
- Search the community and support articles
- Microsoft 365 and Office
- Subscription, account, billing
- Search Community member
Ask a new question

Checking licence changes in audit logs
Hi everyone,
This morning I found out that 5 of our users had lost their o365 licenses. I had to manually assign these licenses again. When i want to check the audit logs, to see what happened, I notice that the change of licenses is not logged. Do I need to turn this kind of logging manually on?
Kind regards,
Rick van Oosterhout
Report abuse
Replies (7) .
2 people found this reply helpful
Was this reply helpful? Yes No
Sorry this didn't help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
Thanks for your feedback.
How can I check if those are turned on and if not, how can I turn those on?
- Microsoft Agent |
You could follow the picture to search licenses assigned logs again.
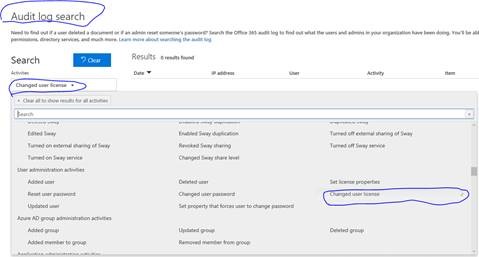
If the action that assigning licenses is still not logged, it can take up to 24 hours for the admin events related audit log entry to be displayed in the search results.
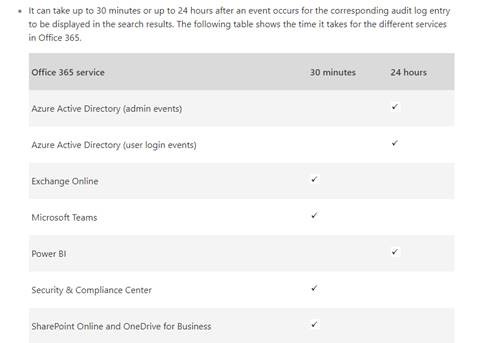
Here is Search the audit log in the Office 365 Security & Compliance Cente r for your reference.
Besides, if the issue occurs again, I would like to collect following information:
1.Are these users Online users or local AD users?
2.What licenses do they have before these license lost?
May I know if the issue has been resolved? If you need further assistance, please share more information I mentioned with us.
The issue has not been resolved yet. When I audit for license changes, I get 0 results.
The users are online users, and we are all using a office365 business license.
Recently, there is Service Incident as the picture shows:
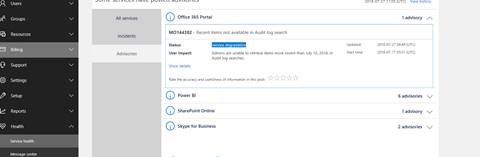
You might be affected by the Service Incident. For further assistance, I would like to collect your tenant information via private message. Please check it.
Thank you for your understanding.
Best Regards,
We haven't hear back from you. Do you need further assistance? If so, please share more information I mentioned in private message.
Question Info
- Norsk Bokmål
- Ελληνικά
- Русский
- עברית
- العربية
- ไทย
- 한국어
- 中文(简体)
- 中文(繁體)
- 日本語
An Admin's Guide to Navigating Audit Logs in Office 365

