- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial

Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
- Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
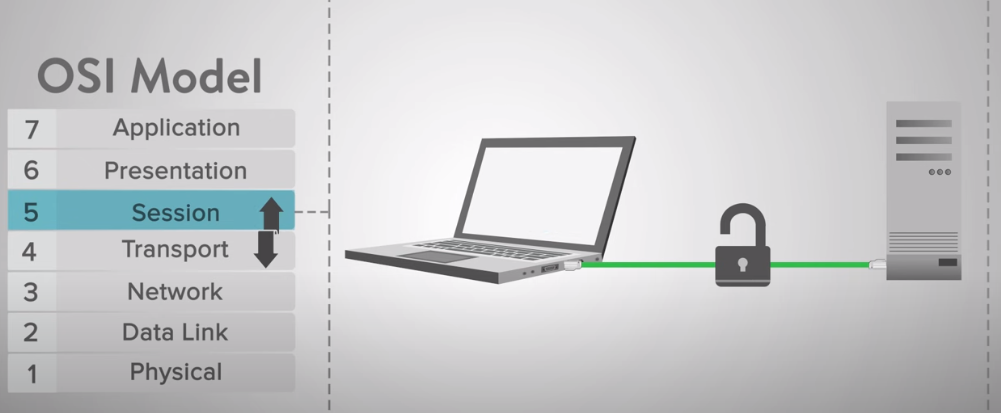
- Session Layer in OSI model
Presentation Layer in OSI model
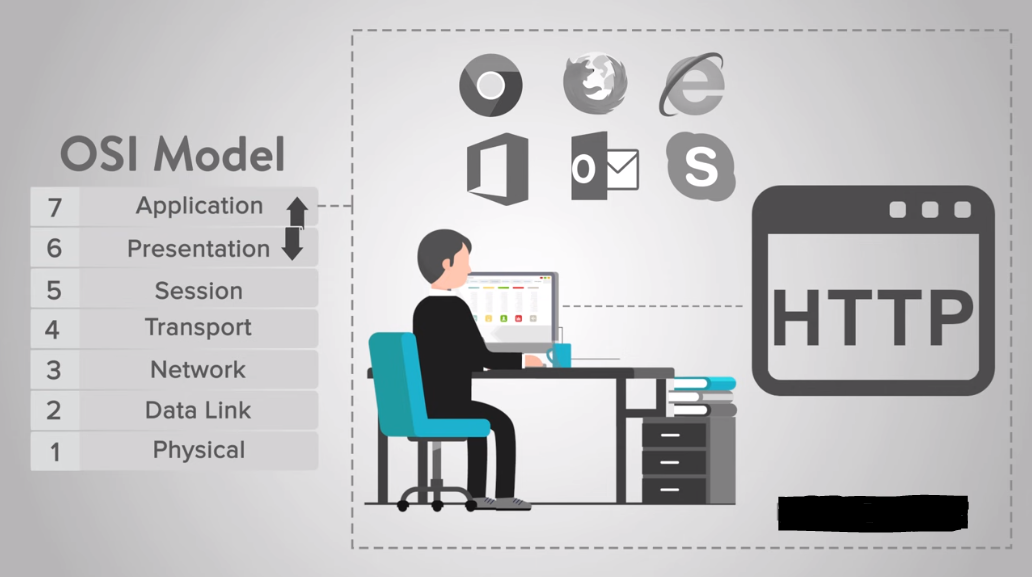
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.
Please Login to comment...
Similar reads.

Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.
OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
Please Whitelist This Site? I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :) If you like The TCP/IP Guide, please consider the download version . It's priced very economically and you can read all of it in a convenient format without ads. If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK. Thanks for your understanding! Sincerely, Charles Kozierok Author and Publisher, The TCP/IP Guide
The presentation layer is the sixth layer of the OSI Reference Model protocol stack, and second from the top. It is different from the other layers in two key respects. First, it has a much more limited and specific function than the other layers; it's actually somewhat easy to describe, hurray! Second, it is used much less often than the other layers; in many types of connections it is not required.
The name of this layer suggests its main function as well: it deals with the presentation of data. More specifically, the presentation layer is charged with taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. It also takes care of any special processing that must be done to data from the time an application tries to send it until the time it is sent over the network.
Here are some of the specific types of data handling issues that the presentation layer handles:
The reason that the presentation layer is not always used in network communications is that the jobs mentioned above are simply not always needed. Compression and encryption are usually considered “optional”, and translation features are also only needed in certain circumstances. Another reason why the presentation layer is sometimes not mentioned is that its functions may be performed as part of the application layer.
The fact that the translation job done by the presentation layer isn't always needed means that it is common for it to be “skipped” by actual protocol stack implementations. This means that protocols at layer seven may talk directly with those at layer five. Once again, this is part of the reason why all of the functions of layers five through seven may be included together in the same software package, as described in the overview of layers and layer groupings .
PrepBytes Blog
ONE-STOP RESOURCE FOR EVERYTHING RELATED TO CODING
Sign in to your account
Forgot your password?
Login via OTP
We will send you an one time password on your mobile number
An OTP has been sent to your mobile number please verify it below
Register with PrepBytes
Presentation layer in osi model.
Last Updated on March 7, 2024 by Abhishek Sharma

