Networking | Cloud | DevOps | IaC

IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
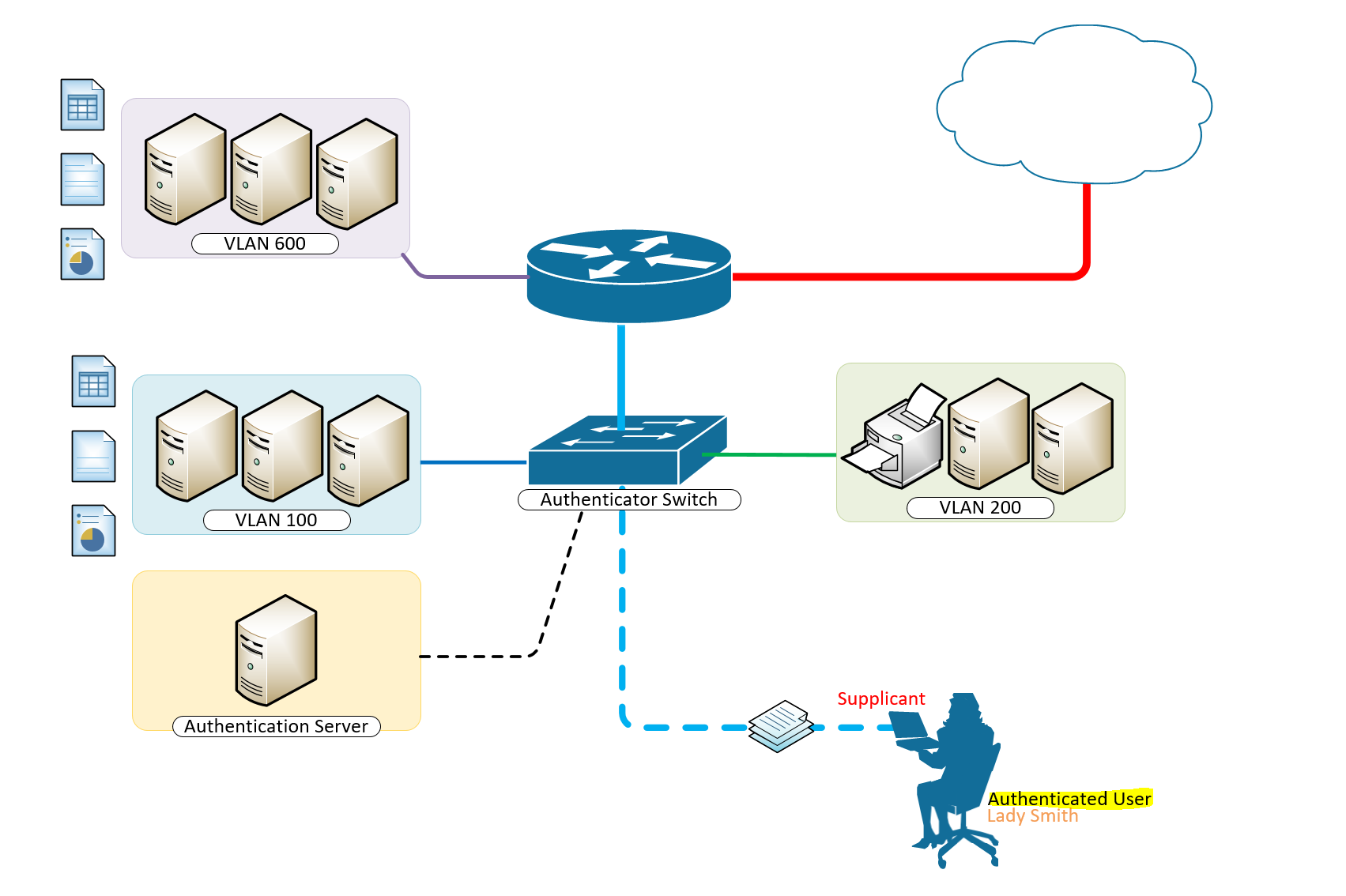
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server

Dynamic VLAN Assignment: Wireless
Dynamic VLAN Assignment
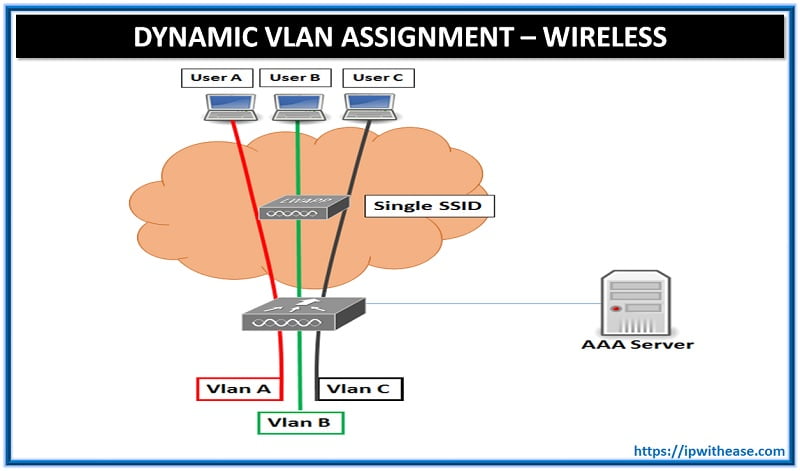
Objective: To dynamically Assign Wireless User to VLAN based on user credentials. This type of setup is called “Dynamic VLAN Assignment”
Description: Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco Secure ACS. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
Related- Cisco ACS vs ISE Comparison
Therefore, when a client attempts to associate to a LAP registered with a controller, the LAP passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes certain Internet Engineering Task Force (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that should be assigned to the wireless client. The SSID ( WLAN , in terms of WLC) of the client does not matter because the user is always assigned to this predetermined VLAN ID.
WLC Configuration
This configuration requires these steps:
Configure the WLC with the Details of the Authentication Server
- Configure the Dynamic Interfaces (VLANs)
- Configure the WLANs ( SSID )
It is necessary to configure the WLC so it can communicate with the RADIUS server to authenticate the clients, and also for any other transactions.
Complete these steps:
- From the controller GUI, click Security .
- Enter the IP address of the RADIUS server and the Shared Secret key used between the RADIUS server and the WLC.
This Shared Secret key should be the same as the one configured in the RADIUS server under Network Configuration > AAA Clients > Add Entry. Here is an example window from the WLC:
Configure the Dynamic VLAN (Interfaces)
This procedure explains how to configure dynamic interfaces on the WLC. As explained earlier in this document, the VLAN ID specified under the Tunnel-Private-Group ID attribute of the RADIUS server must also exist in the WLC.