The Office 365 audit log should be your go-to tool for tracking user and administrative activity in your tenant. Use it to check user log-in patterns, communication, file view, edit, and share actions. Ultimately, it’s one of the best tools available for governing your Microsoft 365 and seeing what’s happening in your environment.
In this article:
- How to set up and enable audit logs in Office 365
- Creating audit log retention policies
- Recommendations for security events to audit
Use cases for Microsoft 365 audit logs
- An alternative to Office 365 audit logs
Set up and enable audit logs in Office 365
Enabling audit logs within your organization requires distinct admin privileges. For example, the Audit Logs role is required to enable audit logs in Exchange Online. These privileges are assigned to global administrators by default. You can read more about the specific permissions levels required here .
Before you turn on audit logs in your M365 tenant, you’ll first need to confirm whether audit logging is currently enabled. To do so, you can run the following command in Exchange Online PowerShell :
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabled
A response of “True” to the above command indicates that audit logging is currently enabled. Conversely, a response of “False” indicates that logging is currently disabled for your M365 environment.
It is worth noting that SharePoint logging needs to be turned on separately for each site collection. This can be accomplished in an automated fashion with PowerShell; however, there are limitations to this approach. You cannot, for example, connect to an exposed endpoint to collect specific logs for custom reports. Additionally, when retrieving logs from SharePoint, logs from all other services will be ignored, and thus won’t be included in the search results.
You will be able to see audit logs in M365 audit log search results for specific services as soon as 30 minutes after setup, but it can take up to 24 hours for all services to begin storing logs.
Checking audit logs in Microsoft 365
Go to the Microsoft 365 Admin Center and select the security tab in the left pane. Click on the audit button to open the audit log page. You can search the audit log based on time, activities, and users.
Enter and select the suspected user's name in the user field, choose a date range, and specify an activity to filter for. In this case, you should enter "deleted file," or "file download" as the activity you want to check for.
Alternatively, you can access aggregated logs from these M365 services via the Microsoft Purview compliance portal or use the Search-UnifiedAuditLog cmdlet in Exchange Online PowerShell to search this centralized collection of logs.
Your search results can be exported to a CSV file for additional processing as needed; however, log data retrieved in this format can be unwieldy as it will contain all manner of metadata that you will more than likely not need, and that will likely mask the data that you do need.
In addition to the above methods of accessing audit logs, you can also retrieve them programmatically via the available REST APIs.
For more insights on pulling log-on reports from Azure Active Directory, read this blog .
Creating audit log retention policies in Office 365
You can only create an audit log retention policy from the compliance portal. Visit compliance.microsoft.com and log in with a user account enabled to configure your organization's policy.
Once logged in, find the audit tab in the left side pane. Click on the tab to access the audit log retention setup page.
To create a policy, you need to fill in the policy name, description, duration, priority, users, and record type fields. Every field is required except the users and record type fields, which are interdependent. You can skip filling in the user field if you specify the record type for the policy.
Did you know? According to research, 50% of Microsoft 365 users are not managed by default security policies. Read more here.
Rules for setting up Microsoft 365 audit log retention policies
Policy creation limits.
Your organization can have a maximum of 50 audit log retention policies.
Special licenses for longer log retention periods
Logs are retained for 90 days/365 days, depending on your license. The E3/E1 license saves audit data for 90 days (per user).
You need an E5 license to retain an audit log for more than 90 days from the time the log was generated. If you want to retain an audit log for the maximum duration of 10 years, you will need a 10-year audit log retention add-on license in addition to an E5 license.
Depending on the industry, your company may need to keep data longer than 90 days or 365 days. This makes the 10-year audit log retention license important. If you cannot justify the cost, consider downloading and storing audit logs outside Office 365.
Your audit data will be deleted after your audit trail retention period expires. You can use the add-on 10-year storage license to keep your audit data for up to 10 years. Again, your industry determines how long you should keep your data.
Custom policy prioritization
Office 365 will honor your custom retention policy over the default retention policies in your environment. If you create a retention policy for Exchange mailbox activity that is longer than the default settings, the custom settings will override the default setting.
Audit download limit
Admins cannot download more than 50,000 event entries per download. So if your company creates between 50,000 – 100,000 events per day, you have to download the audit twice.
Audit logs can help you better govern your Microsoft 365 environment for your organization. Here are use cases for using them to implement and maintain compliance rules within the organization—ultimately helping you prevent data breaches, check fraud, and monitor performance.
Meet compliance requirements:
Office 365 audit log makes it easy for your company to file data handling reports to meet regulatory requirements. As an admin, you are responsible for ensuring compliance requirements are met in your department or across the board.
Govern your Microsoft 365 environment:
Audit logs provide a comprehensive view of activities within your Microsoft 365 environment, enabling you to identify patterns, detect anomalies, and see when certain policies are not being followed.
Watch my recent webinar on-demand for insights on how to create an action plan for governance in Microsoft 365.
Provide evidence for investigators or litigation:
Audit log reports make it easy to prosecute erring team members who leak or misuse sensitive company data. You can pull records of the employee's activity in the 365 environment and answer what, when, where, and how of the event.
Also, when investigators request specific user activity data during an investigation, you can provide an accurate report. In the EU, companies are required to provide the information requested by a reliable institution for an ongoing investigation.
Investigate a compromised account:
Using Audit log eliminates guesswork when investigating a compromised account.
Admins are responsible for filling in reports when a breach occurs, and these reports need to be as clear as day. You can rely on audit logs for information to create a detailed report for investigation.
Understand product adoption and ROI on investment:
Audit logs product usage insights allows you to review a product's adoption level and determine the ROI.
Purchasing an Office 365 service is a significant investment that must be justified in business use. You can use the Office 365 audit log to determine how your team is getting value from a service.
Ensure data sovereignty:
You can use Office 365 audit log to get detailed information about access to company data from an unauthorized location.
If your company operates in a country with data sovereignty laws, you must monitor where users access company data. An employee on holiday outside the country shouldn't access geo-restricted data.
Recommended security events to monitor and audit in Microsoft 365
From my 16 years of experience in Microsoft and IT, these are the top security events I recommend you to monitor. Auditing these events regularly will help your organization ensure better governance, compliance and security for Microsoft 365.
See how to automate governance to monitor and enforce policies with CoreView.
1. Changes to important roles
APT29 , also known as Cozy Bear, has been actively pursuing M365 deployments since 2022. In order to access Microsoft 365 resources covertly, the gang is disabling Microsoft Purview in order to gain admin rights and attack from within.
That is why it is important that administrators need to know when changes are made to important roles. To find this information, they can visit the Azure portal, and perform a search on the Core Directory service and RoleManagement categories, which will return a list of all changes to roles within their environment.
Alternatively, they can search the Unified Audit Log via the Office 365 Security & Compliance Center, which will also include the logs of all Microsoft 365 applications.
2. Changes to Groups
The main method for granting access to Active Directory resources is through groups. Additional group kinds are supported by Azure AD .
Users can make their own groups and add other users to them while using programs like Teams and Outlook, for instance. Users occasionally form groups to facilitate more effective communication with customers, suppliers, and business partners, which raises the risk of unintentional disclosure of sensitive information.
Go to the Azure portal and choose either the Directory service or GroupManagement categories under the Audit logs section to identify group changes in Azure AD.
PULL BOX: “Coreview gives the subsidiaries of large groups autonomy in the administration of M365 subscriptions, while reducing risk.” Read the rest of the review here .
3. Changes to applications
Multiple bridges between apps and services, including those hosted on-premises, are maintained by Azure AD. This introduces failure spots while also being a tool for collaboration and communication.
Any improperly configured applications could end up being highly disruptive, especially if customers can't access the business' website or make payments, or if staff can't use the apps they need to do their jobs. As a result, it is necessary to be able to recognize and react to changes in applications in order to avoid potential downtime and lost income.
In the Azure portal, you can view the audit logs for each application you have installed. Most audit events come from either the ApplicationManagement or UserManagement categories, although you may need to drill through numerous events in order to find the ones that are relevant to you.
4. Resource creation
When a user creates a Teams site, a number of additional resources are also created, such as Outlook calendars and group inboxes, a OneNote notebook, a SharePoint site, and more.
As one might anticipate, the fact that resources are being created automatically "under the hood" can pose a security risk if administrators are unaware of them or don't keep a close eye on them.
You can find the audit logs relating to the creation of resources in the Azure portal, by searching the UserManagement and GroupManagement categories under the Azure Active Directory section. Alternatively, you can search the Unified Audit Log in the Office 365 Security & Compliance Center, which will list all resources that are created and modified.
5. Sharing important files and anonymous links
The open sharing capabilities of both SharePoint Online and OneDrive for Business introduce a number of security risks, as it makes it a lot easier to accidentally share sensitive data with the wrong recipients.
To make matters worse, users are sometimes allowed to share a link to a document containing sensitive data, which external users can access anonymously.
Check out these tips for managing external users in your Microsoft 365 tenant. Download now .
In addition to monitoring the audit logs for anomalous sharing practices, it is generally a good idea to restrict the sharing capabilities of both platforms.
To find events relating to file sharing and access request activities in SharePoint and OneDrive you will need to search the Unified Audit Logs in the Office 365 Security & Compliance Center.
6. Guest access in Teams
As above, the ability for users to grant “Guest access” in Teams is another area that needs close attention.
In the wake of the pandemic, many organizations were scrambling to switch to a remote working model, and thus many chose to use Teams for remote collaboration and communication.
With that shift came a plethora of security challenges. Few organizations had spent the time to carefully review the sharing settings, and thus prevent users from inviting guests – some of whom may be granted full access to Team’s files, chats, meetings, and so on.
To find a list of all Guest users (or user creation events), search the Unified Audit Log in the Office 365 Security & Compliance Center. You can also limit the search by date range. Alternatively, in the Azure portal you can perform a search using the following filters:
- Service — Core Directory
- Category — UserManagement
- Activity — Add user
7. Teams being created or deleted
In addition to monitoring Guest access in Teams, you will also want to keep a close eye on which Teams are being created and deleted. By default, users are granted the ability to create and delete Teams, as and when they choose.
While it is possible to disable this functionality, doing so will hinder collaboration. Not only that, but administrators may also want to create and delete Teams themselves, and those actions will also need to be monitored. Unfortunately, there’s no distinction between Microsoft 365 groups created by Teams, and other groups in Azure AD.
However, in the Azure portal you can narrow down the results by setting the Service to Core Directory and the Category to GroupManagement. As always, you can also search the Unified Audit Log in the Office 365 Security & Compliance Center, although this will take longer, and you will still need to filter the Microsoft 365 groups to find out which teams were created/deleted.
Looking for an alternative way to manage and secure Microsoft Teams? See how CoreView helps organizations with Teams governance and compliance .
8. Forwarding inbound email messages
Forwarding inbound email messages is a perfectly sound practice.
That said, it is generally a good idea for administrators to keep track of changes to email forwarding, as malicious actors will sometimes set up auto-forwarding on email accounts that they have compromised.
The problem, however, is that neither Azure AD nor Microsoft 365 allow administrators to monitor these changes in the audit logs. Instead, they must export the full Exchange Online audit logs as a CSV file, and search for {“name”:”DeliverToMailboxAndForward”,”value”:”True”}.
9. Non-owner mailbox activity
It is not uncommon for a member of the technical support team to access mailbox accounts that are not theirs, and in some cases, employees use shared mailbox accounts.
Likewise, administrators could easily grant themselves access to an executive’s account and snoop around.
Whatever the scenario, it’s generally not a good idea to allow users to access mailbox accounts that don’t belong to them, and if you do, be sure to monitor them for suspicious activity.
Mailbox events can only be found in the Unified Audit Log, which allows you to view the following events;
- Sent message using Send On Behalf permission
- Added or removed user with delegate access to calendar/folder
- Sent message using Send As permission
- Added delegate mailbox permission
- Removed delegate mailbox permission
“Coreview is an easy to use Microsoft 365 license and governance management tool.” Read the full review on G2 .
10. Failed sign-in attempts
It is crucially important that you monitor all failed sign-in attempts, as attackers will frequently try to brute-force account passwords.
To see a list of failed sign-in attempts, go to the Sign-ins screen under Monitoring, and select Failure from the Status drop-down menu. Then, you will need to scrutinize each of the listed sign-in events for malicious activity
What are audit logs?
Audit logs are an internal record of events that take place in your M365 environment. They show administrators what, who, where, when, and how of any event (user action) in their environment.
These events can be all sorts of things, such as administrative actions like changes in tenant configuration settings in Exchange and SharePoint and user actions like page and file views throughout the system.
They are collected from services within your M365 environment independently from each other, and so they contain distinct information according to their source. For example, audit logs collected from SharePoint sites include the following information:
- Items that have been edited
- Items that have been checked in and checked out
- Items that have been moved or copied to other locations in the site collection
- Items that have been deleted or restored
- Changes to content types and columns
- Search queries
- Changes to user accounts and permissions
- Changed audit settings and deleted audit log events
- Workflow events
- Custom events
By default, audit logging is turned on for Office 365 and Microsoft 365 enterprise organizations. That means you can review past user actions in your tenant if you've never done so. Since it can be turned off by a global administrator, only trusted senior managers should have global admin access.
When audit logs are enabled, user and admin activity within your M365 environment is collected and stored for 90 days, and potentially longer depending on your license type.
Microsoft 365 audit log features
Office 365 audit trail offers an array of functions compared to the SharePoint audit logs. It collates the audit logs of all the apps in your environment in one unified, searchable log.
As an admin, you can view the logs for SharePoint, One Drive, Azure AD, Teams, etc. You will find the audit logs for your organization in Office 365 security & compliance center.
Over 999 event types recorded: Microsoft 365 audit log captures about 1000 event types in an environment, including edit, share, create a folder, file download, etc.
100s of metadata stored: Office 365 shares what, when, where, how, and who for every event in your environment. It also shares granular information such as the IP, location, username, time zone, and browser of the user who performed an action under review.
An alternative solution to audit and govern Microsoft 365
Microsoft has an array of tools to help you govern and secure Microsoft 365. But, that still means you must be proactive when monitoring and managing your environment with the tools available.
Adopting CoreSuite is a simpler and resource-efficient approach to using Office 365 service optimally. With CoreSuite, you can:
- Monitor and alert IT admins if something unusual occurs with advanced auditing & incident response
- Ensure ongoing compliance with both internal and external policies and regulations with continuous monitoring and alerting
- Prevent future security threats with automated resolution
Learn how CoreView helps organizations govern Microsoft 365 with automation or explore the benefits of our advanced auditing and incident response . Or, if you’d like to see for yourself how it works, take a self-guided tour of the product today.
Explore related resources

