2019.2895334 .
Walker-Roberts, S., M. Hammoudeh, O. Aldabbas, M. Aydin, and A. Dehghantanha. 2020. Threats on the horizon: Understanding security threats in the era of cyber-physical systems. Journal of Supercomputing 76 (4): 2643–2664. https://doi.org/10.1007/s11227-019-03028-9 .
Web of Science. 2021. Web of Science: Science Citation Index Expanded. https://clarivate.com/webofsciencegroup/solutions/webofscience-scie/ . Accessed 11 May 2021.
World Economic Forum. 2020. WEF Global Risk Report. http://www3.weforum.org/docs/WEF_Global_Risk_Report_2020.pdf . Accessed 13 May 2020.
Xin, Y., L. Kong, Z. Liu, Y. Chen, Y. Li, H. Zhu, M. Gao, H. Hou, and C. Wang. 2018. Machine learning and deep learning methods for cybersecurity. IEEE Access 6: 35365–35381. https://doi.org/10.1109/ACCESS.2018.2836950 .
Xu, C., J. Zhang, K. Chang, and C. Long. 2013. Uncovering collusive spammers in Chinese review websites. In Proceedings of the 22nd ACM international conference on Information & Knowledge Management.
Yang, J., T. Li, G. Liang, W. He, and Y. Zhao. 2019. A Simple recurrent unit model based intrusion detection system with DCGAN. IEEE Access 7: 83286–83296. https://doi.org/10.1109/ACCESS.2019.2922692 .
Yuan, B.G., J.F. Wang, D. Liu, W. Guo, P. Wu, and X.H. Bao. 2020. Byte-level malware classification based on Markov images and deep learning. Computers & Security 92: 12. https://doi.org/10.1016/j.cose.2020.101740 .
Zhang, S., X.M. Ou, and D. Caragea. 2015. Predicting cyber risks through national vulnerability database. Information Security Journal 24 (4–6): 194–206. https://doi.org/10.1080/19393555.2015.1111961 .
Zhang, Y., P. Li, and X. Wang. 2019. Intrusion detection for IoT based on improved genetic algorithm and deep belief network. IEEE Access 7: 31711–31722.
Zheng, Muwei, Hannah Robbins, Zimo Chai, Prakash Thapa, and Tyler Moore. 2018. Cybersecurity research datasets: taxonomy and empirical analysis. In 11th {USENIX} workshop on cyber security experimentation and test ({CSET} 18).
Zhou, X., W. Liang, S. Shimizu, J. Ma, and Q. Jin. 2021. Siamese neural network based few-shot learning for anomaly detection in industrial cyber-physical systems. IEEE Transactions on Industrial Informatics 17 (8): 5790–5798. https://doi.org/10.1109/TII.2020.3047675 .
Zhou, Y.Y., G. Cheng, S.Q. Jiang, and M. Dai. 2020. Building an efficient intrusion detection system based on feature selection and ensemble classifier. Computer Networks 174: 17. https://doi.org/10.1016/j.comnet.2020.107247 .
Download references
Open Access funding provided by the IReL Consortium.
Author information
Authors and affiliations.
University of Limerick, Limerick, Ireland
Frank Cremer, Barry Sheehan, Arash N. Kia, Martin Mullins & Finbarr Murphy
TH Köln University of Applied Sciences, Cologne, Germany
Michael Fortmann & Stefan Materne
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Barry Sheehan .
Ethics declarations
Conflict of interest.
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Below is the link to the electronic supplementary material.
Supplementary file1 (PDF 334 kb)
Supplementary file1 (docx 418 kb), rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cremer, F., Sheehan, B., Fortmann, M. et al. Cyber risk and cybersecurity: a systematic review of data availability. Geneva Pap Risk Insur Issues Pract 47 , 698–736 (2022). https://doi.org/10.1057/s41288-022-00266-6
Download citation
Received : 15 June 2021
Accepted : 20 January 2022
Published : 17 February 2022
Issue Date : July 2022
DOI : https://doi.org/10.1057/s41288-022-00266-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cyber insurance
- Systematic review
- Cybersecurity
- Find a journal
- Publish with us
- Track your research

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/cybersecurity

Cybersecurity
NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and future challenges.
Some NIST cybersecurity assignments are defined by federal statutes, executive orders and policies. For example, the Office of Management and Budget (OMB) mandates that all federal agencies implement NIST’s cybersecurity standards and guidance for non-national security systems. Our cybersecurity activities also are driven by the needs of U.S. industry and the broader public. We engage vigorously with stakeholders to set priorities and ensure that our resources address the key issues that they face.
NIST also advances understanding and improves the management of privacy risks, some of which relate directly to cybersecurity.
Priority areas to which NIST contributes – and plans to focus more on – include cryptography, education and workforce, emerging technologies, risk management , identity and access management, measurements, privacy, trustworthy networks and trustworthy platforms.
Additional details can be found in these brief and more detailed fact sheets.
Featured Content
Cybersecurity topics.
- Cryptography
- Cybersecurity education and workforce development
- Cybersecurity measurement
- Identity & access management
- Privacy engineering
- Risk Management
- Securing emerging technologies
- Trustworthy networks
- Trustworthy platforms
The Research
Projects & programs.

Exposure Notification – protecting workplaces and vulnerable communities during a pandemic

Trustworthy Networks of Things
Cryptographic module validation program (cmvp).

Cyber-Physical Systems/Internet of Things for Smart Cities
Additional resources links.

NIST Drafts Major Update to Its Widely Used Cybersecurity Framework

NIST Awards $3.6 Million for Community-Based Cybersecurity Workforce Development

NIST Releases Version 2.0 of Landmark Cybersecurity Framework

NIST Offers Guidance on Measuring and Improving Your Company’s Cybersecurity Program
Cybersecurity Insights Blog
Giving nist digital identity guidelines a boost: supplement for incorporating syncable authenticators, protecting model updates in privacy-preserving federated learning, updates on nist’s interagency international cybersecurity standardization working group, data distribution in privacy-preserving federated learning, nice webinar: reintegrating justice-involved individuals into cybersecurity careers, nice webinar: equity strategies in youth apprenticeship programs and partnerships, nice webinar: empowering refugee communities in cybersecurity roles, 2024 iris experts group (ieg) meeting, stay in touch.
Sign up for our newsletter to stay up to date with the latest research, trends, and news for Cybersecurity.
Custom Essay, Term Paper & Research paper writing services
- testimonials
Toll Free: +1 (888) 354-4744
Email: [email protected]
Writing custom essays & research papers since 2008
154 exceptional cybersecurity research topics for you.