The OSI (Open Systems Interconnection) model is a conceptual framework used to understand the functions of a telecommunication or computing system. It consists of seven layers, each responsible for specific tasks. The sixth layer, known as the Presentation Layer, plays a crucial role in ensuring that data exchanged between systems is readable and usable. Let’s explore the functions and importance of the Presentation Layer in the OSI model.
What is Presentation Layer in OSI Model?
The Presentation Layer, the sixth layer of the OSI (Open Systems Interconnection) model, is responsible for ensuring that data exchanged between systems is in a format that can be interpreted and used by the receiving system. It performs various functions, including data translation, encryption, compression, and formatting, to facilitate efficient and secure communication between networked devices.
Functions of the Presentation Layer
Below are some of the functions of the Presentation Layer in OSI Model:
- Data Translation: The Presentation Layer translates data from the format used by the application layer into a format that can be transmitted over the network. This includes encoding, compression, and encryption.
- Data Formatting: It ensures that data is formatted according to the specifications of the application layer. This includes converting between different character sets, such as ASCII and Unicode.
- Data Compression: The Presentation Layer compresses data to reduce the amount of bandwidth required for transmission, improving network efficiency.
- Data Encryption: It encrypts data to ensure that it remains secure during transmission, protecting it from unauthorized access.
- Data Syntax: The Presentation Layer defines the syntax for data representation, ensuring that both the sender and receiver understand the structure of the data being exchanged.
Importance of the Presentation Layer
Importance of Presentation Layer are:
- Data Integrity: By ensuring that data is formatted correctly and encrypted, the Presentation Layer helps maintain the integrity of data during transmission.
- Interoperability: The Presentation Layer enables different systems to communicate with each other by ensuring that data is translated into a common format that both systems understand.
- Efficiency: Data compression reduces the amount of data that needs to be transmitted, improving network efficiency and reducing bandwidth requirements.
- Security: Encryption provided by the Presentation Layer ensures that data remains secure and protected from unauthorized access.
Conclusion The Presentation Layer is a crucial component of the OSI model, responsible for ensuring that data exchanged between systems is in a format that can be understood and used. By performing functions such as data translation, formatting, compression, and encryption, the Presentation Layer plays a vital role in maintaining data integrity, facilitating interoperability, and ensuring the security of data during transmission.
FAQs related to Presentation Layer in OSI Model
Here are some of the FAQs related to Presentation Layer in OSI Model:
Q1: What is the role of the Presentation Layer in the OSI model? The Presentation Layer ensures that data exchanged between systems is in a usable format, performing functions such as data translation, encryption, compression, and formatting.
Q2: How does the Presentation Layer ensure data security? The Presentation Layer encrypts data before transmission, making it unreadable to unauthorized parties, thus ensuring data security.
Q3: Why is data compression important in the Presentation Layer? Data compression reduces the size of data packets, leading to faster transmission speeds and optimized bandwidth usage, which is crucial in high-traffic networks.
Q4: How does the Presentation Layer facilitate interoperability between systems? By translating data into a common format that both sender and receiver understand, the Presentation Layer enables different systems to communicate with each other seamlessly.
Q5: Can the Presentation Layer be bypassed in data transmission? While it is possible to bypass the Presentation Layer in some cases, doing so can lead to compatibility issues between systems and is not recommended.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Linked List
- Segment Tree
- Backtracking
- Dynamic Programming
- Greedy Algorithm
- Operating System
- Company Placement
- Interview Tips
- General Interview Questions
- Data Structure
- Other Topics
- Computational Geometry
- Game Theory
Related Post
Quantum cryptography, introduction to sniffers, multiplexing and demultiplexing in transport layer, transport layer responsibilities, tacacs+ and radius.
Presentation Layer
Last Edited
What is the Presentation Layer?
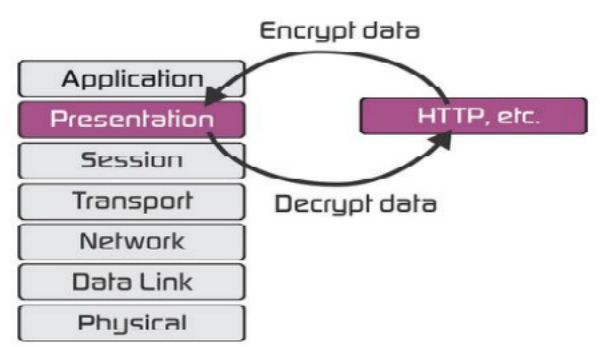
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model . The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. The network redirector also functions at this layer.
Presentation Layer functions
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. Layer 6 is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: Encryption at the transmitter and decryption at the receiver
- Compression: Data compression to reduce the bandwidth of the data to be transmitted. The primary role of data compression is to reduce the number of bits to be transmitted. Multimedia files, such as audio and video, are bigger than text files and compression is more important.
Role of Presentation Layer in the OSI Model
This layer is not always used in network communications because its functions are not always necessary. Translation is only needed if different types of machines need to talk with each other. Encryption is optional in communication. If the information is public there is no need to encrypt and decrypt info. Compression is also optional. If files are small there is no need for compression.
Explaining Layer 6 in video
Most real-world protocol suites, such as TCP/IP , do not use separate presentation layer protocols. This layer is mostly an abstraction in real-world networking.
An example of a program that loosely adheres to layer 6 of OSI is the tool that manages the Hypertext Transfer Protocol (HTTP) — although it’s technically considered an application-layer protocol per the TCP/IP model.
However, HTTP includes presentation layer services within it. HTTP works when the requesting device forwards user requests passed to the web browser onto a web server elsewhere in the network.
It receives a return message from the web server that includes a multipurpose internet mail extensions (MIME) header. The MIME header indicates the type of file – text, video, or audio – that has been received so that an appropriate player utility can be used to present the file to the user.
In short, the presentation layer
Makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there, in a closed network.
- ensures proper formatting and delivery to and from the application layer;
- performs data encryption; and
- manages serialization of data objects.
The OSI Model’s 7 Layers, Explained
The seven layers in the Open Systems Interconnection (OSI) model each serve a specific function and work together to create an efficient network communication system.
The Open Systems Interconnection (OSI) model is a framework in network communication that simplifies complex network interactions into a structured format.
What Is the OSI Model?
The Open Systems Interconnection model is a framework in network communication designed to simplify complex network interactions into a structured format. This architecture has seven layers, each of which serves a specific function. All seven layers work together to create a robust and efficient network communication system.
Each of its seven layers has a distinct role, ensuring efficient data transfer from one device to another . The OSI model is essential for understanding how data is transmitted in a network and is also a practical guide for network protocol design and problem solving.
learn more about cybersecurity An Introduction to Microsegmentation in Network Security
The OSI model, developed by the International Organization for Standardization , outlines the essential functions of networking and telecommunications systems for practical application. It plays a crucial role in telecommunications, where vendors use it to define the features and capabilities of their products and services.
This approach allows for a detailed explanation of different aspects of network communication, including transport protocols, addressing schemes and data packaging methods. As a result, the OSI model resolves the complexities of network communication and fosters a more integrated and coherent digital world .
The 7 Layers of the OSI Model
Each layer of the OSI model serves a specific function, yet they work in harmony to create a robust and efficient network communication system. Understanding these layers provides valuable insights into the complexities of network design and operation, showcasing the intricate nature of modern digital communication.
Layer 7: Application Layer
Functionality: The Application Layer is the closest to the end user. It facilitates user interaction with networked systems, providing interfaces and protocols for web browsers, email clients and other applications.
Key protocols: Protocols like HTTP, FTP and SMTP operate at this layer, enabling services such as web browsing, file transfers and email communications.
Layer 6: Presentation Layer
Role: The Presentation Layer acts as a translator, converting data formats from the application layer into a network-compatible format and vice versa. It ensures that data sent from one system is readable by another.
Data formatting: This layer is responsible for data encryption and compression, playing a significant role in maintaining data privacy and efficient transmission.
Layer 5: Session Layer
Managing sessions: It establishes, manages and terminates sessions between applications. This layer ensures that sessions are maintained for the duration of the communication.
Coordination: The Session Layer coordinates communication between systems, managing dialogues and synchronizing data exchange.
Layer 4: Transport Layer
Data segmentation and control: The Transport Layer is crucial for segmenting data into smaller packets. It ensures end-to-end data integrity and delivery, managing flow control, error correction and sequencing.
Protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are key protocols in this layer, differing in their approach to data transmission.
Layer 3: Network Layer
Routing and addressing: This layer is responsible for logical addressing and routing data packets across different networks. It determines the best path for data to travel from source to destination.
Internet protocol: The Internet Protocol (IP), fundamental for internet data exchange, operates at this layer.
Layer 2: Data Link Layer
Framing and MAC addressing: The Data Link Layer frames data into packets. It handles physical addressing through MAC addresses, ensuring that data is directed to the correct hardware.
Error detection: This layer is also involved in error detection and handling, improving overall data transmission reliability.
Layer 1: Physical Layer
Physical transmission: The Physical Layer deals with the physical aspects of data transmission, including cable types, electrical signals and data rates.
Hardware components: It involves hardware components like cables, switches and network interface cards, forming the foundation of network communication.
How Data Flows in the OSI Model
Understanding this data flow process is crucial for professionals, as it aids in diagnosing and troubleshooting network issues, designing efficient network solutions and ensuring robust data security and management.
Encapsulation Process
When data is sent, it begins at the Application Layer and moves down through the layers. At each stage, it is encapsulated with the necessary headers, trailers, and other control information relevant to that layer. For instance, at the Transport Layer, data is segmented and encapsulated with port numbers, while at the Network Layer, IP addresses are added.
Each layer plays a role in preparing the data for transmission. The Presentation Layer may encrypt the data for security, while the Data Link Layer ensures it is formatted into frames suitable for physical transmission.
Data Transmission Across the Network
The Physical Layer transmits the raw bits over a physical medium, such as a cable or wireless network. This transmission is the actual movement of data across the network. In cases where data must move across different networks, the Network Layer’s routing functionalities become crucial. It ensures that data packets find the most efficient path to their destination.
Decapsulation Process
Upon reaching the destination, the data moves up the OSI model, with each layer removing its respective encapsulation. The Data Link Layer, for instance, removes framing, and the Transport Layer checks for transmission errors and reassembles the data segments. Once the data reaches the Application Layer, it is in its original format and ready to be used by the receiving application, whether it’s an email client, a web browser or any other networked software.
Seamless Data Flow
The OSI model ensures that each layer only communicates with its immediate upper and lower layers, creating a seamless flow. This layered approach means changes in one layer’s protocols or functionalities can occur without disrupting the entire network.
OSI Model Advantages
The OSI model is a cornerstone in network architecture for several reasons:
Simplification of network design
The OSI model’s layered approach breaks down complex network processes, making design and operation more manageable. Each layer focuses on a specific aspect of communication, allowing for independent development and easier troubleshooting.
Standardization and interoperability
It establishes universal standards for network communication, enabling different technologies to interact seamlessly. This interoperability is crucial for the efficient functioning of diverse network devices and applications.
Flexibility and Scalability
Adaptable to technological advancements, the OSI model allows individual layers to evolve without overhauling the entire system. This scalability makes it suitable for various network sizes and types.
Enhanced Security
Security measures are integrated at multiple layers, providing a robust defense against threats. Each layer can address specific security concerns, leading to comprehensive network protection.
Real-World Applications of the OSI Model
The OSI model’s influence extends well beyond theoretical concepts, playing a crucial role in various practical aspects of networking:
Network Design and Protocol Development
Network professionals use the OSI model as a blueprint for structuring and developing robust networks. It guides the creation of new protocols, ensuring seamless integration and functionality across different network layers.
Efficient Troubleshooting and Management
In troubleshooting, the OSI model provides a systematic approach for identifying issues, from physical connectivity to application-level errors. It also aids in network maintenance and performance optimization, addressing each layer to enhance overall efficiency.
Cybersecurity Strategy
The model is foundational in crafting layered security strategies . By implementing security measures at different layers, it offers comprehensive protection against various cyber threats. Understanding the OSI layers is key in detecting and mitigating attacks targeting specific network segments.
Educational and Training Tool
It serves as an essential framework in networking education, helping students and professionals alike understand complex network operations. The OSI model is a cornerstone in training programs , emphasizing the intricacies of network architecture and security.
safety first When and How to Run a Phishing Simulation