Dialysis Provider Gets Data Analysis Under Control
Ready to make microsoft 365 work for you let us show you how..
Subscribe for Practical 365 updates
Please turn off your ad blocker and refresh the page to subscribe.
You may withdraw your consent at any time. Please visit our Privacy Statement for additional information
Azure Active Directory
Why microsoft 365 license assignment dates can be misleading.

Table of Contents
Just When Did a User Account Receive a License?
My article about using the Microsoft Graph PowerShell SDK to generate a licensing report for a tenant is quite popular. The intention of the script is to illustrate the principles of retrieving license information for Azure AD user accounts with the SDK cmdlets. It’s not to deliver a fully-finished licensing report solution. If you’re looking for a more polished report, you can either consider an ISV license management product or upgrade the script to meet your needs.
A recent comment asked about retrieving license assignment data to know when accounts receive licenses. It’s an interesting question and I’m sure it’s information that administrators might find useful in some circumstances.
Azure AD Account Properties Used by Licensing
Azure AD user accounts have two properties of interest for licensing. The first is assignedLicenses , which details the assigned licenses for the account. This example shows that the account has one license identified by an SKU and that three of the service plans are disabled (see this article for details about license management with the Microsoft Graph PowerShell SDK).
The second property is assignedPlans and contains the service plans from all assigned licenses. A service plan is a not-for-sale license component like Exchange_S_Enterprise , the Exchange Online component that’s bundled into Office 365 E3 and Office 365 E5. The assignedPlans property notes if a service plan is enabled or deleted (removed) and the assignment date. Here’s an edited version of what you might see for an account with an Office 365 E5 license:
Multiple service plans are listed for the same service. That’s because some services (like Exchange Online) are responsible for the delivery of multiple services. For example, Exchange Online delivers both email services and the information barriers service to accounts with Office 365 E5 licenses.
TEC Talk: Five Things Microsoft 365 Security Administrators Should Do in 2023
Don’t miss Tony Redmond’s free TEC Talk on March 23rd at 11:00 am EST.
Figuring Out License Assignment Dates
The assignment information for a service plan includes a timestamp. Is it therefore valid to find a service plan associated with a license and assume that its assignment date reflects when an administrator assigned the license to an account?
Regretfully, no. The problem is that the license assignment information reported by the Graph APIs doesn’t distinguish between human-initiated and system-initiated actions. Microsoft tweaks licenses all the time to add or remove service plans (for example, to introduce the Viva Engage Core service plan for products like Office 365 E3 ). These actions occur in the background and tenant administrators aren’t aware of when they happen. The APIs treat a license update performed by Microsoft as the same as when an administrator assigns a license or disables a service plan for a user account. In a nutshell, this means that the reported assignment date is valid but tells you nothing about the last time an administrator managed licenses for an account.
Figure 1 illustrates the problem. This information comes from selecting a known service plan (information protection) from the Office 365 E3 SKU and using it to report the assignment date for the license. I see accounts like Paul Robichaux whom I know received their license well before August 12, 2019.
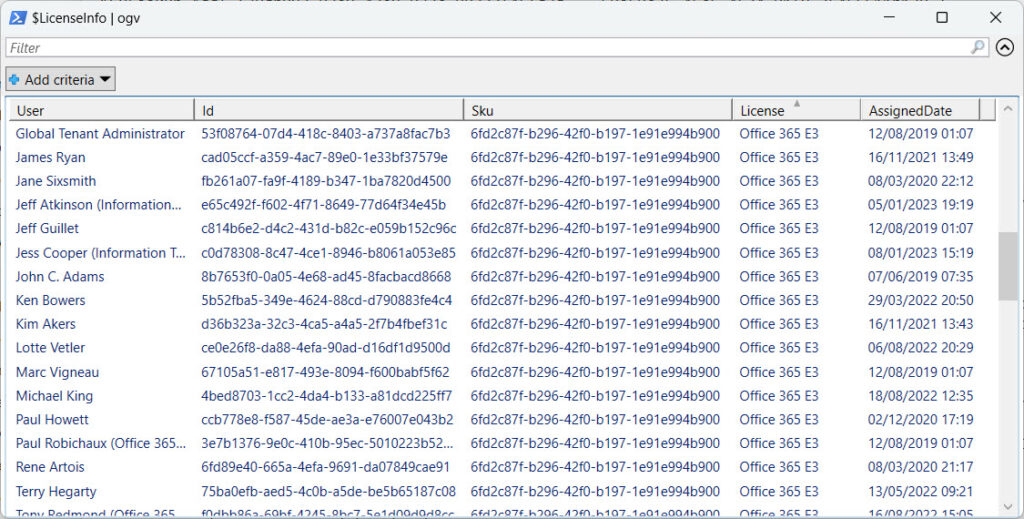
Nevertheless, the license assignment data is accurate in one sense in that someone or something assigned the license to the account on that date. The possibility that the action might have been a reassignment of a previously held license is another matter.
Tracking License Assignment Dates
To analyze license assignment dates for accounts, I wrote a script that:
- Defines a hash table of license/SKU identifier (the key) and a service plan identifier that I know exists in the SKU. For example, the Teams Premium license (989a1621-93bc-4be0-835c-fe30171d6463) includes the Teams Webinars Pro service plan (78b58230-ec7e-4309-913c-93a45cc4735b).
- Runs the Get-MgUser cmdlet to find all licensed users.
- For each user, find the set of currently enabled licenses and service plans. Then loop through the licenses to check the assigned date for a service plan that belongs to that license (that’s where the hash table comes in).
- Report the date for each user (Figure 1 shows an extract).
- The script also outputs an assignment date for each license (European dates shown).
Here’s the code. The information about product/SKU and service plan identifiers is available online .
Using the License Assignment State API
PowerShell being PowerShell, there’s usually an alternative method to explore to do something. In this instance, we can use the Graph License Assignment State API to retrieve the timestamp stored in the Graph for the last time the license assignment changed. This is a relatively new API, and its timestamps only go back to mid-2022. However, it might be an option to explore.
The Azure AD Product names and service plan identifiers for licensing page includes the option to download a CSV file containing license and service plan identifiers. Microsoft updates the CSV file regularly and it’s a useful tool to have.
In my case, I wanted to resolve product identifiers into human-understandable names, so I downloaded the file and loaded it into an array. I then selected the properties I needed, sorted them to create unique values, and loaded the data into a hash table for fast lookup. If your tenant uses some newly-introduced licenses, you might need to “patch” the data by inserting them into the table. I do this below for the Teams Premium test and Viva Suite licenses.
To find the license assignment state for a user account, we can do this:
The code generates output like:
Using the Audit Log to Track License Assignments
The audit log is the other source of information about license assignments. I’ve covered this topic previously and concluded that although the data revealed by audit events needs some work to uncover, it does tell you when administrators assigned or removed licenses from user accounts. The problem is that the audit log is only available for Office 365 E3 licenses (and above) and audit events are only available for 90 days (Office 365 E3) or 365 days (Office 365 E5). Many organizations get around this problem by offloading audit data to a SIEM like Splunk or Microsoft Sentinel .
Various Methods Exist, All Flawed
Getting back to the original question, various methods exist to track license assignments:
- Use a service plan-assigned date.
- Use the license assignment state date.
- Use the audit data.
All methods have their downsides. It would be nice if Microsoft noted a timestamp for the last administrator-initiated change for each license assigned to user accounts, but they don’t and leave the task of assignment interpretation to administrators. Just another thing to add to the list…
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!
About the Author