In the example, the user1 is specified with the Tunnel-Private-Group ID of 10 (VLAN =10) on the RADIUS server.
You can see the same dynamic interface (VLAN=10) configured in the WLC in this example. From the controller GUI, under the Controller > Interfaces window, the dynamic interface is configured.
- Click Apply on this window.
This takes you to the Edit window of this dynamic interface (VLAN 10 here).
Enter the IP Address and default Gateway of this dynamic interface
Note: Because this document uses an internal DHCP server on the controller, the primary DHCP server field of this window points to the Management Interface of the WLC itself. You can also use an external DHCP server, a router, or the RADIUS server itself as a DHCP server to the wireless clients. In such cases, the primary DHCP server field points to the IP address of that device used as the DHCP server. Refer to your DHCP server documentation for more information.
- Click Apply .
Now you are configured with a dynamic interface in your WLC. Similarly, you can configure several dynamic interfaces in your WLC. However, remember that the same VLAN ID must also exist in the RADIUS server for that particular VLAN to be assigned to the client.
Configure the WLANs (SSID)
This procedure explains how to configure the WLANs in the WLC.
- From the controller GUI, choose WLANs > New in order to create a new WLAN.
The New WLANs window is displayed.
- Enter the WLAN ID and WLAN SSID information.
You can enter any name to be the WLAN SSID. This example uses VLAN10 as the WLAN SSID.
- Click Apply in order to go to the Edit window of the WLAN SSID10.
Normally, in a wireless LAN controller, each WLAN is mapped to a specific VLAN (SSID) so that a particular user that belongs to that WLAN is put into the specific VLAN mapped. This mapping is normally done under the Interface Name field of the WLAN SSID window.