OSI Model vs. TCP/IP Model
While the OSI model offers a detailed conceptual framework, the TCP/IP model is recognized for its practical application in today’s internet-driven world.
Structural Differences
OSI model : Introduced as a comprehensive, protocol-independent framework, the OSI model details seven distinct layers, offering a more granular approach to network communication.
TCP/IP model : Developed earlier by the U.S. Department of Defense, the TCP/IP model consists of four layers (Application, Transport, Internet and Network Access), combining certain OSI layers.
Theoretical vs. Practical Approach
OSI model : Developed as a theoretical and universal networking model, it’s used more for educational purposes to explain how networks operate.
TCP/IP model : This model is designed around specific standard protocols, focusing on solving practical communication issues. It leaves sequencing and acknowledgment functions to the transport layer, differing from the OSI approach.
Adoption and Use
OSI model: While not widely implemented in its entirety, the OSI model’s clear layer separation is influential in protocol design and network education; simpler applications in the OSI framework may not utilize all seven layers, with only the first three layers (Physical, Data Link, and Network) being mandatory for basic data communication.
TCP/IP model : The dominant model used in most network architectures today, especially in internet-related communications. In TCP/IP, most applications engage all layers for communication.
Frequently Asked Questions
Why is the osi model important.
The OSI model is crucial for standardizing network communication and ensuring interoperability between various devices and systems. It simplifies network design and troubleshooting and serves as a fundamental educational tool in networking.
What are the 7 layers of the OSI model?
Layer 1: Physical Layer — Transmits raw data.
Layer 2: Data Link Layer — Manages direct links and framing.
Layer 3: Network Layer — Handles addressing and routing.
Layer 4: Transport Layer — Ensures reliable data transfer.
Layer 5: Session Layer — Manages connections.
Layer 6: Presentation Layer — Translates data formats.
Layer 7: Application Layer — Interfaces with applications.
Recent Expert Contributors Articles