Tony Redmond
Where do we get the billingenddate for the subcriptions of our tenants in O365 Products without using the MsolSubscription in powershell
Billing date for subscriptions is coming (or so I hear from Microsoft)
I really wanted something like this to be native from Microsoft but found the same — automated changes by Microsoft reset the date making it an unreliable data source. I wrote a script that gathers user licensing information similar to your methods above, compares to log file from the previous run, and keeps a running date for when that subscription was initially assigned. I store everything on a SPO site and have that data going back to 2019 when I first started. It’s been VERY helpful when making additional decisions about reclamation, especially comparing to things like the Project usage report. Newly assigned license that hasn’t been used in 90 days after assignment? Older license that hasn’t been used in 180 days? Those get made available for others to use. Without knowing when the assignment occurred, those decisions can’t be made. Having the initial assignment data within a week’s worth of time has been good enough for us.
Original script was using AzureAD module, but I migrated to Microsoft Graph PowerShell SDK last year. There is probably some solution out there that would have taken care of all this for us, but this was also a great way to learn how to interact with the Microsoft Graph PowerShell SDK and serves us well, even if there is occasional maintenance needed.
Yep. This is a real pain…
Besides the audit log for User License Updated (individual changes), we would also need to check AD group membership changes and AD group assigned licenses, correct?
Yep. I cover reporting of group-based licensing in https://practical365.com/group-based-licensing-report/
Leave a Reply Cancel reply
Latest articles.

Celebrating 25 Years of Active Directory
Active Directory is now 25 years old! In this blog, we embark on a journey through the history and enduring significance of Active Directory over its lifespan, including what's to come in the future.
- Microsoft 365

All About Pagination with the Graph and the Graph PowerShell SDK
When you're new to Graph API requests, you might not know pagination and end up retrieving less data from queries than is available. In this article, we explain how to use pagination to retrieve data using Graph queries and SDK cmdlets.
- Microsoft Graph

Cloud Security News, AI, Copilots and more: The Practical 365 Podcast S4 E16
On this episode of the Practical 365 podcast, Steve Goodman and Rich Dean chat about TEC Europe 2024 and cover some of the most important topics in the world of Microsoft 365, including Entra ID Conditional Access changes to be aware of, Copilot for Security reaching GA, plus lots more.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Permissions in the Microsoft Purview compliance portal
- 1 contributor
The Microsoft Purview compliance portal supports directly managing permissions for users who perform compliance tasks in Microsoft 365. Using the new Permissions page in the compliance portal, you can manage permissions to users for compliance tasks in features like device management, Microsoft Purview Data Loss Prevention, eDiscovery, insider risk management, retention, and many others. Users can perform only the compliance tasks that you explicitly grant them access to.
To view the Permissions tab in the compliance portal, users need to be a global administrator or need to be assigned the Role Management role (a role is assigned only to the Organization Management role group). The Role Management role allows users to view, create, and modify role groups.

Permissions in the compliance portal are based on the role-based access control (RBAC) permissions model. RBAC is the same permissions model that's used by most Microsoft 365 services, so if you're familiar with the permission structure in these services, granting permissions in the compliance portal will be familiar. It's important to remember that the permissions managed in the compliance portal don't cover the management of all the permissions needed in each individual service. You'll still need to manage certain service-specific permissions in the admin center for the specific service. For example, if you need to assign permissions for archiving, auditing, and MRM retention policies, you'll need to manage these permissions in the Exchange admin center .
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview compliance portal trials hub . Learn details about signing up and trial terms .

Relationship of members, roles, and role groups
A role grants permissions to do a set of tasks; for example, the Case Management role lets users work with eDiscovery cases.
A role group is a set of roles that enable users do their jobs across compliance solutions the compliance portal. For example, by adding users to the Insider Risk Management role group, designated administrators, analysts, investigators, and auditors are configured for the necessary insider risk management permissions in a single group. The compliance portal includes default role groups for tasks and functions for each compliance solution that you'll need to assign people to. Generally, we recommend simply adding individual users as members to the default compliance role groups as needed.