In the example provided, it is the job of the RADIUS server to assign a wireless client to a specific VLAN upon successful authentication. The WLANs need not be mapped to a specific dynamic interface on the WLC. Or, even though the WLAN to dynamic interface mapping is done on the WLC, the RADIUS server overrides this mapping and assigns the user that comes through that WLAN to the VLAN specified under the user Tunnel-Group-Private-ID field in the RADIUS server.
- Check the Allow AAA Override check box in order to override the WLC configurations by the RADIUS server.
- Enable the Allow AAA Override in the controller for each WLAN (SSID) configured.
When AAA Override is enabled, and a client has AAA and controller WLAN authentication parameters that conflict, client authentication is performed by the AAA (RADIUS) server. As part of this authentication, the operating system moves clients to a VLAN returned by the AAA server. This is predefined in the controller interface configuration.
For instance, if the corporate WLAN primarily uses a Management Interface assigned to VLAN 2, and if the AAA Override returns a redirect to VLAN 100, the operating system redirects all client transmissions to VLAN 100 even if the physical port to which VLAN 100 is assigned. When AAA Override is disabled, all client authentication defaults to the controller authentication parameter settings, and authentication is only performed by the AAA server if the controller WLAN does not contain any client-specific authentication parameters.
Continue Reading:
CONFIGURE INTERFACES ON WIRELESS CONTROLLER 5508
Wireless Interview Questions
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.” – Rashmi Bhardwaj (Author/Editor)
Related Posts

CISCO VSS vs JUNIPER VC
Introduction to CIFS Protocol
BGP FlowSpec: DDoS Mitigation
Leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Questions tagged [dynamic-vlan-assignment]
The dynamic-vlan-assignment tag has no usage guidance.
- Learn more…
- Unanswered (my tags)
NPS Dynamic VLAN Catch-All
- windows-server-2019
- dynamic-vlan-assignment
Yealink phones fail to get IP once assigned voice VLAN via DHCP (Mikrotik)
How does VLAN subnetting work on IPv6?
DHCPS - single mac whitelist, multiple subnets
OpenWRT Dynamic VLAN
- freeradius2
dynamic VLANs on cheap Access Point after switch
802.1x dynamic vlan assignment not assigning vlan.
Open vSwitch double VLAN tagging is ignored
- kvm-virtualization
- linux-networking
- openvswitch
Cisco switch VLANing based on MAC address
VLAN configuration
Assign VLAN per user credentials on VPN connections
How do I setup dynamic VLAN assignment on an autonomous Cisco 1142n?
- access-point

Vlan Management Policy Server ( VMPS) Configuration and Management
- cisco-catalyst
Dynamic VLANs with FreeRadius, OpenLDAP & Cisco WLC
How do I dynamically hand out dhcp and automatically put specific pc's on a specified vlan?
- network-design
Freeradius on Linux with dynamic VLAN assignment via AD
- active-directory
Need help getting Dynamic VLAN Assignment working with RADIUS and Dell PowerConnect 3524
- dell-powerconnect
How to configure FreeRadius to accept all authentication requests?
- authentication
Assign computers to specific VLANs with Dell PowerConnect 3524/6224
- mac-address
- The Overflow Blog
- Why configuration is so complicated
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
Related Tags
Hot network questions.
- How can the knight traverse a chessboard to make a path that sums to 100
- Is there a good term for a 'paper trail' that actually consists of e-mail communication?
- Mathematica yields repeated solutions when only one exists
- Why do valence electrons not push each other away?
- Best way to slice bread to keep it fresh
- Does the equivalence principle only apply for the gravitational field of an infinitely sized body?
- What does "6" mean in glibc.so.6?
- Different estimates of Least Squares and Maximum Likelihood Estimates under non-normality
- Reviewer rejects a paper and then publishes the same results as their own?
- Does the Intel 8080 ANI instruction clear or update the half-carry?
- Book on Hilbert spaces, including non-separable
- Double parenthesis in academic writing
- Is this dialogue Got or get?
- Risk of not capping old hose spigot
- Speed up Manipulate when including several static 3d plots in Show
- I forgot an item on board an airplane on a regular flight. Who should I contact to get it back?
- What was Silk Spectre II's relationship with superheroics?
- Is mathematical truth empirical?