If you are studying computer science or IT-related course, you will encounter such a task. It is one of the most technical assignments, primarily in the era of advanced digital technologies. Students may not have the muscles to complete such papers on their own. That is why we provide expert help and ideas to make the process easier.
Do you want to excel in your cybersecurity paper? Here is your number one arsenal!
What You Need To Know About Cyber Security Research Topics
A cybersecurity paper deals with the practices of protecting servers, electronic systems, computers, and networks from malicious attacks. Although most students think this only applies to computers, it also applies to mobile computing and other business models.
There are various categories in cybersecurity, including:
Network security Application security Information security Operational security Disaster recovery and business continuity
Therefore, your cybersecurity topics for research should:
Examine the common security breaches in systems and networks Offer practical ways of protecting computers from such attacks Highlight the legal and ethical implications of hacking and other related practices Point out the challenges encountered in combating cybercrime
Since this is a technical paper, you should endeavor to do your research extensively to prevent rumors and unverified facts. The topics should also inform and educate people who are not conversant with cybersecurity in simple terms. Avoid using jargon at all costs, as this will make the paper difficult to read and understand.
Are you worried about where you can get professional cybersecurity topics and ideas? Well, here are a few of the most reliable sources that can furnish you with top-rated issues.
- Government legislation on cybersecurity (Acts of Parliament)
- The UN Office of Counter-Terrorism (Cybersecurity initiatives)
- The CISCO magazine
- Forbes also has excellent coverage on cybersecurity
You can find impressive topic ideas from these sources and more. Furthermore, news headlines and stories on cybersecurity can also help you gather many writing ideas. If all these prove futile, use our tip-top writing prompts below:
Quality Cyber Security Thesis Topics
- Impacts of coronavirus lockdowns on cybersecurity threats in the US
- Why ethical hacking is contributing to more harm than good
- The role of computer specialists in combating cyber threats before they occur
- Technological trends that are making it difficult to manage systems
- Are passwords reliable when protecting computer systems?
- Effects of having more than one systems administrator in a company
- Can the government shut down the dark web once and for all?
- Why should you bother about the security of your mobile device?
- Evaluate reasons why using public WIFI can be harmful to your security
- The role of cybersecurity seminars and conferences
- How universities can produce ethical computer hackers who can help the society
- How to counter-terrorism with advanced cybersecurity measures
- Impacts of teaching children how to use computers at a tender age
- Latest innovations that are a threat to cybersecurity
- The role of monitoring in combating frequent cyber attacks
- How social media is contributing to cyber attacks
- Discuss the relationship between cyberbullying and cybersecurity
- Why fingerprints may be the best method of protecting devices
- The role of YouTube in contributing to the rising number of hackers
Top Research Topics For Cyber Security For Master Thesis
- Impact of cyber threats on attaining the sustainable development goals
- Why websites are becoming easy to hack in the 21 st century
- Effects of not having an SSL certificate for a website
- Discuss the security threats associated with WordPress websites
- Impacts of frequent maintenance while the website is still running
- How computer colleges can contribute to a safe cyberspace
- Latest cyber threats to business and financial websites
- Discuss the implications of cyber threats on privacy
- The role of Facebook in advancing cyberbullying and hacking
- Is hacking becoming a global epidemic in the digital world?
- Why using Cyber Cafes may be detrimental to your digital security
- The role of systems analysts in responding to data breaches
- How cybersecurity movies are contributing to cyber threats
- Should hackers face lifetime jail imprisonment when found guilty?
- Loopholes in cyber laws that make the practice challenging to curtail
Good Thesis Topics For Cyber Security
- The relationship between privacy and data security in computing
- Why cloud computing offers a haven for computer hackers
- The role of character and human-based behavior in cybersecurity
- How to determine safe organizational security management and policy
- How the Internet of Things is promoting cyber attacks
- Effects of using cracked computer software
- Are biometrics in cybersecurity able to put off hackers?
- The role of studying mobile platform security
- Why companies should frequently monitor their firewalls
- The role of antimalware in curbing cyber attacks
- Why is Ransomware a headache to most companies handling big data?
- How does antivirus software improve the security of your computer?
- Compare and contrast between the security of UNIX and Ubuntu
- The role of data encryption technologies in ensuring system security
- Is the process of encrypting viruses safe?
Top-Grade Thesis Topics For Cyber Security
- Describe the effectiveness of cybersecurity audits on company systems
- Is it proper to conduct device synchronization?
- Why is it difficult to manage the security of an intranet?
- Discuss the effects of logging in to many devices at the same time
- Evaluate the significance of computer forensics
- How are hackers inventing new ways of breaching the systems of companies?
- Why it is necessary to review the data protection laws
- Practices that increase the vulnerability of a system to cyber attacks
- Can organizations implement impenetrable network systems?
- Why administrators should check the background of users before giving them rights and privileges
- The role of risk management cybersecurity
- Discuss the impact of reverse engineering on computing systems
- Effects of a cyber-attack on a company’s economic performance
- What legal frameworks work best for a computer company?
- The role of social engineering in cybersecurity
Information Security Research Topics
- The implication of the proliferation of the internet globally
- Innovative technologies used in keeping off hackers
- The role of information communication technologies in maintaining the security
- Are online courses on informative security practical?
- Why should people avoid sharing their details on Facebook?
- Effects of using your image on social media
- The role of pseudo names and nicknames on social media
- Discuss the implications of Wi-Fi hacking apps on mobile phones
- How to detect malicious activity on a system
- Evaluate the potential threats of conduct self-hacking on a system
- The impact of sharing personal details with hiring agencies
- How con artists lure unsuspecting applicants into giving out their details
- Effects of frequent maintenance on systems
- How to strengthen the firewall of an information system
- The role of the media in propagating security breaches to information systems
Latest Computer Security Research Topics
- Tricks that black hat hackers use to infiltrate company systems
- How children learn about cybersecurity from their parents
- The impact of watching hacking movies and TV series
- How various companies are protecting themselves from cyber attacks
- Why every company should have a systems security consultant
- Discuss the implication of digital piracy
- Threats that biometrics are bringing to digital systems
- How to block a network intrusion before it causes any effect
- Why MacOS is challenging to infiltrate, unlike Windows
- Results of two-step authentication security measures for login systems
- The role of updating computer systems during working days
- Evaluate times of the year when hackers infiltrate systems the most
- Why it isn’t easy to manage big data on the cloud
- What happens during a system breakdown and maintenance?
- Discuss the role of data synchronization in creating a backup
Network Security Research Paper Topics
- The impact of having self-configuring and decentralized network systems
- Effects of ad-hoc networks for large companies
- Discuss the role of wireless sensor networks in contributing to security breaches
- How malicious nodes join a network
- Why it is difficult to detect a passive network attack
- How active network attacks reduce a network’s performance
- Evaluate the various parameters used in network security
- Analyze how a black hole affects a network system
- Describe techniques used in detecting malicious nodes on networks
- How to improve the safety of a company network
- The role of data encryption in maintaining the security of a network
- Describe the various channels of establishing secure algorithms in a network
- How does RSA increase the safety of a particular network?
- Effective policies and procedures for maintaining network security
- The role of a unique ID and Password in securing a website
Computer Security Research Topics
- Why it is challenging to maintain endpoint security
- The role of a critical infrastructure cybersecurity
- How to create secure passwords for your computer network
- The part of scanning for malware often on your PC
- How to detect apps that invade your privacy unknowingly
- Why ordering software from the black market is a threat to security
- Safe computing techniques for first-time computer users
- The role of digital literacy in preventing hacking
- Why most online users fall to online scams
- The role of smartphones in enhancing cybersecurity threats
- Evaluate the mobile landscape concerning data security
- The implication of private email accounts in data breaches
- Sites that contain a barrel of internet criminals
- How to develop comprehensive internet security software
- How children can navigate the internet safely
Impressive Cyber Crime Research Topics
- Why cyber currencies are a threat to online security
- Why cyberbullying is rampant in the 21 st century unlike in any other time
- The impact of online persuasion campaigns on cybersecurity
- Why teenagers are victims of cyberbullying than adults
- Discuss the effects of technology evolution on cybercrime
- How online hackers collect information without the knowledge of the victim
- Traits of a robust cybersecurity system
- Practices that can help reduce cybercrime in institutions of higher learning.
- Effects of global coordinated cyber attacks
- The penalties of cyber-attack in the First Amendment
- Why the world is experiencing increased cyber attacks
- Critical concepts of cyber attacks
- Cybercriminals and enterprises
- Role of NGOs in combating cyber terrorism
- Cyberbullying in campus
World-Class Cyber Security Thesis Ideas
- Effects of the cyber-attack on Sony in 2014
- The role of globalization in enhancing cybersecurity
- How to prevent automotive software from malicious cyber attacks
- The role of cyber technology in changing the world since the 1990s
- How the private sector is essential in combating cyber threats
- Computer infrastructure protection against cyber attacks
- Impact of social networking sites on cybersecurity
- Threats that cyber-attacks pose the national security of a country
- How cyber monitoring affects ethical and legal considerations
- Factors leading to the global nature of cyber attacks
- Analyze law enforcement agencies that deal with cyber attacks
- Evaluate cyber-crime court cases
- Evolution of the cybersecurity industry
- Cyber terrorism in the US
- Implementing adequate data protection strategies
We offer paper writing help on any cybersecurity topic. Try us now!