Permissions needed to use features in the compliance portal
To view all of the default role groups that are available in the compliance portal and the roles that are assigned to the role groups by default, see Roles and role groups in the Microsoft Defender XDR and Microsoft Purview compliance portals .
Managing permissions in the compliance portal only gives users access to the compliance features that are available within the compliance portal. If you want to grant permissions to other features that aren't in the compliance portal, such as Exchange mail flow rules (also known as transport rules), you'll need to use the Exchange admin center .
Azure roles in the compliance portal
The roles that appear in the Microsoft Entra ID > Roles section of the compliance portal Permissions page are Microsoft Entra roles. These roles are designed to align with job functions in your organization's IT group, making it easy to give a person all the permissions necessary to get their job done. You can view the users currently assigned to each role by selecting an Admin role and viewing the role panel details. To manage members of a Microsoft Entra role, select Manage members in Microsoft Entra ID. This choice redirects you to the Azure management portal.
Administrative units
Administrative units let you subdivide your organization into smaller units, and then assign specific administrators that can manage only the members of those units. They also allow you to assign administrative units to members of role groups in Microsoft Purview solutions, so that these administrators can manage only the members (and associated features) of those assigned administrative units. Visit Administrative units for detailed information about using and configuring administrative units.
Add users or groups to a Microsoft Purview built-in role group
Complete the following steps to add users or groups to a Microsoft Purview role group:
Sign into the permissions area of the compliance portal using credentials for an admin account in your Microsoft 365 organization, and go to Permissions to select the link to view and manage compliance roles in Microsoft 365.
- Expand the Microsoft Purview solutions section and select Roles .
On the Role groups for Microsoft Purview solutions page, select a Microsoft Purview role group you want to add users to, then select Edit on the control bar.
On the Edit members of the role group page, select Choose users or Choose groups .
Security groups are supported only in Microsoft 365 commercial cloud organizations.
Select the checkbox for all users or groups you want to add to the role group.
Select Select .
If the selected users or groups need organization-wide access as part of this role group assignment, go to Step 10.
If the selected users or groups need to be assigned to administrative units, select the users or groups and select Assign admin units .
On the Assign admin units pane, select the checkbox for all the administrative units you want to assign to the users or groups. Select Select .
Select Next and Save to add the users or groups to the role group. Select Done to complete the steps.
Remove users or groups from a Microsoft Purview built-in role group
Complete the following steps to remove users or groups from a Microsoft Purview role group:
- Sign into the permissions area of the compliance portal using credentials for an admin account in your Microsoft 365 organization, and go to Permissions to select the link to view and manage the Microsoft Purview compliance roles.
- On the Role groups for Microsoft Purview solutions page, select a Microsoft Purview role group you want to remove users or groups from, then select Edit on the control bar.
- On the Edit members of the role group page, select the checkbox for all users or groups you want to remove to the role group.
- Select Remove members , then select Next .
- Select Save to remove the users or groups from the role group. Select Done to complete the steps.
Create a custom Microsoft Purview role group
Complete the following steps to create a custom Microsoft Purview role group:
- Sign into the permissions area of the compliance portal using credentials for an admin account in your Microsoft 365 organization, and go to Permissions .
On the Role groups for Microsoft Purview solutions page, select Create role group .
On the Name the role group page, enter a name for the custom role group in the Name field. The name of the role group can't be changed after creation of the role group. If needed, enter a description for the custom role group in the Description field. Select Next to continue.
On the Add roles to the role group page, select Choose roles .
Select the checkboxes for the roles to add to the custom role group. Select Select .
Select Next to continue.
On the Add members to the role group page, select Choose users (or Choose groups if applicable).
Select the checkboxes for the users (or groups) to add to the custom role group. Select Select .
If the selected users or groups need organization-wide access as part of this role group assignment, go to Step 14.
Select Next .
On the Review the role group and finish page, review the details for the custom role group. If you need to edit the information, select Edit in the appropriate section. When all the settings are correct, select Create to create the custom role group or select Cancel to discard the changes and not create the custom role group.
Update a custom Microsoft Purview role group
Complete the following steps to update a custom Microsoft Purview role group:
- On the Role groups for Microsoft Purview solutions page, select a Microsoft Purview role group you want to update, then select Edit on the control bar.
- On the Name the role group page, update the description for the custom role group in the Description field. The name of the custom role group can't be changed. Select Next .
- On the Edit roles of the role group page, you can select Choose roles to add roles to update the roles assigned to the role group. You can also select any of the currently assigned roles and select Remove roles to remove the roles from the role group. After you've updated the roles, select Next .
- On the Edit members of the role group page, you can select Choose users or Choose groups to add users or groups assigned to the role group. To update the administrative units for users or groups, select any of the currently assigned user or groups and select Assign admin units . You can also select any of the currently assigned users and groups and select Remove members to remove the users or groups from the role group. After you've updated the members, select Next .
- On the Review the role group and finish page, review the details for the custom role group. If you need to edit the information, select Edit in the appropriate section. When all the settings are correct, select Save to update the custom role group or select Cancel to discard the changes and not update the custom role group.
Delete a custom Microsoft Purview role group
Complete the following steps to delete a custom Microsoft Purview role group:
- On the Role groups for Microsoft Purview solutions page, select a Microsoft Purview role group you want to delete, then select Delete on the control bar.
- On the Delete role group dialog, select Delete to delete the role group or select Cancel to cancel the deletion process.
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Office 365 audit logs navigation guide
Last updated: March 20, 2024
14 min read
Table of contents
Office 365 Audit logs are your go-to resource if you’re interested in what’s going on in your environment, be that managing Office 365 Groups , or what’s going on with your various resources on Azure, or even who is accessing and moving files around.
In some cases, because of regulations, you might need to keep a record of the various actions that are performed on the environment. Since Office 365 has a rigid data retention period for Office 365 audit logs, you might even need to handle and store them using a custom solution.
We’ve already talked about audit logs on SharePoint On-premises in the SharePoint Audit Logs: A Key to Better SharePoint Management blog. The reasons why you might want to keep the Office 365 audit logs at hand hasn’t changed that much in the move from SharePoint On-premises to Office 365.
If we call SharePoint On-premises a complex platform, Office 365 is a huge ecosystem containing multiple interconnected services (Exchange, Teams, Azure, and OneDrive, just to name the more popular ones). Any solution that tracks Office 365 activity for the purposes of auditing must include activity made on the services that make up the platform.
Now, what options do we have when we need to do Office 365 auditing? A few, and I’ll give an overview of SharePoint’s audit log reports and Office 365 audit logs for admins.
SharePoint Online audit log reports
If you’ve worked with SharePoint On-premises and have seen its audit logs, you’ll notice a lot has stayed the same in its move to the cloud . These logs can answer most of the questions you might have regarding your SharePoint sites. The SharePoint Online audit log reports will give you information about:
- Edited items
- Checked-out and checked-in items
- Items that have been moved and copied to other locations in the site collection
- Deleted and restored items
- Changes to content types and columns
- Search queries
- Changes to user accounts and permissions
- Changed audit settings and deleted audit log events
- Workflow events
- Custom events
There is no longer an option to record opened, downloaded, and viewed items in the cloud version. I would guess that was changed in order to reduce the resource cost on Microsoft’s side since those events are the most frequently occurring and usually the least critical. But I can’t find any official article on this omission.
How to turn on Office 365 audit logs
To enable Office 365 auditing, SharePoint audit logging needs to be set up for each site collection separately , but you can automate it with a simple PowerShell script and a list of your site collections.
SharePoint Online’s audit logs have a few constraints. The minor one is that you cannot access the raw audit log data programmatically. Unlike on-premises, there is no endpoint you can connect to if you want to access the collected records to create custom reports.
You can however choose from a selection of Excel reports that should satisfy most of your needs, but you’ll have to generate reports for each site collection separately . This also means that if you want to process the data further, you’re stuck with downloading and parsing Excel documents.
The bigger constraint relates to what is not collected: everything outside of SharePoint is ignored . In an environment such as Office 365, this means many actions, such as any performed in Azure Active Directory or Exchange for instance, will not be visible here.
Note that these logs have a maximum data retention period of 90 days, which is something Syskit Point can help you with as it can store Office 365 audit logs for longer periods .
Office 365 audit logs
Office 365 audit logs capture details about system configuration changes and access events, with details to identify who was responsible for the activity, when and where the activity took place, and what the outcome of the activity was.
Where are Office 365 audit logs stored?
You can find Office 365 audit logs in the Microsoft Purview Compliance Center . While other logs are limited in scope to a particular service, these are collected from multiple Office 365 services and consolidated into a single, searchable log (and they catch page and file views).
How do I know if Office 365 audit logs are enabled?
Audit logs are enabled by default, but Microsoft still recommends checking the auditing status when setting up a new Microsoft 365 tenant.
To check if it’s turned on, navigate to the Audit log search and click the Start recording user and admin activity button if it is displayed. You will have to wait a few hours for the service to prepare itself for use, but you won’t need to do this more than once per tenant.
Once the preparation on the Office side is complete, audited events will start appearing in the log. Depending on the particular service, it can take up to 30 minutes or even up to 24 hours for an event to be shown in the audit log. Here’s the full list of audited services and actions.
How long are Office 365 audit logs kept?
As of October 17, 2023, logs are kept for 180 or 365 days, depending on the license. They can be retained for longer than the default 180 days if the user who generates the audit log (that is, the user who performs the audited activity) is assigned an Office 365 E5 of Microsoft 365 E5 license or has a Microsoft 365 E5 Compliance or E5 eDiscovery and Audit add-on license. It is possible to retain audit logs for up to 10 years, but the user must also be assigned a 10-year audit log retention add-on license in addition to an E5 license. You can find more information on audit log retention policies here .
You can export the results of a search into a CSV file to store and analyze further. The format is not made to be read by humans at a glance; it is a CSV file containing JSON objects, but that also makes it easy for processing by an application. The main issue you’ll come across is that most of the properties are lumped into an AuditData JSON, which contains very different properties depending on the audit event .
There’s also the option of programmatically downloading the audit logs for use in your solutions. This way, you can regularly download the newly available events using the available API’s, using either PowerShell or REST.
Accessing audit logs through Exchange management tools
This method is easier to use since you’ll only need to have PowerShell installed and have either the Audit Logs or View-Only Audit Logs role assigned in Exchange (global admins should have this by default).
To connect to an Exchange Online with PowerShell, this is the script you’ll want to run:
This will establish a connection to Exchange Online and allow you to run cmdlets associated with Exchange. After you’re done with the session, it’s recommended to close it using the following:
If you’re having trouble with the execution policy on your machine, you will need to first run:
The only Exchange cmdlet we’re interested in right now is Search-UnifiedAuditLog. It has a simple basic signature but allows for a lot of customization (find out more here ).
This command will return audit records for the specified date , up to a maximum of 100. You can specify a larger number of records to return, or you can use paging by specifying a SessionId and using the ReturnNextPreviewPage SessionCommand.
The returned data contains the general data about the event (RecordType, CreationData, UserIds, and Operations) and the AuditData JSON, which contains the event description and whose properties depend on the specific event type.
All the data contained in the Security & Compliance Search can be queried from here , which effectively means they share the same data retention period. This is important to note because the other method differs in this regard.
You can find more info about connecting to Exchange Online by remote PowerShell here .
Office 365 management API
This API provides access to events from Office 365 audit logs. The data available here is the same as shown in the search log, with very few differences. The major one being you can only get data for the last 7 days , while others make the data available for up to 90 days.
The audit data is made available using blobs – the service periodically collects events and organizes them into these collections (or blobs), which can then be downloaded. The events contained in the blobs are not in any particular order but are bundled up according to the time when the service collected them .
This means that an older event might appear in a very recent blob (according to Microsoft, in case of a service outage, this might mean a delay of 5 days or more). What this means is that you cannot use this service for alerts since there is no guarantee an event will be made available in a timely manner.
Of the two possible APIs to use to collect Office 365 audit logs, this one is the recommended one .
How to start collecting data?
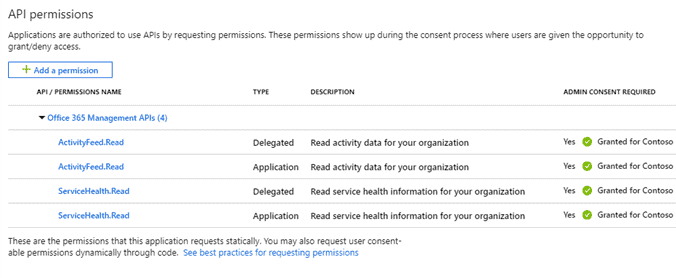
To start collecting this data, you will need to create a new application on your Azure first. Then, using that application, we’ll start subscriptions for the various event content types available. The application requires the ActivityFeed.Read and ServiceHealth.Read application and delegated permissions, and you’ll need to generate a client secret to authenticate your application.
We’ll use the client secret in the next steps, so make sure to store it somewhere.
The following examples will be written in PowerShell, but they can be easily rewritten in almost any other programming language.
Using the following script and the values of your clientId, clientSecret and tenantDomain, we’ll get an access token that we can use in subsequent calls to the API.
The headerParams attribute now contains the access token . Using this token, we’ll be able to start the subscriptions to each of the audit types (Audit.AzureActiveDirectory, Audit.Exchange, Audit.SharePoint, Audit.General, and DLP.All). To start a subscription, run this command:
To start a subscription for the other audit types, simply replace the contentType parameter value with the names of the other audit types.
You can check the activated subscriptions with the following:
Assuming the scripts ran successfully, you should now be able to query for audit blobs and download their contents like so:
This request will return a JSON object containing content uris for events that have been made available today. You can choose a different time period by specifying a startTime and endTime parameter (both need to be specified and must not span more than 24 hours).
In any case, the returned JSON object should contain uris we can use to collect events collected in the time period (remember, we don’t have a guarantee the event actually occurred in that time period, only that it was collected then). An example of such a request and uri would look like this:
This will return a collection of events in a JSON format. The events have schemas depending on the audit event type they’re describing. Microsoft has defined about two dozen different schemas (a couple more or less, depending on how you count them since a few are considered base and aren’t used independently of others). Each event will have CreationTime, RecordType, Operation, and ResultStatus properties.
According to its type, it will also have several other properties used to describe the details of the action that created the record (these extra details can be found by examining a single row in the Audit log search and expanding the More information tab). This can be anything from the user that initiated the action, where the action was made, or what the target was.
How to understand these properties?
Some of these properties are easier to make sense of than others since connecting an email to a particular user is straightforward. But it’s much less so to connect a group id to a group name or a team site id to an Office 365 Group. Microsoft has documented the schemas and their properties , but note that some record types are not officially documented.
You can find out more about the Office 365 Management API by checking out the official resources .
If we compare the PowerShell API to the REST one, we can see that the Search-UnifiedAuditLog cmdlet, with its numerous optional parameters is more suited for searching and filtering logs in search of a specific record, but not so much for collecting new records as they’re coming in since a record’s creation time is not the same time the record was made available. The REST API is much more appropriate for collecting and storing audit records. Since the collection of events in the blobs does not change, you only need to collect new blobs as they become available.
Where Syskit Point comes in
We’ve seen that finding what you’re looking for is rarely easy. Especially if you just want an overview of what’s happening with a given user or site. The default logs are verbose, and because they are generic, they tend not to focus on what is important in a given context. The filters are nice, but you need to know the exact URL of an object beforehand to view the actions associated with it.
The data retention is stingy, although understandably so since Microsoft needs to store a lot of data. And every extra day of data retention they allow means an enormous amount of extra storage space required on their end. For this and other reasons, we’ve made our own custom solution for storing, searching, and exporting Office 365 audit logs . It stores data locally, meaning you can decide how much of it you want to store and for how long.
It’s easily accessible from most reports, allowing you to easily check the audit logs related to a certain SharePoint site and the items in its document libraries, or you can easily check the list of actions made by or on a certain user . We’ve tried to make it as easy as possible to read so you can see what’s important at a glance.
Discover, secure, and control M365
Manage your company’s Microsoft 365 ecosystem with Syskit Point, a scalable platform that will help you govern and secure your environment while giving you deep visibility into your entire inventory.
Subscribe to our Newsletter
Thank you for joining our community!
Related Posts