- How can Diethyl Methylphosphonate be reduced into Diethyl Methylphosphonite?
- Is it possible for a humanoid to learn English within a few days, just from observing conversations?
- Can two interfering light beams create radio waves?
- The usage of the modal verb "must be"
- Which Vault-Tec Vaults are referenced in the Fallout TV series’ season 1 finale?
- Why is my render preview different from what the render result?
- Skip to content
- Skip to search
- Skip to footer
Configure VLANs on Wireless LAN Controllers
Available Languages
Download options.
- PDF (684.0 KB) View with Adobe Reader on a variety of devices
- ePub (625.9 KB) View in various apps on iPhone, iPad, Android, Sony Reader, or Windows Phone
- Mobi (Kindle) (386.8 KB) View on Kindle device or Kindle app on multiple devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes how to configure Virtual LANs (VLANs) on Wireless LAN controllers (WLCs).
Prerequisites
Requirements.
This procedure assumes that there is a functional DHCP server to provide IP addresses to the access points (APs) that are registered to the controller.
Components Used
Catalyst switch that runs Cisco IOS ® Software.
Cisco WLC 8540 that runs software version 8.10.190.0.
- Access Points
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Dynamic Interfaces on WLCs
Dynamic interfaces, also known as VLAN interfaces, are created by users and designed to be analogous to VLANs for wireless LAN clients.
A controller can support up to 512 dynamic interfaces (VLANs). Each dynamic interface is individually configured and allows separate communication streams to exist on any or all of a controller’s distribution system ports. Each dynamic interface controls VLANs and other communications between controllers and all other network devices, and each acts as a DHCP relay for wireless clients associated to Wireless LANs (WLANs) mapped to the interface.
It is possible to assign dynamic interfaces to distribution system ports, WLANs, the Layer 2 management interface, and the Layer 3 ap-manager interface. It is also possible to map the dynamic interface to a backup port.
Configure zero, one, or multiple dynamic interfaces on a distribution system port. However, all dynamic interfaces must be on a different VLAN or IP subnet from all other interfaces configured on the port. If the port is untagged, all dynamic interfaces must be on a different IP subnet from any other interface configured on the port.
For information about maximum number of VLANs supported on a Cisco WLC platform, see the respective Cisco WLC platform datasheet. Cisco recommends the use of tagged VLANs for dynamic interfaces.
VLANs with WLAN controllers use this model:
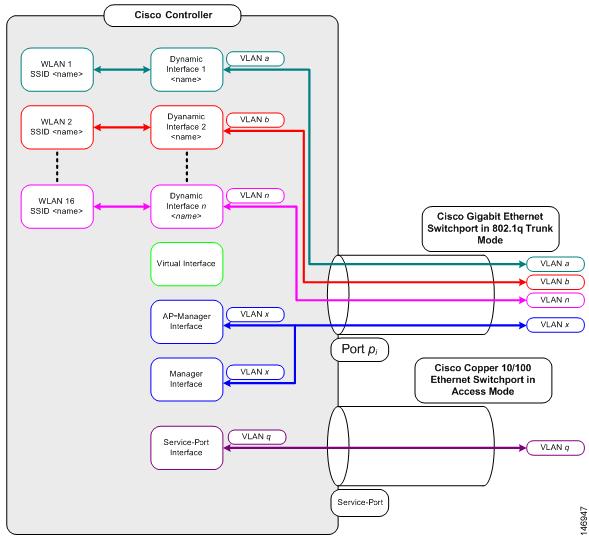
Prerequisites for Configuration of Dynamic Interfaces
To configure the dynamic interface of the controller , use tagged VLANs for dynamic interfaces.
Restrictions on Configuration Dynamic Interfaces
These restrictions apply for the configuration of dynamic interfaces on the controller:
- Wired clients cannot access management interface of the Cisco 2504 WLC with the IP address of the AP Manager interface.
- For SNMP requests that come from a subnet that is configured as a dynamic interface, the controller responds but the response does not reach the device that initiated the conversation.
- If a DHCP proxy and/or a RADIUS source interface is used, ensure that the dynamic interface has a valid routable address. Duplicate or overlapped addresses across controller interfaces are not supported.