Top 111+ Stunning Cybersecurity Research Topics For 2023

Are you confused about cybersecurity and its research topics? So here, in this blog, we will discuss cybersecurity research topics. This article is important If you are studying computer science or a cybersecurity course.
If you want good grades in cybersecurity research topics, you should pick the latest cybersecurity research topics for your academic exam or test. Here, you can choose the good and latest cybersecurity research topics.
You know that cybercrime is increasing day by day because millions of people use the internet. Several applications deal with the internet, and people normally use the internet for bank transactions, food delivery, online shopping, social media, gaming, etc. Attackers can steal your information, data, and money with the help of malicious software, So we need cybersecurity services.
What is Cybersecurity?
Table of Contents
Cybersecurity is a process of preventing unauthorized access or protecting networks, devices, and data from digital attacks. Cybersecurity is also known as IT(Information Technology)Security which is designed to prevent threats against network systems, applications, and other platforms. In simple words, It prevents or protects any information, data, and others.
Here Are Some of the Best Writing Tips From Statanalytica’s Expert
As you might already know that a well-planned action and a set of useful tools will also help you write a high-quality research paper. On the other hand, remaining motivated throughout the process.
- By choosing an interesting topic for your research paper.
- Conduct some research to find reputable sources.
- Clearly state your cybersecurity thesis.
- A rough plan should be created.
- Finish your paper by drafting it.
- Make sure your content is properly formatted.
- Make sure you understand the assignment before you begin writing your research paper.
Let’s Discuss the 111+ Stunning Cybersecurity Research Topics
Below we listed 111+ cybersecurity research topics that can be used in 2023:
Top 10 Cyber Security Topics of 2023
Here are the top 10 cyber security topics of 2023:
- Can strong passwords protect information?
- Is security in critical infrastructure important?
- The importance of end-user education
- Cloud security posture management
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- Do biometrics ensure the security of iPhones?
Latest Cybersecurity Research Topics of 2023
- Is removable media a threat?
- Cybersecurity standards for automotive
- How to prevent social engineering attacks
- Security breaches of remote working
- How to prevent phishing attacks
- Physical security measures in banks
- Privacy settings of social media accounts
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How does two-factor authentication work?
- Cryptography
- Discuss the importance of intranet security
- Rise of Automotive Hacking
- What is ethical hacking?
- The evolution of phishing and how it is becoming more sophisticated
- Which antivirus software is the best in the world?
- The most up-to-date and trending cybersecurity technology
- How can organizations prevent network attacks?
- What is Digital Piracy?
- Application of biometrics in cyber security?
- Identity theft on the Internet
- Risk management in computing
- Rise of computer forensics
- Threats are analyzed using digital forensic techniques
- What is a Remote Access VPN?
- Digital security and Social Networks
- The risks of using public Wi-Fi networks
- Popular online scams in 2022
- Artificial intelligence security systems
Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
Topics for Application Security Research
- Discuss SQL injection attacks.
- Inadequately configured security protocols.
- Talk about data leaks in mobile apps.
- Backend access control is critical.
- Logging has many advantages for applications.
- Malicious apps are available on Google Play.
- AI applications: ethical constraints and opportunities.
- What is the effect of insecure deserialization?
- The most effective application security testing practices.
- Apps are vulnerable to XSS attacks.
Information Technology Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2022
- Discuss digital piracy in 2022
- critical cyber-attack concepts
- Social engineering and its importance
Operational Security Research Topics In 2023
- Securing containerized applications in cloud environments.
- Implementing secure remote access policies for remote workers.
- Evaluating the effectiveness of endpoint protection solutions.
- Protecting against DNS tunneling attacks.
- Securing cloud-based storage solutions.
- Developing secure mobile device management policies.
- Analyzing the effectiveness of honeypots in detecting attacks.
- Securing software supply chains against attacks.
- Investigating the effectiveness of deception technologies in cybersecurity.
- Developing secure network segmentation strategies.
- Evaluating the effectiveness of network traffic analysis solutions.
- Analyzing the effectiveness of two-factor authentication in securing systems.
- Securing critical infrastructure against cyber threats.
- Developing secure email policies to prevent phishing attacks.
- Investigating the use of artificial intelligence in cybersecurity.
- Developing secure DevOps practices.
- Analyzing the effectiveness of security information and event management (SIEM) solutions.
- Securing the Internet of Things (IoT) devices.
- Evaluating the effectiveness of password management solutions.
- Developing secure incident response strategies.
Topics for a Research Paper on CyberCrime Prevention
- Criminal Specialization.
- Drug Courts.
- Capital Punishment.
- Criminal Courts.
- Crime Prevention.
- Community Corrections.
- Criminal Law.
- Criminal Justice Ethics.
Computer and Software Security Research Topics
- Learn algorithms for data encryption.
- Concept of risk management security.
- How to develop the best internet security software.
- What are Encrypting viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC.
- Infiltrating a Mac OS X operating system.
- What are the effects of RSA on network security?
- How do encrypting viruses work?
- DDoS attacks on IoT devices.
Computer and Software Cyber Security Topics
- The importance of updating computer software.
- How to safeguard your computer against malware and other threats.
- The best security practices for your computer and software.
- The various types of cyber security threats and how to avoid them.
- The significance of cyber security education and awareness.
- The importance of cyber security in protecting critical infrastructure.
Data Security Research Topics
- Importance of backup and recovery.
- Benefits of logging for applications.
- Understand physical data security.
- Importance of Cloud Security.
- In computing, the relationship between privacy and data security.
- Discuss the effects of a black hole on a network system.
Application Security Topics
- Detect Malicious Activity on Google Play Apps.
- Dangers of XSS attacks on apps.
- Insecure Deserialization Effect.
- Check Security protocols.
CyberSecurity Law Research Paper Topics
- Strict cybersecurity laws in China.
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries cybersecurity laws.
- Discuss The Pipeline Security Act in the United States.
If you are interested in criminal research topics, then here are the best criminal justice research topics for you.
How to Choose The Best Cybersecurity Research Topics in 2023
There are a few factors to consider when selecting cybersecurity research topics. The first and main thing to consider is to ensure that the topic is current and relevant. Because cyber security is a changing field. As a result, it is very crucial to select a topic that will be relevant for a few months.
On the other hand, the second thing to consider is to select an interesting and engaging topic. Because cyber security can be a dry subject, it is critical to select a topic that will keep readers interested.
Finally, it is very important to select a researchable topic. There are several cybersecurity topics available, but not all of them are simple to research. Choose a topic about which there is a lot of information.
- Determine your target audience
- Define your research objectives
- Choose a topic that your audience will find both interesting and relevant
- Conduct preliminary research to ensure that there is sufficient information available on your chosen topic
- Make sure your topic is focused enough to fit into a single research paper
Research Area in Cyber Security
Cybersecurity is extensive, and constantly evolving field. On the other hand, its research takes place in many areas:

- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
Get More Cybersecurity Research Topics
In this blog, we have covered the 111+ best cybersecurity research topics. These cybersecurity topics help in your exam or test. If you have any difficulty with cybersecurity research topics, you can take cybersecurity research paper help or research paper assignment help at a very affordable price.
Here are some of the benefits of taking cybersecurity research topics help from us.
- 24 Hours Availability
- On-time Delivery
- Free Corrections
- Money-Back Guarantee
- Affordable Deals
- Professional Experts
You can contact us any time and impress your teacher by choosing a good cybersecurity research topic.
This is the end of the post, which is about cybersecurity research topics. On the other hand, we mentioned 111+ stunning cybersecurity research topics for 2023 offer an excellent opportunity for researchers to explore and address critical cybersecurity challenges. However, the ever-evolving technological landscape presents new security challenges every day, and it is essential to keep up with the latest trends to stay ahead of cyber threats.
On the other hand, these research topics provide many areas to explore, from network security, the internet of things, and software security to network security, cryptography, and data security. I hope you like this post.
Q1. What are the types of cyber security threats?
There are several different types of cyber security threats. More popular are Trojan horses, worms, ransomware, and phishing scams. These types of threats can be very dangerous for the cyber system.
Q2. What are the most controversial topics in criminal justice?
1. Prisoners being granted the right to work 2. Carrying a concealed weapon 3. Prison rape and violence 4. Plea agreement/bargain 5. Rehab vs. reform. 6. Is an eyewitness testimony effective? 7. Enforcement and effectiveness of stalking laws. 8. Rape culture and the victim’s rights
Q3. What are the main cyber threats of 2023?
There are multiple cyber security threats, but the main social threats of 2023 are email impersonation and phishing. On the other hand, email impersonation is a phishing technique in which a fake email address that appears to be legitimate is used.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
This is a potential security issue, you are being redirected to https://csrc.nist.gov .
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Drafts for Public Comment
- All Public Drafts
- NIST Special Publications (SPs)
- NIST interagency/internal reports (NISTIRs)
- ITL Bulletins
- White Papers
- Journal Articles
- Conference Papers
- Security & Privacy
Applications
Technologies.
- Laws & Regulations
- Activities & Products
- News & Updates
- Cryptographic Technology
- Secure Systems and Applications
- Security Components and Mechanisms
- Security Engineering and Risk Management
- Security Testing, Validation, and Measurement
- Cybersecurity and Privacy Applications
- National Cybersecurity Center of Excellence (NCCoE)
- National Initiative for Cybersecurity Education (NICE)
Security and Privacy
- digital signatures
- key management
- lightweight cryptography
- message authentication
- post-quantum cryptography
- random number generation
- secure hashing
- cybersecurity supply chain risk management
- general security & privacy
- access authorization
- access control
- Personal Identity Verification
- public key infrastructure
- personally identifiable information
- privacy engineering
- categorization
- continuous monitoring
- controls assessment
- privacy controls
- security controls
- risk assessment
- roots of trust
- system authorization
- advanced persistent threats
- information sharing
- intrusion detection & prevention
- vulnerability management
- accessibility
- testing & validation
- acquisition
- asset management
- audit & accountability
- awareness training & education
- configuration management
- contingency planning
- incident response
- maintenance
- media protection
- patch management
- personnel security
- physical & environmental protection
- program management
- security automation
- reliability
- artificial intelligence
- cloud & virtualization
- combinatorial testing
- personal computers
- quantum information science
- smart cards
- operating systems
- communications & wireless
- cyber-physical systems
- cybersecurity education
- cybersecurity framework
- cybersecurity workforce
- industrial control systems
- Internet of Things
- mathematics
- positioning navigation & timing
- small & medium business
Laws and Regulations
- Comprehensive National Cybersecurity Initiative
- Cybersecurity Strategy and Implementation Plan
- Cyberspace Policy Review
- Executive Order 13636
- Executive Order 13702
- Executive Order 13718
- Executive Order 13800
- Executive Order 13905
- Executive Order 14028
- Executive Order 14110
- Federal Cybersecurity Research and Development Strategic Plan
- Homeland Security Presidential Directive 7
- Homeland Security Presidential Directive 12
- OMB Circular A-11
- OMB Circular A-130
- Cyber Security R&D Act
- Cybersecurity Enhancement Act
- E-Government Act
- Energy Independence and Security Act
- Federal Information Security Modernization Act
- First Responder Network Authority
- Health Insurance Portability and Accountability Act
- Help America Vote Act
- Internet of Things Cybersecurity Improvement Act
- Federal Acquisition Regulation
Activities and Products
- annual reports
- conferences & workshops
- quick start guides
- reference materials
- standards development
- financial services
- hospitality
- manufacturing
- public safety
- telecommunications
- transportation
The Future of Cybersecurity with the Rising Tide and Threat Powered by AI

In today's digital age, artificial intelligence (AI) and cybersecurity have converged, giving rise to a dynamic battleground for the future of digital security. As AI technologies continue to evolve, so too do the capabilities of cybercriminals, necessitating innovative strategies to counter emerging threats. AI will be the great accelerator of threat levels as it increases the speed and sophistication of cybersecurity threats. Daniel Tobok , one of the founding thought leaders in the space, has spent years workshopping his theories and strategies for dealing with threats.
Tobok is not just a cybersecurity professional; he is a pioneer with a track record spanning nearly three decades. With over ten thousand cyber-attack reviews and thousands of successful recovery missions to his credit, Tobok's expertise is unparalleled. Having founded and led multiple successful cybersecurity ventures, Tobok is a trusted advisor to businesses worldwide, shaping the future of cyber resilience through his visionary approach.
Cyber threats powered by AI represent a new frontier in digital warfare, where malicious actors leverage sophisticated algorithms to launch targeted attacks at unprecedented scale and speed. AI technology is increasingly used in cybersecurity incidents, with cybercriminals employing advanced methods like AI-driven malware and deepfake technology to enhance their attacks and avoid detection.
The days of assuming cyber security breaches were reserved for simply big corporations or government are history,” says Tobok . “We are all at risk. Each and every one of us is far more digitally connected than ever before. Accessing WiFi in public areas, online banking, social media platform interactions, and watching our favourite shows and movies via digital means — we all live online now. Our exposure levels are at an all-time high and rising. And artificial intelligence is learning this firsthand, in real-time thus amplifying the risk profile for us all.
As cyber threats evolve, cybersecurity defenses must also. AI-powered cybersecurity solutions promise enhanced threat detection, predictive analytics, and automated response capabilities. Machine learning algorithms can analyze vast amounts of data to identify anomalous behavior and potential security breaches in real-time, enabling proactive defense measures.
AI is fundamentally changing the landscape of cybersecurity by revolutionizing how threats are detected, analyzed, and mitigated. AI-powered cybersecurity solutions can immediately analyze vast amounts of data to identify patterns indicative of potential cyber threats. “Historically, cyber security would summon a knee-jerk reaction to an inbound threat or breach of privacy,” explains Tobok. “Cyber security is reactive, while Cyber Certainty™ is being proactive. Rather than worrying about the path to recovery and response to digital compromise, what’s now and next is getting ahead of the cyber threat indicators, trends, and emerging portals of opportunity for threat actors to strike. Creating and maintaining digital stability in one’s digital and online presence, both internally and externally.”
Automated response capabilities, powered by AI, allow cybersecurity systems to respond to threats in real time without human intervention. These security tools can automatically block suspicious IP addresses, quarantine infected devices, and mitigate the impact of cyber attacks, reducing response times and minimizing damage.
Tobok is a pioneer in the cybersecurity space, having started in the industry during its earliest days. He’s had a first-hand view and front-row seat in the earliest days of cyber threat and reconciliation, dating back to the earliest days of cyber security. Tobok spent years analyzing, data-forming, and crystallizing theories, strategies, and architecture.
In response to the escalating cyber threat landscape, Tobok has authored his own urban cyber security philosophy called Cyber Certainty™, a revolutionary view and approach setting a new standard for resilience in the face of cyber-attacks. Cyber Certainty™ emphasizes being more invincible and less vulnerable digitally, empowering organizations to adopt a proactive and holistic approach to cybersecurity.
“Cyber security is like a knee-jerk reaction to an inbound threat or an obvious breach of privacy,” explains Tobok. “Cyber Certainty™, however, is more about being proactive. Rather than worrying about the response to a business or assets being compromised, it is more important to be proactive. Cyber Certainty™ is about creating and maintaining digital stability in one’s digital and online presence, both internally and externally.”
As the founder and CEO of CYPFER, Tobok leads one of the world's fastest-growing collective geniuses’ for Cyber Certainty™. So brilliant in fact, The Institute of Futurization, an organization focused on thought leadership, research, and tracking trends for industry combatting the downside to futurization, engaged Tobok as Chief Lead on their global project, Cyber Intelligence & Global Affairs initiatives where Tobok aggregates research, data, and analytics to produce predictions and approaches for the future of cybersecurity upset and turmoil. With offices in five countries, CYPFER is poised to become the global standard for cybersecurity thinking and strategy in an AI-driven new reality for leaders, businesses, and governments.
With AI continuing to reshape the cybersecurity landscape, organizations must remain vigilant and adaptable in the face of evolving threats. By embracing innovative strategies and leveraging AI-powered cybersecurity solutions, businesses can enhance their resilience and safeguard their digital assets against emerging threats. With visionary leaders like Tobok at the helm, the future of cybersecurity holds promise, empowering organizations to navigate the complexities of the digital age with confidence and certainty.
ORIGINAL RESEARCH article
This article is part of the research topic.
Cybersecurity and Artificial Intelligence: Advances, Challenges, Opportunities, Threats
A comprehensive investigation of clustering algorithms for User and Entity Behavior Analytics Provisionally Accepted