How to manage SharePoint storage

10 advantages of using Power BI

Microsoft Teams usage report breakdown
update: 7/11/2017 If you want to quickly check a single user, see my new blog . update: 5/26/2017 BIG speed improvement thanks to NickC, who commented on my post. Also, thanks to my colleague Andy, I’ve updated the progress bar calculation so that this script can run on Windows Server 2008 R2. Thanks guys!
(You’ll need to connect to Azure AD (MSOL) prior to running this script, more info on that here .)
In Office 365, licenses (also called SKUs) give users access to various Office 365 services. Each SKU defines a list of services. However, a user might not have access to all services of a given SKU. This is typical when onboarding users to Office 365 for the first time, some organizations choose to disable certain services while leaving others enabled. Office 365 PowerShell is useful to view the status of services on a given user account. This can become tricky when dealing with user accounts that have been assigned multiple SKUs.
In addition, performing a full-service audit (all users/all skus) in PowerShell can be incredibly challenging. This is primarily due to the way Azure AD (MSOL) stores the collection SKUs for a given user. The indexing is dynamic and based on the order of SKU enablement (assignment). For example, I assign User1 with E3 first and EMS second, then the index for E3 is [0] and the index for EMS is [1]. Then for User2 I assign EMS first and E3 second, the indexing for this account is the reverse and EMS is [0] and E3 is [1].
*Note that this index assignment is consistent in both PowerShell and the UI ; however , if you enable/disable any services on a previously-assigned SKU using the UI , it will move that SKU to index [0]. If you use PowerShell, it will leave index number intact.
Many blogs which touch on this topic will hard-code the index to [0] in their PowerShell samples, and the assumption is your users have only one SKU or the SKU you care about is on index [0]. For example, blogs will say run the following to get service status for User1.(Get-MsolUser -UserPrincipalName [email protected] ).Licenses[0].ServiceStatus
In my experience nearly every organization has more than one SKU. And often there is little to no consistency in the order of enablement nor consistency on which the SKUs are assigned. For example, I worked with one organization that had several thousand users and 28 different SKUs!
I wrote this script to be able to get around the dynamic index limitation, and it will get all licensed users and list their SKUs and corresponding services (and status). I hope this helps you in managing your licenses in Office 365.
(Thank you to Andy Pituch, Rianna Richardson, and Ryan Jackson for their input on this blog)

Softwarelicensing
Office 365 License Management for Maximum Efficiency
February 29, 2024
To manage Office 365 licenses effectively:
- Monitor License Usage : Keep track of how licenses are used within your organization.
- Automate License Assignments : Use tools to assign and manage licenses efficiently.
- Utilize Third-Party Tools : Leverage specialized software for deeper management capabilities.
- Regular Audits : Conduct periodic checks to ensure optimal usage and compliance.
- Clear Policies : Establish and maintain straightforward guidelines for license use.
- Train IT Administrators : Ensure those managing licenses are well-informed and skilled.
Reduced Administrative Burden in Office 365 License Management:
Assigning licenses to users, modifying app and service access, managing guest user licenses, the importance of efficient office 365 license management.