- Do not use ap-manager as the interface name to configure dynamic interfaces as ap-manager is a reserved name.
This section presents the information to configure the features described in this document.
Note : Use the Command Lookup Tool ( registered customers only) to find more information on the commands used in this document.
Catalyst Switch that Runs Cisco IOS Software
Note : VLAN number 999 is used as native VLAN here. This means the untagged traffic that arrives at the WLC port comes from vlan 999. In this document, the WLC has management port with tagged VLAN 1, which means traffic to/from the WLC management interface goes on VLAN 1 and VLAN 999 is not used by the WLC.
WLAN Controller VLAN Configuration in GUI
Complete these steps on the WLAN controller.
From the WLC GUI, navigate to Controller > Interfaces . The Interfaces page lists all the interfaces that are configured on the WLC. In order to create a new dynamic interface, click New .
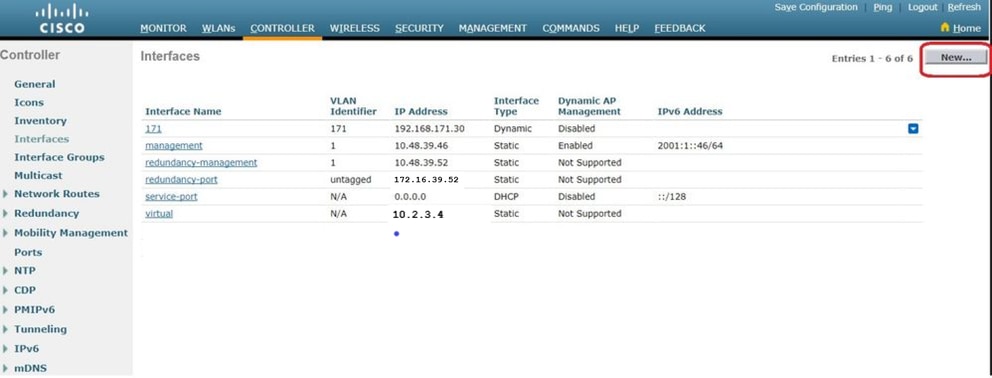
Enter the parameters specific to this VLAN. Some of the parameters include the IP Address , Netmask , Gateway , and the Primary DHCP Server IP address, and click Apply .
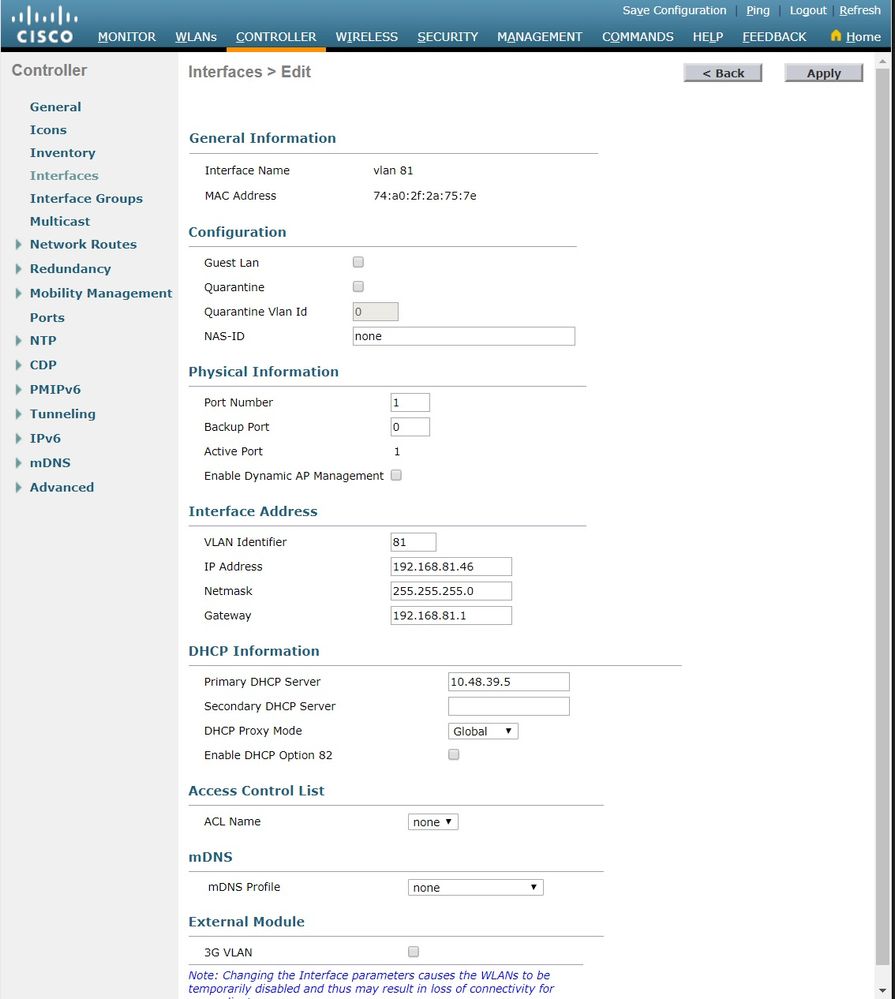
Note : The IP address assigned to this interface acts as the DHCP relay for a client to obtain an IP address from the DHCP server. For example, when a client attempts to associate to a WLAN/SSID (step 5 in this configuration) mapped to this dynamic interface, it performs a local subnet broadcast to identify the DHCP server. The controller sends a request to the DHCP server (or to itself if it is the DHCP server for the segment) with the IP address of this dynamic interface as relay IP to the DHCP server configured for this interface. The DHCP server assigns an IP address to the client from the configured DHCP scope.