- 1 BV TECH S.p.A., Italy
The final, formatted version of the article will be published soon.
Government agencies are now encouraging industries to enhance their security systems to detect and respond proactively to cybersecurity incidents. Consequently, equipping with a security operation center that combines the analytical capabilities of human experts with systems based on Machine Learning (ML) plays a critical role. In this setting, Security Information and Event Management (SIEM) platforms can effectively handle network-related events to trigger cybersecurity alerts. Furthermore, a SIEM may include a User and Entity Behavior Analytics (UEBA) engine that examines the behavior of both users and devices, or entities, within a corporate network. In recent literature, several contributions have employed ML algorithms for UEBA, especially those based on the unsupervised learning paradigm, because anomalous behaviors are usually not known in advance. However, to shorten the gap between research advances and practice, it is necessary to comprehensively analyze the effectiveness of these methodologies. This paper proposes a thorough investigation of traditional and emerging clustering algorithms for UEBA, considering multiple application contexts, i.e., different user-entity interaction scenarios. Our study involves three datasets sourced from the existing literature and fifteen clustering algorithms. Among the compared techniques, HDBSCAN and DenMune showed promising performance on the state-of-the-art CERT behavior-related dataset, producing groups with a density very close to the number of users.
Keywords: clustering, data analytics, machine learning, UEBA, unsupervised learning
Received: 24 Jan 2024; Accepted: 22 Apr 2024.
Copyright: © 2024 Artioli, Maci and Magrì. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) or licensor are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
* Correspondence: Dr. Antonio Maci, BV TECH S.p.A., Milan, Lombardy, Italy
People also looked at
Cybersecurity for Researchers
Tuesday, October 22, 2024
1pm via Zoom
This brown bag session will focus on secure campus tools and services that Research IT and Berkeley IT offer to researchers, tips on navigating campus security processes, and cybersecurity best practices for keeping your research and research subjects safe. In partnership with the UC Berkeley Information Security Office and Industry Alliances Office.
Unearthing APT44: Russia’s Notorious Cyber Sabotage Unit Sandworm
Written by: Gabby Roncone, Dan Black, John Wolfram, Tyler McLellan, Nick Simonian, Ryan Hall, Anton Prokopenkov, Luke Jenkins, Dan Perez, Lexie Aytes, Alden Wahlstrom
With Russia's full-scale invasion in its third year, Sandworm (aka FROZENBARENTS) remains a formidable threat to Ukraine. The group’s operations in support of Moscow’s war aims have proven tactically and operationally adaptable, and as of today, appear to be better integrated with the activities of Russia’s conventional forces than in any other previous phase of the conflict. To date, no other Russian government-backed cyber group has played a more central role in shaping and supporting Russia’s military campaign.
Yet the threat posed by Sandworm is far from limited to Ukraine. Mandiant continues to see operations from the group that are global in scope in key political, military, and economic hotspots for Russia. Additionally, with a record number of people participating in national elections in 2024, Sandworm’s history of attempting to interfere in democratic processes further elevates the severity of the threat the group may pose in the near-term.
Given the active and diffuse nature of the threat posed by Sandworm globally, Mandiant has decided to graduate the group into a named Advanced Persistent Threat: APT44 . As part of this process, we are releasing a report, “ APT44: Unearthing Sandworm ”, that provides additional insights into the group’s new operations, retrospective insights, and context on how the group is adjusting to support Moscow’s war aims.
Key Findings
Sponsored by Russian military intelligence, APT44 is a dynamic and operationally mature threat actor that is actively engaged in the full spectrum of espionage, attack, and influence operations. While most state-backed threat groups tend to specialize in a specific mission such as collecting intelligence, sabotaging networks, or conducting information operations, APT44 stands apart in how it has honed each of these capabilities and sought to integrate them into a unified playbook over time. Each of these respective components, and APT44’s efforts to blend them for combined effect, are foundational to Russia’s guiding “information confrontation” concept for cyber warfare.

Figure 1: APT44’s spectrum of operations
APT44 has aggressively pursued a multi-pronged effort to help the Russian military gain a wartime advantage and is responsible for nearly all of the disruptive and destructive operations against Ukraine over the past decade. Throughout Russia’s war, APT44 has waged a high intensity campaign of cyber sabotage inside of Ukraine. Through the use of disruptive cyber tools, such as wiper malware designed to disrupt systems, APT44 has sought to impact a wide range of critical infrastructure sectors. At times, these operations have been coordinated with conventional military activity, such as kinetic strikes or other forms of sabotage, in an attempt to achieve joint military objectives.
However, as the war has endured, APT44’s relative focus has transitioned away from disruption to intelligence collection. The group’s targets and methods have shifted significantly in the second year of the war, with increasing emphasis placed on espionage activity intended to provide battlefield advantage to Russia’s conventional forces. For example, one long-running APT44 campaign has assisted forward-deployed Russian ground forces to exfiltrate communications from captured mobile devices in order to collect and process relevant targeting data. APT44’s approach to supporting Russia’s military campaign has evolved considerably over the past two years.

Figure 2: APT44’s wartime disruptive activity
We assess with high confidence that APT44 is seen by the Kremlin as a flexible instrument of power capable of servicing Russia's wide ranging national interests and ambitions, including efforts to undermine democratic processes globally.
Despite being an arm of Russia’s military, the group’s sabotage activity is not limited to military objectives and also spans Russia’s wider national interests, such as driving the Kremlin’s political signaling efforts, responses to crises, or intended non-escalatory responses to perceived slights to Moscow’s stature in the world.
APT44’s support of the Kremlin’s political objectives has resulted in some of the largest and most consequential cyber attacks in history. These operations include first-of-their-kind disruptions of Ukraine's energy grid in the winters of 2015 and 2016, the global NotPetya attack timed to coincide with Ukraine’s Constitution Day in 2017, and the disruption of the opening ceremony of the 2018 Pyeongchang Olympics in response to Russia's doping ban from the games, to name a few.

Figure 3: Timeline of consequential pre-war APT44 operations
Due to its history of aggressive use of network attack capabilities across political and military contexts, APT44 presents a persistent, high severity threat to governments and critical infrastructure operators globally where Russian national interests intersect. The combination of APT44's high capability, risk tolerance, and far-reaching mandate to support Russia’s foreign policy interests places governments, civil society, and critical infrastructure operators around the world at risk of falling into the group's sights on short notice.
We also judge APT44 to present a significant proliferation risk for new cyber attack concepts and methods. Continued advancements and in-the-wild use of the group’s disruptive and destructive capabilities has likely lowered the barrier of entry for other state and non-state actors to replicate and develop their own cyber attack programs. Russia itself is almost certainly alert to and concerned about this proliferation risk, as Mandiant has observed Russian cybersecurity entities exercise their ability to defend against categories of disruptive cyber capabilities originally used by APT44 against Ukraine.
Looking Ahead
APT44 will almost certainly continue to present one of the widest and highest severity cyber threats globally. It has been at the forefront of the threat landscape for over a decade and is responsible for a long list of firsts that have set precedents for future cyber attack activity. Patterns of historical activity, such as efforts to influence elections or retaliate against international sporting bodies, suggest there is no limit to the nationalist impulses that may fuel the group’s operations in the future.
As Russia’s war continues, we anticipate Ukraine will remain the principal focus of APT44 operations. However, as history indicates, the group’s readiness to conduct cyber operations in furtherance of the Kremlin’s wider strategic objectives globally is ingrained in its mandate. We therefore assess that changing Western political dynamics, upcoming elections, and emerging issues in Russia’s near abroad will also continue to shape APT44’s operations for the foreseeable future.
Protecting the Community
As part of our research, we take various steps to protect customers and the community:
- Upon discovery, all identified websites and domains are added to Safe Browsing to protect users from further exploitation.
- All targeted Gmail and Workspace users are sent government-backed attacker alerts , notifying them of the activity, encouraging potential targets to enable Enhanced Safe Browsing for Chrome, and ensuring them that all devices are updated.
- Where possible, Mandiant sends victim notifications via the Victim Notification Program .
- If you are a Google Chronicle Enterprise+ customer, Chronicle rules were released to your Emerging Threats rule pack, and IOCs are available for prioritization with Applied Threat Intelligence .
- A VirusTotal Collection featuring APT44-related indicators of compromise is now available for registered users.
We are committed to sharing our findings with the security community to raise awareness, and with companies and individuals that might have been targeted by these activities.
Read the APT44 report for our full analysis of this group, a detailed list of malware used by APT44 since 2018, hunting rules for detecting the malware, and a list of Mandiant Security Validation actions organizations can use to validate their security controls.
- Threat Intelligence
Related articles