Presentation Layer Of OSI Model For Beginners
Presentation Layer:
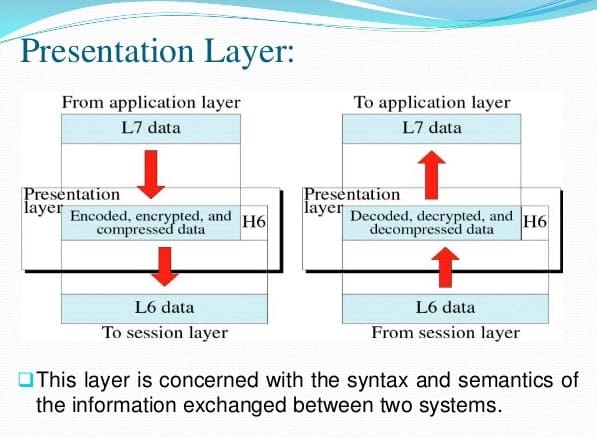
Presentation Layer is the sixth layer in the OSI model and here are some of the functionalities of the presentation layer:
Translation
Before being transmitted, the data remains in the form of characters and numbers. This data has to be changed to bitstreams before transmission. The presentation layer is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats that a network requires and the format a computer needs.
It carries out the process of encryption at the transmitter end and the process of decryption at the receiver end.
Encryption and decryption are ways to protect the confidentiality of the data stored on computer systems or wired over the internet or other computer networks.
Also Read: Network Layer Of OSI Mode: Functionalities and Protocols
In terms of security, modern-day encryption methods play a vital role in the security assurance of IT systems and communications as they can provide not only confidentiality but also, authentication and integrity.
Data compression
Data compression is also known by different names like source coding or bit-rate reduction. As evident from these names, data compression involves encoding information using fewer bits than the original representation. So in this way, the data compression can be either lossy or lossless.
Even though lossless compression reduces bits by identifying and eliminating statistical redundancy, no data information is lost in the lossless compression.
On the other hand, the lossy compression reduces bits by identifying unnecessary information and removing it.
Data compression is useful in computer networks because it helps in the following ways:
- Reducing resource usages such as data storage space or transmission capacity. B
- Reducing the need for an expensive hardware for the data representation. For example, if a video is highly compressed before transmission, an expensive hardware might be required to decompress the video data before playing it.
Thus, data compression is also very helpful in real-time applications over the internet like real-time video or audio streaming.
Data conversion
There are different types of operating systems such as Windows, Linux, Mac OS etc. are being used all around the world. Data conversion is, thus, responsible for the conversion of computer data from one format to another.
Different computers encode data in different ways on the basis of certain standards. On top of that, each computer program handles data in a different manner. Data conversion comes in handy in those situations when the representation of data is needed on different platforms.
The presentation layer can be composed of two sublayers: common application service element (CASE) and specific application service element (SASE).
Also Read: LLC Layer (Logical Link Control): Data Link Layer Of OSI Model
The common application service element sublayer provides services for the application layer and request services from the session layer. It provides support for common application services whereas the specific application service element sublayer provides application specific services (protocols) like remote database access, file transfer, virtual terminal.
If you have any comments or thoughts related to it, feel free to ask and correct us. Also, don’t miss our complete coverage on the Computer networks .
A passionate adventure traveller over Trekkerpedia.com and Author of the book 'The Girl from the Woods'.
Similar Posts

Here’s Everything You Need To Know About Electric Car Batteries
lithium-ion electric car battery

Difference Between HDMI, VGA, DisplayPort, DVI, Thunderbolt, And MHL
Short Bytes: When it comes to connecting your laptop, Blu-ray player, DVR, and other things to…

Want A New Job In 2023? Start Your Search Now
Plan & fix it before 2023!

Don’t Be Fooled By Redmi Note 7 Pro’s 48MP Camera
Xiaomi has once again challenged its rivals in the budget segment by launching Redmi Note 7…

What Is Peacock TV? Streaming Plans, Pricing & Everything Else
Is Peacock TV worth your money?
What Is Disk Defragmentation? Do I Really Need To Defrag My PC?
Short Bytes: These days, fragmentation doesn’t cause the computers to slow down much as it used…

Unveiling the Interpreter: Fortifying the Presentation Layer’s Role in Cybersecurity
- March 28, 2024
Cherise Esparza
Welcome back to Tea with C. As we navigate deeper into the OSI model, today’s spotlight shines on Layer 6: the Presentation Layer. The Presentation Layer, often likened to an adept interpreter in the digital realm, plays a pivotal role in the seamless transmission and reception of data across the network.
At its essence, the Presentation Layer is tasked with data translation, encryption, and compression. It ensures that the information sent from the application layer is suitably formatted for transmission across the network and can be accurately interpreted by the receiving system. This layer is a universal translator for network communications, bridging different data formats into a universally understood language.
Encryption protocols at this layer are vital for securing data at rest and in transit. They are the bedrock of data integrity and confidentiality, shielding sensitive information from prying eyes and potential cyber threats. This is where the magic of transforming data into a secure format occurs, making it an essential battleground for cybersecurity efforts.
However, the Presentation Layer is not without its vulnerabilities. Some of the most insidious security threats stem from weaknesses in the coding practices used to develop applications interacting at this layer. Buffer overflows, SQL injections, and cross-site scripting are prime examples of exploits that can lead to significant security breaches. These vulnerabilities underscore the critical importance of secure coding practices and robust input validation procedures to fend off attackers.
The roles vital to securing the Presentation Layer span a broad spectrum of cybersecurity expertise. Network security analysts play a key role in scrutinizing the data exchange protocols and ensuring that encryption measures are robust and correctly implemented. Developers adhere to a secure development lifecycle, ensuring that code is thoroughly vetted and sanitized before deployment. Lastly, the overarching vigilance of security analysts dedicated to network monitoring and logging forms the backbone of a comprehensive security strategy at this layer.
Ensuring the security of the Presentation Layer is a multifaceted challenge that requires a concerted effort from all parties involved in the development and deployment of network applications. As we gear up for our following discussion on the final layer of the OSI model , the Application Layer, remember that each layer presents unique challenges and opportunities for enhancing our cybersecurity posture. Join us next week as we conclude our exploration of the OSI model.
Share this post
Recent articles.