Note : It is mandatory to have a valid IP address for technical reasons, but this IP address is not used unless DHCP proxy or radius interface overwrite (under WLAN config) are enabled.
Note : The Interface Name or VLAN name is used as radius attribute (airespace-interface-name) to return a VLAN name instead of number.
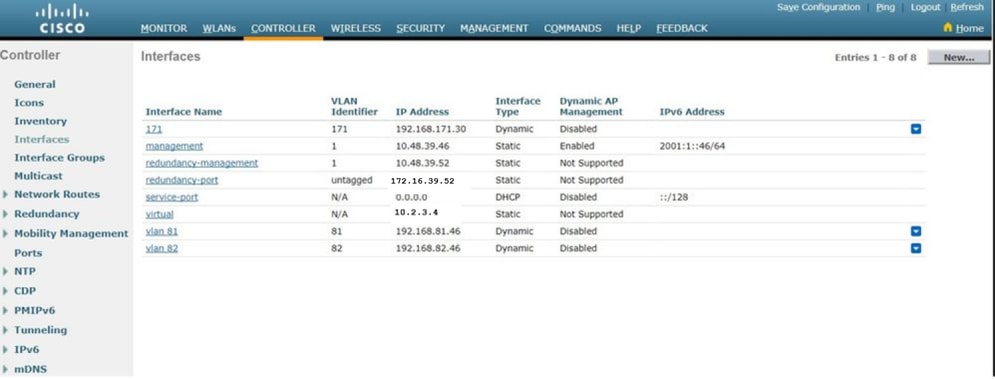
Verify the interface configuration. Click the Controller tab in the menu at the top of the window, and choose Interfaces from the menu on the left.
WLAN Controller VLAN Configuration in CLI
Use this section in order to configure your VLAN via command-line interface (CLI).
- Create the interface and the associated VLAN tag. The command is config interface create interface_namevlan_id.
Note : If there is a space in the VLAN/WLAN name as is the case in this example, make sure the name is in quotes.
- Define the IP address and default gateway. The command is config interface interface_nameIP_addressnetmaskgateway.
- Define the DHCP server. The command is config interface dhcp dynamic-interface <interface-name> primary <primary-server> [secondary] <secondary-server> .
- Issue this command in order to map the interface to a physical port: config interface port operator_defined_interface_name physical_ds_port_number .
- Verify the interface configuration. The command is show interface summary .
- Define the WLAN. The command is config wlan create wlan_idname .
- Define the interface for the WLAN. The command is config wlan interface wlan_idinterface_name . (W-8540-1) >config wlan interface 2 "vlan 81"
- Verify the WLAN and the associated interface. The command is show wlan summary .
Use this section to confirm that your configuration works properly.
Catalyst Switches Verification
Catalyst switch that runs Cisco IOS Software: show running-config interface interface_type interface_number .