FakeNet-NG Levels Up: Introducing Interactive HTML-Based Output
By Mandiant • 6-minute read
Apache XML Security for C++ Library Allows for Server-Side Request Forgery
Cutting edge, part 4: ivanti connect secure vpn post-exploitation lateral movement case studies.
By Mandiant • 31-minute read
SeeSeeYouExec: Windows Session Hijacking via CcmExec
Weekly: HC3 Social Engineering Warning, ReliaQuest Q1 Phishing Report, Microsoft Copilot ShadowTalk: Powered by ReliaQuest
In this episode of ShadowTalk, host Chris, along with Gjergji and James, discuss the latest news in cyber security and threat research. Topics this week include: Health sector Cybersecurity Coordination Center (HC3) issues alert warning regarding attackers using social engineering to target IT helpdesk's across the health sectorReliaQuest releases it's findings from it's Q1 Phishing reportHow improper permissions can lead to problems with new Microsoft Copilot AIResources: https://www.reliaquest.com/blog/health-care-social-engineering-campaign/https://www.reliaquest.com/blog/phishing-tactics-and-trends-2024/
- More Episodes
- © 2024 ShadowTalk: Powered by ReliaQuest
- About Campus Insider

- Search Search
5 Research Topics in Cybersecurity
In 2022, market and consumer data firm Statista reported that cyberattacks would cost individuals and companies $8.4 trillion globally that year. By 2027, it projected, the cost would rise to $23.8 trillion. Cyberattacks occur when individuals gain unauthorized access to digital systems and information for malicious purposes. Their enormous cost to people and organizations makes it critical to protect systems, software and data against those attacks.
The term “cybersecurity” refers to efforts to protect corporate or personal electronic equipment against these costly attacks. Understanding the vulnerabilities that can allow unauthorized and damaging access to digital systems is a key component in cybersecurity research. An advanced degree in information security management can help professionals learn how cybersecurity risks are evolving, what cybersecurity risks to look for in their own organizations and how to address them.
What Is Cybersecurity Research?
Cybersecurity research focuses on reviewing digital tools and processes to reveal potential vulnerabilities. Research on cybersecurity topics ranging from the Internet of Things (IoT) to work-from-home (WFH) information security can help people and companies stave off data breaches in those key areas.
Cybersecurity professionals can rely on computer science research tactics such as testing web browsers and online applications to uncover areas that a hacker could exploit to gain unauthorized data access. They can also turn to empirical research that examines issues related to cybersecurity from various angles, from criminal science to international relations, and that offers approaches to address those concerns.
In fact, conducting research about potential security threats and information technology (IT) trends is a key responsibility of cybersecurity professionals, such as information security analysts.
Why Is Cybersecurity Research Important?
The value of cybersecurity research is growing due to the proliferation of connected devices that allow cybercriminals to access digital information — and as the costs associated with successful cyberattacks increase.
The origin of cyberattacks can be computers and the systems that run them, but it can also be any of hundreds of everyday devices that use technology to collect and share data. From smartphones to medical equipment, the tools that cyberattackers can compromise generate or store a staggering amount of data.
Statista reports that the amount of data created, copied, downloaded and read globally in 2010 was 2 zettabytes. By 2025, Statista predicts, the capacity of the data in use around the world will reach 181 zettabytes.
The growth in the use of data is occurring alongside a host of issues, from COVID-19-related disruptions to geopolitical events, that can make the technology that shares and stores it more vulnerable to attack. Conducting research on cybersecurity topics can assist IT professionals in protecting these large amounts of data during challenging times by helping them:
- Understand the vulnerabilities of digital tools and processes
- Determine the significance of data breach impacts
- Prioritize their efforts to ensure protection of critical information
5 Current Research Topics in Cybersecurity?
Today’s most pressing research topics in cybersecurity go beyond password protection and firewalls. A global pandemic, geopolitical events and technological advances are also behind some key topics that are now driving cybersecurity research. Below are five of those top cybersecurity research topics.
1. Artificial Intelligence
Artificial intelligence (AI), in which machines complete tasks that traditionally had required humans to perform, today is helping computing professionals observe and analyze activity related to large amounts of digital data. The efficiency of using AI for cybersecurity can lead to significant savings as organizations respond to data compromises. The shortened response time led companies to an average of $3 million in savings in those situations, according to a 2022 report from IBM.
One key research topic for cybersecurity professionals is how best to use AI to find potential vulnerabilities and remove them — before cyberattackers use that same technology to find those security risks and exploit them.
However, AI in the wrong hands can also present a cybersecurity risk. AI can also be a tool for misusing data, with cybercriminals relying on this technology to create inauthentic emails and phone messages to trick users into providing personal data. The increasing reliance on AI makes this issue even more important for cybersecurity researchers, with Statista projecting in 2022 that the AI software market would reach $126 billion around the world by 2025.
2. Digital Supply Chains
Digital supply chain systems monitor and evaluate the functions of each party in the chain, to help them produce and distribute products more efficiently. Hackers can exploit the technology used in this process, making cyberattacks an additional threat to supply chains already experiencing disruptions related to the pandemic.
For example, technology research firm Gartner, predicted in 2022 that by 2025, a total of 45 percent of companies would suffer digital attacks on their supply chains. This percentage is three times higher than the percentage from 2021. A 2022 report from cybersecurity company Venafi found that 82 percent of chief information officers feared that their organizations’ supply chains were vulnerable to this type of attack.
Cybersecurity professionals today are investigating potential digital security risks in supply chains, while corporate leaders are seeking out suppliers that focus on researching — and correcting — these vulnerabilities.
3. Internet of Things
The IoT refers to the ability to connect almost any device with the internet and with other connected tools. From kitchen appliances to wearable fitness gadgets, numerous products and tools are part of the IoT. Statista reported in 2022 that more than 11 million devices were digitally connected in 2021. The firm also projected that more than 29 billion devices would be IoT connected by 2030.
The many devices that rely on the IoT measure and process vast amounts of data, and the networks and cloud systems that hold and share that data present a host of security risks. A key area of cybersecurity research has been tracking these vulnerabilities. Manufacturers, consumers and governments have begun using the knowledge gathered by cybersecurity researchers to establish practices and policies that safeguard against the risks these researchers are finding.
4. State-Sponsored Attacks
Cyberattacks from government actors seeking state secrets are nothing new, but a growing trend is for hackers seeking this unauthorized access to target organizations and individuals with no government affiliation. The ultimate goal can be intelligence, technology theft, supply chain disruption or even influencing internal politics through disinformation.
A 2022 Forbes article noted that in 2023, more than 70 nations were set to conduct elections, and the digital activities related to these events, including reports about them, are a frequent target of hostile government actors. Additionally, countries involved in armed conflicts increasingly rely on cyberattacks to gain advantage over enemy governments, even when it involves interfering with the work of private companies and citizens.
These trends have made it critical for cybersecurity researchers to learn more about potential vulnerabilities in government networks, attacks on private companies that can impact critical infrastructure, and the security of elections.
5. Working From Home
Fueled by pandemic restrictions, the number of WFH employees exploded in recent years. The number of remote workers will reach more than 36 million in the U.S. by 2025, according to 2020 projections from freelancing platform Upwork.
The many employees based at off-site locations have made managing data security difficult for companies, whose workers may use unprotected devices to access and transmit business information. That leaves the employees vulnerable to attacks that target sensitive data or threaten malicious activity unless the company meets the hackers’ demands.
Adding to the security risk is the proliferation of work and other activity that requires the use of the internet and internet-based tools like videoconferencing. A 2021 Pew Research Center survey showed that 40 percent of Americans had relied on these types of tools and processes in new ways since the pandemic began in early 2020. Cybersecurity professionals are studying how best to protect employees — and the corporate data they use in their work — from cyberattackers.
Take a Leadership Role in Cybersecurity
Cybersecurity research can shed light on issues with data protection — and the tools and processes that provide it. If you’re ready to help guide your organization’s response to cybersecurity issues, explore Augusta University Online’s Master of Science (MS) in Information Security Management program.
Through online courses focused on Certified Information Systems Security Professional (CISSP) certification elements, students can gain the knowledge to help their employers navigate today’s cybersecurity challenges. Explore how AU Online’s MS in Information Security Management can help you reach your career goals.
Built In, “What Is Artificial Intelligence?” Cybersecurity and Infrastructure Security Agency, Cyber Threats and Advisories Forbes, “The Top Five Cybersecurity Trends in 2023” Gartner, “7 Top Trends in Cybersecurity for 2022” IBM, “Cost of Data Breach 2022: A Million Dollar Race to Detect and Respond” IBM, What Is Cybersecurity? Journal of Cybersecurity, About the Journal Microsoft, What Is a Cyberattack? Network World, “What Is IoT? The Internet of Things Explained” Oracle, “Digital Supply Chain Explained” Pew Research Center, “The Internet and the Pandemic” Statista, Estimated Cost of Cybercrime Worldwide From 2016 to 2027 Statista, Number of Internet of Things (IoT)-Connected Devices Worldwide From 2019 to 2021, With Forecasts From 2022 to 2030 Statista, Revenues From the Artificial Intelligence (AI) Software Market Worldwide From 2018 to 2025 Statista, Volume of Data/Information Created, Captured, Copied, and Consumed Worldwide From 2010 to 2020, With Forecasts From 2021 to 2025 TechRadar Pro, “Why Cybersecurity Research Is Now More Important Than Ever” The Conversation, “5 Ways the COVID-19 Pandemic Has Forever Changed Cybersecurity” Upwork, Upwork Study Finds 22% of American Workforce Will Be Remote by 2025 U.S. Bureau of Labor Statistics, Information Security Analysts Venafi, “Study: 82% of CIOs Say Their Software Supply Chains Are Vulnerable” Vivaldi, “An Insight Into Security Research and Ethical Hacking”