Managing Office 365 licenses efficiently is like finding the perfect balance between cost and performance in a high-performance car.
Ensuring your organization gets the most out of its investment in Microsoft’s cloud-based productivity suite is essential.
Efficient license management can lead to significant cost savings, enhanced user experience, and reduced administrative burden.
But how can you achieve this perfect balance? Let’s dive deeper into the key areas where efficient license management can significantly impact your organization.
Cost Savings in Office 365 Licensing

- Avoid overspending by only purchasing necessary licenses.
- Regularly review and adjust license allocations.
- Utilize the “needs attention dashboard” for insights.
- Identify licenses that aren’t fully utilized.
- Eliminate redundant or unused licenses.
- Think of it as trimming excess from a high-performance car.
- Power BI supports Pro license reporting.
- Gain comprehensive insights for optimal license management.
By strategically managing your Office 365 licenses, you can significantly reduce unnecessary expenses and enhance your organization’s efficiency.

Just like regular car maintenance, Office 365 licenses require ongoing management. By optimizing and automating this process, you can:
- Streamline license management to minimize their time and effort.
- Compare it to a smart car monitoring system that signals when service is needed.
- Microsoft’s self-service alerts in the license management dashboard inform of any changes or issues.
- Conflicting license reporting detects license discrepancies, ensuring optimal allocation and reducing errors.
This approach maintains a streamlined licensing environment, like keeping a vehicle in top condition with minimal effort.
Strategies for Effective Office 365 License Management

Understanding the importance of efficient Office 365 license management, consider these strategies as tools for optimization, akin to a skilled mechanic fine-tuning a high-performance car:
- Regularly check license usage for compliance and optimal allocation.
- Use tools like the Microsoft 365 Admin Center for comprehensive oversight.
- Simplify the process, akin to using a car’s cruise control.
- Utilize PowerShell scripts, third-party tools, or the Microsoft 365 Admin Center.
Utilizing third-party tools for Office 365 license management is akin to a mechanic using specialized tools for car maintenance.
These tools enhance the management of Microsoft’s technology, improve subscription management, and augment monitoring and administrative tasks.
They offer comprehensive solutions for the complexities of Office 365 license management.
Suggested Tools for Managing Office 365 Licenses:
- CoreView : For detailed insights and management controls.
- AvePoint : Offers migration, management, and protection solutions.
- ShareGate : Useful for migration and management tasks.
Each tool provides unique capabilities to simplify and streamline the management of Office 365 licenses, addressing specific organizational needs and challenges.
Managing Licenses Through Microsoft 365 Admin Center

The Microsoft 365 Admin Center is essential for managing Office 365 licenses, akin to a car’s dashboard. This tool allows organizations to:
- Assign Licenses to Users : Equipping employees with necessary tools and services, like handing over car keys.
- Unassign Licenses : Remove licenses from inactive users and reallocate resources efficiently.
- Modify Access : Tailoring app and service access for optimal license usage.
Regularly reviewing and updating these assignments ensures a cost-effective and efficient licensing environment, maintaining optimal operation like a well-tuned high-performance car.
Assigning licenses in the Microsoft 365 Admin Center ensures employees have the necessary tools. This process, similar to handing over car keys, involves:
- Selecting the user in the Admin Center.
- Choosing ‘Licenses and Apps’.
- Expanding the Licenses section.
- Selecting licenses for assignment.
- Saving changes.
This method ensures efficient license allocation. Additionally, the Licenses page in the Admin Center provides valuable information about your products, helping to manage and optimize license distribution effectively.
Unassigning Licenses from Users in Microsoft 365 Admin Center:
- Remove licenses from inactive users, like reallocating car resources.
- Use either the Active User’s page or the Licenses page.
- Ensure no payment for unused licenses.
- Leads to a cost-effective licensing environment.
This streamlined approach ensures your organization only uses and pays for the licenses it needs, maintaining efficiency and cost-effectiveness.
Modifying app and service access for users in Office 365 is like fine-tuning the settings on your high-performance car to achieve optimal performance.
It allows organizations to ensure that users only have access to the apps and services they need, ultimately improving security and productivity.
To modify app and service access for users in the Microsoft 365 admin center, simply select the user from the list of users, select the app or service to remove access or be modified, and then click the “Modify” button.
By regularly reviewing and updating app and service access for users, organizations can ensure that their workforce can access the tools and services they need while minimizing the risk of data breaches and unauthorized access.
Overcoming Common Office 365 License Management Challenges

Office 365 license management can be complex and challenging, much like navigating the twists and turns of a racetrack in a high-performance car.
However, organizations can optimize their licensing environment and achieve better results by understanding and addressing common challenges.
In this section, we’ll discuss some of the common Office 365 license management challenges, such as aligning licensing costs with business units, ensuring license compliance, and managing guest user licenses, and explore how organizations can overcome these challenges to drive greater efficiency and success in their Office 365 licensing efforts.
By implementing the strategies and best practices outlined in this blog post, organizations can successfully navigate the complexities of Office 365 license management and overcome common challenges.
Aligning Licensing Costs with Business Units
One of the organization’s most significant challenges when managing Office 365 licenses is aligning licensing costs with business units.
This challenge is akin to fine-tuning the fuel consumption of your high-performance car to ensure that each component is operating at peak efficiency.
To effectively align licensing costs with business units, organizations must clearly understand their current and projected needs to assign licenses, assess their existing licenses and license inventory, and identify the most cost-effective licensing solution.
Monitoring license usage, automating license assignments, and utilizing third-party tools effectively align licensing costs with business units.
By implementing these strategies, organizations can ensure that they only pay for the licenses they need, optimize their license allocation, and ultimately reduce overall Office 365 licensing expenses.
Ensuring License Compliance
Ensuring license compliance is like adhering to the rules of the road in your high-performance car. It can help organizations avert potential legal issues and financial penalties, streamline licensing costs, and monitor software usage.
To ensure license compliance, organizations can conduct regular license audits, establish clear license policies, and provide training to IT administrators.
By implementing these best practices, organizations can avoid the pitfalls of non-compliance and ensure that their Office 365 licensing environment remains compliant and cost-effective.
Managing guest user licenses in Office 365 is like accommodating passengers in your high-performance car. It requires organizations to have enough licenses to provide access to necessary tools, turns, apps, and services for external users while maintaining security and compliance.
Organizations can effectively manage guest user licenses, assign licenses to users, unassign licenses from users, modify the app and service access, and ensure license compliance.
By implementing these strategies, organizations can optimize their guest user licensing environment, ensuring that external users can access the tools and services they need while minimizing the risk of data breaches and unauthorized access.
Best Practices for Office 365 License Management