Fortifying Cybersecurity: Unpacking the Enhancements in CSF 2.0’s ‘Protect’ Function
The need for robust cybersecurity measures has never been more apparent in the rapidly advancing digital landscape. With cyber threats becoming increasingly sophisticated, the National

SecurityGate Unveils New Channel Program
HOUSTON, April 16, 2024 /PRNewswire/– SecurityGate, the provider of the leading SaaS platform for OT cyber improvement, is excited to announce the launch of its new

Deep Dive into the “Identify” Function: Transitioning from the 2018 Framework to CSF 2.0
Understanding an organization’s digital assets and systems in the ever-changing cybersecurity landscape is crucial to ensure effective security. The “Identify” function of the National Institute

Announcing General Availability of ISA/IEC 62443-2-1 Workflow in the SecurityGate Platform
We are thrilled to share that we have added ISA/IEC 62443-2-1 to the SecurityGate Platform. This update will assist users in creating a robust IACS

The Evolution of the Govern Function in the Cybersecurity Framework: A Closer Look at CSF 2.0
In the realm of cybersecurity, staying ahead of threats necessitates not just reactive measures but a proactive and structured approach to safeguarding digital assets. The

Fortifying the Frontlines: Navigating the Complexities of Application Layer Security
Welcome to another engaging session at Tea with C, where we unravel the mysteries of cybersecurity one layer at a time. Today, our focus ascends
5120 Woodway Dr. Suite 9003 Houston, TX 77056
SecurityGate c/o Talent Garden Calabiana Via Arcivescovo Calabiana, 6, 20139 Milano, Italy
- Privacy Policy
- Terms of Service
- Support Terms
Platform Tour
Channel program, case studies, the business of cyber series.
Understanding the Role of the Presentation Layer in Data Format Translation and Security
1. introduction.
According to a recent study conducted by the Institute of Electrical and Electronics Engineers (IEEE), the presentation layer is responsible for ensuring that the data is in a format that is acceptable to the application layer. This includes data compression and decompression, encryption and decryption, and character set conversion. In today’s data-driven world, the ability to effectively manage and secure data is becoming increasingly important, and understanding the role of the presentation layer in this process is crucial.
This article will explore the techniques and technologies used in the presentation layer to perform data format translation, compression and decompression, and encryption and decryption. This will include a discussion of the benefits and limitations of these techniques, as well as real-life examples and case studies of their implementation. By the end of this article, readers will have a solid understanding of the role and functions of the presentation layer in the OSI model and how it contributes to secure and efficient data transmission.
2. The role of the presentation layer
The presentation layer, also known as the syntax layer, is the sixth layer in the OSI model. It ensures that the data is in a format acceptable to the application layer. This includes data format translation, compression and decompression, encryption and decryption, and character set conversion. It acts as an interface between the application layer and the rest of the layers in the OSI model.
Data Format Translation:
The presentation layer is responsible for translating data between different formats so the application layer can understand it. For example, it may convert a file from one format, such as TIFF, to another format, such as JPEG. This ensures that the data is in a form that is compatible with the application layer and can be processed accordingly.
Compression and Decompression:
Another essential function of the presentation layer is data compression and decompression. The layer compresses the data before sending it to the next layer, the network layer. This reduces the amount of data that needs to be transmitted, reducing the time required for the data to be shared. Once the data reaches the destination, the decompression process takes place, and the data is restored to its original form. There are various compression and decompression techniques like LZ77, LZ78, and Huffman coding that are used to compress and decompress data.
3. Data compression and decompression techniques
Data compression and decompression are essential functions of the presentation layer in the OSI model. Compression refers to reducing the amount of data that needs to be transmitted. At the same time, decompression restores the data to its original form once it reaches the destination. The use of compression techniques can significantly reduce the amount of time required for data to be transmitted, as well as reduce the bandwidth needed for transmission.
The presentation layer’s most commonly used compression techniques include LZ77, LZ78, and Huffman coding.
LZ77 is a lossless data compression algorithm that Abraham Lempel and Jacob Ziv first introduced in 1977. It replaces repeated instances of a data string concerning the original series. LZ77 is a dictionary-based algorithm that uses a sliding window to identify and replace repeated data instances. This technique is effective at compressing data that contains many repeated patterns, but it can be less effective on highly random data.
LZ78 is another lossless data compression algorithm that Lempel and Ziv introduced in 1978. It is similar to LZ77 but uses a different data compression approach. Instead of using a sliding window, LZ78 uses a dictionary of previously encountered data strings. This approach allows LZ78 to achieve higher compression ratios than LZ77 but also requires more memory and processing power.
Huffman coding:
Huffman coding is a lossless data compression algorithm introduced by David Huffman in 1952. Huffman coding is a variable-length coding algorithm that assigns shorter codes to more frequently occurring symbols in the data. This technique is especially effective for compressing data that contains many repeating characters, such as text or DNA sequences.
Each technique has its advantages and disadvantages; LZ77 and LZ78 are simpler than Huffman coding and can be implemented quickly. With a limited amount of memory, on the other hand, Huffman coding is more efficient in terms of compression ratio, but it is more complex and memory-intensive.
In real-life examples, all three algorithms have been used in various applications. For instance, LZ77 has been used to compress data in the telecommunications industry, and LZ78 has been used in data storage devices like hard drives and flash drives. In contrast, Huffman coding compresses text, images, audio and video files.
4. Encryption and decryption in the presentation layer
Encryption and decryption are essential security measures that are used to protect sensitive information as it is transmitted over a network. In the OSI model, encryption and decryption occur at the presentation layer. The presentation layer is responsible for ensuring that the data is in a format acceptable to the application layer, and it also ensures that the information is protected during transmission.
Encryption refers to converting plain text into an unreadable form, known as ciphertext. The ciphertext can only be read and understood by someone with the correct decryption key. Decryption, on the other hand, is the process of converting ciphertext back into plain text using the right decryption key.
The importance of encryption and decryption in the presentation layer is clear, especially with the rise of cyber threats. It ensures that only authorised parties can access and understand the sensitive information being transmitted. Without encryption and decryption, sensitive data would be vulnerable to eavesdropping and tampering.
There are two main types of encryption and decryption methods that are commonly used in the presentation layer: symmetric key encryption and asymmetric key encryption.
Symmetric key encryption:
Symmetric key encryption is a method of encryption where the same key is used for both encryption and decryption. This method is fast and efficient, but it also has some drawbacks. The main disadvantage is that the key must be securely exchanged between the sender and the receiver before any encryption can occur.
Asymmetric key encryption:
Asymmetric key encryption, also known as public key encryption, is a method of encryption where a pair of keys is used. One key is used for encryption, and the other is used for decryption. This method is more secure than symmetric key encryption because the key used for encryption can be made public, while the key used for decryption is kept private.
In real life, symmetric key encryption is used for bulk encryption, for example, in the transportation of email, instant messaging and other types of data where the speed of encryption is more important than key exchange. On the other hand, Asymmetric key encryption is often used for digital signatures, online transactions and handshaking in secure connections.
5. Common Attacks on the Presentation Layer
The Presentation Layer in the OSI model ensures data security during transmission. However, like any other layer in the OSI model, it is also vulnerable to various attacks, vulnerabilities, and threats. These can have severe consequences, such as unauthorised access or manipulation of sensitive information.
One standard attack on the presentation layer is a “format string attack”. This occurs when an attacker can insert random formatting characters into a string, which can then be used to disrupt the normal execution of a program. This can lead to various consequences, including buffer overflows, which can be used to execute arbitrary code or crash the system.
Another attack that targets the presentation layer is “malicious code injection”. This occurs when an attacker can insert malicious code into a seemingly benign file or message. This can be done by exploiting vulnerabilities in data format translation or compression/decompression mechanisms. Once the malicious code is executed, it can cause various types of damage, such as data loss, unauthorised access to sensitive information, or even complete system compromise.