Augusta University Online
Related articles.

Health Information Management vs. Health Informatics

Addressing Health Disparities in Public Health

Public Health Educator: Salary and Job Description

Remote Learning Resources for Students and Teachers
- Internet ›
Cyber Crime & Security
- Length of impact after a ransomware attack U.S. Q1 2020- Q2 2022
Average duration of downtime after a ransomware attack at organizations in the United States from 1st quarter 2020 to 2nd quarter 2022
Additional Information
Show sources information Show publisher information Use Ask Statista Research Service
United States
Q1 2020 to Q2 2022
attacks on business and organizations
The figures have been taken from several publications. The source adds the following information: "The figures represent the amount of time that the impacted organizations experienced some amount of material interruption or showed less than 100 percent productivity as a result of the attack."
Other statistics on the topic Healthcare and cybercrime in the U.S.
- Number of data compromises and impacted individuals in U.S. 2005-2023
- Average cost per data breach in the United States 2006-2023
- Average total cost per data breach worldwide 2020-2023, by industry
- Cybercrime incidents worldwide 2021-2022, by industry and organization size
- Immediate access to statistics, forecasts & reports
- Usage and publication rights
- Download in various formats
You only have access to basic statistics.
- Instant access to 1m statistics
- Download in XLS, PDF & PNG format
- Detailed references
Business Solutions including all features.
Statistics on " Healthcare and cybercrime in the United States "
- Data breaches worldwide 2021-2022, by target industry and organization size
- Global commonly breached type of data 2021-2022, by attack pattern
- U.S. number of data sets affected in data breaches Q1 2020-Q4 2023
- Data breach density in the U.S. Q3 2022-Q3 2023
- Private data violation incidents in the U.S. 2020-2023, by industry
- Most frequent cyber attacks in the global healthcare industry 2022, by type
- Ransomware attack count on U.S. healthcare organizations 2019-2023 YTD, by state
- U.S. healthcare sector breadth of ransomware attacks 2020-2022
- U.S. healthcare breadth of IoT and IoMT cyberattacks 2020-2022
- U.S. impact of ransomware on healthcare institutions 2022
- U.S. healthcare sector impact of disruptive cyberattacks 2022
- Ransomware attacks downtime estimated cost U.S. healthcare 2019-2023 YTD
- Ransomware attacks caused average downtime U.S. healthcare 2019-2023 YTD, by days
- Number of data compromises in the U.S. healthcare sector 2005-2023
- U.S. number of resolved health data breaches 2019-2023 YTD
- Number of large-scale data breaches in the U.S. healthcare industry 2009-2022
- Biggest healthcare data breaches to date in the U.S. as of 2023
- Biggest healthcare data breaches in the U.S. in 2022
- U.S. number of health data records exposed in data breaches 2009-2022
- U.S. healthcare data breach reporting entity distribution 2022, by type
- Health records impacted by data breaches in the U.S. H2 2022-H1 2023, by location
- U.S. health data breaches caused by hacking 2014-2022
- Causes of healthcare data breaches in the U.S. 2022, by number of data breaches
- U.S. health data breaches 2022, by cause
- Global cost per breached data record 2014-2023
- Estimated ransom demanded from U.S. healthcare organizations 2019-2023 YTD
- Median costs of all cyber attacks in the U.S and Europe 2021-2023, by country
- U.S. healthcare IoT/IoMT cybersecurity budget change factors 2022
- Annual U.S. healthcare sector IoT/IoMT device security spend 2022
- Frequency of cybersecurity training in healthcare organizations U.S. 2022
- Cybersecurity awareness training types in healthcare organizations U.S. 2022
- Cybersecurity budget change in healthcare organizations U.S. 2022-2023
- Ransom payment readiness in healthcare organizations U.S. 2022
- U.S. number of OCR penalties for HIPAA violations 2008-H1 2023
- Annual amount of HIPAA violation penalties 2008-H12023
- U.S. OCR penalties for HIPAA violations 2023
Other statistics that may interest you Healthcare and cybercrime in the United States
- Basic Statistic Cybercrime incidents worldwide 2021-2022, by industry and organization size
- Basic Statistic Data breaches worldwide 2021-2022, by target industry and organization size
- Basic Statistic Global commonly breached type of data 2021-2022, by attack pattern
- Premium Statistic U.S. number of data sets affected in data breaches Q1 2020-Q4 2023
- Premium Statistic Data breach density in the U.S. Q3 2022-Q3 2023
- Basic Statistic Number of data compromises and impacted individuals in U.S. 2005-2023
- Basic Statistic Private data violation incidents in the U.S. 2020-2023, by industry
Cyberattacks
- Premium Statistic Most frequent cyber attacks in the global healthcare industry 2022, by type
- Basic Statistic Ransomware attack count on U.S. healthcare organizations 2019-2023 YTD, by state
- Basic Statistic U.S. healthcare sector breadth of ransomware attacks 2020-2022
- Basic Statistic U.S. healthcare breadth of IoT and IoMT cyberattacks 2020-2022
Impact of cyberattacks
- Basic Statistic Length of impact after a ransomware attack U.S. Q1 2020- Q2 2022
- Basic Statistic U.S. impact of ransomware on healthcare institutions 2022
- Basic Statistic U.S. healthcare sector impact of disruptive cyberattacks 2022
- Basic Statistic Ransomware attacks downtime estimated cost U.S. healthcare 2019-2023 YTD
- Basic Statistic Ransomware attacks caused average downtime U.S. healthcare 2019-2023 YTD, by days
Data breaches
- Premium Statistic Number of data compromises in the U.S. healthcare sector 2005-2023
- Basic Statistic U.S. number of resolved health data breaches 2019-2023 YTD
- Basic Statistic Number of large-scale data breaches in the U.S. healthcare industry 2009-2022
- Premium Statistic Biggest healthcare data breaches to date in the U.S. as of 2023
- Premium Statistic Biggest healthcare data breaches in the U.S. in 2022
- Premium Statistic U.S. number of health data records exposed in data breaches 2009-2022
- Premium Statistic U.S. healthcare data breach reporting entity distribution 2022, by type
- Premium Statistic Health records impacted by data breaches in the U.S. H2 2022-H1 2023, by location
Causes of healthcare data breaches
- Premium Statistic U.S. health data breaches caused by hacking 2014-2022
- Basic Statistic Causes of healthcare data breaches in the U.S. 2022, by number of data breaches
- Premium Statistic U.S. health data breaches 2022, by cause
Cost of security incidents
- Premium Statistic Average cost per data breach in the United States 2006-2023
- Premium Statistic Global cost per breached data record 2014-2023
- Premium Statistic Average total cost per data breach worldwide 2020-2023, by industry
- Basic Statistic Estimated ransom demanded from U.S. healthcare organizations 2019-2023 YTD
- Premium Statistic Median costs of all cyber attacks in the U.S and Europe 2021-2023, by country
Health cybersecurity
- Basic Statistic U.S. healthcare IoT/IoMT cybersecurity budget change factors 2022
- Basic Statistic Annual U.S. healthcare sector IoT/IoMT device security spend 2022
- Premium Statistic Frequency of cybersecurity training in healthcare organizations U.S. 2022
- Basic Statistic Cybersecurity awareness training types in healthcare organizations U.S. 2022
- Basic Statistic Cybersecurity budget change in healthcare organizations U.S. 2022-2023
- Basic Statistic Ransom payment readiness in healthcare organizations U.S. 2022
Penalties for HIPAA violations
- Basic Statistic U.S. number of OCR penalties for HIPAA violations 2008-H1 2023
- Basic Statistic Annual amount of HIPAA violation penalties 2008-H12023
- Basic Statistic U.S. OCR penalties for HIPAA violations 2023
Further Content: You might find this interesting as well