WLAN Controller VLAN Verification
Troubleshoot.
Use this section to troubleshoot your configuration.
Troubleshoot Procedure
Complete these instructions in order to troubleshoot your configuration.
Ping from the WLAN controller to the default gateway that is configured on the VLAN routed interface, and then ping in the opposite direction.
WLAN controller:
(W-8540-1) >ping 192.168.81.1 Send count=3, Receive count=3 from 192.168.81.1 (W-8540-1) >
VLAN routed interface:
w-backbone-6k#ping 192.168.81.46 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.81.46, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms w-backbone-6k#
If the pings are unsuccessful, deploy a packet capture/sniffer at the switch and check in order to verify proper VLAN tagging.
Note : When you initiate the ping from your controller to a Layer 3 gateway, which is on the same subnet as your dynamic interface, the controller appears to source the ping from the dynamic interface.
Revision History
Contributed by Cisco Engineers
- Tiago Antunes Customer Engineering Delivery Technician
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )
This Document Applies to These Products
- Wireless LAN Controller Software
Dynamic VLAN assignment
Larger WLAN infrastructures often require individual WLAN clients to be assigned to certain networks. Assuming that the WLAN clients are always within range of the same APs, then assignment can be realized via the SSID in connection with a particular IP network. If on the other hand the WLAN clients frequently change their position and logon to different APs then, depending on the configuration, they may find themselves in a different IP network.
For WLAN clients to remain within a certain network independent of their current WLAN network, dynamically assigned VLANs can be used. Unlike the situation where VLAN IDs are statically configured for a certain SSID, in this case a RADIUS server directly assigns the VLAN ID to the WLAN client.
- The WLAN clients of two employees log into an AP in the WPA2-secured network with the SSID 'INTERNAL'. During registration, the RADIUS requests from the WLAN clients are directed to the AP. If the corresponding WLAN interface is in the operating mode 'managed' the RADIUS requests are automatically forwarded to the WLC. This forwards the request in turn to the defined RADIUS server. The RADIUS server can check the access rights of the WLAN clients. It can also use the MAC address to assign a certain VLAN ID, for example for a certain department. The WLAN client in Marketing, for example, receives the VLAN ID '10' and WLAN client from Research & Development receives '20'. If no VLAN ID is specified for the user, the SSID's primary VLAN ID is used.
- The WLAN clients of the guests log into the same AP in the unsecured network with the SSID 'PUBLIC'. This SSID is statically bound to the VLAN ID '99' and leads the guests into a certain network. Static and dynamic VLAN assignment can be elegantly operated in parallel.
- Activate VLAN tagging for the WLC. This is done in the physical parameters of the profile by entering a value greater than '0' for the management VLAN ID.
- For authentication via 802.1x, go to the encryption settings for the profile's logical WLAN network and choose a setting that triggers an authentication request.
- To check the MAC addresses, activate the MAC check for the profile's logical WLAN network. Note: For the management of WLAN modules with a WLC, a RADIUS server is required to operate authentication via 802.1x and MAC-address checks. The WLC automatically defines itself as the RADIUS server in the APs that it is managing—all RADIUS requests sent to the AP are then directly forwarded to the WLC, which can either process the requests itself or forward them to an external RADIUS server.
- To forward RADIUS requests to another RADIUS server, use LANconfig to enter its address into the list of forwarding servers in the configuration section 'RADIUS servers' on the Forwarding tab. Alternatively, external RADIUS servers can be entered in WEBconfig under Menu tree > LCOS Setup > RADIUS > Server > Forward servers . Also, set the standard realm and the empty realm to be able to react to different types of user information (with an unknown realm, or even without a realm).
- Configure the entries in the RADIUS server so that WLAN clients placing requests will be assigned the appropriate VLAN IDs as based on the identification of certain characteristics.
www.lancom-systems.com
LANCOM Systems GmbH | A Rohde & Schwarz Company | Adenauerstr. 20/B2 | 52146 Wuerselen | Germany | E‑Mail [email protected]


IMAGES
VIDEO
COMMENTS
This document introduces the concept of dynamic VLAN assignment. The document describes how to configure the wireless LAN controller (WLC) and a RADIUS server to assign wireless LAN (WLAN) clients into a specific VLAN dynamically. Prerequisites Requirements. Ensure that you meet these requirements before you attempt this configuration:
In order to accomplish dynamic VLAN assignment with WLCs based on ISE to AD group mapping, these steps must be performed: ISE to AD integration and configuration of authentication and authorization policies for users on ISE. WLC configuration in order to support dot1x authentication and AAA override for SSID 'office_hq'.