- Like routine car maintenance, audits ensure licensing compliance, cost-effectiveness, and optimal usage.
- Identify and redistribute unused licenses, preventing unnecessary expenses.
- Create explicit guidelines, like setting driving rules, to avoid ambiguity and ensure adherence to licensing agreements.
- Equip them with the skills to manage the licensing environment effectively, akin to providing expert driving lessons for optimal car performance.
- Incorporate a mix of on-the-job training, online courses, and mentoring.
By implementing these practices, organizations can enhance the efficiency and compliance of their Office 365 licensing, ensuring peak operational performance.
Effective Office 365 license management is crucial for both efficiency and cost-effectiveness in organizations.
The critical advice includes:
- Regular License Audits : Ensuring compliance and optimal usage.
- Clear Licensing Policies : Setting guidelines for usage and compliance.
- Training for IT Administrators : Empowering them with the skills to manage licenses effectively.
Adopting these strategies leads to a well-maintained and efficiently operated Office 365 environment.
Frequently Asked Questions
How do i manage my office 365 licenses.
Managing Office 365 License is an easy process. From the Microsoft account dashboard, go to Services & Subscriptions, then view all of the associated products.
Then in the Microsoft 365 admin center, go to Billing > Licenses. Select the license type and appropriate subscription on the Licenses page and assign the license to the user account. You can manage your Office 365 Licenses quickly and efficiently in just a few steps.
How do I check my Office 365 license?
You can quickly check your Office 365 license by accessing the Billing section in the Office 365 Admin Portal. From there, click on Licenses to view a real-time report of the total number of your active subscriptions and how many licenses are automatically assigned.
What is the difference between Office 365 and Microsoft 365 Licenses?
The main difference between Office 365 and Microsoft 365 is that Office 365 is a cloud-based suite of productivity apps with services included. At the same time, Microsoft 365 is a bundle of services, including Office 365 plus additional features. In short, Office 365 provides productivity applications, while Microsoft 365 provides productivity and other services.
What is the difference between Microsoft 365 E3 and EMS E3?
Microsoft 365 E3 includes Windows 10 Enterprise E3, which is not included in Office 365 E3 + EMS E3. Windows 10 Enterprise E3 allows organizations to take advantage of more advanced security features, deployment methods, compatibility methods, and productivity features than Office 365 E3 + EMS E3 offers.
How do I view Licenses in Office 365 Admin Center?
To view your Office 365 licensing information, simply visit the Billing > Licenses page in the Office 365 Admin Center. From there, you can check your assigned and unassigned licenses and review which users are licensed, unlicensed, or guests in an associated office here.

Fredrik Filipsson brings two decades of Oracle license management experience, including a nine-year tenure at Oracle and 11 years in Oracle license consulting. His expertise extends across leading IT corporations like IBM, enriching his profile with a broad spectrum of software and cloud projects. Filipsson's proficiency encompasses IBM, SAP, Microsoft, and Salesforce platforms, alongside significant involvement in Microsoft Copilot and AI initiatives, enhancing organizational efficiency.
View all posts

Update License Button
What is the update license button what does it do .
The Update License button appears in the backstage when clicking on the File menu, between the Account and Feedback buttons. When clicking on the Update License button, the user will be guided through a few simple steps to ensure the license on the device is up to date. This may be useful immediately after a new purchase or entitlement occurs.
Why is it showing up? Does this mean my license is out of date?
The Update License button appears in all Microsoft 365 Apps beginning with version 2401 (Build 17231.20194). The button is always visible, and its presence does not imply that the current license is out of date.
Normally the product license for Microsoft 365 Apps will be refreshed in the background automatically, but it can take up to 72 hours for new purchases or entitlements to be reflected on client devices. The Update License button is a quick and convenient way to immediately update the license.
Why am I asked to sign in?
Signing in is required to ensure that the license update process uses the correct identity.
Why do I need to restart my apps?
Closing all apps and restarting ensures that all apps have access to the current license.
How do I know if the license update was successful?
If successful, the license update process will prompt to restart any Microsoft 365 apps that are open. If there was an issue obtaining an updated license, a dialog will be shown with an error message and error code.
To confirm the product license currently in use in any Microsoft 365 App, open the File menu and choose Account . Under Product Information, the name of the currently licensed product and included apps will be shown.

Need more help?
Want more options.
Explore subscription benefits, browse training courses, learn how to secure your device, and more.

Microsoft 365 subscription benefits

Microsoft 365 training

Microsoft security

Accessibility center
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge.

Ask the Microsoft Community

Microsoft Tech Community

Windows Insiders
Microsoft 365 Insiders
Was this information helpful?
Thank you for your feedback.

IMAGES
VIDEO
COMMENTS
Here is Search the audit log in the Office 365 Security & Compliance Cente r for your reference. Besides, if the issue occurs again, I would like to collect following information: 1.Are these users Online users or local AD users? 2.What licenses do they have before these license lost? Regards, Eli
This is a quick video to show how you can check user license changes record in Audit log. Microsoft 365 Compliance URL -https://compliance.microsoft.com/audi...
A message was sent, replied to or forwarded. This activity is only logged for users with an Office 365 or Microsoft 365 E5 license. For more information, see Audit (Premium). Sent message using Send As permissions: SendAs: A message was sent using the SendAs permission. This means that another user sent the message as though it came from the ...
The audit events generated for license assignments to user accounts available in the Azure AD audit log and Office 365 audit log are inconsistent and incomplete. Subscribe for Practical 365 updates ... This seems to be yet another example where the Azure AD Audit logs failed to capture the required audit events for license assignments. A week ...
Go to the Microsoft 365 Admin Center and select the security tab in the left pane. Click on the audit button to open the audit log page. You can search the audit log based on time, activities, and users. Enter and select the suspected user's name in the user field, choose a date range, and specify an activity to filter for.
I tried to assign a license to an account in my testbed - I can see the license being assigned under the specific user Audit logs and the actor is my admin account ... That's all he would need to ask. He wouldn't be looking for M365 Support to speak into the actual Audit History. I do agree that M365 Support can be a bit slow in final ...
The basic steps in generating a report are in two stages. First, we create two data (CSV) files containing: The product licenses (SKUs) used in the tenant. The service plans belonging to the product licenses. A service plan is something like Exchange Online Plan 2 or Teams which is bunded in a product license like Office 365 E3.
The problem is that the audit log is only available for Office 365 E3 licenses (and above) and audit events are only available for 90 days (Office 365 E3) or 365 days (Office 365 E5). Many organizations get around this problem by offloading audit data to a SIEM like Splunk or Microsoft Sentinel. Various Methods Exist, All Flawed
Sign into the permissions area of the compliance portal using credentials for an admin account in your Microsoft 365 organization, and go to Permissions. Expand the Microsoft Purview solutions section and select Roles. On the Role groups for Microsoft Purview solutions page, select Create role group.
Discover, secure, and control M365. Manage your company's Microsoft 365 ecosystem with Syskit Point, a scalable platform that will help you govern and secure your environment while giving you deep visibility into your entire inventory. Office 365 is a huge ecosystem. This blog post will help you navigate Office 365 audit logs and gain insight ...
Office 365 PowerShell is useful to view the status of services on a given user account. This can become tricky when dealing with user accounts that have been assigned multiple SKUs. In addition, performing a full-service audit (all users/all skus) in PowerShell can be incredibly challenging.
To effectively manage Office 365 licenses: Identify Needs: Determine the specific requirements of your organization. Choose the Right License: Select licenses based on these needs. Purchase License: Buy licenses from Microsoft or its partners. Assign Licenses: Allocate them to users through the Office 365 admin center.
To manage Office 365 licenses effectively:. Monitor License Usage: Keep track of how licenses are used within your organization.; Automate License Assignments: Use tools to assign and manage licenses efficiently.; Utilize Third-Party Tools: Leverage specialized software for deeper management capabilities.; Regular Audits: Conduct periodic checks to ensure optimal usage and compliance.
6 Spice ups. user827215 (CMD88) January 28, 2022, 7:47am 2. You should be able to use the audit log feature in Azure Active Directory to track licensing changes. That said, you really, really need to set up separate logins for you and the helpdesk contact. Ideally with using PIM to give just-in-time access too.
The Update License button appears in the backstage when clicking on the File menu, between the Account and Feedback buttons. When clicking on the Update License button, the user will be guided through a few simple steps to ensure the license on the device is up to date. This may be useful immediately after a new purchase or entitlement occurs.