IMAGES
VIDEO
COMMENTS
60+ Latest Cyber Security Research Topics for 2024. The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics /ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time.
If you're still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic. A comprehensive list of cybersecurity-related research topics. Includes 100% free access to a webinar and research topic evaluator.
Cyber Security Research Topics. Cyber Security Research Topics are as follows: The role of machine learning in detecting cyber threats. The impact of cloud computing on cyber security. Cyber warfare and its effects on national security. The rise of ransomware attacks and their prevention methods.
9 👩💻Cyber Security Topics on Computer and Software. There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and ...
Machine learning and AI are research topics in cybersecurity, aiming to develop algorithms for threat detection, enhance intelligence and automate risk mitigation. However, security risks like adversarial attacks require attention. Using AI/ML to Analyse Cyber Threats - This cyber security research paper analyses cyber threats and could ...
These great topics for cybersecurity can make you more knowledgeable about the current trends. Risk management in computing. The most common causes of a data breach in the 21 st. The best way to protect your device and synchronize the data. The significance of computer forensics in the current digital era.
About the journal. Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore ...
Abstract. This paper presents a systematic review of empirical research on cybersecurity issues. 14 empirical articles about cybersecurity, published in the two top IS journals, MISQ (12) and ISR ...
Keywords: Cybersecurity, Artificial Intelligence, Adversarial machine learning . Important Note: All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements. Frontiers reserves the right to guide an out-of-scope manuscript to a more suitable ...
Today's most pressing research topics in cybersecurity go beyond password protection and firewalls. A global pandemic, geopolitical events and technological advances are also behind some key topics that are now driving cybersecurity research. Below are five of those top cybersecurity research topics. 1. Artificial Intelligence.
A short, spoken-word summary from CSIS's Daniel Byman on his report with Daniel W. Linna Jr. and V.S. Subrahmanian, Government Use of Deepfakes: The Questions to Ask. CSIS's cybersecurity research and analysis work covers cyber warfare, encryption, military cyber capacity, hacking, financial terrorism, and more.
The Institute of Information Engineering (IIE) is a national research institute in Beijing that specializes in comprehensive research on theories and applications related to information technology. IIE strives to be a leading global academic institution by creating first-class research platforms and attracting top researchers.
The journal publishes research articles and reviews in the areas including, but not limited to: • Cryptography and its applications. • Network and critical infrastructure security. • Hardware security. • Software and system security. • Cybersecurity data analytics. • Data-driven security and measurement studies. • Adversarial ...
204 Research Topics on Technology & Computer Science. A List of 580 Interesting Research Topics [2024 Edition] A List of 179 Problem Solution Essay Topics & Questions. 193 Interesting Proposal Essay Topics and Ideas. 226 Research Topics on Criminal Justice & Criminology.
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category. Evaluation of the operation of antimalware in preventing cyber attacks.
The researchers analysed 965 cybersecurity research papers published between 2012 and 2016. They created a taxonomy of the types of data that are created and shared and then analysed the data collected via datasets. ... various databases were queried to collect relevant literature on the topic of cybersecurity and cyber risks. Due to the spread ...
Overview. NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in ...
Each of these working groups focuses on a unique topic or aspect of cloud security, including AI, IoT, DevSecOps, and much more. Then, every month, research publications created by these working groups and reviewed by the industry are released on the CSA website, free for anyone to download and read. In this article, we've defined 12 CSA ...
154 Exceptional Cybersecurity Research Topics For You. If you are studying computer science or IT-related course, you will encounter such a task. It is one of the most technical assignments, primarily in the era of advanced digital technologies. Students may not have the muscles to complete such papers on their own.
On the other hand, we mentioned 111+ stunning cybersecurity research topics for 2023 offer an excellent opportunity for researchers to explore and address critical cybersecurity challenges. However, the ever-evolving technological landscape presents new security challenges every day, and it is essential to keep up with the latest trends to stay ...
The Gartner Top Trends in Cybersecurity 2024 survey finds emerging pressure from: In response, cybersecurity leaders are working to equip their functions with agile and responsive capabilities. The 2024 trends report shows their actions and priorities center on nine practices, technical capabilities and structural reforms — each helping ...
Topics Select a term to learn more about it, and to see CSRC Projects, Publications, News, Events and Presentations on that topic. ... Federal Cybersecurity Research and Development Strategic Plan; ... OMB Circular A-11; OMB Circular A-130; laws. Cyber Security R&D Act; Cybersecurity Enhancement Act; E-Government Act; Energy Independence and ...
AI-powered cybersecurity solutions can immediately analyze vast amounts of data to identify patterns indicative of potential cyber threats. "Historically, cyber security would summon a knee-jerk ...
Government agencies are now encouraging industries to enhance their security systems to detect and respond proactively to cybersecurity incidents. Consequently, equipping with a security operation center that combines the analytical capabilities of human experts with systems based on Machine Learning (ML) plays a critical role. In this setting, Security Information and Event Management (SIEM ...
Cybersecurity for Researchers. Tuesday, October 22, 2024. 1pm via Zoom. This brown bag session will focus on secure campus tools and services that Research IT and Berkeley IT offer to researchers, tips on navigating campus security processes, and cybersecurity best practices for keeping your research and research subjects safe.In partnership ...
In this episode of ShadowTalk, host Chris, along with Marken, discuss the latest news in cyber security and threat research. This weeks topics include: Palo Alto Critical Vulnerability under active exploitation ReliaQuest research on VPN attack surface managementOptum Healthcare data breached by Ran…
APT44 has aggressively pursued a multi-pronged effort to help the Russian military gain a wartime advantage and is responsible for nearly all of the disruptive and destructive operations against Ukraine over the past decade. Throughout Russia's war, APT44 has waged a high intensity campaign of cyber sabotage inside of Ukraine.
In this episode of ShadowTalk, host Chris, along with Gjergji and James, discuss the latest news in cyber security and threat research. Topics this week include: Health sector Cybersecurity Coordination Center (HC3) issues alert warning regarding attackers using social engineering to target IT helpdesk's across the health sectorReliaQuest ...
Today's most pressing research topics in cybersecurity go beyond password protection and firewalls. A global pandemic, geopolitical events and technological advances are also behind some key topics that are now driving cybersecurity research. Below are five of those top cybersecurity research topics. 1. Artificial Intelligence.
Length of impact after a ransomware attack U.S. Q1 2020- Q2 2022. Published by Ani Petrosyan , Apr 12, 2024. As of the second quarter of 2022, the average length of interruption after ransomware ...