Complete these steps: From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add. Complete the configuration with the username, password, and user group as shown in the image: Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment.
The SSID (WLAN, in terms of WLC) of the client does not matter because the user is always assigned to this predetermined VLAN ID. The RADIUS user attributes used for the VLAN ID assignment are: IETF 64 (Tunnel Type)—Set this to VLAN. IETF 65 (Tunnel Medium Type)—Set this to 802 IETF 81 (Tunnel Private Group ID)—Set this to VLAN ID.
This document describes the concept of dynamic VLAN assignment and how to configure wireless LAN controller (WLC) and a RADIUS server to assign a wireless LAN (WLAN) clients to a specific VLAN dynamically. In this document, the RADIUS server is an Access Control Server (ACS) that runs Cisco Secure Access Control System Version 5.2.oduction
Create Network Policy Constraints for Accounting Group for VLAN 200. Create Network Policy Settings for Accounting Group for VLAN 200. Configuration Example. Here's an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization ...
Dynamic VLAN Assignment. Objective: To dynamically Assign Wireless User to VLAN based on user credentials. This type of setup is called "Dynamic VLAN Assignment" Description: Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user.This task of assigning users to a specific VLAN is handled by a RADIUS ...
•EachVLANhasa/24mask. •ACS5.2hasaself-signedcertificateinstalled. Configuring WLC (CLI) ThissectionshowsconfiguringWLAN,RADIUSServerandDHCPPoolforClientVLAN.
Configure a RADIUS Server and WLC for Dynamic VLAN Assignment - Cisco. Also, if I understand correctly, now you are evaluating products for deploying MSI. In this case, take a look at our cloud-based solution Action1 for deploying different types of software (msi and exe) on all computers on your network at the same time. Thanks for the info.
Really need to see some config here to even begin to understand what is going on with any certainty. If ISE is really sending over VLAN 0 and the WLC is accepting it, then simply unchecking the Allow AAA Override option on the WLC (WLANs -> <WLAN ID> -> Advanced) should prevent that if you aren't passing anything else from AAA and can take a bit more time finding the problem in your ISE config.
Complete these steps: From the ISE GUI, navigate to Administration > Network Resources > Network Devicesand select Add. Complete the configuration with the WLC management IP address and RADIUS shared secret between WLC and ISE as shown in the image: Step 2. Configure internal users on Cisco ISE.
This document describes the concept of dynamic VLAN assignment. Prerequisites The document describes how to configure the wireless LAN controller (WLC) and Identity Services Engine (ISE) server in order to assign wireless LAN (WLAN) clients into a specific VLAN dynamically. Requirements Cisco recommends that you have knowledge of these topics:
I'm trying to add a flow to a KVM machine using Open vSwitch 1.10.2 for it's networking, which double tag all traffic comming from one of the virtual machine's ports. I'm using the following command ... kvm-virtualization. linux-networking. vlan. openvswitch. dynamic-vlan-assignment. Itamar Tal. 1.
Add to Favorites. This case will reveal how to configure dynamic vlan assignment via radius. In some situation you would like to bind a mac-address to a specific VLAN and allow a host to get access the network only to a specific VLAN. You can use any Radius server, Huawei recommended solution is Agile Controller.
It is possible to assign dynamic interfaces to distribution system ports, WLANs, the Layer 2 management interface, and the Layer 3 ap-manager interface. It is also possible to map the dynamic interface to a backup port. ... This means the untagged traffic that arrives at the WLC port comes from vlan 999. In this document, the WLC has management ...
Dynamic VLAN assignment. Larger WLAN infrastructures often require individual WLAN clients to be assigned to certain networks. Assuming that the WLAN clients are always within range of the same APs, then assignment can be realized via the SSID in connection with a particular IP network. If on the other hand the WLAN clients frequently change ...