In addition to these specific attacks, the presentation layer is vulnerable to more general threats, such as “man-in-the-middle” or “replay” attacks. These are attacks in which an attacker intercepts and alters communications between two parties to gain unauthorised access to sensitive information. Such attacks can occur on any OSI model layer, but they are particularly dangerous when they target the presentation layer, as the attacker can manipulate or intercept data in transit.
6. How to Secure the Presentation Layer
Securing the Presentation Layer in the OSI model is crucial for protecting sensitive information during transmission. There are various security best practices that organisations can implement to protect against attacks, vulnerabilities, and threats on this layer.
One critical best practice is to keep software and systems up-to-date with the latest security patches and updates. This ensures that known vulnerabilities are fixed, making it harder for attackers to exploit them. It’s also important to regularly monitor systems and networks for signs of suspicious activity, such as unusual traffic patterns or login attempts.
Another best practice is to use secure protocols for data transmission and storage. Examples of secure protocols used at the Presentation Layer are Transport Layer Security (TLS) and Secure Sockets Layer (SSL), which encrypt communications between parties. Additionally, the use of robust encryption and decryption mechanisms, such as symmetric and asymmetric key encryption, can help protect against man-in-the-middle and replay attacks.
Enforcing strict access controls and implementing a solid data classification system can also secure the presentation layer. This includes access controls to limit who can view, modify or delete sensitive data and a data classification system which can help determine how data is handled, processed and protected.
Implementing a robust incident response plan that includes detailed procedures for identifying, containing and reporting security incidents can also be a valuable asset in case of a security breach. It’s also important to regularly train employees on security best practices and to make them aware of the importance of security in the presentation layer.
In addition, performing regular penetration testing, Vulnerability Assessments, and security audits can also help to identify and address security vulnerabilities. This can include testing the effectiveness of encryption and decryption mechanisms, evaluating the robustness of access controls, and identifying potential vulnerabilities in data format translation and compression/decompression mechanisms.
7. Conclusion
In conclusion, the presentation layer in the OSI model is a critical component in the data transmission process. Its functions include data format translation, data compression and decompression, and encryption and decryption. These functions are vital to ensure that the data is in a format compatible with the application layer and to protect the data during transmission.
We have discussed how the presentation layer plays a vital role in the OSI model. The techniques and technologies used in the presentation layer to perform data format translation, compression and decompression, encryption and decryption. The article also includes the advantages and disadvantages of each technique, real-life examples and case studies, if applicable, that illustrate the concepts and makes them more relatable.
The topic of the presentation layer in the OSI model is essential for anyone working in the network security and communications field, as it provides an understanding of how data is protected and formatted during transmission. We hope this article has provided a comprehensive understanding of the role and functions of the presentation layer in the OSI model.
However, it’s important to note that the Presentation Layer, like any other layer in the OSI model, is also vulnerable to various attacks, vulnerabilities, and threats. Therefore, it is crucial to implement security best practices to protect against these threats, such as keeping software and systems up-to-date with the latest security patches and updates, using secure protocols, and robust encryption and decryption mechanisms. Strict access controls, incident response plans, and regular security assessments can also help secure the Presentation Layer.
8. FAQs on the Presentation Layer
- How does the presentation layer ensure data format compatibility?
The presentation layer ensures data format compatibility by providing a set of protocols and standards for data representation and encoding. These protocols, such as ASCII or Unicode, define a standard format for data so that it can be easily understood and processed by different systems. This helps to ensure that data can be exchanged between other systems without loss of meaning or integrity.
- How does the presentation layer protect data during transmission?
The presentation layer protects data during transmission by using various encryption techniques to ensure that the data is secure as it is transmitted over a network. Encryption is the process of converting plaintext data into a coded format (ciphertext) unreadable by unauthorised parties. Standard encryption methods used at the presentation layer include SSL (Secure Sockets Layer) and TLS (Transport Layer Security).
- What are some standard encryption algorithms used in the presentation layer?
Some standard encryption algorithms used in the presentation layer include:
- RSA (Rivest-Shamir-Adleman)
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (Triple Data Encryption Standard)
- What is the difference between symmetric and asymmetric encryption in the presentation layer?
Symmetric key encryption and asymmetric key encryption are both encryption methods that are used to protect data during transmission, but they use different techniques to secure the data.
Symmetric key encryption uses a single shared key for encryption and decryption, meaning that the sender and receiver both have to use the same key to encrypt and decrypt the data.
Asymmetric key encryption, also called public-key encryption, uses a pair of keys, one for encryption (the public key) and one for decryption (the private key). So the sender uses the recipient’s public key to encrypt the data, and the recipient uses their private key to decrypt the data.
- How does the presentation layer handle data format translation for different data types?
The presentation layer handles data format translation for different data types using a set of protocols and standards for data representation and encoding. These protocols, such as ASCII or Unicode, define a standard format for data so that it can be easily understood and processed by different systems. The presentation layer can also use data conversion algorithms to convert data between other formats, such as a Word document to a PDF.
- How does the presentation layer interact with other layers in the OSI model?
The presentation layer, the sixth layer in the OSI model, acts as an intermediary between the application layer (layer 7) and the session layer (layer 5). It is responsible for translating data between different formats and encoding schemes, and it is also responsible for compressing and decompressing data. The presentation layer communicates with the application layer to convert the data it receives into a format the application can understand. It also communicates with the session layer to establish, manage, and terminate sessions between networked devices.
- How do changes in data formats affect the presentation layer?
Changes in data formats can have a significant impact on the presentation layer, as the presentation layer is responsible for converting data between different formats. The presentation layer must be updated when data formats change to support the new design. If this is done, the presentation layer can convert the data, which may be unreadable or lost. Additionally, there are changes in the protocol or standard used in the presentation layer. In that case, it will affect the compatibility with other systems, so the sending and receiving ends have to use the same protocol. Otherwise, they would not be able to understand each other.
- How does the presentation layer handle data compression and decompression in real-time communications?
The presentation layer is responsible for compressing and decompressing data in real-time communications. Compression reduces data size to improve transmission efficiency, while decompression restores the data to its original format. The presentation layer uses various compression algorithms to compress data and the same algorithms to decompress the data when it is received.
In real-time communications, the presentation layer might use lossless compression algorithms to compress the data in order not to lose any information but at the same time still be able to compress the data to a smaller size.
- How can data integrity be maintained in the presentation layer?
Data integrity in the presentation layer can be maintained using encryption, secure hash algorithms, and error-detection codes.
Encryption is the process of converting plaintext data into a coded format (ciphertext) that is unreadable by unauthorised parties. This helps to protect data from unauthorised access and modification during transmission.
Secure hash algorithms are used to create a unique digital signature for each piece of data, which can be used to verify the integrity of the data upon receipt. This helps to detect any changes or modifications that may have occurred during transmission.
Error-detection codes are used to detect errors in the data during transmission and can help to correct these errors.
Additionally, the presentation layer can also use a digital signature or digital certificate to ensure the authenticity of data, which is the process of using a digital signature to ensure that the data is not tampered with during transmission.

Computer Network
- Operating Systems
- Computer Fundamentals
- Interview Q
Physical Layer
Data link layer, network layer, routing algorithm, transport layer, application layer, application protocols, network security.
Interview Questions
- Send your Feedback to [email protected]
Help Others, Please Share

Learn Latest Tutorials
Transact-SQL
Reinforcement Learning
R Programming
React Native
Python Design Patterns
Python Pillow
Python Turtle
Preparation

Verbal Ability

Company Questions
Trending Technologies
Artificial Intelligence
Cloud Computing
Data Science
Machine Learning
B.Tech / MCA
Data Structures
Operating System
Compiler Design
Computer Organization
Discrete Mathematics
Ethical Hacking
Computer Graphics
Software Engineering
Web Technology
Cyber Security
C Programming
Control System
Data Mining
Data Warehouse


Exploring the Layer of the OSI Model Used for Formatting, Compressing, and Encrypting Data
Michelle Rossevelt
July 11, 2023
Data Encryption
In this Article:
Introduction
The OSI (Open Systems Interconnection) model is a conceptual framework that describes the communication functions of a telecommunication or computer system. It is divided into seven layers, each with a specific function in the communication process. In this article, we will explore the layer of the OSI model used for formatting, compressing, and encrypting data. The Presentation Layer is crucial in ensuring data is transmitted securely and efficiently between devices. Let’s jump in and learn more about this important OSI model layer.
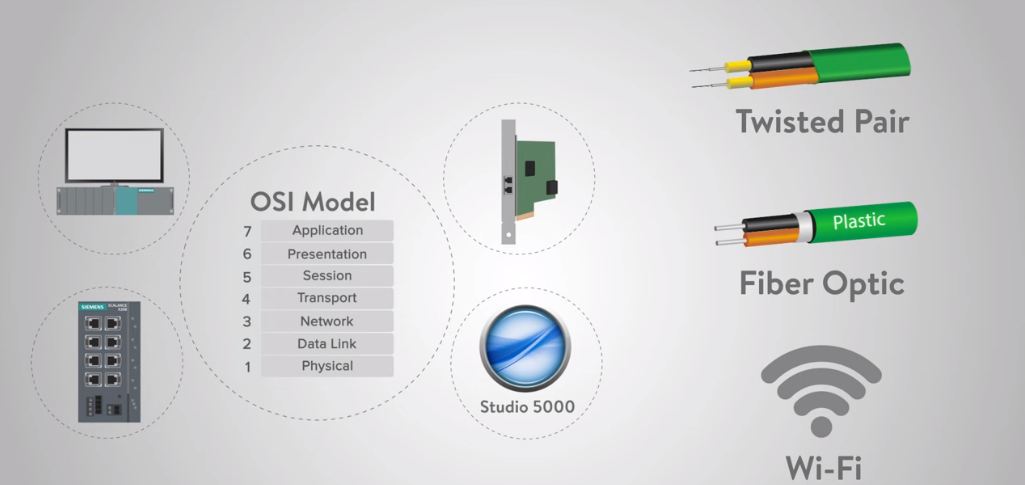
Overview Of OSI Model
The OSI model is a theoretical agenda that standardizes communication between different computer systems. It was established by the International Organization for Standardization (ISO) in 1984 and consists of seven layers. Each layer is accountable for a specific function in the communication process, and they work together to confirm that data is transmitted accurately and securely.
Layers Of OSI Model
The seven layers of the OSI model are:
1. Physical Layer: This layer transmits raw data over a physical medium such as cables or airwaves.
2. Data Link Layer: This layer is responsible for reliable data transmission over a physical link.
3. Network Layer: This layer controls routing data between different networks .
4. Transport Layer: This layer is reliable data transmission between devices.
5. Session Layer: This layer manages and maintains communication sessions between devices.
6. Presentation Layer: This layer formats, compresses, and encrypts data .
7. Application Layer – This layer provides services to end-users, such as email, web browsing, and file sharing.
Which Layer In The OSI Model Is Required For Formatting, Compressing, And Encrypting Data?
The layer in the OSI model responsible for formatting, compressing, and encrypting data is the Presentation Layer .
Presentation Layer
The Presentation Layer, the sixth layer in the OSI model, is responsible for formatting, compressing, and encrypting data . This layer ensures that data is presented in a format that can be known by the receiving device, regardless of the format in which it was sent. It also handles encryption and decryption of data to ensure secure transmission .
Comparison With Other Layers
Session Layer
The Session Layer, the fifth layer in the OSI model, establishes, manages, and terminates sessions between devices. It provides authentication, authorization, and accounting services to ensure secure device communication . The Presentation Layer works closely with the Session Layer to ensure that data is presented in a format both devices can understand during the session.
Application Layer
The Application Layer, the seventh and topmost layer in the OSI model, provides services to the end-user applications. The layer interacts directly with the user and provides file transfers , email, and web browsing services. The Application Layer also provides protocols that enable communication between applications running on different devices. Examples of protocols at this layer include HTTP, FTP, SMTP, and DNS.
Function Of The Presentation Layer
The Presentation layer is the formatting, encrypting, and compressing of data transmitted across the network. It confirms that the data is in a format that can be understood by the receiving device, regardless of the format used by the sending device. It also handles data conversion between different character sets and data formats. In summary, the Presentation layer prepares the data for delivery and ensures that the receiving device can properly interpret it.
Some Protocols Operating At Presentation Layer
Some protocols that operate at the Presentation layer include:
1. JPEG (Joint Photographic Experts Group) – used for compressing and decompressing image files
2. MPEG (Moving Picture Experts Group) – used for compressing and decompressing video files
3. American Standard Code for Information Interchange – ASCII is used for encoding text data
4. TLS (Transport Layer Security) – used for encrypting data during transmission
5. SSL (Secure Sockets Layer) – used for encrypting data during transmission
6. GIF (Graphics Interchange Format) – used for compressing and decompressing image files
7. PNG (Portable Network Graphics) – used for compressing and decompressing image files
These are just a few examples of protocols that operate at the Presentation layer. Many others perform different functions depending on the type of data being transmitted.
Which Layer In The TCP/IP Model Is Used For Formatting, Compressing, And Encrypting Data?
In the TCP/IP model, the Presentation Layer is used for formatting, compressing, and encrypting data . This layer ensures that data is in a format the receiving application can understand. It also handles encryption and decryption of data , as well as compression and decompression of data. However, it is important to note that no protocols use only the Presentation Layer. Instead, protocols like SSL/TLS and MIME use the Presentation and Application Layers to provide secure communication and multimedia support.
The Presentation layer plays a crucial role in the OSI model by ensuring that data is properly formatted, encrypted, and compressed for transmission across different networks and systems. Without this layer, data transmission would be inefficient, unreliable, and vulnerable to security threats . By understanding the functions and protocols of the Presentation layer, network engineers and IT professionals can optimize their networks for better performance and security.
The Presentation layer is an essential component of the OSI model that plays a vital role in ensuring efficient and secure data transmission. Its functions and protocols are critical for optimizing network performance and protecting against security threats. As technology advances , network engineers and IT professionals must stay up-to-date on the latest developments in the Presentation layer and other OSI model layers to ensure their networks’ continued success and security.
Frequently Asked Questions (FAQs)
How does the presentation layer format, compress, and encrypt data.
The Presentation layer is responsible for formatting, compressing, and encrypting data before transmitting it across the network. It formats the data into a standard format that can be understood by the receiving device, regardless of the format used by the sending device. It also compresses the data to reduce the data that needs to be transmitted, improving network performance. Finally, it encrypts the data to ensure it is secure and cannot be intercepted or read by unauthorized parties. Overall, the Presentation layer is crucial in ensuring data is properly prepared for transmission and remains secure during transit.
What Are Some Commonly Used Encryption Algorithms In The Presentation Layer?
There are various encryption algorithms used in the presentation layer, including Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Rivest Cipher (RC4). These algorithms provide different levels of security and are widely employed to protect sensitive data during transmission.
Can The Presentation Layer Perform Data Encryption Without The Need For Encryption At Higher Layers?
Yes, the presentation layer can independently encrypt data without the need for encryption at higher layers. However, for robust security , it is recommended to implement encryption at multiple layers of the OSI model, including the presentation layer, transport layer, and application layer.
The Ultimate Guide to IPsec VPN Encryption Modes
Unlocking the truth: a deep dive into cell phone data security.
Data Security and Encryption Softwares.
Folder Lock
What . Why . How
Testimonials
Blog Sitemap
Legal Notices
Privacy Policy
Password Protect Folder
Ransomeware Protection
Last Updated on January 23, 2024 by admin

IMAGES
VIDEO
COMMENTS
Prerequisite : OSI Model. Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required ...
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
The presentation layer establishes the way in which information is presented, typically for display or printing. Data encryption and character set conversion (such as ASCII to EBCDIC) are usually associated with this layer. Category: OSI model.
Encryption and decryption of data communications are also performed at the presentation layer. Here, encryption methods and keys exchange between the two communicating devices. Only the sender and receiver can properly encode and decode data so it returns to a readable format.
Compression: Compression (and decompression) may be done at the presentation layer to improve the throughput of data. (There are some who believe this is not, strictly speaking, a function of the presentation layer.) Encryption: Some types of encryption (and decryption) are performed at the presentation layer. This ensures the security of the ...
The Presentation Layer is a crucial component of the OSI model, responsible for ensuring that data exchanged between systems is in a format that can be understood and used. By performing functions such as data translation, formatting, compression, and encryption, the Presentation Layer plays a vital role in maintaining data integrity ...
Key functions of the Presentation Layer in the OSI model include: Data Encryption: It securely encrypts data to prevent unauthorized access during transmission. Data Compression: It reduces data ...
Data compression is also a function of Layer 6. If necessary, data may be compressed to improve data throughput over network communication. Some common Layer 6 protocols are ASCII, JPEG, GIF, MPEG, and PNG. Another main function of the presentation layer is the encryption and decryption of data sent across a network. Most encryption ...
The presentation layer is a very important layer because it handles encryption, decryption, and the conversion of complex data into flat-byte strings, a format that is easily transmittable. The ...
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model. The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation ...
The Presentation Layer may encrypt the data for security, while the Data Link Layer ensures it is formatted into frames suitable for physical transmission. Data Transmission Across the Network. The Physical Layer transmits the raw bits over a physical medium, such as a cable or wireless network. This transmission is the actual movement of data ...
The presentation layer is an important layer in the OSI model because it is responsible for some of the important services like data conversion, data compression, encryption, and decryption.
The Presentation Layer, often likened to an adept interpreter in the digital realm, plays a pivotal role in the seamless transmission and reception of data across the network. At its essence, the Presentation Layer is tasked with data translation, encryption, and compression.
The presentation layer provides the ability to translate the data to suit the applications needs. Some of the format types found in this layer are as follows: ASCII, EBCDIC, JPEG, MPEG, TIFF, Binary, and so on. This layer is also able to provide encryption and compression if the application layer asks it to do so.
The presentation layer is concerned with preserving the meaning of information sent across a network. The presentation layer may represent (encode) the data in various ways (e.g., data compression, or encryption), but the receiving peer will convert the encoding back into its original meaning. The presentation layer concerns itself with the ...
Furthermore, understanding the sixth layer benefits cybersecurity professionals, as the presentation layer takes care of data encryption. Some common threats at this level include encoding attacks, encryption attacks, and decryption downgrade attacks. Therefore, professionals use the presentation layer to secure data transmitted over a network.
The simplest way to describe the OSI presentation layer is as follows: it is where machine-readable code gets processed into something the end user can use later in the application layer.
Layer 1 - Physical Layer. Data Link Layer Encryption. The Physical Layer is the lowest layer in the OSI model and is responsible for the transmission and reception of raw data between devices. It defines the physical characteristics of the communication medium, such as the voltage levels, data rates, and cable specifications.
The presentation layer, also known as the syntax layer, is the sixth layer in the OSI model. It ensures that the data is in a format acceptable to the application layer. This includes data format translation, compression and decompression, encryption and decryption, and character set conversion. It acts as an interface between the application ...
It is a 6th layer in the OSI model that translates one data format into another data format. The presentation layer may also be called the translation layer or syntax layer. You have learned about the functions of the presentation layer, such as translation, encryption & decryption, and compression & decompression.
There are various encryption algorithms used in the presentation layer, including Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Rivest Cipher (RC4). These algorithms provide different levels of security and are widely employed to protect sensitive data during transmission.